In this chapter, you will learn about hacking web application components and how to describe what occurs during a web application attack. You will also gain knowledge about effective countermeasures to help safeguard systems.
- 1.
Identify web application components.
- 2.
Describe web application attacks.
- 3.
Identify countermeasures.
Web Application Attacks
- 1.
Scanning is the first step, which starts with running a port scan to find the open HTTP and HTTPS ports. This also helps determine which services are running and retrieve the default page from each open port.
- 2.
Information gathering is the step that occurs when the attacker parses each page to find regular links and works to determine the structure of the site and the logic of the applications. They also check pages for comments that may help in gaining access to restricted files.
- 3.
Testing is another step in web application attacks. When an attacker is getting ready for an attack, they run a test process for each of the application scripts and look for development errors.
- 4.
Planning the attack occurs when the attacker selects a specific attack based on the information gathered.
- 5.
Launching the attack is the last step, which occurs when the attacker goes after each web application identified as being vulnerable.
Cross-Site Scripting Attack
When a user visits a web site, the user may log in. If the site is using a server-side script, it generates a welcome page, and a cookie is placed on the user’s computer. The cookie is retrieved any time the web site is visited.
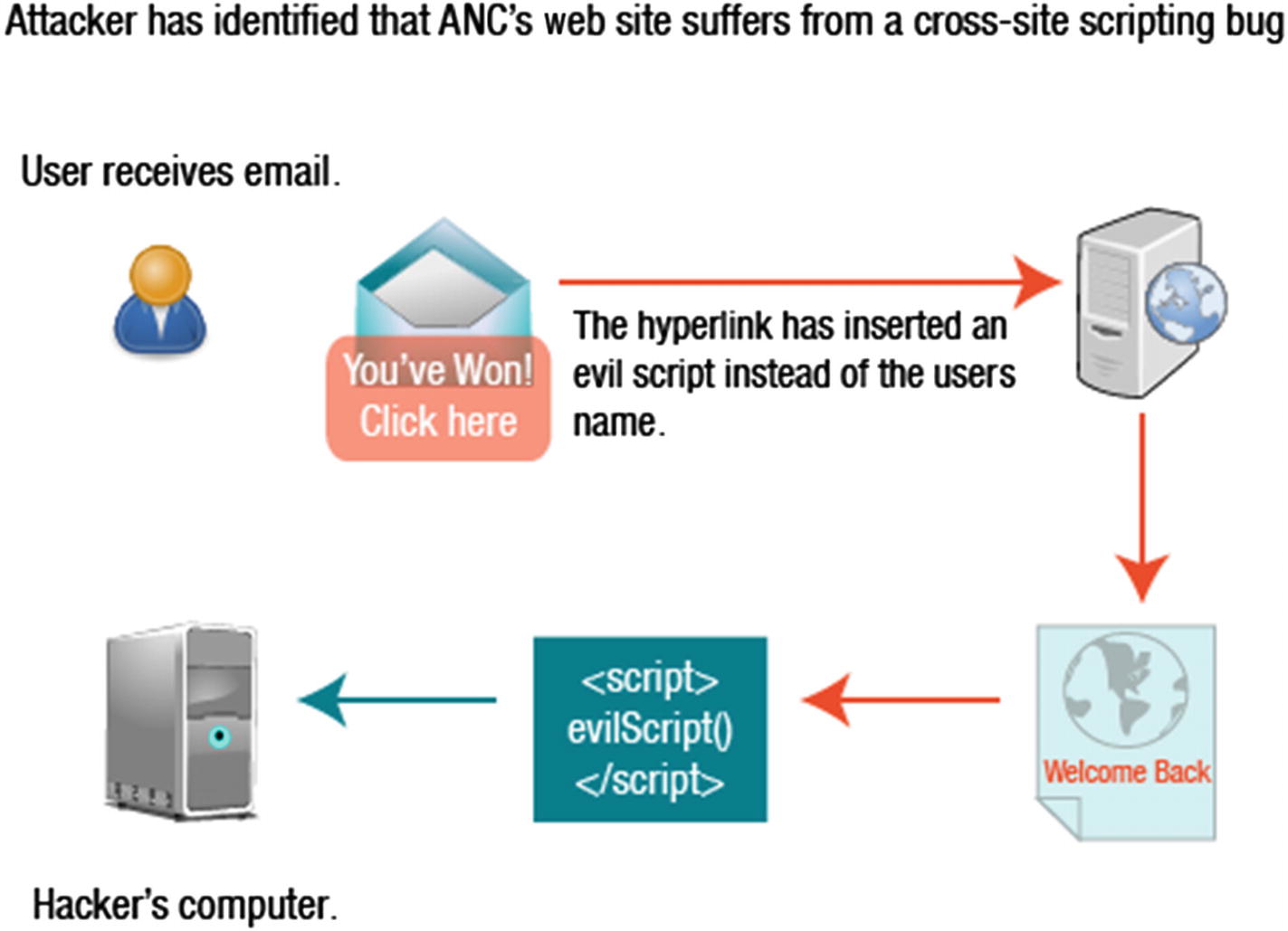
Cross-site scripting attack
Countermeasures
Validate all form fields, hidden fields, headers, cookies, and query strings.
Review code for all places where input from an HTTP request comes as output through HTML.
Limit input fields. Script attacks require a lot of characters.
SQL Injection
A SQL injection attack will work if the application does not properly validate user input before passing it to a SQL statement. The attacker bypasses normal security measures to obtain direct access to valuable data. SQL injection attacks use SQL statements to control database data.
Applications use SQL statements to authenticate users to the application, validate roles and access levels, store and obtain information, and link to other data sources. A countermeasure is to not allow unchecked user input to database queries.
Cookie/Session Poisoning
Cookies are used to maintain a session state tying an individual to a web application. Cookie poisoning allows an attacker to inject malicious content to obtain unauthorized information.
User IDs
Passwords
Account numbers
Shopping cart contents
User’s private information
Session IDs
There are several purposes for cookies. One is so sites can “remember” you while you are browsing. Persistent cookies are stored on the computer’s hard disk while non-persistent cookies are stored in memory and secure cookies are transferred through SSL.
Threats that come with saving cookies are that the attacker can use the cookie for authentication in accessing a system and they can rewrite session data.
Never store simple text or weak passwords in your system.
Implement cookie timeouts.
Tie the cookie authentication credentials to an IP address.
Provide a logout function.
Use a MAC to protect a cookie’s integrity.
Parameter/Form Tampering
This attack takes advantage of the hidden or fixed fields as the only security measure for certain operations. An attacker will change these parameters to bypass the security mechanism. Attribute parameters characterize the behavior of the page being uploaded.
When a form is submitted using a GET method, all form parameters and values appear in the query string, which the user sees. The attacker can tamper with the query string. A good countermeasure is to perform a validity check on all forms.
Buffer Overflow
Web applications and server software can have buffer overflow errors. If there is a buffer overflow in the server product, it is usually common knowledge. If a web application uses those libraries, it becomes vulnerable to a buffer overflow attack.
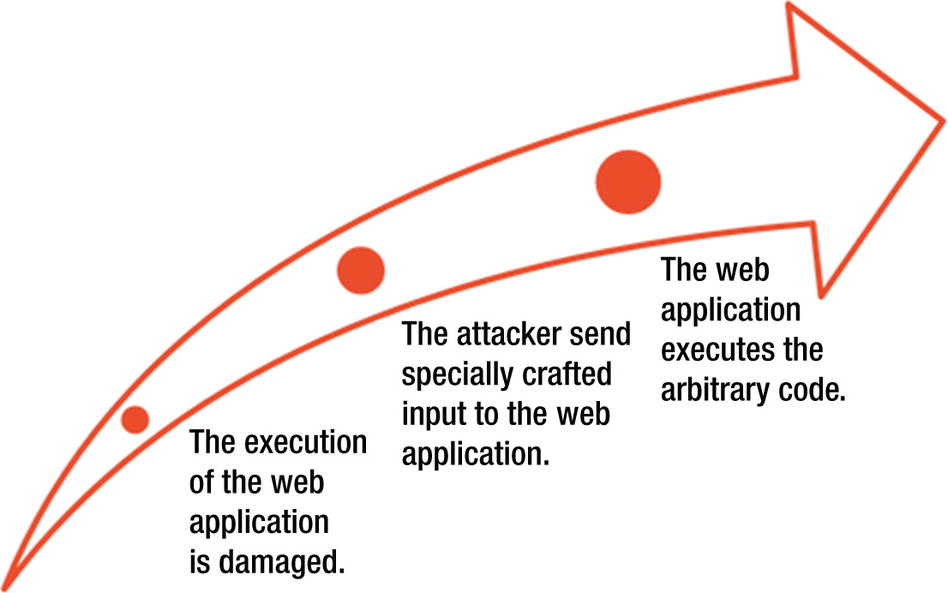
Buffer overflow
Error Message Interception
You may have seen a “404 – Not Found” error message if you have experienced a problem surfing the Web. Error messages can also contain site-specific information which would allow an attacker to learn information about the application architecture. They can be used to determine the technologies used in web applications, to determine the success of an attack attempt, and to gather information for future attacks. An effective countermeasure is to use a generic error message.
Other Attacks
Directory traversal allows the attacker to browse for directories and files. Having a strong configuration will prevent information leakage.
Cryptographic interception occurs when attackers look for handoff points where data is temporarily unprotected. To prevent this, you should use SSL and advanced private-key protection.
Authentication hijacking is when attackers take advantage of insecure credential and identify management. To prevent this, you should authenticate over secure channels and use SSL and advanced private-key protection.
Log tampering occurs when the attacker deletes logs and changes user information to destroy evidence of an attack. Preventative measures against log tampering include digital sign and time-stamp logs.
DMZ protocol attacks limit protocols allowed into the DMZ to FTP, SMTP, DNS, HTTP, and HTTPS. One way to protect against this attack is to use an intrusion prevention system.
Security management exploits occur when the attacker can modify protection policies, add new policies, and modify applications, system data, and resources. All management functions should be firewalled to prevent this type of attack.
Zero day attacks happen when time elapses between the time a vulnerability is discovered and the time that a corrective patch is issued. To prevent this, stay updated with the latest hotfixes and patches, employ a firewall, and enable heuristic scanning.
Network access attacks occur when attackers use spoofing, bridging, ACL attacks, and stack attacks. Use an inspection network firewall, NAT, or network ACLs to prevent this attack.
TCP fragmentation is when the attacker fragments an attack into multiple TCP packets. Prevention includes using firewall rules to inspect the traffic directed at the web server.
Using Nmap
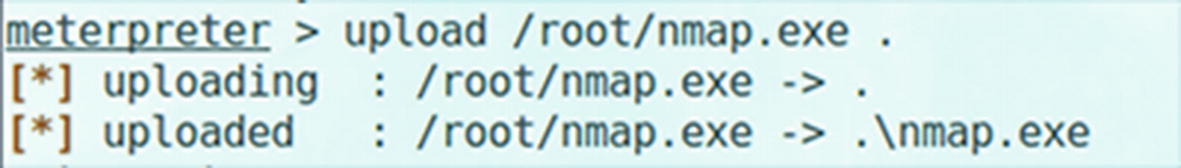
Uploading Nmap
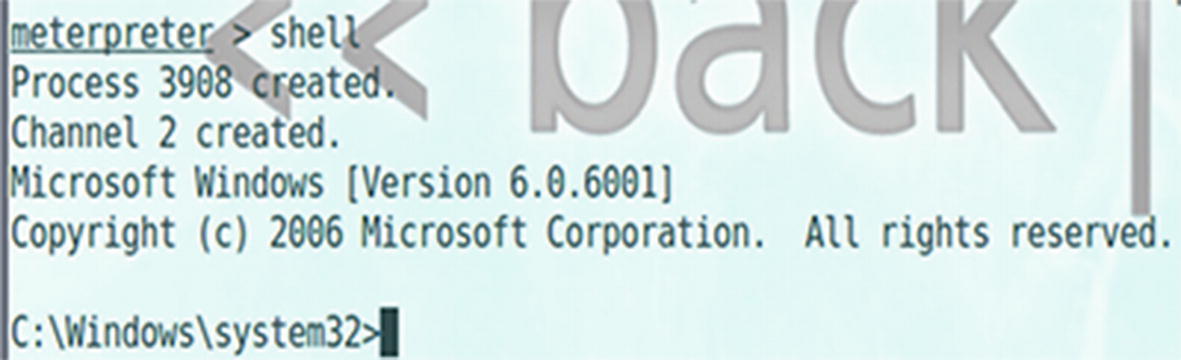
Opening a reverse shell
Nmap scan
Using ncat
Ncat options
Establishing a Session

Establishing a session
Summary
In this chapter, you reviewed several different types of attacks that can take place on web applications. You also learned how to categorize web application attacks and about countermeasures that can be used to safeguard against these types of attacks.
