What Are You Auditing Within the IT Infrastructure?
Across the infrastructure, an audit should focus primarily on the following three objectives:
Examine the existence of relevant and appropriate security policies and procedures.
Verify the existence of controls supporting the policies.
Verify the effective implementation and ongoing monitoring of the controls.
Examining risk and IT controls throughout the IT infrastructure can be complex given the breadth of components across organizations. There are, however, a lot of similarities between different IT departments. It is helpful to define and, if necessary, break up the scope of the audit into manageable areas or domains of security responsibility. Figure 3-1 illustrates these seven domains, which include the following:
User Domain—The end users of the systems, including how they authenticate into the systems.
Workstation Domain—The end users’ operating environment.
LAN Domain—The equipment that makes up the local area network (LAN). A LAN is a computer network for communications between systems covering a small physical area.
LAN-to-WAN Domain—The bridge between the LAN and the wide-area network (WAN). A WAN is a network that covers a large area, often connecting multiple LANs.
WAN Domain—The equipment and activities outside of the LAN and beyond the LAN-to-WAN Domain.
Remote Access Domain—The access infrastructure for users accessing remote systems.
System/Application Domain—Systems on the network that provide the applications and software for the users.
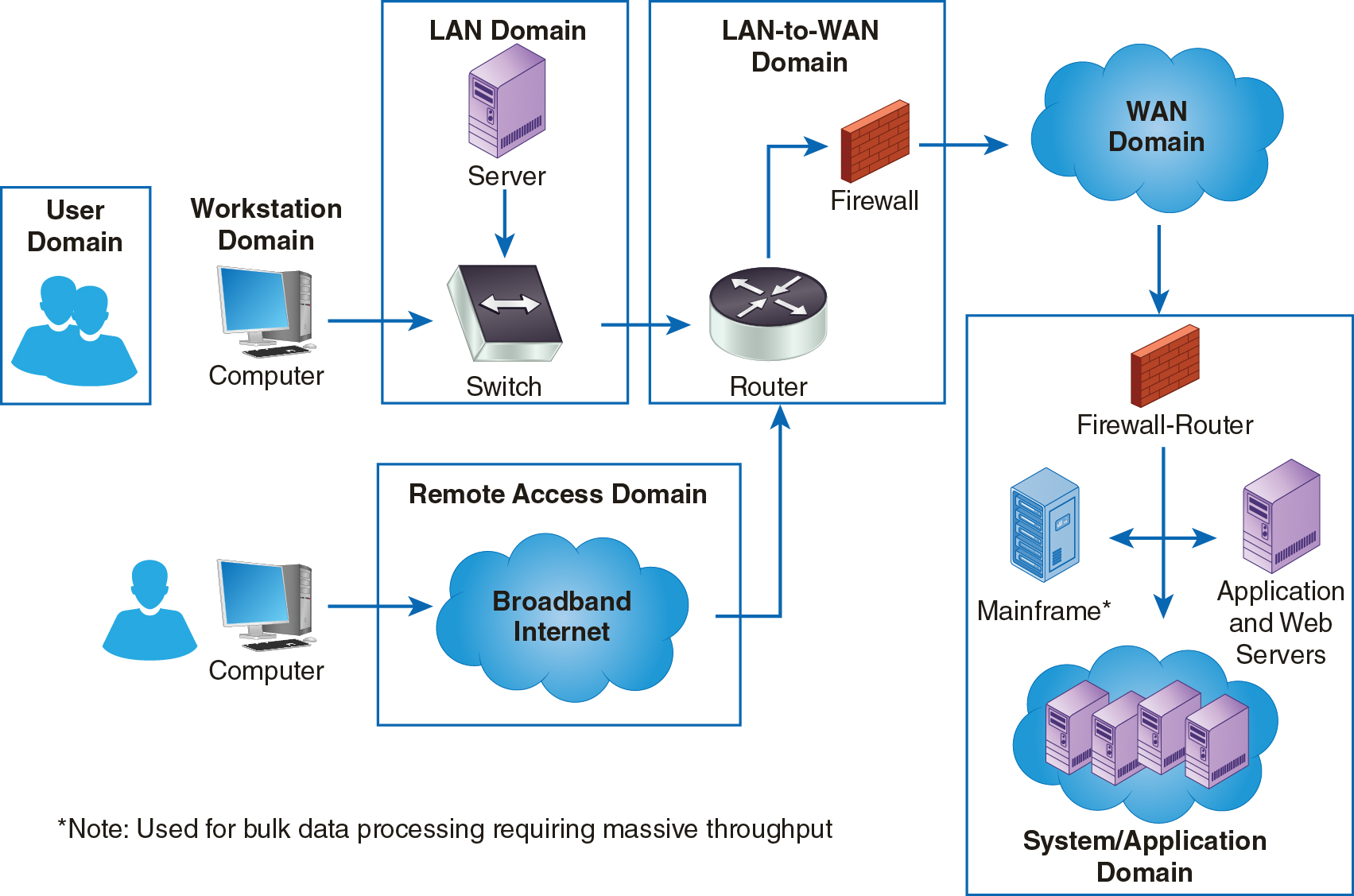
FIGURE 3-1 The seven domains of a Typical IT infrastructure.
Within these seven domains, IT consists of hardware, software, network communications, protocols, applications, and data. Additionally, each domain is implemented within a physical space and includes people interacting with logical and physical aspects of the system. Breaking the audit into domains helps to define clear boundaries and determines the extent by which interconnected systems will be examined. An attacker needs to exploit a vulnerability in only one domain; however, each domain needs to be examined carefully. It only takes an exploit in one domain to weaken the others.
Although it is possible to separate these domains logically, there are many similarities concerning what is audited. For example, the following questions apply across all domains:
Are there adequate policies and procedures in place?
Are operating system security systems following standards and best practices?
Are auditing logs configured, and are they being reviewed?
Are appropriate authentication mechanisms in place?
Are access control lists in place and configured correctly?
Are systems patched from known vulnerabilities?
Are disaster recovery and failover plans in place?
What change control processes are in place, and are they followed?
This list represents only a small sample of questions to be asked and areas to be assessed. What is important to understand is that although each domain has its own unique characteristics, there are many overlapping requirements and controls.
User Domain
The User Domain covers the end users of information systems. An audit of the User Domain should be considered for anyone accessing the organization’s information systems, including not just employees but nonemployees as well, such as contractors and consultants. This domain considers the roles and responsibilities of the users. It should examine all policies that relate to them—specifically, access policies.
The policies that apply might include the following:
Acceptable use policy
System access policy
Internet access policy
Email policy
Additionally, the User Domain includes the method by which the user authenticates to resources. Depending on the organization’s policy, users can authenticate in several ways. Regardless of the method used, the intent is to ensure that users are indeed who they claim to be.
Policies must account for different roles within an organization. To illustrate this point, for purposes of discussion in this chapter we focus on six basic user roles as follows:
Employees —These are regular staff employees of the organization.
System administrator—These are employees who work in the IT department and provide administrative support to the systems and databases.
Security personnel—These individuals are responsible for designing and implementing a security program within an organization.
Contractors—These are temporary workers who can be assigned to any role.
Guests and general public—This is a class or group of users who assess a specific set of applications.
Auditors—These are individuals who evaluate controls for design and effectiveness.
We will discuss users’ unique business requirements for access to information and how access rights are assigned to ensure segregation of duties. Later in this chapter, we align these unique user types to specific security policy examples. Table 3-3 summarizes a high-level mapping of users to their individual needs for access.
TABLE 3-3 Typical Domain User’s need for access.
| TYPE OF USER | NEED FOR ACCESS | TYPICAL ACCESS RIGHTS |
|---|---|---|
| Employees | Need to access specific applications in the production environment | Access is limited to specific applications and information. |
| System Administrators | Need to access systems and databases to support applications | Access is broad and unlimited in context to the role. For example, database administrators may have unlimited access to the database but not the operating system. |
| Security Personnel | Need to protect networks, systems, and applications, and information | Access is provided to set permissions, review logs, monitor activity, and respond to incidents. |
| Contractors | Temporary workers needing the same access as a full-time worker in the same role | Access is the same as a full-time worker. |
| Guest and General Public | Need to access specific application functions | Access is assigned to a type of user and not to the individual. |
| Auditors | Need to review and assess controls | Access often includes unlimited read access to logs and configuration settings. |
Workstation Domain
The Workstation Domain refers to any computing device used by end users. This device is usually a desktop or laptop computer. However, a “workstation” can be any device that accesses data. This includes browsers on a mobile device, such as a smartphone or an Internet-attached device, and includes the following:•
Desktop computers
Laptop computers
Printers
Scanners
Handheld computers and mobile devices
Modems
Wireless access points
Each of these devices should be authorized to access and connect to the organizational network and information resources. Thereafter, an audit of this domain would also ensure proper procedures and controls around maintaining the system hardware and software. Any desktop operating system, for example, should comply with the standards defined by the organization. The audit would take into consideration those security controls already applied. Standard operating systems and patch levels are typically mandated as well as specific configuration controls and the presence of anti-malware, desktop firewalls, and other security controls.
A Malicious Code Protection standard, for example, describes controls for preventing malicious software from infecting a workstation. An example of control statements in a Malicious Code Protection standard would be as follows:
Anti-malware software will be used on all devices connected to the organization’s network. IT staff shall be responsible to ensure that all devices have an approved version and release of anti-malware software installed and that a mechanism is in place to keep malware definitions appropriately current.
In order to prevent malicious code propagation, no executable software, regardless of the source, may knowingly be installed on devices connected to the organization’s networks without prior IT staff approval.
IT staff will verify that software is free of malicious code before it is installed onto a device.
Users must not intentionally disable anti-malware software unless directed to do so by IT staff.
Software and data coming from any device connected to the organization’s network that is distributed to another organization or customer shall be checked using the latest malware definitions and found to be free of malicious code prior to distribution.
If symptoms of malicious code are detected, users shall immediately alert their agency staff.
Users must not try to eradicate malicious code without the assistance and direction of IT staff. Procedures shall be established and relayed to users for handling malicious code contamination incidents.
LAN Domain
The LAN Domain refers to the organization’s LAN infrastructure. A LAN allows two or more computers to connect within a small physical area. The small area could be a home, office, or a group of buildings. LANs provide each computer on the network access to centralized resources, such as file servers and printers. In addition, they provide an easy method by which all the computers can be administered. Various other elements comprise the LAN Domain, including the physical connections required, such as the wiring, and networking equipment, such as hubs and switches. An audit of the LAN Domain can examine various elements, such as the following:
Logon mechanisms and controls for access to the LAN
Hardening and configuration of LAN systems
Backup procedures for servers
The power supply for the network
Each device on the network must be protected or else all devices can be at risk. A LAN is generally considered a trusted zone. Communications across a LAN are not usually protected as thoroughly as they might be if they were sent outside the LAN. A malicious person, for example, might be able to capture data going across the network quite easily. This is more easily done if hubs are used instead of switches. The attacker could simply plug into any network port in the building and capture valuable data. On the other hand, switches would require an attacker to have physical access to the switch. To prevent this, switches must be placed in secured rooms or secured closets.
LAN-to-WAN Domain
While a LAN typically covers a smaller defined geographical area, a WAN provides for long-distance communication to extend a network across a wider geographic area. Thus, a WAN can connect multiple LANs together. The transition from a LAN to a WAN typically involves equipment such as a router or a firewall. A router is used to forward data between different networks. A firewall is another common component. A firewall is placed between networks and is designed to permit authorized access while blocking everything else.
The WAN Domain is considered an untrusted zone. It might be made up of components outside the direct control of the organization and is often more accessible by attackers. The area between the trusted and untrusted zone, the LAN-to-WAN Domain, is protected with one or more firewalls. This is also called the boundary, or edge.
The public side of the boundary is often connected to the Internet and has public Internet Protocol (IP) addresses. These IP addresses are accessible from anywhere in the world. Attackers constantly probe public IP addresses looking for open ports and vulnerabilities. A high level of security is required to keep the LAN-to-WAN Domain secure.
An audit is critical to ensure that the environment is controlled correctly to prevent unauthorized access. Many components and controls work together to provide security. Organizations should carefully manage the configurations of all devices in this domain, such as firewalls, routers, and intrusion detection systems.
A Firewall Controls standard, for example, describes how LAN firewalls should handle application traffic. This kind of traffic includes web, email, and telnet traffic. The standard should also describe how the firewall should be managed and updated. The following are examples of statements from a typical Firewall Control standard: The default policy for the firewall for handling inbound traffic must block all packets and connections unless the traffic type and connections have been specifically permitted.
The firewall standard, for example, may block the following types of traffic:
Inbound traffic from a nonauthenticated source system with a destination address of the firewall system itself. This type of packet normally represents some type of probe or attack against the firewall. One common exception to this rule would be in the event the firewall system accepts delivery of inbound email (SMTP on port 25). In this event, the firewall must allow inbound connections to itself, but only on port 25.
Inbound traffic with a source address indicating that the packet originated on a network behind the firewall. This type of packet likely represents some type of spoofing attempt.
Inbound traffic containing ICMP (Internet Control Message Protocol) traffic. Since ICMP can be used to map the networks behind certain types of firewalls, ICMP must not be passed in from the Internet or any untrusted external network.
Reproduced from Wack, John, Ken Cutler, and Jamie Pole. 2002. “Guidelines on Firewalls and Firewall Policy: Recommendations of the National Institute of Standards and Technology.” National Institute of Standard sand Technology. https://www.usmd.edu/usm/adminfinance/itcc/firewallpolicynis.pdf
WAN Domain
The WAN Domain provides end-to-end connectivity between LANs. Like the LAN-to-WAN Domain, this environment includes routers, firewalls, and intrusion detection systems, but it also has many more telecommunications components. Examples include channel service unit/data service unit, codecs, and backbone circuits.
For most private businesses, the WAN is the Internet. A business may, however, lease semiprivate lines from telecommunications companies. These lines are semiprivate because they are rarely leased by only a single company. Instead, they are shared with other unknown companies. Again, the Internet is an untrusted zone. Any host on the Internet with a public IP address is at significant risk of attack, and you should expect any host on the Internet to be attacked even if that just means it is scanned for open ports and vulnerabilities. A significant amount of security is required to keep hosts in the WAN Domain safe. WAN audits help ensure the WAN is operating and configured as expected and is conforming to corresponding policies and standards.
Control standards for the LAN-to-WAN Domain address webpage content and access controls, Internet user proxy controls, demilitarized zone (DMZ) architecture controls, and more.
Remote Access Domain
The Remote Access Domain refers to the technology that controls how end users connect to an organization’s LAN remotely. An example is someone who needs to connect to the office network from their home or on the road. The Remote Access Domain is made up of authorized users who access organization resources remotely. Access most often occurs over unsecured transports such as the Internet. Other unsecured transports include dial-up via a modem. Mobile workers often need access to the private LAN while traveling or working from home, for example. Mobile workers are granted this access using remote access solutions, such as a virtual private network (VPN), can create an encrypted communications tunnel over a public network such as the Internet. Because the Internet is largely untrusted, remote access might represent a significant risk. Attackers can access unprotected connections. They might try to break into the remote access servers as well. Using a VPN is an example of a control to reduce the risk. VPNs, however, have their vulnerabilities. For example, how does a user authenticate with the VPN? An attacker can gain access via the secured encrypted tunnel back to the corporate data just by knowing or guessing the credentials of the authorized user.
An audit should carefully consider the governing policies and procedures as well as the type of access provided.
For example, a VPN control standard may describe the security requirements for VPN and other remote access connections to the organization’s network. The following are examples of control statements you might find in this standard:
Approved users (employees and authorized vendors) may use the VPN services.
VPN use is to be controlled using either a one-time password authentication such as a token device or a public/private key system with a strong passphrase as described in the Multifactor Authentication to VPN Standard.
When actively connected to the corporate network, VPNs will force all traffic to and from the computer over the VPN tunnel: all other traffic will be dropped.
Dual (split) tunneling is NOT permitted; only one network connection is allowed.
VPN gateways will be set up and managed by the organization’s network operational groups.
All computers connected to the organization’s internal networks via VPN or any other technology must use the most up-to-date anti-virus software that is the corporate standard (provide URL to this software); this includes personal computers.
VPN users will be automatically disconnected from the organization's network after 30 minutes of inactivity. The user must then log on again to reconnect to the network.
The VPN concentrator is limited to an absolute connection time of 24 hours.
Users of computers that are not organization-owned equipment must configure the equipment to comply with the organization's VPN and network policies.
Only InfoSec-approved VPN clients may be used.
System/Application Domain
The System/Application Domain is made up of the many systems and software applications that users access. This, for example, includes mainframes, application servers, web servers, proprietary software, and applications. Mail servers send and receive email. Database servers host data that are accessed by users, applications, or other servers. Domain Name System (DNS) servers provide name-to-IP address resolution for clients. Knowledge within this domain can be very specialized. Operators may focus on one specific aspect, such as mail servers, and be quite familiar with associated security ramifications. On the other hand, that same person might know very little about databases.
Like the desktop operating system, server operating systems should be hardened to authorized baselines and configured according to policies and standards with the appropriate controls.
An Information Classification standard, for example, helps employees determine the classification of information that’s generated, accessed, transmitted, and stored by the organization. This type of control standard also helps you identify procedures to protect the confidentiality, integrity, and availability of organizational data based on its classification. Information classification is also essential for complying with local and federal regulations regarding privacy and confidentiality of information. The following are example control statements in an information classification standard:
All employees and contractors share in the responsibility for ensuring that the organization’s information assets receive an appropriate level of protection by observing this Information Classification policy.
Company managers or information “owners” shall be responsible for assigning classifications to information assets according to the standard information classification system presented.
Where practicable, the information category shall be embedded in the information itself.
All company associates shall be guided by the information category in their security-related handling of company information.
