Chapter 7. Security Controls for Mobile and Small Form Factor Devices
This chapter covers the following topics:
Enterprise Mobility Management: This section covers secure control and administration of mobile devices and the strategies and tools involved.
Security Implications/Privacy Concerns: Topics covered include the features found in many mobile devices, the security implications of these features, and approaches to mitigating any security issues.
Wearable Technology: This section discusses wearable computing devices such as cameras, watches, and fitness devices and security issues related to these devices.
This chapter covers CAS-003 objective 2.3.
Users are increasingly demanding the right to use mobile devices such as smartphones and tablets on the enterprise network. This creates a big security issue as these devices spend much of their life outside the network. Moreover, users are embracing wearable technology such as cameras, watches, and fitness devices. This chapter discusses the security implications of these devices and what can be done to prevent vulnerabilities associated with them.
Enterprise Mobility Management
Almost everyone today has at least one mobile device. But the popularity of mobile devices has brought increasing security issues for security professionals. The increasing use of mobile devices combined with the fact that many of these devices connect using public networks with little or no security provides security professionals with unique challenges. The following sections cover some of the issues and mitigations involved in managing mobile devices.
Containerization
One of the issues with allowing the use of personal devices in a bring your own device (BYOD) initiative is the possible mixing of sensitive corporate data with the personal data of the user. Containerization is a newer feature of most mobile device management (MDM) software that creates an encrypted “container” to hold and quarantine corporate data separately from that of the users. This allows for MDM policies to be applied only to that container and not the rest of the device.
Configuration Profiles and Payloads
MDM configuration profiles are used to control the use of devices; when these profiles are applied to the devices, they make changes to settings such as the passcode settings, Wi-Fi passwords, virtual private network (VPN) configurations, and more. Profiles also can restrict items that are available to the user, such as the camera. The individual settings, called payloads, may be organized into categories in some implementations. For example, there may be a payload category for basic settings, such as a required passcode, and other payload categories, such as email settings, Internet, and so on.
Personally Owned, Corporate-Enabled
When a personally owned, corporate-enabled policy is in use, the organization users purchase their own devices but allow the device to be managed by corporate tools such as MDM software.
Application Wrapping
Another technique to protect mobile devices and the data they contain is application wrapping. Application wrappers (implemented as policies) enable administrators to set policies that allow employees with mobile devices to safely download an app, typically from an internal store. Policy elements can include elements such as whether user authentication is required for a specific app and whether data associated with the app can be stored on the device.
Remote Assistance Access
When a company chooses to institute either a BYOD or corporate-owned, personally enabled (COPE) initiative, security professionals should think about supporting the users, especially if the MDM software significantly alters their experience with the device. Many vendors of MDM software provide remote assistance capabilities. For example, Mobile Device Manager Plus from ManageEngine provides an Android remote control feature that can also be used to manage iOS and Windows phones.
VNC
Another option for providing support is to use virtual network computing (VNC) technology. This graphical desktop sharing system uses the Remote Frame Buffer (RFB) protocol to remotely control another computer. A mobile version of VNC can be installed for this purpose.
Screen Mirroring
While screen mirroring is typically used to project a computer, tablet, or smartphone screen to a TV, it can also be used to project to a remote support individual. Because that is not something this feature was made for, however, the process can be a bit complicated. In most cases, the support features in MDM software are more robust and user friendly than screen mirroring.
Application, Content, and Data Management
While we have already discussed one method of securing data and applications—by using containerization—mobile management solutions can use other methods as well. Conditional access defines policies that control access to corporate data based on conditions of the connection, including user, location, device state, application sensitivity, and real-time risk. Moreover, these policies can be granular enough to control certain actions within an application, such as preventing cut and paste. Finally, more secure control of sharing is possible, allowing for the control and tracking of what happens after a file has been accessed, with the ability to prevent copying, printing, and other actions that help control sharing with unauthorized users.
Over-the-Air Updates (Software/Firmware)
An over-the-air update is simply an update that occurs over a wireless connection. Firmware updates, referred to as firmware over-the-air (FOTA), may occur using the same process as the updates discussed later in this section, or they may be performed with special firmware and operating system update tools, such as the FOTA flash programming tools from Zeeis. Zeeis is a comprehensive, cloud-based mobile/embedded software update and management system.
Two other types of updates smartphones can receive are PRI and PRL updates. Let’s look at what those are. Product release information (PRI) is a connection between a mobile device and a radio. From time to time the PRI may need to be updated, and such updates may add features or increase data speed. The preferred roaming list (PRL) is a list of radio frequencies that resides in the memory of some kinds of digital phones. The PRL lists frequencies the phone can use in various geographic areas. The areas are ordered by the bands the phone should try to use first; it is basically a priority list that indicates which towers the phone should use.
When roaming, the PRL may instruct the phone to use the network with the best roaming rate for the carrier rather than the one with the strongest signal at the moment. As carrier networks change, an updated PRL may be required.
The baseband processor is the chip that controls RF waves, thereby managing all antenna functions. An update makes the code in the chip current.
All mobile devices may require one or more of these update types at some point. In many cases, these updates happen automatically, or “over-the-air.” In many cases, you may be required to disable Wi-Fi and enable data for these updates to occur.
Remote Wiping
Remote wipes are instructions sent remotely to a mobile device that erase all the data, typically used when a device is lost or stolen. In the case of the iPhone, this feature is closely connected to the locater application Find My iPhone.
Android phones do not come with an official remote wipe. You can, however, install an Android app that will do this. Once the app Lost Android is installed, it works in the same way as the iPhone remote wipe.
Android Device Manager, which is loaded on newer versions of Android, is available for download to any version of Android from 2.3 onward, and it provides almost identical functionality to the iPhone.
While the methods just mentioned do not make the use of MDM software, it is a function that also comes with the software and consent to remote wipe should be required of any user who uses a mobile device in either a BYOD or COPE environment.
SCEP
Simple Certificate Enrollment Protocol (SCEP) provisions certificates to network devices, including mobile devices. As SCEP includes no provision for authenticating the identity of the requester, two different authorization mechanisms are used for the initial enrollment:

Manual: The requester is required to wait after submission for the CA operator or certificate officer to approve the request.
Preshared secret: The SCEP server creates a “challenge password” that must be somehow delivered to the requester and then included with the submission back to the server.
Security issues with SCEP include the fact that when the preshared secret method is used, the challenge password is used for authorization to submit a certificate request. It is not used for authentication of the device.
BYOD
Bring your own device (BYOD) initiatives are discussed in Chapter 1, “Business and Industry Influences and Associated Secuerity Risks.”
COPE
Corporate-owned, personally enabled (COPE) is a strategy in which an organization purchases mobile devices, and users manage those devices. Organizations can often monitor and control the users’ activity to a larger degree than with personally owned devices. Besides using these devices for business purposes, employees can use the devices for personal activities, such as accessing social media sites, using email, and making calls. COPE also gives the company more power in terms of policing and protecting devices. Organizations should create explicit policies that define the allowed and disallowed activities on COPE devices.
VPN
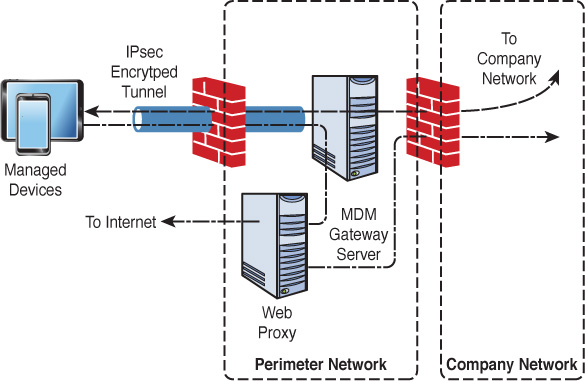
Most MDM solutions also offer the ability to create a VPN connection from the Internet to a mobile gateway of some sort, located inside the enterprise’s perimeter firewall. Once the tunnel is created (typically using Internet Protocol Security [IPsec]), all traffic (even traffic destined for the Internet) goes to the gateway and is then forwarded to either the internal network or the Internet. When forwarded to the Internet, it is usually routed through a web proxy that makes the connections on behalf of the device. This process is depicted in Figure 7-1.

Application Permissions
While there are certainly ways to control the installation and use of software (for example, using Group Policy in Windows), mobile application management (MAM) software provides granular control through the use of application permissions that can be applied to users with respect to certain applications that handle sensitive information. For more, see the section “Application, Content, and Data Management,” earlier in this chapter.
Side Loading
Side loading is a method of installing applications on a mobile device from a computer rather than from an app store, such as Google Play or the Apple App Store. Typically, these applications come from a third party or are developed by the organization itself.
Android devices install these apps in Android package (APK) format. When apps are side loaded, a change in the security settings is required to allow unknown sources of apps.
iOS devices allow side loading using a tool called Xcode 7, which requires the creation of a developer account on the Apple developer site.
Unsigned Apps/System Apps
Unsigned applications are code that cannot be verified to be what it purports to be or to be free of malware. While many unsigned applications present absolutely no security issues, most enterprises wisely choose to forbid their installation. MDM software and security settings in the devices themselves can be used to prevent installation of unsigned apps.
System apps come preinstalled on a device. While these apps probably present no security issue, it might be beneficial to remove them to save space and to improve performance as some of them run all the time. It may also be the desire of the organization to prevent features in these apps that may disclose information about the user or the device that could lead to social engineering attacks. These apps can be removed by following the instructions on the vendor site.
Context-Aware Management
Context-based authentication and management take multiple factors or attributes into consideration before authenticating and authorizing an entity. Rather than simply rely on the presentation of proper credentials, the system looks at other factors when making the access decision. Context-based security solves many issues suffered by non-context-based systems.
The following are some of the key solutions context-based authentication provides:

It helps prevent account takeovers made possible by simple password systems.
It helps prevent many attacks made possible by the increasing use of personal mobile devices.
It helps prevent many attacks made possible by the user’s location.
Context-based systems can take a number of factors into consideration when a user requests access to a resource. In combination, these attributes can create a complex set of security rules that can help prevent vulnerabilities that password systems may be powerless to detect or stop. The following sections look at some of these attributes.
Geolocation/Geofencing
At one time, cybersecurity professionals knew that all the network users were safely in the office and behind a secure perimeter created and defended with every tool possible. That is no longer the case. Users now access your network from home, wireless hotspots, hotel rooms, and all sort of other locations that are less than secure.
When you design authentication, you can consider the physical location of the source of an access request. A scenario for this might be that Alice is allowed to access the Sales folder at any time from the office but only from 9 to 5 from her home and never from elsewhere.
Authentication systems can also use location to identify requests to authenticate and access a resource from two different locations in a very short amount of time, one of which could be fraudulent. Finally, these systems can sometimes make real-time assessments of threat levels in the region where a request originates.
Geofencing is the application of geographic limits to where a device can be used. It depends on the use of Global Positioning System (GPS) or radio frequency identification (RFID) technology to create a virtual geographic boundary.
User Behavior
It is possible for authentication systems to track the behavior of an individual over time and use the information gathered to detect when an entity is performing actions that, while within the rights of the entity, differ from the normal activity of the entity. Such actions could indicate that the account has been compromised.
The real strength of an authentication system lies in the way you can combine the attributes just discussed to create very granular policies. For example, say that Gene can access the Sales folder from 9 to 5 if he is in the office and is using his desktop device. However, he can access it only from 10 to 3 using his mobile device in the office but not at all from outside the office.
The main security issue is that the complexity of rule creation can lead to mistakes that actually reduce security. A complete understanding of the system is required, and special training should be provided to anyone managing such a system. Other security issues include privacy issues, such as user concerns about the potential misuse of information used to make contextual decisions. These concerns can usually be addressed through proper training about the power of context-based security.
Security Restrictions
The key capability sought when implementing a context-based management system for mobile is the ability to change the security settings applied to the user and device based on the context, as evidenced by the attributes of the connection covered in this section.
Time-Based Restrictions
Cybersecurity professionals have for quite some time been able to prevent access to a network entirely by configuring login hours in a user’s account profile. However, they have not been able to prevent access to individual resources on a time-of-day basis until recently. For example, you might want to allow Joe to access the sensitive Sales folder during the day from the office but deny him access to that folder from home. Or you might configure the system so that when Joe accesses resources after certain hours, he is required to give another password or credential (a process often called step-up authentication) or perhaps even have a text code sent to his email address that must be provided to allow this access.
Frequency
A context-based system can make access decisions based on the frequency with which the requests are made. Because multiple requests to log in coming very quickly can indicate a password-cracking attack, the system can use this information to deny access or require that the older connection be terminated prior to making the new connection. It also can indicate that an automated process or malware, rather than an individual, is attempting this operation.

Security Implications/Privacy Concerns
One of the biggest obstacles presented by BYOD or COPE initiatives is the security issues that are inherent with mobile devices. Many of these vulnerabilities revolve around storage devices. Let’s look at a few.
Data Storage
While protecting data on a mobile device is always a good idea, in many cases an organization must comply with an external standard regarding the minimum protection provided to the data on the storage device. For example, the Payment Card Industry Data Security Standard (PCI DSS) enumerates requirements that payment card industry players should meet to secure and monitor their networks, protect cardholder data, manage vulnerabilities, implement strong access controls, and maintain security policies.
The different storage types share certain issues and present issues unique to each type.
Non-Removable Storage
The storage that is built into a device may not suffer all the vulnerabilities shared by other forms but is still data at risk. One tool at our disposal with this form of storage that is not available with others is the ability to remotely wipe the data if the device is stolen. At any rate, the data should be encrypted with AES-128 or AES-256 encryption. Also, a backup copy of the data should be stored in a secure location.
Removable Storage
While removable storage may be desirable in that it may not be stolen if the device is stolen, it still can be lost and stolen itself. Removable storage of any type represents one of the primary ways data exfiltration occurs. If removable storage is in use, the data should be encrypted with AES-128 or AES-256 encryption.
Cloud Storage
While cloud storage may seem like a great idea, it presents many unique issues. Among them are the following:
Data breaches: cloud providers may include safeguards in service-level agreements (SLAs), ultimately the organization is responsible for protecting its own data, regardless of where it is located. When this data is not in your hands—and you may not even know where it is physically located at any point in time—protecting your data is difficult.
Authentication system failures: These failures allow malicious individuals into the cloud. This issue is sometimes made worse by the organization itself when developers embed credentials and cryptographic keys in source code and leave them in public-facing repositories.
Weak interfaces and APIs: Interfaces and application programming interfaces (APIs) tend to be the most exposed parts of a system because they’re usually accessible from the open Internet.
Transfer/Backup Data to Uncontrolled Storage
In some cases, users store sensitive data in cloud storage that is outside the control of the organization, using sites such as Dropbox. These storage providers have had their share of data loss issues as well. Policies should address and forbid this type of storage of data from mobile devices.
USB OTG
USB On-the-Go (USB OTG) is a specification first used in late 2001 that allows USB devices, such as tablets or smartphones, to act as either USB hosts or USB devices. With respect to smartphones, USB OTG has been used to hack around the iPhone security feature that requires a valid iPhone username and password to use a device after a factory reset. This feature is supplied to prevent the use of a stolen smartphone that has been reset to factory defaults but can be defeated with a hack using USB OTG.
Device Loss/Theft
Of course, one of the biggest threats to mobile devices is a loss or theft of a device containing irreplaceable or sensitive data. Organizations should ensure that they can remotely lock and wipe devices when this occurs. Moreover, policies should require that corporate data be backed up to a server so that a remote wipe does not delete data that resides only in the device.
Hardware Anti-Tamper
Anti-tamper technology is designed to prevent access to sensitive information and encryption keys on a device. Anti-tamper processors, for example, store and process private or sensitive information, such as private keys or electronic money credit. The chips are designed so that the information is not accessible through external means and can be accessed only by the embedded software, which should contain the appropriate security measures, such as required authentication credentials. Some of these chips take a different approach and zero out the sensitive data if they detect penetration of their security, and some can even do this with no power.
eFuse
An eFuse can be used to help secure a stolen device. For example, the Samsung eFuse uses an efuse to indicate when an untrusted (non-Samsung) path is discovered. Once the eFuse is set (when the is discovered), the device cannot read the data previously stored.
TPM
Trusted Platform Module (TPM) chips, once present only on laptops, have made their way into mobile devices. TPM is covered in Chapter 6, “Security Controls for Host Devices.”
Rooting/Jailbreaking
While rooting, or jailbreaking, a device allows for the user to remove some of the restrictions of the device, it also presents security issues. Jailbreaking removes the security restrictions on an iPhone or iPad. Rooting is the term associated with removing security restrictions on an Android device. Both of these terms mean apps are given access to the core functions of the phone, which normally requires user approval. For example, it allows the installation of apps not found in the Apple App Store. One of the reasons those apps are not in the App Store is because they are either insecure or are malware masquerading as a legitimate app. Finally, a rooted or jailbroken device receives no security updates, which makes it even more vulnerable.
Push Notification Services
Push notification services allow unsolicited messages to be sent by an application to a mobile device even when the application is not open on the device. Although these services can be handy, there are some security best practices when developing them:

Do not send company confidential data or intellectual property in the message payload.
Do not store your Secure Sockets Layer (SSL) certificate and list of device tokens in your web root.
Be careful not to inadvertently expose Apple Push Notification service (APN) certificates or device tokens.
Geotagging
Geotagging, the process of adding geographic identification metadata to various media, is enabled by default on many smartphones—to the surprise of some users. In many cases, this location information can be used to locate where images, video, websites, and SMS messages originated. At minimum, this information can be used to carry out a social engineering attack. This information has been used, for example, to reveal the locations of high-valued goods. In an extreme case, four U.S. Apache helicopters were destroyed by terrorists on the ground when their location was given away by geotagged photos made by a crew member.
Encrypted Instant Messaging Apps
One of the most used features on a smartphone is the texting feature. Many sensitive exchanges take place through text. While encrypted texting may not be provided on a mobile device, plenty of applications will do this, and some of them are free.
Tokenization
Tokenization, a new emerging standard for mobile transactions, uses numeric tokens to protect cardholders’ sensitive credit and debit card information. This is a great security feature that substitutes the primary account number with a numeric token that can be processed by all participants in the payment ecosystem.
OEM/Carrier Android Fragmentation
Android fragmentation refers to the overwhelming number of versions of Android that have been sold. The issue is that many users are still ruining older versions for which security patches are no longer available. The fault typically lies with the phone manufacturer for either maintaining use of an operating system when a new one is available or customizing the operating system (remember that Android is open source) so much that the security patches are incompatible. Organizations should consider these issues when choosing a phone manufacturer.
Mobile Payment
One of the latest features of mobile devices is the ability to pay for items using the mobile device instead of a credit card. Various technologies are used to make this possible, and they have attendant security issues. Let’s look at how these technologies work.
NFC-Enabled
A new security issue facing both merchants and customers is the security of payment cards that use near-field communication (NFC), such Apple Pay and Google Wallet. While NFC is a short-range type of wireless transmission and is therefore difficult to capture, interception is still possible. Fortunately, payment transmissions are typically encrypted. In any case, some measures can help secure these payment mechanisms:

Lock the mobile device. Devices must be turned on or unlocked before they can read any NFC tags.
Turn off NFC when not in use.
For passive tags, use an RFID/NFC-blocking device.
Scan mobile devices for unwanted apps, spyware, and other threats that may siphon information from mobile payment apps.
Inductance-Enabled
Inductance is the process used in NFC to transmit information from the mobile device to the reader. Coils made of ferrite material use electromagnetic induction to transmit information. Therefore, an inductance-enabled device would be one that supports a mobile payment system.
Mobile Wallet
An alternative technology used in mobile payment is the Mobile Wallet used by online companies like PayPal and Amazon Payments. In such a system, the user registers a credit card number and is issued a PIN that can be used to authorize payments. The PIN identifies the user and the card and enables the merchant to charge the card.
Peripheral-Enabled Payments (Credit Card Reader)
Credit card readers that can read from a mobile device at close range are becoming ubiquitous, especially with merchants that operate in remote locations, such as cabs, food trucks, and flea markets. Figure 7-2 shows one such device reading a card. To be secure, there must some sort of encryption between the peripheral and the card reader. An example of a system that provides such encryption is Apple Pay.
Tethering
One way that many mobile devices can connect to other devices is thorough a hotspot or when tethered to another device. It is common for a mobile device to be able to act as an 802.11 hotspot for other wireless devices in the area. There are also devices dedicated solely to performing as mobile hotspots.
When one mobile device is connected to another mobile device for the purpose of using the Internet connection, it is said to be “tethered” to the device providing the access. While use of such a connection can be done by using 802.11, it can also be done by using Bluetooth or a USB cable between the devices. Sometimes, tethering incurs an additional charge from the provider. Let’s look at these connection methods.
USB
Because a USB connection uses bounded media, it may be the safest way to make a connection. The only way a malicious individual could make this kind of connection is to gain physical access to the mobile device. So physical security is the main way to mitigate this potential breach.
Spectrum Management
Spectrum management is the process of managing and allocating radio frequencies for specific uses. In the United States, this is done by the National Telecommunications and Information Administration (NTIA). NTIA is collaborating with the Federal Communications Commission (FCC) to make available a total of 500 MHz of federal and non-federal spectrum over the next 10 years for mobile and fixed wireless broadband use. This will nearly double the amount of commercial spectrum to support the growing demand by consumers and businesses for wireless broadband services.
Bluetooth 3.0 vs. 4.1
Bluetooth is another option for tethering. There have been a number of versions of Bluetooth, with each version adding speed or features. Version 3.0 offers 20 Mbps per second. Also, a mobile device can adjust to operate at the minimum power level needed to still retain a quality connection, while increasing the power of the Bluetooth connection if the phone moves farther from the tethered device. Version 4.1 uses the Bluetooth Low Energy (LE) protocol, which allows smart devices to remain connected for longer periods of time without draining the battery.
For more on Bluetooth, see Chapter 6.
Authentication
There are several ways to authenticate to a mobile device. Some of the more advanced methods of authentication appeared first on mobile devices. The following sections cover these methods.
Swipe Pattern
Swipe patterns presumably only known to the user can be used to dismiss a screen lock. The main issue with this is that someone nearby may be viewing the swipe pattern. Some recent research has shown it to be more difficult to observe the entry of a PIN than the application of a swipe pattern over the shoulder. Care should be taken to make swipe patterns in a way that cannot be stolen.
Gesture
In gesture authentication, the user is shown a picture to use as a guide and applies a pattern of gestures on the photo. The gesture pattern as well as the picture would be chosen ahead of time and stored on the device. The gesture pattern applied by the user is compared to the pattern in the stored sample.
Three main security issues are present with gesture authentication. The first is that a user may observe the gesture pattern over the shoulder. The second presents itself when malware installs a keylogger on the mobile device, which can capture the gesture pattern. Finally, in a smudge attack, the attacker recovers the pattern from the oily residue on the touchscreen.
PIN Code
Of course, the most common method of authentication is the use of a PIN. This method is susceptible to both keyloggers and observation through shoulder surfing. Of course, with any password or PIN, social engineering attacks, dictionary attacks, and brute-force attacks can occur.
Biometric
Biometric devices use physical characteristics to identify the user. Such devices are becoming more common in the business environment. Biometric systems include hand scanners, retinal scanners, and soon, possibly, DNA scanners. To gain access to biometrically protected mobile device, you must pass a physical screening process.
A company adopting biometric technologies needs to consider the potential controversy. (Some authentication methods are considered more intrusive than others.) The company must also consider the error rate and accept the fact that errors can include both false positives and false negatives. Most mobile device vendors that adopt biometric authentication allow this feature to be disabled. Companies should carefully weigh the advantages and disadvantages of using biometrics.
The following sections look at the most common ways biometrics are implemented on mobile devices.
Facial
A facial scan records facial characteristics, including bone structure, eye width, and forehead size. This biometric method uses eigenfeatures or eigenfaces, neither of which captures a picture of a face. With eigenfeatures, the distances between facial features are measured and recorded. With eigenfaces, measurements of facial components are gathered and compared to a set of standard eigenfaces. For example, a person’s face might be composed of the average face plus 21% from eigenface 1, 83% from eigenface 2, and –18% from eigenface 3. Many facial scan biometric devices use a combination of eigenfeatures and eigenfaces.
Fingerprint
A fingerprint scan usually scans the ridges of a finger for matching. A special type of fingerprint scan called minutiae matching is more microscopic in that it records the bifurcations and other detailed characteristics. Minutiae matching requires more authentication server space and more processing time than ridge fingerprint scanning. Fingerprint scanning systems have a lower user acceptance rate than many other systems because users are concerned with how the fingerprint information will be used and shared.
Iris Scan
An iris scan scans the colored portion of the eye, including all rifts, coronas, and furrows. Iris scans have a higher accuracy than any other biometric scan type.
Malware
Mobile devices can suffer from viruses and malware just like laptops and desktops. Major antivirus vendors such as McAfee and Kaspersky make antivirus and anti-malware products for mobile devices that provide the same real-time protection as the products do for desktops. The same guidelines apply for these mobile devices: Keep them up-to-date by setting the devices to check for updates whenever connected to the Internet.
Unauthorized Domain Bridging
Most mobile devices can act as wireless hotspots. When a device that has been made a member of a domain acts as a hotspot, it allows access to the organizational network to anyone using the hotspot. This access, called unauthorized domain bridging, should be forbidden. Software can prevent this. For example, a software operative on the network may allow activation of only a single communications adapter while inactivating all other communications adapters installed on each computer authorized to access the network.
Baseband Radio/SOC
System on a chip (SoC) has become typical inside mobile device electronics for reducing energy use. A baseband processor is a chip in a network interface that manages all the radio functions. A baseband processor typically uses its own RAM and firmware. Because the software that runs on baseband processors is usually proprietary, it is impossible to perform an independent code audit. In 2014, makers of the free Android derivative Replicant announced that they had found a backdoor in the baseband software of Samsung Galaxy phones that allowed remote access to the user data stored on the phone.
Augmented Reality
Augmented reality (AR) is a view of a physical, real-world environment whose elements are “augmented” by computer-generated or extracted real-world sensory input such as sound, video, graphics, or GPS data. Many mobile devices support AR when the proper apps are installed. An interesting AR device is the Twinkle in the Eye contact lens. This lens, which is implanted in an eye, is fabricated with an LED, a small radio chip, and an antenna. The unit is powered wirelessly by the RF electrical signal and represents the start of research that could eventually lead to screens mounted onto contact lenses inside human eyes. When this lens technology is perfected, we will no longer need mobile devices, as AR chips will eventually be able to be implanted into our eyes and ears, making humans the extension of their own reality.
SMS/MMS/Messaging
Short Message Service (SMS) is a text messaging service component of most telephone, Internet, and mobile telephony systems. Multimedia Messaging Service (MMS) handles messages that include graphics or videos. Both SMS and MMS present security challenges. Because messages are sent in cleartext, they are susceptible to spoofing and spamming.
Wearable Technology
Now we have a new digital technology called wearable technology, which encompasses digital devices that we place somewhere on our body. The following sections survey some of these devices and then look at security implications.
Devices
In the beginning, wearable devices were mainly fitness trackers. Such a device was basically a heart monitor with a wireless connection to the computer. But now wearable devices are almost fully functional computer systems. The following sections look at some of the most popular devices.
Cameras
Wearable cameras are often used by police and others who need hands-free cameras. Although wearable cameras can be worn on the head, the arm, and other places, the type of camera used by police is shown in Figure 7-3.
Watches
A smart watch is a computer you can wear on your wrist. While early on these devices were limited in the tasks they could perform, today’s devices run mobile operating system and are fully functional computers—although with small screens. These devices run either proprietary operating systems or Android. The Apple model runs an operating system called Watch OS.
A smart watch is typically paired to a smartphone for the purpose of accessing calls and messages, and it contains GPS features as well. The following are some of the features you may find in smart watches:

Anti-loss alert
Time display
Call vibration
Caller ID
Answer call
Micro USB input port
These devices have security issues, such as:

The data connection to a smartphone is usually Bluetooth, which makes the watch susceptible to any attacks on the paired mobile device.
Information to the smartphone is transmitted in plaintext.
Fitness Devices
While many smart watches can also act as fitness monitors, some devices specialize in tracking your movement. Fitness monitors read your body temperature, heart rate, and blood pressure, while also tracking where you are for the purpose of determining the distance you ran or walked and the time it took to do so.
Some fitness trackers are wristbands that can track the information discussed and communicate wirelessly to an application on a computer. One of these devices is shown in Figure 7-4. Other, more sophisticated units combine a strap that goes around the chest with a watch or band that collects the information gathered by the sensors in the band.
Glasses
By now everyone has heard about and probably seen Google Glass, the most well-known and recognizable computing device worn as glasses. Just in case you haven’t, Figure 7-5 shows a drawing of the glasses. While the devices caused quite a stir, Google announced in early 2015 that sales to individuals would cease for two years while the technology was improved. In July 2017, it was announced that the Google Glass Enterprise Edition would be released.
Figure 7-5 Google Glass
While Google Glass is worn as glasses, there is a small screen just to the side of one of the eyes that houses the computer screen (think Cyborg). The user can view the screen at any time by just casting a glance at it. Many promising uses have been proposed for the devices, a number of them in the healthcare field. Although sales of the devices to individuals was halted, sales to organizations that have or are working to find ways to use the glasses continue.
Medical Sensors/Devices
Just as sensors connected to networks have changed the management of plants and buildings, connected sensors are changing the monitoring of patient well-being. These sensors are used for:

Drug delivery
Surgery
Orthopedics
Robotic Surgery
Therapeutic uses
Security issues with these devices mainly focus on communicating information wirelessly to other devices or systems. Keep in mind that privacy concerns are very important with personal health information.
Headsets
A wearable device that is not based on glasses but around a headset format is the HC1 headset computer by Zebra (see Figure 7-6). It can respond to voice commands and body movements.
Security Implications
As with any other computing devices that transmit information or are connected to networks, mobile and wearable devices have security issues. The following sections cover some of these.
Unauthorized Remote Activation/Deactivation of Devices or Features
In some cases, unsecured devices may be activated or deactivated or features might be enabled or disabled in an unauthorized fashion or by unauthorized users. For example, Bluetooth devices that are left in a discoverable mode might be vulnerable to Bluetooth attacks. To prevent such issues, either disable Bluetooth or make the device undiscoverable.
Encrypted and Unencrypted Communication Concerns
As discussed earlier in this chapter, in relation to fitness devices and medical sensors, some devices transmit information in an unencrypted format. Because this is sensitive information and the transmission is wireless, this is a big privacy and security concern. To prevent this issue, encrypt all sensitive transmissions
Physical Reconnaissance
In many cases, malicious individuals simply observe a user in the process of using a device to obtain information that can then be used to compromise the device or another device. Users should be taught to perform operations such as entering a PIN or using a gesture to authenticate in a private manner.
Personal Data Theft
Data theft sometimes results from theft of a device. In this case, the remote wipe feature can be used to prevent data theft. In many cases, data theft results from transmission of sensitive data in cleartext. Many devices transmit data in cleartext, and sometimes they do it wirelessly. Choosing a device that does not transmit data in cleartext is advised.
Health Privacy
As discussed earlier in this chapter, personal health information is at risk when medical devices or sensors transmit data wirelessly. These transmissions should be encrypted to prevent the disclosure of any health-related data.
Digital Forensics on Collected Data
Several unique challenges are presented to those collecting digital forensics information from a mobile device. Mobile device vendors frequently change form factors, operating system file structures, data storage, services, peripherals, and even pin connectors and cables. As a result, forensic examiners must use different forensic processes with mobile devices than with desktop computers. Companies have stepped up and created data acquisition tools such as Cellebrite UFED, Susteen Secure View, and Micro Systemation XRY that make this job much easier for digital forensics experts.
When forensic data is collected, it should be considered very sensitive information and protected by strong access control and encrypted where it is stored.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple choices for exam preparation: the exercises here and the practice exams in the Pearson IT Certification test engine.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 7-1 lists these key topics and the page number on which each is found.

Table 7-1 Key Topics for Chapter 7
Key Topic Element |
Description |
Page Number |
List |
SCEP authorization methods |
332 |
Mobile VPN process |
333 |
|
List |
Context-based authentication benefits |
334 |
List |
BYOD policies |
336 |
List |
Push notification best practices |
339 |
List |
Securing NFC-enabled devices |
340 |
List |
Features of smart watches |
346 |
List |
Security issues with smart watches |
347 |
List |
Uses for medical sensors |
348 |
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Digital Security Standard (DSS)
near-field communication (NFC)
product release information (PRI)
virtual network computing (VNC)
Review Questions
1. Which of the following creates an encrypted area to hold and quarantine corporate data separately from that of the users?
virtualization
containerization
COPE
VNC
2. Which strategy calls for an organization to purchase mobile devices and the users to manage those devices?
COPE
BYOD
VNC
RFB
3. Which of the following is used to control the use of a device and, when applied to a device, makes changes to settings such as the passcode settings?
payload
container
plug-in
configuration profile
4. Which of the following enables administrators to set policies that allow employees with corporate-owned or personal mobile devices to safely download an app, typically from an internal store?
payload
application wrapper
container
plug-in
5. Which of the following are individual settings in an MDM configuration profile?
payloads
plug-ins
signatures
wrappers
6. Which of the following is a graphical desktop sharing system that uses the Remote Frame Buffer (RFB) protocol to remotely control another computer?
RDP
VNC
NAC
RCP
7. Which of the following is information on the connection between a mobile device and a radio?
VNC
PRL
PRI
RCP
8. Which of the following is a list of radio frequencies residing in the memory of some kinds of digital phones?
VNC
PRL
PRI
RCP
9. Which of the following is a process in which instructions can be sent remotely to a mobile device to erase all the data when the device is stolen?
memory dump
SCEP
remote wipe
PRL
10. Which of the following is used to provision certificates to network devices, including mobile devices?
SCEP
BYOD
COPE
OSCP