Cryptography is the technique of taking plain, legible text and implementing an algorithm to it to encrypt it to produce ciphertext, which seems to be gibberish before it is decrypted. To maintain confidentiality, encryption is used.
In this chapter, you will take a look at the encryption algorithms used today and how you can apply encryption to maintain two of the three security principles—confidentiality and integrity. You will learn about public key cryptography, digital signatures, and how to examine encrypted email.
- 1.
Recognize public key cryptography.
- 2.
Identify a digital signature.
- 3.
Define a message digest.
- 4.
Define the secure sockets layer (SSL).
- 5.
Analyze encrypted email.
Symmetric Encryption
Even for the oldest ciphers, holding a same key is the basis. Both sides need to know the direction and amount of shift being carried out in shift ciphers.
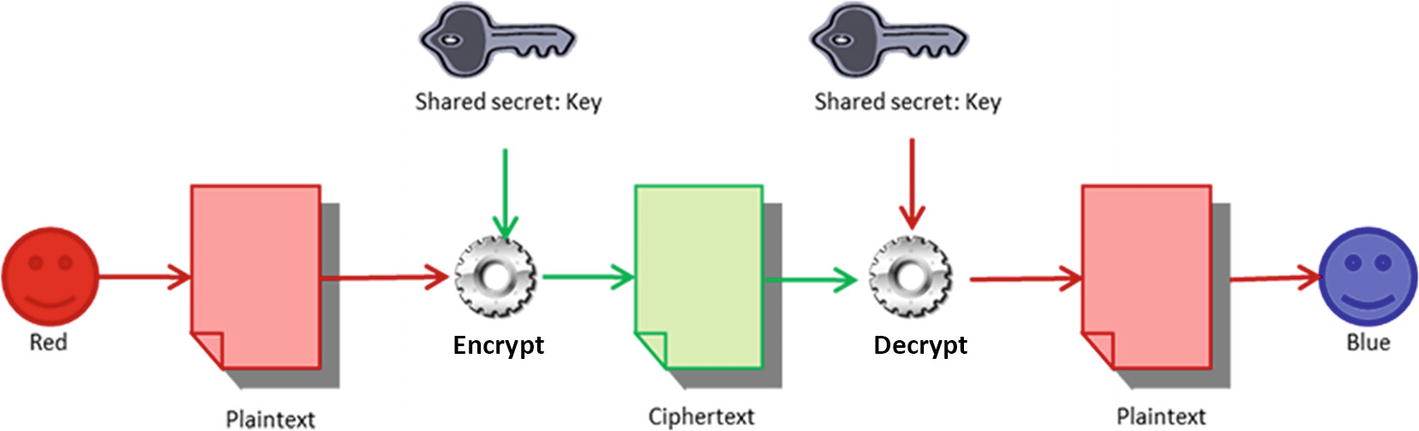
Cryptographic public and private keys being used to encrypt and decrypt
Symmetric Algorithms
Symmetric Algorithms
Symmetric algorithm | Main characteristics |
|---|---|
DES | Block cipher with a block size of 64, 56-bit key length |
3DES | Uses either two or three keys and involves multiple encryptions which go through the DES algorithm three times |
AES | A block cipher that splits the data input into blocks of 128, 192, or 256 bits. The key sizes are 128, 192, and 256 bits, with the key size impacting the number of rounds used in the algorithm |
CAST | Uses block size of 64 bits for 64- and 128-bit keys (128-bit block size for the 256-bit key version) |
RC6 | Runs well on 32-bit computers and is resistant to brute force attacks (128-bit block size, keys sizes: 128, 192, and 256) |
RC4 | Stream cipher which uses key lengths of 8 to 2048 bits, most vulnerable to possibility of weak keys |
Blowfish | Block mode cipher, using 64-bit blocks and a variable key length from 32 to 448 bits. On 32-bit machines, it runs well. |
IDEA | Block mode cipher using 64-bit block size and 128-bit key |
Asymmetric Encryption
Asymmetric encryption is also known as public key encryption. This method relies on having a key pair—the public key and a private key. The two keys are mathematically related, but you cannot figure out the private key just because you know someone’s public key.
A key pair gets generated. The public key gets published to a third-party server where others will be able to access it. A user’s private key stays with the user (within the software application, for example). One key locks the plaintext or encrypts it, and the other unlocks the ciphertext or decrypts it. Neither key is able to execute both functions alone. Without compromising security, the public key can be published, whereas the private key must not be disclosed to someone not allowed to read the messages.
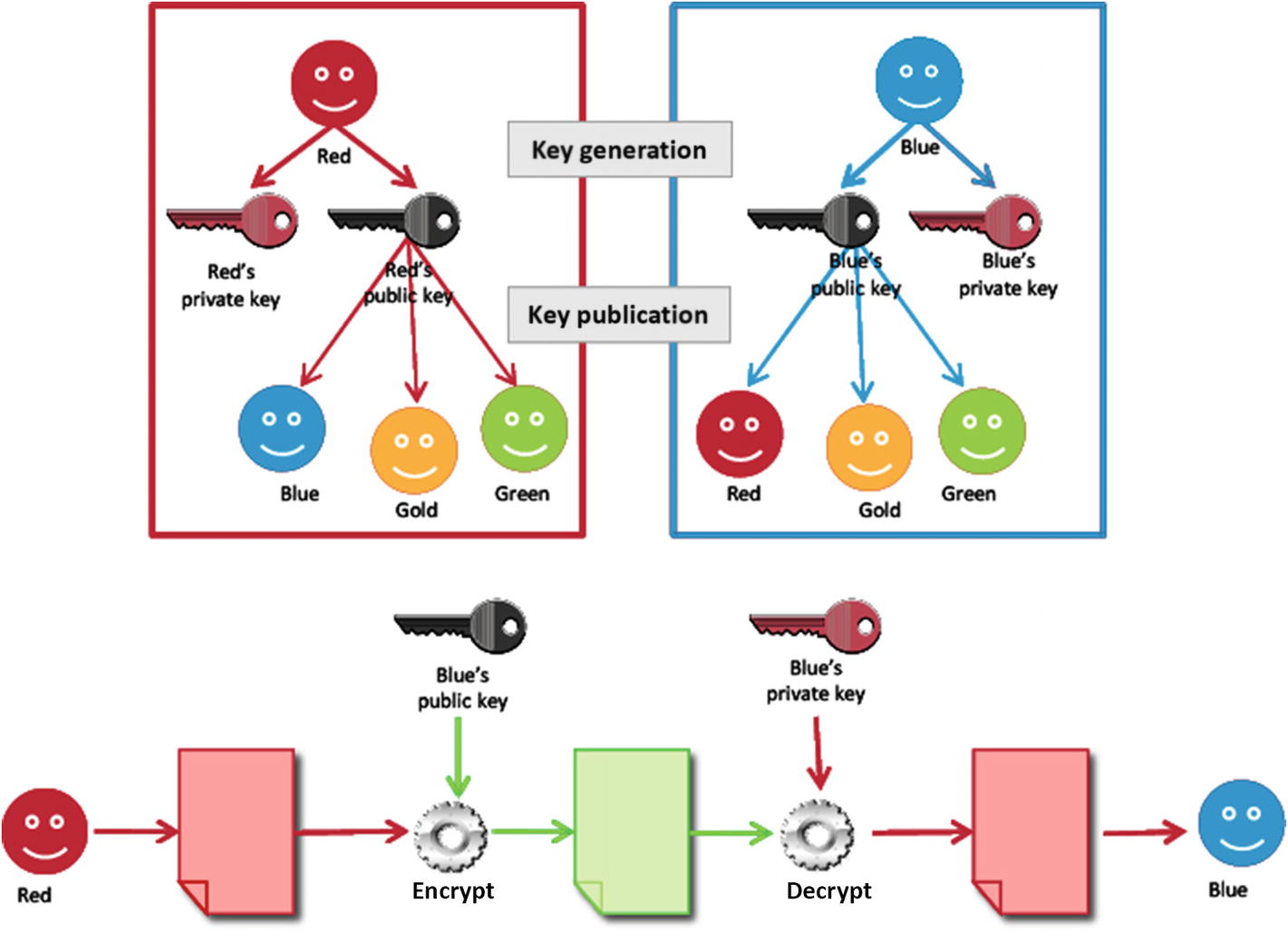
How to encrpt a message based on the example above
Asymmetric Algorithms
Asymmetric Algorithms
Asymmetric Algorithms | Main Characteristics |
|---|---|
RSA | Used for encryption and digital signatures and also uses the product of two very large prime numbers (between 100 and 200 digits long and of equal length) |
Diffie-Hellman | An electronic key exchange method of the Secure Sockets Layer (SSL) protocol that enables the sharing of a secret key |
ElGamal | Free for use (was never patented) and is used as the U.S. government standard for digital signatures |
Elliptic Curve Cryptography (ECC) | Works on the basis of elliptic curves |
Hashing Functions
Hashing functions are used to ensure that a message or data has not changed. In other words, we are talking about maintaining integrity. If you download a program from the Internet, you may see that a message digest value is noted using a particular hashing algorithm. After you download the file, use a hash calculator on that file. Your result should be an exact match to the value provided at the website. If the values are not the same , it means that the file has been tampered with in some way.
Hash Algorithms
SHA: A compression function is applied to data input by an SHA algorithm. It can take up to 264 bits and then compresses it down to a lower number of bits (i.e. 160 bits for SHA-1). Longer versions are recognized as SHA-2 (SHA-256, SHA-384, and SHA-512). A longer hash result implies it is much more difficult to successfully attack.
Message Digest (MD): MD5 is message digest algorithm that produces a 128-bit hash for a message of any length and divides the message into blocks of 512-bit.
Cryptography Algorithm Use: Confidentiality
For both stored data and transmitted data, maintaining confidentiality is often essential. Symmetric encryption is preferred in both cases due to its speed and also because the size of the object being encrypted can be greatly increased by certain asymmetric algorithms.
For a stored item, a public key is generally unnecessary since the item is encrypted to secure it against other people’s access. For the transmitted data, public key cryptography is generally used for the exchange of secret key, and symmetric cryptography is then used to maintain confidentiality of the data being transmitted.
Asymmetrical cryptography maintains confidentiality, but its size and speed make it easier to protect small units’ confidentiality for tasks like electronic key exchange. In all cases, the complexity of the algorithms and the length of the keys ensure the confidentiality of the data in question.
The confidentiality of the data stored or transmitted is created and maintained through the use of a cryptography algorithm. Maintaining integrity is an integral part of the security of the message. The hash functions determine the digests of the message, and this ensures the message’s integrity. In addition, the sender of the message can no longer deny that they have sent a message that is significant in the electronic exchanges of data. Finally, authentication enables people prove that they are who they claim they are.
Cryptography Algorithm Use: Digital Signatures
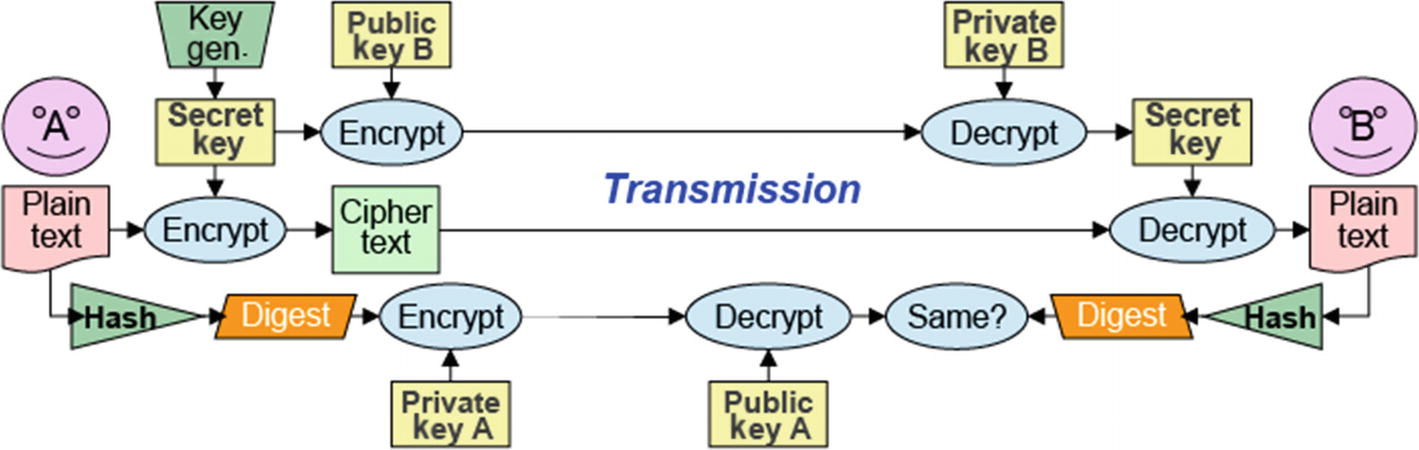
Hashing functions and asymmetric cryptography used to create digital signatures
When it comes to online transactions, digital signatures can provide non-repudiation, which is important to ensure that a party to a contract or communication cannot refuse the authenticity of their signature on a paper in the first place. Non-repudiation in this sense relates to the ability to ensure that a party to a contract must acknowledge the authenticity of their signature on a paper.
Secure Sockets Layer (SSL)
Secure Sockets Layer, or SSL , manages the encryption of information being transmitted over the Internet. SSL uses both asymmetric and symmetric authentication mechanisms and is responsible for carrying out the SSL handshake. The process starts with a request from a client for a secure connection and a response from a server. Both sides need to agree on a widely held protocol.
SSL Handshake
- 1.
The client sends its SSL version number, cipher settings, and session-specific data to the server.
- 2.
The server sends the same plus its own certificate. If the resource requested requires client authentication, the server requests the client’s certificate.
- 3.
The client authenticates using the information it has received.
- 4.
The client encrypts a seed value with the server’s public key and sends it to the server. If the server requests client authentication, the client also sends the client certificate.
- 5.
If the server requests client authentication, the server attempts to authenticate the client certificate.
- 6.
The server uses its private key to decrypt the secret and then generates a master secret.
- 7.
Both the client and the server use the master secret to generate the session key, a symmetric key.
- 8.
The client informs server that future messages will be encrypted with the session key.
- 9.
The server informs the client the same.
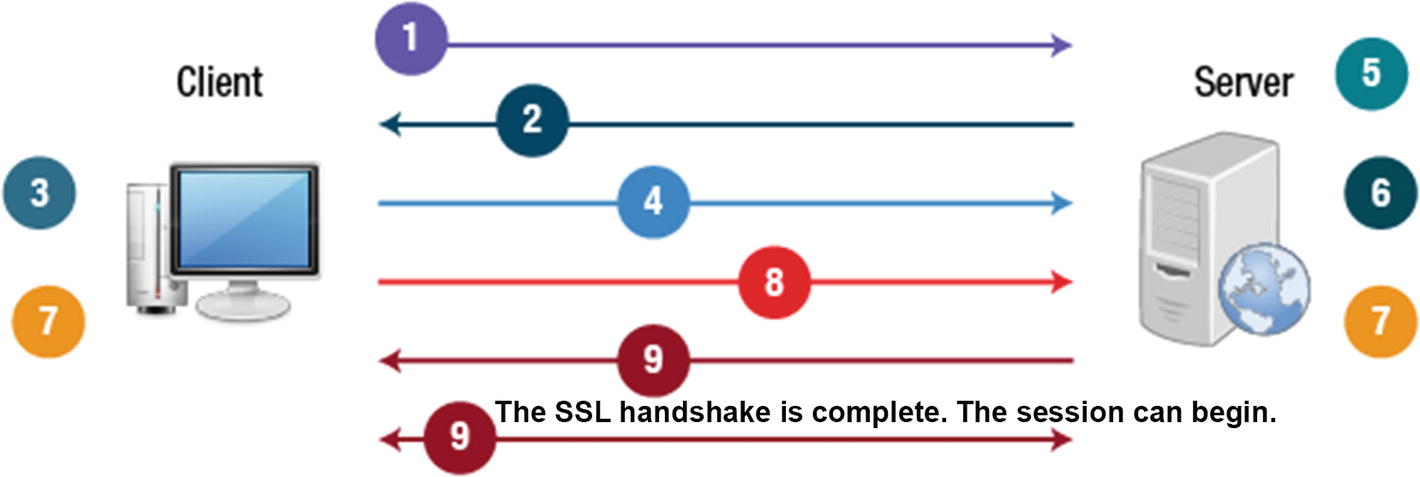
SSL handshake process
Secure Shell (SSH)
SSH is the safe alternative for the insecure application of Telnet. Telnet enables users to connect between systems. Though Telnet is still used, it has some disadvantages.
SSH uses an SSH daemon to open a protected transport channel between machines on each end. These daemons initiate contact through TCP port 22 and then communicate in a secure mode over higher ports. One of SSH’s strengths is its support for several different protocols for encryption.

Remote Access Protocol using SSH
Cryptographic Applications
Pretty Good Privacy (PGP) apps can be incorporated into common email programs to perform most day-to-day encryption tasks by utilizing a combination of symmetric and asymmetric encryption protocols.
One of PGP’s distinctive features is its potential of using both symmetric and asymmetric methods of encryption, leveraging each method’s strengths and also avoiding each method’s weaknesses. Symmetric keys are used for bulk encryption, benefiting from the efficiency and speed of symmetric encryption. The symmetric keys are passed by asymmetric methods, which capitalize on this method’s flexibility.
TrueCrypt is a solution for encryption that is open source. It is intended for symmetric disk-based file encryption. It includes AES ciphers and the ability to construct a deniable volume, encryption stored within encryption, which prevents volume detection. TrueCrypt can carry out file encryption and whole disk encryption. The complete hard drive of a computer, along with the operating system, is encrypted by whole disk encryption.
FreeOTFE is just like TrueCrypt. As an open source, freely accessible program, it provides on-the-fly disk encryption. It is able to encrypt files up to whole disks with several common ciphers, like AES.
Gnu Privacy Guard (GnuPG) is an open source implementation of the Pretty Good Privacy (OpenPGP) specification. It’s a public key encryption program that is intended to secure electronic communications like emails. It works in the same way as PGP and provides a method to manage public/private keys. Encryption of the file system has become a standard means of protecting data when in storage. Even hard drives with built-in AES encryption are available.
BitLocker . Microsoft launched BitLocker with its Encrypting File System (EFS). It is a boot-sector encryption method, which helps protect data on the most recent Windows operating systems. BitLocker uses AES encryption to automatically encrypt all files on the hard drive. All encryption takes place in the background and decryption happens smoothly when data is required. You can store the decryption key in a TPM or on a USB key.
Attacks Against Cryptography
Asymmetric encryption is also known as public key encryption. This method relies on having a key pair—the public key and a private key. The two keys are mathematically related, but you cannot figure out the private key just because you know someone’s public key.
The process begins by generating a key pair. The public key gets published to a third-party server where others will be able to access it. A user’s private key stays with the user (within the software application, for example). One key locks the plaintext or encrypts it, and the other unlocks the ciphertext or decrypts it. Neither key is able to execute both functions alone. Without compromising security, the public key can be published, whereas the private key must not be disclosed to someone not allowed to read the messages.
For example, say you needed to send Jane an encrypted message. You use Jane’s public key, accessed via a third-party server, to encrypt the message, and then you send it to her. Jane uses her private key to decrypt the message. If Karl intercepted the message, he would not be able to decrypt the message even though he also has access to Jane’s public key.
It is important to be aware of the different types of attacks known to occur against cryptography. Passive attacks occur with the use of Wireshark and tcpdump. Active attacks involve the use of birthday attacks, mathematical attacks, and man-in-the-middle. Advanced attacks include the use of cryptanalysis, brute force attacks, and pattern analysis.
Encrypting Email
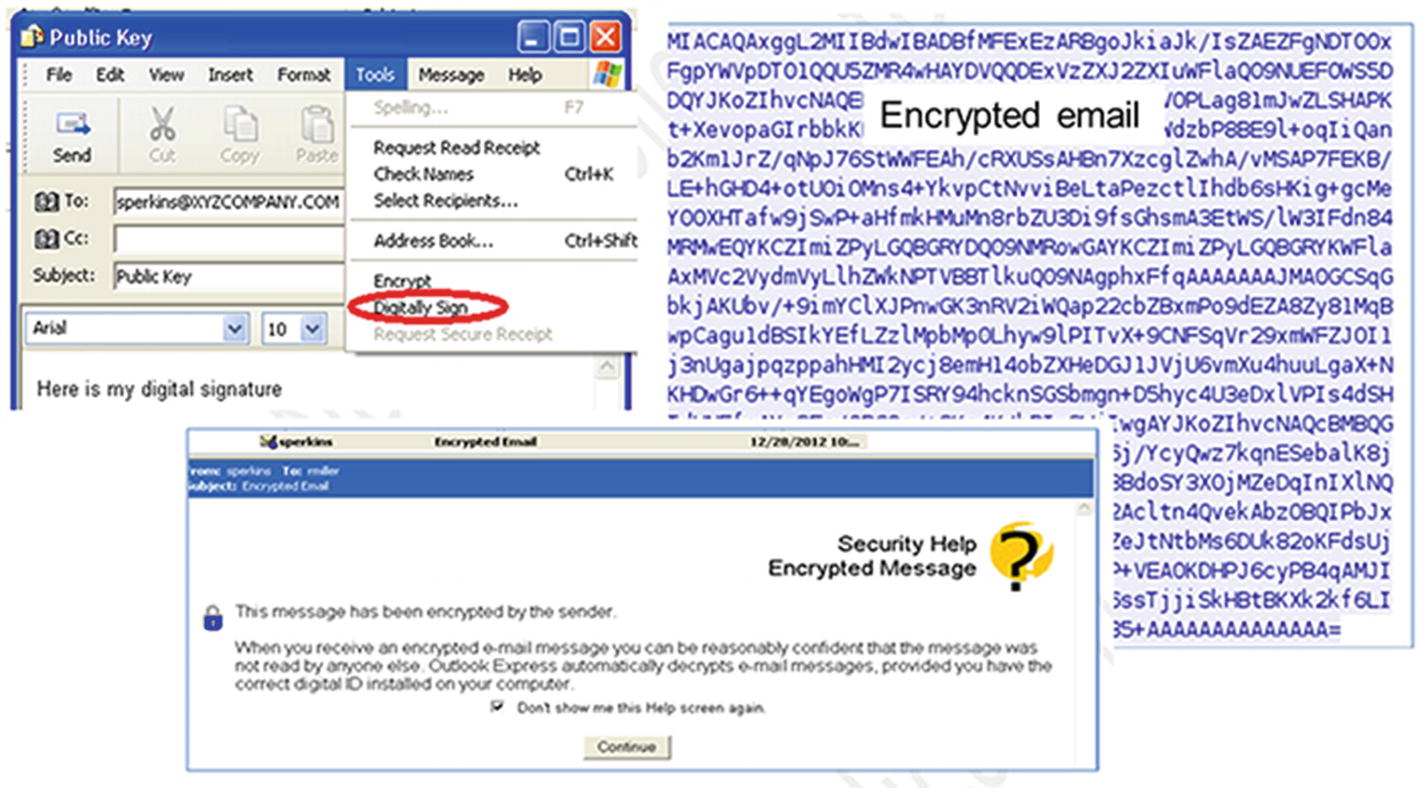
How to select the Digitally Sign option from the Tools dropdown menu. The Security Help Encrypted Message advises that the message has been encrypted by the sender
Summary
In this chapter, you learned that cryptography is a process used to take plain readable text and apply an algorithm to it, encrypting it to create ciphertext. This ciphertext appears unreadable until it is decrypted. You reviewed encryption algorithms, how to apply encryption to ensure confidentiality and integrity, key cryptography, digital signatures, and how to analyze encrypted email.
