Chapter 5
Identity and Access Management (Domain 5)
- Which of the following is best described as an access control model that focuses on subjects and identifies the objects that each subject can access?
- An access control list
- An implicit denial list
- A capability table
- A rights management matrix
- Jim's organization-wide implementation of IDaaS offers broad support for cloud-based applications. Jim's company does not have internal identity management staff and does not use centralized identity services. Instead, they rely upon Active Directory for AAA services. Which of the following options should Jim recommend to best handle the company's on-site identity needs?
- Integrate on-site systems using OAuth.
- Use an on-premises third-party identity service.
- Integrate on-site systems using SAML.
- Design an internal solution to handle the organization's unique needs.
- Which of the following is not a weakness in Kerberos?
- The KDC is a single point of failure.
- Compromise of the KDC would allow attackers to impersonate any user.
- Authentication information is not encrypted.
- It is susceptible to password guessing.
- Voice pattern recognition is what type of authentication factor?
- Something you know
- Something you have
- Something you are
- Somewhere you are
- If Susan's organization requires her to log in with her username, a PIN, a password, and a retina scan, how many distinct authentication factor types has she used?
- One
- Two
- Three
- Four
- Charles wants to deploy a credential management system (CMS). He wants to keep the keys as secure as possible. Which of the following is the best design option for his CMS implementation?
- Use AES-256 instead of 3DES.
- Use long keys.
- Use an HSM.
- Change passphrases regularly.
- Brian is a researcher at a major university. As part of his research, he logs into a computing cluster hosted at another institution using his own university's credentials. Once logged in, he is able to access the cluster and use resources based on his role in a research project, as well as using resources and services in his home organization. What has Brian's home university implemented to make this happen?
- Domain stacking
- Federated identity management
- Domain nesting
- Hybrid login
- Place the following steps in the order in which they occur during the Kerberos authentication process.
- Client/server ticket generated
- TGT generated
- Client/TGS key generated
- User accesses service
- User provides authentication credentials
- 5, 3, 2, 1, 4
- 5, 4, 2, 1, 3
- 3, 5, 2, 1, 4
- 5, 3, 1, 2, 4
- What major issue often results from decentralized access control?
- Access outages may occur.
- Control is not consistent.
- Control is too granular.
- Training costs are high.
- Callback to a landline phone number is an example of what type of factor?
- Something you know
- Somewhere you are
- Something you have
- Something you are
- Kathleen needs to set up an Active Directory trust to allow authentication with an existing Kerberos K5 domain. What type of trust does she need to create?
- A shortcut trust
- A forest trust
- An external trust
- A realm trust
- Which of the following AAA protocols is the most commonly used?
- TACACS
- TACACS+
- XTACACS
- Super TACACS
- Which of the following is not a single sign-on implementation?
- Kerberos
- ADFS
- CAS
- RADIUS
- As shown in the following image, a user on a Windows system is not able to use the Send Message functionality. What access control model best describes this type of limitation?
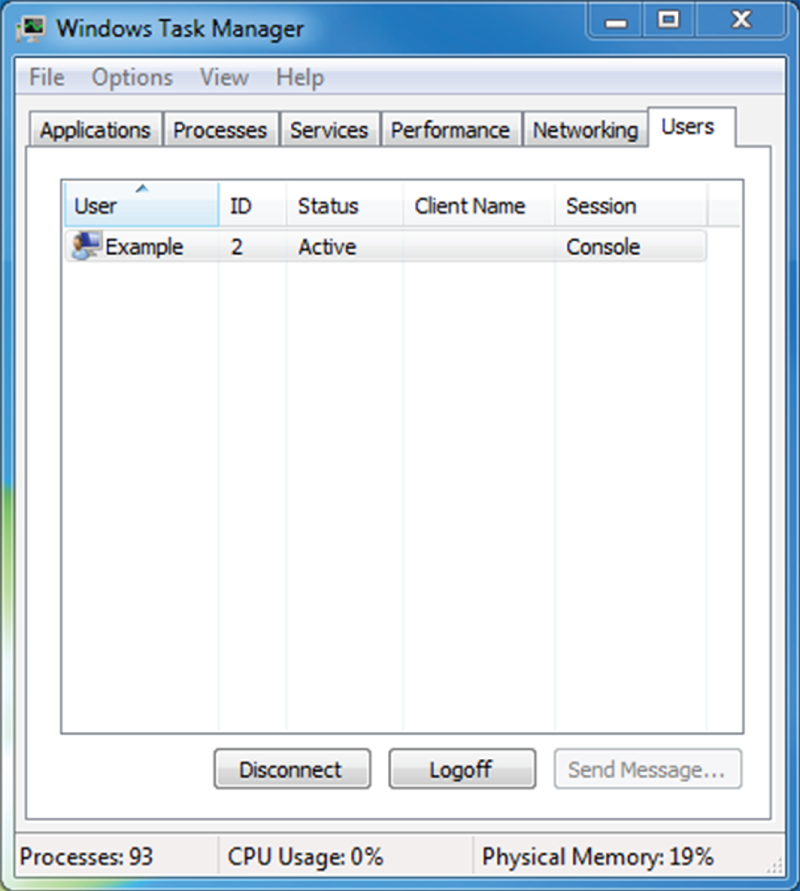
- Least privilege
- Need to know
- Constrained interface
- Separation of duties
- What type of access controls allow the owner of a file to grant other users access to it using an access control list?
- Role-based
- Nondiscretionary
- Rule-based
- Discretionary
- Alex's job requires him to see protected health information (PHI) to ensure proper treatment of patients. His access to their medical records does not provide access to patient addresses or billing information. What access control concept best describes this control?
- Separation of duties
- Constrained interfaces
- Context-dependent control
- Need to know
For questions 17–19, please use your knowledge of the Kerberos logon process and refer to the following diagram:

- At point A in the diagram, the client sends the username and password to the KDC. How is the username and password protected?
- 3DES encryption
- TLS encryption
- SSL encryption
- AES encryption
- At point B in the diagram, what two important elements does the KDC send to the client after verifying that the username is valid?
- An encrypted TGT and a public key
- An access ticket and a public key
- An encrypted, time-stamped TGT and a symmetric key encrypted with a hash of the user's password
- An encrypted, time-stamped TGT and an access token
- What tasks must the client perform before it can use the TGT?
- It must generate a hash of the TGT and decrypt the symmetric key.
- It must accept the TGT and decrypt the symmetric key.
- It must decrypt the TGT and the symmetric key.
- It must send a valid response using the symmetric key to the KDC and must install the TGT.
- Jacob is planning his organization's biometric authentication system and is considering retina scans. What concern may be raised about retina scans by others in his organization?
- Retina scans can reveal information about medical conditions.
- Retina scans are painful because they require a puff of air in the user's eye.
- Retina scanners are the most expensive type of biometric device.
- Retina scanners have a high false positive rate and will cause support issues.
- Mandatory access control is based on what type of model?
- Discretionary
- Group-based
- Lattice-based
- Rule-based
- Greg wants to control access to iPads used throughout his organization as point-of-sale terminals. Which of the following methods should he use to allow logical access control for the devices in a shared environment?
- Use a shared PIN for all point-of-sale terminals to make them easier to use.
- Use OAuth to allow cloud logins for each user.
- Issue a unique PIN to each user for the iPad they are issued.
- Use Active Directory and user accounts for logins to the iPads using the AD userID and password.
- What is the best way to provide accountability for the use of identities?
- Logging
- Authorization
- Digital signatures
- Type 1 authentication
- Jim has worked in human relations, payroll, and customer service roles in his company over the past few years. What type of process should his company perform to ensure that he has appropriate rights?
- Re-provisioning
- Account review
- Privilege creep
- Account revocation
- Biba is what type of access control model?
- MAC
- DAC
- Role BAC
- ABAC
- Which of the following is a client/server protocol designed to allow network access servers to authenticate remote users by sending access request messages to a central server?
- Kerberos
- EAP
- RADIUS
- OAuth
- Henry is working with a web application development team on their authentication and authorization process for his company's new application. The team wants to make session IDs as secure as possible. Which of the following is not a best practice that Henry should recommend?
- The session ID token should be predictable.
- The session ID should have at least 64 bits of entropy.
- The session length should be at least 128 bits.
- The session ID should be meaningless.
- Angela uses a sniffer to monitor traffic from a RADIUS server configured with default settings. What protocol should she monitor, and what traffic will she be able to read?
- UDP, none. All RADIUS traffic is encrypted.
- TCP, all traffic but the passwords, which are encrypted.
- UDP, all traffic but the passwords, which are encrypted.
- TCP, none. All RADIUS traffic is encrypted.
- What type of access control best describes NAC's posture assessment capability?
- A mandatory access control
- A risk-based access control
- A discretionary access control
- A role-based access control
- When an application or system allows a logged-in user to perform specific actions, it is an example of what?
- Roles
- Group management
- Logins
- Authorization
- Alex has been employed by his company for more than a decade and has held a number of positions in the company. During an audit, it is discovered that he has access to shared folders and applications because of his former roles. What issue has Alex's company encountered?
- Excessive provisioning
- Unauthorized access
- Privilege creep
- Account review
- Geoff wants to prevent privilege escalation attacks in his organization. Which of the following practices is most likely to prevent horizontal privilege escalation?
- Multifactor authentication
- Limiting permissions for groups and accounts
- Disabling unused ports and services
- Sanitizing user inputs to applications
- Jim's Microsoft Exchange environment includes servers that are located in local data centers at multiple business offices around the world as well as an Office 365 deployment for employees who are not located at one of those offices. Identities are created and used in both environments and will work in both. What type of federated system is Jim running?
- A primary cloud system
- A primary on-premise system
- A hybrid system
- A multitenant system
- What type of access control scheme is shown in the following table?
Highly Sensitive Red Blue Green Confidential Purple Orange Yellow Internal Use Black Gray White Public Clear Clear Clear - RBAC
- DAC
- MAC
- TBAC
- Michelle's company is creating a new division by splitting the marketing and communications departments into two separate groups. She wants to create roles that provide access to resources used by each group. What should she do to maintain the appropriate security and rights for each group?
- Put both the marketing and communications teams into the existing group because they will have similar access requirements.
- Keep the marketing team in the existing group and create a new communications group based on their specific needs.
- Keep the communications team in the existing group and create a new marketing group based on their specific needs.
- Create two new groups, assess which rights they need to perform their roles, and then add additional rights if required.
- When a subject claims an identity, what process is occurring?
- Login
- Identification
- Authorization
- Token presentation
- Dogs, guards, and fences are all common examples of what type of control?
- Detective
- Recovery
- Administrative
- Physical
- Susan's organization is updating its password policy and wants to use the strongest possible passwords. What password requirement will have the highest impact in preventing brute-force attacks?
- Change maximum age from 1 year to 180 days.
- Increase the minimum password length from 8 characters to 16 characters.
- Increase the password complexity so that at least three character classes (such as uppercase, lowercase, numbers, and symbols) are required.
- Retain a password history of at least four passwords to prevent reuse.
- Alaina is performing a regularly scheduled review for service accounts. Which of the following events should she be most concerned about?
- An interactive login for the service account
- A password change for the service account
- Limitations placed on the service account's rights
- Local use of the service account
- When might an organization using biometrics choose to allow a higher FRR instead of a higher FAR?
- When security is more important than usability
- When false rejection is not a concern due to data quality
- When the CER of the system is not known
- When the CER of the system is very high
- After recent reports of undesired access to workstations after hours, Derek has been asked to find a way to ensure that maintenance staff cannot log in to workstations in business offices. The maintenance staff members do have systems in their break rooms and their offices for the organization, which they still need access to. What should Derek do to meet this need?
- Require multifactor authentication and only allow office staff to have multifactor tokens.
- Use rule-based access control to prevent logins after hours in the business area.
- Use role-based access control by setting up a group that contains all maintenance staff and then give that group rights to log into only the designated workstations.
- Use geofencing to only allow logins in maintenance areas.
- Nick wants to do session management for his web application. Which of the following are common web application session management techniques or methods? (Select all that apply.)
- IP tracking
- Cookies
- URL rewriting
- TLS tokens
For questions 43–45, please use your knowledge of SAML integrations and security architecture design and refer to the following scenario and diagram:
Alex is in charge of SAML integration with a major third-party partner that provides a variety of business productivity services for his organization.
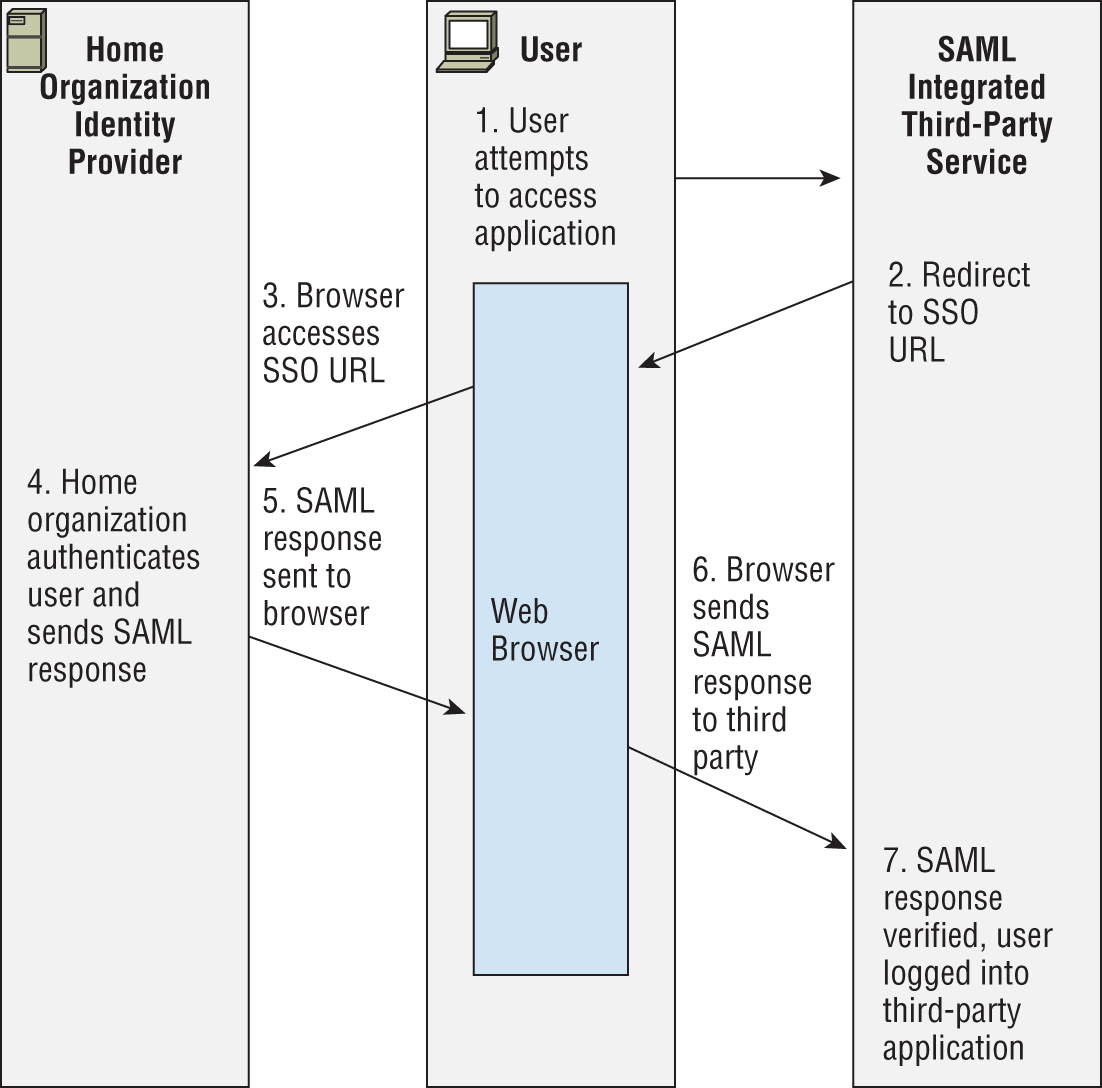
- Alex is concerned about eavesdropping on the SAML traffic and also wants to ensure that forged assertions will not be successful. What should he do to prevent these potential attacks?
- Use SAML's secure mode to provide secure authentication.
- Implement TLS using a strong cipher suite, which will protect against both types of attacks.
- Implement TLS using a strong cipher suite and use digital signatures.
- Implement TLS using a strong cipher suite and message hashing.
- If Alex's organization is one that is primarily made up of off-site, traveling users, what availability risk does integration of critical business applications to on-site authentication create, and how could he solve it?
- Third-party integration may not be trustworthy; use SSL and digital signatures.
- If the home organization is offline, traveling users won't be able to access third-party applications; implement a hybrid cloud/local authentication system.
- Local users may not be properly redirected to the third-party services; implement a local gateway.
- Browsers may not properly redirect; use host files to ensure that issues with redirects are resolved.
- What solution can best help address concerns about third parties that control SSO redirects as shown in step 2 in the diagram?
- An awareness campaign about trusted third parties
- TLS
- Handling redirects at the local site
- Implementing an IPS to capture SSO redirect attacks
- Susan has been asked to recommend whether her organization should use a MAC scheme or a DAC scheme. If flexibility and scalability are important requirements for implementing access controls, which scheme should she recommend and why?
- MAC, because it provides greater scalability and flexibility because you can simply add more labels as needed
- DAC, because allowing individual administrators to make choices about the objects they control provides scalability and flexibility
- MAC, because compartmentalization is well suited to flexibility and adding compartments will allow it to scale well
- DAC, because a central decision process allows quick responses and will provide scalability by reducing the number of decisions required and flexibility by moving those decisions to a central authority
- Which of the following tools is not typically used to verify that a provisioning process was followed in a way that ensures that the organization's security policy is being followed?
- Log review
- Manual review of permissions
- Signature-based detection
- Review the audit trail
- Jessica needs to send information about services she is provisioning to a third-party organization. What standards-based markup language should she choose to build the interface?
- SAML
- SOAP
- SPML
- XACML
- During a penetration test, Chris recovers a file containing hashed passwords for the system he is attempting to access. What type of attack is most likely to succeed against the hashed passwords?
- A brute-force attack
- A pass-the-hash attack
- A rainbow table attack
- A salt recovery attack
- Google's identity integration with a variety of organizations and applications across domains is an example of which of the following?
- PKI
- Federation
- Single sign-on
- Provisioning
- Amanda starts at her new job and finds that she has access to a variety of systems that she does not need to accomplish her job. What problem has she encountered?
- Privilege creep
- Rights collision
- Least privilege
- Excessive privileges
- When Chris verifies an individual's identity and adds a unique identifier like a user ID to an identity system, what process has occurred?
- Identity proofing
- Registration
- Directory management
- Session management
- Selah wants to provide accountability for actions performed via her organization's main line of business application. What controls are most frequently used to provide accountability in a situation like this? (Select all that apply.)
- Enable audit logging.
- Provide every staff member with a unique account and enable multifactor authentication.
- Enable time- and location-based login requirements.
- Provide every staff member with a unique account and require a self-selected password.
- Charles wants to provide authorization services as part of his web application. What standard should he use if he wants to integrate easily with other web identity providers?
- OpenID
- TACACS+
- RADIUS
- OAuth
- The company that Cameron works for uses a system that allows users to request privileged access to systems when necessary. Cameron requests access, and the request is pre-approved due to his role. He is then able to access the system to perform the task. Once he is done, the rights are removed. What type of system is he using?
- Zero trust
- Federated identity management
- Single sign-on
- Just-in-time access
- Elle is responsible for building a banking website. She needs proof of the identity of the users who register for the site. How should she validate user identities?
- Require users to create unique questions that only they will know.
- Require new users to bring their driver's license or passport in person to the bank.
- Use information that both the bank and the user have such as questions pulled from their credit report.
- Call the user on their registered phone number to verify that they are who they claim to be.
- Susan's organization is part of a federation that allows users from multiple organizations to access resources and services at other federated sites. When Susan wants to use a service at a partner site, which identity provider is used?
- Susan's home organization's identity provider
- The service provider's identity provider
- Both their identity provider and the service provider's identity provider
- The service provider creates a new identity
- A new customer at a bank that uses fingerprint scanners to authenticate its users is surprised when he scans his fingerprint and is logged in to another customer's account. What type of biometric factor error occurred?
- A registration error
- A Type 1 error
- A Type 2 error
- A time of use, method of use error
- What type of access control is typically used by firewalls?
- Discretionary access controls
- Rule-based access controls
- Task-based access control
- Mandatory access controls
- When you input a user ID and password, you are performing what important identity and access management activity?
- Authorization
- Validation
- Authentication
- Login
- Kathleen works for a data center hosting facility that provides physical data center space for individuals and organizations. Until recently, each client was given a magnetic-strip-based keycard to access the section of the facility where their servers are located, and they were also given a key to access the cage or rack where their servers reside. In the past month, a number of servers have been stolen, but the logs for the passcards show only valid IDs. What is Kathleen's best option to make sure that the users of the passcards are who they are supposed to be?
- Add a reader that requires a PIN for passcard users.
- Add a camera system to the facility to observe who is accessing servers.
- Add a biometric factor.
- Replace the magnetic stripe keycards with smartcards.
- Theresa wants to allow her staff to securely store and manage passwords for systems including service accounts and other rarely used administrative credentials. What type of tool should she implement to enable this?
- Single sign-on
- A federated identity system
- A password manager
- A multifactor authentication system
- Olivia wants to limit the commands that a user can run via
sudoto limit the potential for privilege escalation attacks. What Linux file should she modify to allow this?- The bash
.binconfiguration file - The
sudoersfile - The bash
.allowedconfiguration file - The
sudontfile
- The bash
- Which objects and subjects have a label in a MAC model?
- Objects and subjects that are classified as Confidential, Secret, or Top Secret have a label.
- All objects have a label, and all subjects have a compartment.
- All objects and subjects have a label.
- All subjects have a label and all objects have a compartment.
For questions 65–67, please refer to the following scenario and diagram:
Chris is the identity architect for a growing e-commerce website that wants to leverage social identity. To do this, he and his team intend to allow users to use their existing Google accounts as their primary accounts when using the e-commerce site. This means that when a new user initially connects to the e-commerce platform, they are given the choice between using their Google account using OAuth 2.0 or creating a new account on the platform using their own email address and a password of their choice.

- When the e-commerce application creates an account for a Google user, where should that user's password be stored?
- The password is stored in the e-commerce application's database.
- The password is stored in memory on the e-commerce application's server.
- The password is stored in Google's account management system.
- The password is never stored; instead, a salted hash is stored in Google's account management system.
- Which of the following is responsible for user authentication for Google users?
- The e-commerce application.
- Both the e-commerce application and Google servers.
- Google servers.
- The diagram does not provide enough information to determine this.
- What type of attack is the creation and exchange of state tokens intended to prevent?
- XSS
- CSRF
- SQL injection
- XACML
- Questions like “What is your pet's name?” are examples of what type of identity proofing?
- Knowledge-based authentication
- Dynamic knowledge-based authentication
- Out-of-band identity proofing
- A Type 3 authentication factor
- Madhuri creates a table that includes assigned privileges, objects, and subjects to manage access control for the systems she is responsible for. Each time a subject attempts to access an object, the systems check the table to ensure that the subject has the appropriate rights to the objects. What type of access control system is Madhuri using?
- A capability table
- An access control list
- An access control matrix
- A subject/object rights management system
- During a review of support tickets, Ben's organization discovered that password changes accounted for more than a quarter of its help desk's cases. Which of the following options would be most likely to decrease that number significantly?
- Two-factor authentication
- Biometric authentication
- Self-service password reset
- Passphrases
- Brian's large organization has used RADIUS for AAA services for its network devices for years and has recently become aware of security issues with the unencrypted information transferred during authentication. How should Brian implement encryption for RADIUS?
- Use the built-in encryption in RADIUS.
- Implement RADIUS over its native UDP using TLS for protection.
- Implement RADIUS over TCP using TLS for protection.
- Use an AES256 pre-shared cipher between devices.
- Jim wants to allow cloud-based applications to act on his behalf to access information from other sites. Which of the following tools can allow that?
- Kerberos
- OAuth
- OpenID
- LDAP
- Ben's organization has had an issue with unauthorized access to applications and workstations during the lunch hour when employees aren't at their desk. What are the best types of session management solutions for Ben to recommend to help prevent this type of access?
- Use session IDs for all access and verify system IP addresses of all workstations.
- Set session timeouts for applications and use password-protected screensavers with inactivity timeouts on workstations.
- Use session IDs for all applications, and use password-protected screensavers with inactivity timeouts on workstations.
- Set session timeouts for applications and verify system IP addresses of all workstations.
- What type of authentication scenario is shown in the following diagram?
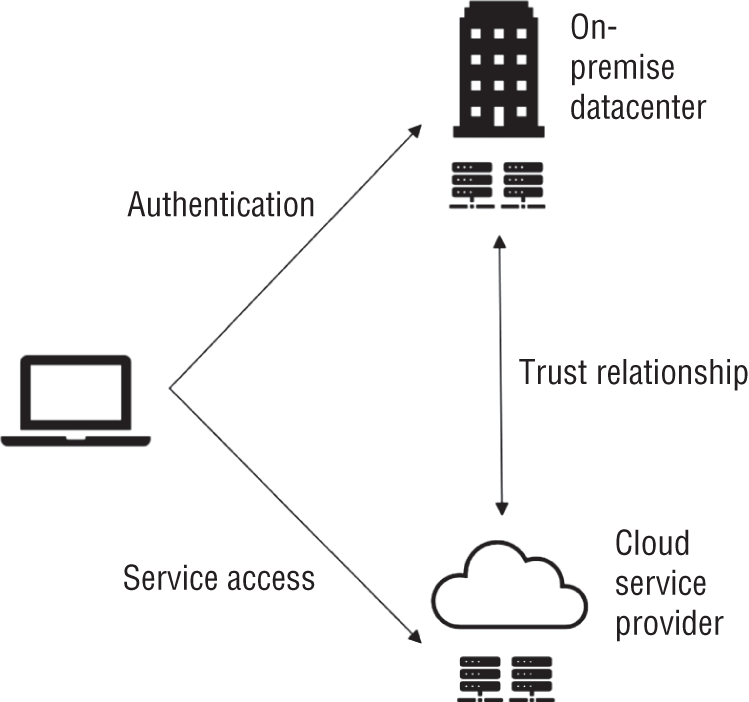
- Hybrid federation
- On-premise federation
- Cloud federation
- Kerberos federation
- Chris wants to control access to his facility while still identifying individuals. He also wants to ensure that the individuals are the people who are being admitted without significant ongoing costs. Which solutions from the following options would meet all of these requirements? (Select all that apply.)
- Security guards and photo identification badges
- RFID badges and readers with PIN pads
- Magstripe badges and readers with PIN pads
- Security guards and magstripe readers
- A device like Yubikey or Titan Security Key is what type of Type 2 authentication factor?
- A token
- A biometric identifier
- A smart card
- A PIV
- What authentication technology can be paired with OAuth to perform identity verification and obtain user profile information using a RESTful API?
- SAML
- Shibboleth
- OpenID Connect
- Higgins
- Jim wants to implement an access control scheme that will ensure that users cannot delegate access. He also wants to enforce access control at the operating system level. What access control mechanism best fits these requirements?
- Role-based access control
- Discretionary access control
- Mandatory access control
- Attribute-based access control
- The security administrators at the company that Susan works for have configured the workstation she uses to allow her to log in only during her work hours. What type of access control best describes this limitation?
- Constrained interface
- Context-dependent control
- Content-dependent control
- Least privilege
- Ben uses a software-based token that changes its code every minute. What type of token is he using?
- Asynchronous
- Smart card
- Synchronous
- Static
- Firewalls are an example of what type of access control mechanism?
- Mandatory access control
- Attribute-based access control
- Discretionary access control
- Rule-based access control
- Michelle works for a financial services company and wants to register customers for her web application. What type of authentication mechanism could she use for the initial login if she wants to quickly and automatically verify that the person is who they claim to be without having a previous relationship with them?
- Request their Social Security number.
- Use knowledge-based authentication.
- Perform manual identity verification.
- Use a biometric factor.
- Megan's company wants to use Google accounts to allow users to quickly adopt their web application. What common cloud federation technologies will Megan need to implement? (Select all that apply.)
- Kerberos
- OpenID
- OAuth
- RADIUS
- Session ID length and session ID entropy are both important to prevent what type of attack?
- Denial of service
- Cookie theft
- Session guessing
- Man-in-the-middle attacks
- The access control system for Naomi's organization checks if her computer is fully patched, if it has a successful clean anti-malware scan, and if the firewall is turned on among other security validations before it allows her to connect to the network. If there are potential issues, she is not permitted to connect and must contact support. What type of access control scheme best describes this type of process?
- MAC
- Rule-based access control
- Role-based access control
- Risk-based access control
- Isabelle wants to prevent privilege escalation attacks via her organization's service accounts. Which of the following security practices is best suited to this?
- Remove unnecessary rights.
- Disable interactive login for service accounts.
- Limit when accounts can log in.
- Use meaningless or randomized names for service accounts.
- What danger is created by allowing the OpenID relying party to control the connection to the OpenID provider?
- It may cause incorrect selection of the proper OpenID provider.
- It creates the possibility of a phishing attack by sending data to a fake OpenID provider.
- The relying party may be able to steal the client's username and password.
- The relying party may not send a signed assertion.
- Jim is implementing a cloud identity solution for his organization. What type of technology is he putting in place?
- Identity as a service
- Employee ID as a service
- Cloud-based RADIUS
- OAuth
- Kristen wants to control access to an application in her organization based on a combination of staff member's job titles, the permissions each group of titles need for the application, and the time of day and location. What type of control scheme should she select?
- ABAC
- DAC
- MAC
- Role BAC
- When Alex sets the permissions shown in the following image as one of many users on a Linux server, what type of access control model is he leveraging?
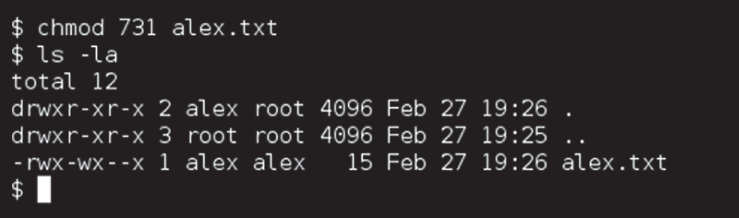
- Role-based access control
- Rule-based access control
- Mandatory access control (MAC)
- Discretionary access control (DAC)
- Joanna leads her organization's identity management team and wants to ensure that roles are properly updated when staff members change to new positions. What issue should she focus on for those staff members to avoid future issues with role definition?
- Registration
- Privilege creep
- Deprovisioning
- Accountability
- What type of authorization mechanism is shown in the following chart?
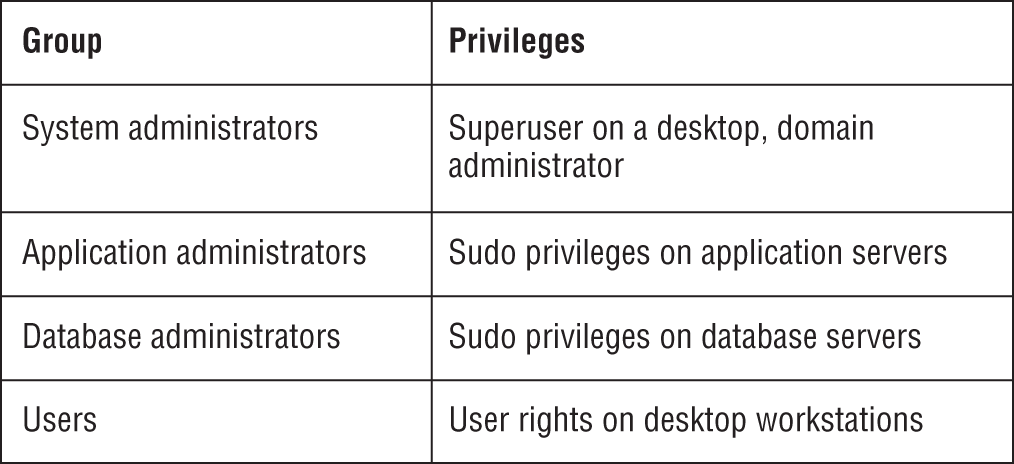
- RBAC
- ABAC
- MAC
- DAC
- Susan is troubleshooting Kerberos authentication problems with symptoms including TGTs that are not accepted as valid and an inability to receive new tickets. If the system she is troubleshooting is properly configured for Kerberos authentication, her username and password are correct, and her network connection is functioning, what is the most likely issue?
- The Kerberos server is offline.
- There is a protocol mismatch.
- The client's TGTs have been marked as compromised and de-authorized.
- The Kerberos server and the local client's time clocks are not synchronized.
- Brian wants to explain the benefits of an on-premise federation approach for identity to his organization's leadership. Which of the following is not a common benefit of a federated identity system?
- Ease of account management
- Single sign-on
- Prevention of brute-force attacks
- Increased productivity
- The bank that Aaron works for wants to allow customers to use a new add-on application from a third-party partner they are working with. Since not every customer will want or need an account, Aaron has suggested that the bank use a SAML-based workflow that creates an account when a user downloads the app and tries to log in. What type of provisioning system has he suggested?
- JIT
- OpenID
- OAuth
- Kerberos
- What authentication protocol does Windows use by default for Active Directory systems?
- RADIUS
- Kerberos
- OAuth
- TACACS+
- Valerie needs to control access to applications that are deployed to mobile devices in a BYOD environment. What type of solution will best allow her to exercise control over the applications while ensuring that they do not leave remnant data on the devices used by her end users?
- Deploy the applications to the BYOD devices and require unique PINs on every device.
- Deploy the application to desktop systems and require users to use remote desktop to access them using enterprise authentication.
- Deploy the applications to the BYOD devices using application containers and require unique PINs on every device.
- Use a virtual hosted application environment that requires authentication using enterprise credentials.
- Match the following authorization mechanisms with their descriptions:
- Role-BAC
- Rule BAC
- DAC
- ABAC
- MAC
- An access control model enforced by the operating system.
- Permissions or rights are granted based on parameters like an IP address, time, or other specific details that match requirements.
- Sometimes called policy-based access control, this model uses information about the subject to assign permissions.
- A model where subjects with the proper rights can assign or pass those rights to other subjects.
- Used to assign permissions based on job or function.
- Match each of the numbered authentication techniques with the appropriate lettered category. Each technique should be matched with exactly one category. Each category may be used once, more than once, or not at all.
Authentication technique
- Password
- ID card
- Retinal scan
- Smartphone token
- Fingerprint analysis
Category
- Something you have
- Something you know
- Something you are
- Match the following identity and access controls with the asset type they are best suited to protect. Each only has one option.
- Information assets
- Systems
- Mobile devices
- Facilities
- Partner applications
- Discretionary access controls
- Badge readers
- Federated identity management
- Biometric authentication
- User accounts with multifactor authentication
