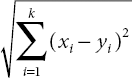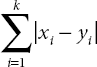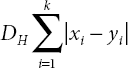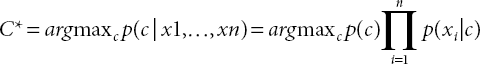2
Machine Learning and Big Data in Cyber-Physical System: Methods, Applications and Challenges
Janmenjoy Nayak1*, P. Suresh Kumar2, Dukka Karun Kumar Reddy2, Bighnaraj Naik3 and Danilo Pelusi4
1Department of Computer Science and Engineering, Aditya Institute of Technology and Management (AITAM), K Kotturu, India
2Dept. of Computer Sc. & Engg., Dr. Lankapalli Bullayya College of Engineering, Visakhapatnam, India
3Dept. of Computer Application, Veer Surendra Sai University of Technology, Burla, India
4University of Teramo, Agostino Campus, Teramo, Italy
Abstract
One of the most considerable and emerging methodologies, defined by the integration of physical and computational processes as cyber-physical systems. These systems are emphasized to supervise the data processing and synchronize it among the cyber computational processes and physically connected systems. Machine learning crafts the intelligent control process by instilling astute self-learning processes with automated and indicative capabilities. The main point of this literature is to give overall survey of cyber-physical system challenges and to accomplish the ideal degree of integration in automation and intelligence in diverse domains for the progress of emerging systems. This chapter aims to provide the advances and challenges for significant research and development of existing and future cyber physical-based technologies using machine learning methods. The research challenges are primarily summarized as i) large-scale data collection, in the integration of systems from IoT, smart cities as well as industries, ii) the synchronization of interconnectivity and intelligence of these frameworks requires a shared perspectives model with decision making, iii) control technique, management service, model-based design, network security, and resource allocation, iv) safety, security, robustness, and reliability is a vital challenge because of errors, security attacks, improbability in the environment, security, and protection of physical systems.
Keywords: IoT, cyber-physical system, machine learning, big-data
2.1 Introduction
Cyber-physical systems (CPS) are physically designed engineered systems, where the operational models are supervised, synchronized, regulated, and incorporated through computing and communication core. Numerous constraints lie ahead on the economically important areas of health-care, aerospace, transportation, agriculture, manufacturing, buildings, defense, and energy. The scheme of design, the architecture building, and the authentication of cyber-physical systems propound numerous technical issues and challenges, which must be taken into consideration by a multi-disciplinary community of educators and researchers [1]. CPS entail enhanced design tools that facilitate design methodology that supports scalability and complexity management. They require cybersecurity to avoid malicious attacks and intrusion detection. CPS is smart, intelligent, and real-time feedback systems, which support validation and verification like assurance, simulation, certification, etc. They are networked and distributed systems possibly through wireless sensing and actuation. In expansion to the challenging constraints of scope, control and scale of CPS give growth to an additional major challenge concerning the confidentiality of the people who make use of the systems [2].
The increasing complexity of IoT networks also focuses on the security problems confronted by such networks. The rise of IoT network complexity is due to too many devices are interconnected with each other through the internet at the side with enormous data originated by these devices. At the side, the development of IoT, novel security issues arise while conventional security issues become more severe. The major reasons are the heterogeneity and the substantially large scale of the objects [3]. As the threats on IoT devices are flattering in a common fashion and the security metrics are based on the developemental aspects of software as well as network, so the hackers can expand control and transmit out malicious activities and attack other devices close to the compromised systems or nodes [4]. Due to the natural significance of its low-power and low-memory nature of these devices, these devices do not comprise of malware protection or virus protection software. The inexistence of malware and virus defense system in IoT devices make them extremely vulnerable to turn into bots and bring out the malicious movement to other devices in the network. When an IoT device is hacked, the invader will be capable of taking control on forwarding and routing operations of the hijacked device. In accumulation to various other devices in the network by attacking, the attackers preserve the gain to access, for sensitive information transmitted and collected by the IoT devices. This absence of integrity, confidentiality, and security of data in IoT has the impending nature to disrupt the pervasive implementation of this technology. These technological constraints are typically correlated to wireless technologies, energy, scalability, and distributed in nature. At the same time, security hurdles require the capability to make sure by confidentiality, authentication, integrity, end-to-end security, etc.
The advancement and operational lifecycle of all IoT hubs and devices must enforce the complete security in all aspect. The distributed system has exceptional factors of threat for devices. The existing distributed systems offer considerable opportunities for the introduction of malicious or insecure software. They have the capacity for browsing and hacking. Indeed distributed systems are proposed to sustain a medium or low area of risk in business, but still, need to be cautious today and not to put down unprotected. These attacks do not imperil data integrity but lead to expensive and inconvenient. So, the critical characteristic nature of these applications performed in real-time existing systems and security for distributed systems is an inherent requirement [4].
The main contribution of this chapter are:
- A brief overview to the CPS mechanism with the integration of physical processes, computation, and networking.
- Importance of Human-in-the-loop connected to CPS, with emphasis on the functionality of human in cooperation with CPS.
- Analytical study about the research of decision making through machine learning (ML) algorithms applied in CPS and other research works of CPS related to IoT and Big-data through computational methods and frameworks for sensing, processing, and storage of substantial amount of data.
- Understanding the technology possesses of CPS in various application fields.
This paper is structured as follows: Section 2.2 elaborates the CPS architecture with its components. Section 2.3 provides a brief human-in-loop cyber-physical systems description. Sections 2.4, 2.5, and 2.6 discusses a brief study of major-related research in the area of ML Section 2.7 summarizes the critical analysis with analyzing the impact of ML and big data approaches in CPS. Section 2.8 illustrates the conclusion with future concerns.
2.2 Cyber-Physical System Architecture
CPS is a promising and exploring area which deals with the integration and overlapping of numerous fields of science and technology. The architectural design of CPS as shown in Figure 2.1. The operations of engineered and physical systems are integrated, coordinated, controlled, monitored by a communication and computing system. CPS comprises the communication by a set of networked agents with the physical world. The network agents incorporate devices like actuators, sensors, communication devices, and control processing units.
The CPS interacts through networks of a physical system with wireless sensors intelligently composed and embedded computing systems with securely coupled. The collective intelligence system functions to coordinate for knowledge integration and data pre-processing across heterogeneous, multidisciplinary domains of sensors. The real-time systems feedback control is held by the computation process with support to different time scale asynchronous event processing. In the architecture of computation and controller, the computation process is used to hold feedback control of real-time event triggered systems. This suits the asynchronous realtime event dispensation with variation time scale. The architecture of the controller assures the security of cyber networks, through taking apart reliable tasks from unreliable tasks with considerations on the safety and latency. The actuator network is self-possessed with control nodes, which receives control instructions from computation control and sends the instructional control to consequent nodes with a collaborative design of scheduling and feedback control [5].
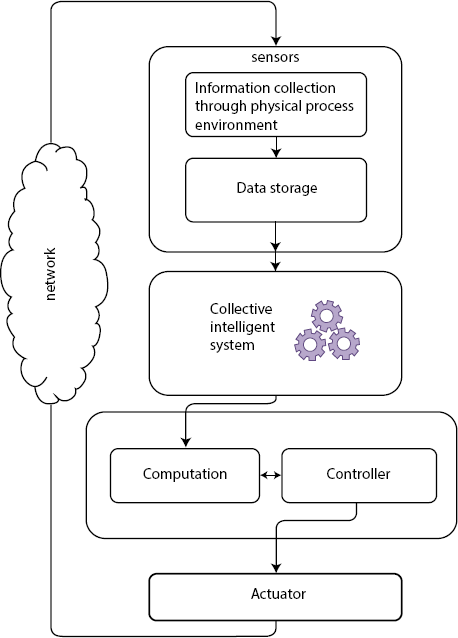
Figure 2.1 Cyber-physical system architecture.
2.3 Human-in-the-Loop Cyber-Physical Systems (HiLCPS)
The rapid technological advancement in embedded systems and communication technologies and the availability of low-cost sensors has to lead to the development of next-generation hardware/software systems called CPS. These systems interact with the physical world to support human–machine interaction. Moreover, the development of HiLCPS consists of more powerful applications with enormous latent for the daily routine of human life. A HiLCPS system (Figure 2.2) consists of some components of real-time security-based activities, the involvement of humans in a loop, cyber-based components (CPS), and the physical environment. With the use of body and brain interface (brain sensors), HiLCPS is can infer the user’s objective for the measurement of cognitive capabilities. The features like control of physical processes by monitoring variables and obtaining broad knowledge of controlled environment using ML to furnish timely and specific decisions have made CPS more popular to meet the requirements of new challenging applications and future smart services. Moreover, the increased use of CPS may result in challenges such as security, performance, stability, reliability, and robustness that could have major consequences on society, economy, and environment. Therefore designing accurate, secure, and efficient CPS in applications such as transportation, energy, medical and healthcare, defense, manufacturing, and agriculture is emerging as an interesting area of research. However, the use of intelligent based methods in security systems or to design a perfect secured system has always been a challenging aspect for the researchers. Also, issues like arbitrary failures and various cyber-attacks in CPS make those more vulnerable. If any sort of unusual activity is detected by the intrusion detector, apposite action needs to be taken for minimizing the risk to harm the system. The unintended activity caused by the random failures or repeated cyber-attacks results smashes up to the physical objects as well the users who are dependent on it. So, protecting CPS from vulnerable attacks and repeated failures has always been an important measure. Various approaches based on rule integration [6, 7], statistics [7, 8], data mining [9, 10] and cryptography [11, 12] are developed to handle the aforementioned problems. However, different limitations [13] such as the requirement of prior knowledge in case of rule integration and statistics based approaches; high complexity in case of data mining based approaches; lesser capability to handle the malicious attacks with legal privileges in case of cryptography-based approaches, give a new direction for the scope of advance research. By using the combination of qualitative and quantitative techniques, ML techniques can find the approximate and efficient solution in an affordable time. Several hybrid ML based approach is developed to provide a unique high-end solution for the large scale CPS, which cannot be achieved by a single method.

Figure 2.2 Integration of ML with HiLCPS.
2.4 Machine Learning Applications in CPS
In this section various ML approaches such as k-nearest neighbors, decision trees, Naïve Bayes, support vector machine, random forest, multilayer perceptron, linear regression, and their studies in the CPS have been studied.
2.4.1 K-Nearest Neighbors (K-NN) in CPS
K-NN is a straight forward supervised ML algorithm classifier. Classification is achieved by identifying the nearest neighbors from the samples. To evaluate a data point in a sample, its neighbor sample points are considered and recurrently ‘K’ number of values may be determined. This is the reason it is named as the K-NN algorithm [14]. There are various methods to calculate the distance between testing and training point such as Euclidian distance, Manhattan distance, and hamming distance (Equations (2.1)–(2.3)). Classification of testing is completely based on the training examples and it is also named as the lazy learning algorithm. Classification purely depends on the value of ‘K’ and different ‘K’ values will produce variation in results.
de Mello and Stemmer [15] investigated K-NN classifier in golden images and some background samples to inspect surface mounted devices. From the investigated results such as confusion matrix, kappa statistics, MAE, RMSE, it proves the features that are related to the histogram is the perfect method to differentiate various components from images. So that it will classify missing, shifting, identify rotation or wrong devices. Table 2.1 shows various studies of CPS using K-NN.
Table 2.1 Various applications in CPS using K-NN.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | Cellular connectivity of CPS | Massive measurement data | KNN, NB, RF | Accuracy | [16] |
| 2 | Cyber-Physical Social Systems | Corpus | NB, KNN, DT, SVM | MAE, RMSE, RAE, RRSE, SSE, SST, D2 | [17] |
| 3 | CIoT-based cyber-physical system | CASIA, TIDE | NB, SVM, LR, J48, KNN | Accuracy, Precision, Recall, F-Measure, ROC | [18] |
| 4 | CPS for Stroke Detection | EEG | KNN, SVM, MLP | Precision, Recall | [19] |
| 5 | CPS of an offshore gas turbine | PI system | MLP, DT, RF, KNN, LR, NB | MAE, RMSE, RAE, Accuracy, Error% | [20] |
| 6 | Attacks in Cyber-Physical Systems | Random Dataset | KNN, ANN, SVM, GNB, DT | Precision, Recall, Accuracy | [21] |
| 7 | CPS in Cyber Manufacturing | Random dataset | RF, KNN | Accuracy | [22] |
| 8 | Detection of Parkinson disease | UCI-Parkinson dataset | CBR, FKNN, RF, RB, J48, SVM, | Error rate, Accuracy, Precision, Sensitivity, Specificity, F-measure | [23] |
| 9 | Medical CPS | Health care datasets | KNN, SVM, NB, DT, Fuzzy | Recall, F-Measure | [24] |
| 10 | Embedded Emotion recognition using CPS | MANHOB, DEAP | KNN | Accuracy, Sensitivity, and Specificity | [25] |
| 11 | Mobile Edge Computing | 10 Datasets | NB, RF, DT, SVM, K-Means, KNN, MLP, RNN, | Accuracy | [26] |
| 12 | An energycyber-physical system | Real-Time dataset | DT, DA, SVM, KNN | Accuracy, Precision, Recall, F1-measure | [27] |
| 13 | Attacks in CPS | MITM, DoS | KNN, DT, RF | TP, TN, FP, FN | [28] |
| 14 | Intrusions Detection in Aerospace | UNSW-NB15, KDDCUP 99, ML-IDS | K-NN, SVM, RF, NB, MLP | Precision, Recall, Accuracy, TP Rate, FP Rate | [14] |
| 15 | Cyber-physical water supply systems | Anomalous dataset | KNN, MNB, BNB, GNB | Accuracy | [29] |
2.4.2 Support Vector Machine (SVM) in CPS
SVM is a non-probabilistic binary classifier that is based on the hyperplane in feature space that will minimize the classification risk compared to optimal classification. This hyperplane is trained to differentiate between two classes and it splits the data in the best possible way. SVM is familiar with its generalizability towards solving real-life problems [14]. The main objective of SVM is to isolate from the set of classes. However, in some cases, it cannot do so because of its non-linearity, and ‘Kernel’ helps to obtain the intended solution. Generally used kernel functions are the sigmoid kernel, Gaussian kernel, linear kernel, and radial basis kernel, etc. [30].
Hossain et al. [18] used a method to verify the authenticity in CIoT. After getting the final image’s feature vector, SVM helps to classify the images as authentic or forged type. To validate the performance of the model they utilized measures such as false-positive rate, true-positive rate, kappa statistics, MAE, RMSE, etc. From the experimented results it is evident that, the performance of their proposed approach is dominative over others. Table 2.2 shows different studies in CPS using SVM.
Table 2.2 Various applications in CPS using SVM.
| S. No. | Application | Dataset | Method | Evalution factor | Ref. |
|---|---|---|---|---|---|
| 1 | Power system disturbence | 15 Datasets | RF, NB, SVM, Jripper, Adaboost | Accuracy, Precision, Recall, F-Measure | [31] |
| 2 | Defending unknown attacks in CPS | VET Zoo | K-means, TF, IDF SVM | TP, FP, Accuracy, Precision, ROC | [32] |
| 3 | Attacks in CPS | SWaT | SVM, RF, DT, NN, NB | TP, FP, Precision, Recall, Accuracy, FA, TTBM | [33] |
| 4 | CPSS | Corpus | NB, KNN, DT, SVM | MAE, RMSE, RAE, RRSE, SSE, SST, D2 | [17] |
| 5 | TOLA based on CPS | Random dataset | SVM, KNN, NB | Accuracy | [34] |
| 6 | Safety risk monitoring of CPPS | event_ warning detail | SVM, NN, MA, AR, GEP, EPABT | MAE, MAPE, MSE, | [35] |
| 7 | Cloud-based Cyber-physical intrusion detection | Random dataset | MLP, RNNLSTM, LR, DT, RF, SVM | Accuracy | [36] |
| 8 | Estimation of a safety Critical CPS | Real Time dataset | ANN-LMBP, DT, SVM, RF | R2, RMSE, Training Time, Testing Speed | [37] |
| 9 | CPS Manufacturing | Dataset with Blackslash Issues | SVM | Accuracy | [38] |
| 10 | On-Chip LiDAR Sensors in CPS | Random dataset | MLP SVM | CCR, ECR, MAE, RMSE, RAE, RRSE | [39] |
| 11 | Automotive CPS | IMU | SVM, NN, RNN, LSTM | Confusion Matrix, Accuracy | [40] |
| 12 | Attacks in Cyber-Physical Systems | Random Dataset | KNN, ANN, SVM, GNB, DT | Precision, Recall, Accuracy | [21] |
| 13 | Cyber-Physical-Social Systems | Dataset from AMAZON | SVM, CCNN, NB | Accuracy | [41] |
| 14 | Industry 4.0 | ABS, bCMS, and TCM | SVM, Naive Bayes,and J48 decision-tree | AUC | [42] |
| 15 | Detection of Parkinson disease | UCI- Parkinson dataset | CBR, FKNN, RF, RB, J48, SVM | Error rate, Accuracy, Precision, Sensitivity, Specificity, F-measure | [23] |
| 16 | Medical CPS | Health care datasets | KNN, SVM, NB, DT, Fuzzy | Recall, F-Measure | [24] |
| 17 | CPS for Thermal stress in 3D Printing | Random dataset | LR, MLP, SVM | MAE, RMSE, R2, MSE | [43] |
| 18 | Image annotation in Cyber-Physical-Social Systems | Corel-5K, IAPR TC-12 | CNN, KSVM | Precision, Recall, F1 measure | [44] |
| 19 | Cyber-Physical Production Systems | Collected data from CPPS | DT, RF, ANN, SVM | Precision, Recall, Accuracy | [45] |
| 20 | CPS for Thermal stress in 3D Printing | Random Dataset | LR, MLP, SVM | MAE, RMSE, R2, MSE | [43] |
| 21 | Resistance Spot Welding (RSW) | RSW Quality | Linear Regression, SVM, MLP, RF | MSE, MAPE | [46] |
| 22 | Mobile Edge Computing | 10 Datasets | NB, RF, DT, SVM,KMeans, KNN, MLP, RNN | Accuracy | [26] |
| 23 | Big Data in Agriculture CPS | IoT Dataset from Luochuan Apple | GA-SVM | MSE | [47] |
| 24 | An energy-cyber-physical system | Real Time dataser | DT, DA, SVM, KNN | Accuracy, Precision, Recall, F1-measure | [27] |
| 25 | Intrusions Detection in Aerospace | UNSW-NB15, KDDCUP 99, ML-IDS | K-NN, SVM, RF, NB, MLP | Precision, Recall, Accuracy, TP Rate, FP Rate | [14] |
2.4.3 Random Forest (RF) in CPS
RF as its name implies, comprises a huge number of decision trees. Decision Trees are considered as building blocks for RF. It provides an algorithm to gauge the missing values in the RF classifier and if trees in the forest are more, then the accuracy can be accurately predicted. A RF is an ensemble approach that is operated by setting up a large number of decision trees at the time of training based on a random subgroup of training examples [33]. It is a combination of various classifiers and every classifier comes up with a vote that is the most frequent class.
Majdani et al. [20] simulated RF in the oil and gas industry especially in the area of predictive maintenance which will be used to forecast remote environmental conditions. Suppleness is achieved by combining a RF with computational intelligence. Table 2.3 represents various studies in CPS using RF.
Table 2.3 Different metrics in RF.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | Power system disturbance | 15 Datasets | Random Forest, Naïve Bayes, SVM, Jripper, Adaboost | Accuracy, Precision, Recall, F-Measure | [31] |
| 2 | Big Data in Cloud Computing Environment | URL Reputation, YouTube Video, Bag of Words, Gas sensor arrays, Patient, Outpatient, Medicine, Cancer | Parallel Random Forest, RF, DRF, Spark-MLRF | OOB Error Rate, Accuracy | [48] |
| 3 | Attacks in CPS | SWaT | SVM, RF, DT, NN, NB | TP, FP, Precision, Recall, Accuracy, FA, TTBM | [33] |
| 4 | CPS maintenance | Industrial dataset | NB, DT, RF, NN | Precision, Recall | [49] |
| 5 | Cloud-based Cyber-physical intrusion detection | Random dataset | MLP, RNNLSTM, LR, DT, RF, SVM | Accuracy | [36] |
| 6 | Estimation of a safety Critical CPS | Real-Time dataset | ANN-LMBP, DT, SVM, RF | R2, RMSE, Training Time, Testing Speed | [37] |
| 7 | CPS in Cyber Manufacturing | Random dataset | RF, KNN | Accuracy | [22] |
| 8 | Detection of Parkinson disease | UCI- Parkinson dataset | CBR, FKNN, RF, RB, J48, SVM | Error rate, Accuracy, Precision, Sensitivity, Specificity, F-measure | [23] |
| 9 | Classification in IoT | Real-Time health care database | RF, Map Reducer | Precision, Recall, F-measure, Sensitivity, Specificity, Accuracy | [50] |
| 10 | Resistance Spot Welding (RSW) | RSW Quality | Linear Regression, SVM, MLP, RF | MSE, MAPE | [46] |
| 11 | Mobile Edge Computing | 10 Datasets | NB, RF, DT, SVM,KMeans, KNN, MLP, RNN | Accuracy | [26] |
| 12 | Bio-Modality Spoofing in Medical CPS | Face, Iris, Fingerprint by Warsaw, Replay-Attack, LiveDet 2015 | RF, CNN | Accuracy, FAR, FRR | [51] |
| 13 | Intrusions Detection in Aerospace | UNSW-NB15, KDDCUP 99, ML-IDS | K-NN, SVM, RF, NB, MLP | Precision, Recall, Accuracy, TP Rate, FP Rate | [14] |
2.4.4 Decision Trees (DT) in CPS
The main precedence to consider DT is its intuitive utterance of knowledge with good accuracy, and ease implementation [14]. In DT, every internal node can be considered as a test to an attribute, the branch can be represented as a result of that test, and the class label is represented by a leaf. Each record is navigated from the root node to leaf and the class label is assigned to it [33]. It uses function at every branch for the availability of the record and popularly used functions are gini index, information gain, and gain ratio. The estimated probability will be less in case the tree grows larger, which affects the number of records in the branches i.e. records will be less. Therefore, pruning is one of the important techniques that will increase the performance of the model [52]. It reduces the complexity of the final classifier, and hence it improves the accuracy by reduction of overfitting. Pruning is classified into two categories such as prepruning and post pruning. In post pruning, the tree will be built first and then branches will be reduced so that the DT level will be reduced. On the other hand, at the time of decision tree building pre pruning is helpful at overfitting.
Bezemskij et al. [53] have developed a method to provide security in small-remote controlled robotic vehicles which will observe the cyberattacks against physical impact. To generate the decision rules, they used decision trees which are evaluated against DoS and command injection attacks. The impact of decision trees in CPS of various studies is illustrated in Table 2.4.
Table 2.4 Various applications in CPS using decision trees.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | CP Intrusion detection on a robotic vehicle | Real-Time dataset | DT C5.0 | Confusion Matrix, Accuracy, FPR, FNR, AUC-ROC | [54] |
| 2 | Mobile Cyber-Physical systems | Real-Time dataset | DT C5.0 | FPR, FNR, Accuracy, AUC-ROC | [55] |
| 3 | Attacks in CPS | SWaT | SVM, RF, DT, NN, NB | TP, FP, Precision, Recall, Accuracy, FA, TTBM | [33] |
| 4 | CPS maintenance | Industrial dataset | NB, DT, RF, NN | Precision, Recall | [49] |
| 5 | Cyber-Physical Social Systems | Corpus | NB, KNN, DT, SVM | MAE, RMSE, RAE, RRSE, SSE, SST, D2 | [17] |
| 6 | CIoT-based cyberphysical system | CASIA, TIDE | NB, SVM, LR, J48, KNN | Accuracy, Precision, Recall, F-Measure, ROC | [18] |
| 7 | Cloud-based Cyberphysical intrusion detection | Random dataset | MLP, RNNLSTM, LR, DT, RF, SVM | Accuracy | [36] |
| 8 | Estimationof a safety Critical CPS | Real-Time dataset | ANN-LMBP, DT, SVM, RF | R2, RMSE, Training Time, Testing Speed | [37] |
| 9 | CPS of an offshore gas turbine | PI system | MLP, DT, RF, KNN, LR, NB | MAE, RMSE, RAE, Accuracy, Error % | [20] |
| 10 | Fog-cloud based cyberphysical system | MBD | J48 DT | Accuracy, Specificity, Precision, Recall, MAE, RMSE, RRSE, RAE | [56] |
| 11 | Attacks in Cyber-Physical Systems | Random Dataset | KNN, ANN, SVM, GNB, DT | Precision, Recall, Accuracy | [21] |
| 12 | Industry 4.0 | ABS, bCMS, and TCM | SVM, Naive Bayes,and J48 decision-tree | AUC | [42] |
| 13 | Medical CPS | Health care datasets | KNN, SVM, NB, DT, Fuzzy | Recall, F-Measure | [24] |
| 14 | Mobile Edge Computing | 10 Datasets | NB, RF, DT, SVM, K-Means, KNN, MLP, RNN, | Accuracy | [26] |
| 15 | An energy-cyber-physical system | Real-Time dataset | DT, DA, SVM, KNN | Accuracy, Precision, Recall, F1-measure | [27] |
| 16 | CP Intrusion detection on a robotic vehicle | Real-Time dataset | DT C5.0 | Confusion Matrix, Accuracy, FPR, FNR, AUC-ROC | [54] |
2.4.5 Linear Regression (LR) in CPS
This is a statistical technique used to evaluate the association between the input variable and output variable i.e. it assumes the relationship among independent and dependent variables that positioned the straight line to the data [57]. The relationship is expressed as a prediction function as in Equation (2.4).
Where x1, x2, x3, …,xn are features and w0, w1, w2, w3, …, wn are weights.
Miao et al. [43] have used linear regression to adjust the settings in nozzle temperature automatically. They investigated the performance of LR, MLP, and SVM and among which, LR outperformed. From the experimental results, it is evident that the CPS reduced the distortion notably. Table 2.5 shows various studies in CPS using LR.
Table 2.5 Different applications in CPS using linear regression.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | CIoT-based cyber physical system | CASIA, TIDE | NB, SVM, LR, J48, KNN | Accuracy, Precision, Recall, F-Measure, ROC | [18] |
| 2 | Cloud based Cyberphysical intrusion detection | Random dataset | MLP, RNNLSTM, LR, DT, RF, SVM | Accuracy | [36] |
| 3 | CPS of an offshore gas turbine | PI system | MLP, DT, RF, KNN, LR, NB | MAE, RMSE, RAE, Accuracy, Error% | [20] |
| 4 | Resistance Spot Welding (RSW) | RSW Quality | Linear Regression, SVM, MLP, RF | MSE, MAPE | [46] |
2.4.6 Multi-Layer Perceptron (MLP) in CPS
MLP is a broad application in ML which is an information processing model inspired by biological nervous systems like a human brain structure. It learns by itself by giving supervised training to meet the requisite complex and non-linear relations, without any pre-model. MLP is composed of several layers, every layer has neurons, which will filter the information many times. These are used to classify the data effectively [14]. Every neuron has a set of input features (xi) and linked weights (wi).
Majdani et al. [20] proposed context-aware CPS through an adaptive multi-tiered framework, which can be utilized for smart data acquisition and data processing, with minimizing the human intervention. The developed component framework is based on MLP with error back-propagation. Compliance is accomplished through the combination of computational intelligence and ML techniques. Table 2.6 represents the studies in CPS using a MLP.
Table 2.6 Various applications in CPS using multi-layer perceptron.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | Inspecting surface mounted devices | Golden Images | ROI Algorithm, KNN, MLP | Confusion matrix, Kappa Statistics, MAE, RMSE | [15] |
| 2 | Attacks in CPS | SWaT | SVM, RF, DT, NN, NB | TP, FP, Precision, Recall, Accuracy, FA, TTBM | [33] |
| 3 | CPS maintenance | Industrial dataset | NB, DT, RF, NN | Precision, Recall | [49] |
| 4 | CP-SRS | real-life data | NN-SLM, NB-SLM | Confusion matrix | [58] |
| 5 | Image Classification for CPS | Random dataset | CNN, GA | Accuracy, Training time, Model extensibility | [59] |
| 6 | Intrusion detection using MCPS | KDD 99 Dataset | Evolving NN, DT | Performance gain, Training time comparison | [60] |
| 7 | CPS in Cyberattacks | actor-critic NN, deep reinforcement learning algorithm | – | [61] | |
| 8 | Anomaly Detection in Cyber-Physical Systems | SWaT | LSTM-RNN | Accuracy | [62] |
| 9 | Safety risk monitoring of CPPS | event_ warningdetail | SVM, NN, MA, AR, GEP, EPABT | MAE, MAPE, MSE, | [35] |
| 10 | Cloud-based Cyberphysical intrusion detection | Random dataset | MLP, RNNLSTM, LR, DT, RF, SVM, | Accuracy | [36] |
| 11 | Estimation of a safety Critical CPS | Real-Time dataset | ANN-LMBP, DT, SVM, RF | R2, RMSE, Training Time, Testing Speed | [37] |
| 12 | CPS of an offshore gas turbine | PI system | MLP, DT, RF, KNN, LR, NB | MAE, RMSE, RAE, Accuracy, Error% | [20] |
| 13 | On-Chip LiDAR Sensors in CPS | Random dataset | MLP SVM | CCR, ECR, MAE, RMSE, RAE, RRSE | [39] |
| 14 | Automotive CPS | IMU | SVM, NN, RNN, LSTM | Confusion Matrix, Accuracy | [40] |
| 15 | Attacks in CPS | Random Dataset | KNN, ANN, SVM, GNB, DT | Precision, Recall, Accuracy | [21] |
| 16 | CPSS | Dataset from AMAZON | SVM, CCNN, NB | Accuracy | [41] |
| 17 | Intrusions Detection system | – | Generative adversarial ANN, ANN | – | [63] |
| 18 | Vehicular Cyber-Physical Systems | SUMO | CNN | Delay, throughput, packet delivery ratio, and network load | [64] |
| 19 | CPS for Thermal stress in 3D Printing | Random dataset | LR, MLP, SVM | MAE, RMSE, R2, MSE | [43] |
| 20 | Image annotation in Cyber-Physical-Social Systems | Corel-5K, IAPR TC-12 | CNN, KSVM | Precision, Recall, F1 measure | [44] |
| 21 | Resistance Spot Welding (RSW) | RSW Quality | LR, SVM, MLP, RF | MSE, MAPE | [46] |
| 22 | Fingerprint in smart CPS | – | KPCA, APADAE, PSO, BP, SVM | Accuracy, precision, Recall, F-Score | [65] |
| 23 | Mobile Edge Computing | 10 Datasets | NB, RF, DT, SVM, K-Means, KNN, MLP, RNN, | Accuracy | [26] |
| 24 | Intrusions Detection in Aerospace | UNSW-NB15, KDDCUP 99, ML-IDS | K-NN, SVM, RF, NB, MLP | Precision, Recall, Accuracy, TP Rate, FP Rate | [14] |
2.4.7 Naive Bayes (NB) in CPS
Bayesian networks are the probabilistic graphical analysis model giving a likelihood of events subject to certain evidence. It is equipped for utilized with discreet data in any structure. NB is considered to be the effective learning algorithm in ML which works efficiently on the principle of conditional independence assumption. Each attribute in the data set is given the same weight and they equally contribute to the outcome. These are from Bayesian inferences which will deduce the events that are evaluated previously. This assumption results in reducing the high density and considers input characteristics are independent. It can combine knowledge and past data. It is mathematically represented in Equation (2.5).
Misra et al. [17] have proposed ML classifiers such as NB to classify learning-based prediction. Two experiments were conducted to check the destination prediction and bandwidth. Performance evaluation is increased by using ensemble techniques. Table 2.7 represents the studies in CPS using NB.
2.5 Use of IoT in CPS
Nowadays, advancements in present technologies in communication and sensor are increasing on the IoT and CPS. With the advancement in the internet, the capability of adopting CPS for the scope of the process has expanded exponentially [67]. We can define IoT as a system that has physical objects with sensors communicated through the internet via wired or wireless. Soon, IoT is going to play a major role in human’s life, every device or physical object is connected via IoT [68]. The advancement of the CPS has great potential with IoT. Table 2.8 describes various studies and advancements in CPS related using IoT.
Table 2.7 Various applications in CPS using Naïve Bayes.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | Power system disturbance | 15 Datasets | One R, Nnge, Random Forest, Naïve Bayes, SVM, Jripper, Adaboost | Accuracy, Precision, Recall, F-Measure | [31] |
| 2 | Attacks in CPS | SWaT | SVM, RF, DT, NN, NB | TP, FP, Precision, Recall, Accuracy, FA, TTBM | [33] |
| 3 | CPS maintenance | Industrial dataset | NB, DT, RF, NN | Precision, Recall | [49] |
| 4 | CP-SRS | real-life data | NN-SLM, NB-SLM | Confusion matrix | [58] |
| 5 | Autonomous Robotics | A dataset with physical and cyber features | Bayesian Networks | ROC, AUC | [53] |
| 6 | CIoT-based CPS | CASIA, TIDE | NB, SVM, LR, J48, KNN | Accuracy, Precision, Recall, F-Measure, ROC | [18] |
| 7 | CPS in gas turbine | PI system | MLP, DT, RF, KNN, LR, NB | MAE, RMSE, RAE, Accuracy, Error% | [20] |
| 8 | CPS in Laser Surface Heat treatment | Real-Time | Dynamic Bayesian networks | TP, FP, TN, FN, Sensitivity, Specificity | [66] |
| 9 | Cyber-Physical-Social Systems | Dataset from AMAZON | SVM, CCNN, NB | Accuracy | [41] |
| 10 | Industry 4.0 | ABS, bCMS, and TCM | SVM, Naive Bayes,and J48 decision-tree | AUC | [42] |
| 11 | Medical CPS | Health care datasets | KNN, SVM, NB, DT, Fuzzy | Recall, F-Measure | [24] |
| 12 | Intrusions Detection in Aerospace | UNSW-NB15, KDDCUP 99, ML-IDS | K-NN, SVM, RF, NB, MLP | Precision, Recall, Accuracy, TP Rate, FP Rate | [14] |
| 13 | Cyber-physical water supply systems | anomalous dataset | KNN, MNB, BNB, GNB | Accuracy | [29] |
2.6 Use of Big Data in CPS
A variety of realities such as numbers, words, the depiction of things, or even scrutiny measurements are considered as data. In CPS, the procedure of assembling, shaping, and examining a massive amount of data for mining valuable information is termed as big data analytics. The current computing world is observing an advanced era of big data. Big data is the assortment of large-scale information or huge data such as jet engines, stock exchanges as well as social media sites and it is expanding exponentially with the period. The characteristics of big data include volume, variety, velocity, and variability [68]. Volume is associated with size which plays a crucial role in validating worth out of data. Variety is related to different behavior and resources of data. Velocity is the rate of data and variability is the irregularity that hinders the process of being competent to seize and manage the data professionally. Enhanced decision making, improved customer service, and better operational efficiency are some advantages of big data. Big data is of three types: structured, unstructured as well as semi-structured. Data that accessed effortlessly, practiced, and accumulated in the stable format is known as structured data, and data with no structure is termed as unstructured data. Whereas, semi-structured data consists of both structured as well as unstructured data. These types of big data have been categorized as 1) streaming data, 2) social media data and 3) publicly available data. Where, streaming data can hold a huge amount of data and we can examine as it achieves and create outcomes on what type of information need to keep and what type of data needs to avoid. Social media data is in the form of either unstructured or semi-structured data, thus it postures a limited test at utilization and assessment. Likewise, publicly available data access huge amount of information through open databases such as the CIA World Fact book, the European Union Open Data Entry, or the US government’s data. Big data can be used in many places including education, health care, banking, government, retail, manufacturing, and many more. It allows people to assess information over an existing generation of skills and architectures that maintain eminent speed, storage, detaining information, and assessment. Due to the continuing rise of collected data, large databases were built by the corporation to contribute, aggregate, and extract meaning as of individual data. As a result, overall data regarding privacy, security, intellectual property, and even liability must be recognized in a big data world [86]. Usage of big data offers industries to raise their revenue, acquire additional goals during the origin of novel applications, save money, improve efficiency, and lower the rate of existing applications. On the other hand, the data stream of traffic above the network directs to troubles of big data due to their variety, volume, and properties of speed. Also, privacy, authenticity, convenience, and discretion concerning outsourced information are the major considerations of big data from safety perception. Security has become important since the procedure of big data has amplified. Therefore, intrusion plays a vital role in the allotment of big data.
Table 2.8 Role of IoT in CPS.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | Manufacturing systems | – | UML-based approach | Min, max, avg, stddev | [69] |
| 2 | Intrusion Detection | KDD’99 | MLP | Accuracy, FP Rate | [70] |
| 3 | Advanced Manufacturing and Medicine | – | GENI and FIRE | Not mentioned | [67] |
| 4 | Images Authenticity | Autonomous sources | OC-LBP | TPR, FPR, recall, Precision, FMeasure, ROC | [18] |
| 5 | Industrial | – | not mentioned | – | [71] |
| 6 | Predicting users preferences and interests | Autonomous sources | COLLABORATIVE, CONTENT BASED and HYBRID FILTERING | – | [72] |
| 7 | Mosquito-Borne Diseases | Autonomous sources | fog computing | Temporal Network Analysis | [56] |
| 8 | Industrial Manufacturing | Autonomous sources | CA-Module, A-Hub, LSP | Physical manufacturing resources | [73] |
| 9 | Misbehavior Detection | Collection of Compliance Data | SPECIFICATIONBASED rules | Lightweight Statistical Analysis | [74] |
| 10 | Mobile Edge Computing | 10 Datasets | NB, RF, DT, SVM,KMeans, KNN, MLP, RNN, | Accuracy | [26] |
| 11 | Intrusions Detection in Aerospace | synthetic data, KDDCup 99 | 6LoWPAN | Precision, Recall, Accuracy, TP rate, FP rate | [14] |
Nowadays, big data analytics for resolving the problems of the intrusion detection system has been attracting many researchers, as it supports the learning of enormous volumes of information with several formats from varied resources and detects anomalies. Generally, the assortment of systems for identifying and prohibiting the threatful attack has been categorized as antivirus, intrusion detection systems or intrusion prevention systems, etc. though the referred systems are advantageous in abundant methods, still they are incapable to evade such kind of offensive surreptitious cyber threats. The motivation behind the incompetent of these techniques is the production of a huge quantity of information that is hard and instance unmanageable to examine. So, it is unproblematic to fail to mark the major offensive dangerous actions. Big Data analytics (BDA) can sort through an enormous quantity of data in a fast manner and various systems can become more efficient as well as effective [75]. Authenticating the immeasurable quantity of data in contented networks can be a most important confront for the reason that there is an extremely high quantity of dissimilar kinds of origins: blogs, SNP (social networking platforms) and the contents (comments, articles as well as tweets, etc.) that contain or stored in those SNP. For that reason, there is a need for deriving trouble-free policies for authenticating those kinds of content and control content commendations from further end users. The commended end-users themselves have to be evaluated based on lying on the status and confidence criterion.
Table 2.9 Big data in cyber-physical system.
| S. No. | Application | Dataset | Method | Evaluation factor | Ref. |
|---|---|---|---|---|---|
| 1 | Tracking and synchronization problems | Autonomous sources | FFLM-CTSP | Lyapunov Exponent and Absolute error | [76] |
| 2 | Specification and Design Method | Autonomous sources | Architecture Analysis & Design Language | QoS | [77] |
| 3 | Big Data in Cloud Computing Environment | URL Reputation, YouTube Video, Bag of Words, Gas sensor arrays, Patient, Outpatient, Medicine, Cancer | Parallel Random Forest, RF, DRF, Spark-MLRF | OOB Error Rate, Accuracy | [48] |
| 4 | Educational | Autonomous sources | TOLA | Complexity, Efficiency, and Accuracy | [34] |
| 5 | Industrial | Smart factory features | Agent-Based Data Analysis | Corr.Coef,RAE (%) | [78] |
| 6 | Social data | Autonomous sources | Tensor Computation and Optimization Model | High-order Singular Value Decomposition | [79] |
| 7 | Socio-cyber network:human behaviors | The social network, healthcare, and intelligent transportation system | Graph-theory | Throughput | [80] |
| 8 | Industrial | Autonomous sources | Industrial cloud, the IoT, and big data methods | Not mentioned | [81] |
| 9 | Privacy and security | Autonomous sources | Weibull distribution | Performance, Reliability and mean time failure | [82] |
| 10 | Energy Efficient Machining | Autonomous sources | Energy efficient machining system, Fruit Fly Optimization | RMSE | [83] |
| 11 | Agricultural | Agricultural Cyber-Physical Datasets | GA-SVM | Minimum, Maximum, Mean, Standard Deviation, Skewness, Kurtosis | [47] |
| 12 | Computation | – | high-order singular value decomposition | Error Measurement, Sweep Number Comparison, Incremental tensor | [84] |
| 13 | Health Care (SARS-CoV) | Not mentioned | J48graft, RNN | Success rate, Failure rate, latency and accuracy | [70] |
| 14 | Design and development of a predictive maintenance | Autonomous sources | Offline Association Rule Algorithm and Predictive Maintenance | Support, Confidence | [85] |
CPS has various operations include sensing data from many sensor networks. The main goal of big data in CPS is to analyze data streams that are huge, rapid, and heterogeneous. Table 2.9 represents studies in CPS in the area of Big data.
2.7 Critical Analysis
The cyber-physical system is assorted with different levels of network connectivity and abstraction, because of its current significance in industry, academia, and government. The fundamental hypothesis is that a wide scope of services can be utilized in the collaboration of networks. On the other hand, an extensive and systematic research review on CPS is not found. So, this paper leads to an in-depth literature study on CPS by inspecting existing literature from 2014 to 2020 by considering the articles from standard archives like Elsevier, Springer Link, Research gate, IEEE Explore, and peer reviewed journals. Various researches exploring techniques, algorithms, and frameworks concerning CPS are considered for this work. Especially, 75 papers studying CPS are grouped into ML, IoT, and Big data. The substance of the studies is summarized into three categorical works with year, author, and publication, area of application, data-set, the proposed method, and evaluation factors.
Based on the literature study from Tables 2.1 to 2.9, it is evident that in the year 2017 maximum number of research works was published with the k-NN, SVM, RF, DT, LR, MLP, and NB algorithm. Figure 2.3 shows the ML algorithms with CPS versus the number of publications each year. Figure 2.4 shows the number of published work of CPS with several ML methods, IoT, and Big-Data.
Figure 2.5 shows the development of CPS through various ML methods and it is evident that SVM based models are on a higher priority than other methods such as MLP, K-NN, DT, NB, RF, and LR.
Figure 2.6 concludes the number of CPS works concerning big data, ML, and IoT. The ML approaches are used in wide with 118 from our work and then with big data and IoT.
The application areas of CPS integrated with ML are briefly classified into the industry, security, medical, agriculture, research, and education in our work as shown in Figure 2.7. The SVM and MLP are the most popularly used algorithms for industrial application and security. K-NN and SVM are widely used for medical applications. The DT, NB, and MLP are also widely used for research, SVM in agriculture, and no application in the area of education. Figure 2.8 elaborates on the application areas of CPS concerning ML, IoT, and big data. The ML approaches are getting largely used in industry, security-based model development, and medical domain. It’s clear that IoT and big data are emerging in the fields of industry, security, medical, and research, but there is no major proposed literature studies in the application fields of agriculture and education.

Figure 2.3 Machine learning algorithms with CPS.
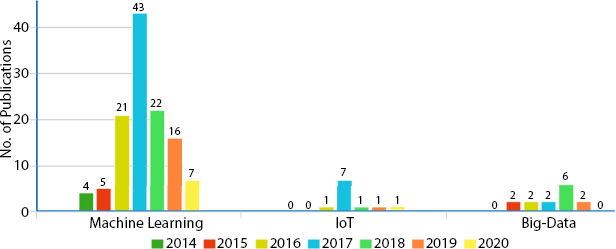
Figure 2.4 Number of publications for ML, IoT, and Big-Data with year wise.
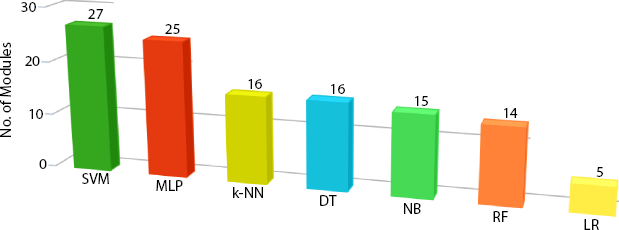
Figure 2.5 Number of machine learning algorithms proposed with CPS.

Figure 2.6 Distinguish approaches with CPS.
The evaluation factors play a key role in identifying the effectiveness of an algorithm or framework of a developed system. Here individual study has been made for each ML model with evaluating factors. The widely used evaluation factors are accuracy, precision, recall, MAE, RMSE and other factors for the K-NN approach, as shown in Figure 2.9.

Figure 2.7 Applications of ML with CPS.
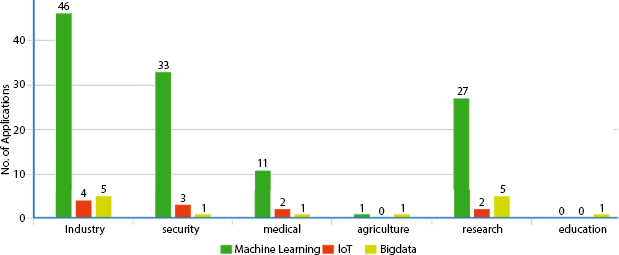
Figure 2.8 Applications of ML, IoT and Big data with CPS.
Similarly, for SVM, RF, DT, MLP, and NB approach widely used factors are accuracy, precision, recall, F-measure, and others as shown in Figures 2.10–2.14.
The LR approach widely used factors such as accuracy, RMSE, MSE, MAE, and others for performance comparison as shown in Figure 2.15.
The researcher had taken the liberty to recognize different research work through a variety of methodologies and frameworks through big data and IoT concerning CPS models. The evaluation factors that are taken into considerations for big data with CPS models accuracy, support, confidence, and other factors are shown in Figure 2.16. Similarly, for IoT with CPS models, the evaluating factors are accuracy, TPR, FPR, recall, precision, and others as shown in Figure 2.17.
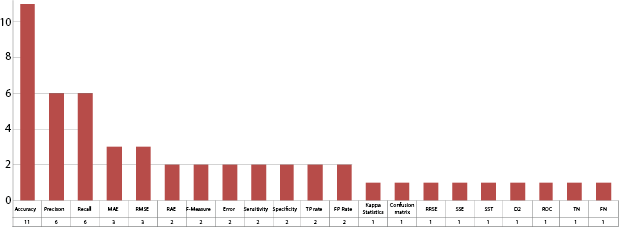
Figure 2.9 K-NN evaluation factors.
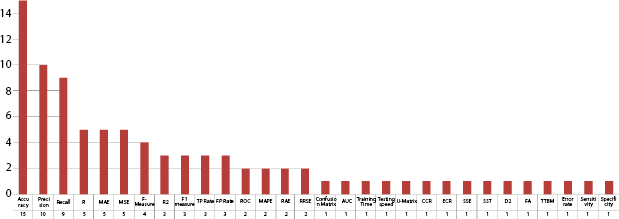
Figure 2.10 SVM evaluation factors.
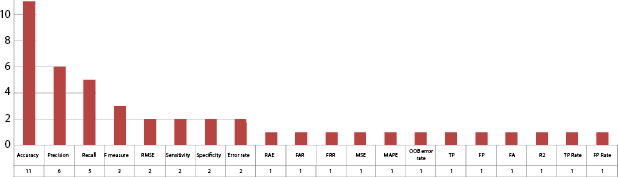
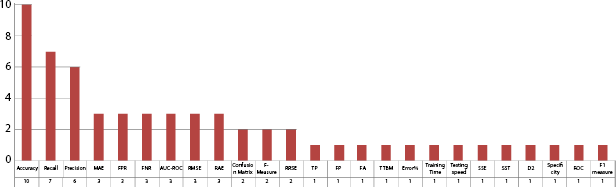
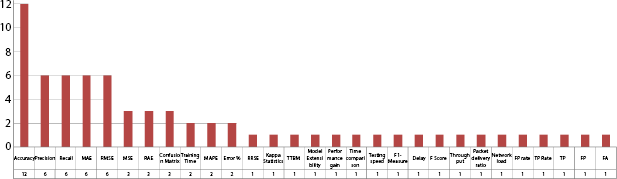

Figure 2.14 NB evaluation factors.
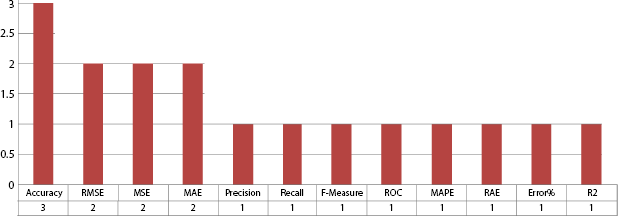
Figure 2.15 LR evaluation factors.
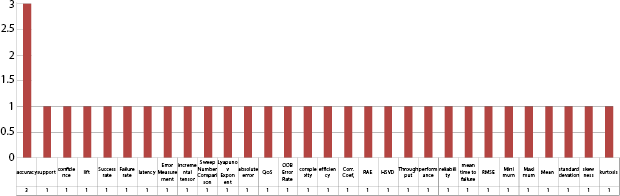
Figure 2.16 Big Data evaluation factors.
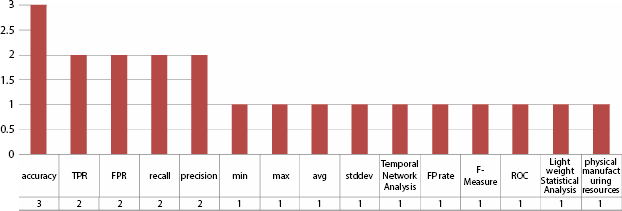
Figure 2.17 IoT evaluation factors.
The literature study shows that for CPS the most widely used datasets are UCI-Parkinson, SWaT, UNSW-NB15, KDDCUP-99, and ML-IDS. However, the rest of the dataset is the random and autonomous dataset.
2.8 Conclusion
Indeed for a secure and prosperous society, we require a great advancement in the fields of defense systems, smart infrastructure buildings and environmental control, renewable energy and smart grid, healthcare system and biomedical, cyber-security, industrial domain platforms, agriculture, education, vehicles, robotic systems, and diagnostic capabilities. The prospect is related to CPS that will lead to multifaceted systems involved by the web of associations and self-driven adaptability through complex logic. As these are perplexing versatile systems that have the developing behavior and require systems joining with other devices through engineering work in their design and operation. So, the need for developing methods, theory, and tools will help the engineers to manage the complexity in design and operations. The study emphasizes CPS and its applications with a computational algorithm, which effectively extracts the affluent statistical representations through the latest evaluation factors, technologies, and approaches in ML, IoT, and big-data framework. All these applications of the system will help us categorically, collaborate, and share assets to achieve the physical procedure. Competent ML architecture is preferred based on comparing their performance in various scenarios. The experimental results of the research community show that ML techniques give enhanced results in terms of precision, recall, and accuracy. The ML approaches demonstrate that the proposed models can be utilized in compelled environments of CPS through a model predictive control, due to their significant advancements and impressive results.
The huge data is computationally inefficient to analyze and progress in the field of CPS through ML because detecting data from numerous IoT sensor systems, handling the acquired data is a big task. This enormous amount of data is processed and extracted into valuable information systems. But the entire process is computationally inefficient due to high energy consumption overhead for the computation process and memory factors. So the mounting space between CPS with the IoT and big data analytics demands novel tools that resolve the challenges confronted by big data velocity, volume, and variety. To analyze the stream of big data, novel architecture systems with cutting edge tools are required to integrate review and decipher useful knowledge from huge streams of data with the CPS. The factors like accuracy and success rate of the big data tools are high when related to other traditional ML, for establishing a better perceptive in extracting knowledge from the data.
The scope of future work emphasis
- On various advanced ML techniques that are needed for CPS.
- The availability of a significantly fair large promissory data-set is required, but the absence of information is a considerable problem.
- The advanced IoT and big data framework architecture must come into play for extracting and sensing knowledge from the data with more scalable, efficient, robust, and secure.
- More research on CPS in the fields of agriculture and education is needed.
References
1. Rajkumar, R.R., Lee, I., Sha, L., Stankovic, J., Cyber-physical systems: The next computing revolution, in: Proceedings of the 47th Design Automation Conference on—DAC ‘10, vol. 19, no. 3, p. 731, 2010.
2. Noble, B. and Flinn, J., Wireless, self-organizing cyber-physical systems, in: NSF Work. Cyber-Physical Syst., Austin, TX, pp. 1–3, 2006, [Online]. Available: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.83.9627&rep=rep1&type=pdf.
3. Zhang, Z.-K., Cho, M.C.Y., Wang, C.-W., Hsu, C.-W., Chen, C.-K., Shieh, S., IoT Security: Ongoing Challenges and Research Opportunities, in: 2014 IEEE 7th International Conference on Service-Oriented Computing and Applications, pp. 230–234, Nov. 2014.
4. Johnson, A.P., Al-Aqrabi, H., Hill, R., Bio-Inspired Approaches to Safety and Security in IoT-Enabled Cyber-Physical Systems. Sensors, 20, 3, 844, Feb. 2020.
5. Sun, C., Ma, J., Yao, Q., On the architecture and development life cycle of secure cyber-physical systems. J. Commun. Inf. Networks, 1, 4, 1–21, Dec. 2016.
6. Sharma, V., You, I., Yim, K., Chen, I.-R., Cho, J.-H., BRIoT: Behavior Rule Specification-Based Misbehavior Detection for IoT-Embedded Cyber-Physical Systems. IEEE Access, 7, c, 118556–118580, 2019.
7. Kuhnle, A. and Lanza, G., Application of Reinforcement Learning in Production Planning and Control of Cyber Physical Production Systems, pp. 123–132, Springer Berlin Heidelberg, 2019.
8. Banerjee, S., Al-Qaheri, H., Bhatt, C., Handling uncertainty in IoT design: An approach of statistical machine learning with distributed second-order optimization, in: Healthcare Data Analytics and Management, pp. 227–243, Elsevier, 2019.
9. Keshk, M., Sitnikova, E., Moustafa, N., Hu, J., Khalil, I., An Integrated Framework for Privacy-Preserving based Anomaly Detection for Cyber-Physical Systems. IEEE Trans. Sustain. Comput., 1–1, 2019.
10. Krismayer, T., Rabiser, R., Grünbacher, P., A constraint mining approach to support monitoring cyber-physical systems. In International Conference on Advanced Information Systems Engineering, Springer, Cham, pp. 659–674, June 2019.
11. Sepulveda, J., Liu, S., Bermudo Mera, J.M., Post-Quantum Enabled Cyber Physical Systems. IEEE Embed. Syst. Lett., 11, 4, 106–110, Dec. 2019.
12. Genge, B., Haller, P., Duka, A.V., Engineering security-aware control applications for data authentication in smart industrial cyber–physical systems. Future Gener. Comput. Syst., 91, 206–222, 2019.
13. Han, S., Xie, M., Chen, H.-H., Ling, Y., Intrusion Detection in Cyber-Physical Systems: Techniques and Challenges. IEEE Syst. J., 8, 4, 1052–1062, Dec. 2014.
14. Maleh, Y., Machine Learning Techniques for IoT Intrusions Detection in Aerospace Cyber-Physical Systems, in: Studies in Computational Intelligence, vol. 836, pp. 205–232, Springer International Publishing, Cham, 2020.
15. de Mello, A.R. and Stemmer, M.R., Inspecting surface mounted devices using k nearest neighbor and Multilayer Perceptron, in: 2015 IEEE 24th International Symposium on Industrial Electronics (ISIE), vol. 2015-Septe, pp. 950–955, Jun. 2015.
16. Ide, C., Nick, M., Kaulbars, D., Wietfeld, C., Forecasting Cellular Connectivity for Cyber-Physical Systems: A Machine Learning Approach, in: Machine Learning for Cyber Physical Systems, O. Niggemann and J. Beyerer (Eds.), pp. 15–22, Springer Berlin Heidelberg, Berlin, Heidelberg, 2016.
17. Misra, S., Goswami, S., Taneja, C., Multivariate Data Fusion-Based Learning of Video Content and Service Distribution for Cyber Physical Social Systems. IEEE Trans. Comput. Soc. Syst., 3, 1, 1–12, Mar. 2016.
18. Hossain, M.S., Muhammad, G., AL Qurishi, M., Verifying the Images Authenticity in Cognitive Internet of Things (CIoT)-Oriented Cyber Physical System. Mob. Netw. Appl., 23, 2, 239–250, Apr. 2018.
19. Laghari, A., Memon, Z.A., Ullah, S., Hussain, I., Cyber Physical System for Stroke Detection. IEEE Access, 6, c, 37444–37453, 2018.
20. Majdani, F., Petrovski, A., Doolan, D., Evolving ANN-based sensors for a context-aware cyber physical system of an offshore gas turbine. Evol. Syst., 9, 2, 119–133, Jun. 2018.
21. Wang, J., Tu, W., Hui, L.C.K., Yiu, S.M., Wang, E.K., Detecting Time Synchronization Attacks in Cyber-Physical Systems with Machine Learning Techniques, in: 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), pp. 2246–2251, Jun. 2017.
22. Wu, M., Song, Z., Moon, Y.B., Detecting cyber-physical attacks in CyberManufacturing systems with machine learning methods. J. Intell. Manuf., 30, 3, 1111–1123, Mar. 2019.
23. Devarajan, M. and Ravi, L., Intelligent cyber-physical system for an efficient detection of Parkinson disease using fog computing. Multimed. Tools Appl., 78, 23, 32695–32719, Dec. 2019.
24. Li, W., Meng, W., Su, C., Kwok, L.F., Towards False Alarm Reduction Using Fuzzy If-Then Rules for Medical Cyber Physical Systems. IEEE Access, 6, c, 6530–6539, 2018.
25. Miranda Calero, J.A., Marino, R., Lanza-Gutierrez, J.M., Riesgo, T., Garcia-Valderas, M., Lopez-Ongil, C., Embedded Emotion Recognition within Cyber-Physical Systems using Physiological Signals, in: 2018 Conference on Design of Circuits and Integrated Systems (DCIS), pp. 1–6, Nov. 2018.
26. Chen, Y., Zhang, Y., Maharjan, S., Alam, M., Wu, T., Deep Learning for Secure Mobile Edge Computing in Cyber-Physical Transportation Systems. IEEE Netw., 33, 4, 36–41, Jul. 2019.
27. Song, K., Anderson, K., Lee, S., An energy-cyber-physical system for personalized normative messaging interventions: Identification and classification of behavioral reference groups. Appl. Energy, 260, November 2019, 114237, Feb. 2020.
28. Zhang, F., Kodituwakku, H.A.D.E., Hines, J.W., Coble, J., Multilayer Data-Driven Cyber-Attack Detection System for Industrial Control Systems Based on Network, System, and Process Data. IEEE Trans. Industr. Inform., 15, 7, 4362–4369, Jul. 2019.
29. Meleshko, A.V., Desnitsky, V.A., Kotenko, I.V., Machine learning based approach to detection of anomalous data from sensors in cyber-physical water supply systems. IOP Conf. Ser. Mater. Sci. Eng., 709, 3, 033034, Jan. 2020.
30. Wang, Y., Amin, M.M., Fu, J., Moussa, H.B., A Novel Data Analytical Approach for False Data Injection Cyber-Physical Attack Mitigation in Smart Grids. IEEE Access, 5, 26022–26033, 2017.
31. Borges Hink, R.C., Beaver, J.M., Buckner, M.A., Morris, T., Adhikari, U., Pan, S., Machine learning for power system disturbance and cyber-attack discrimination, in: 2014 7th International Symposium on Resilient Control Systems (ISRCS), pp. 1–8, Aug. 2014.
32. Huda, S. et al., Defending unknown attacks on cyber-physical systems by semi-supervised approach and available unlabeled data. Inf. Sci. (Ny)., 379, 211–228, Feb. 2017.
33. Junejo, K.N. and Goh, J., Behaviour-Based Attack Detection and Classification in Cyber Physical Systems Using Machine Learning, in: Proceedings of the 2nd ACM International Workshop on Cyber-Physical System Security—CPSS ‘16, no. Ml, pp. 34–43, 2016.
34. Song, J., Zhang, Y., Duan, K., Shamim Hossain, M., Rahman, S.M.M., TOLA: Topic-oriented learning assistance based on cyber-physical system and big data. Future Gener. Comput. Syst., 75, 200–205, Oct. 2017.
35. Li, Q. et al., Safety Risk Monitoring of Cyber-Physical Power Systems Based on Ensemble Learning Algorithm. IEEE Access, 7, c, 24788–24805, 2019.
36. Loukas, G., Vuong, T., Heartfield, R., Sakellari, G., Yoon, Y., Gan, D., Cloud-Based Cyber-Physical Intrusion Detection for Vehicles Using Deep Learning. IEEE Access, 6, 3491–3508, 2018.
37. Lv, C. et al., Levenberg–Marquardt Backpropagation Training of Multilayer Neural Networks for State Estimation of a Safety-Critical Cyber-Physical System. IEEE Trans. Industr. Inform., 14, 8, 3436–3446, Aug. 2018.
38. Saez, M., Maturana, F., Barton, K., Tilbury, D., Anomaly detection and productivity analysis for cyber-physical systems in manufacturing, in: 2017 13th IEEE Conference on Automation Science and Engineering (CASE), vol. 2017-Augus, pp. 23–29, Aug. 2017.
39. Castaño, F., Beruvides, G., Haber, R.E., Artuñedo, A., Obstacle Recognition Based on Machine Learning for On-Chip LiDAR Sensors in a Cyber-Physical System. Sensors, 17, 9, 2109, Sep. 2017.
40. Shin, J., Baek, Y., Eun, Y., Son, S.H., Intelligent sensor attack detection and identification for automotive cyber-physical systems, in: 2017 IEEE Symposium Series on Computational Intelligence (SSCI), vol. 2018-Janua, pp. 1–8, Nov. 2017.
41. Yuan, X., Sun, M., Chen, Z., Gao, J., Li, P., Semantic Clustering-Based Deep Hypergraph Model for Online Reviews Semantic Classification in Cyber-Physical-Social Systems. IEEE Access, 6, c, 17942–17951, 2018.
42. Alenazi, M., Niu, N., Wang, W., Savolainen, J., Using Obstacle Analysis to Support SysML-Based Model Testing for Cyber Physical Systems, in: 2018 IEEE 8th International Model-Driven Requirements Engineering Workshop (MoDRE), no. 1, pp. 46–55, Aug. 2018.
43. Miao, G., Hsieh, S.-J., Segura, J.A., Wang, J.-C., Cyber-physical system for thermal stress prevention in 3D printing process. Int. J. Adv. Manuf. Technol., 100, 1–4, 553–567, Jan. 2019.
44. Ning, Z., Zhou, G., Chen, Z., Li, Q., Integration of Image Feature and Word Relevance: Toward Automatic Image Annotation in Cyber-Physical-Social Systems. IEEE Access, 6, 44190–44198, 2018.
45. Lee, J., Noh, S., Kim, H.-J., Kang, Y.-S., Implementation of Cyber-Physical Production Systems for Quality Prediction and Operation Control in Metal Casting. Sensors, 18, 5, 1428, May 2018.
46. Ahmed, F., Jannat, N.-E., Gavidel, S.Z., Rickli, J., Kim, K.-Y., A Conceptual Framework for Cyber-physical System in Connected RSW Weldability Certification. Procedia Manuf., 38, 2019, 431–438, 2019.
47. Ruan, J., Jiang, H., Li, X., Shi, Y., Chan, F.T.S., Rao, W., A Granular GA-SVM Predictor for Big Data in Agricultural Cyber-Physical Systems. IEEE Trans. Industr. Inform., 15, 12, 6510–6521, Dec. 2019.
48. Chen, J. et al., A Parallel Random Forest Algorithm for Big Data in a Spark Cloud Computing Environment. IEEE Trans. Parallel Distrib. Syst., 28, 4, 919–933, Apr. 2017.
49. Alexis, L. and Bueno, M.L.P., Towards Adaptive Scheduling of Maintenance for Cyber-Physical Systems, vol. 9952, Springer International Publishing, Cham, 2016.
50. Lakshmanaprabu, S.K., Shankar, K., Ilayaraja, M., Nasir, A.W., Vijayakumar, V., Chilamkurti, N., Random forest for big data classification in the internet of things using optimal features. Int. J. Mach. Learn. Cybern., 10, 10, 2609– 2618, Oct. 2019.
51. Mowla, N.I., Doh, I., Chae, K., On-Device AI-Based Cognitive Detection of Bio-Modality Spoofing in Medical Cyber Physical System. IEEE Access, 7, 2126–2137, 2019.
52. Da Xu, L. and Duan, L., Big data for cyber physical systems in industry 4.0: A survey. Enterp. Inf. Syst., 13, 2, 148–169, Feb. 2019.
53. Bezemskij, A., Loukas, G., Gan, D., Anthony, R.J., Detecting Cyber-Physical Threats in an Autonomous Robotic Vehicle Using Bayesian Networks, in: 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), vol. 2018-Janua, pp. 98–103, Jun. 2017.
54. Vuong, T.P., Loukas, G., Gan, D., Performance Evaluation of Cyber-Physical Intrusion Detection on a Robotic Vehicle, in: 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, pp. 2106–2113, Oct. 2015.
55. Vuong, T.P., Loukas, G., Gan, D., Bezemskij, A., Decision tree-based detection of denial of service and command injection attacks on robotic vehicles. 2015 IEEE Int. Work. Inf. Forensics Secur. WIFS 2015—Proc., no. Table I, pp. 1–6, 2015.
56. Sood, S.K. and Mahajan, I., Fog-cloud based cyber-physical system for distinguishing, detecting and preventing mosquito borne diseases. Future Gener. Comput. Syst., 88, 764–775, Nov. 2018.
57. Shanthamallu, U.S., Spanias, A., Tepedelenlioglu, C., Stanley, M., A brief survey of machine learning methods and their sensor and IoT applications, in: 2017 8th International Conference on Information, Intelligence, Systems & Applications (IISA), vol. 2018-Janua, pp. 1–8, Aug. 2017.
58. Li, C., Rusák, Z., Horváth, I., Ji, L., Validation of the reasoning of an entry-level cyber-physical stroke rehabilitation system equipped with engagement enhancing capabilities. Eng. Appl. Artif. Intell., 56, 185–199, Nov. 2016.
59. Wang, Y., Song, B., Zhang, P., Xin, N., Cao, G., A Fast Feature Fusion Algorithm in Image Classification for Cyber Physical Systems. IEEE Access, 5, c, 9089–9098, 2017.
60. Mowla, N., Doh, I., Chae, K., Evolving neural network intrusion detection system for MCPS, in: 2018 20th International Conference on Advanced Communication Technology (ICACT), vol. 6, no. 4, pp. 1040–1045, Feb. 2018.
61. Feng, M. and Xu, H., Deep reinforecement learning based optimal defense for cyber-physical system in presence of unknown cyber-attack, in: 2017 IEEE Symposium Series on Computational Intelligence (SSCI), vol. 2018-Janua, pp. 1–8, Nov. 2017.
62. Goh, J., Adepu, S., Tan, M., Lee, Z.S., Anomaly Detection in Cyber Physical Systems Using Recurrent Neural Networks, in: 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), pp. 140–145, 2017.
63. Belenko, V., Chernenko, V., Kalinin, M., Krundyshev, V., Evaluation of GAN Applicability for Intrusion Detection in Self-Organizing Networks of Cyber Physical Systems, in: 2018 International Russian Automation Conference (RusAutoCon), pp. 1–7, Sep. 2018.
64. Jindal, A., Aujla, G.S., Kumar, N., Chaudhary, R., Obaidat, M.S., You, I., SeDaTiVe: SDN-Enabled Deep Learning Architecture for Network Traffic Control in Vehicular Cyber-Physical Systems. IEEE Netw., 32, 6, 66–73, Nov. 2018.
65. Chen, Y., Du, T., Jiang, C., Sun, S., Indoor location method of interference source based on deep learning of spectrum fingerprint features in Smart Cyber-Physical systems. EURASIP J. Wirel. Commun. Netw., 2019, 1, 47, Dec. 2019.
66. Ogbechie, A., Díaz-Rozo, J., Larrañaga, P., Bielza, C., Dynamic Bayesian Network-Based Anomaly Detection for In-Process Visual Inspection of Laser Surface Heat Treatment, in: Machine Learning for Cyber Physical Systems, J. Beyerer, O. Niggemann, C. Kühnert (Eds.), pp. 17–24, Springer Berlin Heidelberg, Berlin, Heidelberg, 2017.
67. Cecil, J., Internet of Things (IoT)-Based Cyber-Physical Frameworks for Advanced Manufacturing and Medicine, in: Internet of Things and Data Analytics Handbook, pp. 545–561, John Wiley & Sons, Inc., Hoboken, NJ, USA, 2016.
68. Babiceanu, R.F. and Seker, R., Big Data and virtualization for manufacturing cyber-physical systems: A survey of the current status and future outlook. Comput. Ind., 81, 2015, 128–137, Sep. 2016.
69. Thramboulidis, K. and Christoulakis, F., UML4IoT—A UML-based approach to exploit IoT in cyber-physical manufacturing systems. Comput. Ind., 82, 259–272, Oct. 2016.
70. Alpano, P.V.S., Pedrasa, J.R.I., Atienza, R., Multilayer perceptron with binary weights and activations for intrusion detection of Cyber-Physical systems, in: TENCON 2017—2017 IEEE Region 10 Conference, vol. 2017-Decem, pp. 2825–2829, Nov. 2017.
71. Barnard, A., Frechette, S., Srinivasan, V., Industrial Internet of Things, Springer International Publishing, Cham, 2017.
72. Sawant, S.D., Sonawane, K.V., Jagani, T., Chaudhari, A.N., Representation of recommender system in IoT using cyber physical techniques, in: 2017 International conference of Electronics, Communication and Aerospace Technology (ICECA), vol. 2017-Janua, pp. 372–375, Apr. 2017.
73. Tao, F., Cheng, J., Qi, Q., IIHub: An Industrial Internet-of-Things Hub Toward Smart Manufacturing Based on Cyber-Physical System. IEEE Trans. Industr. Inform., 14, 5, 2271–2280, May 2018.
74. You, I., Yim, K., Sharma, V., Choudhary, G., Chen, I.-R., Cho, J.-H., On IoT Misbehavior Detection in Cyber Physical Systems, in: 2018 IEEE 23rd Pacific Rim International Symposium on Dependable Computing (PRDC), vol. 2018-Decem, pp. 189–190, Dec. 2018.
75. Oseku-Afful, T., The use of Big Data Analytics to protect Critical Information Infrastructures from Cyber-attacks, Information Security, Univ. Technol. Dep. Comput. Sci. Electr. Sp. Eng. Master Thesis, pp. 1–64, 2016.
76. Liu, L., Zhao, S., Yu, Z., Dai, H., A big data inspired chaotic solution for fuzzy feedback linearization model in cyber-physical systems. Ad Hoc Netw., 35, 97–104, Dec. 2015.
77. Selvaraj, H., Zydek, D., Chmaj, G., Progress in Systems Engineering, vol. 366, Springer International Publishing, Cham, 2015.
78. Queiroz, J., Leitão, P., Oliveira, E., Industrial Cyber Physical Systems Supported by Distributed Advanced Data Analytics, in: Studies in Computational Intelligence, vol. 694, pp. 47–59, 2017.
79. Wang, X., Yang, L.T., Chen, X., Han, J.-J., Feng, J., Tensor, A., Computation and Optimization Model for Cyber-Physical-Social Big Data. IEEE Trans. Sustain. Comput., 4, 4, 326–339, 2017.
80. Ahmad, A. et al., Socio-cyber network: The potential of cyber-physical system to define human behaviors using big data analytics. Future Gener. Comput. Syst., 92, 868–878.
81. Cheng, B.O., Zhang, J., Hancke, G.P., Industrial Cyber-Physical Systems, in: 2019 IEEE 28th International Symposium on Industrial Electronics (ISIE), no. March, pp. 1620–1622, Jun. 2019.
82. Gifty, R., Bharathi, R., Krishnakumar, P., Privacy and security of big data in cyber physical systems using Weibull distribution-based intrusion detection. Neural Comput. Appl., 31, S1, 23–34, Jan. 2019.
83. Liang, Y.C., Lu, X., Li, W.D., Wang, S., Cyber Physical System and Big Data enabled energy efficient machining optimisation. J. Clean. Prod., 187, 46–62, Jun. 2018.
84. Wang, X., Wang, W., Yang, L.T., Liao, S., Yin, D., Deen, M.J., A Distributed HOSVD Method with Its Incremental Computation for Big Data in Cyber-Physical-Social Systems. IEEE Trans. Comput. Soc. Syst., 5, 2, 481– 492, 2018.
85. Yang, F.-N. and Lin, H.-Y., Development of A Predictive Maintenance Platform for Cyber-Physical Systems, in: 2019 IEEE International Conference on Industrial Cyber Physical Systems (ICPS), pp. 331–335, May 2019.
86. Britel, M., Big data analytic for intrusion detection system, 2018 Int. Conf. Electron. Control. Optim. Comput. Sci. ICECOCS 2018, no. 1, pp. 1–5, 2019.
*Corresponding author: [email protected]