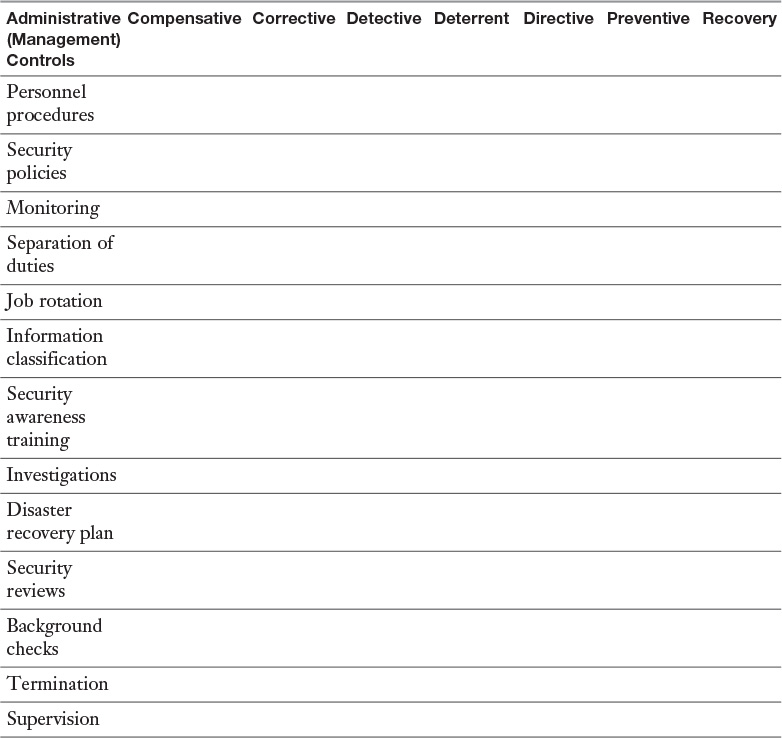
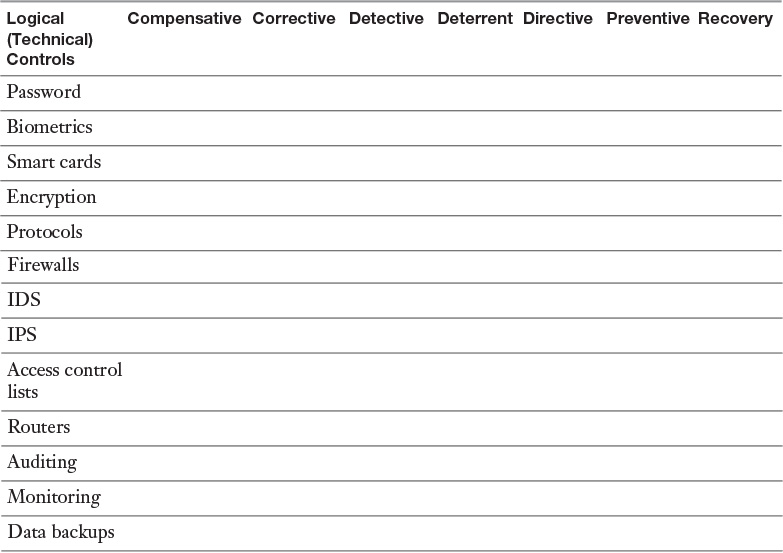
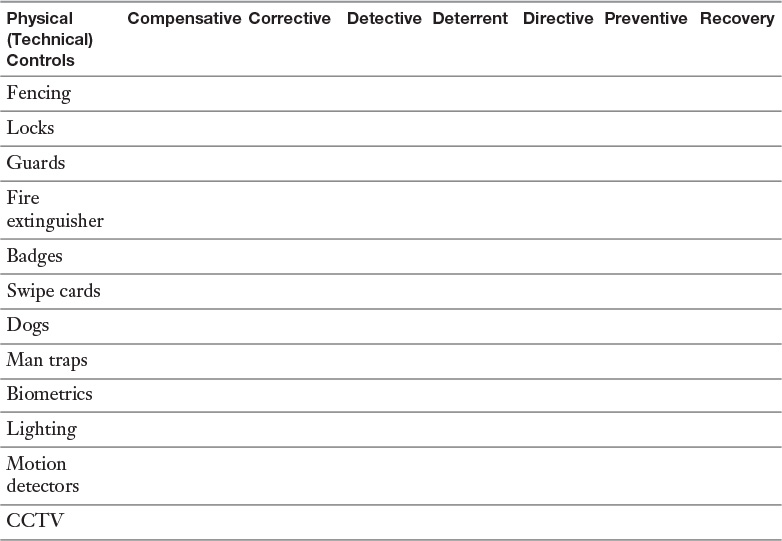
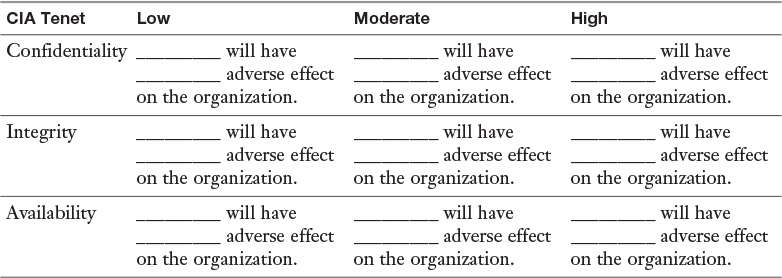
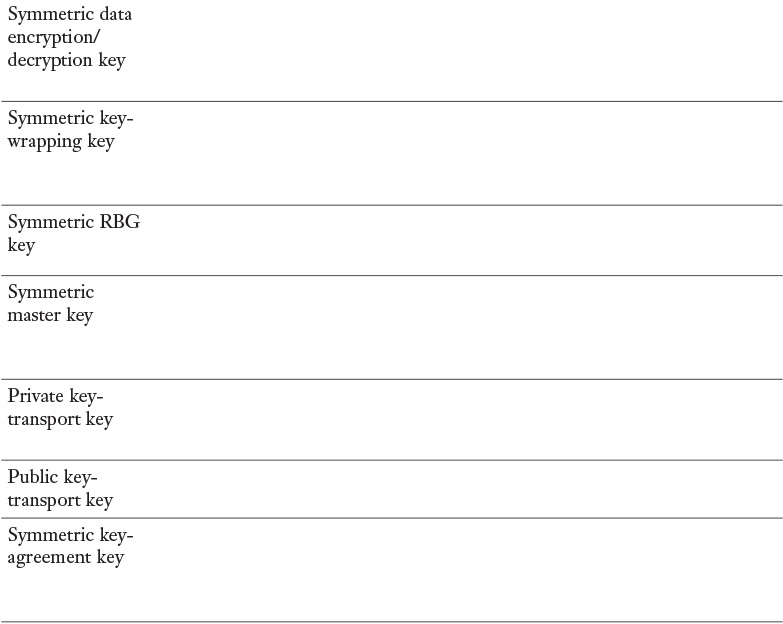
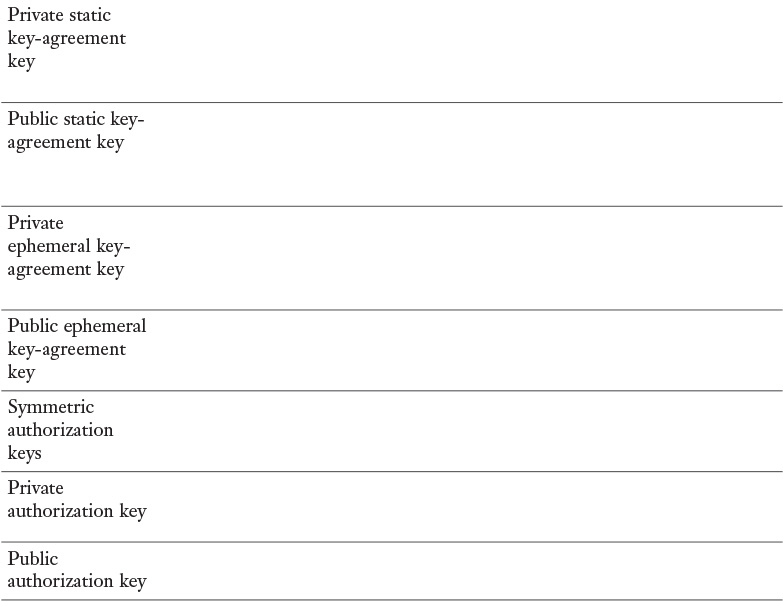
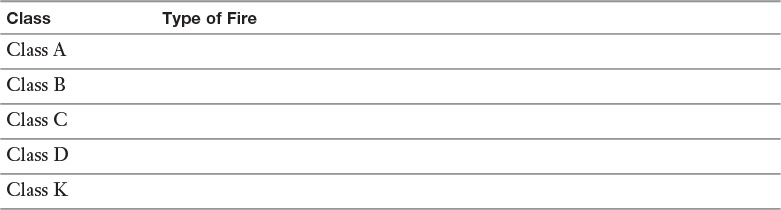
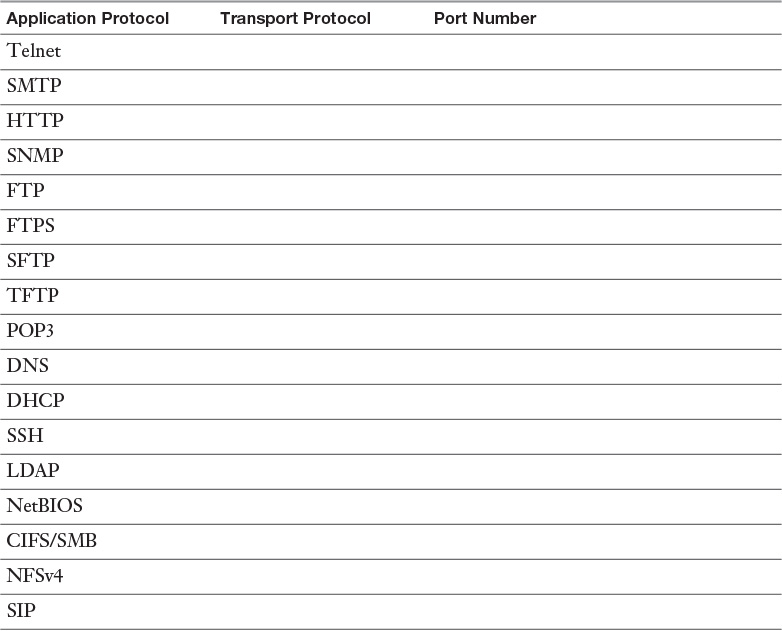
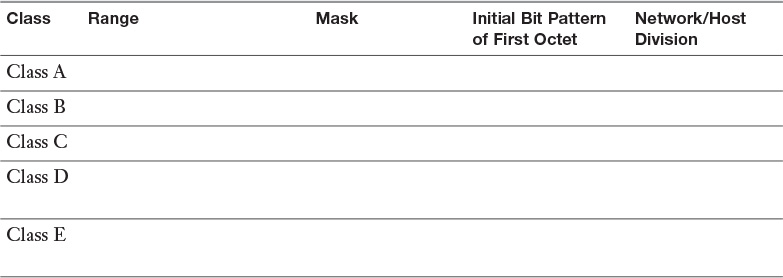
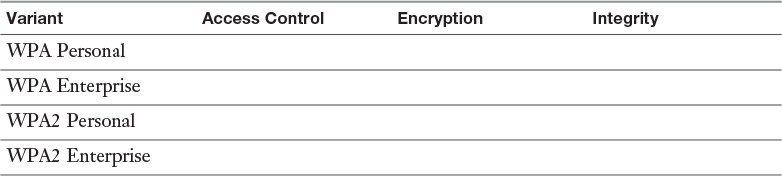
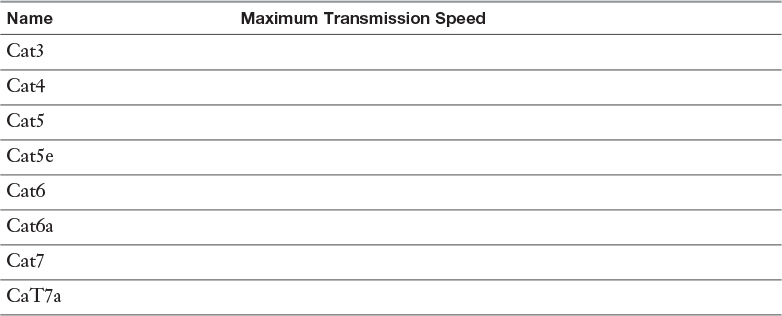
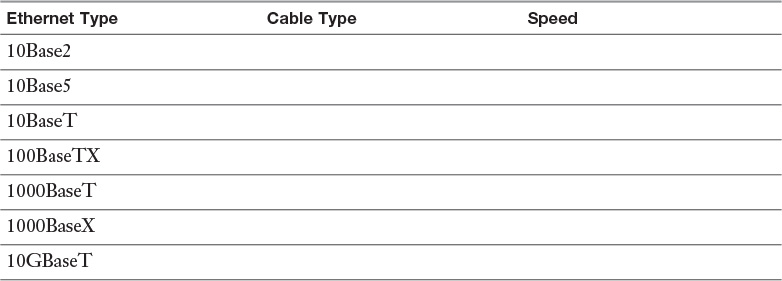
Appendix A. Memory Tables
Chapter 1
As part of determining how critical an asset is, you need to understand the following terms:
![]() Maximum tolerable downtime (MTD): The _______ amount of time that an organization can tolerate a single resource or function being down. This is also referred to as _______.
Maximum tolerable downtime (MTD): The _______ amount of time that an organization can tolerate a single resource or function being down. This is also referred to as _______.
![]() Mean time to repair (MTTR): The _______ required to _______ a single resource or function when a disaster or disruption occurs.
Mean time to repair (MTTR): The _______ required to _______ a single resource or function when a disaster or disruption occurs.
![]() Mean time between failure (MTBF): The _______ a device will operate before a _______ occurs. This amount is calculated by the _______. System reliability is increased by a _______ MTBF and _______ MTTR.
Mean time between failure (MTBF): The _______ a device will operate before a _______ occurs. This amount is calculated by the _______. System reliability is increased by a _______ MTBF and _______ MTTR.
![]() Recovery time objective (RTO): The _______ after a disaster or disruptive event within which a resource or function must be _______ to avoid unacceptable consequences. RTO assumes that an acceptable period of downtime exists. RTO should be smaller than _______.
Recovery time objective (RTO): The _______ after a disaster or disruptive event within which a resource or function must be _______ to avoid unacceptable consequences. RTO assumes that an acceptable period of downtime exists. RTO should be smaller than _______.
![]() Work recovery time (WRT): The _______ between RTO and MTD, which is the remaining time that is left over after the RTO before reaching the maximum tolerable.
Work recovery time (WRT): The _______ between RTO and MTD, which is the remaining time that is left over after the RTO before reaching the maximum tolerable.
![]() Recovery point objective (RPO): The _______ to which the disrupted resource or function must be _______.
Recovery point objective (RPO): The _______ to which the disrupted resource or function must be _______.