AWS gives you multiple services, features, and tools to build scalable, de-coupled, and secure cloud applications. AWS supports web application development in programming languages such as Python, JAVA, .NET, PHP, Ruby, and mobile application development as well as Android and iOS platforms by providing Software Development Kits (SDKs). Alongside this, it provides the following tools for developing applications in the AWS cloud environment:
- Integrated development environments (IDEs) such as Visual Studio and Eclipse
- Command-line tools such as AWS CLI, AWS tools for PowerShell, and so on
- Services for running these applications, such as Elastic Compute Cloud, AWS Elastic Beanstalk, and Amazon EC2 Container Service
- Tools and services for developing serverless applications such as AWS Serverless Application Model (SAM) and AWS Lambda respectively
- Managed services such as AWS CodeCommit for source control and AWS CodeDeploy for automation of code deployment process
When you develop and deploy web and mobile applications in the cloud using the above-mentioned services, tools, and features, you need to secure it from SQL injections, unwanted traffic, intrusions, Distributed Denial of Service (DDoS) attacks, and other similar threats. Furthermore, you need to ensure that all requests sent to AWS through your applications are secure and recognized by AWS as authorized requests. Your applications that are deployed on EC2 instances should be able to communicate securely with other AWS services such as the Simple Storage Service (S3) or Relational Database Service (RDS). Securing applications in AWS is as critical as securing your data and infrastructure in AWS.
In this lesson, we will learn about securing web and mobile applications in AWS cloud. We will begin with Web Application Firewall (WAF), an AWS service that secures your web applications from common threats by creating access control lists to filter threats. We will learn the following about AWS WAF:
- Benefits of AWS WAF
- Working with AWS WAF
- Security automation with AWS WAF
Moving on we will walk you through securing API requests by learning to sign these requests while communicating with AWS services and resources.
Furthermore, we will learn about a couple of AWS services, as follows, that are extremely useful in securing our applications in the cloud.
- Amazon Cognito: A managed AWS service for authenticating user data for your mobile applications.
- Amazon API Gateway: A managed AWS service for securing, creating, and managing APIs.
AWS WAF is a web application firewall that helps you define various rules in the form of conditions and access control lists to secure your web applications from common security threats, such as cross-site scripting, DDoS attacks, SQL injections, and so on. These threats may result in application unavailability or an application consuming excessive resources due to an increase in malicious web traffic.
You secure your websites and web applications by monitoring, controlling, and filtering HTTP and HTTPS requests received by the Application Load Balancer and Amazon CloudFront. You can allow or reject these requests based on various filters, such as the IP address sending these requests, header values, URI strings, and so on. These security features do not impact the performance of your web applications.
AWS WAF enables you to perform three behaviors--allowing all requests other than the ones that are specified by the access control lists; blocking all requests other than the ones that have been allowed access by the access control lists; counting all requests that are allowable as per the rules set in access control lists. You can use AWS WAF to secure websites hosted outside of the AWS cloud environment, as Amazon CloudFront supports origins outside of AWS. You can configure the Amazon CloudFront to display a custom error page when a request matches your WAF rule and then block it.
It is integrated with CloudWatch and CloudTrail so you can monitor the WAF metrics in real time, such as the number of blocked requests and near real-time and historical audit logs of WAF API respectively. The following figure shows the AWS WAF workflow:

Figure 1: AWS Web Application Firewall
Let us look at the most popular benefits of AWS WAF:
- Increased protection against web attacks: You get protection for your web applications through AWS WAF. It will filter the web traffic based on the access control lists and rules that you can configure for most common web exploits, such as blocking specific IP addresses or blocking matching query strings containing malicious web traffic, and so on.
- Security integrated with how you develop applications: AWS WAF enables you to configure all of its features through its APIs and through the AWS Management Console. It also imbibes the culture of DevSecOps in your organization as the development team takes ownership of securing applications by using WAF and adding rules at multiple areas and levels throughout the application development cycle. So you have a developer writing code and adding WAF rules, a DevOps engineer that will deploy this code, and a security auditor who will audit all application security in place of web applications.
- Ease of deployment and maintenance: AWS WAF is integrated with Amazon CloudFront and the Application Load Balancer. This makes it easy for you to deploy web applications by making them part of your Content Delivery Network (CDN) or by using the Application Load Balancer that is used to front all your web servers. You do not need to install any additional software on any servers or anywhere in your AWS environment. Moreover, you can write rules in one place and deploy them across all your web applications hosted across various resources in your AWS environment.
- Improved web traffic visibility: You can set up metrics and dashboards for all your web application requests that are evaluated against your WAF rules in Amazon CloudWatch. You can monitor these metrics in near real-time and gauge the health of your web traffic. You can also use this metrics information to modify the existing WAF rules or create new ones.
- Cost effective web application development: AWS WAF prevents you from creating, managing, and deploying your own custom web monitoring and firewall solution. It allows you to save development costs for your custom web application firewall solution. AWS WAF, like other AWS services, allows you to pay only for what you use without any upfront commitment or a minimum fee. It has a flexible pricing model depending on the number of rules deployed and traffic received by your web application in terms of HTTP and HTTPS requests.
When working with AWS WAF, you begin by creating conditions for matching malicious traffic; next, you combine one or more of these conditions as rules and these rules are combined as web access control lists. These web access control lists can be associated with one or multiple resources in your AWS environment such as Application Load Balancers or CloudFront web distributions.
- Conditions: You can define one of the following conditions available in AWS WAF when you would either want to allow or block requests based on these conditions:
- Cross-site scripting
- Geo match
- IP addresses
- Size constraints
- SQL injection
- String and regex matching
The following figure shows an example of an IP address condition where multiple suspicious IP addresses are listed. You can list one IP address as well as range of IP addresses in your conditions.

Figure 2: AWS WAF condition
- Rules: You combine conditions to create rules for requests that you want to either allow, block, or count. There are two types of rules:
- Regular rules: These rules are created by combining conditions only. For example, a regular rule will contain requests originating from a specific IP address.
- Rate-based rules: These rules are similar to regular rules with the addition of a rate limit. Essentially, these rules count the requests every 5 minutes originating from a source and, this enables you to take an action based on the pre-defined rate limit for a rule.
The following diagram shows a couple of rules in the AWS WAF dashboard:
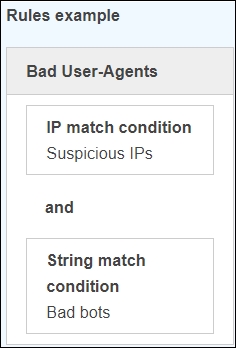
Figure 3: AWS WAF rules
- Web ACL: A set of rules combined together forms a web ACL. You define an action such as allow, block, or count for each rule. Along with these actions, you also define a default action for each rule of your web ACL in scenarios when a request does not meet any of the three conditions for a rule.
The following figure (available in AWS documentation) shows a web ACL containing a rate based rule and regular rules. It also shows how it evaluates the condition for these rules and how it performs actions based on these checks:

Figure 4: AWS WAF Web ACL
