INTRODUCTION
The dizzying pace of information systems innovation has made vast expanses of information available to organizations and the public. Design flaws and technical vulnerabilities often bring unintended consequences, usually in the form of information theft and disclosure. Attacks from nation-states and cybercriminal organizations are increasing dramatically. The result is a patchwork of laws, regulations, and standards such as Sarbanes–Oxley, GDPR, CCPA, Gramm–Leach-Bliley, HIPAA, PCI DSS, PIPEDA, NERC CIP, CMMC, and scores of U.S. state laws requiring public disclosure of security breaches involving private information. The relatively new Cybersecurity & Infrastructure Security Agency (CISA) has become a prominent voice in the United States, and executive orders require organizations to improve defenses and disclose breaches. As a result of these laws and regulatory agencies, organizations are required or incentivized to build or improve their information security programs to avoid security breaches, penalties, sanctions, lawsuits, and embarrassing news headlines.
These developments continue to drive demand for information security professionals and information security leaders. These highly sought-after professionals play a crucial role in developing better information security programs that reduce risk and improve confidence in effective systems and data protection.
The Certified Information Security Manager (CISM) certification, established in 2002, has become the leading certification for information security management. Demand for the CISM certification has grown so much that the once-per-year certification exam was changed to twice per year in 2005 and is now offered continually. In 2005, the CISM certification was accredited by the American National Standards Institute (ANSI) under the international standard ISO/IEC 17024:2012 and is also one of the few certifications formally approved by the U.S. Department of Defense in its Information Assurance Technical category (DoD 8570.01-M). In 2018 and again in 2020, CISM was awarded the Best Professional Certification by SC Media. There are now more than 50,000 professionals with the certification, and the worldwide average salary for CISM holders is more than US$149,000.
Founded in 1969 as the Electronic Data Processing Auditors Association (EDPAA), ISACA is a solid and lasting professional organization. Its first certification, Certified Information Systems Auditor (CISA), was established in 1978.
Purpose of This Book
Let’s get the obvious out of the way: This is a comprehensive study guide for the security management professional who needs a serious reference for individual or group-led study for the Certified Information Security Manager (CISM) certification. The content in this book contains the technical information that CISM candidates are required to know. This book is one source of information to help you prepare for the CISM exam, but it should not be thought of as the ultimate collection of all the knowledge and experience that ISACA expects qualified CISM candidates to possess. No single publication covers all of this information.
This book is also a reference for aspiring and practicing IT security managers, security leaders, and CISOs. The content required to pass the CISM exam is the same content that practicing security managers must be familiar with in their day-to-day work. This book is a definitive CISM exam study guide as well as a desk reference for those who have already earned their CISM certification.
This book is also invaluable for information security professionals who are not in leadership positions today. You will gain considerable insight into today’s information security management challenges. This book is also helpful for IT and business management professionals working with information security leaders who need to understand what they are doing and why.
This is an excellent guide for anyone exploring a security management career. The study chapters explain the relevant technologies, techniques, and processes used to manage a modern information security program. This is useful if you are wondering what the security management profession is all about.
How to Use This Book
This book covers everything you’ll need to know for ISACA’s CISM certification examination. Each chapter covers specific objectives and details for the exam, as ISACA defines in its job practice areas. The chapters and their sections correspond precisely to the CISM job practice that ISACA updates from time to time, most recently in mid-2022.
Each chapter has several components designed to effectively communicate the information you’ll need for the exam.
• The topics covered in each chapter are listed in the first section to help map out your study.
• Tips in each chapter offer great information about how the concepts you’re reading about apply in a place I like to call “the real world.” Often, they may give you more information on a topic covered in the text.
• Exam Tips are included to highlight areas you need to focus on for the exam. They won’t give you any exam answers, but they help you know about important topics you may see on the test.
• Notes may be included in a chapter as well. These bits of information are relevant to the discussion and point out extra information.
• Fifteen practice questions at the end of each chapter are designed to enable you to attempt some exam questions on the topics covered in the domain.
• Access to an online question bank is available from TotalTester Online, customizable practice exam software with 300 practice exam questions.
• A glossary contains about 650 terms used in the information security management profession.
About This Second Edition
ISACA has historically recalibrated the contents of its certifications every five years. I learned that ISACA would update the CISM job practice (the basis for the exam and the requirements to earn the certification) in early 2022, effective in mid-2022. To ensure that this information is up to date, Wendy Rinaldi and I developed a plan for the second edition as quickly as possible; this book is the result of that effort.
The new CISM job practice information was made available in March 2022. We began work at that time to update the second edition manuscript. This has been updated to reflect all of the changes in the CISM job practice and changes in information security and information technology since the first edition was published.
Changes to the CISM Job Practice
For the 2022 CISM job practice, ISACA reformatted how the practice areas are described. Previously, each job practice had a set of Knowledge Statements and Task Statements. In the 2022 model, each job practice consists of two major categories with three to six subtopic areas each. This is followed by 37 Supporting Tasks for CISM that are not specifically associated with the four domains. Table 1 illustrates each previous and current CISM job practice and its corresponding chapters in this book, along with the structure of the new job practice and coverage in this book.
As is typical for each new job practice and revision of this CISM Certified Information Security Manager All-in-One Exam Guide, I performed a gap analysis to understand what subject matter was added to the new job practice and what was eliminated. My conclusion: ISACA made no significant additions or changes to the CISM 2022 job practice besides numerous structural changes and changes in the weighting between domains.
Several topics are new or expanded from the first edition, including the following:
• The distinction between control frameworks, program management frameworks, risk management frameworks, and architecture frameworks (with examples of each)
• Mention and discussion of a published information security framework that is older than most living people in the world
• New challenges in obtaining cyber-insurance policies
• Bow-tie risk analysis
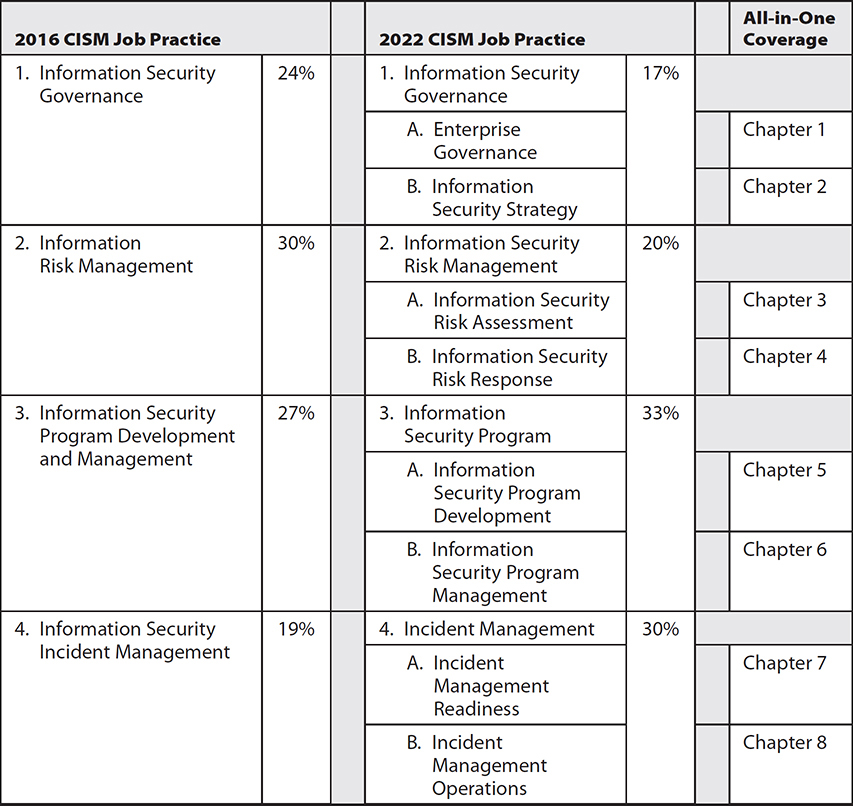
Table 1 Previous and Current CISM Job Practices and Corresponding Chapters
• Control architecture, implementation, and operation
• Controlled unclassified information (CUI)
• Crisis communications and crisis management
• Crosswalks
• Cybersecurity maturity model certification (CMMC)
• Data debt
• Data governance
• Distributed workforce
• Endpoint detection and response (EDR)
• European ETSI standards
• Extended detection and response (XDR)
• Foreign Corrupt Practices Act (FCPA)
• Groupthink
• Information governance
• Integrated risk management (IRM)
• MITRE ATT&CK framework
• Network traffic analysis (NTA)
• NIST SP 800-171 and SP 800-172
• Passwordless authentication
• Personnel classification
• Reference architectures
• Functional and nonfunctional requirements
• Risk and control ownership
• Security orchestration, automation, and response (SOAR)
• Software as a service (SaaS) disaster recovery
• SaaS security incident response
• Technical debt
• Threat intelligence platform (TIP)
• Three lines of defense
• Workforce transformation, remote work, and hybrid work models
• Zero-trust network architecture
• Addition of about 70 new entries and several cross-references to the glossary (and a few deprecated entries such as SAS-70, SET, and S-HTTP removed)
By the time we completed this book, even more new developments, technologies, techniques, and breaches provided additional insight and the promise of still more changes. Like the surface of Saturn’s moon, Io, our profession is ever-changing. The technology boneyard is filled with vendors, products, protocols, techniques, and methodologies that once held great promise, later replaced with better things. This underscores the need for security leaders (and IT, audit, and risk professionals) to stay current by reading up on current events, new technologies, and techniques. Some last-minute changes that may not be fully reflected in the manuscript include the following:
• ISO/IEC 27001:2013 was replaced by ISO/IEC 27001:2022 in early 2022.
• ISO/IEC 27002:2013 is scheduled to be replaced by ISO/IEC 27002:2022 in late 2022.
• A new U.S. national law on privacy may have been enacted.
• Additional U.S. presidential Executive Orders on the topic of cybersecurity may have been issued.
Becoming a CISM Professional
To become a CISM professional, you must pay the exam fee, pass the exam, prove that you have the necessary education and experience, and agree to uphold ethics and standards. To keep your CISM certification, you must take at least 20 continuing education hours each year (120 hours in three years) and pay annual maintenance fees. This life cycle is depicted in Figure 1.
The following list outlines the primary requirements for becoming certified:
• Experience A CISM candidate must submit verifiable evidence of at least five years of professional work experience in information security management. Experience must be verified and gained within the ten years preceding the application date for certification or within five years from passing the exam. Experience waivers are available for as many as two years.
• Ethics Candidates must commit to adhering to ISACA’s Code of Professional Ethics, which guides the personal and professional conduct of those certified.
• Exam Candidates must receive a passing score on the CISM exam. A passing score is valid for up to five years, after which the passing score is void. A CISM candidate who passes the exam has a maximum of five years to apply for CISM certification; candidates who pass the exam but fail to act after five years must retake the exam if they want to become CISM certified.
• Education Those who are certified must adhere to the CISM Continuing Professional Education Policy, which requires a minimum of 20 continuing professional education (CPE) hours each year, with a total requirement of 120 CPEs over each three-year certification period.
• Application After successfully passing the exam, meeting the experience requirements, and reading through the Code of Professional Ethics and Standards, a candidate is ready to apply for certification. An application must be received within five years of passing the exam.
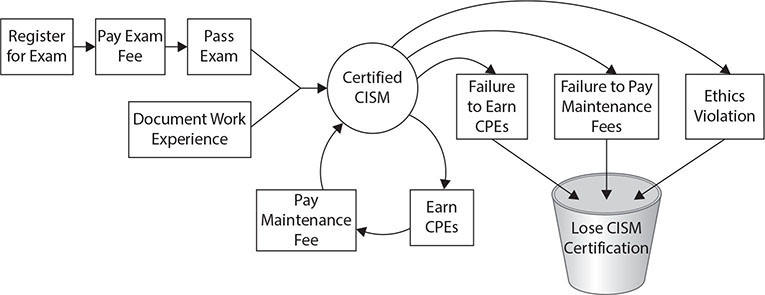
Figure 1 The CISM certification life cycle (Source: Peter Gregory)
Experience Requirements
To qualify for CISM certification, you must have completed the equivalent of five years of total work experience in information security management. Additional details on the minimum certification requirements, substitution options, and various examples are discussed next.
Direct Work Experience
You must have a minimum of five years of work experience in the field of information security management. This is equivalent to roughly 10,000 actual work hours, which must be related to three or more of the CISM job practice areas, as follows:
• Information security governance Establish and/or maintain an information security governance framework and supporting processes to ensure that the information security strategy is aligned with organizational goals and objectives.
• Information security risk management Manage information risk to an acceptable level based on risk appetite to meet organizational goals and objectives.
• Information security program Develop and maintain an information security program that identifies, manages, and protects the organization’s assets while aligning to information security strategy and business goals, thereby supporting an effective security posture.
• Incident management Plan, establish, and manage the capability to detect, investigate, respond to, and recover from information security and disaster incidents to minimize business impact.
All work experience must be completed within the ten-year period before completing the certification application or within five years from the date of initially passing the CISM exam. You will need to complete a separate Verification of Work Experience form for each segment of experience.
Substitution of Experience
Up to two years of direct work experience can be substituted with the following to meet the five-year experience requirement. Only one waiver is permitted.
Two Years
• Certified Information Systems Auditor (CISA) in good standing
• Certified Information Systems Security Professional (CISSP) in good standing
• MBA or master’s degree in information security or a related field; transcripts or a letter confirming degree status must be sent from the university attended to obtain the experience waiver
One Year
• Bachelor’s degree in information security or a related field
• Skill-based or general security certification
• One full year of information systems management experience
Here is an example of a CISM candidate whose experience and education are considered for CISM certification: A candidate graduated in 2002 with a bachelor’s degree in computer science. They spent five years working for a software company managing IT, and in January 2015, they began managing information security. In January 2017, they took some time off work for personal reasons. In 2019, they earned their Security+ certification and rejoined the workforce in December 2019, working as a risk manager for a public company in its enterprise risk management department. The candidate passed the CISM exam in June 2022 and applied for CISM certification in September 2022. Do they have all of the experience required? What evidence will they need to submit?
• Skills-based certification The candidate obtained their Security+ certification, which equates to a one-year experience substitution.
• Two years of direct experience They can count their two full years of information security management experience in 2015 and 2016.
• One-year substitution They cannot take into account one year of IT management experience completed between January 2002 to January 2007, because it was not completed within ten years of their application.
• One-year direct experience The candidate would want to utilize their new risk manager experience for work experience.
The candidate would need to send the following with their application to prove the experience requirements are met:
• Verification of Work Experience forms filled out and signed by their supervisors (or any superior) at the software company and the public company, verifying both the security management and non–security management work conducted
• Transcripts or letters confirming degree status sent from the university
ISACA Code of Professional Ethics
Becoming a CISM professional means adhering to the ISACA Code of Professional Ethics, a formal document outlining what you will do to ensure the utmost integrity in a way that best supports and represents the profession. Specifically, the ISACA code of ethics requires ISACA members and certification holders to do the following:
• Support the implementation of, and encourage compliance with, appropriate standards and procedures for the effective governance and management of enterprise information systems and technology, including audit, control, security, and risk management.
• Perform their duties with objectivity, due diligence, and professional care, in accordance with professional standards.
• Serve in the interest of stakeholders in a lawful manner, while maintaining high standards of conduct and character and not discrediting their profession or the association.
• Maintain the privacy and confidentiality of information obtained in the course of their activities unless disclosure is required by legal authority. Such information shall not be used for personal benefit or released to inappropriate parties.
• Maintain competency in their respective fields and agree to undertake only those activities they can reasonably expect to complete with the necessary skills, knowledge, and competence.
• Inform appropriate parties of the results of work performed, including the disclosure of all significant facts known to them that, if not disclosed, may distort the reporting of the results.
• Support the professional education of stakeholders in enhancing their understanding of the governance and management of enterprise information systems and technology, including audit, control, security, and risk management.
Failure to comply with this Code of Professional Ethics can result in an investigation into a member’s or certification holder’s conduct and, ultimately, disciplinary measures, including the forfeiture of hard-won certification(s).
You can find the full text and terms of enforcement of the ISACA Code of Ethics at www.isaca.org/ethics.
The Certification Exam
The certification is offered throughout the year in several examination windows. You have several ways to register; however, I highly recommend planning and registering early regardless of your chosen method.
In 2022, as I write, the schedule of exam fees in U.S. dollars is
• CISM application fee: $50
• Regular registration: $575 member/$760 nonmember
As I write this, we’re emerging from the global COVID-19 pandemic. During the pandemic, ISACA and other certification bodies adapted and developed remotely proctored exams that permitted test-takers to sit for a certification exam from their residence. I have observed that ISACA has returned to tests administered at testing centers while continuing to offer remotely proctored exams for those who prefer remote testing. I’ll discuss both options in this section.
Once your registration is complete, you will immediately receive an e-mail acknowledging this. Next, you will need to schedule your certification exam. The ISACA web site will direct you to the certification registration page, where you will select a date, time, and (optionally) location to take your exam. When you confirm the date, time, and location for your exam, you will receive a confirmation via e-mail. You will need the confirmation letter to enter the test location—make sure to keep it unmarked and in a safe place until test time.
Onsite Testing Center
When you arrive at the test site, you will be required to sign in, and you may be required to sign an agreement. Also, you will be asked to turn in your smartphone, wallet or purse, and other personal items for safekeeping. The exam proctor will read aloud the rules you must follow while taking the exam. These rules will address matters such as breaks, drinking water, and snacks. While you take the exam, you will be supervised by the proctor, who may monitor you and your fellow test-takers by video surveillance in the test center to ensure that no one can cheat.
Remote Proctored Testing
If you have registered for a remote proctored exam, you must meet all of the technical requirements. ISACA has published the “Remote Proctoring Guide” that includes all of the necessary technical requirements and describes the step-by-step procedures for taking the exam.
A remote proctored exam means you’ll be taking the exam on your own computer in your residence or other location. You’ll be in live contact with an exam proctor, and your webcam will be turned on throughout the exam so that the proctor can observe while you take the exam to ensure you are not cheating through the use of reference materials (books or online). You will also be required to use your webcam to show the entire room to your proctor, to demonstrate that you do not have reference materials or information anywhere in view.
To be eligible for a remote proctored exam, you must have a supported version of Windows or macOS, a current Google Chrome or other Chromium (such as Brave, SRware Iron) browser, a webcam with at least 640×480 resolution, a microphone, and a stable broadband Internet connection. You must be able to install the PSI Secure Browser and modify firewalls and other administrative tasks on the day of the exam (this requires administrative privileges on the computer you are using, which might be a problem if you are using a company-issued computer).
You’ll be required to log in to your My ISACA account when your exam is scheduled. Next, you’ll navigate to your certifications, find the exam you have scheduled, and launch the exam. You’ll be directed to perform several tasks, including installing the secure browser and closing several other programs on your computer, such as other web browsers and programs such as Adobe Reader, Word, Excel, and any others that could include reference material.
You are not permitted to speak or perform gestures during the exam. In short, you cannot be seen to perform any action that may be an indication of aid by an accomplice.
You’ll be required to verify your ID by holding it near your webcam so that the proctor can see it to confirm that you, not someone else, are taking the exam. You will also be required to use your webcam to show the entire room to your proctor.
After completing all steps, the proctor will release the exam and you may begin.
Exam Questions
Each registrant has four hours to take the exam, with 150 multiple-choice questions representing the four job practice areas. Each question has four answer choices; you must select only one best answer. You can skip questions and return to them later, and you can also flag questions you want to review later if time permits. While you are taking your exam, the time remaining will appear on the screen.
When you have completed the exam, you’ll be directed to close the exam. At that time, the exam will display your pass or fail status, reminding you that your score and passing status are subject to review. You will be scored for each job practice area and then provided one final score. All scores are scaled. Scores range from 200 to 800; a final score of 450 is required to pass.
Exam questions are derived from a job practice analysis study conducted by ISACA. The selected areas represent tasks performed in a CISM’s day-to-day activities and the background knowledge required to develop and manage an information security program. You can find more detailed descriptions of the task and knowledge statements at www.isaca.org/credentialing/cism/cism-exam-content-outline.
Exam Coverage
The CISM exam is quite broad in its scope. It covers four job practice areas, as shown in Table 2.
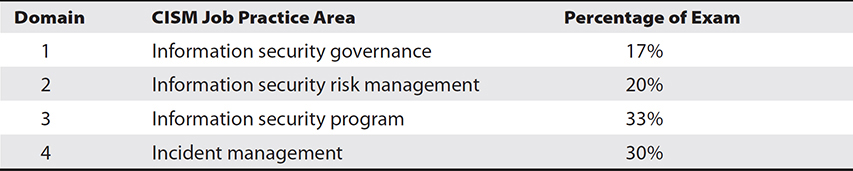
Table 2 CISM Exam Practice Areas
Independent committees have been developed to determine the best questions, review exam results, and statistically analyze the results for continuous improvement. Should you come across a horrifically difficult or strange question, do not panic. This question may have been written for another purpose. A few questions on the exam are included for research and analysis purposes and will not be counted against your score. The exam contains no indications in this regard, so do your best to answer every question.
Preparing for the Exam
The CISM certification requires that CISM candidates possess much knowledge and experience. You need to map out a long-term study strategy to pass the exam. The following sections offer some tips to help guide you to, through, and beyond exam day.
Before the Exam
Consider the following list of tips on tasks and resources for exam preparation. They are listed in sequential order.
• Read the candidate’s guide For information on the certification exam and requirements for the current year, go to www.isaca.org/credentialing/exam-candidate-guides and select the guide in your language of choice.
• Register If you can, register early for any cost savings and solidify your commitment to moving forward with this professional achievement.
• Schedule your exam Find a location, date, and time, and then commit.
• Become familiar with the CISM job practice areas The job practice areas serve as the basis for the exam and requirements. Beginning with the 2022 exam, the job practice areas have changed. Ensure that your study materials align with the current list at www.isaca.org/credentialing/cism.
• Download and study the ISACA Glossary It’s important for you to be familiar with ISACA’s vocabulary, which you can download from www.isaca.org/resources/glossary.
• Know your best learning methods Everyone has preferred learning styles, whether self-study, a study group, an instructor-led course, or a boot camp. Try to set up a study program that leverages your strengths.
• Self-assess Run through practice exam questions available for download (see the appendix for more information). ISACA may offer a free online CISM self-assessment.
• Iterative study Depending on your work experience in information security management, I suggest you plan your study program to take at least two months but as long as six months. During this time, periodically take practice exams and note your areas of strength and weakness. Once you have identified your weak areas, focus on those areas weekly by rereading the related sections in this book, retaking practice exams, and noting your progress.
• Avoid cramming We’ve all seen the books on the shelves with titles that involve last-minute cramming. The Internet reveals various web sites that teach individuals how to cram for exams. Research sites claim that exam cramming can lead to susceptibility to colds and flu, sleep disruptions, overeating, and digestive problems. One thing is certain: many people find that good, steady study habits result in less stress and greater clarity and focus during the exam. Because of the complexity of this exam, I highly recommend the long-term, steady-study option. Study the job practice areas thoroughly. There are many study options. If time permits, investigate the many resources available to you.
• Find a study group Many ISACA chapters and other organizations have formed specific study groups or offer less expensive exam review courses. Contact your local chapter to see whether these options are available to you. In addition, be sure to keep your eye on the ISACA web site. And use your local network to find out whether there are other local study groups and helpful resources.
• Confirmation letter Recheck your confirmation letter. Do not write on it or lose it. Put it in a safe place and note on your calendar when you will need to arrive at the site. Confirm that the location is the one you selected and is nearby.
• Logistics check Check the candidate guide and your confirmation letter for the exact time you are required to report to the test site (or log in from home if you registered for a remote proctored exam). A few days before the exam, check the site—become familiar with the location and tricks to getting there. If you are taking public transportation, be sure to look at the schedule for the day of the exam: if your CISM exam is on a Saturday, public transportation schedules may differ from weekday schedules. If you are driving, know the route and where to park your vehicle.
• Pack The night before, place your confirmation letter and a photo ID in a safe place, ready to go. Your ID must be a current, government-issued photo ID that matches the name on the confirmation letter and must not be handwritten. Examples of acceptable forms of ID are passports, driver’s licenses, state IDs, green cards, and national IDs. Leave behind food, drinks, laptops, cell phones, and other electronic devices, because they are not permitted at the test site. For information on what can and cannot be brought to the exam site, see the CISM exam candidate guide at www.isaca.org/credentialing/cism.
• Notification decision Decide whether you want your test results e-mailed to you. You will have the opportunity to consent to e-mail notification of the exam results. If you are fully paid (zero balance on exam fee) and have agreed to the e-mail notification, you should receive a one-time e-mail approximately eight weeks from the exam date with the results.
• Sleep Make sure you get a good night’s sleep before the exam. Research suggests that you avoid caffeine at least four hours before bedtime. Keep a notepad and pen next to the bed to capture late-night thoughts that might keep you awake, eliminate as much noise and light as possible, and keep your room a suitable temperature for sleeping. In the morning, rise early so as not to rush and subject yourself to additional stress.
Day of the Exam
On the day of the exam, follow these tips:
• Arrive early Check the Bulletin of Information and your confirmation letter for the exact time you are required to report to the test site. The confirmation letter and the candidate guide explain that you must be at the test site no later than approximately 30 minutes before testing time. The examiner will begin reading the exam instructions at this time, and any latecomers will be disqualified from taking the test and will not receive a refund of fees.
• Observe test center rules There may be rules about taking breaks. This will be discussed by the examiner, along with exam instructions. If you need something during the exam and are unsure about the rules, be sure to ask first. For information on conduct during the exam, see the ISACA Exam Candidate Information Guide at www.isaca.org/credentialing/exam-candidate-guides.
• Answer all exam questions Read questions carefully, but do not try to overanalyze. Remember to select the best solution based upon the CISM Job Practice and ISACA’s vocabulary. There may be several reasonable answers, but one is better than the others. If you aren’t sure about an answer, mark the question, so that after working through all the questions, you can return to any marked questions (and others) to read them and consider them more carefully. Above all, don’t try to overanalyze questions, and do trust your instincts. Do not try to rush through the exam; there is plenty of time to take as much as a few minutes for each question. But at the same time, do watch the clock so that you don’t find yourself going so slowly that you won’t be able to answer every question thoughtfully.
• Note your exam result When you have completed the exam, you should see your pass/fail result. Your results may not be in large, blinking text; you may need to read the fine print to get your preliminary results. If you passed, congratulations! If you did not pass, observe any remarks about your status; you will be able to retake the exam—you’ll find information about this on the ISACA web site.
After the Exam
A few weeks from the exam date, you will receive your exam results by e-mail or postal mail. Each job practice area score will be noted in addition to the final score. All scores are scaled. Should you receive a passing score, you will also receive the application for certification.
Those unsuccessful in passing will also be notified. These individuals will want to closely look at the job practice area scores to determine areas for further study. They may retake the exam as often as needed on future exam dates, as long as they have registered and paid the applicable fees. Regardless of pass or fail, exam results will not be disclosed via telephone, fax, or e-mail (except for the consented e-mail notification).
Applying for CISM Certification
You must submit evidence of a passing score and related work experience to apply for certification. Remember that you have five years to apply for CISM certification after you receive a passing exam score. After this time, you will need to retake the exam before you can apply. In addition, all work experience submitted must have occurred within ten years of your new certification application.
To complete the application process, you need to submit the following information:
• CISM application Note the exam ID number in your exam results letter, list the information security management experience and any experience substitutions, and identify which CISM job practice area (or areas) your experience pertains to.
• Verification of Work Experience forms These must be filled out and signed by your immediate supervisor or a person of higher rank in the organization to verify your work experience noted on the application. You must fill out a complete set of Verification of Work Experience forms for each separate employer.
After you’ve submitted the application, you will wait approximately eight weeks for processing. Then, if your application is approved, you will receive an e-mail notification, followed by a package in the postal mail containing your letter of certification, certificate, and a copy of the Continuing Professional Education Policy. You can then proudly display your certificate and use the “CISM” designation on your résumé, e-mail, social media profiles, and business cards.
Retaining Your CISM Certification
There is more to becoming a CISM professional than passing an exam, submitting an application, and receiving a paper certificate. Becoming a CISM professional is an ongoing and continuous lifestyle. Those with CISM certification agree to abide by the code of ethics, meet ongoing education requirements, and pay annual certification maintenance fees. Let’s take a closer look at the education requirements and explain the costs of retaining certification.
Continuing Education
The goal of professional continuing education requirements is to ensure that individuals maintain CISM-related knowledge to help them successfully develop and manage security management programs. To maintain CISM certification, individuals must obtain 120 continuing education hours within three years, with a minimum requirement of 20 hours per year. Each CPE hour accounts for 50 minutes of active participation in educational activities.
What Counts as a Valid CPE Credit?
For training and activities to be utilized for CPEs, they must involve technical or managerial training directly applicable to information security and information security management. The following activities have been approved by the CISM certification committee and can count toward your CPE requirements:
• ISACA professional education activities and meetings
• ISACA members can take Information Systems Control Journal CPE quizzes online or participate in monthly webcasts, earning CPEs after passing a quiz
• Non-ISACA professional education activities and meetings
• Self-study courses
• Vendor sales or marketing presentations (10-hour annual limit)
• Teaching, lecturing, or presenting on subjects related to job practice areas
• Publication of articles and books related to the profession
• Exam question development and review for any ISACA certification
• Passing related professional examinations
• Participation in ISACA boards or committees (20-hour annual limit per ISACA certification)
• Contributions to the information security management profession (10-hour annual limit)
• Mentoring (10-hour annual limit)
For more information on acceptable CPE credit, see the Continuing Professional Education Policy at www.isaca.org/credentialing/how-to-earn-cpe/#cpe-policy.
Tracking and Submitting CPEs
Not only are you required to submit a CPE tracking form for the annual renewal process, but you also should keep detailed records for each activity. Records associated with each activity should include the following:
• Name of attendee
• Name of sponsoring organization
• Activity title
• Activity description
• Activity date
• Number of CPE hours awarded
It is best to track all CPE information in a single file or worksheet. ISACA has developed a tracking form for your use in the Continuing Professional Education Policy. To make it easy on yourself, consider keeping all related records such as receipts, brochures, and certificates in the same place. Documentation should be retained throughout the three-year certification period and for at least one additional year afterward. Evidence retention is essential, as you may someday be audited. If this happens, you will be required to submit all paperwork. So why not be prepared?
For new CISMs, the annual and three-year certification period begins on January 1 of the year following certification. You are not required to report CPE hours for the first partial year after your certification; however, the hours earned from the time of certification to December 31 can be utilized in the first certification reporting period the following year. Therefore, should you get certified in January, you will have until the following January to accumulate CPEs. You will not have to report them until you report the totals for the following year, in October or November. This is known as the renewal period. You will receive an e-mail directing you to the web site to enter CPEs earned over the year. Alternatively, the renewal will be mailed to you, and then CPEs can be recorded on the hard-copy invoice and sent with your maintenance fee payment. CPEs and maintenance fees must be received by January 15 to retain certification.
Notification of compliance from the certification department is sent after all the information has been received and processed. If ISACA has questions about your submitted information, you will be contacted directly.
Sample CPE Records
Table 3 contains an example of CPE records.
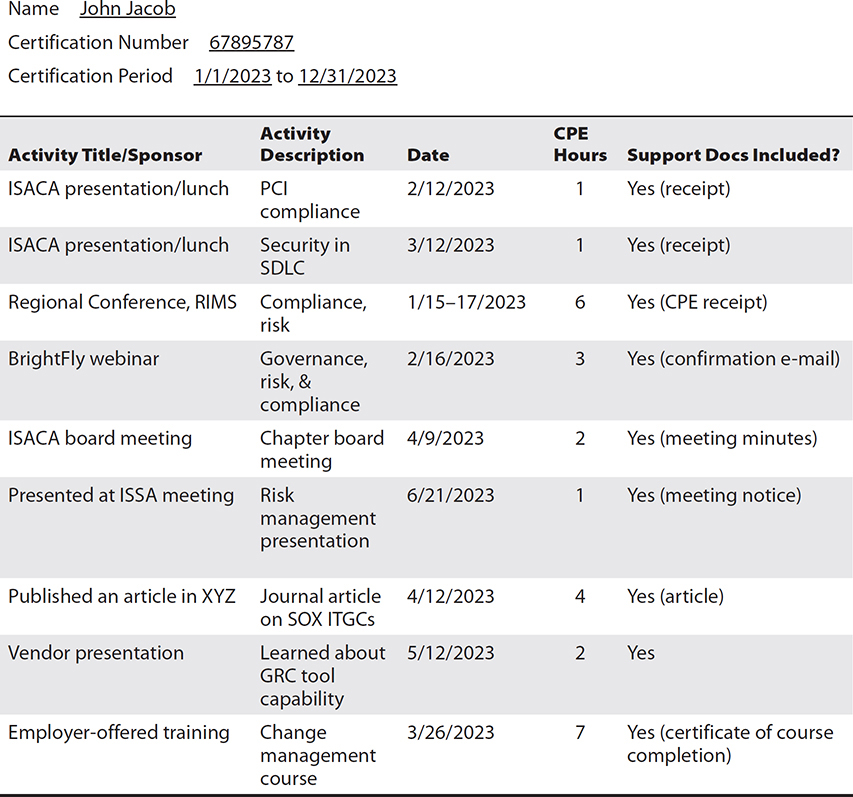
Table 3 Sample CPE Records
CPE Maintenance Fees
To remain CISM certified, you must pay CPE maintenance fees each year. These annual fees are (as of 2022) $45 for members and $85 for nonmembers. The fees do not include ISACA membership and local chapter dues (neither is required to maintain your CISM certification). More information is available from www.isaca.org/credentialing/cism/maintain-cism-certification.
Revocation of Certification
A CISM-certified individual may have his or her certification revoked for the following reasons:
• Failure to complete the minimum number of CPEs during the period
• Failure to document and provide evidence of CPEs in an audit
• Failure to submit payment for maintenance fees
• Failure to comply with the Code of Professional Ethics, which can result in investigation and ultimately lead to revocation of certification
If you have received a revocation notice, contact the ISACA Certification Department at https://support.isaca.org/ for more information.
Living the CISM Lifestyle
Being a CISM-certified individual involves much more than passing the exam, participating in continuous learning, and paying the annual maintenance fees. There are numerous opportunities to get involved in local, national, and global activities and events to help you grow professionally and meet other risk management professionals.
Find a Local Chapter
ISACA has more than 200 chapters in about 100 countries around the world. Chances are there is a chapter near you. I attended many ISACA chapter meetings and other events in Seattle when I lived there, where engaging speakers spoke on new topics, and I met many like-minded security and audit professionals over the years.
Local chapters rely entirely on volunteers, and there is room for you to help in some way. Some chapters have various programs, events, study groups, and other activities that enrich participants professionally. Most of my ISACA experiences happen in my local chapter.
Attend ISACA Events
ISACA puts on fantastic in-person conferences with world-class keynote speakers, expert presentations, vendor demonstrations and exhibits, a bookstore, and opportunities to meet other security, risk, and audit professionals. I find ISACA conferences enriching to the point of being overwhelming. With so many learning and networking opportunities, I have found myself nearly exhausted at the end of an ISACA conference.
Join the Online Community
ISACA has an online community known as Engage, in which participants can discuss any topic related to security, risk, audit, privacy, and IT management. You can read and participate in online discussions, ask questions, help others with their questions, and make new professional connections. You can join Engage at https://engage.isaca.org/.
Pay It Forward Through Mentorship
If you are at the point in your career where you qualify for and have a reasonable prospect of passing the CISM exam, chances are you have had a mentor or two earlier, and maybe you have one now. As you grow in your professional stature, others will look to you as a potential mentor. Perhaps someone will ask if you would consider mentoring him or her. The world needs more, and better, information security professionals and leaders. Mentoring is a great way to “pay it forward” by helping others get into the profession and grow professionally. Mentoring will enrich your life as well.
Volunteer
As a nonprofit organization, ISACA relies upon volunteers to enrich its programs and events. There are many ways to help, and one or more of these volunteer opportunities may suit you:
• Speak at an ISACA event Whether you make a keynote address or host a session on a specific topic, speaking at an ISACA event is a mountaintop experience. You can share your knowledge and expertise on a particular topic with attendees, but you’ll learn some things too.
• Serve as a chapter board member Local chapters don’t run by themselves; they rely on volunteers—working professionals who want to improve the lot of other professionals in the local community. Board members can serve in various ways, from financial management to membership to events.
• Start or help a CISM study group Whether part of a local chapter or a chapter at large, consider starting or helping a group of professionals who want to learn the details of the CISM job practice. I am a proponent of study groups because study group participants make the best students: they take the initiative to take on a big challenge to advance their careers.
• Write an article ISACA has online and paper-based publications that feature articles on various subjects, including current developments in security, privacy, risk, and IT management from many perspectives. If you have specialized knowledge on some topic, other ISACA members can benefit from this knowledge if you write about it.
• Participate in a credential working group ISACA works hard to ensure that its many certifications remain relevant and up to date. Experts worldwide in many industries give of their time to ensure that ISACA certifications remain the best in the world. ISACA conducts online and in-person working groups to update certification job practices, write certification exam questions, and publish updated study guides and practice exams. I contributed to the first CRISC certification working group in 2013 when ISACA initially developed the CRISC certification exam; I met many like-minded professionals, some of whom I am still in regular and meaningful contact with.
• Participate in ISACA CommunITy Day ISACA organizes a global effort of local volunteering to make the world a better, safer place for everyone. Learn about the next CommunITy day at https://engage.isaca.org/communityday/.
• Write certification exam questions ISACA needs experienced subject matter experts willing to write new certification exam questions. ISACA has a rigorous, high-quality process for exam questions that includes training. You could even be invited to an in-person exam item writing workshop. You can find out more about how this works at www.isaca.org/credentialing/write-an-exam-question.
Please take a minute to reflect upon the quality and richness of the ISACA organization and its many world-class certifications, publications, and events. These are all fueled by volunteers who made ISACA into what it is today. Only through your contribution of time and expertise will ISACA continue in its excellence for future security, risk, privacy, and IT professionals. And one last thing you can only experience on your own: volunteering helps others and enriches you. Will you consider leaving your mark and making ISACA better than you found it? For more information about these and many other volunteer opportunities, visit www.isaca.org/why-isaca/participate-and-volunteer.
Continue to Grow Professionally
Continual improvement is a mindset and lifestyle built into IT service management and information security, and it’s even a formal requirement in ISO/IEC 27001! I suggest you periodically take stock of your career status and aspirations, be honest with yourself, and determine what mountain you will climb next. If needed, find a mentor who can guide you and give you solid advice.
Although this may not immediately make sense to you, know this: helping others, whether through any of the volunteer opportunities listed here, or in other ways, will enrich you personally and professionally. I’m not talking about feathers in your cap or juicy items in your résumé, but rather the growth in character and wisdom that results from helping and serving others, particularly when you initiated the helping and serving.
Professional growth means different things to different people. Whether it’s a better job title, more money, a better (or bigger, or smaller) employer, a different team, more responsibility, or more certifications, embarking on long-term career planning will pay dividends. Take control of your career and your career path. This is yours to own and shape as you will.
Summary
Becoming and being a CISM professional is a lifestyle, not just a one-time event. It takes motivation, skill, good judgment, persistence, and proficiency to be a strong and effective leader in information security management. The CISM certification was designed to help you navigate the security management world more easily and confidently.
Each CISM job practice area is discussed in detail in the following chapters, and additional reference material is presented. Not only is this information helpful for those of you who are studying before taking the exam, but it is also meant to serve as a resource throughout your career as an information security management professional.


