IT Security Assessment Results: Risk, Threats, and Vulnerabilities
Any existing security assessment should include details about risk as part of the workpapers. Details include full documentation of the identified threats, vulnerabilities, and resulting risks. The findings inform management of the resulting risk to the environment. This information provides management with the data necessary to make informed decisions to manage risk. The results will help drive how resources are allocated to address potential uncertainties.
The key components of the assessment should include the following:
Introduction—This provides the purpose and scope of the assessment. This includes the systems, personnel, locations, and other details about the assessed environment.
Approach—This describes the methods taken. This includes those involved as part of the assessment and the techniques and tools used to collect information. A description of the risk scale or matrix used should also be discussed.
System characterization—This provides details about the infrastructure systems. This includes the hardware, software, data, interfaces, and associated users. A discussion of existing technical, management, and operational controls may be included.
Threat statement—This is a complete outline of potential threat sources and associated activities.
Assessment results—This provides details on vulnerabilities and threats—specifically, the pairing of threats with vulnerabilities that can be exploited.
Summary—This provides a concise review of the observations as well as risk levels. This may include any recommendations.
The assessment should describe the approach in detail. This includes the methodology used and details about the approach and definitions. A good practice is to use an established approach to assessing risks. Table 7-1, Table 7-2, Table 7-3, and Table 7-4 are adapted from NIST SP 800-30, “Risk Management Guide for Information Technology Systems.”
TABLE 7-1 Likelihood determination ratings and descriptions.
| Likelihood Level | Weight Factor | Description |
|---|---|---|
| High | 1.0 | The threat source is highly motivated, and sufficiently capable and controls to prevent the vulnerability from being exercised are ineffective. |
| Medium | 0.5 | The threat source is motivated and capable, but controls are in place that may impede successful exercise of the vulnerability. |
| Low | 0.1 | The threat source lacks motivation or capability, or controls are in place to prevent or at least significantly impede the vulnerability from being exercised. |
TABLE 7-2 Impact levels and descriptions.
| Magnitude of Impact | Weight Factor | Impact Description |
|---|---|---|
| High | 100 | Exercise of the vulnerability may result in a highly costly loss of major tangible assets or resources. Exercise of the vulnerability may significantly violate, harm, or impede an entity’s mission, reputation, or interest. Exercise of the vulnerability may result in human death or serious injury. |
| Medium | 50 | Exercise of the vulnerability may result in the costly loss of tangible assets or resources. Exercise of the vulnerability may violate, harm, or impede an entity’s mission, reputation, or interest. Exercise of the vulnerability may result in human injury. |
| Low | 10 | Exercise of the vulnerability may result in the loss of some tangible assets or resources. Exercise of the vulnerability may noticeably affect an entity’s mission, reputation, or interest. |
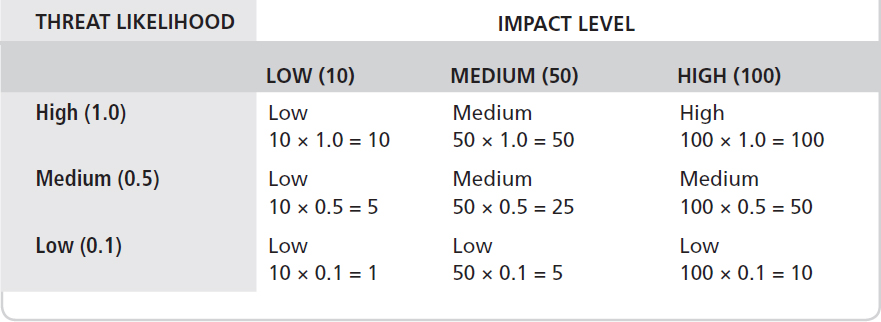
TABLE 7-3 Resulting risks as a product of impact and threat likelihood.
TABLE 7-4 Risk level descriptions.
| Risk Level | Risk Description |
|---|---|
| High | If an observation or finding is evaluated as a high risk, there is a strong need for corrective measures. An existing system may continue to operate, but a corrective action plan must be put in place as soon as possible. |
| Medium | If an observation is rated as medium risk, corrective actions are needed, and a plan must be developed to incorporate these actions within a reasonable period of time. |
| Low | If an observation is described as low risk, management must determine whether corrective actions are still required or decide to accept the risk. |
Table 7-1 provides the definitions for determining the likelihood of a threat. The assessment should then describe the next step to determine the impact that would result from a vulnerability being exploited. Table 7-3 provides the impact levels and associated definitions. Next, the report should provide a determination of the resulting risk. The resulting risk is based on the threat likelihood and the impact the threat would have if successful. Table 7-4 provides the method to determine risk. It is based on multiplying the likelihood of a threat occurring by the impact the threat might have.
Risk level can be assigned to each audit finding. The risk level can be based on the resulting product of threat likelihood multiplied by the impact level provides a rating of risk. In this example, it would be categorized as low, medium, or high. Table 7-5 provides the description of the resulting rating. This also includes actions that must be taken as a result.
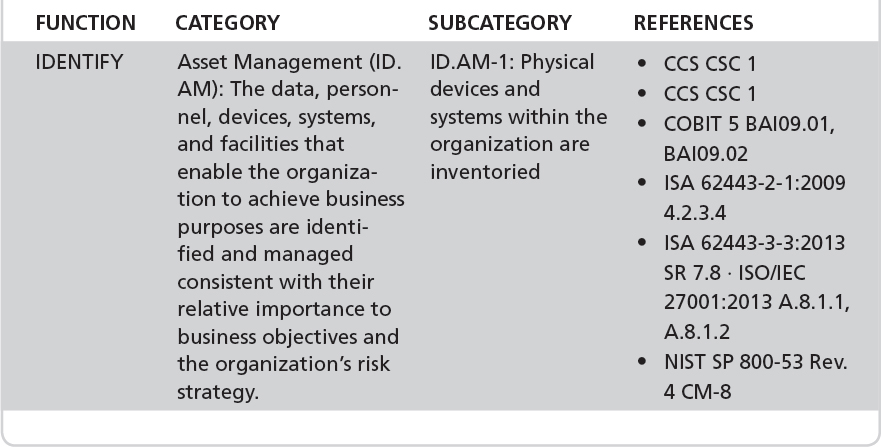
TABLE 7-5 NIT CSF Cybersecurity Framework mapping for ID.AM-1.
The results of the assessment should include a pairing of identified vulnerabilities with associated threats. For each pair, the report includes a brief description of the threat and vulnerability. It should also give a description of existing controls in place to reduce the risk. The results from the previous tables should also be included as summary items. This includes the threat likelihood rating, risk impact rating, and overall risk rating.
The following is an example of a vulnerability/threat pair analysis: “Weak passwords are vulnerable to hackers.” These passwords are more easily guessed or cracked by automated programs. The existing control enforces passwords to be alphanumeric and at least five characters long. The likelihood, impact, and risk rating are all medium. As a result of the risk, a recommended control such as increasing password complexity or length should be documented.