Chapter 8
Software Development Security (Domain 8)
- Susan provides a public RESTful API for her organization's data but wants to limit its use to trusted partners. She intends to use API keys. What other recommendation would you give Susan to limit the potential abuse of the service?
- Limit request rates
- Force HTTP-only requests
- Avoid tokens due to bandwidth constraints
- Blacklist HTTP methods such as GET, POST, and PUT
- Darren is conducting a threat hunting exercise and would like to look for botnet indicators of compromise. Which of the following are common ways that attackers leverage botnets? (Select all that apply.)
- Mining cryptocurrency
- Conducting brute-force attacks
- Scanning for vulnerable systems
- Conducting man-in-the-middle attacks
- Which one of the following statements is not true about code review?
- Code review should be a peer-driven process that includes multiple developers.
- Code review may be automated.
- Code review occurs during the design phase.
- Code reviewers may expect to review several hundred lines of code per hour.
- Kathleen is reviewing the Ruby code shown here. What security technique is this code using?

- Parameterization
- Typecasting
- Gem cutting
- Stored procedures
- Jessica is reviewing her organization's change management process and would like to verify that changes to software include acceptance testing. Which process is responsible for achieving this goal?
- Request control
- Change control
- Release control
- Configuration control
- Ashley is investigating an attack that compromised an account of one of her users. In the attack, the attacker forced the submission of an authenticated request to a third-party site by exploiting trust relationships in the user's browser. What type of attack most likely took place?
- XSS
- CSRF
- SQL injection
- Session hijacking
- Arnold is creating a new software package and is making use of the OpenSSL library. What term best describes the library he is using?
- Open source
- COTS
- Third-party
- Managed
- Jaime is a technical support analyst and is asked to visit a user whose computer is displaying the error message shown here. What state has this computer entered?
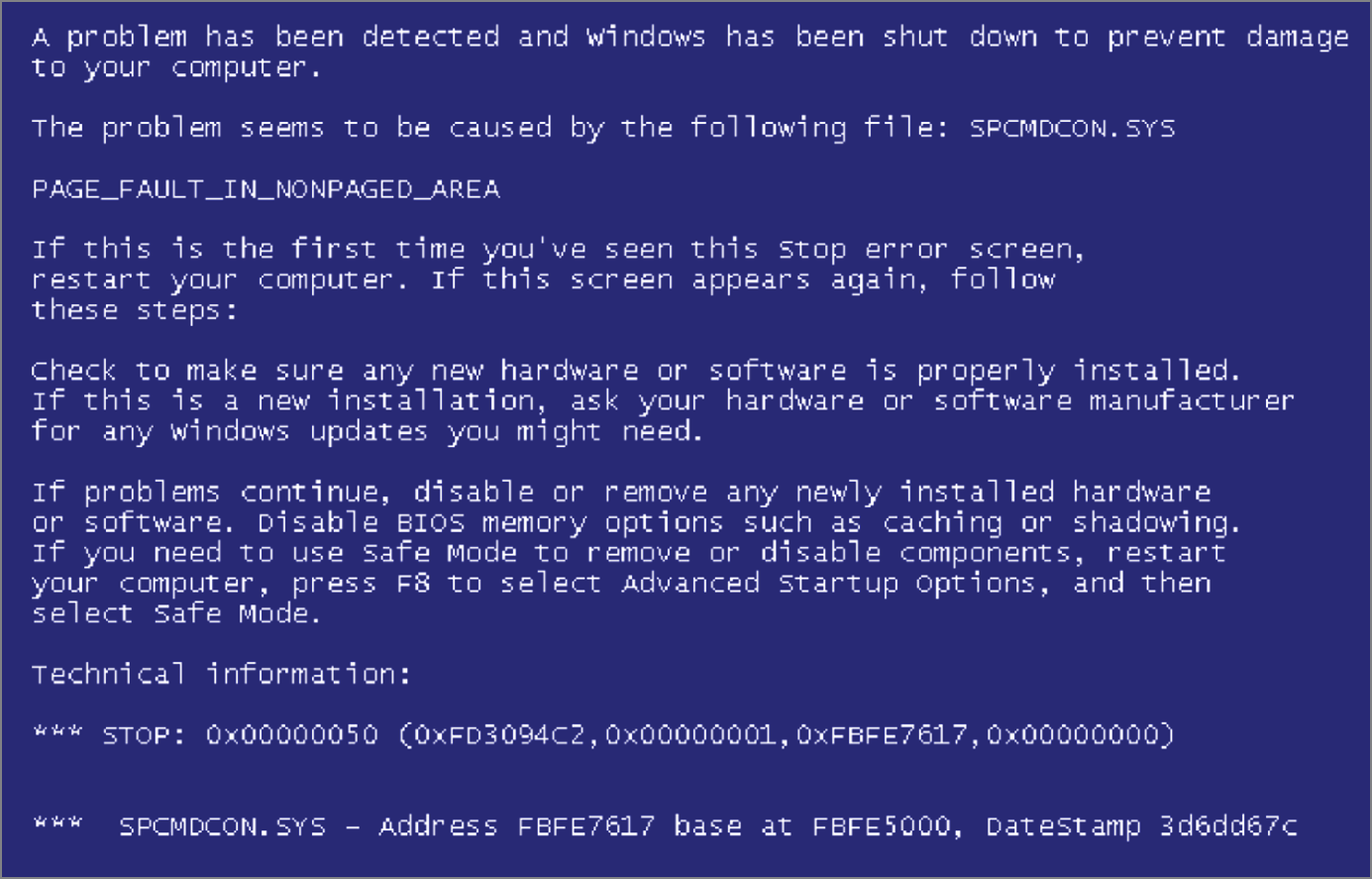
- Fail open
- Irrecoverable error
- Memory exhaustion
- Fail secure
- Joshua is developing a software threat modeling program for his organization. Which of the following are appropriate goals for the program? (Select all that apply.)
- To reduce the number of security-related design flaws
- To reduce the number of security-related coding flaws
- To reduce the severity of non-security-related flaws
- To reduce the number of threat vectors
- In the diagram shown here, which is an example of a method?

-
Account -
Owner -
AddFunds -
Balance
-
- Wanda is reviewing the application development documentation used by her organization and finds the lifecycle illustration shown here. What application development method is her organization using?
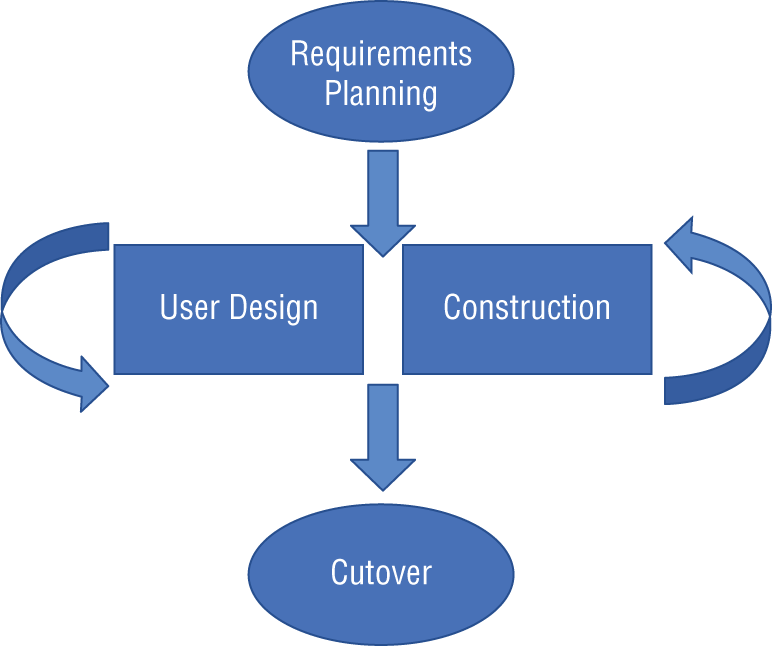
- Waterfall
- Spiral
- Agile
- RAD
- Which one of the following testing methodologies typically works without access to source code?
- Dynamic testing
- Static testing
- White-box testing
- Code review
- Lucca is analyzing a web application that his organization acquired from a third-party vendor. Lucca determined that the application contains a flaw that causes users who are logged in to be able to take actions they should not be able to in their role. What type of security vulnerability should this be classified as?
- Data validation
- Session management
- Authorization
- Error handling
- Bobby is investigating how an authorized database user is gaining access to information outside his normal clearance level. Bobby believes that the user is making use of a type of function that summarizes data. What term describes this type of function?
- Inference
- Polymorphic
- Aggregate
- Modular
- Taylor would like to better protect the applications developed by her organization against buffer overflow attacks. Which of the following controls would best provide this protection?
- Encryption
- Input validation
- Firewall
- Intrusion prevention system
- Kayla recently completed a thorough risk analysis and mitigation review of the software developed by her team and identified three persistent issues:
- Cross-site scripting
- SQL injection
- Buffer overflows
What is the most significant deficiency in her team's work identified by these issues?
- Lack of API security
- Improper error handling
- Improper or missing input validation
- Source code design issues
For questions 17–20, please refer to the following scenario:
Robert is a consultant who helps organizations create and develop mature software development practices. He prefers to use the Software Capability Maturity Model (SW-CMM) to evaluate the current and future status of organizations using both independent review and self-assessments. He is currently working with two different clients.
Acme Widgets is not very well organized with its software development practices. It does have a dedicated team of developers who do “whatever it takes” to get software out the door, but it does not have any formal processes.
Beta Particles is a company with years of experience developing software using formal, documented software development processes. It uses a standard model for software development but does not have quantitative management of those processes.
- What phase of the SW-CMM should Robert report as the current status of Acme Widgets?
- Defined
- Repeatable
- Initial
- Managed
- Robert is working with Acme Widgets on a strategy to advance their software development practices. What SW-CMM stage should be their next target milestone?
- Defined
- Repeatable
- Initial
- Managed
- What phase of the SW-CMM should Robert report as the current status of Beta Particles?
- Defined
- Repeatable
- Optimizing
- Managed
- Robert is also working with Beta Particles on a strategy to advance their software development practices. What SW-CMM stage should be their next target milestone?
- Defined
- Repeatable
- Optimizing
- Managed
- Which one of the following database keys is used to enforce referential integrity relationships between tables?
- Primary key
- Candidate key
- Foreign key
- Master key
- Brynn believes that a system in her organization may have been compromised by a macro virus. Which one of the following files is most likely to be the culprit?
-
projections.doc command.com-
command.exe -
loopmaster.exe
-
- Victor created a database table that contains information on his organization's employees. The table contains the employee's user ID, three different telephone number fields (home, work, and mobile), the employee's office location, and the employee's job title. There are 16 records in the table. What is the degree of this table?
- 3
- 4
- 6
- 16
- Carrie is analyzing the application logs for her web-based application and comes across the following string:
../../../../../../../../../etc/passwdWhat type of attack was likely attempted against Carrie's application?
- Command injection
- Session hijacking
- Directory traversal
- Brute-force
- When should a design review take place when following an SDLC approach to software development?
- After the code review
- After user acceptance testing
- After the development of functional requirements
- After the completion of unit testing
- Tracy is preparing to apply a patch to her organization's enterprise resource planning system. She is concerned that the patch may introduce flaws that did not exist in prior versions, so she plans to conduct a test that will compare previous responses to input with those produced by the newly patched application. What type of testing is Tracy planning?
- Unit testing
- Acceptance testing
- Regression testing
- Vulnerability testing
- What term is used to describe the level of confidence that software is free from vulnerabilities, either intentionally designed into the software or accidentally inserted at any time during its lifecycle, and that the software functions in the intended manner?
- Validation
- Accreditation
- Confidence interval
- Assurance
- Victor recently took a new position at an online dating website and is responsible for leading a team of developers. He realized quickly that the developers are having issues with production code because they are working on different projects that result in conflicting modifications to the production code. What process should Victor invest in improving?
- Request control
- Release control
- Change control
- Configuration control
- Tom is assessing security risks related to a database he manages. Examining user access controls, he determines that users have access to individual records in a table that match their clearances, but if they pull multiple records, that collection of facts has a higher classification than the classification of any of those facts standing alone and exceeds the permitted access. What type of issue has Tom identified?
- Inference
- SQL injection
- Multilevel security
- Aggregation
- Ron leads a team of software developers who find themselves often re-creating code that performs common functions. What software development tool could he use to best address this situation?
- Code repositories
- Code libraries
- IDEs
- DAST
- Vivian would like to hire a software tester to come in and evaluate a new web application from a user's perspective. Which of the following tests best simulates that perspective?
- Black box
- Gray box
- Blue box
- White box
- Referring to the database transaction shown here, what would happen if no account exists in the Accounts table with account number 1001?
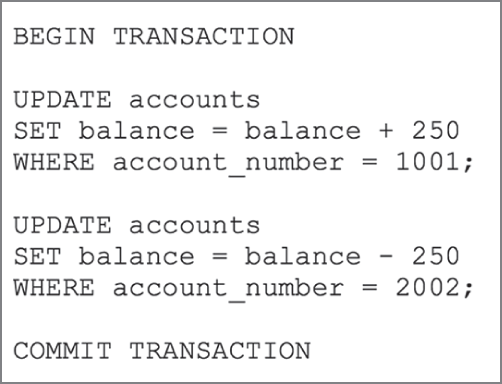
- The database would create a new account with this account number and give it a $250 balance.
- The database would ignore that command and still reduce the balance of the second account by $250.
- The database would roll back the transaction, ignoring the results of both commands.
- The database would generate an error message.
- Brandon is a software developer seeking to integrate his software with a popular social media site. The site provides him with software libraries that he can use to better integrate his code as well as other tools that make his work easier. What term best describes the service he is using?
- SDK
- DLP
- IDE
- API
- Kim is troubleshooting an application firewall that serves as a supplement to the organization's network and host firewalls and intrusion prevention system, providing added protection against web-based attacks. The issue the organization is experiencing is that the firewall technology suffers somewhat frequent restarts that render it unavailable for 10 minutes at a time. What configuration might Kim consider to maintain availability during that period at the lowest cost to the company?
- High availability cluster
- Failover device
- Fail open
- Redundant disks
- What type of security issue arises when an attacker can deduce a more sensitive piece of information by analyzing several pieces of information classified at a lower level?
- SQL injection
- Multilevel security
- Parameterization
- Inference
- Greg is battling a malware outbreak in his organization. He used specialized malware analysis tools to capture samples of the malware from three different systems and noticed that the code is changing slightly from infection to infection. Greg believes that this is the reason that antivirus software is having a tough time defeating the outbreak. What type of malware should Greg suspect is responsible for this security incident?
- Stealth virus
- Polymorphic virus
- Multipartite virus
- Encrypted virus
For questions 37–40, please refer to the following scenario:
Linda is reviewing posts to a user forum on her company's website, and when she browses a certain post, a message pops up in a dialog box on her screen reading “Alert.” She reviews the source code for the post and finds the following code snippet:
<script>alert('Alert');</script> - What vulnerability definitely exists on Linda's message board?
- Cross-site scripting
- Cross-site request forgery
- SQL injection
- Improper authentication
- What was the likely motivation of the user who posted the message on the forum containing this code?
- Reconnaissance
- Theft of sensitive information
- Credential stealing
- Social engineering
- Linda communicates with the vendor and determines that no patch is available to correct this vulnerability. Which one of the following devices would best help her defend the application against further attack?
- VPN
- WAF
- DLP
- IDS
- In further discussions with the vendor, Linda finds that they are willing to correct the issue but do not know how to update their software. What technique would be most effective in mitigating the vulnerability of the application to this type of attack?
- Bounds checking
- Peer review
- Input validation
- OS patching
- Hannah is a software developer working on creating statistical software using the R programming language. She uses the RStudio tool, shown here, to assist her in writing this code. What term best describes this tool?

- SDK
- IDE
- API
- DLP
- Lauren wants to use a software review process for the application she is working on. Which of the following processes would work best if she is a remote worker who works different hours from the rest of her team?
- Pass around
- Pair programming
- Team review
- Fagan inspection
- Alan is deploying Java code to a variety of machines in his environment and must install the JVM on those machines first. What term best describes the JVM in this case?
- Repository
- Change manager
- Runtime
- Sandbox
- Christine is nearing the final stages of testing a new software package. Which one of the following types of software testing usually occurs last and is executed against test scenarios?
- Unit testing
- Integration testing
- User acceptance testing
- System testing
- Alexis' organization recently moved to a CI/CD approach for software development where they intend to speed up the deployment of code supporting their website. What is the most reasonable frequency that they can expect to achieve using this type of approach?
- Monthly deployments
- Weekly deployments
- Daily deployments
- Hundreds of daily deployments
- Amber is conducting a threat intelligence project and would like to find a source of information on threats to her organization's web applications. Which of the following organizations is widely considered as the definitive source for information on web-based attack vectors?
- (ISC)2
- ISACA
- OWASP
- Mozilla Foundation
- Chris is a software developer, and he is actively writing code for an application. What phase of the Agile process is he in?
- Planning
- Sprints
- Deployment
- Development
- Alyssa's team recently implemented a new system that gathers information from a variety of different log sources, analyzes that information, and then triggers automated playbooks in response to security events. What term best describes this technology?
- SIEM
- Log repositories
- IPS
- SOAR
- Chris is reviewing the code of an open source application that he is planning to use in his organization. He finds the code excerpt shown here:
int myarray[10];myarray[10] = 8;What type of attack is taking place?
- Mismatched data types
- Overflow
- SQL injection
- Covert channel
- Which one of the following database issues occurs when one transaction writes a value to the database that overwrites a value that was needed by transactions with earlier precedence?
- Dirty read
- Incorrect summary
- Lost update
- SQL injection
- Belinda would like to better protect users of her organization's web application from cookie stealing attacks. Which one of the following is the most effective control against this type of session hijacking attack?
- TLS
- Complex session cookies
- SSL
- Expiring cookies frequently
- In a software configuration management program, what is the primary role of the CAB?
- Approve the credentials of developers.
- Facilitate lessons learned sessions.
- Review and approve/reject code changes.
- Prioritize software development efforts.
- Which one of the following tools is commonly used by software developers to interact with and manage code that is stored in code repositories?
-
grep -
git -
lsof -
gcc
-
- While evaluating a potential security incident, Harry comes across a log entry from a web server request showing that a user entered the following input into a form field:
CARROT'&1=1;--What type of attack was attempted?
- Buffer overflow
- Cross-site scripting
- SQL injection
- Cross-site request forgery
- Which one of the following is not an effective control against SQL injection attacks?
- Escaping
- Client-side input validation
- Parameterization
- Limiting database permissions
- Jason is reviewing the documentation for a software development project and comes across the diagram shown here. What type of diagram is he examining?
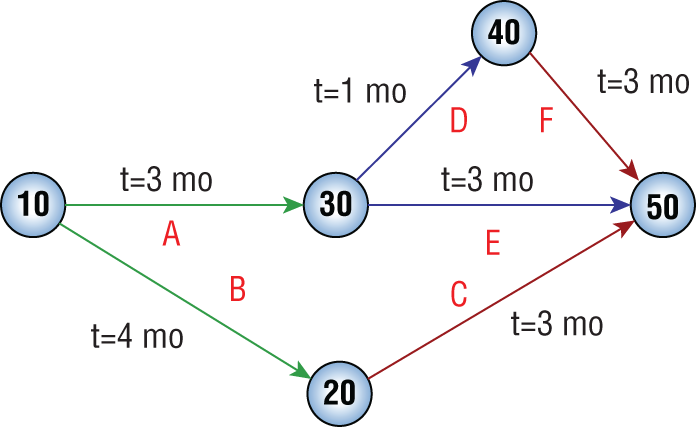
- WBS chart
- PERT chart
- Gantt chart
- Wireframe diagram
- In what software testing technique does the evaluator retest a large number of scenarios each time that the software changes to verify that the results are consistent with a standard baseline?
- Orthogonal array testing
- Pattern testing
- Matrix testing
- Regression testing
- Haley is reviewing code created by her organization for its possible exposure to web application vulnerabilities. Which one of the following conditions may make an application most vulnerable to a cross-site scripting (XSS) attack?
- Input validation
- Reflected input
- Unpatched server
- Promiscuous firewall rules
- Roger is conducting a software test for a tax preparation application developed by his company. End users will access the application over the web, but Roger is conducting his test on the back end, evaluating the source code on the web server. What type of test is Roger conducting?
- White box
- Gray box
- Blue box
- Black box
- Which of the following statements is true about heuristic-based antimalware software?
- It has a lower false positive rate than signature detection.
- It requires frequent definition updates to detect new malware.
- It has a higher likelihood of detecting zero-day exploits than signature detection.
- It monitors systems for files with content known to be viruses.
- Martin is inspecting a system where the user reported unusual activity, including disk activity when the system is idle and abnormal CPU and network usage. He suspects that the machine is infected by a virus, but scans come up clean. What malware technique might be in use here that would explain the clean scan results?
- File infector virus
- MBR virus
- Service injection virus
- Stealth virus
- Tomas discovers a line in his application log that appears to correspond with an attempt to conduct a directory traversal attack. He believes the attack was conducted using URL encoding. The line reads as follows:
%252E%252E%252F%252E%252E%252Fetc/passwdWhat character is represented by the %252E value?
- .
- ,
- ;
- /
- An attacker posted a message to a public discussion forum that contains an embedded malicious script that is not displayed to the user but executes on the user's system when read. What type of attack is this?
- Persistent XSRF
- Nonpersistent XSRF
- Persistent XSS
- Nonpersistent XSS
- Which one of the following is not a principle of the Agile software development process?
- Welcome changing requirements, even late in the development process.
- Maximizing the amount of work not done is essential.
- Clear documentation is the primary measure of progress.
- Build projects around motivated individuals.
- Gavin is an internal auditor tasked with examining the change management practices of his organization. He would like to review a series of changes made to a software package to determine whether they were properly documented. Where should he turn for a description of each proposed change?
- CAB
- RFC
- SOAR
- SIEM
- Neal is working with a DynamoDB database. The database is not structured like a relational database but allows Neal to store data using a key-value store. What type of database is DynamoDB?
- Relational database
- Graph database
- Hierarchical database
- NoSQL database
- In the transaction shown here, what would happen if the database failed in between the first and second update statements?

- The database would credit the first account with $250 in funds but then not reduce the balance of the second account.
- The database would ignore the first command and only reduce the balance of the second account by $250.
- The database would roll back the transaction, ignoring the results of both commands.
- The database would successfully execute both commands.
- Tareck's organization makes use of a significant amount of COTS software. He recently discovered a significant buffer overflow vulnerability in the code of a COTS software package that is crucial to his business. What is the most likely way that Tareck can get this corrected?
- Work with his software development team to modify the code.
- Notify the vendor and request a patch.
- Deploy an intrusion prevention system.
- Update firewall rules.
- Which one of the following statements is true about software testing?
- Static testing works on runtime environments.
- Static testing performs code analysis.
- Dynamic testing uses automated tools, but static testing does not.
- Static testing is a more important testing technique than dynamic testing.
- David is working on developing a project schedule for a software development effort, and he comes across the chart shown here. What type of chart is this?

- Work breakdown structure
- Functional requirements
- PERT chart
- Gantt chart
- Barry is a software tester who is working with a new gaming application developed by his company. He is playing the game on a smartphone to conduct his testing in an environment that best simulates a normal end user, but he is referencing the source code as he conducts his test. What type of test is Barry conducting?
- White box
- Black box
- Blue box
- Gray box
- Miguel recently completed a penetration test of the applications that his organization uses to handle sensitive information. During his testing, he discovered a condition where an attacker can exploit a timing condition to manipulate software into allowing him to perform an unauthorized action. Which one of the following attack types fits this scenario?
- SQL injection
- Cross-site scripting
- Pass the hash
- TOC/TOU
- What part of the security review process are the input parameters shown in the diagram used for?

- SQL injection review
- Sprint review
- Fagan inspection
- Attack surface identification
- What application security process can be described in these three major steps?
- Decomposing the application
- Determining and ranking threats
- Determining countermeasures and mitigation
- Fagan inspection
- Threat modeling
- Penetration testing
- Code review
- Which one of the following approaches to failure management is the most conservative from a security perspective?
- Fail open
- Fail mitigation
- Fail clear
- Fail closed
- What software development model is shown in the figure?

- Waterfall
- Agile
- Lean
- Spiral
- Mark is considering replacing his organization's customer relationship management (CRM) solution with a new product that is available in the cloud. This new solution is completely managed by the vendor, and Mark's company will not have to write any code or manage any physical resources. What type of cloud solution is Mark considering?
- IaaS
- CaaS
- PaaS
- SaaS
- Which one of the following change management processes is initiated by users rather than developers?
- Change request
- Change control
- Release control
- Design review
- Teagan would like to better protect his organization against database inference attacks. Which one of the following techniques is an effective countermeasure against these attacks?
- Input validation
- Parameterization
- Polyinstantiation
- Server-side validation
- Ursula is a government web developer who recently created a public application that offers property records. She would like to make it available for other developers to integrate into their applications. What can Ursula create to make it easiest for developers to call her code directly and integrate the output into their applications?
- Object model
- Data dictionary
- API
- Primary key
- Nathan recently completed a software development project where he integrated the organization's network operations stack with their development processes. As a result, developers can modify firewall rules from their code on an as-needed basis. What term best describes this ability?
- Agile
- IaC
- SDS
- DevOps
- TJ is inspecting a system where the user reported a strange error message and the inability to access files. He sees the window shown in this figure. What type of malware should TJ suspect?
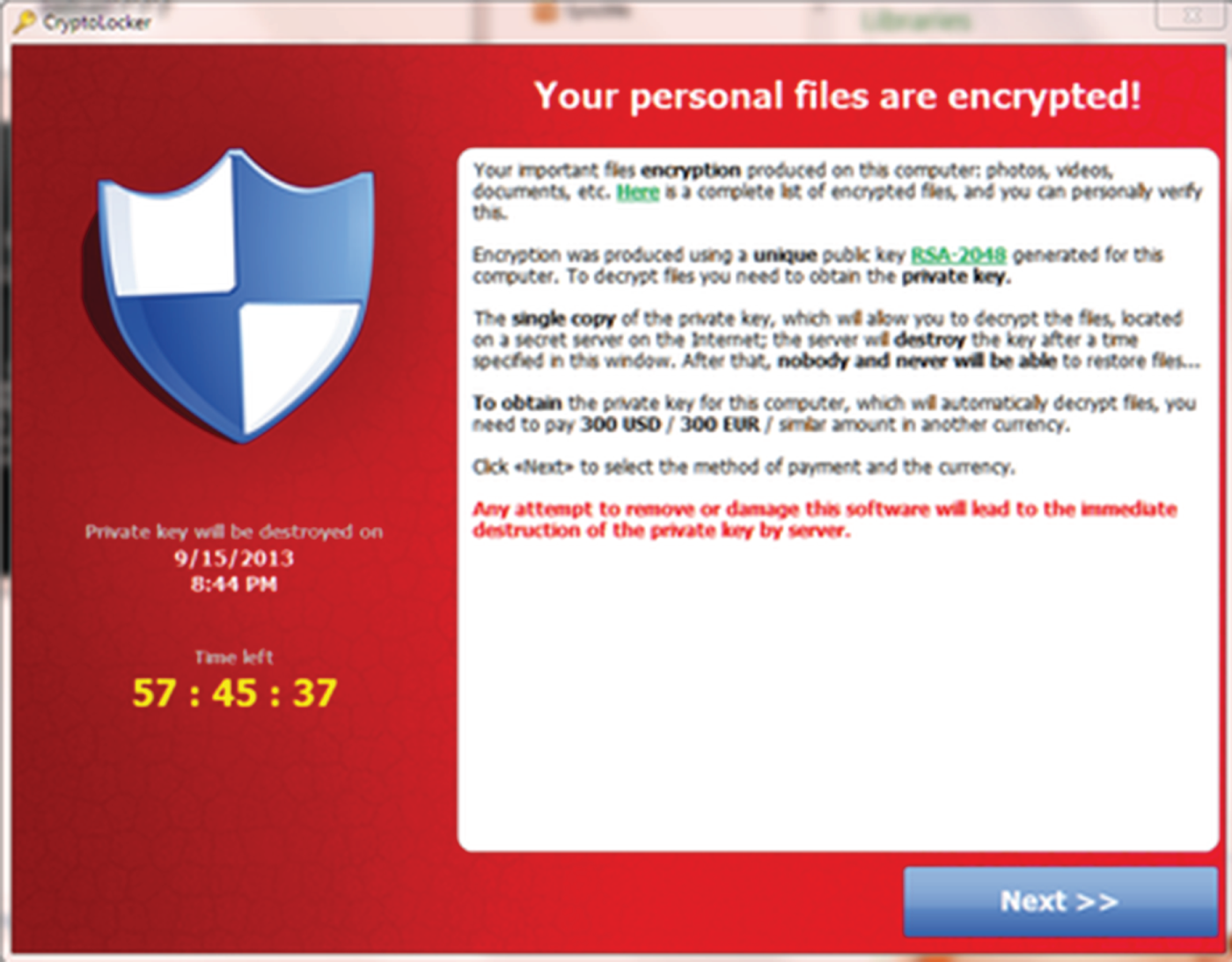
- Service injection
- Encrypted virus
- SQL injection
- Ransomware
- Charles is developing a mission-critical application that has a direct impact on human safety. Time and cost are less important than correctly functioning software. Which of the following software development methodologies should he choose given these requirements?
- Agile
- DevOps
- Spiral
- Waterfall
- Which one of the following types of artificial intelligence attempts to use complex computations to replicate the partial function of the human mind?
- Decision support systems
- Expert systems
- Knowledge bank
- Neural networks
- At which level of the Software Capability Maturity Model (SW-CMM) does an organization introduce basic lifecycle management processes?
- Initial
- Repeatable
- Defined
- Managed
- Lucas runs the accounting systems for his company. The morning after an essential was fired, systems began mysteriously losing information. Lucas suspects that the fired employee tampered with the systems prior to his departure. What type of attack should Lucas suspect?
- Privilege escalation
- SQL injection
- Logic bomb
- Remote code execution
- Which one of the following principles would not be favored in an Agile approach to software development?
- Processes and tools over individuals and interactions
- Working software over comprehensive documentation
- Customer collaboration over contract negotiations
- Responding to change over following a plan
- What technique do API developers most commonly use to limit access to an API to authorized individuals and applications?
- Encryption
- Input validation
- API keys
- IP filters
- Reggie recently received a letter from his company's internal auditors scheduling the kickoff meeting for an assessment of his group. Which of the following should Reggie not expect to learn during that meeting?
- Scope of the audit
- Purpose of the audit
- Expected timeframe
- Expected findings
- Which one of the following is the proper order of steps in the waterfall model of software development?
- Requirements, Design, Testing, Coding, Maintenance
- Requirements, Design, Coding, Testing, Maintenance
- Design, Requirements, Coding, Testing, Maintenance
- Design, Requirements, Testing, Coding, Maintenance
- Renee is a software developer who writes code in Node.js for her organization. The company is considering moving from a self-hosted Node.js environment to one where Renee will run her code on application servers managed by a cloud vendor. What type of cloud solution is Renee's company considering?
- IaaS
- CaaS
- PaaS
- SaaS
- Tom is writing a software program that calculates the sales tax for online orders placed from various jurisdictions. The application includes a user-defined field that allows the entry of the total sale amount. Tom would like to ensure that the data entered in this field is a properly formatted dollar amount. What technique should he use?
- Limit check
- Fail open
- Fail secure
- Input validation
- Brian is helping implement a new software testing methodology for his organization and would like to review the completeness of his toolkit. Which of the following would be considered dynamic application security testing (DAST) tools? (Select all that apply.)
- Code review
- Fuzzing
- Static analysis
- Web application vulnerability scanning
- What approach to technology management integrates the three components of technology management shown in this illustration?
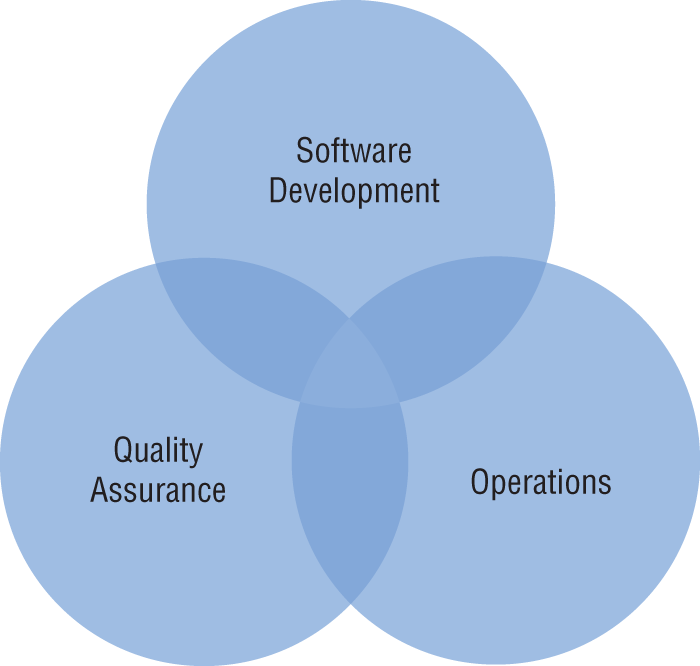
- Agile
- Lean
- DevOps
- ITIL
- Olivia is conducting a risk analysis of a web application that her organization obtained from a third party and is concerned that it might contain vulnerabilities. Which one of the following activities might she take to best mitigate the risk?
- Deploy a WAF.
- Implement strong encryption.
- Purchase an insurance policy.
- Discontinue use of the software.
- Which one of the following database concurrency issues occurs when one transaction reads information that was written to a database by a second transaction that never committed?
- Lost update
- SQL injection
- Incorrect summary
- Dirty read
- What software development concept was pioneered by the Defense Department in the 1990s as an effort to bring together diverse product development teams?
- Integrated product team
- Agile methodology
- Scrum approach
- User stories
- Frank is working to select a new cloud service that will provide object storage for an application being developed by his team. What category of cloud service is Frank planning to use?
- SaaS
- IaaS
- FaaS
- PaaS
- Match the numbered code testing methods to their lettered definition:
Code testing methods
- Regression testing
- Integration testing
- Unit testing
- System testing
Definitions
- Testing on a complete integrated product
- A testing method that focuses on modules or smaller sections of code for testing
- A testing method that is used to verify that previously tested software performs the same way after changes are made
- A testing method used to validate how software modules work together
- Match the following numbered terms to their lettered definitions:
- Session hijacking
- Cross-site scripting
- Cross-site request forgery
- SQL injection
- An attack that injects a malicious script into otherwise trusted websites
- An attack that is designed to execute commands against a database via an insecure web application
- An exploitation method that often involves cookies or keys to gain unauthorized access to a computer or service
- An attack that forces a user to execute unwanted actions in a website or application they are currently logged into
