Chapter 4: Understanding Security Principles
On a network, there are many applications and network protocols. These are like the vehicles that transport our data from a source to a destination. While many of these network protocols are designed with good intentions to help users communicate and share resources, threat actors such as hackers use these protocols to distribute their malware and compromise other systems on a network. As an upcoming cybersecurity professional, it's important you understand the challenges security professionals experience when networking technologies change various aspects of data types as messages are passed between networks.
Throughout this chapter, you will learn about the pillars of information security and how they are used within any organization, be it large or small, to create a secure network designed to protect its users, devices, and data. Furthermore, you will learn about various security deployments, key security terminologies, and access control models. These key topics will help you understand what is needed and expected from a cybersecurity and information security professional within the industry. In the chapter, you will learn about various types of Security Operation Centers (SOCs) and the challenges security analysts face when network technologies affect data types on a network. Hackers will not wait for cybersecurity professionals to be ahead of the game – it is our responsibility to stay up to date and ahead of the bad guys.
In this chapter, we will cover the following topics:
- Understanding a security operation center
- Understanding the security tools used to inspect data types on a network
- Understanding the impact of data visibility through networking technologies
- Understanding how threat actors transport malicious code
- Delving into data types used during security monitoring
Technical requirements
To follow along with the exercises in this chapter, please ensure that you have met the following hardware and software requirements:
- Oracle VirtualBox 6.1.16: https://www.virtualbox.org/wiki/Downloads
- Kali Linux 2020.3: https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/
Link for Code in Action video https://bit.ly/3tXoOLS
Understanding a security operation center
In very large organizations such as an Internet Service Provider (ISP), you will often find a Network Operation Center (NOC). The NOC is responsible for monitoring the day-to-day network operations, performance, and services of a corporate network on a 24/7 basis. Even in large private organizations, there is usually an NOC that monitors the network to ensure everything is working as expected and to resolve any network outages, and to perform maintenance and upgrades. As more cyber attacks are occurring every day, the need for a dedicated team of persons with a specialized skill set to help safeguard and fight against cyber attacks is now ever-increasing. This is where the need for an SOC comes in to help us. An SOC is a type of operation center that is designed to monitor all security events on an enterprise network and remediate any threats.
An SOC can be implemented as an in-house solution or outsourced to a Managed Security Service Provider (MSSP). Many security companies, such as Cisco and IBM, have their own SOC, which sells their services and solutions to customers who are interested in having a dedicated team of persons to proactively monitor and manage the security posture of their networks. Even some ISPs have a dedicated SOC to monitor both their own network and their customers' networks as well.
An SOC gathers security intelligence from clients' networks to improve their threat monitoring and incident handling procedures. Additionally, an SOC uses the security intelligence that is shared and disclosed to the public community by various organizations. To put it simply, imagine your organization has an in-house SOC that does not use security intelligence from any trusted sources on the internet. If a new threat emerges and invades your organization's network, the SOC analysts and technologies may not detect or even recognize the new threat. This is a bad thing. It's important that each SOC uses security intelligence from trusted sources in addition to its own information learned from clients' networks. As more security intelligence is gathered by an SOC, the team of security analysts and engineers is able to improve the threat detection of newly emerging threats and incident response strategies.
The following diagram shows a representation of sharing security intelligence between multiple trusted sources:
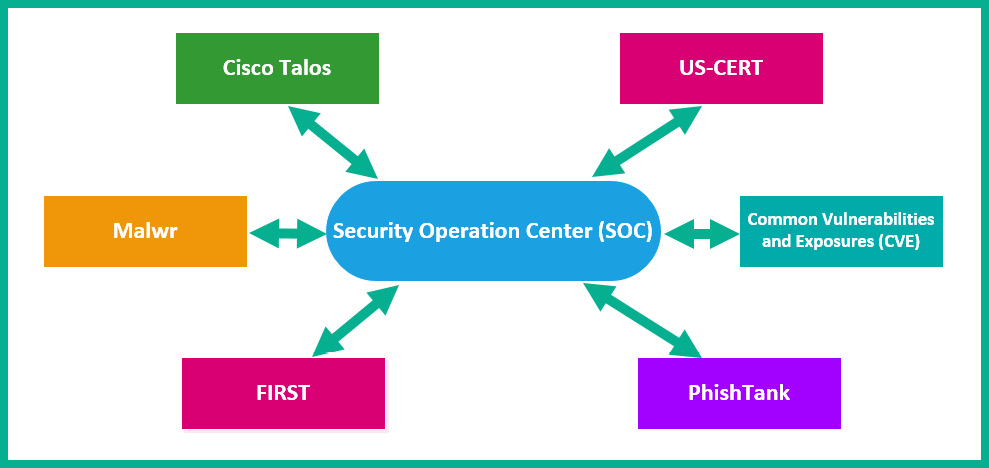
Figure 4.1 – Various security intelligence sources
Let's look at these in detail:
- Cisco Talos is Cisco's global security and threat intelligence team, which gathers security analytics from all of Cisco's security solutions and appliances. They actively hunt for new emerging threats on the internet by using the data sent by Cisco's security products back to Talos. If Talos discovers a never-seen-before threat in the wild, they will execute the threat within a sandbox and perform reverse engineering techniques to determine its intent. Additionally, Talos will push a security update to all their security solutions globally to prevent any outbreaks while sharing the threat intelligence data with others in the cybersecurity community.
Tip
More information on Cisco Talos can be found at https://talosintelligence.com/.
- US-CERT is the United States Computer Emergency Readiness Team. This team is responsible for managing any cyber threats and attacks within the United States. Due to the increasing number of cyber attacks on various countries, each nation is developing and implementing their own national team tasked with preventing, managing, and remediating cyber attacks and threats at a national level for their country. As many nations already have their own national incident response team in place, governments recommend that for each known cyber attack that occurs within their country, whether it occurs within a private or public organization, a report should be made to the national incident response team. Such information helps the national team to understand and gather statistics on the types of cyber attacks, the intent of the malware or threat actor, and even the types of organizations that are the most targeted. Furthermore, the national response team is also responsible for helping other organizations combat cyber attacks and preventing the threat from spreading at a national level.
Important note
More information about US-CERT can be found at https://us-cert.cisa.gov/.
- Malwr is a community that helps cybersecurity professionals in performing dynamic malware analysis. They are also the creators of the well-known malware sandboxing environment known as Cuckoo. Cuckoo is an open source malware analysis sandbox that allows a user to upload malware into the sandbox for dynamic analysis. The sandbox contains many popular tools that a reverse malware engineer will need to disassemble malware and observe its behavior. Using Cuckoo, a security researcher can drop malware into the sandbox and execute it while observing it live.
Important note
More information about Cuckoo can be found at https://cuckoosandbox.org/.
- PhishTank is a community-driven website that focuses on fighting the war against phishing attacks. The website allows anyone to submit a domain or URL that allows the community to validate whether the domain is a trusted or phishing website.
Important note
More information about PhishTank can be found at https://www.phishtank.com/.
- Common Vulnerabilities and Exposures (CVE) is a publicly accessible database that is widely used by many professionals within the field of security. When a security researcher discovers a new vulnerability within an application, system, or network, the researcher will register the vulnerability on the CVE official website. The registration will allow the security researcher to insert all related data about the vulnerability, such as a description and other related references. Once the registration is complete, an official CVE number is assigned. This information can then be shared with the security community. An example is CVE-2017-0144, which describes the types of systems that are affected by the EternalBlue vulnerability. You can visit this URL to learn more about CVE-2017-0144: https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2017-0144.
- FIRST (Forum of Incident Response and Security Teams) is an organization that was created with the intent of helping security researchers and professionals to share information that can help others minimize the impact of a security incident and prevent cyber threats.
Important note
To learn more about FIRST, please visit https://www.first.org/.
Types of SOC
Within the industry, there are three types of SOC. These SOCs share a single goal, which is to monitor and manage the security threats and posture of their clients' networks, although their overall operations differ.
The following are the three different types of SOC:
- A threat-centric SOC
- A compliance-based SOC
- An operation-based SOC
A threat-centric SOC is designed to actively hunt for threats and malicious activities on a network. This team uses various tools and techniques to actively discover any new vulnerabilities that any new and emerging threats may be able to exploit. Additionally, the threat-centric SOC gathers security intelligence about any new threats that have been discovered by another security team and is shared within the cybersecurity community. An example is Cisco's security intelligence team, known as Cisco Talos. They actively monitor the security status of all their security appliances and solutions that are installed by their clients. If one of their security appliances, such as Next-Generation Firewall (NGFW), detects some type of anomaly, the NGFW will send the information to Cisco Talos, where the team will perform further analysis on the potential threat. If the security intelligence team determines the anomaly to be a threat, Cisco Talos will push an update to all their security solutions and appliances globally to combat the threat. This is the benefit of having access to security and threat intelligence.
With a threat-centric SOC, the team can also share their security intelligence with other security organizations. Typically, an SOC should not only depend on the security intelligence created based on the information from a client's network, but also use the intelligence of other trusted security intelligence sources. Sharing information helps other security teams to learn about new threats and attacks discovered by professionals within the industry.
A threat-centric SOC uses the U.S. Department of Energy (DOE) Computer Incident Advisory Capability (CIAC) model, now known as the Department of Energy Integrated Joint Cybersecurity Coordination Center (JC3-CIRC). This model is made up of the following six phases of security incident response:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons learned
In Part 4: Security Policies and Procedures of this book, we will take a deep dive into discussing each phase of incident response and procedures. You will also learn how to deal with security incidents and implement a proper incident response plan within your organization.
Important note
The NIST SP800-61 Revision 2 guide, Computer Security Incident Handling Guide, is recommended for developing incident response strategies and handling procedures.
A compliance-based SOC operates a bit differently compared to a threat-centric unit. This type of SOC proactively monitors the security posture of its clients' networks by ensuring that compliance is met on systems and the networks. With compliance being the primary method of ensuring security, compliance simply means that a system, network, or organization has met the minimum requirements of a set of rules, policies, or standards. An example of compliance is the Health Insurance Portability and Accountability Act (HIPAA), which is a standard that all healthcare providers need to implement to ensure that their systems and networks are secure so as to prevent any leakage of Protected Health Information (PHI). In some countries, it is required by law that various organizations are compliant within their operating industry, especially when data has to be protected. A compliance-based SOC focuses on ensuring that its clients' systems and networks are compliant depending on the clients' work industry.
This allows the SOC to quickly detect any unauthorized changes to the network and identify misconfigurations, which can eventually lead to a cyber attack. Many cyber attacks are the result of misconfigurations on devices. Imagine if a network engineer forgot to disable the Telnet remote access protocol on an internet-connected router for a large organization. A threat actor could perform a port scan on the company's router, determine whether Telnet is enabled, and attempt to remotely access the device without permission. During my time in the networking industry, I've seen many devices within various organizations containing misconfigurations that have resulted in cyber attacks. A compliance-based SOC may not be as focused on threat hunting as we may want, but ensuring each system on its customers' networks is compliant simply reduces the possibility of cyber attacks.
An operation-based SOC is usually an in-house team for a single organization. This type of SOC primarily focuses on monitoring the entire security posture of the internal network only. Many organizations build their own internal SOC as they realize there is a need for dedicated staff with cybersecurity training and certifications. In this type of SOC, you will find persons who specialize in incident response and threat management. Such persons are needed as an outbreak may happen on the company's network at any time. It's important to quickly contain it before it spreads and infects/compromises other systems on the network. If a Computer Emergency Response Team (CERT) does not exist within an organization, should an outbreak occur, the damage will be extreme.
In the next section, you will learn about the building blocks and workflow that an SOC uses to ensure that the team can efficiently and effectively detect and stop cyber threats.
Elements of an SOC
Building an SOC requires a very well-formulated structure that contains the right persons, technologies, and processes that can all work together to proactively detect, mitigate, and remediate cyber attacks and threats. Each day, hackers are discovering new ways to compromise their targets, and cybersecurity professionals are required to stay one step ahead of threat actors. It's important when building an SOC that you have all the right building blocks to ensure the unit is efficient and very effective in defending against the cyber threats of tomorrow.
The following are common metrics that an SOC uses to measure its performance:
- Dwell Time: This is the length of time for which an attacker has gained access to a system/network until their actions are detected and block.
- Mean Time to Detect: This is the average time a security analyst within an SOC takes to identify and validate whether an intrusion (security incident) has occurred on a system or network.
- Mean Time to Respond: This is the average time a security professional within an SOC takes to stop and remediate an intrusion.
- Mean Time to Contain: This is the average time a security professional within an SOC takes to stop an intrusion (security incident) from causing damage to data and other systems on the network.
- Time to Control: This is the time that is required by a security professional within an SOC to stop a malware attack on the network
The following are the essential building blocks and elements of an SOC:
- People
- Processes
- Technologies
Let's look at each of them in detail.
People
According to ISO 20000, which focuses on IT service management, it is essential that the Information Technology (IT) department has sufficient persons with the right qualifications and skill set to ensure that the entire team is very effective and efficient in its daily duties so as to guarantee that business objectives are met in terms of using IT resources and services. Similarly, in an SOC, it's important that the team is made up of various persons with the right cybersecurity training, qualifications, and skill set to ensure that the entire SOC is proactive in defending against threats.
An SOC should contain the following job roles:
- Security analyst
- Security engineer
- Security incident responder
- Security manager
Within an SOC, there are different tiers of security professionals, such as tier 1, tier 2, and tier 3. Each tier within an operation center has a unique job role and function. If tier-1 personnel are unable to resolve an issue, it is escalated to the next level, tier 2, and so on.
The following diagram shows a graphical representation of the SOC:
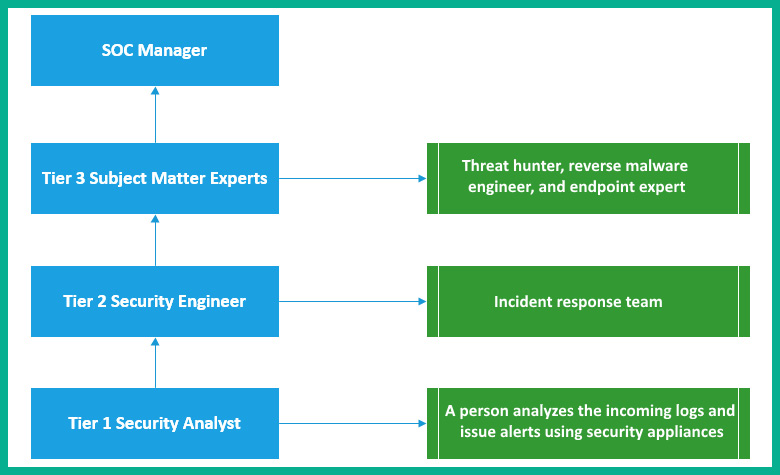
Figure 4.2 – SOC job roles
The first tier within an SOC is commonly referred to as Tier 1 Security Analyst. The tier-1 security analyst is usually the frontline person within the SOC. This person proactively monitors all incoming logs, notifications, and alerts from security systems and appliances on the network. Any incoming alert is verified by the analyst to ensure it is not a false positive. Once an alert has been verified as a true positive, the security analyst will immediately create a ticket with all the necessary information and begin acting on it.
Important note
A false positive is when a security system triggers a false alert for a threat that does not exist. A true positive is when a security system triggers an alert when a threat exists on the system.
The second tier within an SOC is commonly referred to as Tier 2 Security Engineer or Tier 2 Incident Responder. The tier-2 professional is responsible for implementing changes on security solutions and appliances, implementing security updates to systems, configuring and administering endpoint solutions, and even performing incident response for any outbreak on the network.
At tier 3, you will have experts who are experts in reverse malware engineering, threat hunting, computer forensics, firewall configurations, and so on. These professionals are commonly referred to as Tier 3 Subject Matter Experts (SMEs) simply because each person has a unique role within tier 3.
Leading the SOC, you will find the SOC Manager, who is the professional that operates as the point of contact for the SOC and manages all the persons and resources in the entire SOC.
Processes
The processes of an SOC are quite straightforward. To get a better understanding, imagine you are working as a tier-1 security analyst in an SOC for a regional ISP. Your daily duties are to monitor all incoming alerts from various security tools, appliances, and applications on the network. For each alert the SOC receives, the tier-1 team needs to investigate to determine whether it's a false positive. Security solutions and appliances can sometimes generate false alerts for legitimate network traffic and applications on the network. It's important that each alert is not taken lightly.
If the tier-1 security analyst determines that a threat does exist, a ticket is created containing all the necessary information for tracking the security incident. If the tier-1 security analyst is unable to resolve the security incident, the ticket is escalated to tier 2 for further analysis and investigation. If the tier-2 team is unable to resolve the incident, it is escalated to the experts within the SOC, the tier-3 SMEs, who will have the necessary tools, technologies, and skill set to resolve the issues and close the ticket.
Technologies
Without technologies within an SOC or in any organization unit, it would be quite challenging to perform many tasks. An SOC uses a wide range of tools and technologies that help to monitor and detect threats as they happen on the network. An essential tool every SOC needs is a Security Information and Event Management System (SIEM).
An SIEM is used to collect and filter large amounts of data and alerts for security professionals. Imagine that an SOC is receiving hundreds or even thousands of alerts on an average day; the tier-1 security analyst would be extremely overwhelmed, checking each security application and device individually. Implementing an SIEM helps security professionals to improve on the time taken to detect and analyze threats while managing their resources to implement any mitigation and remediation solutions. Keep in mind that an SIEM does not stop a cyber threat or an attack; all it does is process large amounts of incoming logs and alerts for security devices on the network, and indicate which logs a tier-1 security analyst needs to investigate.
An SOC uses a wide range of security tools, which allows security professionals to perform various tasks to help detect, investigate, and resolve security incidents.
The following are examples of categories of tools and technologies that are required within an SOC:
- Vulnerability assessment and management tools
- Threat intelligence tools
- Security monitoring tools
- Network mapping tools
- Event correlation and analysis tools
- Endpoint management tools
- Network traffic analysis tools
The following diagram shows how alerts and logs are fed into an SIEM appliance:
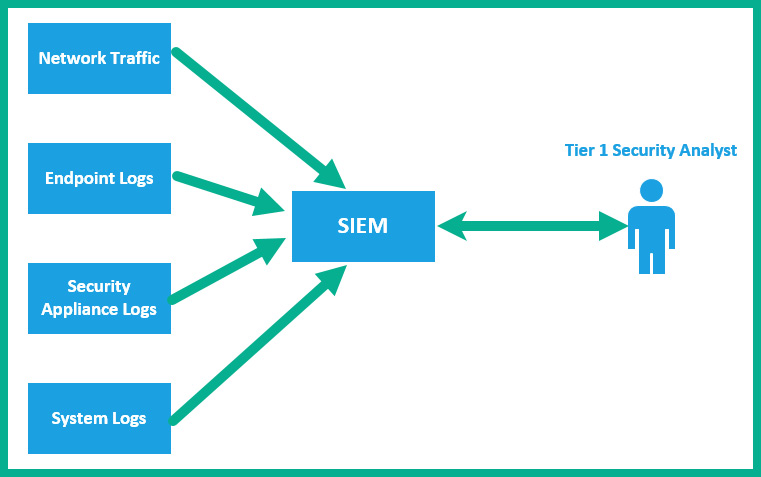
Figure 4.3 – Implementation of an SIEM
As shown in the preceding diagram, notice that all the logs from various systems are being sent to the SIEM for event correlation and analysis. The tier-1 security analyst will proactively monitor the alerts from the SIEM for any security incidents. Implementing an SIEM to help with security logging and incident monitoring saves a lot of time, especially having an SIEM provide a single pane of glass that allows security analysts to observe security incidents that may occur in real time on the network.
By completing this section, you have learned about the importance of building a dedicated team of security professionals to help defend your network from threat actors.
Understanding the security tools used to inspect data types on a network
In this section, you will discover various data types on a network and the importance of using various security tools to help you identify and track applications and data types on a network.
Attack surface and vulnerability
Many security teams are working continuously to reduce the likelihood or risk of being a victim of a cyber attack or experiencing a threat outbreak on their internal network; the key is to reduce the attack surface. The attack surface is defined as the total points on a system or network at which a threat actor could gain unauthorized access to steal data. To put it simply, reducing the attack surface within an organization reduces the number of security weaknesses (vulnerabilities), and therefore reduces the likelihood of a cyber attack.
To reduce the attack surface, security professionals need to quickly and continuously search for vulnerabilities on their networks and implement remediation actions and security controls where necessary. Security professionals use both free and commercial tools to help them discover and remediate vulnerabilities and vulnerability management.
The following are some popular tools for vulnerability management:
- Tenable.io
- Nexpose
- Qualys Vulnerability Management
- Tripwire IP360
A security professional can centrally deploy these vulnerability management tools on their network to manage the vulnerabilities within their entire organization with pre-configured templates and automated scanning with reporting. Once a vulnerability has been discovered, the tool will provide recommended actions and next steps, such as how to remediate the vulnerability and whether any security controls should be implemented.
The following screenshot shows an example of a Nessus report regarding a vulnerability on a target system:
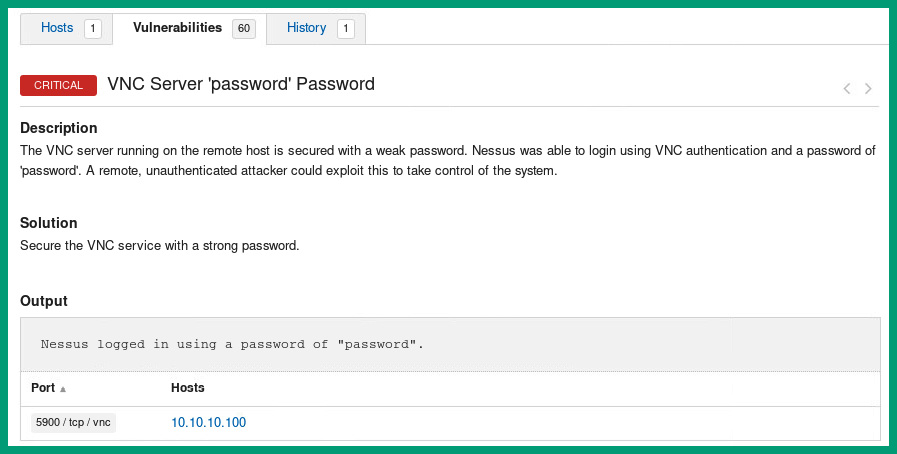
Figure 4.4 – Nessus output
Nessus is one of the most popular vulnerability scanners within the industry and is widely used by security professionals. In the previous screenshot, Nessus was able to discover a CRITICAL vulnerability, and provide a description and solution to remediate the vulnerability to reduce the attack surface on the target system.
tcpdump
tcpdump is a command-line interface tool that is used to capture packets on a network. It is a very powerful and popular network protocol analyzer. It has similar capabilities as Wireshark, which allows tcpdump to display in-depth details about each packet and its contents.
Lab – Using tcpdump to capture network traffic
In this lab, you will learn how to get started using tcpdump to capture packets on a network for traffic analysis. To get started with this exercise, please observe the following instructions:
- Download and install VirtualBox on your computer. You can download VirtualBox from the official website at https://www.virtualbox.org/wiki/Downloads.
- Download the Kali Linux VirtualBox image from https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/.
- Right-click on the Kali Linux virtual image and choose Open with | VirtualBox Manager, as shown here:
Figure 4.5 – Opening the virtual file using VirtualBox
- The VirtualBox import wizard will open. Simply click Import to begin importing the virtual image into VirtualBox, shown as follows:

Figure 4.6 – Importing a virtual machine into VirtualBox
- Once the importing process is complete, click on Settings, shown as follows:
Figure 4.7 – Accessing the settings for the virtual machine
- Next, click on Network and attach Adapter 1 to NAT, shown as follows:

Figure 4.8 – Enabling internet access on a virtual machine
Click OK to save the settings for the Kali Linux virtual machine.
- Now start the Kali Linux virtual machine and log in with kali as both the username and password, shown as follows:

Figure 4.9 – Kali Linux logo prompt
- Open the Linux Terminal. The following screenshot shows how to easily locate it on the Kali Linux interface:

Figure 4.10 – Locating the Linux Terminal on Kali Linux
- Next, let's verify our Ethernet interface ID by using the sudo ifconfig command. Kali Linux will ask you to verify your identity. Simply use kali as the password, as shown in the following snippet:

Figure 4.11 – Verifying interfaces on Kali Linux
Our Ethernet interface has been identified as eth0 and has a private IPv4 address. This address is NATed via VirtualBox to the physical network interface card (NIC) on the computer for internet access.
- Let's now test the internet connectivity using the command ping 8.8.8.8 –c 4, shown as follows:

Figure 4.12 – Testing internet connectivity
As expected, the Kali Linux virtual machine has internet access because we are able to ping Google's public DNS server.
- Next, let's use tcpdump to capture traffic that is leaving our Kali Linux machine with a destination of port 443 for web servers that are using the HTTPS protocol. Use the following command to allow tcpdump to capture network traffic on the eth0 interface:
sudo tcpdump -i eth0 -nn -s0 -v port 443 -w /home/kali/Desktop/tcpdump_capture.pcap
Ensure that you open your web browser and browse to a few websites to generate traffic. The –nn syntax informs tcpdump to not resolve hostnames or port numbers. The –s0 syntax will allow TCP to capture packets of any size. The –v simply implies making the output verbose, the port syntax allows you to specify a port filter, and the –w command will allow tcpdump to write the contents to an offline file for later analysis:
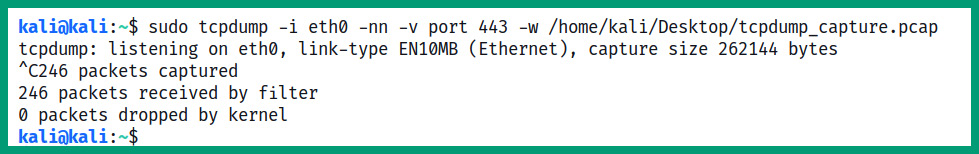
Figure 4.13 – Writing tcpdump data to an offline file
When tcpdump is capturing network traffic and writing to an offline file, it will not display the live traffic in the Terminal window. You will notice the packet count increase as more traffic is captured based on the filter. To stop the capture, press Ctrl + C on your keyboard.
- Next, we can use the command sudo tcpdump -r /home/kali/Desktop/tcpdump_capture.pcap to read and display the contents of the tcpdump_capture.pcap file, shown as follows:

Figure 4.14 – Reading a packet capture using tcpdump
Each unique flow within a packet capture can be easily identified using a 5-tuple, which consists of the same source and destination IP address, source and destination port numbers, and layer 3 protocol.
- Let's use Wireshark to provide a better presentation of the packet capture. To open Wireshark, click on the Kali icon in the top-left corner, and then 09 – Sniffing & Spoofing | wireshark, shown as follows:

Figure 4.15 – Opening Wireshark on Kali Linux
You may be prompted to authenticate your identity on Kali Linux when opening Wireshark. Ensure that you use kali as the password.
- Once Wireshark is opened, click File |Open | Look in: / > home | kali | Desktop | tcpdump_capture.pcap to load the file. The following shows an example of the packet capture loaded in Wireshark:
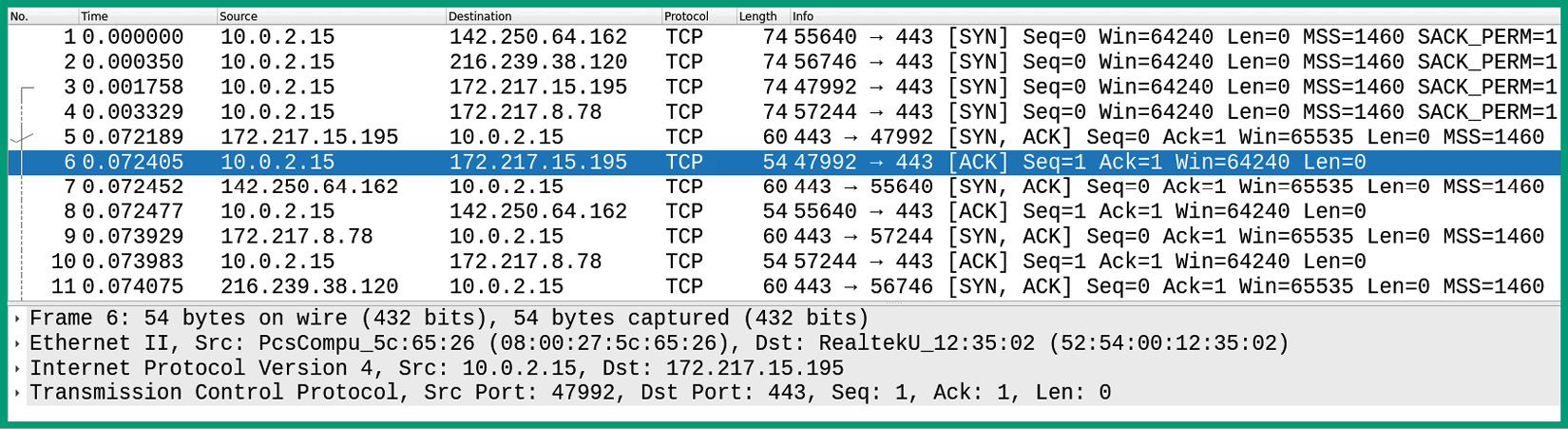
Figure 4.16 – Packet capture in Wireshark
Notice how Wireshark presents the data in an easily readable format. Each line represents a unique flow on the network. Each flow contains a source and destination IP address, source and destination port, and a layer 3 protocol. Simply by clicking on a flow, Wireshark provides in-depth details about each packet in its lower pane.
Important note
To learn more about the capabilities of tcpdump, you can view the man page for it on Kali Linux by using the man tcpdump command.
Having completed this exercise, you have learned how to perform a packet capture using tcpdump and how to use Wireshark to help with offline analysis.
NetFlow
NetFlow is both a protocol and framework that was created by Cisco. NetFlow allows network and security professionals to gather session data from network and security devices. Such data allows professionals to determine the various data types moving across a corporate network and provides accountability for network traffic.
Network engineers can use this data for the following purposes:
- Networking troubleshooting
- Networking planning
- Monitoring security threats and attacks
- Network monitoring for performance
However, NetFlow is not designed to capture the entire packet contents like a full packet capture. Rather, it captures information based on the flow of traffic. NetFlow uses the following elements to identify a unidirectional flow of traffic from a sender to a destination:
- Source IP address
- Destination IP address
- Source port number
- Destination port number
- Layer 3 protocol
- Class of service (CoS)
- Device interface
Important note
The 5-tuple is used to identify a unicast flow of traffic. The 5-tuple consists of a source IP address, destination IP address, source port, destination port, and layer 3 protocol.
In other words, NetFlow captures data about the actual data; it captures metadata about the flow of traffic. All messages, such as packets, have the same flow elements – the source and destination IP address, source and destination port numbers, layer 3 protocol, CoS, and device interface ID are all grouped into a single flow on a NetFlow capture.
Application visibility and control
As an up-and-coming cybersecurity professional, it is important that you understand which tools are able to provide you with in-depth details of applications that are using the network and the type of traffic that is being transported by various network services. Cisco created Next-Generation Network-Based Application Recognition (NBAR2), which allows a network and/or security engineer to easily discover and classify various types of applications that are using a network. NBAR2 is integrated into the Cisco Application Visibility and Control (AVC) system, which uses a combination of technologies and techniques to detect and analyze network-based applications. The AVC is useful for identifying P2P traffic, voice and video traffic, email and web-based traffic, and even file-sharing traffic types on the network.
Using Cisco AVC, you will be able to see exactly the type of traffic that is consuming your network and the most frequently used types of applications as well. Additionally, the Cisco Prime solution can be integrated within the network to provide network management and reporting for network professionals.
Web content filtering
Cisco Web Security Appliance (WSA) is used to filter both inbound and outbound web traffic to protect employees on an enterprise network. WSA inspects the content of HTTP and HTTPS traffic to ensure that threat actors do not encode malicious code such as exploits within web-based traffic. WSA generates logs for each transaction that occurs between a client and web server. These logs can be customized to include specific details for security engineers.
Email content filtering
Similar to Cisco WSA, Cisco Email Security Appliance (ESA) inspects both inbound and outbound email-based traffic. Cisco ESA can create log messages based on malware detection, the delivery of messages, whitelist and/or blacklist policies, and even the operating system of the appliance itself.
Having completed this section, you have learned how various security tools are used to inspect various data types of traffic on a network. In the next section, you will discover how networking technologies impact data visibility by changing the content of data as it passes through a network.
Understanding the impact of data visibility through networking technologies
In this section, you will learn how networking technologies and various IP services can affect data visibility. As traffic is transported between one device and another, there are many network protocols that help to deliver a message from a source to a destination. Some of these technologies modify the contents of the original message that was created by the sender and, due to the change of content, such as source IP address or even using encryption, can create a challenge for security professionals to determine the true source and destination, as well as the actual data that is being transported through the network.
Access control lists
Routers are used to interconnect two or more different networks. Cisco routers do not just move packets from one network to another; they allow a network security engineer to implement special rules known as access control lists (ACLs). ACLs are used to filter traffic by observing the source and destination IP addresses, source and destination service ports, and the layer 3 protocol. However, ACLs provide very basic security filtering, which means they operate only at layer 3 and layer 4 of the TCP/IP protocol suite and they are not able to see data at the application layer. Since malware and other malicious code are hidden within the application layer, ACLs will not be able to prevent many cyber attacks and threats on a network. Therefore, it is not recommended to depend only on the ACLs on a router to protect your network from attacks and other threats.
To get a better idea of how ACLs work, let's take a look at the following topology:
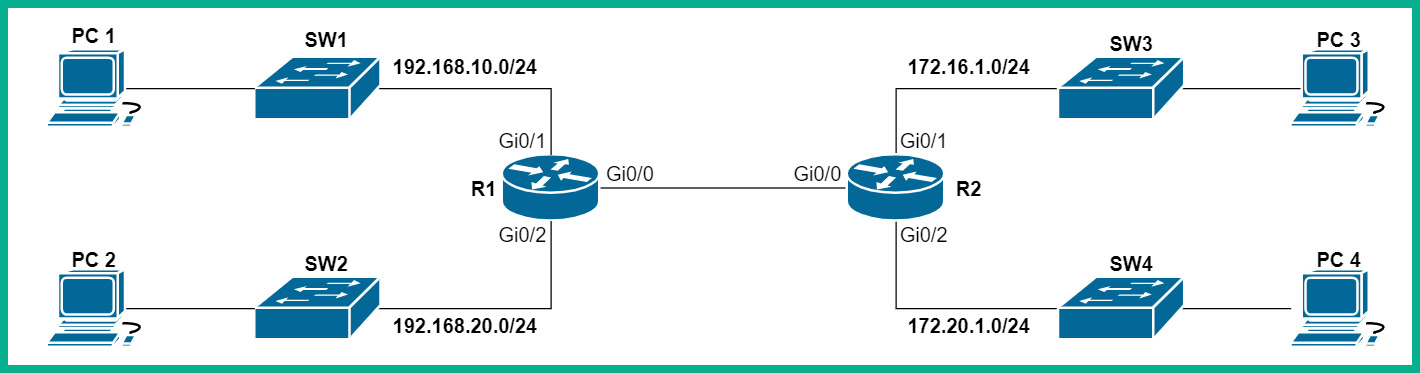
Figure 4.17 – Network topology
On R1, we can restrict ICMP messages originating from the 192.168.10.0/24 network to any destination simply by implementing the following ACL rule on the router:
R1(config)# access-list 101 deny icmp 192.168.10.0 0.0.0.255 any echo
R1(config)# access-list 101 deny icmp 192.168.10.0 0.0.0.255 any echo-reply
R1(config)# access-list 101 permit ip any any
Additionally, access-list 101 will be assigned to R1's GigabitEthernet 0/1 interface in the inbound direction using the following Cisco commands:
R1(config)#interface GigabitEthernet 0/1
R1(config-if)#ip access-group 101 in
R1(config-if)#exit
Access list 101 will prevent any device on the 192.168.10.0/24 network from sending any ICMP messages to any destination networks, but they will be allowed to send all other traffic types.
The following snippet shows PC1 is unable reach PC2 as the result of using the ACL to filter ICMP messages using the router:
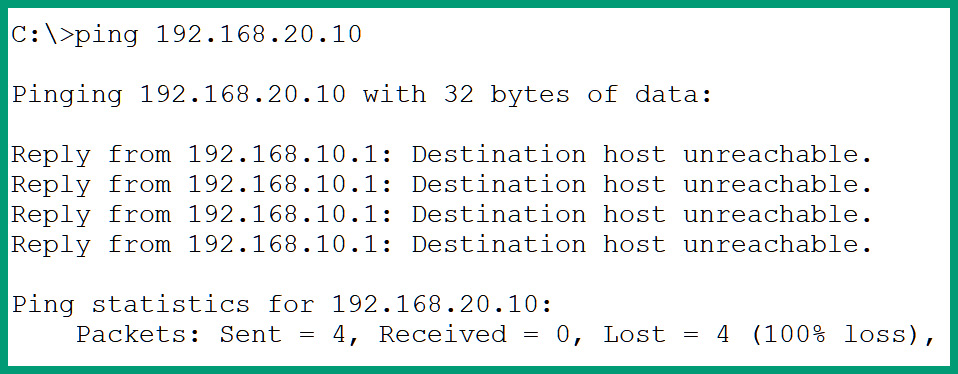
Figure 4.18 – ICMP blocked
Additionally, using the show access-lists command provides us with the statistics of the number of times a rule within the ACL was used to filter traffic. The following snippet shows that the first Access Control Entry (ACE) blocked the 4 ICMP Echo Request messages from entering the router:

Figure 4.19 – Viewing ACLs on a Cisco router
Threat actors use ICMP to create communication channels with their command and control (C2) servers, tunnel other traffic types using ICMP, and perform data exfiltration. Denying ICMP traffic on your network will reduce these types of attacks.
To better secure your network, it's recommended to use the following Cisco security solutions:
- Next-Generation Firewall (NGFW)
- Advanced Malware Protection (AMP)
- Email Security Appliance (ESA)
- Web Security Appliance (WSA)
These devices go beyond the inspection boundaries of ACLs and perform deeper analysis at layer 7, the application layer protocol where malicious code and exploits are hidden.
NAT and PAT
Network Address Translation (NAT) is an IP service on routers that are commonly used to translate one IP address to another. NAT allows a private IPv4 network to communicate with a public IPv4 network such as the internet. Since private IPv4 addresses are non-routable on the internet, NAT allows the router to translate the source private IPv4 address to a source public IPv4 address before the packet is sent out to the internet. This allows all devices on the internet to see the source of the message originating from a public IPv4 host device (router).
The following diagram shows that PC 1 wants to send a message to the Public Server on the internet:

Figure 4.20 – Before NAT translation
PC 1 has a private source IPv4 address of 192.168.1.10, which is non-routable on the internet. This means that PC 1 traffic will not be allowed on the internet. However, the router is connected to the internet and has a public IPv4 address assigned to its GigiabitEthernet 0/0 interface. When the router accepts the packet from PC 1, it will inspect the source and destination IP address. It will then translate the private source address from 192.168.1.10 to 209.65.1.2.
The following diagram shows the source and destination IP addresses after the address translation:

Figure 4.21 – Post NAT translation
When the public server receives the message, it will see the source as 209.65.1.2 and not PC 1. With Port Address Translation (PAT), the router takes advantage of the source and destination service port numbers. PAT allows many private IP addresses to be translated into a single public IP address, as shown in the following diagram:

Figure 4.22 – Observing PAT
As there are many benefits of using NAT and PAT, these two IP services can create a challenge for security professionals when performing security monitoring on traffic on a network. Since multiple IP addresses can be mapped to one or more public IP addresses, this allows an entire private network to be hidden before a single public IP address. With PAT, multiple private IP addresses can be mapped to a single public IP address. This complicates security monitoring a lot more. Therefore, any traffic on the internet or traffic that has been NAT will not allow security engineers to see the true source of the packets.
Tunneling, encapsulation, and encryption
Tunneling allows a user to insert one data type into another. This is one method that attackers use to exfiltrate data and deliver their malicious payload to and from victims' systems without being detected. Imagine an attacker wants to send HTTP messages to a server on the internet, but the perimeter firewall is configured to block all outbound HTTP traffic but allow ICMP messages. The attacker can take the HTTP message and encapsulate it into ICMP messages before sending it through the firewall. Older firewalls do not support Deep Packet Inspection (DPI), which allows newer, next-generation firewalls to inspect data at all layers of the TCP/IP protocol suite.
Therefore, a network with an older firewall will determine the outbound traffic as the ICMP data type and allow the traffic. However, a next-generation firewall with DPI will inspect the application layer of the outbound messages and determine that the data type is really HTTP and not ICMP.
Attackers also use data encryption as a method to conceal their malicious payloads from being detected by a security application. Many security appliances are unable to decrypt messages for further inspection. This method allows a threat actor to evade detection. However, next-generation security appliances have the capabilities to perform SSL decryption, which allows a firewall to decrypt an encrypted packet for further inspection. This allows the firewall to look inside the encrypted data before allowing the traffic to pass.
Unsecure network protocols such as HTTP, SMTP, and even Telnet transport application layer data in plaintext. These protocols create a security concern as users' data could be captured by a threat actor. A security engineer will be able to perform an in-depth inspection of the data being transported by these plaintext protocols. However, if trusted secure protocols such as HTTPS or SSH are used on a network, security monitoring tools will not be able to see the actual data that is being transported, simply because the actual data will be encrypted. NGFWs have a DPI feature that allows the firewall appliances to inspect encrypted packets.
This means that if a threat actor is using a secure protocol to exfiltrate data, or even establish a connection between a compromised system on an internal network on a C2 server, the security team will not be able to see the actual data because it is encapsulated within the trusted secure protocol. Threat actors always think of new and strategic methods to ensure that their exploits and malicious code are not detected by security controls and appliances.
Peer-to-Peer (P2P) and TOR
Peer-to-Peer (P2P) networking allows a host device to share resources directly with another host either on the same network or a remote network. P2P traffic can be found in situations involving file sharing over a network such as the internet or even an internal network. The idea of P2P file sharing is a major concern as a device can host a file while allowing many other devices and unknown users to access the file. A common P2P file-sharing service is Torrent. There are many users on the internet who use various Torrent manager applications to share files with others. A major security concern is the fact that a user can have a file to share over a torrent service and allow multiple unknown users from around the world to establish a connection with the hosting machine. A threat actor can use P2P file-sharing services to distribute malware via this medium to other systems and users without their knowledge.
Additionally, there is P2P networking that uses processor sharing on a host computer. Imagine that a user named Bob decides to visit a website using a standard web browser. For the duration that Bob is on the website, the web server accesses the computing power of the CPU on Bob's computer. This type of P2P networking uses the CPU resource of the user's device to perform very high-level calculations and tasks, such as mining cryptocurrency and performing tasks for scientific research.
Lastly, a P2P network is commonly used for instant messaging (IM) communication. Threat actors can also distribute malware via IM services. Imagine a user's computer has been compromised – a threat actor could send malicious payloads to the victim's contacts. If any person executes (opens) the payload, a backdoor can be created and a reverse connection from the victim to the attacker's machine can be established. Within the industry, there are many IM solutions that provide additional levels of security compared with many other providers. Cisco has its own IM platform known as Cisco Jabber, which provides IM, voice, and video collaboration services for organizations.
Tor is a networking platform that utilizes the infrastructure and protocols on the internet. Tor has seen a lot of popularity from many users and security professionals, as it is known for providing anonymity on the internet. The Tor network is made up of many relay nodes, which route your traffic from one node to another. Therefore, when your traffic exits the last Tor node, the destination device will not be able to trace the true origin of the traffic simply because the traffic was routed to many nodes within the Tor network. Each time your device sends traffic to the Tor network (also known as the onion network), a random path is always chosen to increase the anonymity of the sender's traffic.
The following diagram shows an example of a Tor network:
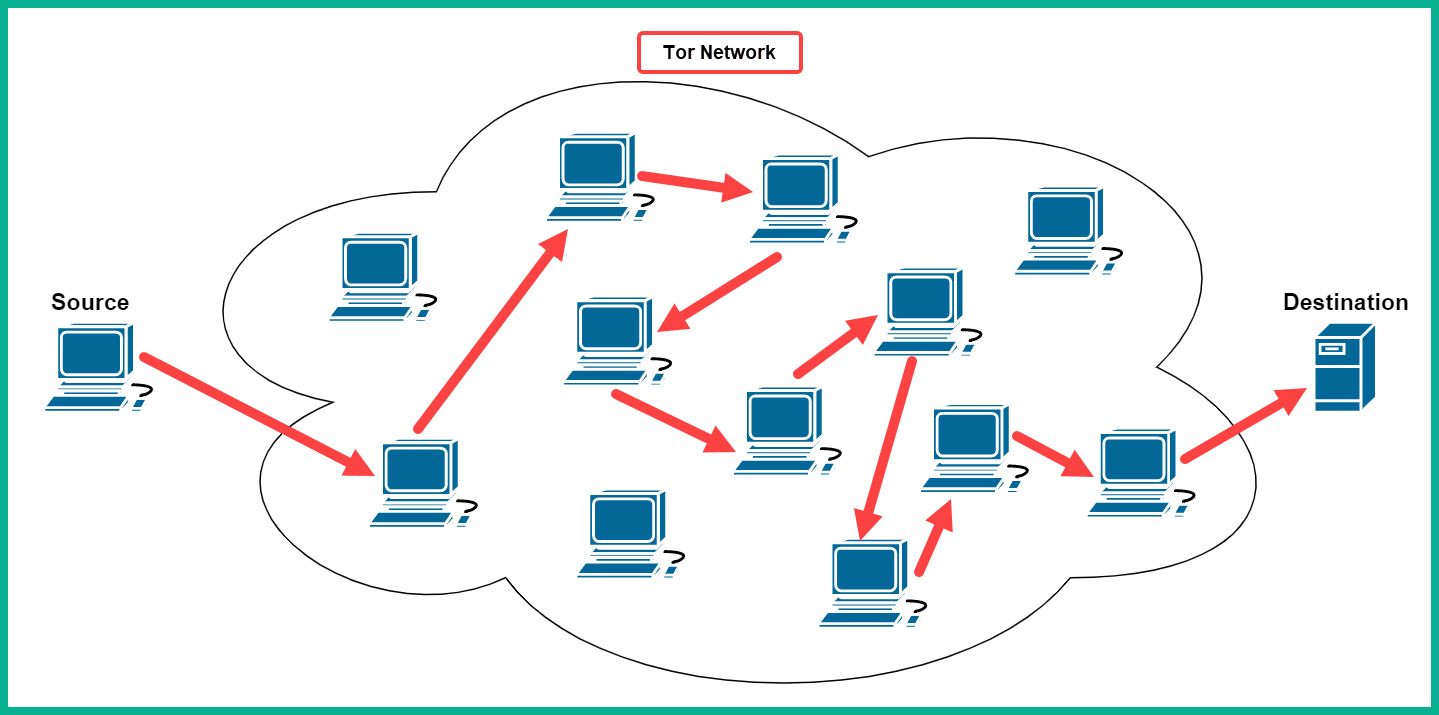
Figure 4.23 – The user's traffic is moving across the Tor network
As shown in the diagram, a user starts the Tor service on their computer and uses the special Tor browser to send traffic to a destination. The Tor service chooses a random node to forward the traffic; each node along the path only knows about the next-hop node and nothing more. Each node will only be able to read the routing information on how to forward the packets to the next device and not the actual contents of the message (data). Keep in mind that the Tor browser establishes an encrypted end-to-end encrypted session across the Tor network. Lastly, when the message reaches the last Tor node within the session, the message is then sent to the final destination.
Tor creates a lot of concerns regarding security within the cybersecurity industry. Threat actors commonly use the Tor service to access the dark web, establish C2 communications, and distribute malware. Security engineers will not be able to see the real source and destination IP addresses and data because traffic routed through Tor is encrypted.
Load balancing
Load balancers are special networking devices that distribute incoming network traffic (load) evenly across multiple servers. Imagine you want to visit the Amazon shopping website. As a typical user, we see a single domain of www.amazon.com and think it's only a single web server that is providing the service to millions of users across the internet. If this were true, Amazon's website server would be continuously flooded with many transactions and would become overwhelmed. Load balancers are implemented on a network when there are redundant resources available, such as multiple web servers hosting the same content. The load balancer will take any incoming load and distribute it between each server without overwhelming them.
The following diagram shows a simple deployment of a load balancer on a network:
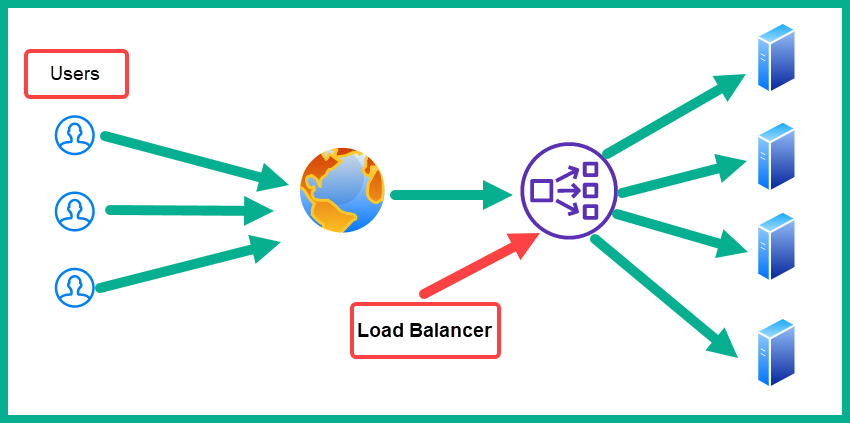
Figure 4.24 – Load balancer on a network
As shown in the diagram, there are multiple users on the internet who are sending their traffic to a destination web server. When the load balancer receives the inbound traffic, it will distribute the traffic to a web server that is currently underutilized rather than sending the load to a server that is overwhelmed.
Load balancers can trigger security alerts on monitoring applications. Some load balancers will send probes to destination servers to determine whether the path is active and the server is online, and the network is at optimal performance before forwarding a sender's traffic to a destination server. Sometimes these probes from load balancing applications can be detected as malicious because threat actors also use probes to determine the statuses of their target devices.
Next-gen IPS event types
Cisco's Next-Generation Intrusion Prevention System (NGIPS) adds an additional layer of security to a network, monitoring, analyzing, and filtering both inbound and outbound traffic. Compared with traditional IPS, the Cisco NGIPS appliance provides additional functionalities that allow the device to inspect packets beyond IP and service ports. The NGIPS security appliance can perform an inspection at the application layer of the TCP/IP, in search of any threats that may be hidden.
The Cisco NGIPS security appliance provides the following features and capabilities:
- Intrusion Prevention System
- Application visibility and control
- URL filtering
- Cisco's Advanced Malware Protection (AMP) and sandboxing
- FirePOWER analytics and automation
- Identity policy control and VPN
With the new line of products from Cisco, NGIPS integrates the Cisco FirePOWER services into its engine to provide additional security features. This service allows NGIPS to provide both reputation- and category-based URL filtering. This feature is useful for security engineers who want to prevent employees of a corporate network from visiting websites and domains that are not suitable for work and may contain malicious content.
The Cisco NGIPS security appliance generates various security events. As an upcoming cybersecurity professional who will be working with IPS appliances, it's important you are aware of the following event types:
- Connection events – These events are generated when a device establishes a session with another device on the network. When a session is detected by NGIPS, it creates a connection log that contains all the information about the session/connection itself. Each connection log will contain essential data, such as date and timestamps, source and destination IP addresses, and any other additional information that can be used to identify the session. Additionally, if an ACL blocks traffic on a router or firewall, the name of the ACL is also inserted within the connection event log on the device. To put it simply, the name of the ACL will also be recorded as part of the connection event as it will help security engineers to determine which ACL denied the traffic.
- Intrusion events – As you have learned already, an IPS proactively monitors and inspects each packet that enters and leaves the network. The IPS searches each packet, checking for any malicious code or exploits that are encapsulated in trusted network protocols. If NGIPS detects a potential threat in a packet, it will create a security event (log) containing the date and timestamp, the type of exploit or malicious code, the source and destination of the packet, and a description. This is known as an intrusion event on the Cisco NGIPS security appliance.
- Host or endpoint events – Cisco NGIPS can detect when system administrators connect a new device to a network. Therefore, when a new or existing device such as a computer is connected to the network, Cisco NGIPS can detect the host and create a log message of the host's information, such as the device's hardware and IP address details.
- Network discovery events – These are logs that have been generated due to a change on the network. Policies are created by security engineers on an NGIPS appliance to collect various types of data about the network for monitoring purposes.
- NetFlow events – NetFlow flow data can be captured on NGIPS, which can later be exported by a security engineer.
By completing this section, you have gained the essential skills to understand how IP services and other networking technologies can affect network traffic and the security monitoring of a network. In the next section, you will learn how threat actors use common network protocols to exfiltrate data.
Understanding how threat actors transport malicious code
In this section, you will learn how threat actors use trusted protocols to help transport their malicious code, such as exploits, across a network and even exfiltrate data without being detected. You will learn how DNS, NTP, HTTP and HTTPS, and email-based traffic can be easily overlooked on a corporate network.
The domain name system
Each day, there are millions of devices that exchange domain name system (DNS) messages between servers on private networks and the internet. The DNS is a network protocol that allows you to resolve a hostname to an IP address. To put it simply, imagine you want to visit Cisco's website at www.cisco.com. Since each device on a network and the internet requires an IP address, you will need the IP address for Cisco's website.
Unfortunately, many people do not know the IP addresses of any of the servers we visit on a daily basis. To save us the trouble, a DNS server is like a huge database repository that contains various DNS entries, such as a hostname to IP address mappings. Our computer will ask a DNS server for the IP address of each hostname that we are attempting to establish a connection with.
Hackers also exploit the lack of security controls, which organizations do not implement to monitor and detect DNS-based cyber attacks. Imagine you're a hacker who has compromised a target organization's network. You are moving around the network and soon discover important files that contain confidential financial records about the organization. One technique you can use to exfiltrate the data by reducing the risk of getting caught is to convert the files into DNS queries and have those DNS queries be sent outside the compromised network to a fake DNS server you own on the internet. Since many companies do not monitor their inbound and outbound DNS traffic, they will think it's regular outbound DNS traffic and not realize an attacker is exfiltrating data by encapsulating it into DNS queries.
Important note
Data is usually converted using a tool such as PacketWhisper. On the DNS server side, the attacker will capture messages using a packet sniffer such as Wireshark and use PacketWhisper once more to reassemble the DNS queries back in the data.
The following snippet shows fake DNS messages that were captured using Wireshark:
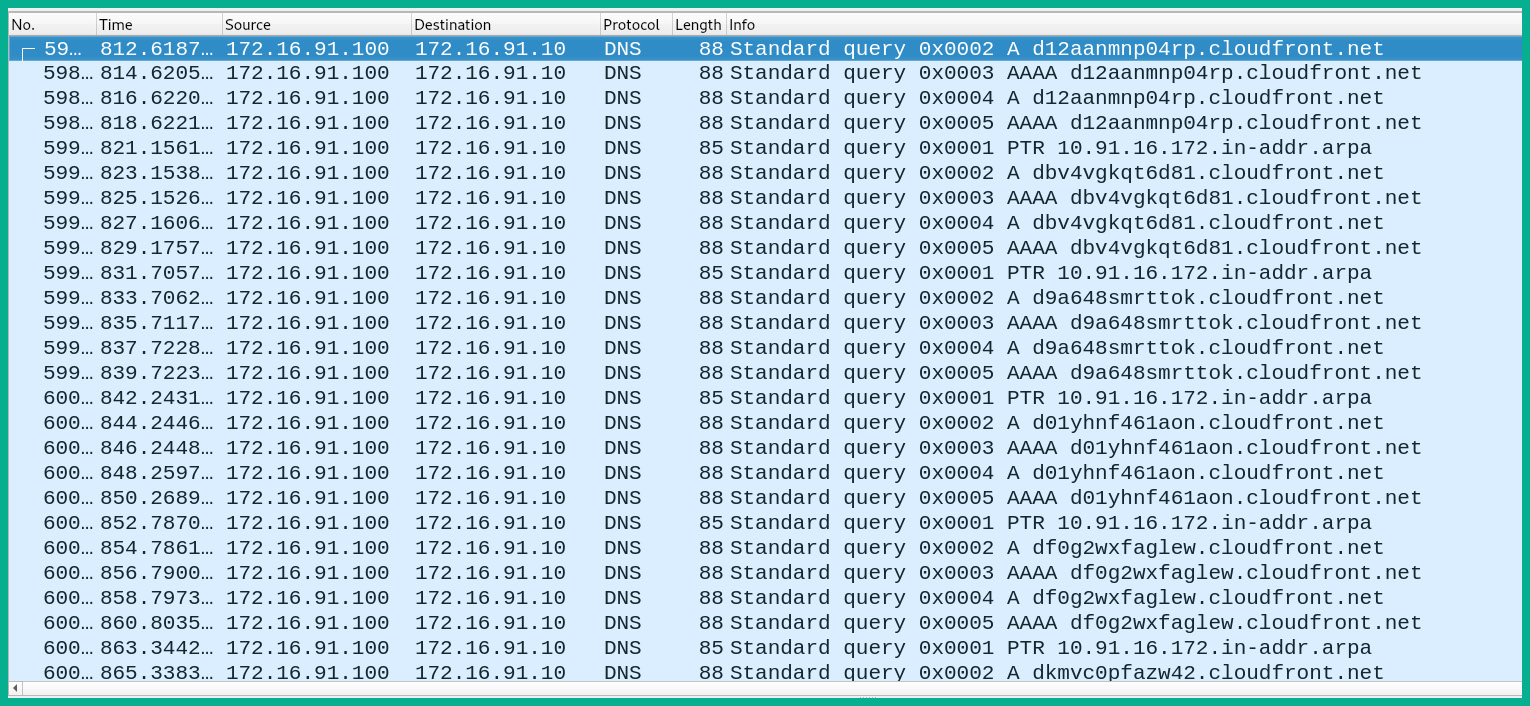
Figure 4.25 – Fake DNS messages
The preceding screenshot shows a Wireshark capture of an attacker exfiltrating data from a compromised device. The victim's computer has an IP address of 172.16.91.100 and the fake server is using an IP address of 172.16.91.10. The attacker converted an Excel spreadsheet file into a DNS message to evade detection by network-based security controls. Notice that each DNS query message contains a randomly generated subdomain from the cloudfront.net parent domain.
There are various types of malware, such as ransomware and botnets, that use the DNS to communicate back to their C2 servers, which are controlled by a threat actor. As a security engineer, it is recommended to implement security controls to protect your DNS traffic for your organization. Cisco Umbrella is a DNS security solution that proactively monitors DNS traffic for any type of DNS-based threats, such as malware, botnets, phishing domains, and C2 traffic.
The Network Time Protocol
The Network Time Protocol (NTP) plays a very simple but important role on a network for both network and security professionals. NTP is primarily used to synchronize time on a network. Imagine you are the network administrator for a large organization with hundreds of devices. Having to manually configure the time on each device would be a very challenging task. Manually configuring time would lead to human error and misconfigurations, and not all devices would have exactly the same time. The accuracy of time on a network is important simply because devices generate syslog messages for every event that occurs on the host device. These events can be system-, network-, and even security-related. As good practice, it's wise to always ensure that syslog messages are configured to include both a date and timestamp with each message. Therefore, it's critical that the time and date on the host device are very accurate.
The following diagram shows an example of how syslog messages are sent over a network:

Figure 4.26 – Syslog messages over a network
As shown in the preceding diagram, events occur often on a network, and when they do, network and security devices generate syslog messages and send them to a log management server where the network administrator or a security analyst can analyze and investigate the cause of the event.
Within the NTP hierarchy, there are different levels of NTP servers that provide the time to other devices on a network. Each level is referred to as a stratum. Each stratum is assigned a number. The lower the number, the closer a stratum level is to the most accurate time source, which is Stratum 0.
The following diagram shows an example of an NTP stratum hierarchy:

Figure 4.27 – NTP hierarchy
As shown in the preceding diagram, the Stratum 0 device is configured with accurate time; the company's router is operating as an NTP client, which allows it to receive the accurate time from Stratum 0. The network administrator also configures the router to operate as an NTP server (Stratum 1) for devices within the internal network.
Important note
NTP uses UDP port 123. This means that any device that is operating as an NTP server will listen on port 123 by default. Syslog is both a protocol and framework for log management and uses UDP port 512 by default.
As a security engineer, when analyzing security incidents and log messages, the log analyzer tool, such as the SIEM appliance, will display the security incidents in sequential order based on the timestamps of each inbound message. Having proper timekeeping helps security engineers and analysts to track the proper chain of events that took place before, during, and after a security incident on a network.
Hackers will attempt to de-synchronize the time on the network and/or take down your NTP server. If time is not synchronized properly during a cyber attack, security engineers will have a bit of a challenge determining the proper sequence of the security incident. Imagine a cyber attack happens, but the log messages have older timestamps. This will confuse the security professionals as to when exactly the attack began and how long it lasted. Security engineers need to ensure that the NTP server is protected from various types of cyber attacks and threats, and even use a secure implementation of NTP, such as NTP with authentication and NTPsec.
Web-based traffic
The Hypertext Transfer Protocol (HTTP) allows us to communicate with web servers. HTTP is an essential protocol on a network; without it, browsing websites would be a very difficult task. HTTP is an unsecure protocol that transfers data in plaintext. This means anyone that is between the source and destination of an HTTP connection will be able to view the contents as is. Since HTTP contains this vulnerability within the application, threat actors are able to intercept and modify the contents of HTTP messages between the sender and the recipient. Imagine a user is attempting to log in to their favorite website and the web server is using HTTP. When the user sends their username and password, it is sent in plaintext, and if a threat actor exists between the user's device and the destination web server, the threat actor will be able to capture the user's account details.
Another common attack is where threat actors perform iFrame injection on an existing website. When a threat actor compromises a website or web server, they will insert an iFrame within the website, which allows malicious scripts or malware to be loaded onto a victim's computer without their knowledge as the iFrame is invisible. This allows the malware or malicious script to be downloaded from another domain or website through the iFrame.
Using the more secure version of this protocol, HTTP Secure (HTTPS), prevents threat actors from seeing sensitive details within packets as they are sent across a network. HTTPS encrypts HTTP messages between the client and the web server to provide confidentiality. HTTPS uses Transport Layer Security (TLS) for data encryption between the client device and the web server. However, with data encryption on HTTPS, security monitoring solutions tend to have a difficult time monitoring security. Since the protocol encrypts messages, security monitoring appliances and applications will not be able to see the actual contents of packets. What if malware is converting data in HTTPS messages and sending it outbound to the threat actor on the internet? How will the security engineer discover the attack? Some security appliances, such as NGFWs, support a feature known as DPI, which allows the security appliance to decrypt the message and observe the contents to determine whether a threat exists before forwarding the message to its destination.
Furthermore, the Web Reputation filtering service found in Cisco's security solutions has the functionality to detect whether a website is attempting to download content to a user's device from an untrusted source. This solution helps prevent cyber attacks that leverage iFrame injections by threat actors.
Email-based traffic
Almost all organizations today exchange emails as it's a lot faster than sending traditional physical mail to someone. The internet and networking protocols have improved the way in which we communicate with each other in many ways. Threat actors also use email-based protocols such as the Simple Mail Transfer Protocol (SMTP), the Post Office Protocol (POP), and the Internet Message Access Protocol (IMAP) to distribute malware and exfiltrate data from their targets' networks and systems.
The SMTP application layer protocol is used to send emails between devices, such as from a client to an email server, and between email servers as well. Similar to DNS, many organizations do not monitor SMTP traffic that leaves their network. Many IT professionals are unaware that threat actors can spread malware and exfiltrate data using SMTP. This is a very common protocol that is overlooked by many organizations.
Additionally, the POP and IMAP email protocols are used to download emails from the email server to an email client on the user's computer. Threat actors also use these protocols to download malware on a victim's computer, so it is important that security controls are in place to monitor any inbound email messages for malware or any signs of a threat.
By completing this section, you have discovered how threat actors use trusted network protocols to distribute malware and establish C2 communication from a corporate network to the internet. In the next section, you will understand the various types of data that are commonly found and investigated during security monitoring by a security analyst.
Delving into data types used during security monitoring
In this section, you will learn about various data types and their characteristics. As an up-and-coming cybersecurity professional, you will be exposed to many security monitoring tools and systems. Understanding how to identify various data types found within network traffic will help you quickly identify any potential threats and flows of traffic. You will learn about session data, transaction data, full packet capture, statistical data, metadata, and alert data.
Session data
Session data is data about a network session that is usually established between two devices either on the same network or remote networks. Session data contains the following elements, which are used to identify the details within the network session:
- Source and destination IP addresses
- Source and destination service ports
- Layer 3 protocol details and code
Bro is an open source security monitoring tool that helps security professionals to identify various session information from various connections on a network.
Transaction data
The actual data that is exchanged during a session is known as transaction data. Both network and security professionals use protocol analyzers and packet capture applications such as tcpdump and Wireshark to capture and view the actual data that is being sent across the network.
The following screenshot is of transaction data captured using Wireshark:

Figure 4.28 – Transaction data
The preceding screenshot shows transaction data that has been exchanged between a client and a web server. The top portion indicates the HTTP data that has been sent from the client to the server, while the lower portion displays the data sent from the server to the client.
Full packet capture
Full packet capture allows a security professional to capture full packets of all network sessions. This type of capture contains session data, transaction data, and everything else that is being transmitted across the network. Since full packet captures contain all data within each packet, the total size of a capture will be very large and will require a lot of storage. One of the major benefits of performing full packet capture is that it allows a security analyst to see the full details of any network conversations.
The following screenshot shows a full packet capture within Wireshark:

Figure 4.29 – Observing a full packet capture in Wireshark
Imagine a user on the network is downloading a malware application from the internet onto their computer. The security analyst can identify the origin of the malicious application, file type, and size. Additionally, if data is being sent across using HTTP, the security analyst can extract the contents of any HTTP full packet capture. This means that the analyst not only sees the network traffic but also has the capabilities to extract individual file types from a live or offline packet capture. Extracting files types that are transmitted across a network allows a security engineer to recover any suspicious files for further malware analysis.
Statistical data
Statistical data is generated from various security applications and appliances that security professionals use to detect anomalies on their networks. Statistical data can also be defined as data about network traffic, except that this data is used to make predictions on network performance and identify whether a cyber attack is occurring on the network.
Security analysts and engineers use network traffic patterns from captured statistical data and compare them with live or current network traffic. This allows the security analyst to determine whether an anomaly exists on the network.
Extracted content (metadata)
To put it simply, metadata is described as data about the actual data. Imagine there's an image file on your hard drive. When you open the file using an image viewer, you see the image. If you right-click on the image and select the properties pane, you will see data pertaining to the object (image file).
Metadata usually consists of the following:
- The name or title of the object
- Information about the creator
- Information regarding modifications
- Who has access and their privileges
- Any tags or descriptions
The following screenshot shows metadata relating to a text file:
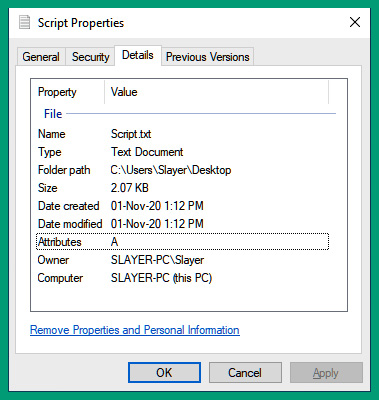
Figure 4.30 – Metadata
As shown in the preceding screenshot, the following metadata can be extracted:
- Name
- Type
- Folder path
- Size
- Date created
- Date modified
- Attributes
- Owner
- Computer
Each of these pieces of data can help a security professional to get an idea of the purpose of the object in the event the object is not recoverable.
Alert data
This type of data is usually generated by a security appliance or application that has detected a security event on the network or system. Systems such as an IPS or Intrusion Detection System (IDS) will generate an alert message once a security violation occurs. The IPS and IDS use various methods of detection, including signature-based and anomaly-based ones. An example of a security event is an IPS detecting malicious traffic such as exploit code being transmitted as network traffic, and the IPS detecting and blocking the threat, and sending an alert to the security analyst.
The following screenshot shows alert data from Snort:

Figure 4.31 – Alert data from an IPS
Snort is an open source Intrusion Detection/Prevention System (IPS/IDS). As shown in the preceding screenshot, we can see the date and timestamps, priority, protocol, the classification of the alert, source and destination IP addresses, source and destination service ports, and a description of each security event. Looking closely at the third entry, we can see that Snort has sent an alert for Potentially Bad Traffic with a source of 172.16.17.248 and a destination of 45.79.85.250. As a security professional, it's important to perform further investigations on this flow of traffic to determine whether a threat is present.
Having completed this section, you have gained knowledge about how to describe various types of data types during security monitoring within cybersecurity operations.
Summary
During the course of this chapter, we have covered a lot of essential topics that every cybersecurity professional will need to know about in their career. You have learned about the need for an SOC and the three types of SOCs and their objectives. We have covered a lot of content on data types and their visibility on a network. You have discovered how networking services and technologies can change the source address of a packet and even how data encryption creates concern in security monitoring. Additionally, you have learned how threat actors use trusted protocols such as email-based protocols to exfiltrate data from corporate networks. It's important that you understand all these topics as they will all play a vital role in your career as a cybersecurity professional.
I hope this chapter has been informative for you and will benefit you on your journey to learning the foundations of cybersecurity operations and acquiring your Cisco Certified CyberOps Associate certification. In the next chapter, you will learn about various cyber threats and techniques that threat actors use to evade detection.
Questions
The following is a short list of review questions to help reinforce your learning and help you identify areas that may require improvement. The answers to the questions can be found in the Assessments section at the end of this book:
- Which of the following SOCs focuses on reducing threats by monitoring the security posture of clients' networks by ensuring that compliance is met on systems and networks?
A) Threat-centric SOC
B) Internal SOC
C) Compliance-based SOC
D) Operation-based SOC
- Which tier of an SOC usually handles incident response?
A) Tier 1
B) Tier 2
C) Tier 3
D) All of the above
- Which of the following tools allows a security professional to detect, analyze, and control network-based applications?
A) Application Visibility and Control (AVC)
B) Next-Generation Network-Based Application Recognition (NBAR2)
C) tcpdump
D) NetFlow
- Which type of IPS event best describes logs that are generated when a security incident occurs?
A) Connection event
B) Host and endpoint event
C) Network discovery event
D) Intrusion event
- Which of the following protocols is used to synchronize time within a network?
A) DHCP
B) DNS
C) NTP
D) IP
- Which data type provides visibility into the actual messages that are exchanged between source and destination hosts?
A) Session data
B) Transaction data
C) Statistical data
D) Alert data
Further reading
The following link is recommended for additional reading:
- Introduction to Cisco IOS NetFlow: https://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/ios-netflow/prod_white_paper0900aecd80406232.html
