Chapter 29
Applying Mitigation Techniques or Controls to Secure an Environment
This chapter covers the following topics related to Objective 4.4 (Given an incident, apply mitigation techniques or controls to secure an environment) of the CompTIA Security+ SY0-601 certification exam:
Reconfigure endpoint security solutions
Application approved list
Application block list/deny list
Quarantine
Configuration changes
Firewall rules
MDM
DLP
Content filter/URL filter
Update or revoke certificates
Isolation
Containment
Segmentation
SOAR
Runbooks
Playbooks
After a security incident has been stabilized, you, as security administrator, should examine lessons learned to prevent reoccurrences of similar incidents. This includes patching server vulnerabilities, restricting access, training employees, or potentially rolling out technologies to better monitor, alert, and respond to threats. Fixing security flaws or vulnerabilities found during post-incident activities should be a priority, but you should apply mitigation techniques immediately. Finally, you should update your security incident response plan to reflect all these preventive measures and ensure security systems are tuned to avoid missing similar events.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read this entire chapter thoroughly or jump to the “Chapter Review Activities” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 29-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 29-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
|---|---|
Reconfigure Endpoint Security Solutions |
1–3 |
Configuration Changes |
4–5 |
Isolation |
6 |
Containment |
7 |
Segmentation |
8 |
SOAR |
9 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Lists are used in every manner of computer and application access. When you allow an application in your system, what type of list do you use?
Approved list
Block list
Allow list
Deny list
2. A block list or deny list is a basic access control capability that denies specific types of what from executing?
LDAP directories
Applications
API interfaces
Scheduled events
3. What is the main function of the quarantine capability?
To safely submit random files to the cloud
To safely copy suspect files
To safely delete suspect files
To safely store suspect files
4. Which attack vector(s) needs to be considered for mobile platforms?
Hardware
Firmware
Mobile OS
All of these answers are correct.
5. Data loss prevention is a type of which of the following?
Corporate protection of physical assets
Assistance with storage of data
Loss prevention process
End-to-end goal
6. Which of the following is a reason you should isolate a host from the network and other hosts?
Virus, Trojan, or other attack
Operating system defect
Downgrading the OS system
Downloading updates
7. Which of the following are not part of the containment phase?
Change passwords.
Disable network connectivity.
Turn off the display.
Place the infected host in a sandbox.
8. Network segmentation is an approach that divides a network into multiple networks. Which of the following is a benefit of a segmented network?
Smaller broadcast domain
Fewer hosts per segment
Ability to apply granular policies
All of these answers are correct.
9. Which system alerts for suspected phishing emails, endpoint attacks, failed user logins, malware, and other threat information come from a variety of detection sources, such as SIEMs, systems, switches, and logging services?
SOAR
Runbook
Playbook
Content filter
Foundation Topics
Reconfigure Endpoint Security Solutions
Endpoints are among the biggest targets for cybercriminals because these devices are especially vulnerable to various attacks. Criminals often attempt to use endpoint devices as entry points to access corporate networks and steal data, leverage existing software vulnerabilities, or hold information hostage. The most effective practices to detect, respond, and protect your endpoints from these threats include a layered defense-in-depth approach.

Application Approved Lists
Antivirus, firewall, and endpoint security management systems generally have application approved lists, sometimes called application whitelists. If you are currently using a block list, you might consider also implementing an application approved list, one that is centrally managed, which gives you more granular control. Application approved lists are where you spend the time up front building the allow list of approved applications. Then with your central management or endpoint security solution, you roll out the allow list enterprisewide. After an incident, you should spend the time building or updating an application approved list and then enable and enforce it. It will keep users from installing unauthorized applications that could lead to breaches. Figure 29-1 shows a typical approved list in Windows. Each application that is loaded or installed shows up on the list, and you can also import applications. Selecting the box to the left of the application allows you to deny or approve the application.
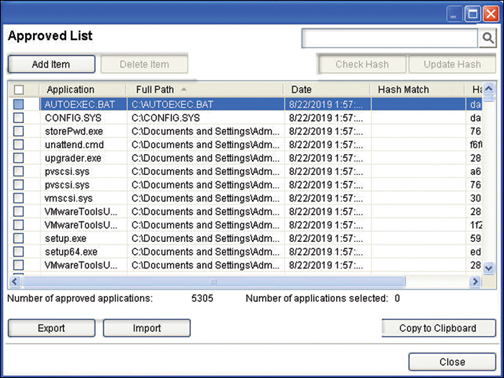
FIGURE 29-1 Windows Application Approved List

Application Block List/Deny List
An application block list or deny list is a basic access control mechanism that denies specific applications or code on the list from being installed or run. After an incident, part of the mitigation strategies should be to review all rogue and unauthorized applications that were installed by the attacker. You can start with these reports to help build your block list/deny list; there are also public block lists you can use to add to your own list. The problem with block lists is the upkeep and maintenance. It’s a simple process for attackers to use renamed or rehashed applications to bypass these lists.
Tip
A block list or deny list provides a list of all applications that the organization deems undesirable or banned and prevents those applications from being installed. An allow list approach uses a list of approved applications. If the application is not on the approved list of software, the application installation is denied or restricted.

Quarantine
The quarantine function is to safely store reported objects such as malware, infected files, or potentially unwanted applications. If Microsoft Defender Antivirus is configured to detect and remediate threats on your device, it quarantines suspicious files. By default, the Microsoft Defender Antivirus virus quarantine storage is located under the following path: C:ProgramDataMicrosoftWindows DefenderQuarantine. Defender creates a threat log during an investigation. This should be one of the places investigators check first for evidence and history of suspect files.
Reverse-engineering these quarantined files can provide insight into the attacker who created, modified, or used the files. After the investigation has wrapped up, the security team should review all files that were quarantined and all those that were missed but eventually were found; reviewing them provides an opportunity to increase the efficacy of the suspect files and increase quarantine. Each antivirus program quarantines its files in different locations. You need to research the antivirus application to locate the files but should be careful when interacting with files in this location.
Figure 29-2 shows the Microsoft Defender Antivirus interface for virus and threat protection, currently running a scan. With managed settings, you can configure multiple items and view logs.
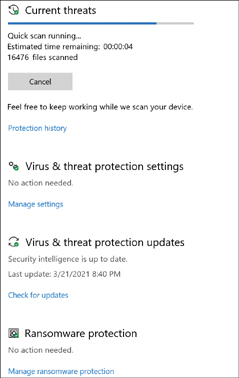
FIGURE 29-2 Microsoft Defender Antivirus Interface for Virus and Threat Protection

Configuration Changes
A flaw in your organization’s security settings, like failing to secure your infrastructure, could leave your entire network and every device connected to it vulnerable to an attack. Configuration vulnerabilities are easily preventable provided secure best practices are followed. Applying mitigation techniques after an incident requires a thorough assessment of all network devices.
Firewall Rules

The firewall was introduced back in 1988, and currently, there are many brands and types of firewalls on the market. These firewalls differ not only in cost but also their functionalities. The firewall at the perimeter of a network is the first line of defense against external attacks. To mitigate the attacks, the firewall divides the network into two zones:
Trusted Zone: Authorized users are in a private network or access a private network.
Least-Trusted Zone: Users from the Internet are trying to access the private network.
The job of the firewall is to either permit or deny the traffic based on the firewall rules. Firewalls filter packets and mitigate attacks; by utilizing best practices and consistent audits before and after attacks, you can reduce exposure and risk. First, you should utilize the National Institute of Standards and Technology (NIST) SP 800-41 guidelines on firewalls. Firewall policies are addressed in Chapter 4 of that document: Chapter 4.1 describes policies based on IP addresses and protocols; Chapter 4.2 addresses policies based on applications; and Chapter 4.3 addresses policies based on user identity. Adherence to the rule of zero trust and least privilege should always be the goal.
TIP
The NIST SP800-41 guidelines for firewalls are located at https://csrc.nist.rip/library/alt-SP800-41-rev1.pdf.

MDM
Mobile device management (MDM) provides functionality and control over enterprise devices by enabling the enrollment of enterprise devices for management functions, such as provisioning devices, tracking inventory, changing configurations, updating, managing applications, and enforcing policies. Unified endpoint management (UEM) expands on MDM by providing unified capabilities and also including content and threat management, identity and access management, and application containerization.
Many organizations administer devices and applications using MDM products/services. MDM primarily deals with segregating corporate data, securing emails, securing corporate documents on devices, enforcing corporate policies, and integrating and managing mobile devices, including laptops and handhelds of various categories. MDM implementations may be either on-premises or cloud-based.
Following are some of the core functions of MDM:
Ensuring that diverse user equipment is configured to a consistent standard/supported set of applications, functions, or corporate policies
Updating equipment, applications, functions, or policies in a scalable manner
Ensuring that users use applications in a consistent and supportable manner
Ensuring that equipment performs consistently
Monitoring and tracking equipment (such as location, status, ownership, activity)
Being able to efficiently diagnose and troubleshoot equipment remotely
MDM functionality can include over-the-air distribution of applications, data, and configuration settings for all types of mobile devices. Most recently, laptops and desktops have been added to the list of systems supported as mobile device management becomes more about basic device management and less about the mobile platform itself. MDM tools are leveraged for both company-owned and employee-owned devices across the enterprise or mobile devices owned by consumers. Consumer demand for bring your own device (BYOD) is now requiring a greater effort for MDM and increased security for both the devices and the enterprise they connect to, especially because employers and employees have different expectations concerning the types of restrictions that should be applied to mobile devices.
Mobile devices are essentially general-purpose computing platforms. They are not restricted to performing one operation and can instead be used in many different fields including medical, industrial, and entertainment. Commercially available mobile devices lack a unified set of features. Each new feature or capability has the potential to introduce new threats to security and privacy. It is important to establish a baseline understanding of the changes that are common to mobile devices. Mobile platforms have several attack vectors that need to be considered: hardware, firmware, mobile OS, applications, and the device combination. Figure 29-3 highlights the various attack vectors on a mobile device.

FIGURE 29-3 Mobile Device Attack Surface
Tip
NIST SP800-124 Rev. 2, Guidelines for Managing the Security of Mobile Devices in the Enterprise is located at https://csrc.nist.gov/publications/detail/sp/800-124/rev-2/draft.
Data Loss Prevention

Data loss prevention (DLP) is an end-to-end goal to make sure that users do not send sensitive or critical information outside the corporate network. The term routinely describes software products that help a network administrator control the data that users can view or transfer. Intellectual property, corporate data, and customer data are some of the types of data you would use a DLP system or software to help protect against exfiltration. These systems, if configured correctly, can also alert you to an unauthorized person (attacker) attempting to transfer data that is classified as sensitive. After an incident, if it is determined that the DLP system not only missed the removal of sensitive documents but did not alert you, you will need to review the policies, restrictions, and alerts that are currently configured and review the attack account to determine what was removed and then document, reconfigure, and test. Your data is not only in your data center but also likely in one or more cloud services. Therefore, you must make sure your DLP system extends to your cloud assets and is enforced. All cloud systems should be considered base components of your data repositories. Because most DLP systems are centrally managed and contain central policies, a routine process should include reviewing and testing each rule. DLP policies can reach down into the endpoint to ensure unauthorized USB thumb drives and other types of unapproved media are disallowed and alerted on. If your DLP solution has these or other capabilities, you should review each item and enforce where corporate policy allows.
TIP
For more information, consult the NIST SP800-171 Rev. 2, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, at https://csrc.nist.gov/publications/detail/sp/800-171/rev-2/final.

Content Filter/URL Filter
Web content filtering is the practice of blocking access to web content that may be deemed offensive or inappropriate, or even contain dangerous items. Often after an investigation you will find that the attacker used a URL or keyword that was not properly blocked, sanitized, or removed from the email or web page; that may have led to the exposure or compromise. Numerous no-cost external third-party lists can help start your base list. Most modern content filter systems should have a subscribe to list that consistently updates the system automatically for questionable URLs and content. On top of that you should add/update the lists to ensure you are blocking sites involved in the compromise. Figure 29-4 shows how a content filter works.

FIGURE 29-4 Content Filter Mechanics
TIP
Although NIST doesn’t have a specific SP dedicated to URL and content filtering, you can find references and best practices in various guides such as NIST SP 800-95 and NIST SP 800-53.

Update or Revoke Certificates
Certificates are among the most important methods for authorizing device access to your network. When one of these systems or hosts has been compromised, lost, stolen, or taken over, it is important to act quickly to remove or revoke the certificate authorizing access. Certificate revocation is the act of invalidating TLS/SSL certificate access before its scheduled expiration date. A certificate should be revoked immediately when its private key shows signs of being compromised. To revoke a certificate from a certificate authority (CA), each system has specific tasks/requirements; in Microsoft, the MMC snap-in allows you to right-click on it in the Issued list, go to All Tasks, and then choose Revoke Certificate. The interface then asks you for a reason code and a timestamp. You enter the data as required and then select OK.
Figure 29-5 shows how a client’s web browser checks the status of the certificate by checking a certificate revocation list (CRL) of the CA.
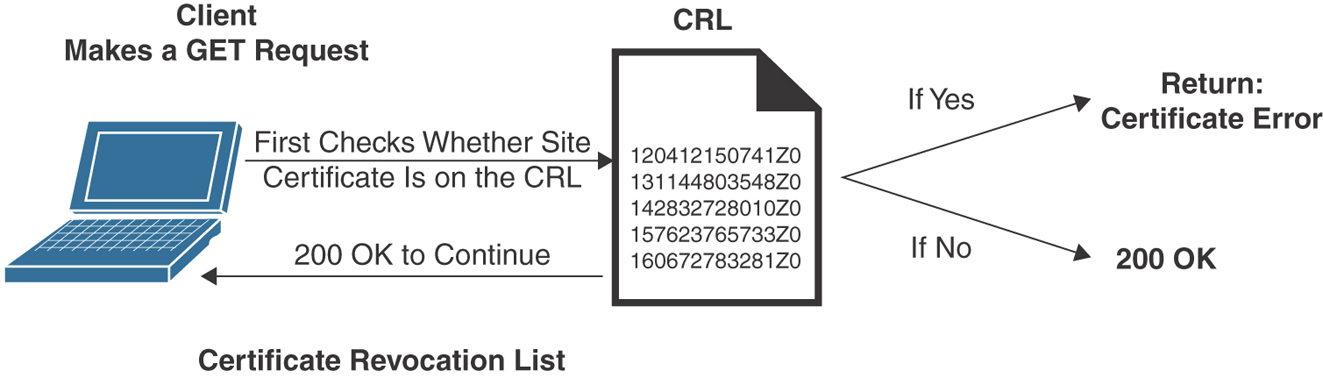
FIGURE 29-5 CRL Checking Process
Tip
RFC5280 details x.509 public key infrastructure certificates and certificate revocation lists. You can find it at https://tools.ietf.org/html/rfc5280.

Isolation
Once a compromised endpoint has been isolated because of malware, a virus, or a Trojan, or it is part of a much wider attack, it is automatically quarantined and isolated or manually isolated. At this point, you should immediately consider three things:
Is there something on this host (private or personal data, or critical evidence) that cannot be obtained from some other source?
Can you safely reimage the device? In other words, can you trust underlying systems, BIOS/UEFI, drivers, firmware, or other operating systems after the reimage?
Can you wait until the investigation is completed before attempting any action?
These questions and corporate policy will help you determine the right course of action. Isolated hosts are good sources of evidence either on the disk/media or in memory, so investigators often want them intact. Investigators can build a list of what was done and how. That list then can be used to help protect these systems in the future. There are ways to isolate a host from the rest of the systems and network so that it can only operate in a sandbox to be observed by analysts and investigators during an incident; this approach allows for greater evidence collection.
TIP
NIST SP 800-123 and SP 800-83 are general guides to server and host security best practices including compromised device isolation. See https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-83r1.pdf.

Containment
When you know where the issue is and what systems have been affected, you should isolate or quarantine those systems so that threats cannot spread through the network. To do this, you need to disable network access for the affected computers and devices, or place them in a sandbox network. Then you need to reset passwords and other credentials, like certificates, and block accounts that seem suspicious or that are not on the list of approved accounts with access. Make sure you don’t delete information that may be useful in forensic investigations, which could help ensure this kind of event does not occur again. After the system has been released, you should run the appropriate measures to recover, remediate, or reimage the system. Ultimately, for a system to have integrity, it is highly recommended that system firmware and BIOS/UEFI be checked and verified and then the system be reimaged.
To perform containment on a system, you disconnect the network connection or disable the port on the switch. If you’re using the system for forensic examination, you create a sandbox network that has faux services like DNS and other hosts to monitor the infected or suspect host.

Segmentation
Network segmentation is an architectural approach that divides a network into multiple networks, subnets, or segments. This segmentation allows network administrators to control the flow of traffic between these networks based on a granular policy. After an incident/investigation has been completed and things return to normal operations, network administrators and engineers should segment high-value networks.
Another type of isolation is more of a secure asset protection segmentation method. In this method, you can use private virtual local-area networks (VLANs) and access control lists (ACLs) to allow only certain hosts in certain networks to talk to other specific hosts, ensuring that device is protected from unwanted access. The inherent weakness of assumed trust is the key reason that many organizations have begun to adopt the zero trust strategy. Zero trust assumes nothing is trustworthy by default, even those already inside the network perimeter.
There are a few types of network segmentation:
Physical segmentation, or separating networks via a firewall or other access controls
Virtual segmentation, where VLANs divide network traffic but devices can still communicate with each other
Figure 29-6 shows network segmentation using firewalls to separate networks. In the middle is a bastion host that both sides can access, typically for sharing files and exchanging data.

FIGURE 29-6 Network Segmentation
Segmenting a network leads to better performance due to less congestion with fewer devices. With fewer hosts per subnet, a segmented network minimizes local traffic and reduces the “noise” in broadcast traffic. Another benefit of a network segmentation policy is that it helps with identification and compliance requirements. One important item to remember after an attack is to split a network into zones that contain data with the same compliance or regulatory rules and restrict access to only authorized IP source addresses.

SOAR
Security Orchestration, Automation, and Response (SOAR) alerts for suspected phishing emails, endpoint attacks, failed user logins, malware, and other threat information that come from a variety of detection sources, such as SIEMs, systems, switches, and logging services. As the SOAR platform aggregates the suspected threats, it automatically triggers a process to inform affected users about the possible threats.
As part of the triage process, the SOAR platform is capable of extracting indicators of compromise (IoCs). The SOAR platform assigns an incident severity value and checks for cross-referencing the data against external threat intelligence databases. If any malicious indicators are found, affected users and administrators are informed with instructions on what to do. The SOAR’s main purpose is to take routine actions and then automate them where a common issue exists, thereby reducing the involvement of an analyst. After an incident, thoroughly reviewing the threat and then building a playbook to respond to that specific item will reduce time to resolution and improve your security posture.
Runbooks

A runbook consists of a series of conditional steps to perform actions such as enriching data, containing threats, and sending notifications automatically as part of the incident response or security operations process. This automation helps accelerate the assessment, investigation, and containment of threats to speed up the overall incident response process. Runbooks can also include human decision-making elements as required, depending on the particular steps needed within the process and the amount of automation the organization is comfortable using. Like playbooks (described in the next section), runbooks can also be used to automatically assign tasks that will be carried out by a human analyst; however, most runbooks are primarily action-based. Figure 29-7 shows a typical automated runbook process flow. When building runbooks, you select components and tie them together to create the desired process flow. Here you can assume a file will be checked as a virus, so you start with the “Start” process. Next, the DNS service does a reverse lookup, potentially obtaining the validity of the file. After that, two processes run: a hash is taken and compared, and the file is submitted to Virus Total to see whether it has previously been reported as a virus. Runbooks can also provide step-by-step processes that a person should follow.

FIGURE 29-7 Automated Runbook Flow
Note
IT operations use a runbook for reference for routine procedures that administrators perform. A playbook normally provides manual orchestration of incident response; newer systems enable you to build and automate runbooks.
Playbooks

A SOAR playbook is a linear-style electronic checklist of required steps and actions needed to successfully respond to specific incident types or threats. Incident response playbooks provide a simple top-down step-by-step approach to orchestration. They help establish formalized incident response processes and procedures within investigations by identifying required steps systematically followed, which can help meet and comply with regulatory requirements. Playbooks support both human and automated actions. An effective use of SOAR playbooks is to document processes and procedures that rely heavily on tasks that humans carry out manually, such as breach notification or highly technical processes such as adding IP addresses to firewalls.
Chapter Review Activities
Use the features in this section to study and review the topics in this chapter.
Review Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 29-2 lists a reference of these key topics and the page number on which each is found.

Table 29-2 Key Topics for Chapter 29
Key Topic Element |
Description |
Page Number |
|---|---|---|
Section |
Application Approved Lists |
822 |
Section |
Application Blocklist/Deny List |
822 |
Section |
Quarantine |
823 |
Section |
Configuration Changes |
824 |
Section |
Firewall Rules |
825 |
Section |
MDM |
825 |
Section |
Data Loss Prevention |
828 |
Section |
Content Filter/URL Filter |
828 |
Section |
Update or Revoke Certificates |
829 |
Section |
Isolation |
830 |
Section |
Containment |
830 |
Section |
Segmentation |
831 |
Section |
SOAR |
832 |
Section |
Runbooks |
833 |
Section |
Playbooks |
834 |
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
mobile device management (MDM)
Review Questions
Answer the following review questions. Check your answers with the answer key in Appendix A.
1. What is the purpose of an application approved list?
2. When a file or application is quarantined, what happens to it?
3. In data loss prevention (DLP) systems, how is exfiltration of sensitive data protected?
4. What is the purpose of revoking a certificate?
5. SOAR requires runbooks and playbooks. Whereas playbooks consist of a number of plays, runbooks are a series of what types of steps?
