Devices and Components Commonly Found in the WAN Domain
The WAN Domain exists to transport network messages from one node to another. In most cases, the WAN is a network that is owned and managed by some other entity. Your ability to affect the WAN’s security is limited or nonexistent. You must ensure that you transmit data across the WAN in a secure fashion using secure protocols and techniques. In this section, you will learn about the devices and components you’ll commonly find in the WAN Domain that support communication, both secure and unsecure. Once you’ve learned about the devices and components, you will learn about controls to ensure compliance in the WAN Domain.
WAN Service Providers
Few organizations have the resources to create and manage their own global WANs. The most common approach to deploying applications and functionality across a WAN is to lease network access from a WAN service provider. A WAN service provider provides WAN bandwidth to subscribing organizations. The WAN transports traffic among subscriber nodes and subscribers pay for the service. The WAN service provider handles all routing, connection media, and hardware issues within the WAN. All the subscribers do is connect to the WAN and use it to send and receive traffic.
The three main concerns when selecting a WAN provider are cost, speed, and stability. Other factors should also be considered when selecting a WAN, but these three are often the most important. Each type of WAN has its own characteristics and works best in different types of environments.
WAN service providers offer several types of WANs for different budgets and performance requirements. Each type of WAN has its strengths and weaknesses. You need to evaluate each option based on your specific needs to find the best fit for your organization. Table 12-1 lists the main types of WANs available from WAN service providers.
TABLE 12-1 WAN options.
| WAN Type | Description | Comments |
|---|---|---|
| Dedicated line/leased line | A point-to-point connection between two physical devices | Most secure, but also one of the most expensive; exclusive access to all bandwidth |
| Circuit switching | A dedicated circuit established between two points for the duration of a conversation | Lower cost, but requires time to establish circuit and circuit switching is slower than the next two options |
| Packet switching | Messages travel in variable-length packets along point-to-point or point-to-multipoint links through WAN switches | Can be substantially faster than circuit switching but media is shared and can suffer congestion |
| Cell relay | Similar to packet switching but with fixed-length cells | Best for transporting voice and data but overhead can reduce speed |
| VPN over Internet | A VPN established between two nodes | Very inexpensive but performance and stability depend on your Internet connection |
Pay attention to the cost of WAN service. Some WAN providers offer services for a fixed monthly fee, whereas other products carry a usage charge. Estimate your monthly usage and calculate your costs for each type of service. That is one of the reasons an SD-WAN is so attractive and more scalable. With SD-WAN, the Internet connection already exists at no additional connection cost to the WAN. Dedicated lines or circuit switching are less scalable as the new connection must be ordered, installed, tested, and is an additional cost.
Dedicated Lines/Circuits
Your particular WAN needs will direct you toward the best WAN choice. If your primary need for a WAN is to connect a small number of LANs to one another, dedicated lines might be the best choice. A dedicated line, also called a dedicated circuit, is a permanent circuit between two endpoints. A single dedicated line works very well when connecting two LANs, campus area networks (CANs), or even metropolitan area networks (MANs). You can connect more than two networks using multiple dedicated lines.
Dedicated lines are fast, secure, and always available. Because no one else shares your dedicated line with you, your organization has exclusive access to the traffic flowing along the line. Of course, the WAN service provider has access to your traffic as well, but no one else should be able to see your traffic. If your budget and connectivity needs support dedicated lines, they can return some of the best performance of all WAN options.
MPLS/VPN WAN or Metro Ethernet
Multiprotocol Label Switching (MPLS) is a very common network model for many midsize and large companies. If your requirements include connecting more than three or four locations—for example, connecting multiple branch offices to the headquarters—dedicated lines will likely be too expensive. Another option in such a case would be MPLS networks supporting a VPN. MPLS works with many WAN technologies and provides very good overall performance using packet-switching and circuit-switching networks. Although MPLS networks are not optimal for high-bandwidth, large-volume network transfers, they work very well in most environments where you need to maintain connections between several other networks.
WAN Layer 2/Layer 3 Switches
Most discussions of network protocols include a discussion of the Open Systems Interconnection (OSI) reference model. The OSI reference model is a generic description for how computers use multiple layers of protocol rules to communicate across a network. The OSI reference model defines seven different layers of communication rules. You will also likely encounter another popular reference model, the Transmission Control Protocol/Internet Protocol (TCP/IP) reference model, when discussing network protocols. The TCP/IP reference model defines four different layers of communication rules. Both models are useful to describe how protocols work and how to implement them in network communications. Figure 12-4 shows the TCP/IP reference model and the OSI reference model.
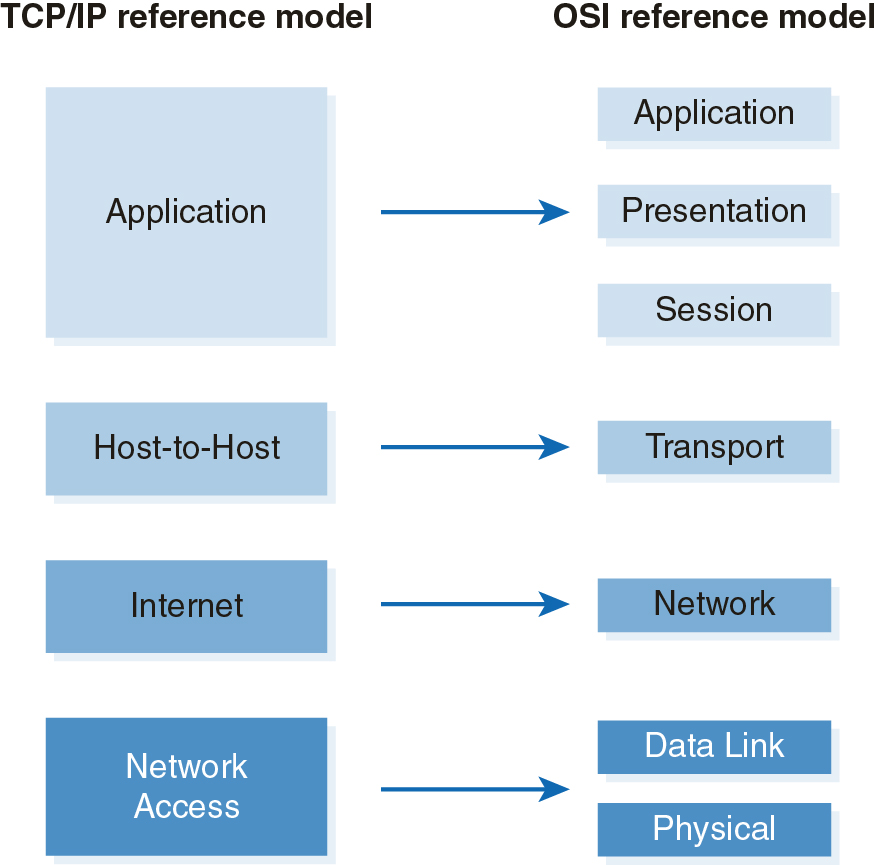
FIGURE 12-4 TCP/IP and OSI Reference models.
You might hear hardware devices or software protocols referred to as Layer 2 devices or Layer 5 protocols. These references generally refer to the OSI reference model layer to describe where the referenced hardware or software operates. In the context of WANs, most WAN protocols operate at OSI Layer 2. MPLS actually operates between Layers 2 and 3 and is sometimes called a Layer 2.5 protocol. Most traditional network switches operate at OSI Layer 2, but newer devices use advanced techniques to provide more sophisticated switching capabilities at OSI Layer 3.
Recall that traditional Layer 2 switches use the Media Access Control (MAC) addresses in each packet to forward the packet to its proper destination. One type of Layer 3 switch extends the concept of a traditional Layer 2 switch by implementing fast Internet Protocol (IP) routing using hardware. Most routing using IP addresses requires software to examine each packet. Software is always slower than hardware, and thus, routing has historically been slower than switching. A Layer 3 switch can greatly speed up routing by using advanced hardware to make the routing decision.
WAN Backup and Redundant Links
All components in all domains can fail. If this happens, it’s important that each component have a backup or alternate component to replace it. Your WAN connection is no exception. If your organization relies on a single WAN connection and that connection fails, access to your WAN fails.
Keep in mind the importance of redundant and alternate WAN connections in the LAN-to-WAN Domain. The issue bears repeating here. Remember that your organization’s ability to use a WAN to communicate with central resources and functions depends on the availability of your WAN to support the connection. A failure anywhere in the WAN violates your organization’s data availability. Make sure you take these steps to protect the availability and security of your data across the WAN Domain:
-
Ensure the SLA for each WAN service provider meets or exceeds the required uptime goals for each WAN.
-
Establish backup or redundant WAN connections—either multiple connections to the same WAN or multiple connections using different WANs.
-
Install backup or redundant connection devices in the WAN Domain to ensure connection hardware failure does not result in a failure to connect to your WAN.
