Chapter 2. Fight in Cyber like the Military Fights in the Physical
Andrew Harris

I started my career in the US Department of Defense as a cybersecurity engineer, ending my stint there as the Chief for Strategic Programs. The more I saw the Department operating what they call Computer Network Defense (CND), fighting in cyberspace, the more overlap I saw in how they were fighting in the other domains—land, air, water, and now space.
It became evident that the same approach the military has used in the physical world should be applied in the cyber one.
The OODA Loop
What I’m referring to is the OODA loop—or the “Observe-Orient-Decide-Act” loop. This was made famous by United States Air Force Colonel John Boyd.1
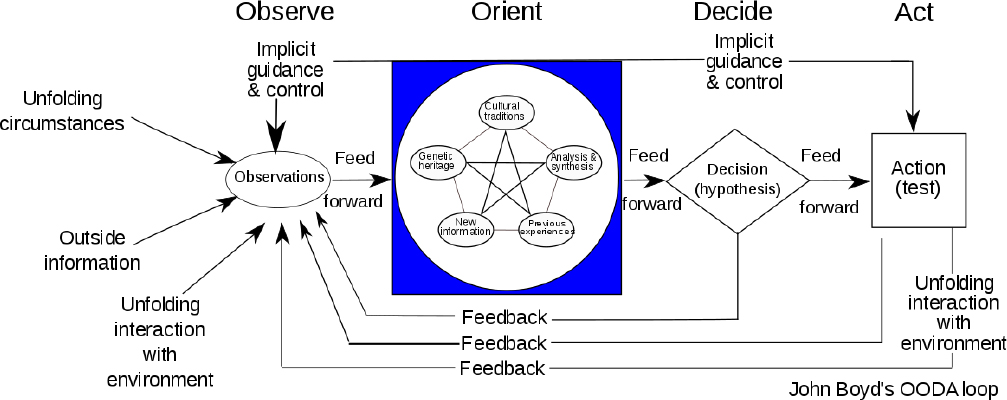
To summarize the concept, the goal is to properly synthesize data and accurately respond to it, faster than your opponent. The last bit is equally important.
How does this relate to cybersecurity? When thinking of responding to cybersecurity incidents and breaches, and within the context of what I call the “Iceberg Effect“(Chapter reference), one needs to discover all observables an adversary has, containing and responding. However, this is rarely ever a one-loop effort.
This activity happens multiple times, enabling cybersecurity professionals to confidently respond to and evict an adversary. For that reason, it’s the feedback loop from one loop into the next loop that is of operational importance.
Prior to performing the first loop, one should ask themselves what feedback they need to see if they’ve been successful. Has the adversary attempted to break out of containment strategies added in the first loop? Has an asset previously unknown to be compromised shown evidence of a previously discovered indicator of compromise (IoC)? After you disabled a compromised user, did you see activity from it elsewhere?
Having this high-level strategy is paramount when strategizing, acquiring products, and operating any product or tool in a production environment, against determined and capable adversaries.
Containment Helps Both Prevent and Inform
Earlier we referenced containment plus the fact that a mission or series of operations is rarely a one-OODA-loop operation. There is a cat-and-mouse game to worry about when responding to any cyber incident.
Containment is necessary for two reasons:
It prevents the adversary, once detected, from achieving its goals or further escalating.
It informs later OODA loops. By setting these containment strategies up, any attempt of breaching the containment model becomes a signal in itself.
Containment can be resetting or disabling an account. If you do this, any attempt to use the specific account again should be immediately investigated—it potentially could be the adversary attempting to use the account, even on a computer you previously had no idea they had access to.
Containment could be separating the identity or control plane (see “Three Fundamental Planes”) where the adversary was discovered from the rest of the network. This sometimes causes pain, but when fighting a real adversary, it’s a necessary step to confidently evict them. This could be performed a few different ways, including segregating accounts, disabling network traffic, forcing a choke point through a firewall (think software-defined networks or SDNs), and so on. Once implemented all attempts to break this new technical control should be reviewed in the following OODA.
1 “John Boyd (military strategist),” Wikipedia, https://en.wikipedia.org/wiki/John_Boyd_(military_strategist)#The_OODA_loop.
