Anatomy of a User Domain
The User Domain is the part in the IT infrastructure that formalizes how information flows in and out of computer systems. This domain defines components you need to control to ensure your environment is compliant with applicable requirements. Figure 8-1 shows the User domain in the context of the seven domains in the IT infrastructure.
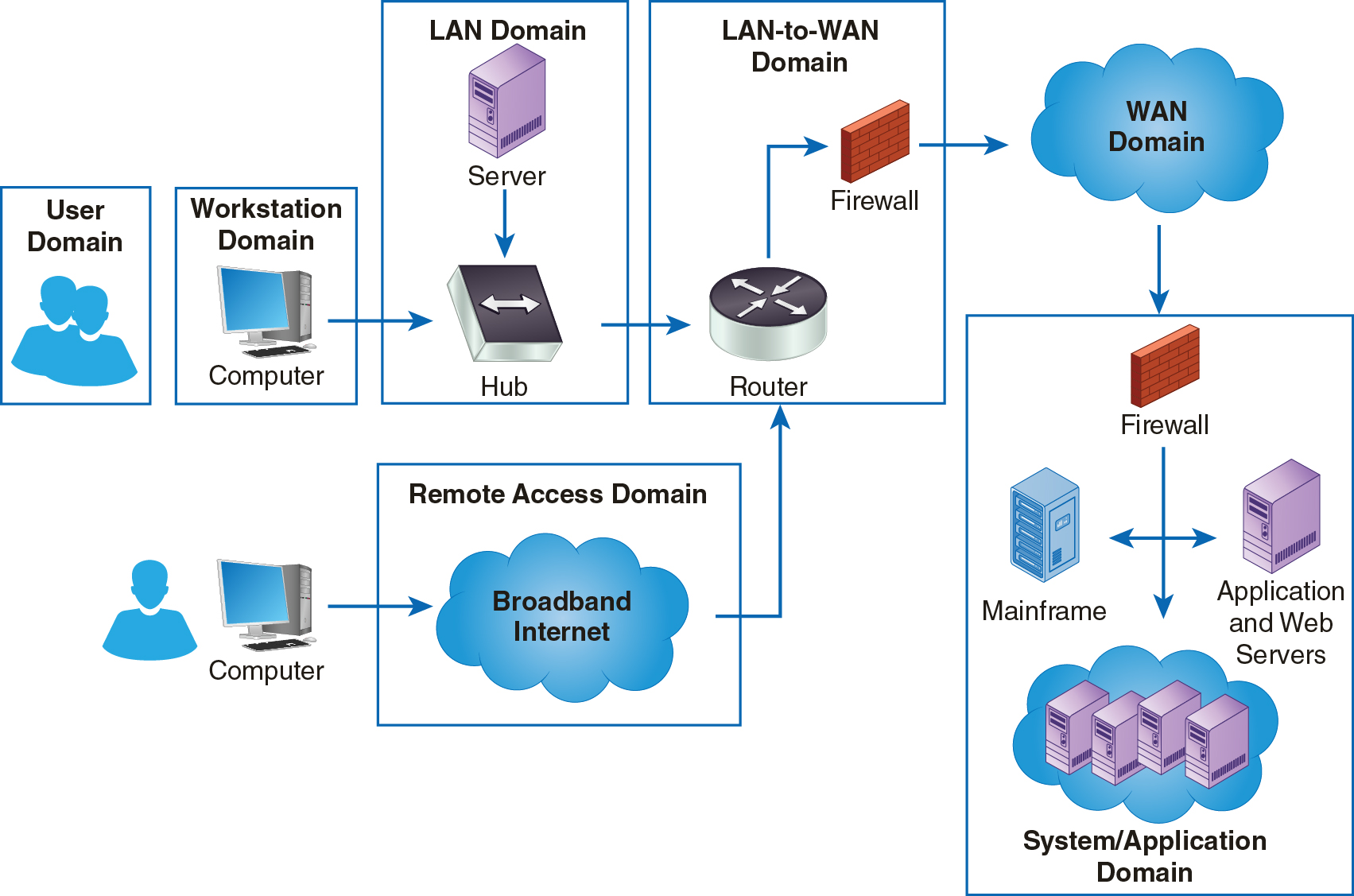
FIGURE 8-1 The User Domain Within the Seven Domains of a Typical IT Infrastructure
User Domain controls are designed to help ensure compliance by placing limits on acceptable user actions. A User Domain control is any mechanism that interacts with a user and reacts when a user’s actions meet certain conditions. The overall purpose of User Domain controls is to restrict user behavior to approved, or compliant, behavior. The User Domain consists of a variety of types of users. Each user type has unique access needs. As the different types of users in the domain grow so does the security complexity. At a minimum, each type of user has unique business needs and, thus, will require unique rights to access certain information.
By limiting what users can do, compliance-related security controls restrict users to appropriate actions. These restrictions can include limits on what users can access and what actions they can perform. Although limiting users to meet compliance requirements might be desirable or even necessary, it can make it more difficult to complete required business functions. One of the difficulties of ensuring security in the User Domain is designing secure controls that still allow and promote necessary business functions.
It is important that you implement compliance requirements in a way that minimizes the impact on business drivers. Business drivers are the components, including people, information, and conditions, that support business objectives. Any negative impact on business drivers can also have a negative impact on your organization’s ability to satisfy business objectives. Carefully research the impact on business drivers before you implement any compliance controls.
Compliance requirements dictate how your organization conducts its activities. Whether the compliance requirement comes from legislation, regulation, industry requirements, or even your organization’s standards, the result is focus. In most cases, your organization can control activities to ensure compliance in multiple ways. Always consider alternative controls to achieve the result that compliance requires. You will find that some controls are less costly and less intrusive than others. Do not just accept the first control that does the job. Often, other controls are just as good but intrude less on your organization’s activities.
You can meet many compliance requirements using one of several controls. If one control has a negative impact on business drivers, consider another control. You can often justify eliminating one control if another control will achieve the same goal (see Figure 8-2).
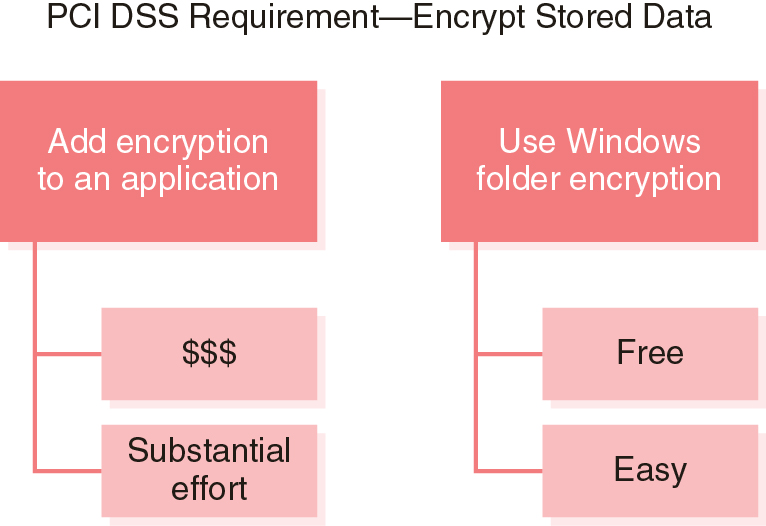
FIGURE 8-2 Alternative Controls
Protecting Data Privacy
Most organizations are composed of many different departments and lines of business. An employee may be full time or part time. An employee may be in a customer-facing role or a back-office corporate function. Regardless of their job in the organization, they will have access to information that needs to be protected.
Each of these users must understand their role and the proper handling of sensitive and private information. Knowing who is accessing the organization’s information and ensuring these individuals are well educated is essential to the success of implementing security policies. These core requirements, employee authentication, and education must be outlined in security policies. Employee access must be managed throughout the life of an employee’s career with the organization. There is always pressure to grant and extend user access so a user can be as productive as possible. There is little tolerance by some executives to wait weeks for access to be set up after an employee joins an organization. Often there is a need to extend the user’s access in response to changing business needs. While there’s significant pressure to grant employees new access rights, the same pressure may not exist to remove access.
An audit should verify that these pressures do not result in shortcuts that could put customers and sensitive data at risk. For example, Health Insurance Portability and Accountability Act (HIPAA) regulation requires all users to be properly trained on how to handle health information. Making sure records reflect the user received training prior to being granted access is one method to assess the effectiveness of this control.
Implementing Proper Security Controls for the User Domain
It takes careful planning in any domain to develop multiple layers of proper security controls. Control layers should complement other layers and work together to avoid exposing a single point of failure. In the User Domain, an acceptable use policy (AUP) for each type of user serves as a training guide and direction document for other controls. Simply put, the AUP is a statement of which actions are acceptable and which ones are not.
The AUP is not the only security control for the User Domain, but it is an important one. Solid User Domain controls help ensure compliance with your organization’s security policy. As you design controls, make sure you develop multiple layers to protect each resource. Your goal should be to force an attacker to defeat several controls to compromise a resource. That way, no single control failure exposes a resource to an attack. But before you can design solid controls, you need to explore components commonly found in the User Domain.
