Firewall Basics
A firewall is a device that connects two or more networks together and restricts the flow of information between the two or more networks according to rules configured in a firewall rule base.
Firewalls have been in use for more than 20 years, but only in the past 10 years (because of the rapid growth of the Internet) has the need for firewalls increased, along with their capabilities.
In an ideal world, a firewall would not be required. You could just allow everybody full access to all your resources, and you could trust them to access what they required. However, in the real world, firewalls have become a necessity for all organizations to limit the access to their resources to users who require access to those resources.
The Internet is a great business enabler, connecting businesses together across the entire world. However, with this enabler comes a great risk. Numerous individuals and organizations specialize in hacking (breaking into other people’s networks for fun or profit).
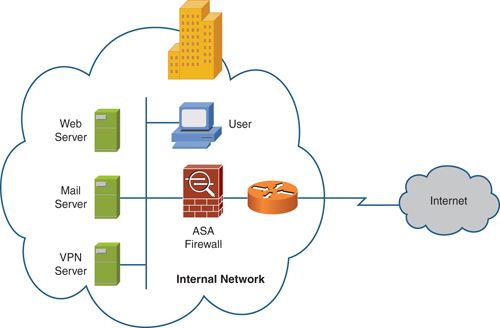
Figure 1 shows a a typical firewall deployment.
Firewalls are deployed to mitigate such risk, allowing the organization to enforce a policy on the firewall that states what can and cannot be accessed. Note, however, that the firewall is only as good as the configuration deployed on it. If the configuration allows an attacker access to a resource, the firewall is not performing in its intended role.
Three types of firewalls are in use today, and are based on the following technologies:
![]() Packet filtering
Packet filtering
![]() Proxy server
Proxy server
![]() Stateful packet filtering
Stateful packet filtering
Packet Filtering
Packet filtering is the oldest type of firewall technology, and it is still put to good use today. Because the name suggests, a packet filter based on an access control list (ACL) is applied to an interface to filter packets traversing the interface. The ACL dictates the security policy or firewall rule base and specifies what traffic can and cannot traverse the firewall.
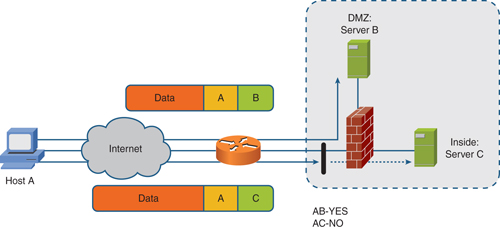
Figure 2 shows a simple packet filter in place.
Most Cisco network devices perform some level of packet filtering implemented as ACLs.
Proxy Servers
Generally, a proxy server is an application that acts as a proxy for a service. The traditional use of a proxy server has been for web traffic. In this instance, a proxy server exists on the inside of the network. Clients are configured to channel any web requests through the proxy server. The proxy server uses its own security features to restrict those who can and cannot use the service.
Because these devices operate at higher layers in the OSI model, they can be resource intensive and may perform more slowly under stress.
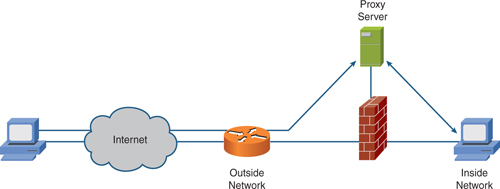
Figure 3 shows the placement of a proxy server within a network.
Stateful Packet Filtering
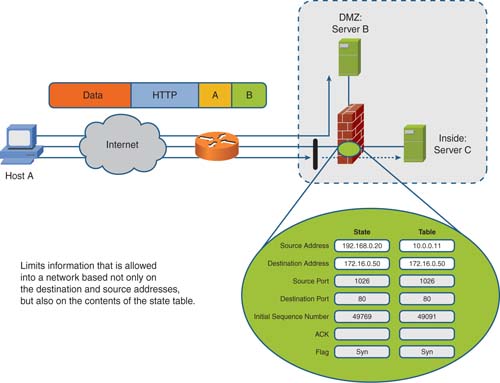
Stateful packet filtering is the method deployed by Cisco Firewall appliances. A stateful packet filter is implemented similarly to a standard packet filter, with the primary difference being that a stateful packet filter maintains complete session state. Every TCP connection or UDP flow, both inbound and outbound, is logged into the stateful session flow table.
All inbound and outbound packets are compared against the session flow table. Return data is permitted through the firewall even though a distinct rule does not allow it based on its entry in the session table. The outbound initiation of a connection permits the return of the traffic.
Figure 4 shows stateful packet filtering.
The Cisco Adaptive Security Appliance
The Cisco Adaptive Security Appliance (ASA) is a key component in the Cisco end-to-end security solution. The ASA is now the market-leading Cisco security appliance and provides enterprise-class, integrated network security services.
The ASA product line offers cost-effective, easy-to-deploy solutions. The product line ranges from compact “plug-and-play” desktop firewalls for small offices to carrier-class gigabit firewalls for the most demanding enterprise and service-provider environments.
Cisco ASA features include the following:
![]() State-of-the-art stateful packet inspection firewall
State-of-the-art stateful packet inspection firewall
![]() User-based authentication of inbound and outbound connections
User-based authentication of inbound and outbound connections
![]() Integrated protocol and application inspection engines that examine packet streams at Layers 4 through 7
Integrated protocol and application inspection engines that examine packet streams at Layers 4 through 7
![]() Highly flexible and extensible modular security policy framework
Highly flexible and extensible modular security policy framework
![]() Robust virtual private network (VPN) services for secure site-to-site and remote-access connections
Robust virtual private network (VPN) services for secure site-to-site and remote-access connections
![]() Clientless and client-based Secure Sockets Layer (SSL) VPN
Clientless and client-based Secure Sockets Layer (SSL) VPN
![]() Full-featured intrusion prevention system (IPS) services for day-zero protection against threats, including application and operating system vulnerabilities, directed attacks, worms, and other forms of malware
Full-featured intrusion prevention system (IPS) services for day-zero protection against threats, including application and operating system vulnerabilities, directed attacks, worms, and other forms of malware
![]() Content security services, including URL filtering, antiphishing, antispam, antivirus, antispyware, and content filtering using Trend Micro technologies
Content security services, including URL filtering, antiphishing, antispam, antivirus, antispyware, and content filtering using Trend Micro technologies
![]() Multiple security contexts (virtual firewalls) within a single appliance
Multiple security contexts (virtual firewalls) within a single appliance
![]() Stateful active/active or active/standby failover capabilities that ensure resilient network protection
Stateful active/active or active/standby failover capabilities that ensure resilient network protection
![]() Transparent deployment of security appliances into existing network environments without requiring re-addressing of the network
Transparent deployment of security appliances into existing network environments without requiring re-addressing of the network
![]() Intuitive single-device management and monitoring services with the Cisco Adaptive Security Device Manager (ASDM) and enterprise-class multidevice management services through Cisco Security Manager
Intuitive single-device management and monitoring services with the Cisco Adaptive Security Device Manager (ASDM) and enterprise-class multidevice management services through Cisco Security Manager
Cisco ASA Product Family
The Cisco ASA product family currently consists of six different models. These range in use all the way from a small office up to an enterprise or service provider network. Because you might expect, the higher the model, the higher the throughput, number of ports, and cost.
The product range consists of the following devices:
Cisco ASA 5505
Cisco ASA 5510
Cisco ASA 5520
Cisco ASA 5540
Cisco ASA 5550
Cisco ASA 5580-20
Cisco ASA 5580-40
Figure 5 shows the Cisco ASA product family.
Cisco ASA 5505
The ASA 5505 is available in two models: a Base model and a Security Plus model. The ASA 5505 is aimed at small businesses, branch offices, and enterprise teleworkers. The ASA 5505 is a small form factor appliance.
![]() Maximum throughput:150 Mb/s
Maximum throughput:150 Mb/s
![]() Maximum connections:10,000 (25,000 Security Plus)
Maximum connections:10,000 (25,000 Security Plus)
![]() Maximum connections/sec:4,000
Maximum connections/sec:4,000
![]() Maximum 3DES/AES throughput:100 Mb/s
Maximum 3DES/AES throughput:100 Mb/s
![]() Maximum VPN sessions:10 (25 Security Plus)
Maximum VPN sessions:10 (25 Security Plus)
![]() Maximum SSL VPN sessions:25
Maximum SSL VPN sessions:25
Cisco ASA 5510
The ASA 5510 is available in two models: a Base model and a Security Plus model. The ASA 5510 is aimed at deployment at the Internet edge. The ASA 5510 is a 19” 1U rack-mountable appliance.
![]() Maximum throughput:300 Mb/s
Maximum throughput:300 Mb/s
![]() Maximum connections:50,000 (130,000 Security Plus)
Maximum connections:50,000 (130,000 Security Plus)
![]() Maximum connections/sec:9,000
Maximum connections/sec:9,000
![]() Maximum 3DES/AES throughput:170 Mb/s
Maximum 3DES/AES throughput:170 Mb/s
![]() Maximum VPN sessions:250
Maximum VPN sessions:250
![]() Maximum SSL VPN sessions:250
Maximum SSL VPN sessions:250
Cisco ASA 5520
The ASA 5520 is aimed at deployment at the Internet edge. The ASA 5520 is a 19” 1U rack-mountable appliance.
![]() Maximum throughput:450 Mb/s
Maximum throughput:450 Mb/s
![]() Maximum connections:280,000
Maximum connections:280,000
![]() Maximum connections/sec:12,000
Maximum connections/sec:12,000
![]() Maximum 3DES/AES throughput:225 Mb/s
Maximum 3DES/AES throughput:225 Mb/s
![]() Maximum VPN sessions:750
Maximum VPN sessions:750
![]() Maximum SSL VPN sessions:750
Maximum SSL VPN sessions:750
Cisco ASA 5540
The ASA 5540 is aimed at deployment at the Internet edge. The ASA 5540 is a 19” 1U rack-mountable appliance.
![]() Maximum throughput:650 Mb/s
Maximum throughput:650 Mb/s
![]() Maximum connections:400,000
Maximum connections:400,000
![]() Maximum connections/sec:25,000
Maximum connections/sec:25,000
![]() Maximum 3DES/AES throughput:325 Mb/s
Maximum 3DES/AES throughput:325 Mb/s
![]() Maximum VPN sessions:5,000
Maximum VPN sessions:5,000
![]() Maximum SSL VPN sessions:2,500
Maximum SSL VPN sessions:2,500
Cisco ASA 5550
The ASA 5550 is aimed at deployment at the Internet edge or within a campus network environment as an internal firewall. The ASA 5550 is a 19” 1U rack-mountable appliance.
![]() Maximum throughput:1.2 Gb/s
Maximum throughput:1.2 Gb/s
![]() Maximum connections:650,000
Maximum connections:650,000
![]() Maximum connections/sec:36,000
Maximum connections/sec:36,000
![]() Maximum 3DES/AES throughput:425 Mb/s
Maximum 3DES/AES throughput:425 Mb/s
![]() Maximum VPN sessions:5,000
Maximum VPN sessions:5,000
![]() Maximum SSL VPN sessions:5,000
Maximum SSL VPN sessions:5,000
Cisco ASA 5580
The ASA 5580 is available in two models: the ASA 5580-20 and the ASA 5580-40. Both models are aimed at service provider or data center deployments and for use as internal firewalls for campus networks. Both ASA 5580 models are 3U 19” rack-mountable appliances.
![]() Maximum throughput:5 Gb/s (10 Gb/s 5580-40)
Maximum throughput:5 Gb/s (10 Gb/s 5580-40)
![]() Maximum connections:1,000,000 (2,000,000 5580-40)
Maximum connections:1,000,000 (2,000,000 5580-40)
![]() Maximum connections/sec:90,000 (150,000 5580-40)
Maximum connections/sec:90,000 (150,000 5580-40)
![]() Maximum 3DES/AES throughput:1 Gb/s
Maximum 3DES/AES throughput:1 Gb/s
![]() Maximum VPN sessions:10,000
Maximum VPN sessions:10,000
![]() Maximum SSL VPN sessions:10,000
Maximum SSL VPN sessions:10,000
Service Modules
The features and functionality of the ASA can be enhanced by introducing a Security Services Module (SSM) into the ASA. You can install SSMs into the 5510, 5520, and 5540 appliances.
NOTE
Because the ASA has only a single SSM slot, it is important to select the appropriate SSM based on your requirements.
Currently, three SSMs are available for the ASA:
![]() Advanced Inspection and Prevention Security Services Module (AIP SSM)
Advanced Inspection and Prevention Security Services Module (AIP SSM)
![]() Content Security and Control Security Services Module (CSC SSM)
Content Security and Control Security Services Module (CSC SSM)
![]() 4-Port Gigabit Ethernet SSM
4-Port Gigabit Ethernet SSM
Figure 6 shows a Cisco ASA SSM.
AIP SSM
The AIP SSM provides a full-featured IPS on a module that it used to stop malicious traffic such as viruses, worms, and directed attacks from entering your network. The AIP SSM is configured the same as the standalone Cisco IPS appliances and benefits from the same code and signature databases as the standalone IPS appliances.
The AIP SSM comes in three models:
![]() AIP-SSM-10 provides 150-Mb/s throughput on the ASA 5510 and 225-Mb/s throughput on the ASA 5520.
AIP-SSM-10 provides 150-Mb/s throughput on the ASA 5510 and 225-Mb/s throughput on the ASA 5520.
![]() AIP-SSM-20 provides 375-Mb/s throughput on the ASA 5520 and 500-Mb/s throughput on the ASA 5540.
AIP-SSM-20 provides 375-Mb/s throughput on the ASA 5520 and 500-Mb/s throughput on the ASA 5540.
![]() AIP-SSM-40 provides 450-Mb/s throughput on the ASA 5520 and 650-Mb/s throughput on the ASA 5540.
AIP-SSM-40 provides 450-Mb/s throughput on the ASA 5520 and 650-Mb/s throughput on the ASA 5540.
CSC SSM
The CSC SSM provides a content security solution within the ASA. The CSC SSM is based on software from Trend Micro that enables you to inspect traffic such as HTTP and Simple Mail Transfer Protocol (SMTP) for viruses, Trojans, and other malicious files.
The CSC SSM works in the same way as most standalone content security platforms, but one benefit is that you can totally integrate it into the ASA without incurring cost of owning a dedicated server to perform the same role.
4-Port Gigabit Ethernet SSM
The 4-port Gigabit Ethernet SSM provides an extra four ports of connectivity to the ASA. The SSM has four copper RJ-45 interfaces and four fiber small form-factor pluggable (SFP) interfaces, but only the copper or fiber interfaces can be used and not a mixture of both (which, if possible, would provide four more interface ports).