Information Security Awareness and Training
Personnel are the weakest link in information security, mainly because of lapses in judgment, inattentiveness, fatigue, work pressure, or a shortage of skills. Personnel are generally considered the largest and most vulnerable portion of an organization’s attack surface. People are sometimes tricked by social engineering attacks such as phishing e-mails that provide attackers with an entry point into an organization’s network. In larger organizations, attackers who send phishing messages to hundreds or thousands of personnel are almost assured that at least one of those people will click a link or open an attachment, leading to the potential compromise of the user’s workstation—the beachhead that the attacker needs to go farther into the network and reach their ultimate objective.
Many organizations conduct security awareness training so that personnel are aware of these common attacks as well as several other topics that mainly fall into the category known as Internet hygiene, which is the safe use of computers and mobile devices while accessing the Internet.
Security Awareness Training Objectives
The primary objective of a security awareness program is the keen awareness, on the part of all personnel, of the different types of attacks they may encounter, together with knowledge of what they are expected to do (and not do) in various situations. Further, personnel are to understand and comply with an organization’s acceptable use policy, security policy, privacy policy, and other applicable policies.
Better security awareness training programs include opportunities to practice skills and include a test at the end of training. In computer-based training, users should be required to successfully pass the test with a minimum score—70 percent is a typical minimum score to complete the course. The best security awareness training courses, whether in-person or online, are engaging and relevant. Although some organizations conduct security awareness training for compliance purposes, many organizations do so for security purposes, with a genuine interest in personnel getting the most value out of the training. The point of security awareness training is, after all, the reduction of risk.
Business records should be created to document when each person receives training. Many organizations are subject to information security regulations that require personnel to complete security awareness training; business records provide ample evidence of users’ completion of training.
Creating or Selecting Content for Security Awareness Training
Security managers need to develop or acquire security awareness training content for organization personnel. The content that is selected or developed should have the following characteristics:
• Understandable The content should make sense to all personnel. Security managers often create content that is overly technical and difficult for nontechnical personnel to understand.
• Relevant The content should be applicable to the organization and its users. For example, training on the topic of cryptography would be irrelevant to the vast majority of personnel in most organizations. Irrelevant content can cause personnel to disengage from further training.
• Actionable The content should ensure that personnel know what to do (and not to do) in common scenarios.
• Memorable The best content will give personnel opportunities to practice their skills at some of the basic tasks important to information security, including selecting and using passwords, reading and responding to e-mail, and interacting with people inside and outside the organization.
Security Awareness Training Audiences
When planning a security awareness program, security managers need to address the entire worker population and should be familiar with their roles in the organization. Managers are tasked with determining which training materials are relevant and necessary to each group of workers, without overburdening workers with training that is not relevant to their jobs.
Consider, for example, workers in a large retail organization, which fall into five categories:
• Corporate workers All use computers, and most use mobile devices for e-mail and other functions.
• Retail floor managers These people work in retail store locations and use computers daily in their jobs.
• Retail floor cashiers All work in retail store locations and do not use computers, but they do collect payments by cash, check, and credit card.
• Retail floor workers All work in retail store and warehouse locations and do not use computers.
• Third-party personnel Any persons from outside companies that regularly access the organization’s networks, systems, or data should be included in portions of security awareness training that are relevant to their tasks and duties.
The security manager of the retail organization should package security awareness training so that each audience receives relevant training. Corporate workers and retail floor managers should probably receive full-spectrum training because they all use computers. Retail floor managers should also receive the same training delivered to retail floor workers and cashiers, because they also work at retail locations and supervise these personnel. Cashiers need training on fraud techniques (counterfeit currency, currency counting fraud, and matters related to credit card payments such as skimming). Retail floor workers probably need no Internet or computer-related security awareness training but can instead receive training on topics related to physical security and workplace safety.
Technical Workers
Technical workers in an organization, typically IT personnel, should be trained in security techniques that are relevant to their positions. Technical workers are responsible for architecture, system and network design, implementation, and administration. Without security training, these workers’ lapses in judgment may result in significant vulnerabilities that could lead to compromises.
Software Developers
Software developers typically receive little or no education on secure software development in colleges, universities, and tech schools. The art of secure coding is new to many software developers. Security training for software developers helps them to be more aware of common mistakes, including the following:
• Broken access control
• Cryptographic failures
• Vulnerabilities that permit injection attacks
• Insecure design
• Security misconfiguration
• The use of outdated components
• Broken authentication and session management that can lead to attacks on other user sessions
• Cross-site scripting
• Sensitive data exposure
• Insufficient attack protection
• Cross-site request forgery
• Underprotected APIs
This list is adapted from the “Top 10 Web Application Security Risks,” published by the Open Web Application Security Project (OWASP), at https://owasp.org/www-project-top-ten/. This organization is dedicated to helping software developers better understand the techniques needed for secure application development and deployment.
Security training for software developers should also include protection of the software development process itself. Topics in secure software development generally include the following:
• Protection of source code
• Source code reviews
• Care when using open source code
• Testing of source code for vulnerabilities and defects
• Archival of changes to source code
• Protection of systems used to store source code, edit and test source code, build applications, test applications, and deploy applications
Some of these aspects are related to the architecture of development and test environments and may not be needed for all software developers.
Third Parties
Security awareness training needs to be administered to all personnel who have access to an organization’s data through any means. Often this includes personnel who are employees of other organizations, so this means that some of those workers need to participate in the organization’s security awareness training. In larger organizations, the curriculum for third-party personnel may need to be altered somewhat because portions of the security awareness training content may not be applicable to outsiders.
New Hires
New employees, as well as consultants and contractors, should be required to attend security awareness training as soon as possible. There is a risk that new employees could make mistakes early in their employment and prior to their training, as they would not be familiar with all the security practices in the organization. Better organizations link access control with security awareness training: New employees are not given access to systems until after they have successfully completed their security awareness training. This gives new workers added incentive to complete their training quickly, since they want to be able to access corporate applications and get to work.
Annual Training Most security awareness programs include annual refresher training for all workers. Required by some regulations, such training is highly recommended, because it helps workers maintain focus on security and Internet safety and helps them avoid common mistakes. Further, because both protective techniques and attack techniques change quickly, annual refresher training keeps workers abreast of these developments.
Training takes time, and people tend to put it off for as long as possible. This is easy to understand, because training takes time away from other important work tasks. Still, the security manager and the organization must ensure that as many workers as possible complete the training. Workers can be offered incentives to complete their training: for example, all workers who complete their training in the first week can be entered into a random drawing for gift cards or other prizes.
Organizations generally choose one of several options for annual training, including:
• Entire organization The organization will develop messaging to the entire organization and conduct annual training at the same time for all workers. The advantage of this is that all-personnel messaging can be utilized in an all-out blitz to get people thinking about this training. One disadvantage is that all workers will be a little less productive at the same time.
• Hire month anniversary The organization enrolls workers in annual training on the month of their original hire date. For example, if a worker’s first day was March 4, 2017, that worker (and all others hired in March) will complete security awareness training annually in the month of March. The advantage of this is that disruptions (minor as they are) are spread throughout the year. A key disadvantage is that there would probably not be an opportunity for all-personnel messaging for training.
• Department The organization enrolls workers in various departments for their annual security training. The advantage of department-centric rotation is that training content can be tailored to the audience.
Awareness Training Communications
Security awareness training programs often utilize a variety of means for imparting Internet hygiene and safe computing information to its workers. Communication techniques often include the following:
• E-mail Security managers may occasionally send out advisories to affected personnel to inform them of developments, such as a new phishing attack. Occasionally, a senior executive will send a message to all personnel to impress the point of security being every worker’s job and that security is to be taken seriously.
• Internal web site Organizations with internal web sites or web portals may from time to time include information security messages.
• Video monitors, posters, and bulletins Sometimes a security message on monitors, posters, or bulletins on various security topics keeps people thinking about information security. Typical subjects include using good passwords, being careful with e-mail, and social engineering.
• Voicemail Organizations may occasionally send voicemail messages to all personnel or groups of affected personnel to inform them of new developments.
• Security fairs Organizations can set up an annual fair or ongoing technology center where users can get answers or view demonstrations of some of the latest threats and exploits to the company. This assists with developing lines of communications between the security team and the users of the computing systems.
Management of External Services
The structures and business models in many organizations have changed dramatically, leading to an increase in the use of external services, or third-party organizations. Organizations rely on goods and services provided by external third parties, and like other cyber risks, third-party cyber risks must be managed. Third-party risk management (TPRM) activities are used to discover and manage risks associated with these external third parties.
TPRM extends the techniques used to identify and treat risk within the organization to include risks present in other organizations that provide services. TPRM exists because of the complexities associated with identifying risks in third-party organizations and because of risks inherent in doing business with third parties. At the core, TPRM is similar to other risk management, but the difference lies in the solicitation of information to identify risks outside of the organization’s direct control.
Many organizations outsource some of their information processing to third-party organizations, often in the form of cloud-based SaaS and platform as a service (PaaS), for economic reasons: it is less expensive to pay for software in a leasing arrangement as opposed to developing, implementing, and maintaining software internally. TPRM practices have advanced significantly in recent years in response to this wave of outsourcing to cloud-based infrastructure and software services. With so much of corporate IT existing in and being managed by other organizations, TPRM practices have changed so that security and risk managers can continue to identify the risks present in their IT operations, much of which is run by other companies.
Benefits of Outsourcing
Organizations that are considering outsourcing operations to third parties need to weigh the benefits and costs carefully to determine whether the effort to outsource will result in measurable improvement in their processing, service delivery, and/or finances.
Outsourcing can offer an organization many benefits:
• Available skills and experience Organizations that have trouble attracting workers with specialized skills often turn to third parties with highly skilled personnel who can benefit a variety of client organizations.
• Economies of scale Specialized third parties can often achieve better economies of scale through discipline and mature practices than organizations are able to achieve.
• Objectivity Some functions are better provided by outsiders. Personnel within an organization may have trouble being objective about some activities, such as process improvement and requirements definitions; in that case, a third-party may offer better solutions. Also, auditors frequently must be from an outside firm to achieve sufficient objectivity and independence.
• Reduced costs When outsourcing involves third parties with offshore personnel, an organization may be able to lower its operating costs and improve its competitive market position through currency exchange rates and differences in standard pay.
When an organization is making an outsourcing decision, it needs to consider these advantages together with risks, as discussed in the next section.
Risks of Outsourcing
In the 1990s, when many organizations rushed to outsource development and support functions to organizations located in other countries, they did so with unrealistic short-term gains in mind and without adequately considering all the real costs and risks of outsourcing. This is not to say that outsourcing to third parties is bad, but many organizations made outsourcing decisions without fully understanding them.
While outsourcing to third parties can bring many tangible and intangible benefits to an organization, it is not without certain risks and disadvantages. Naturally, when an organization employs third parties to perform some of its functions, it relinquishes some control to those third parties.
The risks of outsourcing to third parties include the following:
• Higher than expected costs Reduced costs were the main driver for offshore outsourcing that began in the 1990s. However, many organizations failed to anticipate the actual operational realities and/or the cost savings. For instance, after U.S.-based organizations outsourced to overseas operations, IT personnel had to make many more expensive trips than expected. Also, changes in international currency exchange rates can transform this year’s bargain into next year’s high cost.
• Theft of intellectual property Outsourcing product manufacturing to certain third-world countries has resulted in systematic theft of intellectual property, made manifest by the presence of nearly identical products. Some countries consider the theft of intellectual property as an entitlement, contrary to the rule of law in other countries.
• Poor quality The work product produced by a third party may be lower than was produced when the function was performed in-house.
• Poor performance The third-party service may not perform as expected. The capacity of networks or IT systems used by third parties may cause processing delays or longer than acceptable response times.
• Loss of control An organization that is accustomed to being in control of its workers may experience a loss of control. Making small adjustments to processes and procedures may be more time-consuming or may increase costs.
• Employee integrity and background It may be decidedly more difficult to determine the integrity of employees in a third-party organization, particularly when the organization is located in another country. Some countries, even where outsourcing is popular, lack nationwide criminal background checks and other means for making a solid determination on an employee’s background and integrity.
• Loss of competitive advantage If the services performed by the third party are not flexible enough to meet the organization’s needs, this can result in the organization losing some of its competitive advantage. For example, suppose an organization outsources its corporate messaging (e-mail and other messaging) to a third-party service provider. Later, the organization wants to enhance its customer communication by integrating its service application with e-mail. The e-mail service provider may be unable or unwilling to provide the necessary integration, which will result in a loss of competitive advantage.
• Loss of tribal knowledge Development and operations of any portion of IT produces tribal knowledge—the knowledge accumulated by the personnel doing the work. While many details of architecture, design, implementation, and operations may be documented in more mature organizations, some portion of the information often goes undocumented, remaining in the memories of the personnel involved. For services that are outsourced, that tribal knowledge is largely absent, as the organization’s personnel are not involved in day-to-day details.
• Errors and omissions The third party may make serious errors or fail to perform essential tasks. For instance, a third party may suffer a data security breach that results in the loss or disclosure of sensitive information. This can be a disastrous event when it occurs within an organization’s four walls, but when it happens to a third party, the organization may find that the lack of control will make it difficult to take the proper steps to contain and remedy the incident. If a third party experiences a security breach or similar incident, it may be putting its interests first and only secondarily watching out for the interests of its customers.
• Vendor failure The failure of a third party to deliver may result in increased costs and delays in service or product delivery.
• Differing mission and goals An organization’s employees are going to be loyal to its mission and objectives. However, employees of a third party may have little or no interest in the hiring organization’s interests; instead, they will be loyal to the third party organization’s values, which may at times be in direct conflict. For example, a third party may place emphasis on maximizing billable hours, while the hiring organization emphasizes efficiency. These two objectives are in conflict with each other.
• Difficult recourse If an organization is dissatisfied with the performance or quality of the third party, contract provisions may not sufficiently facilitate a remedy. If the third-party operation is in a different country, applying remediation in the court system may also be futile.
• Lowered employee morale If an organization chooses to outsource some operations to a third party, employees who remain may be upset because some of their colleagues may have lost their jobs as a result of the outsourcing. Further, remaining employees may believe that their own jobs may soon be outsourced or eliminated. They may also believe that their organization is more interested in saving money than in taking care of its employees. Personnel who have lost their jobs may vent their anger at the organization through a variety of harmful actions that can threaten assets or other workers.
• Audit and compliance An organization that outsources part of its operation that is in scope for applicable laws and regulation may find it more challenging to perform audits and achieve compliance. Audit costs may rise, as auditors need to visit the third parties’ work centers. Requiring the third party to make changes to achieve compliance may be difficult or expensive.
• Applicable laws Laws, regulations, and standards in headquarters and offshore countries may impose requirements on the protection of information that may complicate business operations or enterprise architecture.
• Cross-border data transfer Governments around the world are paying attention to the flow of data, particularly the sensitive data of its citizens. Many countries have passed laws that attempt to exert control over data about their citizens when the data is transferred out of their jurisdiction.
• Time zone differences Communications will suffer when an organization outsources some of its operations to offshore third parties that are several time zones distant. It will be more difficult to schedule telephone conferences when there is very little overlap between workers in each time zone. It will take more time to communicate important issues and to make changes.
• Language and cultural differences When outsourcing crosses language and cultural barriers, it can result in less-than-optimal communication and results. The outsourcing organization will express its needs through its own language and culture, but the third party will hear those needs through its own language and culture. Both sides may be thinking or saying, “They don’t understand what we want” and “We don’t understand what they want.” This can result in unexpected differences in work products produced by the outsourcing firm. Delays in project completion or delivery of goods and services can occur as a result.
Identifying Third Parties
Because the topic of third-party risk is relatively new, many existing organizations are just getting started with TPRM programs in their organizations—however, metaphorically speaking, the third-party “horse” is already “out of the barn.” Many organizations today do not have a firm grasp on the identities of all of the third parties they’ve partnered with. Indeed, stakeholders from across an organization may be aware of a few third parties critical to their particular focus, but often there is a total lack of central organization with regard to third-party management. An early step in an organization’s TPRM may involve conducting an initial inventory of third-party vendors.
There is no single place where information about all third-parties may be found. In part, this is because of the varying nature of third parties and the types of goods or services they provide to the organization. It is suggested, then, that the security manager consult with several stakeholders in the organization to identify subsets of third parties. These stakeholders may include the following:
• Legal One of the most important allies to the security manager, the organization’s legal department negotiates purchase and service contracts with third parties. Thus, legal will have a collection of contracts that can identify third parties. Security managers need to understand, however, that legal does not handle contracts for every third party, because some suppliers and vendors do not use contracts. Many online service providers, for example, use simple “click-through” agreements that do not go through the organization’s legal department.
• Procurement The procurement function is a critical part of an organization’s TPRM program. Larger purchases are frequently negotiated by a procurement function or team. Like the legal team, procurement may have a collection (and perhaps even a list) of third parties it has negotiated business deals with.
• Accounts payable Sometimes the only way to learn about some third parties’ involvement is to find out what third parties are being paid for the products or services they provide. Typically, the accounts payable function will remit funds only to organizations that are registered as vendors in the organization’s financial accounting system.
• Information technology (IT) The IT department may have established data connections to certain third parties; it may have specific firewall rules associated with system access granted to third parties; and it may have logical connections between its internal identity and access management (IAM) system and some third parties. Finally, information systems including firewalls, intrusion detection/prevention systems, web content filters, and CASB systems can provide a wealth of information, particularly about third-party services that are offered free of charge. Free online services are so numerous that many organizations are challenged to identify them until they utilize a CASB system (even then, a few may go unnoticed).
• Facilities The facilities department may be aware of third parties not discovered by other means, because of its function: maintaining and supplying processing center locations and work locations. The facilities department likely has several third-party relationships with organizations that do not access IT systems. This is one reason why facilities should be involved in the initial search.
• Department heads and business unit leaders An organization’s department heads and business unit leaders are certainly going to be aware of key third-party relationships, including key suppliers, service providers, and sources of temporary workers.
• Location-specific leaders The saying goes, “The farther away one is from corporate headquarters, the more that business is conducted by expediency than by policy.” In other words, workers in satellite offices are more apt to conduct business with unique, local-to-them third parties that may not be identified otherwise. Security managers may need to tread lightly here so that their quest for information about third parties does not represent a threat to their ongoing internal business relationships and operations.
When conducting an initial inventory, a security manager will, along the way, discover other sources that can identify third-party relationships. Security managers should realize that an initial effort at identifying third parties will probably not identify every one, but most will be identified. Security personnel should be on the lookout for third-party relationships that have not been identified so that they may be brought into the TPRM program.
When building an initial inventory of third parties, the security manager may opt to use a spreadsheet program to track them, adding columns to identify how each third party was identified and those that list criteria used to classify third parties. However, managing third parties by spreadsheet may quickly become a burdensome task. Several vendors and service providers have created purpose-built applications that can be used to manage third parties, including the following (in alphabetical order):
• Allgress
• CyberGRX
• Diligent (formerly Galvanize)
• KY3P
• Lockpath
• Prevalent
• RSA Archer
• ServiceNow
Cloud Service Providers
Organizations moving to cloud-based environments often assumed that those cloud service providers would take care of many or all information security functions, but often this was not the case. This resulted in innumerable breaches, as each party believed that the other was performing key data protection tasks. Most organizations are unfamiliar with the shared responsibility model that delineates which party is responsible for which operations and security functions. Tables 6-14 and 6-15 depict shared responsibility models in terms of operations and security, respectively.
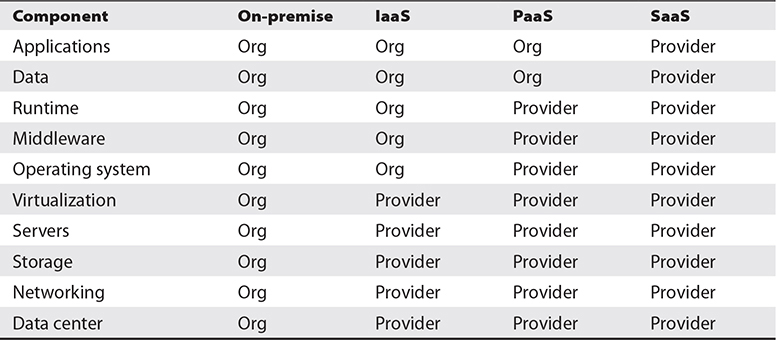
Table 6-14 Cloud Services Operational Shared Responsibility Model
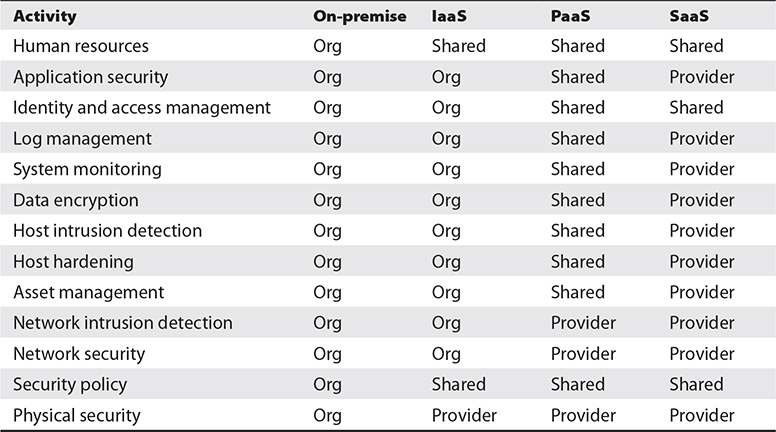
Table 6-15 An Example Cloud Services Security Shared Responsibility Model
Note that the values in Tables 6-14 and 6-15 are not absolutely consistent across different service providers. Instead, these tables serve to illustrate the nature of shared responsibilities between a service organization and its customers. The specific responsibilities for operations and security between an organization and any specific service provider can vary somewhat. It is vital that an organization clearly understand its precise responsibilities for each third-party relationship so that no responsibilities are overlooked or neglected; otherwise, risks may be introduced to the organization’s operations and/or security. The organization is ultimately responsible for ensuring that specific areas are addressed, because if a breach occurs, the organization will be held responsible in the eye of shareholders, board of directors, and customers.
TPRM has been the subject of many standards and regulations that compel organizations to be proactive in discovering risks present in the operations of their critical third-party relationships. Historically, many organizations were not voluntarily assessing their critical third parties. Statistical data about breaches over several years has revealed that more than half of all breaches are caused by inappropriately managed third parties. This statistic illuminates the magnitude of the third-party risk problem and has resulted in the enactment of laws and regulations in many industries that now require organizations to build and operate effective TPRM programs in their organizations. This has also garnered innovation in the form of new tools, platforms, and services that help organizations manage third-party risk more effectively.
TPRM Life Cycle
Managing business relationships with third parties is a life-cycle process that begins when an organization contemplates the use of a third party to augment or support its operations in some way. The life cycle continues during the ongoing relationship with the third party and concludes when the organization no longer requires the third party’s services.
Initial Assessment
Prior to the establishment of a business relationship, an organization will assess and evaluate the third party for suitability. Often this evaluation is competitive, involving two or more third parties vying for the formal relationship. The organization will require that each third party provide information describing its services, generally in a structured manner through a request for information (RFI) or a request for proposal (RFP).
In the RFI and RFP, an organization often includes sections on security and privacy to solicit information about how each third party will protect the organization’s information. This, together with information about the services themselves, pricing, and other information, reveals details that the organization uses to select the third party that will provide services.
Onboarding
Onboarding is the process by which an organization begins a business relationship with a third party. Before utilizing the products or services from a third party, the organization should perform up-front due diligence to understand the level of risk involved in the relationship. Often, an organization will establish a risk level using criteria discussed earlier in this section and will then perform an assessment utilizing questionnaires and other methods according to the scheme shown in Tables 6-17 and 6-18. These activities will uncover issues that may require remediation and/or specific statements in the initial legal agreement between the organization and the third party.
Legal Agreement
Before services can commence, the organization and the third party will negotiate a legal agreement that describes the services provided, service levels, quality, pricing, and other terms. Based on the details discovered in the assessment phase, the organization can develop a section in the legal agreement that addresses security and privacy, which will typically cover these subjects:
• Security and/or privacy program The third party must have a formal security and/or privacy program including but not limited to governance, compliance, policy, risk management, annual risk assessment, internal audit, vulnerability management, incident management, secure development, security awareness training, data protection, and third-party risk.
• Security and/or privacy controls The third party must have a control framework, including linkages to risk management and internal audit.
• Vulnerability management The third party will have policies and procedures for formally identifying and managing vulnerabilities in their systems and processes.
• Vulnerability assessments The third party will undergo penetration tests or vulnerability assessments of its service infrastructure and applications, performed by a competent security professional services firm of the organization’s choosing (or a company that the organization and third party jointly agree upon), with reports made available to the organization upon request.
• External audits and certifications The third party is required to undergo annual SOC 1 and/or SOC 2 Type 2 audits, ISO 27001 certifications, HITRUST certifications, PCI DSS reports on compliance (ROCs), CMMC audits, or other industry-recognized and applicable external audits, with reports made available to the organization upon request.
• Security incident response The third party must have a formal security incident capability that includes testing and training.
• Security incident notification The third party will notify the organization in the event of a suspected and confirmed breach, within a specific time frame, typically 24 hours. The language around “suspected” and “confirmed” needs to be developed carefully so that the third party cannot sidestep this responsibility.
• Right to audit The third party will permit the organization to conduct an audit of the third-party organization without cause. If the third party will not permit this, the organization may insist on the right to audit in the event of a suspected or confirmed breach or other circumstances. Further, the contract should include the right for a competent security professional services firm to perform an audit of the third-party security environment on behalf of the organization (useful for several reasons, including geographic location and that the external audit firm will be more objective). The cost of the audit is usually paid for by the organization, and in some cases the organization will provide credits or compensation for the time incurred by the third party’s team.
• Periodic review The third party will permit an annual onsite review of its operations and security. This can give the organization greater confidence in the third party’s security and operations.
• Annual due diligence The third party will respond to annual questionnaires and evidence requests as part of the organization’s third-party risk program.
• Cyber insurance The third party must carry a cyber-insurance policy with minimum coverage levels and will comply with all requirements in the policy to ensure payout in the event of a security event. A great option is to have the organization be a named beneficiary on the policy, in case a widespread breach results in a large payout to many customers.
• Restrictions on outsourcing Restrict the third party from outsourcing core functions to other organizations.
Organizations with many third parties may consider developing a standard security clause that includes all of these provisions. Then, when a new contract is being considered, the organization’s security team can perform its up-front examination of the third party’s security environment and make adjustments to the security clause as needed.
Organizations will often identify one or more shortcomings in the third party’s security program that it is unwilling or unable to remediate right away. In this case, the organization can compel the third party to enact improvements in a reasonable period of time after the start of the business relationship. For example, suppose a third-party service provider does not have an external audit, such as a SOC 1 or SOC 2 audit, but agrees to undergo such an audit one year in the future. Or perhaps a third-party service provider that has never had external penetration testing performed could be compelled to begin performing penetration testing at regular intervals. Alternatively, the third party could be required to undergo a penetration test and be required to remediate all issues deemed Critical and High before the organization will begin using the third party’s services.
Risk Tiering and Vendor Classification
Most companies have a large number of third-party vendors—so many that they cannot possibly perform all of the due diligence on every vendor. It makes sense, then, to take a risk-based approach to TPRM and apply a level of due diligence to vendors according to the level of risk, by classifying vendors according to risk level and then performing a level of due diligence in proportion to their classification.
To achieve this, an organization needs to establish a few simple criteria, such as the following, by which a vendor can be classified into the appropriate risk level:
• Volume of sensitive customer data The amount of sensitive customer data that the vendor stores on its systems can include contact information, financial information, healthcare information, transaction history, and location. The greater the amount of data or the longer this data resides on a vendor’s information systems, the higher the risk. Generally, organizations use a simple numeric scale to reflect their operations. For example, the criteria might be less than 10,000 records, 10,000 to 1 million records, or greater than 1 million records.
• Volume of sensitive internal data The amount of sensitive internal data that the vendor stores on its systems can include employee information, intellectual property, customer lists, marketing plans, and other data. The greater the amount of data or the longer the vendor stores this data on its information systems, the higher the risk.
• Operational criticality The degree to which the organization depends upon the day-by-day, hour-by-hour, minute-by-minute, or even second-by-second readiness and operation of the vendor on the organization’s product or services output determines its risk factor. For example, a movies-on-demand service may store its content and serve movies to customers via a third-party IaaS vendor. The service depends upon the IaaS vendor for continuous availability; even a few seconds of downtime would interrupt the movie streaming to all of its customers. Incidentally, in this example, the IaaS vendor would be rated as high risk because of the movie’s content stored in its systems.
• Physical access The degree to which a vendor has physical access to the organization’s information processing centers or work centers can be rated together or separately. For instance, technical support vendors may have physical access to information systems in a data center, or service vendors may have physical access to work centers, such as freight delivery, janitorial, plant care, office supplies replenishment, or IT service vendors who maintain copiers, scanners, and other office equipment.
• Access to systems Whether the vendor has the ability to access information systems accessed by the organization should be considered. For example, tech support organizations may have occasional or 24/7 access to specific information systems so that they can perform routine maintenance or help troubleshoot problems. Further, risk ratings may vary depending on the type of systems accessed by third parties (those with large amounts of critical or sensitive data, or systems that are operationally critical, as described in prior criteria).
• Contractual obligations Whether the vendor is required to establish and maintain a security program, security controls, vulnerability management, incident response, or other activities should be considered. Third parties may be rated a higher risk if few or no security requirements are imposed upon them in a contract. While effective third-party risk management seeks to add appropriate security clauses to contracts, security managers may occasionally encounter contracts with third parties where no clauses were included.
No matter what criteria are used in contracting with third-party vendors, organizations typically use criteria to identify the most critical vendors and other third parties. Generally, organizations will classify third parties into three levels of criticality. Table 6-16 depicts a typical third-party risk classification scheme. Based on levels of importance, each organization will construct a unique risk tiering scheme.

Table 6-16 Third-Party Risk Tiering Example
Organizations can use a system similar to Table 6-16 in a number of ways. First, each third party can be scored based on how many of the low, medium, or high categories are met. Or each third party can be assigned a risk level if any single criterion is met at that level. Organizations are cautioned to refrain from overcomplicating tiering or scoring criteria: the objective is to arrive at no more than three, or perhaps four, tier classifications for each vendor. The reason for this is related to third-party assessments, discussed in the next section.
In most organizations, a minority of third parties, perhaps 0.5 to 2 percent, will be assigned to the top risk level. A few more will be assigned to the second risk level—perhaps another 5 to 10 percent. The remainder will be assigned to the third risk level.
From time to time, some third parties will need to be reclassified from one risk level to another. For example, suppose a third-party service provider is hired to perform low-risk services, and its initial risk classification is low. However, that third party might earn more business that represents high risk; unless some triggering mechanism (such as the negotiation of an additional legal contract) is in place, the organization would need to analyze the relationship with each of its third parties annually (or more often) to confirm their risk ratings. Similarly, if a third party is originally classified as high risk but later discontinues performing high-risk services, the third party should be reclassified at a lower risk tier; otherwise, the organization is spending too much effort assessing the third party.
Assessing Third Parties
To discover risks to the business, organizations need to assess their third-party service providers, not only at the onset of the business relationship (prior to the legal agreement being signed, as explained earlier) but periodically thereafter, to identify specific risks represented by those vendors. This assessment process should be considered a part of the internal risk assessment process, though the personnel contacted are not internal personnel, but employees of other companies, with a variable degree of cooperation and willingness to respond. As opposed to performing risk assessments of internal processes and systems, the security manager’s view of information provided by third-party processes and systems may be obscured. Additional focus and effort are required to learn enough about the practices in a third-party organization to draw conclusions about risk.
Organizations assessing third parties often recognize that IT and security controls are not the only forms of risk that require examination. As a result, organizations generally seek other forms of information about critical third parties, including the following:
• Financial risk, including currency exchange risk
• Geopolitical risk
• Inherent risk
• Recent security breaches
• Lawsuits
• Operational effectiveness/capabilities
These and other factors can influence the overall risk to the organization, which can manifest in various ways, including degradations in overall security, failures to meet production or quality targets, and even business failure.
Once an organization has established its third-party risk classification and has begun to identify its third parties and their respective risk tiering, third parties can be assessed. Before assessments can be performed, however, the organization needs to develop a scheme by which assessments take place. In the preceding section, third parties are classified into three or four risk levels. The manner in which assessments are performed depends upon which risk level any particular third party is assigned. Several techniques can be used to assess third parties, including the following:
• Questionnaires Organizations can develop questionnaires to be sent to third parties that include questions about the third party’s IT controls and other business activities to assess how effectively its information is being protected.
• Questionnaire confirmation After completed questionnaires are received from third parties, organizations can take steps to confirm or validate the answers provided. For example, the organization can request evidence in the form of process documents or samples of business records. This can improve (or reduce) confidence in the vendor’s answers and provide a more accurate depiction of control risk.
• Site visit If an organization is not satisfied with the use of questionnaires and confirmation, the organization can send security personnel (or, ironically, outsource this activity to a third party) to conduct a site visit of the third party’s work locations and information processing centers. Although this is the costliest confirmation method, organizations may improve their confidence in the third party by conducting their own onsite assessment.
• External attestations Organizations can compel third parties to undergo external audits or attestations. Established standards such as SOC 1, SOC 2, SSAE 18, ISAE 3402, HITRUST, PCI DSS, CMMC, and ISO/IEC 27001 are examples of control and audit standards that can be used to understand the effectiveness of a third party’s IT controls.
• External business intelligence Organizations often turn to external business intelligence services such as Dunn & Bradstreet or Lexis Nexus. Such services collect information on the financial health of companies, which can help organizations better understand risk factors related to the health and ongoing viability of its third parties. For example, if an organization learns that a particular vendor is under financial stress (perhaps because of problems with its products or services adversely affecting sales), this will raise concern that a partnership could result in degradations in product or service quality, as well as degradations in information protection efforts and effectiveness.
• External cyber intelligence Organizations are beginning to utilize the services of a growing number of companies that gather intelligence on third-party service providers, which sell this information on a subscription basis. These services perform a variety of functions, including security scans and scans of the dark web for signs of an unreported breach. These cyber-intelligence services often perform these services at costs lower than those incurred by organizations that conduct these activities with their own security staff.
• Security scans and penetration tests Organizations can perform security scans or penetration tests on the infrastructure and/or applications of its third parties. Alternatively, organizations can require the third parties to commission these activities from qualified security consulting firms and make the results available to organizations. These activities serve to bolster (or erode) confidence in a third party’s ability to manage its infrastructure and applications, including running an effective vulnerability management program.
• Intrusive monitoring Organizations can sometimes compel a third party to permit the organization to view or receive internal controls data in real time. For instance, an organization could provide a security system to the third party to be installed in its network; the system would provide some form of real-time security intelligence to the organization to give it confidence that the third party’s environment is free of active threats. Or a third party could make certain internal information available to the organization from its own internal security systems. The types of information that can be made available include security and event log data from operating systems, firewalls, intrusion detection/prevention systems, internal vulnerability scan data, network packet header capture, or network full packet capture. These activities, called intrusive monitoring, represent an intrusion of the organization’s visibility into the third party’s environment.
As stated earlier, not all third parties are assessed in the same way. Instead, organizations can establish schemes for assessing vendors according to their risk levels. Table 6-17 depicts such a scheme.
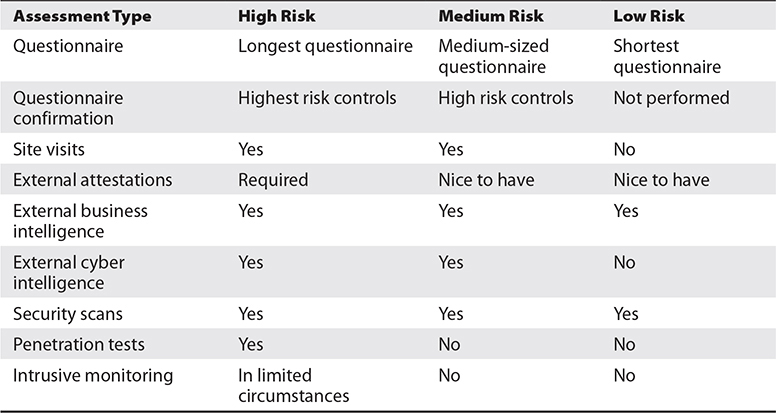
Table 6-17 Assessment Activities at Different Risk Levels
Organizations also need to determine how frequently to perform their assessments of third parties. Table 6-18 shows a sample scheme of assessment frequency.
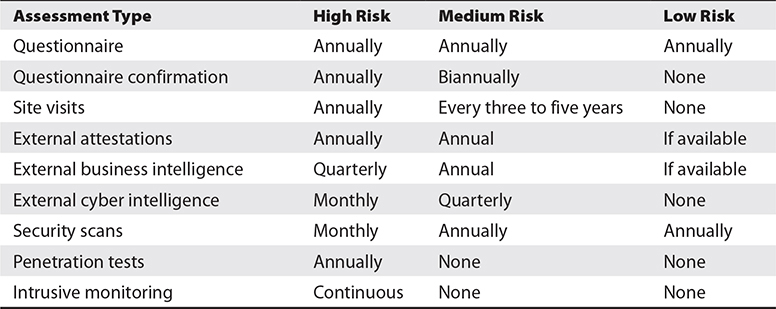
Table 6-18 Assessment Frequency
Some organizations have hundreds to thousands of third-party service providers that require assessments, with the largest organizations having tens of thousands of third parties. Risk tiering is performed precisely because organizations work with so many third parties, and the various types of assessments are time-consuming and expensive to perform. This is why the most thorough assessments are performed only on those that represent the highest risk.
Questionnaires and Evidence
Periodically, a security and/or privacy questionnaire is sent to third-party service providers with a request to answer the questions and return it to the organization in a reasonable amount of time. Often, however, an organization may choose not to rely on the questionnaire answers alone in determining risk. The organization can also request that the third party furnish specific artifacts, such as the following, that serve as evidence to support the responses in the questionnaire:
• Security policy
• Security controls
• Security awareness training records
• New-hire checklists
• Details on employee background checks (not necessarily actual records but a description of the checks performed)
• Nondisclosure and other agreements required to be signed by employees (not necessarily signed copies but blank copies)
• Vulnerability management process
• Secure development process
• Copy of general insurance and cyber-insurance policies
• Incident response plan and evidence of testing
Because a large organization’s third-party providers access, store, and process data in a variety of different ways, the organization may choose to send out different versions of questionnaires appropriate to one or more categories of risk or business operation, to ensure that the majority of questions asked are relevant. Otherwise, large portions of a questionnaire may be irrelevant, which could be frustrating to third parties, which would rightfully complain of wasted time and effort.
Organizations often send different questionnaires according to the third party’s risk level. For example, third parties deemed to be of the highest risk would be sent extensive questionnaires that include requests for many pieces of evidence, medium-risk third parties would be sent less lengthy questionnaires, and low-risk third parties would be sent short questionnaires. Although this practice avoids overburdening low-risk third parties with extensive questionnaires, it also reduces the burden on the organization, because someone has to review the questionnaires and attached evidence. An organization with hundreds of low-risk third-party contracts should avoid being overburdened with analyzing hundreds of questionnaires, each with hundreds of questions, if possible.
Risk Treatment
Organizations that carefully examine the information provided from the third parties may discover some unacceptable practices or situations. In these cases, the organization can analyze the matter and decide on a course of action. For instance, suppose a highly critical third party indicates that it does not perform annual security awareness training for its employees, and the organization finds this unacceptable. To remedy this, the organization analyzes the risk (in a manner not unlike any risk found internally) and decides on a course of action: it contacts the third party in an attempt to compel them to institute annual training.
Sometimes, a deficiency in a third party is not so easily resolved. For example, suppose a third party that has been providing services for many years indicates in its annual questionnaire that it does not use encryption on the most sensitive data it stores. At the onset of the business relationship, this was not a common practice, but it has since become a common practice in the organization’s industry. The service provider, when confronted with this, explains that it is not operationally feasible to implement encryption of stored data in a manner acceptable to the organization, mainly for financial reasons, and because of the significant cost impact on its operations, the third party would have to increase its prices. In this example, the organization and the third party would need to discover the best course of action to ensure that the organization can determine an acceptable level of risk and associated cost.
Proactive Issue Remediation
The only means of exchange between a customer organization and a third party are money, products or services, and reputation. In other words, the only leverage that an organization has against a third party is the withholding of payment and communicating the quality (or lack therein) of the third party to other organizations. This is especially true if the outsourcing crosses national boundaries. Therefore, an organization that is considering outsourcing must carefully consider how it will enforce contract terms so that it receives the quantity and quality goods and services that it is expecting.
Many of the risks of outsourcing to third parties can be remedied through contract provisions such as the following:
• Service level agreement The SLA should provide details on every avenue of work performance and communication, including escalations and problem management.
• Quality Depending upon the product or service, this may translate into an error or defect rate, a customer satisfaction rate, or system performance.
• Security policy and controls Whether the outsourcing firm is safeguarding the organization’s intellectual property, keeping business secrets, or protecting information about its employees or customers, the contract should spell out the details of the security controls that it expects the outsourcing firm to perform. The organization should also require periodic third-party audits and the results of those audits. The contract should contain a “right to audit” clause that allows the outsourcing organization to examine the work premises, records, and work papers on demand.
• Business continuity The contract should require the outsourcing firm to have reasonable measures and safeguards in place to ensure resilience of operations and the ability to continue operations with minimum disruption in the event of a disaster.
• Employee integrity The contract should define how the outsourcing firm will vet its employees’ backgrounds so that it is not inadvertently hiring individuals with a criminal history and so employees’ claimed education and work experience are genuine.
• Ownership of intellectual property If the outsourcing firm is producing software or other designs, the contract must define ownership of those work products and whether the outsourcing firm may reuse any of those work products for other engagements.
• Roles and responsibilities The contract should specify in detail the roles and responsibilities of each party so that each will know what is expected of them.
• Schedule The contract must specify when and how many items of work products should be produced.
• Regulation The contract should require both parties to conform to all applicable laws and regulations, including but not limited to intellectual property, data protection, and workplace safety.
• Warranty The contract should specify terms of warranty for the workmanship and quality of all work products so that there can be no ambiguity regarding the quality of goods or services performed.
• Dispute and resolution The contract should contain provisions that define the process for handling and resolving disputes.
• Payment The contract should specify how and when the outsourcing provider will be paid. Compensation should be tied not only to the quantity but also to the quality of work performed. The contract should include incentive provisions for additional payment when specific schedule, quantity, or quality targets are exceeded. The contract should also contain financial penalties that are enacted when SLA, quality, security, audit, or schedule targets are missed.
The terms of an outsourcing contract should adequately reward the outsourcing firm for a job well done, which should include the prospect of earning additional contracts as well as referrals that will help it to earn outsourcing contracts from other customers.
Responsive Issue Remediation
Rarely do organizations see perfect answers in returned questionnaires. Often, undesirable situations are identified in questionnaires or during questionnaire confirmation. For example, a third party may specify in a questionnaire that it requires its personnel to change their passwords once per year. But suppose the organization would prefer the third party personnel change their passwords more frequently? What if a third party specifies that it never requires its personnel to change their passwords? This is something that an organization would probably find unacceptable. So the organization initiates a discussion with the third party to discover why its personnel are never required to change their passwords, with the hopes that either the organization will find the third party’s explanation acceptable (perhaps they use compensating controls such as an effective MFA system) or the parties will agree that the third party will change its systems to require its personnel to update their passwords with some frequency, perhaps quarterly. Such remediation can be costly and time-consuming, so organizations need to be careful about how often and in which situations it will undergo the process.
Security Incidents
If a security incident occurs in a third-party organization, responding to the incident is more complex, mainly because two or more organizations and their respective security teams are involved. A security incident at a third-party organization is also an incident in its customers’ organizations, and each needs to respond to it. If a third-party organization’s systems are breached, the third-party must respond and perform all of the steps of incident response, such as notifying affecting parties, including its customers.
Customers of third-parties have their own incident response to perform. However, customers are usually not permitted to access detailed event logs or perform forensic analysis on the third-party provider. Often, customers have to wait until the third party’s investigation has concluded. Because this can be frustrating to its customers, third parties can keep their customers informed periodically until the event is closed.
This topic is explored in detail in Chapter 8.
Information Security Program Communications and Reporting
Communications are the lifeblood of an effective information security program. Lacking effective communications, the security program will have difficulty interacting with executive management for the exchange of objectives, risk information, and metrics. Ineffective communications will hamper virtually all other security-related activities and processes. This section explores the various internal and external parties with whom security managers communicate and collaborate.
Security Operations
Security operations are associated with much of the action-oriented activities in an information security program, through its monitoring and response processes. Communications and reporting from security operations may include the following:
• Vulnerability management Operations and trends in vulnerability management, including the discovery of new assets, and the time required to correct vulnerabilities
• Events and incidents Security- and privacy-related events and incidents, including the time required to detect and response to events, types of events, impact of events, any effort or cost of recovery, affected data and systems, and external notifications
• External threat intelligence External information, including noteworthy events, intrusions, defensive techniques, new cybercriminal organizations, and trends
• Use case development Improvements in monitoring, including the ability to detect new types of incidents
• Orchestration and automation Improvements and incidents in SOAR capabilities to help improve efficiency and rapid response to events
• Other operational activities Other routine operations that are a part of a security operations center
The highly technical nature of security operations necessitates reporting in layers, with each layer written with the audience in mind. For instance, an internal operational report may contain considerable amounts of technical jargon and statistics, whereas reporting to senior executives would contain the same information, but simplified and in business terms.
Risk Management
Risk management, the risk analysis and risk treatment function that deals with emerging risk, should periodically produce management reports so that executive leaders can stay informed on many aspects of cyber risk in the organization. Risk management reporting consists of a periodic snapshot of the risk register, including changes in overall security posture, new risks, changes in existing risks, and those risks that have been treated. Reporting would also include tracking of risk remediation and whether it is being performed on schedule and within budget.
Trends in risk management reporting could include risk treatment decisions by risk magnitude, indicating whether an organization’s risk appetite is increasing, decreasing, or staying the same, and the time taken to complete remediation. Reporting may be misleading if it includes only the numbers of items in the risk register and the number of items being selected for risk treatment.
Internal Partnerships
No security manager can hope to accomplish much if they work alone. Effective information security and information risk is a team sport, and each player on the team can help the security manager in different ways. Further, communication with other corporate departments and business units helps to keep the security manager informed on matters of importance.
An effective way to build those partnerships while increasing the effectiveness of the program is to “deputize” team members from other groups. For example, the security manager can partner with administrative assistants, who will lead the data retention program in their respective departments. Or the security manager may designate a person in another business unit (BU) to serve as the information security liaison to share guidance with the BU and report possible risks or issues that impact information security in the organization. None of this is possible unless proper training is provided to the other team members, and time must be allocated for them to fulfil those added duties.
Legal
In most organizations, the legal department functions as the organization’s de facto business risk office, through the negotiation of contract terms with service providers, customers, and other parties. Legal generally always attempts to tip risk in favor of the organization.
Legal and information security can collaborate on the security clauses in almost any contract with customers, suppliers, service providers, and other parties. When other parties send contracts that contain security clauses, the security manager should examine those clauses to ensure that the organization is able to meet all requirements. Similarly, when the organization is considering doing business with another party, the security manager can work with the legal department to make sure that the organization is adequately protected by requiring the other party to take certain steps to protect the organization’s information.
Sometimes an organization will enter into a business relationship without informing or consulting with the security manager, who often would want to perform a risk assessment to identify any important risks that should be known. The best arrangement is for legal to inform the security manager of every new contract it receives so that the security manager can attempt to identify risks at this late stage.
Human Resources
As the steward for information and many activities regarding employees and other workers, human resources (HR) is another important ally of information security. HR can bolster the organization’s security in many ways, including the following:
• Recruiting As HR recruits new employees, it ensures that potential personnel have the appropriate qualifications and that they are inclined to conform to security policy and other policy. In the candidate screening process, HR will perform background checks to confirm the applicant’s education, prior employment, and professional certifications, and to determine criminal history.
• Onboarding HR will ensure that all new employees sign important documents, including nondisclosure agreements, and that they receive their initial training, including security awareness training. In onboarding, new employees will also formally acknowledge receipt of, and pledge conformance to, security policy and other policies. HR will provision human resource information systems (HRISs), which in many organizations are integrated into their identity and access management systems. HR ensures that new employees are assigned to the correct job title and responsibilities, as in some cases this automatically results in new employees receiving “birthright” access to specific information systems and applications.
• Internal transfers HR is responsible for coordinating internal transfers, as employees change from one position or department to another. Internal transfers are somewhat different from promotions; in an internal transfer, an employee may be moving to an entirely different department, where they will need to have access to completely different information systems and applications. Notifying security and IT personnel of internal transfers is important so that employees’ former roles in information systems and applications can be discontinued at the appropriate time, avoiding the phenomena known as accumulation of privileges, where employees with long tenure accumulate access rights to a growing number of roles in information systems and applications, thereby increasing various risks.
• Offboarding HR is responsible for processing the termination, or offboarding, of employees who are leaving the organization for any reason. HR is responsible for ensuring that security, IT, and other departments are notified of the termination so that all access rights can be terminated at the appropriate time. (This is especially important in a dismissal situation, where the organization must “surgically remove” access at precisely the right moment to avoid the risk of the terminated employee, in the heat of the moment, from exacting revenge on the organization through sabotage and other acts.) HR is also responsible for collecting assets issued to a departing employee such as laptop or tablet computers, mobile devices, and related peripherals. HR may also require departing employees to sign nondisclosure and/or noncompete agreements.
• Training In many organizations, HR is the focal point for most or all training for employees and for keeping records of training. Security awareness training, which may be administered by HR, is vital. HR in many organizations is also the focal point for coordinating various communications to employees on topics including training and security reminders.
• Investigations HR conducts investigations into matters such as employee misconduct. Where such misconduct involves any improper use of information systems or computers, HR will partner with information security, which may conduct a forensic investigation to establish a reliable history of events and establish a chain of custody should the matter develop into legal proceedings such as a lawsuit.
• Discipline HR is the focal point for formal disciplinary actions against employees. From an information security perspective, this includes matters of violations of security policy and other policies. Generally, the security manager will present facts and, if requested, an opinion about such matters, but HR is ultimately responsible for selecting the manner and degree of disciplinary action, whether that includes verbal and written warnings, demotion, time off without pay, reduction in compensation, forfeiture of a bonus, removal of privileges, or dismissal.
Facilities
The facilities function provides stewardship of the workplace to ensure that there is adequate space and support for workers in all office locations. The communication between facilities and information security includes the following subject matter:
• Workplace access control Facilities typically manages workplace access control systems such as badge readers and door lock actuators that control which personnel are permitted to access work centers and zones within them. A well-known principle in information security states that adversaries who obtain physical access to computing assets are able to take them over; this reiterates the need for effective access control that prevents unauthorized personnel from accessing those assets.
• Workplace surveillance Video surveillance is the companion detective control that works with preventive controls such as key card systems. Video cameras at building entrances can help corroborate the identity of personnel who enter and leave. Visible surveillance monitors can add a deterrent aspect to surveillance.
• Equipment check-in/check-out Data centers and other locations with valuable assets can implement equipment check-in and check-out functions, whereby personnel are required to record assets coming and going in a log that resembles a visitor log.
• Guest processing Facilities often assists with the identification and processing of guests and other visitors. Security guards, receptionists, or other personnel can check visitors’ government IDs, issue visitor badges, contact the employees being visited, and assist in other ways.
• Security guards Guards represent the human element that provides or supplements access controls and video surveillance. Guards can also assist with equipment check-in/check-out and visitor processing.
• Asset security Through video surveillance, access control, and other means, facilities ensures the protection of assets including data center information-processing systems and office assets, including printers and copiers.
• Personnel safety While not directly in the crosshairs of information security, many security managers are involved in personnel safety, because is closely related to asset security and many of the same protective controls are used.
Information Technology
Information technology and information security represents perhaps the most strategic partnership that the security manager will establish and develop. Many key functions are performed by IT that have security ramifications, requiring effective collaboration and communication between these two teams. These functions include the following:
• Access control IT typically manages day-to-day access control, including issuing credentials to new employees, removing credentials from terminated employees, processing access requests, and resetting credentials. In some organizations, IT may also perform access reviews and recertifications.
• Architecture IT is responsible for the overall architecture of information systems used in the organization. This includes data architecture, network architecture, and systems architecture. In many organizations, the practice of security architecture affects all other aspects of architecture. Open Security Architecture (www.opensecurityarchitecture.org/) defines IT security architecture as “the design artifacts that describe how the security controls (security countermeasures) are positioned, and how they relate to the overall information technology architecture. These controls serve the purpose to maintain the system’s quality attributes: confidentiality, integrity, availability, accountability and assurance services.” In other words, security architecture is the big-picture mission of understanding the interplay between all the security controls and configurations that work together to protect information systems and information assets.
• Configuration and Hardening IT owns the configuration of all operating systems for servers and end-user computing; this includes the development and implementation of hardening standards, which are typically developed by IT in accordance to policy and principles developed by information security.
• Scanning and patching Under the guidance of the security manager, IT often operates vulnerability scanning tools and patch management platforms to ensure that IT assets are free of exploitable vulnerabilities. This has proven to be one of the most critical activities to prevent break-ins by external adversaries.
• Security tools In most organizations, IT operates the organization’s firewalls, intrusion detection/prevention systems, spam filtering, web filtering, and other security tools. Generally, the security manager establishes policies and principles by which these tools are used, and IT implements, maintains, and operates them according to those policies and principles.
• System monitoring IT typically performs monitoring of its assets to ensure that all are operating normally and to manage alarms that indicate the presence of various operational issues.
• Security monitoring In some organizations, IT performs security monitoring of IT assets to be alerted when security issues occur.
• Third-party connections IT may be involved in the setup of data connections to third-party service providers. As part of an organization’s third-party risk program, the security manager needs to be aware of all third-party business relationships as early in the cycle as possible; however, because some vendor relationships escape the scrutiny of security managers early in the process, being informed of new third-party connections may sometimes be the only way a security manager will be aware of new relationships.
Systems Development
Systems development includes software development, systems development, integration, and other activities concerned with the development or acquisition of information systems for use internally or by customers or partners.
Under guidance from the security manager, systems development will manage the entire product development life cycle, with security as an integral part at each stage in the process. Communications and collaboration between systems development and information security include the following topics:
• Security and privacy by design Several activities ensure that all new offerings, components, features, and improvements incorporate security and privacy as part of the design process. This can help the organization avoid issues later in the development process that may be more costly to remediate.
• Secure development Secure coding ensures that all new and changed software is free of exploitable defects that could result in security incidents.
• Security testing Several activities fall under the security testing function, including code-scanning tools used by each developer’s integrated development environment (IDE), unit and system testing to confirm the correct implementation of all security requirements, static application security testing (SAST) scanning tools that are run as part of a nightly build process, and dynamic application security testing (DAST) scanning tools that identify security defects in running applications.
• Code reviews Peer reviews of security-related changes to software source code include security-sensitive functions such as authentication, session management, data validation, and data segregation in multitenant environments. Some organizations incorporate code reviews for changes to all software modules.
• Security review of open source software Some organizations perform reviews of various kinds of some or all open source modules to ensure they are not introducing unwanted security defects into the software application.
• Developer training Periodic training for developers includes techniques on secure development, which helps developers avoid common mistakes that result in security defects that must be fixed later.
• Protection of the development process This includes controls to ensure that only authorized developers may access source code (and this may include restrictions on the quantity of source code that a developer can check out at any given time), security scans of source code upon check-in, and protection of all source code.
Procurement
Larger organizations have procurement or purchasing departments that negotiate prices and business terms for new purchases of hardware, software, and services, as well as renewals for subscriptions and services. The security manager should consider a business relationship with procurement departments. The procurement manager can be sure to notify the security manager whenever any new purchase of hardware and software products or related services is being considered. This enables the security manager to begin any needed due diligence related to the product or service being considered and can weigh in with messaging concerning risks and any needed controls or compensating controls to keep risk within accepted tolerances.
Internal Audit
Virtually all U.S. public companies, and many private companies, have an internal audit (IA) function whose main mission is assurance through independent audits of policies and controls. Although IA departments cannot stipulate how controls, policies, and processes should be designed and operated, IA can still be a collaborative partner on controls, policies, and processes by telling IT, information security, and others whether those controls, policies, and processes can be audited as designed.
Business Unit Managers
It has been said that a security manager can protect the organization only to the extent that he understands how it works. Naturally this necessitates that the security manager communicate and develop relationships with business unit and department managers and leaders throughout the organization. These partnerships help the security manager understand how each business unit and department functions, and it helps identify critical personnel, processes, systems, and outside partners. The main purpose of these partnerships is not for the security manager to inform business unit managers and leaders how security works, but rather to help the security manager negotiate the best and most transparent ways to respond to management as security matters occur within the organization. As these strategic relationships develop, business unit managers and leaders will begin to trust, share information with, and include the security manager in key conversations and processes. Trust leads to conversations on sensitive security topics, resulting in minor and sometimes significant improvements to the business and its security.
Affiliates and Key Business Partners
As the security manager develops strategic relationships throughout the organization, she should set her sights on affiliates, business partners, and other external entities that are deeply involved in the organization’s development and delivery of goods and services. With the extensive information systems integrations that are established between organizations, the security of an organization is dependent upon the security of the organization’s information systems ecosystem—the interconnection of information systems, networks, and business processes. Because many security breaches are connected to third parties, the development of strategic relationships is essential.
External Partnerships
Successful information security is possible only when the security manager communicates and has established relationships with key external organizations. Those key organizations can be identified according to the organization’s industry sector, relevant regulations, information systems in use, geographic locations, and similar considerations.
Law Enforcement
A roof is best repaired on a sunny day. Similarly, security managers should communicate and cultivate relationships with key law enforcement agencies and relevant personnel in those agencies before there is an urgent matter at hand. Organizations and law enforcement can develop a relationship in which trusted information sharing can take place; then, when an emergency such as a security breach occurs, law enforcement will be familiar with the organization and its key personnel and will be able to respond appropriately.
Organizations may benefit by developing relationships with the following agencies:
• United States The Federal Bureau of Investigation (FBI), Secret Service (for organizations dealing in large volumes of credit card transactions), Cybersecurity and Infrastructure Security Agency (CISA), and city and state police cybercrime units, plus InfraGard (www.infragard.org/), a public–private partnership between the FBI and private organizations
• Canada The Royal Canadian Mounted Police (RCMP) and city and provincial cybercrime units
• United Kingdom Security Service (aka MI5, Military Intelligence, Section 5) and city and county cybercrime units
• Globally International Criminal Police Organization (Interpol)
Regulators and Auditors
To the greatest extent possible, regulators and auditors should be viewed as partners and not adversaries. Communicating and developing relationships with regulators and auditors can help the organization improve their business relationship and the tone of interactions. Security managers should also understand regulators’ ethical boundaries. (In some situations, you cannot so much as buy a regulator a cup of coffee to lighten the mood and talk about work or non-work-related matters.)
Standards Organizations
Numerous standards organizations exist in the information security industry, and a multitude of others exist in all other industry sectors. In the information security industry itself, being involved in standards organizations avails the security manager of “insider” information such as “sneak previews” of emerging and updated standards, as well as learning opportunities and even conferences and conventions. These organizations include the following:
• PCI Security Standards Council Involved with protection of credit card data for banks, issuers, processors, and merchants; well-known for PCI DSS and other standards (www.pcisecuritystandards.org)
• Cloud Security Alliance Creates security standards frameworks for cloud-based service providers (https://cloudsecurityalliance.org/)
• Information Security Forum (ISF) Publishes “Standard of Good Practice for Information Security” (www.securityforum.org)
• International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) Development of international standards on numerous topics including security management and IT service management (www.iso.organdwww.iec.ch)
• National Institute for Standards and Technology (NIST) Offers a vast library of special publications on cybersecurity (https://csrc.nist.gov/publications/sp)
Professional Organizations
The information security profession is challenging, not only because of the consequences of ineffective security programs but also because of the high rate of innovation that takes place. Professional organizations such as the following help to fill the need for valuable information through training, professional certifications, local chapter organizations, and conferences:
• ISACA The developer of the Certified Information Security Manager (CISM, the topic of this book), Certified Information Systems Auditor (CISA), Certified in Risk and Information Systems Control (CRISC), and other certifications, with conferences and training events worldwide and numerous chapters around the world. (www.isaca/org)
• Information Systems Security Association (ISSA) Offers conferences and supports numerous local chapters worldwide (www.issa.org)
• International Information Systems Security Certification Consortium (ISC)² Developer of the Certified Information Systems Security Professional (CISSP) and other certifications, conducts extensive training and an annual conference (www.isc2.org)
• Cloud Security Alliance (CSA) Developer of the Cloud Controls Matrix (CCM), the CSA Star program, and the Certified in Cloud Security Knowledge (CCSK) certification, conducts conferences worldwide (https://cloudsecurityalliance.org/)
• International Council of Electronic Commerce Consultants (EC-Council) Developer of the well-known Certified Ethical Hacker (CEH) and Certified Chief Information Security Officer (CCISO) certifications, offers worldwide conferences (www.eccouncil.org)
• SANS Developer of the GIAC family of certifications and conducts numerous training events and conferences globally (www.sans.org)
Security Professional Services Vendors
Security managers need to communicate and develop trusted relationships with one or more security professional services vendors. Because there is so much to know in the information security profession and because threats, practices, and frameworks change so often, having one or more trusted advisors can help a security manager to be continually aware of these developments.
Better security professional services vendors have senior advisors on their staff who are available for brief consultations from time to time. Although these advisors may have sales responsibilities, a skilled security manager can seek their expertise now and then to confirm ideas, plans, and strategies.
Some security professional services vendors have virtual CISOs or CISO advisors on their staff (often former CISOs), who help clients develop long-term security strategies. Often these advisors are billable resources who assist their client organizations in understanding their risks and help develop risk-based security strategies that will make the best use of scarce resources to reduce risk. These types of services are especially useful for smaller organizations that are unable to attract and hire full-time security managers of this caliber.
Security professional services vendors can also assist with a strategy for the acquisition, implementation, and operation of security tools. Trusted advisors who are familiar with security tools can often help a security manager identify the better tools that are more likely to work in their environments.
Security Product Vendors
Security managers need to communicate and establish good business relationships with each of the vendors whose security products and services are in use. Through these relationships, security managers will be better informed in a variety of ways, including product or service updates, workshops and seminars, training, and support. Things do not always go smoothly between product vendors and their customers. Establishing strategic relationships will result in faster and more productive interaction and resolution when problems are encountered.
Trusted advisors can help the security manager identify additional vendors for the purpose of relationship building. A new vendor may offer a product that is a competitor of a product already used in the security manager’s organization, or the vendor may offer a product or service that the organization does not currently use. These relationships help the security manager understand the capabilities that she could utilize in the future.
Compliance Management
Compliance is the state of conformance to applicable policies, standards, regulations, and other requirements. It is the process by which the security manager determines whether the organization’s information systems, processes, and personnel conform to those things. When a security manager develops or adopts a control framework and identifies applicable regulations and legal requirements, he then sees to it that controls and other measures are implemented. Then, as part of the risk management life cycle, he examines those controls, processes, and systems to determine whether they are in compliance with internal and external requirements. As discussed throughout this book, these activities include external audits, internal audits, reviews, and control self-assessments.
As they do with other life cycle processes, security managers need to report on the organization’s compliance with policies, standards, regulations, and other cybersecurity related legal obligations. Only then can management understand the organization’s compliance posture and be aware of any compliance issues that warrant attention.
Applicability
Security managers often find that compliance is complicated by multiple, overlapping standards, regulations, and other legal requirements, each of which may be applicable to various portions of the organization. To understand the coverage of these requirements, the security manager can develop a compliance matrix such as the one shown in Table 6-19.
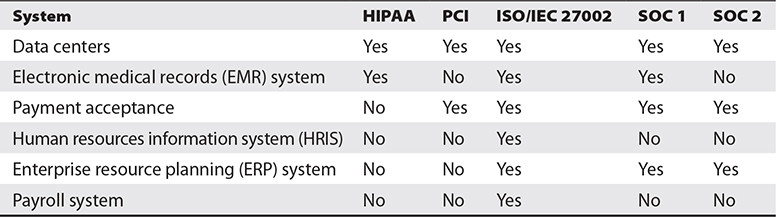
Table 6-19 Example Compliance Matrix Depicting Applicability of Regulations and Standards on Systems
Properly determining applicability helps the security manager better understand what is required of individual information systems and the processes they support. Any organization would be overspending without necessarily reducing risk if it simply applied the requirements from all regulations and other legal obligations to all of its information systems. The result may be a more consistent application of controls but certainly a more expensive application as well. For most organizations, the resources required to develop the means of compliance to applicable regulations is less than the resources required to apply all required controls by all regulations to all systems.
Compliance Risk
As the security manager performs risk assessments and populates the risk register with risk matters requiring discussion and treatment, the security manager should not overlook compliance risk. Compliance risk is associated with any general or specific consequences of the failure to be compliant with an applicable law or other legal obligation.
Suppose, for example, that during a risk assessment, a security manager observes that the organization stores credit card information in plaintext spreadsheets on internal file servers. The security manager can identify at least two risks in this situation:
• Sensitive data exposure The risk register indicates that such sensitive data could be misused by internal personnel, and it may be discovered by a malicious outsider. The costs associated with a forensic investigation, along with potential mitigation costs such as payment for credit monitoring for victims, would be included in the total cost incurred by the organization should this information be compromised.
• Fines and sanctions The risk register notes that the organization could face fines and other sanctions should the organization’s PCI regulators (namely, banks and payment processors) learn of this. The fines and other sanctions are the potential unplanned costs that the organization may incur upon regulators’ discovery of this.
Compliance Enforcement
As the security manager reviews the results of internal and external audits, control self-assessments, and other examinations of systems and processes, she will need to weigh not only the direct risks associated with any negative findings but also the compliance risk. The security manager can apply both of these considerations in any discussions and proceedings during which others in the organizations are contemplating their response to these compliance items.
As a part of a metrics program, the security manager will report on the state of compliance to senior management. Matters of compliance will be reflected in metrics as areas of higher risk, whether these are risks of breach and/or risks of compliance to external regulations with potentially public consequences.
Compliance Monitoring
Rules, regulations, and standards are ever-changing. Information security organizations must find a way to stay current with regard to these changes, so that the organization can proactively plan and anticipate changes that must be made to maintain an acceptable compliance posture. Information security departments often collaborate with corporate legal departments that consume subscription services that inform the organization of changes in laws and regulations. Otherwise, organizations would need to spend considerable time researching applicable laws to be aware of important changes.
Security Awareness Training
Covered earlier in this chapter, security awareness training ensures that an organization’s workers are aware of security and related policies, as well as expectations of behavior and judgment. Reporting for security awareness training may include
• Training sessions conducted
• Employees trained
• Phishing testing results
• Other social engineering testing results
• Trends in worker-related security incidents
Security managers need to understand that an increase in the number of worker-reported security incidents may not be a sign of an increase in the number of incidents, but may instead indicate improved worker awareness on the nature of security incidents and the need to report them.
Technical Architecture
Monitoring and reporting on technical architecture can help the organization understand the progress being made on the theme of security by design. However, security managers reporting on trends in technical architecture need to understand that some types of measurements may be misunderstood. For instance, one could expect that the number of incidents related to the technical environment should decrease as more of the environment is aligned with better architecture models such as zero trust. However, at the same time, event detection capabilities could also improve, yielding an increase in the number of events. This could be interpreted as the new architecture being more vulnerable, but it could also be an indication of improvements in event visibility, meaning that a greater number of undetected events were occurring in older environments.
Personnel Management
In all but the smallest organizations where the security manager acts alone, personnel management is an important aspect of information security management. In many organizations, information security is staffed with a team ranging from two to dozens of people. The security manager is responsible for all aspects of the security team, starting with identifying and hiring candidates, assigning and supervising work, developing new skills, and developing the security team’s “culture within a culture.” All of this requires intentional communication and monitoring.
Finding and Retaining Talent
Security personnel are in high demand, and, consequently, those in the profession command good salaries. However, it can be difficult for organizations to find qualified security professionals, because most organizations have trouble finding skilled, qualified persons that can be attracted away from their current employment. Compensation is creeping upward faster than inflation, and as a result, some organizations cannot afford the talent they need. Because security professionals know they are in high demand, they can choose the types of companies they want to work for, and they can live almost anywhere they want. Today, security professionals who want to be remote workers can do so with comparative ease.
Retaining talent is also a challenge in many organizations. Good technologists seem to become bored with routine and repetition, so keeping them engaged with new challenges can itself be a challenge. Security managers need to find the right balance between their security staff wanting to do “cool, new things” and aligning those desires with actual business needs.
Security managers who are looking to grow their security team or fill open positions often need look no further than their own organization: one or more people in the IT department may aspire to join the security team. Many—if not most—IT security professionals “crossed over” from corporate IT to information security, and this is still a common source for new recruits. People transferring over from IT are already familiar with the business and with IT’s operations and practices. If they are looking to grow into a security career, they’re probably going to be willing to work pretty hard to succeed.
Roles and Responsibilities
As the security manager develops and begins to execute a long-term security strategy, she will identify all the ongoing and occasional tasks that need to be performed by members of the team. Prior to the beginning of this planning, the security manager must understand the difference between roles and responsibilities. A role is a designation that denotes an associated set of responsibilities, knowledge, skills, and attitudes. Example roles include security manager, security engineer, and security analyst. A responsibility is a stated expectation of activities and performance. Example responsibilities include running weekly security scans, performing vendor risk assessments, and approving access requests.
As a security manager analyzes all the required activities in a security team, she may take the approach of listing all the activities, along with estimates of the number of hours per week or hours per month required to perform them. Next, she will group these activities according to subject matter, skill levels, and other considerations. As the associated workloads are tallied, the number of people required will become evident. Then, these groups of responsibilities can be given roles, followed by job titles.
Most security managers, however, do not have an opportunity to build and staff a program from scratch; instead, they are inheriting an existing program from a previous manager. Still, these activities can serve to delineate all required activities, calculate or observe levels of effort, and confirm that roles and responsibilities are assigned to the right personnel who have the required skills and experience to carry them out properly.
Job Descriptions
A job description is a formal description of a position in an organization and usually contains a job title, work experience requirements, knowledge requirements, and responsibilities. Job descriptions are used when an organization is seeking to fill a new or vacant position. The job description will be included in online advertisements to attract potential candidates. In most organizations, HR is the steward of job descriptions. However, when positions become vacant or new positions are opened, HR often will consult with the hiring manager to ensure that the contents of a job description are still accurate and up-to-date.
Job descriptions are also a tool used in professional development. Managers and leadership can develop career paths that represent a person’s professional growth through a progression of promotions or transfers into other positions. Job descriptions are a primary means for a worker to understand what another position is like; interviewing people who are already in a desired position is another means for gaining insight into a position that someone aspires to. A small but effective way to drive a culture of security is to add in specific language regarding the responsibilities that each role plays in protecting the organization’s data and systems used in storing, processing, and transmitting that data.
Culture
As discussed in Chapter 1, culture is the collective set of attitudes, practices, communication, communication styles, ethics, and other behavior in an organization. Culture can be thought of as the collective consciousness of the workers in an organization. It’s hard to describe an organization’s culture because it has to be experienced to be understood.
Security managers seek to understand an organization’s culture so that they may be better and more effective change agents. In organizations that do not regard information security as an important activity, security managers must work to understand the culture and make subtle changes to improve awareness of information security in a form that most workers can understand. Security awareness training, with its attendant messaging from executives, is often regarded as a catalyst for making those subtle changes to the culture.
Security managers and their teams occasionally find they need to develop a “culture within a culture.” The rest of an organization with a laissez-faire attitude toward security may have some catching up to do, but the security team already “gets it”—the ever-conscious awareness of day-to-day activities and whether they are handling and protecting data and systems properly.
Professional Development
Dedicated and committed technologists have a built-in thirst for knowledge and for expanding their boundaries. Information security professionals should have this thirst “on steroids,” because the velocity of change is higher than that in other aspects of information technology. Cyber-criminal organizations are innovating their malware and other attack techniques, manifested through breaches using increasingly novel methods; security tools vendors are innovating their detective and protective wares; security organizations are continually improving many aspects of security management, including control frameworks, auditing techniques, and security awareness messaging. It’s been said that information security professionals must spend four hours each week reading up on these and other new developments just to keep from falling behind. Security managers need to be aware of the present knowledge and skills that each security team member possesses today, what skills are needed in the team in the future, and the professional growth aspirations that drive each team member. Several avenues for professional development are discussed here.
Career Paths A career path is the progression of job responsibilities and job titles that a worker will attain over time. Generally, a worker who is aware of a potential career path within their organization is more likely to remain in the organization. Workers who feel trapped and unable to advance are more likely to consider a position in another organization. With the security employment market as tight as it is, any organization that neglects the topics of professional development and career paths runs the risk of losing good people. Security managers should be aware of any career paths that have been published by their organizations; however, since many organizations don’t develop formal career paths, security managers will want to work one-on-one with each security staff member to determine what their individual career paths will look like.
There are many fields of specialty in information security, including the following:
• Risk management
• Risk analysis
• Information systems auditing
• Penetration testing
• Red / blue / purple team
• Malware analysis
• Security engineering
• Security architecture
• Secure development
• Mobile device security
• Telecommunications and network security
• Social engineering
• Security awareness training
• Forensics
• Cryptography
• Business continuity planning and disaster recovery planning
• Identity and access management
• Identity and access governance
• Data governance and classification
• Threat intelligence
• Third-party risk
• Privacy
Certifications Professional certifications represent skills, knowledge, and experience among security professionals. Certifications are a badge of honor, representing thousands of hours of professional experience as well as the drive to improve oneself. To the extent that team members value the worth of certifications, security managers should encourage their team members to earn additional certifications. Better organizations would not hesitate to reimburse employees’ expenses to earn and maintain their certifications, although, practically speaking, there may be reasonable limits on annual spending in this regard. Security managers should invest time in each of their security staff members to understand their career paths and the certifications they may want to earn along the way.
The most popular non-vendor-related security and privacy certifications are, in rough order of increasing seniority, as follows:
• Entry-Level Cybersecurity Certification This relatively new offering by (ISC)² is in its pilot phase as of the writing of this book. Visit www.isc2.org.
• Security+ Offered by CompTIA, this is considered a popular entry-level security certification. Visit www.comptia.org.
• Systems Security Certified Practitioner (SSCP) Offered by (ISC)², many believe that SSCP is a “junior CISSP,” but this is not the case. SSCP is more technical than the CISSP and is ideal for hands-on security professionals.
• Global Information Assurance Certification (GIAC) Offered by SANS, this family of certifications covers several different topics. Visit www.giac.org.
• Certified Ethical Hacker (CEH) Offered by EC-Council, this certification is ideal for penetration testers and others who want to learn more about the world of vulnerabilities and exploits. Visitwww.eccouncil.org.
• Certified Cloud Security Professional (CCSP) Jointly offered by (ISC)² and the Cloud Security Alliance (CSA), this relatively new certification is sure to become popular. Visit www.isc2.org.
• Certified Information Systems Security Professional (CISSP) Perhaps the most well-known and respected information security certification is popular among strong, established security professionals. It is important for career growth as many organizations require this specific certification for security positions. Visit www.isc2.org.
• Certified Secure Software Lifecycle Professional (CSSLP) Offered by (ISC)², this certification focuses on secure software development. Visit www.isc2.org.
• Certified Data Privacy Solutions Engineer (CDPSE) Offered by ISACA, this is one of ISACA’s newest certifications, focusing on data privacy and leaning into the technical side of the profession.
• Certified Information Security Manager (CISM) Offered by ISACA, this certification is the topic of this book. Visit www.isaca.org.
• Certified Information Systems Auditor (CISA) Also offered by ISACA, this is considered the gold-standard certification for IT auditors. Visit www.isaca.org.
• Certified in Risk and Information Systems Control (CRISC) Offered by ISACA, this is an essential certification for security professionals who work in risk assessment, risk management, and the development of controls and control frameworks. Visit www.isaca.org.
Many IT equipment vendors and IT security tools vendors offer security certifications that represent expertise in various categories of information security. Nearly every major security tools manufacturer has one or more certifications that can be earned. Here is a small sampling:
• Check Point Certified Security Administrator (CCSA)
• Certified Forensic Security Responder (CFSR) from Guidance Software
• Radware Certified Security Specialist (RCSS)
• Metasploit Pro Certified Specialist from Rapid7
• WhiteHat Certified Secure Developer (WCSD)
Training Another important way to retain talent is to provide training for security staff. Again, because security professionals can be afflicted with boredom, they are happiest when they are learning new things. Security managers may fear that if they provide too much training, personnel might leave for greener pastures—but what may happen if they don’t provide enough training? Their personnel would almost certainly feel trapped and be compelled to leave with even more fervor.
Typical organizations provide one week of security training for security professionals. Ideally this means that a security professional is able to attend a one-week conference of her choice. Other companies will pay for web-based training or a number of one-day training courses. One week of training is considered the minimum required for security professionals to stay current in their chosen field. Additional training will be required for security professionals who want to move into a specialty area. Many employers reimburse college and university tuition, often with a yearly cap. This can provide a means for security personnel who want to pursue an undergraduate or graduate degree in information security and related fields.
Personnel-Related Reporting
Reporting that is related to personnel management and development may include the following:
• Performance management As a part of a larger organization’s performance management process, security managers can report on staff member and team attendance, engagement, and performance.
• Staff development Security managers can report on staff development by reporting on training, certifications earned, and mentoring sessions.
• Turnover With security professionals in high demand, security managers should keep an eye on staff turnover and take time to understand why any staff members have left the organizations for greener pastures elsewhere.
• Compensation High demand for security professionals worldwide has resulted in wages and other compensation rising higher than inflation in many cases. An organization’s HR department may not be fully attuned to this matter, making it necessary for the security manager to monitor and report on this.
Project and Program Management
The information security field is undergoing constant change. Organizations with mature risk management programs are discovering new actionable risks, attack techniques used by cybercriminals are undergoing constant innovation, security vendors make frequent improvements in their tools, and the practices of managing security are evolving. IT is also undergoing considerable changes, and organizations are reinventing themselves through process development and changes in the organization chart. Mergers and acquisitions in many industries inflict many broad changes in affected organizations.
The result of this phenomenon of continuous change is the fact that most organizations undertake several information security projects each year. In many organizations, information security personnel are spending more time in projects than they are in routine daily operations. For many security managers, continuous change is the only constant.
In addition to having a deep understanding of IT, risk management, and most or all of the disciplines within security management, a security manager must also be skilled at both project management and program management—the management of several concurrent projects—to orchestrate the parade of changes being undertaken to keep the organization out of trouble. Nevertheless, security managers need to keep their eye on the big picture: the strategy and objectives for the security program and alignment with the business. Every program and project in information security should align with these.
Budget
Budgeting is an essential part of long-term planning for information security and arguably a more difficult undertaking than it is for many other departments. Although the development of an information security strategy (in terms of the capabilities needed) is somewhat more straightforward, obtaining management support for the funding required to realize the strategy can be quite difficult. When executive management does not understand the strategic value of information security, the prospect of funding activities that result in existing business capabilities or capacity seems far different from funding information security, which results in no changes in business capabilities or capacity.
The activities that the security manager needs to include in budgets include the following:
• Staff salaries and benefits
• Temporary staff for special projects and initiatives
• Training and tuition reimbursement
• Equipment
• Software tools
• Support for equipment and software
• Space required in data centers
• Travel
• Maintenance of documents and records
• Team building and recognition
• Contingencies
Often, security managers undertake a detailed analysis on the work required for each function in information security. For instance, a security manager may track time spent on routine processes as well as anticipated but unplanned activities such as incident response and investigations.
IT Service Management
IT service management (ITSM) is the set of activities that occur to ensure that the delivery of IT services is efficient and effective, through active management and the continuous improvement of processes. ITSM consists of several distinct activities:
• Service desk
• Incident management
• Problem management
• Change management
• Configuration management
• Release management
• Service-level management
• Financial management
• Capacity management
• Service continuity management
• Availability management
Each of these activities is described in detail in this section.
ITSM is defined in the IT Infrastructure Library (ITIL) process framework, a well-recognized standard. The content of ITIL is managed by AXELOS. ITSM processes can be audited and registered to the international ISO/IEC 20000:2011 standard.
Service Desk
Often known as the help desk, the IT service desk handles incidents and service requests on behalf of customers by acting as a single point of contact. The service desk performs end-to-end management of incidents and service requests (at least from the perspective of the customer) and is also responsible for communicating status reports to the customer.
The service desk can also serve as a collection point for other ITSM processes, such as change management, configuration management, service-level management, availability management, and other ITSM functions. A typical service desk function consists of frontline analysts who take calls from users. These analysts perform basic triage and are often trained to perform routine tasks such as password resets, troubleshoot hardware and software issues, and assist users with questions and problems with software programs. When analysts are unable to assist a user, the matter is typically escalated to a subject-matter expert who can provide assistance.
Incident Management
ITIL defines an incident as “an unplanned interruption to an IT Service or reduction in the quality of an IT service. Failure of a configuration item that has not yet affected service is also an incident—for example, failure of one disk from a mirror set.” ISO/IEC 20000-1:2011 defines an incident as an “unplanned interruption to a service, a reduction in the quality of a service or an event that has not yet impacted the service to the customer.” Thus, an incident may be any of the following:
• Service outage
• Service slowdown
• Software bug
Regardless of the cause, incidents are a result of failures or errors in any component or layer in IT infrastructure. In ITIL terminology, if the incident has been experienced and its root cause is known, it is considered a known error. If the service desk is able to access the catalog of known errors, this may result in more rapid resolution of incidents, resulting in less downtime and inconvenience. The change management and configuration management processes are used to make modifications to the system to fix the problem temporarily or permanently. If the root cause of the incident is not known, the incident may be escalated to a problem, which is discussed in the next section.
Problem Management
When several incidents have occurred that appear to have the same or a similar root cause, a problem is occurring. ITIL defines a problem as “a cause of one or more incidents.” ISO/IEC 20000-1:2011 defines a problem as the “root cause of one or more incidents” and continues by stating, “The root cause is not usually known at the time a problem record is created and the problem management process is responsible for further investigation.”
The overall objective of problem management is a reduction in the number and severity of such incidents. Problem management can also include some proactive measures, including system monitoring to measure system health and capacity management, which will help management forestall capacity-related incidents.
Examples of problems include the following:
• A server has exhausted available resources, resulting in similar, multiple errors (known as “incidents” by ITSM).
• A software bug in a service is noticed by and affects many users.
• A chronically congested network causes the communications between many IT components to fail.
Similar to incidents, when the root cause of a problem has been identified, the change management and configuration management processes will be enacted to make temporary and permanent fixes.
Change Management
Change management involves using a set of processes to ensure that all changes performed in an IT environment are controlled and performed consistently. ITIL defines change management as follows: “The goal of the change management process is to ensure that standardized methods and procedures are used for efficient and prompt handling of all changes, in order to minimize the impact of change-related incidents upon service quality, and consequently improve the day-to-day operations of the organization.”
The main purpose of change management is to ensure that all proposed changes to an IT environment are vetted for suitability and risk and to ensure that changes will not interfere with one another or with other planned or unplanned activities. To be effective, each stakeholder should review all changes so that every perspective of each change is properly reviewed.
A typical change management process is a formal “waterfall” process that includes the following steps:
1. Proposal or request The person or group performing the change issues a change proposal, which contains a description of the change, the change procedure, the IT components that are expected to be affected by the change, a verification procedure to ensure that the change was applied properly, a back-out procedure in the event the change cannot be applied (or failed verification), and the results of tests that were performed in a test environment. The proposal should be distributed to all stakeholders several days prior to its review.
2. Review Typically in a meeting or discussion about the proposed change, the personnel who will be performing the change discuss the change and answer any of the stakeholders’ questions. Because the change proposal was distributed earlier, each stakeholder should have had an opportunity to read about the proposed change in advance of the review. Stakeholders can discuss any aspect of the change during the review. They may agree to approve the change, or they may request that it be deferred or that some aspect of the proposed change be altered.
3. Approval When a change has been formally approved in the review step, the person or group responsible for change management recordkeeping will record the approval, including the names of the individuals who consented to the change. If, however, a change has been deferred or denied, the person or group that proposed the change will need to make alterations to the proposed change so that it will be acceptable, or they can withdraw the change altogether.
4. Implementation The actual change is implemented per the procedure described in the change proposal. Then the personnel identified as the change implementers perform the actual change to the IT systems identified in the approved change procedure.
5. Verification After the implementers have completed the change, they will perform the verification procedure to make sure that the change was implemented correctly and that it produces the desired result. Generally, this will involve one or more steps, including the gathering of evidence (and directions for confirming correct versus incorrect change) that shows the change was performed correctly. This evidence will be filed with other records related to the change and may be useful in the future, especially if the change is suspected to be the root cause of any problems encountered in the system where this change is made.
6. Post-change review Some or all changes in an IT organization will be reviewed after the change is implemented. The personnel who made the change discuss it with other stakeholders to learn more about the change and whether any updates to future changes may be needed.
These activities should be part of a change control board (CCB) or change advisory board (CAB), a group of stakeholders from IT and every group that is affected by changes in IT applications and supporting infrastructure.
Change Management Records
Most or all of the activities related to a change should include updates to business records so that all of the facts related to each change are captured for future reference. In even the smallest IT organization, there are too many changes taking place over time to expect that anyone will be able to recall facts about each change later. Records that are related to each change serve as a permanent record.
Emergency Changes
Although most changes can be planned in advance using the change management process described here, there are times when IT systems need to be changed right away. Most change management processes include a process for emergency changes that details most of the steps in the nonemergency change management process, but they are performed in a different order. The steps for emergency changes are as follows:
1. Emergency approval When an emergency situation arises, the staff members attending to the emergency should seek management approval for the proposed change via phone, in person, or in writing (typically, e-mail). If the approval was granted by phone or in person, e-mail or other follow-up is usually performed. Who can approve these emergency changes should be designated in advance.
2. Implementation The staff members perform the change.
3. Verification Staff members verify that the change produced the expected result. This may involve other staff members from other departments or end users.
4. Review The emergency change is formally reviewed, which may be performed alongside nonemergency changes with the change control board, the same group of individuals who discuss nonemergency changes.
As with nonemergency changes, emergency changes should be recorded and available for future reference.
Linkage to Problem and Incident Management
Often, changes are made as a result of an incident or problem. Emergency and nonemergency changes should reference specific incidents or problems so that those incidents and problems may be properly closed once verification of their resolution has been completed.
Configuration Management
Configuration management (CM) is the process of recording and maintaining the configuration of IT systems. Each configuration setting is known in ITSM parlance as a configuration item (CI). CIs usually include the following:
• Hardware complement This includes the hardware specifications of each system (such as CPU speed, amount of memory, firmware version, adapters, and peripherals).
• Hardware configuration Settings at the hardware level may include boot settings, adapter configuration, and firmware settings.
• Operating system version and configuration This includes versions, patches, and many operating system configuration items that have an impact on system performance and functionality.
• Software versions and configuration Software components such as database management systems, application servers, and integration interfaces often have many configuration settings of their own.
Organizations with many IT systems may automate the CM function with tools that are used to record and change configuration settings automatically. These tools help to streamline IT operations and make it easier for IT systems to be more consistent with one another. The database of system configurations is called a configuration management database (CMDB).
Linkage to Problem and Incident Management
An intelligent problem and incident management system is able to access the CMDB to help IT personnel determine whether incidents and problems are related to specific configurations. This can be an invaluable aid to those who are seeking to determine a problem’s root cause.
Linkage to Change Management
Many configuration management tools are able to automatically detect configuration changes that are made to a system, including configuration drift, or unintended configuration changes. With some change and configuration management systems, it is possible to correlate changes detected by a configuration management system with changes approved in the change management process. Further, many changes that are approved by the change management process can be performed by configuration management tools, which can be used to push changes out to managed systems.
Release Management
Release management is the ITIL term used to describe the portion of the SDLC where changes in applications are placed into production service. Release management is used to control the changes that are made to software programs, applications, and environments.
The release process is used for several types of changes to a system, including the following:
• Incidents and problem resolution Casually known as bug fixes, these types of changes occur in response to an incident or problem, where it has been determined that a change to application software is the appropriate remedy.
• Enhancements New functions in an application are created and implemented. These enhancements may have been requested by customers, or they may be a part of the long-range vision on the part of the designers of the software program.
• Subsystem patches and changes Changes in lower layers in an application environment may require a level of testing that is similar to what is used when changes are made to the application itself. Examples of changes are patches, service packs, and version upgrades to operating systems, database management systems, application servers, and middleware.
The release process is a sequential process—that is, each change that is proposed to a software program will be taken through each step in the release management process. In many applications, changes are usually assembled into a “package” for process efficiency purposes: it is more effective to discuss and manage groups of changes than it would be to manage individual changes.
The steps in a typical release process are preceded by a typical SDLC process:
1. Feasibility study Activities that seek to determine the expected benefits of a program, project, or change to a system.
2. Requirements definition Each software change is described in terms of a feature description and requirements. The feature description is a high-level explanation of a change to software that may be described using business terms. Requirements are the detailed statements that describe a change in enough detail for a developer to make changes and additions to application code that will provide the desired functionality. Often, end users will be involved in the development of requirements so that they may verify that the proposed software change is really what they desire.
3. Design After requirements have been developed, a programmer/analyst or application designer will create a formal design. For an existing software application, this will usually involve changes to existing design documents and diagrams, but for new applications, the design will need to be created from scratch or copied from similar designs and modified. Regardless, the design will have a sufficient level of detail to permit a programmer or software engineer to complete development without having to discern the meaning of requirements or design.
4. Development When requirements and design have been completed, reviewed, and approved, programmers or software engineers begin development. This involves actual coding in the chosen computer language with approved development tools, as well as the creation or update to ancillary components, such as a database design or application programming interface (API). Developers will often perform their own unit testing, where they test individual modules and sections of the application code to make sure that it works properly.
5. Testing When the developers have finished coding and unit testing, a more formal and comprehensive test phase is performed. Here, analysts, dedicated software testers, and perhaps end users will test all of the new and changed functionality to confirm that it is performing according to requirements. Depending on the nature of the changes, some amount of regression testing is also performed, where functions that were confirmed to be working properly in prior releases are tested again to make sure that they continue to work as expected. Testing is performed according to formal, written test plans that are designed to confirm that every requirement is fulfilled. Formal test scripts are used, and the results of all tests should be recorded and archived. The testing that users perform is usually called user acceptance testing (UAT). Often, automated test tools are used, which can make testing more accurate and efficient. After testing is completed, a formal review and approval are required before the process is allowed to continue.
6. Implementation Next, the software is implemented on production systems. Developers hand off the completed software to operations personnel, who install it according to instructions created by developers. This could also involve the use of tools to make changes to data and database design to accommodate changes in the software. When changes are completed and tested, the release itself is prepared and deployed.
a. Release preparation When UAT and regression testing have been completed, reviewed, and approved, a release management team will begin to prepare the new or changed software for release. Depending upon the complexity of the application and of the change itself, release preparation may involve not only software installation but also the installation or change to database design, and perhaps even changes to customer data. Hence, the software release may involve the development and testing of data conversion tools and other programs that are required so that the new or changed software will operate properly. As with testing and other phases, full records of testing and implementation of release preparation details need to be captured and archived.
b. Release deployment When release preparation is completed (and perhaps reviewed and approved), the release is installed on the target systems. Personnel deploying the release will follow the release procedure, which may involve the use of tools that will make changes to the target system at the operating system, database, or other level; any required manipulation or migration of data; and the installation of the actual software. The release procedure will also include verification steps that will be used to confirm the correct installation of all components.
7. Post-implementation A post-implementation review examines matters of system adequacy, security, return on investment (ROI), and any issues encountered during implementation.
Utilizing a Gate Process
Many organizations utilize a “gate process” approach in their release management process, in which each step of the process undergoes formal review and approval before the next step is allowed to begin. For example, suppose a formal design review will be performed and attended by end users, personnel who created requirements and feature description documents, developers, and management. If the design is approved, development may begin. But if questions or concerns are raised in the design review, the design may need to be modified and reviewed again before development is allowed to begin.
Agile processes utilize gates as well, although the flow of Agile processes is often parallel rather than sequential. The concept of formal reviews is the same, regardless of the SDLC process in use.
Service-Level Management
Service-level management is composed of the set of activities that confirms whether the IT department is providing adequate service to customers. This is achieved through continuous monitoring and periodic review of IT service delivery.
An IT department often plays two different roles in service-level management: As a provider of service to its own customers, the department will measure and manage the services that it provides directly. Also, many IT departments directly or indirectly manage services that are provided by external service providers. Thus, many IT departments are both service provider and customer, and often the two are interrelated, as depicted in Figure 6-15.
Figure 6-15 The different perspectives of the delivery of IT services
Financial Management
Financial management for IT services consists of several activities, including the following:
• Budgeting
• Capital investment
• Expense management
• Project accounting and project ROI
IT financial management is the portion of IT management that takes into account the financial value of IT services that support organizational objectives.
Capacity Management
Capacity management is a set of activities that confirms there is sufficient capacity in IT systems and IT processes to meet service needs. Primarily, an IT system or process has sufficient capacity if its performance falls within an acceptable range, as specified in SLAs. Capacity management is not just a concern for current needs; it must also be concerned about meeting future needs. This is attained through several activities, including the following:
• Periodic measurements Systems and processes need to be regularly measured so that trends in usage can be evaluated to predict future capacity needs.
• Considering planned changes Planned changes to processes and IT systems may impact predicted workload.
• Understanding long-term strategies Changes in the organization, including IT systems, business processes, and organizational objectives, may impact workloads, requiring more (or less) capacity than would be extrapolated through simpler trend analysis.
• Changes in technology Several factors may influence capacity plans, including the expectation that computing and network technologies will deliver better performance in the future and that trends in the usage of technology may influence how end users use technology.
Linkage to Financial Management
One of the work products of capacity management is a projection for the acquisition of additional computer or network hardware to meet future capacity needs. This information needs to be made part of budgeting and spending management processes.
Linkage to Service-Level Management
If there are insufficient resources to handle workloads, capacity issues may result in violations to SLAs. Systems and processes that are overburdened will take longer to respond. In some cases, systems may stop responding altogether.
Linkage to Incident and Problem Management
Systems with severe capacity issues may take excessive time to respond to user requests. In some cases, systems may malfunction or users may give up. Often, users will call the service desk, resulting in the logging of incidents and problems.
Service Continuity Management
Service continuity management is the set of activities that is concerned with the ability of the organization to continue providing services, primarily in the event that a natural or manmade disaster has occurred. Service continuity management is ITIL parlance for the more common terms business continuity planning and disaster recovery planning.
Business continuity is discussed in Chapter 7.
Availability Management
The goal of availability management is the sustainment of IT service availability in support of organizational objectives and processes. The availability of IT systems is governed by the following:
• Effective change management When changes to systems and infrastructure are properly vetted through a change management process, they are less likely to result in unanticipated downtime.
• Effective application testing When changes to applications are made according to a set of formal requirements, review, and testing, the application is less likely to fail and become unavailable.
• Resilient architecture When the overall architecture of an application environment is designed from the beginning to be highly reliable, it will be more resilient and more tolerant of individual faults and component failures.
• Serviceable components When the individual components of an application environment can be effectively serviced by third-party service organizations, those components will be less likely to fail unexpectedly.
Asset Management
Asset management is the collection of activities used to manage the inventory, classification, use, and disposal of assets. It is a foundational activity, without which several other activities could not be effectively managed, including vulnerability management, device hardening, incident management, data security, and some aspects of financial management. Asset management is discussed fully in Chapter 5.
Continuous Improvement
Continuous improvement represents the desire to increase the efficiency and effectiveness of processes and controls over time. It could be said that continuous improvement is a characteristic of an organization’s culture. The pursuit of continuous improvement is a roundabout way of pursuing quality.
A requirement in ISO/IEC 27001 certification requires that management promote continual improvement and that security policy include a commitment to the continual improvement of the information security management system (ISMS). ISO/IEC 27001 also requires that management review the ISMS to identify opportunities for continual improvement. The standard also explicitly requires organizations to “continually improve the suitability, adequacy, and effectiveness of its information security management system.”
NIST SP 800-53 Rev 5, “Security and Privacy Controls for Federal Information Systems and Organizations,” similarly requires that an organization’s risk management program incorporate a feedback loop for continuous improvement. Control SA-15 (6) states that the organization must “require the developer of the system, system component, or system service to implement an explicit process to continuously improve the development process.”
The NIST Cyber Security Framework cites the requirement for continuous improvement throughout the standard. For instance, in the seven steps for creating an information security program, NIST CSF asserts in section 3.2 that “these steps should be repeated as necessary to continuously improve cybersecurity.”
Chapter Review
Controls are the procedures, mechanisms, systems, and other measures designed to reduce risk through compliance to policies. An organization develops controls to ensure that its business objectives will be met, risks will be reduced, and errors will be prevented or corrected.
Controls and control frameworks are used to enforce desired outcomes. Controls need to be carefully considered, as each consumes resources. Security managers need to understand the various types of controls (such as preventive, detective, deterrent, manual, automatic, and so on) so that the correct types of controls can be implemented.
Controls are classified in multiple dimensions so that security professionals can better understand and work with them. Control type descriptors include physical, technical, administrative, preventive, detective, manual, automatic, compensating, and recovery.
An organization’s general computing controls (GCCs) are general in nature and often implemented in different ways on different information systems, based upon their individual capabilities and limitations, as well as applicability.
A control framework is a collection of controls that is organized into logical categories. Well-known control frameworks such as ISO/IEC 27002, NIST SP 800-53, and CIS CSC are intended to address a broad set of information risks common to most organizations. A crosswalk maps two or more control frameworks together.
Before a control can be designed, the security manager needs to have some idea of the nature of risks that a control is intended to address. In a running risk management program, a new risk may have been identified during a risk assessment that led to the creation of an additional control.
After a control has been designed, it should be put into service and then managed throughout its life. Depending upon the nature of the control, this could involve operational impact in the form of changes to business processes and/or information systems. Changes with greater impact will require greater care so that business processes are not adversely affected.
Controls should include metadata that describes the purpose, applicability, scope, classification, measurements, testing procedures, cross references, and more.
The implementation of a new control should be guided by formal processes, not unlike that of systems development: a new control should have a control objective, a design that is reviewed by stakeholders, a test plan that is carried out with results reviewed, a formal authorization to implement the control, and IT and business change management processes to plan its implementation.
Controls that have been placed into service will transition into routine operations. Control owners will operate their controls and try to be aware of any problems, especially early on. Whether controls are automatic or manual, preventive or corrective, their owners are responsible for ensuring that their controls operate correctly in every respect.
It is essential for security managers to understand the technology underpinnings of controls to ensure effective design and operation.
Any organization that implements controls to address risks should periodically examine those controls to determine whether they are working as intended and as designed.
SOC 1 and SOC 2 audits provide assurances of effective control design (Type I and Type II) and implementation (Type II only) in third-party service providers.
An essential function in information security management is the set of activities that determines whether security safeguards are in place and working properly. These activities range from informal security reviews to formal and highly structured security audits.
An audit is a systematic and repeatable process whereby a competent and independent professional evaluates one or more controls, interviews personnel, obtains and analyzes evidence, and develops a written opinion on the effectiveness of a control.
A control self-assessment (CSA) methodology is used by an organization to review key business objectives, risks related to achieving these objectives, and the key controls designed to manage those risks.
Personnel are the primary weak point in information security, mainly because of lapses in judgment, inattentiveness, fatigue, work pressure, or a shortage of skills. Personnel are generally considered the largest and most vulnerable portion of an organization’s attack surface.
Third-party risk management is a critical activity that attempts to identify risks in third-party organizations that have access to critical or sensitive data or that perform critical operational functions. Various techniques are needed to identify and manage risks, because many third parties are less than transparent about their internal operations and risks.
Third parties are assessed mainly through the use of questionnaires and requests for evidence that are sent to them by organizations. Most organizations depend on large numbers of third-party services, so they employ a risk tier scheme to identify the third parties that are the most critical to the organization. Third parties at a higher level of risk undergo more frequent and rigorous risk assessments, while those at lower levels undergo less frequent and less rigorous risk assessments.
The management of business relationships with third parties is a life-cycle process. The life cycle begins when an organization contemplates the use of a third party to augment or support the organization’s operations in some way. The life cycle continues during the ongoing relationship with the third party and concludes when the organization no longer requires the third party’s services.
Communications is the lifeblood of an effective information security program. Lacking effective communications, the security manager will have difficulty interacting with executive management for the exchange of objectives, risk information, and metrics. Ineffective communications will hamper virtually all other security-related activities and processes.
Security programs include a variety of administrative activities that are vital to its success. One important success factor is the development of strategic partnerships with many internal departments within an organization, as well as external organizations and agencies. These partnerships enable the security manager to better influence internal events, learn more about external events, and obtain assistance from outside entities as needed.
IT service management represents a collection of operational activities designed to ensure the quality of IT services and includes several business processes such as service desk, incident management, problem management, change management, configuration management, release management, service-level management, financial management, capacity management, service continuity management, and availability management.
Notes
• The most common approach to controls development is the selection of an already-established control framework, such as those discussed in this chapter. However, an organization is also free to develop a control framework from scratch.
• In a typical security program, the security manager will select a control framework as a starting point and then add, change, or remove controls over time as a result of the risk management process. The initial control framework should be considered only a starting point and not the set of controls that the organization is required to manage permanently.
• Security managers prefer preventive controls but will sometimes need to settle on detective controls.
• The selection of a control framework is less important than the risk management process that will, over time, mold it into the controls that need to exist.
• Many organizations ruminate over the selection of a control framework. Instead, each organization should select a framework and then make adjustments to its controls to suit the business needs. A control framework should generally be considered a starting point, not a rigid and unchanging list of controls—except in cases where regulations stipulate that controls may not be changed.
• Many organizations need to implement multiple control frameworks in response to applicable regulations and other obligations. In such cases, security managers should consider mapping them into a single control framework.
• To the extent than an organization is dependent upon IT for its operations, the organization is equally dependent upon effective cybersecurity to protect its IT.
• Data backup has always been critical, but the rise in ransomware attacks is highlighting the value of backups for business owners.
• Audit planning is multifaceted and includes scope, purpose, methodology, and audience.
• To be effective, security awareness training needs to be relevant and engaging.
• Third-party risk management is best thought of as an extension of an organization’s risk management program, with special procedures for conducting risk assessments of third-party organizations that store, process, or transmit sensitive or critical data on behalf of the organization or that perform critical operations.
• Classifying third parties into risk-based tiers helps to allocate scarce resources by focusing rigorous assessments on third parties based on risk.
• The maturity of an information security program will determine the ability for meaningful reporting to be developed.
• Without effective IT service management, no security manager can hope that information security will become truly effective.
• There is always room for improvement.
Questions
1. The most important factor in the selection of a control framework is:
A. Organization maturity
B. Industry relevance
C. Risk tolerance
D. Risk appetite
2. The life-cycle process that influences controls over time is known as:
A. Third-party risk management
B. External audit
C. Risk management
D. Internal audit
3. The main reason that preventive controls are preferred over detective controls is:
A. Preventive controls stop unwanted events from occurring.
B. Preventive controls are less expensive to implement.
C. Preventive controls are less expensive to audit.
D. Detective controls are, by definition, ineffective.
4. An organization wants to protect itself from the effects of a ransomware attack. What is the best data protection approach?
A. Periodically scan data for malware.
B. Replicate data to a cloud-based storage provider.
C. Replicate data to a secondary storage system.
D. Back up data to offline media.
5. The best definition of general computing controls is:
A. Controls that are general in nature and implemented across all systems
B. The basic safeguards required by Sarbanes–Oxley
C. Policies that apply to all systems and applications
D. Controls that are required to be audited annually
6. Which of the following is the best reason for adopting a standard control framework?
A. Controls can be enacted without time-consuming risk assessments.
B. Audits can begin earlier.
C. Audit results will be more favorable.
D. The organization will be considered more progressive.
7. All of the following statements about ISO/IEC 27002 are correct except:
A. ISO/IEC 27002 can be crosswalked to NIST SP 800-53.
B. ISO/IEC 27002 is a well-known international standard.
C. ISO/IEC 27002 is available free of charge.
D. Copies of ISO/IEC 27002 must be purchased.
8. A security manager in a healthcare clinic is planning to implement HIPAA and PCI DSS controls. Which of the following approaches should be taken?
A. Choose either HIPAA or PCI DSS and use those controls to protect both ePHI and cardholder data.
B. Enact individual HIPAA and PCI DSS controls per a risk assessment.
C. Define the applicability of HIPAA and PCI DSS to those portions of the business where ePHI and cardholder data are used.
D. Apply HIPAA and PCI DSS to the entire organization.
9. Which of the following statements correctly describes the link between risk management and controls?
A. Risk treatment sometimes calls for the enactment of a new control.
B. Controls define the scope of risk assessments.
C. Controls define the scope of risk management.
D. There is no link between risk management and controls.
10. What organization is the governing body for the PCI DSS standard?
A. ISO
B. NIST
C. PCI Security Standards Council
D. VISA and MasterCard
11. Which of the following solutions is most suitable for the following control statement: “Safeguards prevent end users from visiting hazardous web sites”?
A. Cloud access security broker
B. Web content filter
C. Virtual private network
D. Antimalware
12. The philosophy of system and data protection that relies on continual evaluation is known as:
A. Data loss prevention
B. Trust but verify
C. Transitive Trust
D. Zero Trust
13. A review of users’ access to specific information systems is best known as:
A. An audit
B. An activity review
C. A recertification
D. A corrective control
14. The information security department has sent a questionnaire and requests for evidence to a control owner. This activity is best known as a(n):
A. Control self-assessment
B. Audit
C. Review
D. Investigation
15. The most favored practice for security awareness training is:
A. Training at the time of hire
B. Training at the time of hire and annually thereafter
C. Annual training
D. Reading assignments
Answers
1. B. Organizations looking to select a control framework as a starting point for controls should select a framework that aligns with the organization’s industry. For instance, a healthcare organization may start with HIPAA, while a global manufacturer would likely select ISO/IEC 27002.
2. C. The risk management life cycle, over time, will have the greatest influence on an organization’s controls. Newly discovered risks can be managed through the enactment of new controls, for example.
3. A. Preventive controls, when available and feasible, are preferred over detective controls, because they prevent unwanted events from occurring. Detective controls, on the other hand, do not prevent events from occurring.
4. D. Backing up data to offline media is the best of these choices. For the most part, ransomware targets live data storage. Often, data replication capabilities result in the replication of the encryption to secondary storage systems.
5. A. General computing controls, or GCCs, are general in nature and applied across most or all information systems and applications. GCC’s are also known as ITGC’s, or IT General Controls.
6. A. An organization that starts with a standard control framework can enact controls immediately. Without a standard control framework, time-consuming risk assessments would need to be conducted to identify risk areas, followed by control development.
7. C. ISO/IEC 27002, as well as other ISO standards, are not available free of charge and must be purchased for individual users or with a site license.
8. C. The best approach for enacting controls in a hybrid environment such as this is to define the scope of applicability for HIPAA controls and for PCI DSS controls. HIPAA controls shall apply to systems and processes that process electronic protected healthcare information (ePHI), and PCI DSS controls shall apply to systems and processes that process cardholder data.
9. A. In the risk management life cycle, risk assessments are performed and new risks are identified. In risk treatment, sometimes the agreed-upon course of action is the enactment of a new control to mitigate a new risk.
10. C. The PCI Security Standards Council, a consortium of the world’s leading credit card brands (VISA, MasterCard, American Express, Discover, and JCB), is the governing body for the PCI DSS standard and related standards such as PA DSS.
11. B. A web content filter is the best solution for a control that protects users from visiting hazardous web sites.
12. D. Zero Trust (ZT) is the philosophy that focuses on system and data protection, where trust is not granted implicitly but must be continually evaluated at all layers.
13. B. An activity review is a study of users’ access to individual applications or systems to determine whether they access those applications or systems in a given period of time. Users who do not access those applications or systems are candidates for access removal from those systems.
14. A. In a control self-assessment (CSA), a control owner is requested to answer questions about a control and provide evidence such as a written procedure and records.
15. B. The best practice for security awareness training consists of training at the time of hire and annually thereafter. It is important for new workers to be trained on security protocols and expectations, with periodic reminders to ensure continual awareness and awareness of new protocols and threats.


