Compliance Law Requirements and Protecting Data Privacy
It’s not enough to keep your information secure within your network. Keeping your information secure means keeping it secure at all times. This is especially true as data move between domains in the information technology (IT) infrastructure. As organizations rely more and more on remote resources and applications, it becomes crucial to ensure your data are secure as they travel from location to location. A solid security policy that includes compliance with all appropriate requirements should support efficient and cost-effective operations. Implementing the controls necessary to support your security policy in the LAN-to-WAN Domain makes your organization more secure and more effective.
Figure 11-1 shows the LAN-to-WAN Domain in the context of the seven domains in the IT infrastructure.
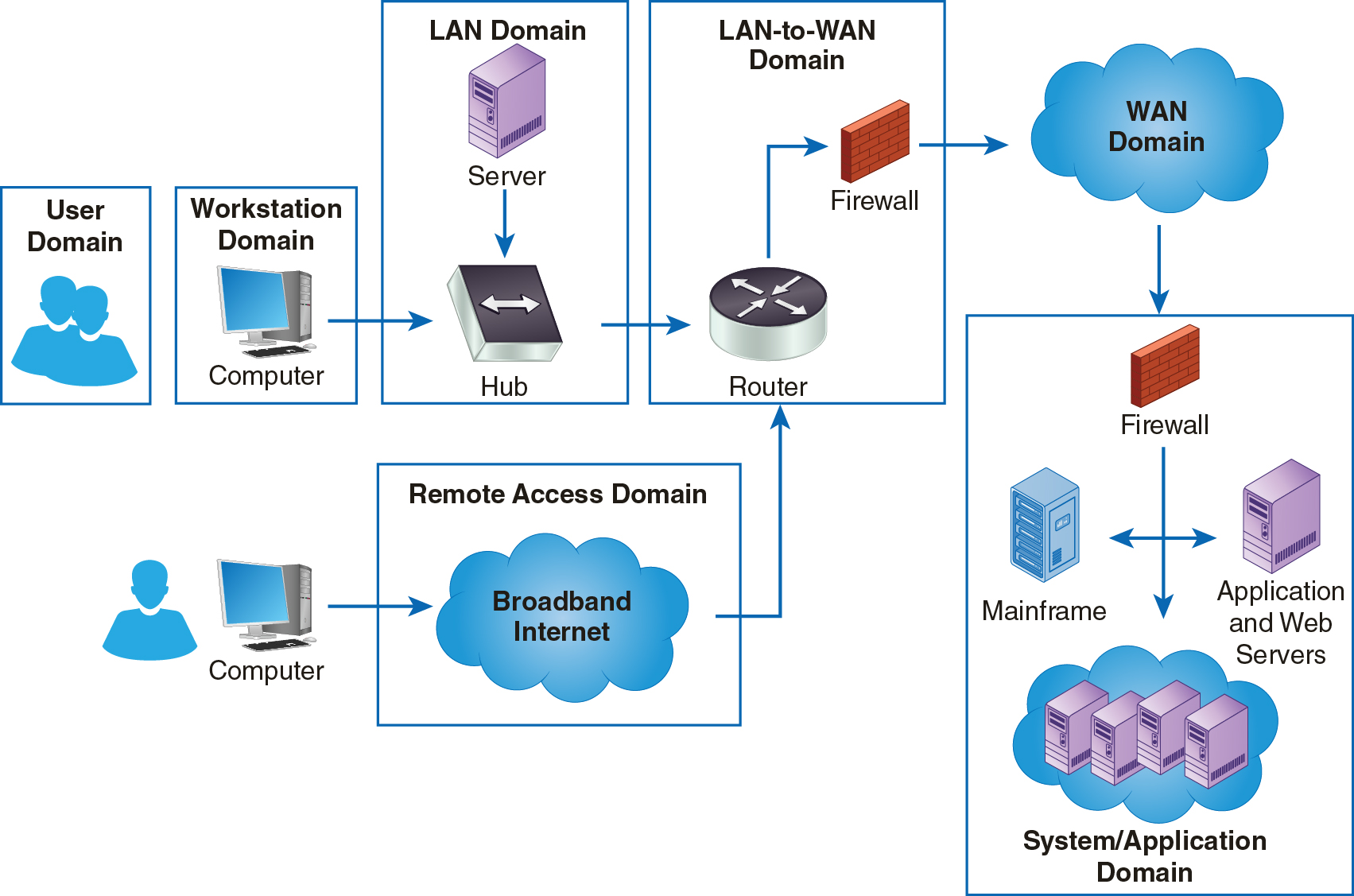
FIGURE 11-1 The LAN-to-WAN Domain Within the Seven Domains of a Typical IT Infrastructure
We value a degree of privacy when it comes to highly personal information about ourselves. For many, what first comes to mind as highly personal information is our financial and medical records. Yet this information is stored in many forms as digital files. Securing and protecting these files is both a trust and legal obligation for an organization. This book focuses on U.S. legal privacy obligations; however, countries throughout the world have similar laws. These laws recognize that data will leave the confines of the local network and define how such data should be transmitted and handled.
In general, it is understood that data privacy must be protected. What is not so clear, however, is what constitutes private data. Depending upon the environment that an organization operates, privacy can take on different meanings. The American Institute of Certified Public Accountants (AICPA) describes privacy obligation as “ensuring privacy, which concerns the rights and obligations of individuals and organizations concerning the collection, use, retention, disclosure, and disposal of personal information comes with risks.” Thus, privacy is about personal information, which might be used to identify an individual. Most privacy examples include the following:
- Name
- Social Security number (SSN)
- Home address or geo location
- Email address
- Physical characteristics such as biometrics
Personal information can also be considered sensitive. Consider for example sensitive financial or health information. When combined with personal information, this information becomes personal and sensitive. The protection of this data is increasingly important when you consider the risks posed by improper use or unauthorized disclosure to name a few.
For both individuals and organizations, the collection of personal data has many benefits. Individuals can benefit from personalized services and targeted offerings. On the other hand, individuals may be subject to spam and identity theft if data are not protected properly. The organizations can be subject to litigation, negative publicity, and even financial loss.
Numerous methods are used to protect privacy data:
Develop appropriate privacy policies.
Establish the position of a privacy officer.
Conduct training and awareness around data handling.
Consider adequate controls around data retention and data destruction.
Conduct regular risk assessments of access controls.
Limit data access and sharing to only what is required.
Consider security technologies such as encryption.
Privacy laws and regulations vary by industry and region. In North America, many states have their own privacy laws. The following are a few examples of privacy laws at the federal and state level:
Health Insurance Portability and Accountability Act (HIPAA)—The Privacy Rule within Title II of the Act is concerned with the security and privacy of health data.
Gramm-Leach-Bliley Act (GLBA)—The Financial Privacy Rule within GLBA is concerned with the collection and disclosure of personal financial information.
Children’s Online Privacy Protection Act (COPPA)—The COPPA contains provisions for websites collecting personal information from children under 13 years of age
SB1386—This California law regulates the privacy of personal information.
Electronic Communications Privacy Act of 2000—This Act regulates that protects the privacy of email and other electronic communications.
Privacy Act of 1974—Limits are imposed on personal information collected by U.S. federal agencies.
Fair Credit Reporting Act (FCRA)—The use of consumer credit information is regulated.
Personal Information Protection and Electronic Documents Act (PIPEDA)—This Canadian law addresses how organizations collect, use, and disclose personal information.
It is important that IT audits consider privacy data and the application of appropriate privacy controls within organizations. First, consider the laws and regulations across multiple boundaries in which business is conducted. Further, the coordination among general counsel, compliance team, and IT is necessary to understand both the legal and security repercussions.
Finally, organizations should consider a privacy audit. A privacy audit would focus on the following:
What are the privacy laws that apply to the organization?
Are the organizational responsibilities defined and assigned (for example, that of the privacy officer and responsibilities of legal)?
Are policies and procedures for creating, storing, and managing privacy data applied and followed?
Are specific controls implemented to securely transmit sensitive data over the Internet?
One of the main concerns when sending data across public networks is confidentiality. Although not all data are confidential, any data you exchange with a remote resource using a WAN is potentially available for anyone else to see over the INTERNET as illustrated in Figure 11-2. Consider all WANs to be hostile and insecure. Your organization controls access to your LANs and has some measure of assurance of how private the LANs are. WANs are different. You don’t have control over who accesses a WAN or who can access data traveling across it. You must deploy sufficient controls to protect the privacy of any data in the LAN-to-WAN Domain.
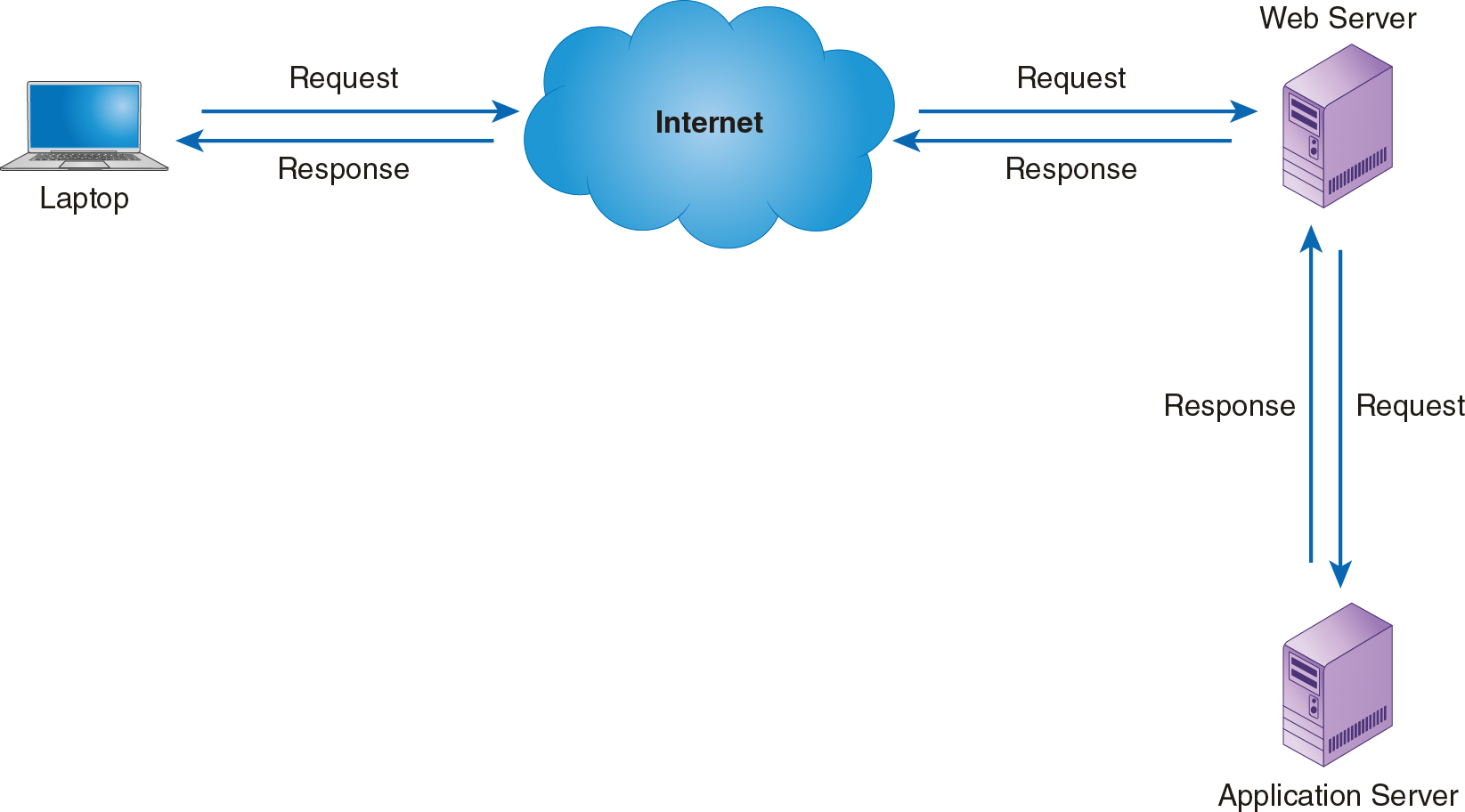
FIGURE 11-2 Exchanging Data with a Remote Service
Implementing Proper Security Controls for the LAN-to-WAN Domain
The primary control type you will use in the LAN-to-WAN Domain for any data passing through is traffic filtering. There are different devices and types of filtering but make sure you aggressively use filtering to stop any inappropriate traffic from flowing in, out, or through your LAN-to-WAN Domain. A collection of well-placed and well-configured firewall devices can dramatically increase your network’s ability to withstand attacks.
Another important control anytime data flows in or out of the LAN-to-WAN Domain is encryption. There are many encryption choices, and the right control depends on how you’ll use the data and which component applies the encryption method. Your application may encrypt your data in another domain. You will learn about different approaches later in this chapter. Some solutions require multiple layers of controls. You select the best controls that support a few general principles:
No data in the LAN-to-WAN Domain should ever be transmitted in cleartext. Anyone can read cleartext data or data that are in the clear.
When using encryption, select the algorithm based on needs. Don’t just select the largest key.
Assume an attacker can intercept and examine any network messages.
A LAN is effective to connect computers within an office or groups of buildings. However, to connect to a customer, vendor, or office across the country or globally, you need to connect to a WAN. Generally, that means connecting through the Internet.
So how do you move data from a secure LAN through an unsecure WAN to a secure LAN? Typically, you would segment a piece of your LAN called a demilitarized zone (DMZ). The term DMZ was taken from the military to describe creating a buffer between two opposing forces. The DMZ sits on the outside of your private network facing the public Internet. These servers provide public-facing access to the business such as public websites. They are especially hardened against security breaches as they are an attack vector. Sitting between the DMZ and internal network are firewalls that filter traffic from the DMZ servers to the private LAN servers. More often than not, the DMZ sits between two layers of firewalls. The first firewall allows limited Internet traffic into the DMZ, and the second highly restricts traffic from the DMZ servers and routes the traffic to the appropriate part of the private network.
A DMZ can control both inbound traffic and outbound traffic. An example of outbound traffic control is content filtering. For example, it may describe the control requirements for employees to limit access to certain websites or to prohibit high bandwidth traffic, such as YouTube videos. Here are several additional examples of policies that deal with LAN-to-WAN connectivity and filtering:
Content blocking tools configuration—Requirements that describe what types of web content should be blocked and how updates are approved
Intrusion detection and prevention tools—Configuration requirements for each product with particular emphasis on that placed in the DMZ
Proxy server—Limit network traffic through specific servers
Firewall configurations—Limit specific network traffic
The auditor should examine procedure and guideline documents. These documents are useful for individuals who must determine how much Internet access should be permitted. The documents establish controls while balancing the risk and the business needs to be connected. The following guideline documents are examples:
DMZ Guidelines—Recommends additional services to be placed in the DMZ and, depending on those services, the additional security requirements
Intrusion Detection and Prevention Systems Guidelines—Recommends how to design an intrusion detection system (IDS) of sensors, collection stations, and alert mechanisms to eliminate or reduce false positives
Content Filtering Guidelines—Recommendations on content filtering options, ways to maintain the list of banned sites, and ways to request access to blocked sites when needed
