CHAPTER 3
Server Operating Systems and Server Roles
In this chapter, you will
• Learn about server roles
• Understand the benefits of virtual servers
• Apply server licensing and installation methods
• Know when to use various server administration methods
• Recognize how scripting can automate server administration
• Understand the importance of asset management and documentation
• Learn about patch management
• Install Windows Server 2019
• Install Ubuntu Linux 20.04.1
Servers are the core of network services. Network operating systems (NOSs) such as UNIX, Linux, and Windows can be used for most standard uses such as file servers, mail servers, and directory servers, but in some cases a line of business application will require a specific platform.
Server Roles
Servers are deployed to offer services that provide some kind of business value to an organization. For example, Domain Name System (DNS) servers provide a name-to-IP address lookup service, mail servers enable communication through e-mail messages, and so on. Planning these roles includes determining whether multiple roles will be co-located on the same server or spread out among multiple servers, which can be physical or virtual.
In the cloud, customers can quickly provision and deprovision virtual servers as needs dictate. Cloud providers such as Microsoft Azure, shown in Figure 3-1, offer virtual machine templates that customers can use to deploy not only the server OS but also additional services, such as a MySQL database server virtual machine.
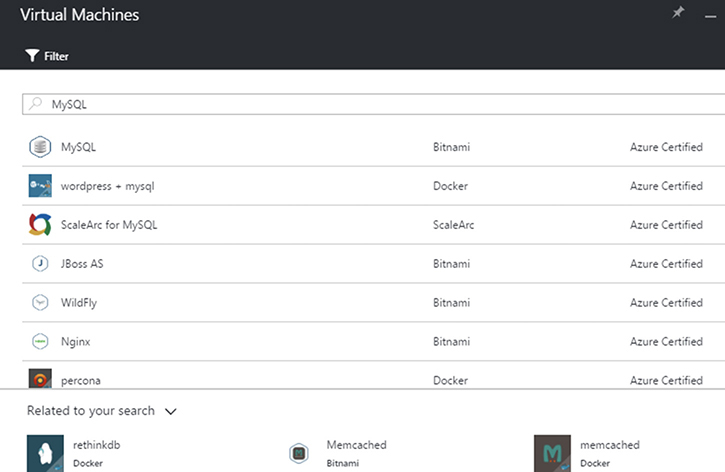
Figure 3-1 Virtual machine templates available in the Microsoft Azure cloud
Cloud virtual machines can offer services not only to other devices running in the cloud but also to Internet consumers and on-premises devices. Connectivity with on-premises devices can be accomplished with the following:
• Site-to-site virtual private network (VPN) connections
• Dedicated connections from on-premises networks to cloud provider networks, bypassing the Internet
After server roles are installed and configured, these services must be enabled to ensure that the service is running when the server comes up. The installation, configuration, and management of server roles vary depending on the specific server OS version. Figure 3-2 shows the Add Roles And Features Wizard that is used to add roles to a Windows server.

Figure 3-2 Installing a Windows server role with the Add Roles And Features Wizard
Infrastructure Roles
The network infrastructure enables devices to communicate with one another. This begins with hardware such as network cables, connectors, routers, switches, network cards, wireless access points, and so on. Then the software components provide network infrastructure services, and this is where our in-depth discussion begins.
DHCP
IPv4 is the standard software communication protocol suite used by modern network devices, although IPv6 is gaining traction. With both IPv4 and IPv6, the Dynamic Host Configuration Protocol (DHCP) is used to provide central IP settings that are delivered to network nodes. This saves technicians from having to configure IP settings manually on each and every device.
Chapter 5 dives into the DHCP packet exchange between DHCP clients and servers. A DHCP server can run on a server OS, or it may run as a service on a router, including a wireless router. DHCP listens for client connections on User Datagram Protocol (UDP) port 67, so firewalls between DHCP clients and servers must allow this traffic to access the DHCP server. Traffic to the DHCP client is addressed to UDP port 68. After the DHCP server role is installed on a server, it must be configured to support the needs of the network, as discussed in the following sections.
DHCP Scopes The first thing that gets configured with DHCP is the scope. Scopes are IP settings grouped together into a manageable unit; they must be activated before they can be used in the DHCP process. Table 3-1 shows common scope settings.

Table 3-1 DHCP Scope Options
DHCP Vendor Classes When communicating with a DHCP server, a network device sends information regarding what type of device it is. For example, a Cisco or Nortel IP phone, an Apple iPhone, Android phone, and HP network printer can all be easily identified. But how is this useful?
DHCP vendor classes, like the one shown in Figure 3-3, let you apply specific IP settings to certain types of network devices. For instance, you could assign an IP address range, default gateway, and DNS server, specifically to Cisco IP phones. This way, your IP phone traffic could be on an isolated network.
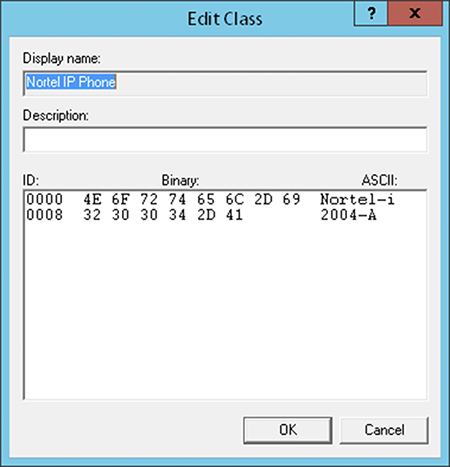
Figure 3-3 DHCP vendor class for Nortel IP phones
You must first determine what specific vendor class data is included in the network transmission. You can find this information by searching the Internet, by visiting the vendor’s web site, or by capturing network traffic related to a specific device type during DHCP transmissions.
APIPA DHCP is a critical infrastructure service, and without it, device communication can be a problem. When DHCP clients can’t reach a DHCP server, they auto-configure themselves using Automatic Private IP Addressing (APIPA).
APIPAs fall in the 169.254.0.1 to 169.254.255.254 range, where 169.254.255.255 is the broadcast address for this network. The client device assigns itself a unique address on the LAN, but the device will not be able to communicate outside of the LAN, and within the LAN it can communicate only with other APIPA hosts. Once DHCP is reachable, the APIPA is no longer used on the network interface.
From the command prompt on a Windows computer, you use the ipconfig command to work with DHCP. The ipconfig /all command shows network details, including whether DHCP is being used, and, if so, the IP address of the DHCP server along with lease information. You’ll find more detail about this in Chapter 5.
IPv6 does something similar, but not exactly the same. A link-local IPv6 address is a unique self-assigned address, but it is always bound to the network interface whether or not DHCP is reachable. Actually, it is used even if you manually configure IPv6 on a host. This type of address has an FE80 network prefix, and it’s used by IPv6 for network communications on the local link, otherwise referred to as a subnet.
When determining the best configuration options for your DHCP scopes, consider the following:
• Talk to the network infrastructure team to determine which valid IPv4 or IPv6 address ranges can be used.
• Environments where clients are connected for short periods of time should have short lease durations to maximize IP address reuse.
• Try to specify at least two default gateways for remote network connectivity in case one router becomes unavailable.
• Try to specify at least two DNS servers in case one becomes unavailable.
• For multihomed (multiple network card) DHCP servers, configure DHCP bindings for the correct network interface.
• Think high availability. What happens if your single DHCP host crashes? Windows servers enable two DHCP hosts to replicate DHCP configuration and lease data between each other.
DNS
DNS is a lookup service, and, much like DHCP, without it, most network communication grinds to a halt. It is most often used to look up an IP address when given a fully qualified domain name (FQDN). Let’s say, for example, that ServerA needs to download updates from windowsupdate.microsoft.com. A DNS query will be sent from ServerA destined for UDP port 53 on ServerA’s configured DNS server. The DNS server will return the IP address for windowsupdate.microsoft.com to ServerA. This is a DNS forward lookup.
Reverse lookups do the opposite: given an IP address in a DNS query, the DNS server looks up and returns the FQDN. This can be useful if you’re looking through firewall logs and notice suspicious activity from a certain IP address and would like to find out the associated host or domain name. Some security appliances can be configured to do this automatically, but at a cost of slowing down the device. Reverse lookups are also commonly used with mail servers as a simple verification method for other connecting Simple Mail Transfer Protocol (SMTP) servers.
DNS Domains DNS is a hierarchy that begins at the top with the root domain. Under the root domain are top-level domains (TLDs) that we’ve all heard of—.com, .org, .net, .mil, .gov, .beer, .uk, and so on—that are maintained by DNS root servers. Figure 3-4 shows the default root hints configured on a Windows DNS server that enable the Windows DNS server to resolve Internet names.
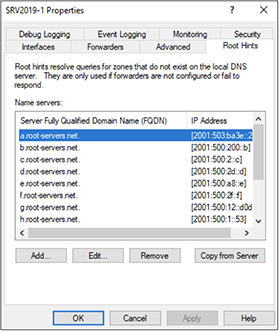
Figure 3-4 Setting Windows DNS server root hints
Companies and individuals can register a unique DNS domain name through a DNS authority such as FreeDNS, GoDaddy, and others. The DNS domain for a company reflects its Internet presence, such as mheducation.com. The internal network for a company might use a different DNS domain name such as mheducation.local. Some services such as Microsoft Active Directory Domain Services (AD DS) require and create a DNS domain in order to function.
A domain, such as mheducation.local, can have subdomains. Examples include sales .mheducation.local and hr.mheducation.local, which could each have data stored on a different DNS server. In this case, a DNS server controlling the data for only mheducation.local is said to be authoritative over the mheducation.local zone. Another DNS server would be authoritative over the sales.mheducation.local zone, and so on.
DNS Resource Records DNS domains contain resource records (RRs), as shown in the DNS Manager screen in Figure 3-5. Different types of RRs are used for different purposes—for example, DNS A records are used to look up IPv4 addresses when a FQDN is provided, and mail exchange (MX) records are used to find SMTP mail servers. Table 3-2 lists common RR types and their uses.

Figure 3-5 DNS resource records from DNS Manager

Table 3-2 DNS Resource Record Types
WINS
Prior to Windows 2000, Microsoft TCP/IP networks relied on the Windows Internet Name Service (WINS) to resolve NetBIOS computer names (maximum 15 characters) to their respective IP addresses. Legacy software may still require this on modern networks, but let’s face it, that would be the exception and not the rule!
WINS is a centralized and replicated database of NetBIOS computer names and their IP addresses; there is no naming hierarchy as there is with DNS. It is installed as a “feature” (as opposed to a “role”) on Windows Server 2019 for backward compatibility. Like DNS, client devices needing WINS must point to the IP address of one or more WINS servers. In the past, client systems each had an LMHOSTS file containing NetBIOS names and IP addresses.
An available alternative is the DNS GlobalNames zone. Instead of WINS, client devices can point to a DNS server, where a zone literally called GlobalNames exists. DNS admins create CNAME (alias) resource records that point to DNS A records. This enables older software using flat computer names to function through DNS.
NTP
Time is of the essence; this is so very true with computer networks, because so many operations depend on accurate date and time stamps. It’s crucial for all devices on the network to agree on the date and the time—log file entries, Microsoft Active Directory (AD) user logon time stamps, and many other activities depend on it!
Network Time Protocol (NTP) is a service that runs on a network host, whether it is UNIX, Linux, Windows, or a Juniper Networks router; it can run on anything, and there are thousands of NTP servers on the Internet. Http://pool.ntp.org is widely used to provide time synchronization for Internet devices.
NTP Tiers NTP is a network service that listens on UDP port 123 for time requests, and there can certainly be more than one NTP server on a network. Different tiers, or stratums, of NTP hosts exist:
• Stratum 0 Time source, or reference clock
• Stratum 1 NTP server connected to Stratum 0 device
• Stratum 2 NTP server gets time over the network from a Stratum 1 host
These stratums imply the delays involved with getting time packets sent over the network in the first place. A Stratum 2 NTP server might be off from UTC time by 10 milliseconds, for example, where a Stratum 1 NTP server might be off by only 1/2 millisecond. Figure 3-6 shows the NTP status on the Windows operating system.

Figure 3-6 Viewing NTP status on a Windows Server
Directory Services
A directory service (DS) is a centralized network database containing objects such as the following:
• Users
• Groups
• Computers
• Network service locators
• Shared folders
• Shared printers
• Software licenses
In the enterprise, this normally means replicating the DS data among servers for redundancy and performance benefits. If one server fails and you’re using DS for user authentication, other remaining servers can handle the authentication. Of course, these DS servers need to be locatable on the network, normally via DNS.
Microsoft network environments tend to use Microsoft AD DS, but there are many other options including OpenLDAP, Oracle Directory Services, and IBM Tivoli Directory Server. These solutions are all based on essentially the same Lightweight Directory Access Protocol (LDAP) standards.
Microsoft Active Directory LDAP provides access to a central network database over an IP network. It listens on TCP ports 389 and 636 (plaintext and encrypted, respectively). Microsoft AD DS, or simply AD, is LDAP-compliant.
AD is a replicated network database that is synchronized between domain controllers (DCs). A DC is a server that is configured to hold a replica of the AD database, which by default lives on the DC at C:WindowsNtdsNtds.dit.
Windows enterprise environments join computers (Windows clients and servers, Linux hosts, and so on) to the AD domain for the purposes of centralized administration (through Group Policies) and centralized authentication. Users with accounts in AD can log on using that account on any domain-joined computer—in other words, we don’t have to create an account for user Bob on every computer with the same password; creating it once in AD suffices.
DCs are discovered by clients through DNS queries. The creation of a DC also creates DNS service location records, which clients use to find the nearest DC. Clients need the DC not only for authentication but also to periodically pull down Group Policy settings configured by the Windows administrator. In other words, AD needs DNS.
AD is a Windows Server role and can be installed and managed using the following:
• Windows PowerShell cmdlets Commands that enable automation
• Server Manager GUI tool on the server or the client
Other Server Roles
We have jobs in IT because we use technology to solve business problems. There are other server roles beyond the basic infrastructure role mentioned so far that you need to understand. Some roles may be on their own server, but you can also co-locate multiple roles on a single server; it depends on the role and the scale of work it will be performing.
Web Server
Web servers use the HyperText Transfer Protocol (HTTP) or its secured variant (HTTPS) to present content to a web browser. The following ports are normally used on a web server:
• TCP 80 Not encrypted
• TCP 443 Encrypted with Transport Layer Security (TLS); Secure Sockets Layer (SSL) is the predecessor and is deprecated
Administrators can choose a different port if they want. The web server transmits data to clients on a higher numbered port such as 45000. If SSL or TLS will be used, a Public Key Infrastructure (PKI) certificate is required for the web server (not clients). Check out Chapter 6 to learn more about crypto and PKI.
Client web browsers normally use DNS to resolve FQDNs to IP addresses; this is so much easier than typing in a difficult-to-remember IP address in the browser’s address bar.
Common web server products include
• Microsoft Internet Information Services (IIS), shown in Figure 3-7

Figure 3-7 Microsoft IIS web server management tool
• Apache
• NGINX (engine X)
Simply stated, a web server listens for HTTP connections and delivers data back to client web browsers. It can become more involved than that, however.
Developers can build static HTML web pages that sit on the web server and are transmitted to clients upon request. Developers can also use server- or client-side scripting languages such as Python (server-side) or JavaScript (client-side) that can dynamically generate page content or take specific actions based on conditions. Client-side scripting is used less often, where possible, because of the security implications of running that code locally on a client computer.
Web server authentication to protected web sites is often performed by an underlying DS, whether the web site is on-premises or in the cloud. Using web Single Sign-On (SSO) means using a single identity store, even between different companies: this is called identity federation.
Application Server
Most of us probably think of database servers when we hear the term “application server.” Although this is partially true, there’s more to application servers than that.
Many people confuse web, database, and application servers. The web server is basically an HTTP engine; it doesn’t address a specific business solution. A database server is essentially a container that could be used for storage and retrieval of relevant data. Now, if our company’s developers build a travel expense application available on the HTTP web server that stores data in a back-end database, we can say we now have an application server; it serves a specific business need.
Common application server database engines include these:
• Microsoft SQL Server
• MySQL
• Oracle Database
If you are building and testing a web application, the cloud comes in quite nicely. It takes very little time to spin up a bunch of virtual machines, some of which are HTTP or database servers. Then once development ceases, you can deprovision these virtual machines so you no longer get charged for them—sounds like a great idea!
File Server
Despite the popularity of cloud storage, file servers are still very important in the enterprise. It’s safe to say that accessing your enterprise network probably performs better than accessing files over the Internet. Sometimes laws or regulations leave us no choice; files must be stored on equipment owned and managed by the company and not a cloud provider.
Windows servers use the Server Message Block (SMB) protocol to make shared folders available to users over the network. Administrators must assign the appropriate share and NTFS file system permissions to access control lists (ACLs) to give user access; you’ll read more on this in Chapter 6.
There are plenty of ways to share folders in Windows (individual files cannot be shared), but here’s how to do it using PowerShell:
![]()
On the client side, we could map a drive letter to the Projects share as follows:
Net use g: \server1projects
Although UNIX and Linux systems can participate in an SMB network using Samba, they can also use their native Network File System (NFS). On the sharing host, the /etc/exports file contains details about which folders clients can mount (only Windows uses drive letters) over the network.
These days, many organizations such as legal firms have turned to document management systems such as Microsoft SharePoint Server or Hummingbird DOCS Open, which make it easy to work with multiple file versions, metadata, and many other document actions.
Print Server
As the name implies, a print server manages the printers on a network. Print servers also spool print jobs from clients using server disk space. Depending on your environment, you may not need or use a print server; instead, client devices can be configured to print directly to network-based printers, but this lack of centralized management control can prove challenging on a larger network.
A print server acts as an intermediary between clients that want to print and the physical printer devices; security and printer settings for many printers can be managed using a centralized administrative tool. Windows shared printers can of course be configured in the GUI by right-clicking a printer name, and they can also be shared using PowerShell as follows:
Set-Printer -Name printer1 -Shared $True -ShareName printer1share
Cloud Printing The idea of cloud printing is to remove any printing dependencies such as operating system versions, print drivers, printing devices, and so on. In addition, cloud printing can be used with mobile devices, which do not offer great printing support—certainly not for a large variety of printing devices.
Many mobile device users save files that they want to print to a cloud storage account that they then access from a laptop or desktop that supports printing. But there’s a better way—cloud printing to the rescue! If your mobile device apps don’t support cloud printing, don’t worry, because there are helper apps for Android, Windows, and iOS devices.
Mail Server
You can run several different types of mail solutions on your server, whether on-premises or in the cloud. They all run as services (or daemons) that enable connections on specific ports, as listed in Table 3-3. Always remember that most network services enable the port number to be changed and that using an encrypted connection means using a different port number.

Table 3-3 Common Mail Protocols
With so many people in the workforce using mobile devices, your mail server will have to accommodate mobile device connections. Of course, the appropriate mobile device e-mail apps will have to be installed and configured correctly.
With bring your own device (BYOD), where employees can use their personal mobile devices for work, mobile device partitioning solutions enable the use of a single mail app for both personal and work e-mail. Most modern mobile device management (MDM) tools support this. Additionally, configurations may, for instance, restrict file attachments from corporate e-mail messages from being stored on personal cloud storage locations. MDM tools can run on-premises or in the cloud.
Routing and Remote Access Service
The server role normally uses at least two network interfaces connected to different networks. Servers with more than one interface are said to be multihomed. Windows server administrators use Routing and Remote Access Service (RRAS) to configure the following:
• IPv4 and IPv6 routing
• Network address translation (NAT)
• Virtual private networks, as shown in Figure 3-8
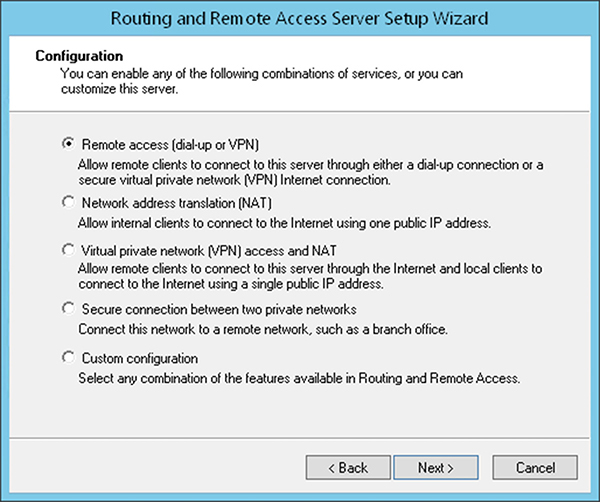
Figure 3-8 RRAS configuration wizard
Say, for example, that you want to configure a NAT router to enable multiple internal stations to access the Internet through a single public IP address. This requires both a public and a private network interface connected to the appropriate networks. Clients simply point to the internal NAT router interface as their default gateway. (For more on IP and default gateways, be sure to devour Chapter 5.) IP routing is used to send network traffic between different subnets. Configuring this requires at least two interfaces in the host.
VPNs enable clients to connect securely to a private destination network over an untrusted network such as the Internet. VPN client software on a device establishes an encrypted tunnel with a VPN host on the work network (must be reachable by clients over the Internet). Anything sent through the tunnel is encrypted. The VPN host then decrypts the traffic and sends it on its way to the Internet network.
Plenty of UNIX and Linux solutions provide RRAS services, including the following:
• IP routing using the ip command
• NAT configuration using the iptables command
• OpenVPN
Virtualization Servers
Virtualization technology (VT) is hot these days, but it’s not new technology. Mainframes have long decoupled applications and user environments from the underlying hardware to enable multiple concurrent isolated computing sessions.
We must also consider the different types of virtualization, including operating system virtualization (this is what most techies think of), user desktop virtualization, application virtualization, and so on. Our focus will be on operating system virtualization.
Common modern virtualization solutions include these:
• VMware vSphere Hypervisor
• Microsoft Hyper-V
• Citrix Hypervisor
• Oracle VM VirtualBox
The combination of slim-profile physical servers (blades) along with running virtual server operating systems maximizes the possible server density in a small server room or a large data center facility. If you monitor hardware use over time for a physical server, in many cases you’ll find that, overall, the hardware isn’t being fully utilized, and you aren’t getting the biggest bang for your buck.
Virtualization is a better use of hardware resources, where multiple virtual machines (VMs) are running simultaneously and sharing the underlying hardware, but each VM doesn’t manage hardware access: that’s the job of the hypervisor.
Hypervisor Types
There are a few types of hypervisors, and each has its place in certain computing environments. One hypervisor might work well on a developer’s laptop, while a different type of hypervisor is best for mission-critical applications. Many companies often use a hybrid of hypervisor solutions. When discussing virtualization, the hypervisor is often called the “host” and each virtual machine is called a “guest.”
Some hypervisors require specific hardware capabilities such as Intel Virtualization Technology (Intel-VT) or AMD Virtualization (AMD-V hardware virtualization support built into the BIOS or UEFI). If you plan on creating a cluster of multiple hypervisor nodes for VM high availability and scalability, moving VMs from one cluster node to another could require physical CPUs to be similar or exactly the same on each node; consult your specific hypervisor documentation to see if this is the case.
Type 1
This type of hypervisor is used for more serious virtualization environments. The hypervisor itself has direct access to physical hardware, and it controls hardware resource access between VMs. You’ll hear this sometimes referred to as a bare-metal hypervisor.
The less stuff running, the quicker it is to patch and the more secure your system. Because Type 1 hypervisors don’t rely on another operating system, they have the benefit of increased security over Type 2 hypervisors.
Examples include
• Microsoft Hyper-V Server
• VMware ESXi
Type 2
This type of hypervisor is an application that runs on top of an existing operating system. This means the hypervisor does not have direct access to hardware; the underlying operating system does.
Examples include
• VMware Workstation Pro (Figure 3-9)

Figure 3-9 VMware Workstation, a Type 2 hypervisor
• Oracle VM VirtualBox
Hypervisor Host Configuration
Running a bunch of VMs at the same time on one set of hardware requires careful planning. It’s not really about the number of VMs (VM density), but rather what type of IT workloads will be running inside those VMs. An SMB file server used by 50 people, for example, won’t need as much horsepower as a Microsoft SharePoint Server used by 5000 people.
Let’s take a look at planning physical hardware for a Type 1 hypervisor in Table 3-4. Remember to read the documentation for your specific solution to see what is and is not supported. For further hardware details refer back to Chapter 2.
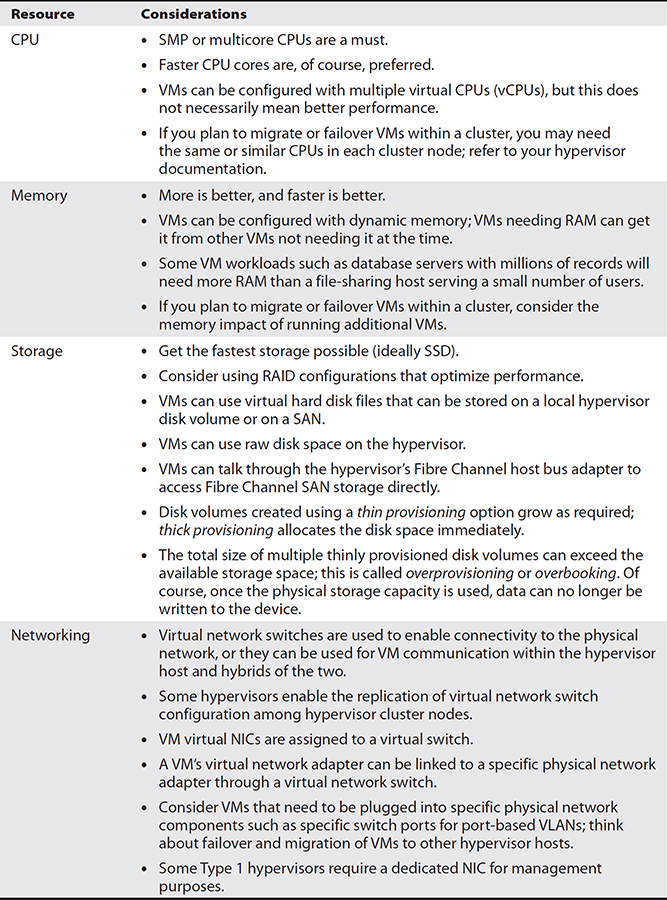
Table 3-4 Type 1 Hypervisor Hardware
Virtual Machine Guest Configuration
Creating a VM (not installing the OS) is like planning the physical hardware for a new server. How much memory, CPU, disk, and network capacity do you need? The answer, of course, depends on the IT workload the server will be running.
VM settings, as shown in Figure 3-10, include the following:

Figure 3-10 Virtual machine settings
• Amount of startup, minimum and maximum, and dynamic memory
• Number of vCPUs and compatibility settings
• Storage such as virtual hard disk files, raw disk space, and SAN storage
• Virtual network interface cards (vNICs) and their connected virtual switches, virtual MAC address, network bandwidth throttling, and VLAN tag settings:
• Bridging Connects to the physical network
• NAT Uses the hypervisor host IP address to access the network
• VM to VM Enables communication only between VMs
• VM and host Enables communications between VMs and the hypervisor host
• Display settings for number of monitors and accelerated graphics
• Integration tools with the host hypervisor for time synchronization, backup services, and so on
• Snapshot/checkpoint settings
Some virtualization solutions provide an integration tools installer that optimizes VM display settings, keyboard and mouse movement, time synchronization with the host, and other settings. Check your hypervisor’s details to make sure you’re getting the most out of your VMs.
Server Installation
Hardware compatibility lists (HCLs) provide details about which specific hardware is supported by a given server OS. You also have to consider the requirements for specific drivers and applications. You may have to supply device drivers during installation if they aren’t detected by the installation program. Server OS minimum requirements must be met, such as Windows Server 2019 requiring a minimum of 2 GB of RAM for a server with the GUI Desktop Experience installation. The crucial aspect of this is ensuring that adequate hardware resources exist to support server workloads.
Server Licensing
Installing and managing servers includes acquiring and tracking software licensing. Open-source licensing applies to some software such as Ubuntu Linux, where the use of default Ubuntu software does not incur a licensing fee, but there are some requirements such as sharing code modifications with the Linux community. Even though some open-source solutions are free, technical support is not.
Some licensing models are based on the server itself (per-server) or in some cases specific to virtual machine server instances (per-instance). For larger enterprises, you can configure a licensing server such as Microsoft Key Management Service (KMS) server that issues and tracks licenses for an entire site. Of course, valid server licenses would have to be made available on this licensing server. This is often accomplished with volume licensing, where a single key can be used to activate a large number of products from a vendor.
Some software such as Microsoft SQL Server use per-core licensing, where a physical or virtual CPU consists of one more CPU cores. Some products apply licensing at the physical CPU socket level, so more physical CPUs means more compute power but also more licensing costs. Some vendor software licensing models, such as the one for Ansys 3D design software, supports current and older versions and sometimes future versions of software, so license backward and forward compatibility is something to consider where applicable.
Subscription-based licensing, such as with cloud solutions Amazon Web Services or Microsoft Office 365, focuses primary on charging customers monthly or annually for the amount of cloud resources used. In the Microsoft Azure cloud, for example, you pay for Windows virtual machines only when they are running (there is a small cost associated with the storage of virtual machine disks in the cloud).
Per-user concurrent licensing applies to the number of users connected to a network server or service at any given time. A five-user license means up to five users can use the software at the same time. Once those users log out, new users can connect to the software up to a maximum of five at a time.
Other licensing options include those tied to a specific device often through a USB hardware key, otherwise called node-locked licenses because they are tied to a specific node. Signature-based licensing is often used with digital rights management (DRM) for gaming or the use of media files: the server issues a signed license, and the client device verifies the signature’s validity before adding the license to the device.
Installing a Type 1 Hypervisor
Most modern Type 1 hypervisors require 64-bit architecture as well as hardware virtualization support. If you’re using true server-class hardware, this won’t be an issue. If you’re testing the hypervisor using standard desktop hardware, you need to be extra careful.
Firmware updates (such as BIOS or the Unified Extensible Firmware Interface [UEFI]) may be required prior to installation, even for indirect reasons, such as network Preboot Execution Environment (PXE) boot, USB device boot support, and so on. If you plan on installing the hypervisor from a DVD or USB, you may also have to change the boot order configuration on your machine.
Installing a Server Operating System
Whether you want to end up with a physical or virtual server OS, there isn’t much difference in the actual OS installation itself.
Common server operating systems include
• Microsoft Windows Server
• Microsoft Windows Server Embedded (for purpose-specific hardware appliances)
• UNIX variants such as BSD, AIX, and Solaris
• Linux variants such as Red Hat, Ubuntu, and SUSE Linux
Keep in mind that many modern OSs have just the bare minimum available with a default installation. You may have to install and enable additional services such as file sharing and web servers.
Server Installation
You can begin the server OS installation from a CD-ROM, a DVD, a USB device, or a shared folder over the network—one way or another, you need access to the installation files. Many on-premises and cloud environments use VM images to create new VMs, but there are many legitimate cases for which you’ll be installing the OS on physical hardware (often called a bare metal installation) and not a virtual machine. This chapter includes lab exercises that step through the installation of a Windows server and a Linux server in VMware Workstation Pro.
Server Installation from an Image
Server OS images may have been already created; in that case, you can apply the image to your new physical or virtual server instead of running the installer from the installation media. You can create and apply server OS images using tools such as these:
• Ghost Solution Suite
• Microsoft System Center Configuration Manager
• Microsoft Deployment Toolkit
• Microsoft DISM.exe command line tool
For example, we can capture a server OS image by booting from alternative media and using DISM:
![]()
In this example, we are capturing an image of c: and storing it on drive e: (presumably an external USB drive).
We can apply an image by booting from alternative media, including booting over the network, using the following:
dism /Apply-Image /Imagefile:e:Imageswin2019.wim /index:1 /ApplyDir:c:
Because multiple images can be stored using the Windows Imaging Format (WIM), we specify the image with the /index parameter. WIM requires the disk to be partitioned and formatted prior to the application of an image.
Server Cloning
The previously mentioned install methods work on physical servers and also for creating virtual machines, but there are a few additional virtual machine options to consider.
You can clone a physical or virtual machine if you have the right tools. For example, VMware Workstation Pro has a built-in virtual machine cloning option that copies one virtual machine to a new one. This can be quicker than other installation methods if the new server should be very similar to the original virtual machine.
When cloning, you may be given the option to create a linked clone, which uses minimal disk space but is linked to the original virtual machine, or you can create a fully independent clone that uses more disk space but is not linked to the original virtual machine. Linked cloned virtual machine changes made after the clone is created are independent from the original virtual machine. Linked clones work well when you need multiple virtual machines using the same standard OS configuration initially.
Physical-to-virtual (P2V) cloning uses a physical server as the source but results in a virtual machine with the same settings. Some tools such as the VMware vCenter Converter utility require a P2V agent to be installed within the physical server OS to read settings.
Virtual Machine Deployment Templates
By using a server deployment template, you can partially or fully automate virtual server deployment. This is true for both on-premises machines and in the public cloud.
Virtual machine templates specify virtual hardware details, OS options, network settings, and so on. This facilitates and expedites the server provisioning process. You can use tools such as Microsoft System Center Virtual Machine Manager (VMM) or VMware vCenter in an on-premises environment to achieve this.
In the public cloud, a deployment template can, once again, partially or fully automate virtual server provisioning. Microsoft Azure uses Azure Resource Manager (ARM) templates to this effect, while in Amazon Web Services (AWS), this is referred to as a CloudFormation template. These types of templates can deploy not only virtual servers but any other type of cloud resource such as databases, web applications, load balancers, and so on.
Scripted Server Installations
Whether you are applying an image or installing from source media, you can also create an answer file to automate some or all of the OS installation. Red Hat Enterprise Linux 8, for example, uses Kickstart files to automate installations.
Automating a Windows server installation can be done with the unattend.xml file created using the Windows Systems Image Manager (SIM), which is a tool included with the Windows Assessment and Deployment Kit (Windows ADK). If you want the answer file read automatically when installing the Windows OS, name it autounattend.xml and place the file on the root of removable media such as a USB thumb drive.
Local vs. PXE
In addition to performing the server OS installation from local media (setup.exe for Windows server installations) or a locally stored image, you can also boot over the network from a PXE. Figure 3-11 shows a PXE boot screen. PXE booting enables OS installation from the installation files, or you can apply an OS image. Prior to installing the server OS from installation media, you can apply updates to the source installation files using a process known as slipstreaming.

Figure 3-11 PXE boot screen
PXE must be supported by the physical or virtual machine’s BIOS or UEFI settings and the NIC itself, and you need a PXE boot server listening on the network. Microsoft Remote Installation Services (RIS) and the newer Windows Deployment Services (WDS) provide this functionality, although there are many vendor solutions out there.
The great thing about PXE installation/imaging is that technicians don’t have to carry around storage devices containing installation files or OS images. The downside is that you’re pulling the OS down to the machine over the network, so network bandwidth use goes up.
PXE boot relies on DHCP to assign IP settings to PXE clients, and it also uses Trivial File Transfer Protocol (TFTP) to download a small boot image OS used for installation and imaging.
Installation Details
When you are actually installing a server OS, if it’s not an automated installation, you may be asked to supply the following:
• Disk layout, including disk partitioning, file system formats, and swap file/partition
• Server name
• IP configuration settings
• Administrative user credentials
• Additional drivers for nonstandard hardware
• Product key or subscription details used to activate the installation and receive updates
• Additional software that should be installed
All of these items can be specified in the Windows unattend.xml and autounattend.xml files for scripted installations.
Server Administration Methods
A Windows Server 2019 installation does not have to have a GUI; this is called a Server Core installation, and it includes a command line environment. Modern Linux distributions support a GUI and offer the technician the option to install it during the installation process.
If you have physical access and the required management permissions to a server, you can manage it locally using command line or GUI tools. Some servers and network devices will allow local access through a local physical serial port where the technician could use a tool such as PuTTY to make a console connection through the port to issue commands.
Windows servers and clients with a GUI can use the Microsoft Management Console (MMC), which is a general tool that enables you to add snap-ins for specific management capabilities. For example, you might run mmc.exe and add the snap-in for Group Policy and certificate management.
You can use GUI tools installed on a client workstation to administer servers remotely over the network. In the case of Windows servers, administrators can download the Remote Server Administration Tools (RSAT) to accomplish this. In Figure 3-12, RSAT tools are being enabled on a client machine.
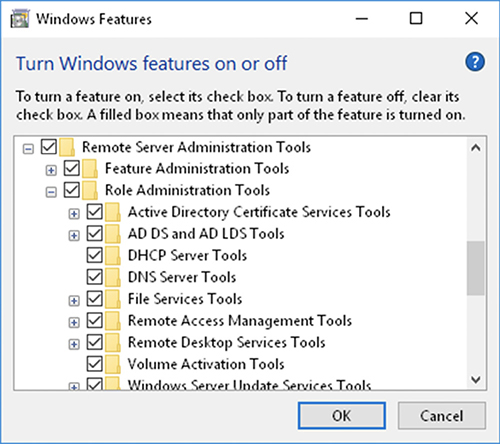
Figure 3-12 Enabling RSAT tools on a Windows client machine
KVM
Instead of having a separate display, keyboard, and mouse for each individual physical server, KVM (keyboard, video, mouse) switches connect the servers to a single display, keyboard, and mouse. You can switch to different servers to manage them locally.
Keyboards and mice have different interfaces; modern devices use USBs, but older input devices use PS/2 or serial connectors. For video, older displays use Video Graphics Array (VGA) connectors, while newer displays use High-Definition Multimedia Interface (HDMI) for both video and audio. Make sure your KVM solution matches the connectors for your devices, or you’ll have to buy adapters to get everything plugged in.
Out-of-Band Remote Administration
Physical and virtual servers must be accessible over the network for management purposes. Although there are plenty of software-based remote management solutions, hardware-based solutions provide more security and reliability. Out-of-band administration provides hardware-level remote access to a host without relying on the OS software running.
Web-Based Enterprise Management (WBEM) is a standardized way of managing and monitoring services and devices from different vendors. Of course, many vendors have their own proprietary management and monitoring tools.
The monitoring of server components such as CPU use, temperature, OS health, and so on, falls under the umbrella of lights-out management (LOM), a remote management solution supported by most vendors.
KVM over IP
These days, a KVM also works over IP (IP KVM or KVM over IP). This enables remote server access even over the Internet, and it can enable hardware-level (out-of-band) remote access if that is supported by your server hardware.
KVM-over-IP switches are hardware appliances with centralized management and auditing tools. For instance, a KVM can require its own authentication in addition to whatever is required by servers themselves.
Traditional software-based remote management solutions such as Virtual Network Computing (VNC), Remote Desktop Protocol (RDP), and Secure Shell (SSH) all depend on the OS function. But what if the system crashes? IP KVM can overcome this, but, again, physical servers must support this out-of-band type of hardware remote management. It also means TCP/IP settings must be configured at the hardware level to enable remote access across WANs.
IPMI
The Intelligent Platform Management Interface (IPMI) is a remote server management solution commonly used with various vendor blade enclosures. Management capabilities include remote power on and power off and disk access, all through out-of-band management. IPMI also provides server monitoring and inventory functionality.
A baseboard management controller (BMC) is the interface between server management tools and the physical server hardware being managed. Server administrators can connect to IPMI management systems locally or over a network.
iLO and iDRAC
Hewlett-Packard’s out-of-band solution is Integrated Lights Out (iLO) management. The iLO solution offers not only secure remote management capabilities, including remote power on and power off, but it also includes server monitoring and alert capabilities.
For hardware-based out-of-band management, Dell servers support Integrated Dell Remote Access (iDRAC). Administrators can connect to remote servers at the hardware level, even using a friendly web browser interface from which a virtual server console can be accessed, which enables remote power on, power off, and access to server storage media. The virtual media option enables administrators to configure the physical server to use media on the technician’s remote administration station for installing software and applying updates.
In-Band Remote Administration
In-band remote management relies on software running within the OS. If the OS hangs, remote management of this type no longer works. Although each OS has its own remote management solutions, you can also use the cross-platform VNC remote control tool.
Many tools use the Simple Network Management Protocol (SNMP) to query management information bases (MIBs) on devices. MIBs are used to gather inventory and statistic data about network devices.
SSH
SSH has long been the standard and secure way of remotely managing not only UNIX and Linux hosts but also network devices such as switches and routers. It supersedes the insecure Telnet protocol, which sends credentials in plaintext.
SSH needs a server-side listener for clients to be able to connect; the standard listening port is TCP 22. Although SSH is normally used for command line remote management, X-forwarding can be enabled within SSH to redirect graphical UNIX and Linux applications to show up on the client computer. In other words, you can interact with UNIX and Linux GUI apps on your Windows client station.
Besides the standard username and password authentication, SSH can also use public-key authentication. An administrator’s public key is stored on the SSH host, and the mathematically related private key is stored on the administrator’s workstation. The keys are used to authenticate the admin to the SSH host.
You can download and configure a free PuTTY tool to make SSH connections to network devices including UNIX and Linux hosts from within a Windows environment, as shown in Figure 3-13.

Figure 3-13 Configuring PuTTY for SSH remote administration
RDP
Windows hosts normally use the Remote Desktop Protocol (RDP) for remote management of both Windows clients and servers. RDP listens on UDP and TCP port 3389 by default.
Newer versions of the Windows Server OSs support Network Level Authentication (NLA) for RDP sessions. NLA improves on older versions of RDP in the following ways:
• Entering the username and password uses client resources, not server resources.
• RDP sessions are encrypted with an SSL certificate.
Figure 3-14 shows how RDP gives admins the ability to access a Windows server remotely to run GUI management tools—but what if the server is installed as Server Core? Server Core is a Windows server option that does not include the GUI. When admins RDP into Server Core, they simply get a command prompt.

Figure 3-14 Connecting to a Windows host using RDP for remote management
WinRM and PowerShell
Windows admins can also use PowerShell to manage Windows servers remotely at the command line. PowerShell depends on the Windows Remote Management (WinRM) service to be configured, to run, and to be accessible through firewalls. Newer versions of WinRM use TCP ports 5985 and 5986 for unencrypted and encrypted connections, respectively.
Outside of PowerShell, you can use the Windows winrs command to execute commands remotely on a Windows host, but you need to ensure that WinRM has been enabled. This can be done via a Group Policy or by using the winrm qc command. You could use winrs with -r to specify the remote host as follows:
Winrs /r:Server1 dir c:
This example will list items on c: on Server1.
Consider the three PowerShell remote management examples in Table 3-5.
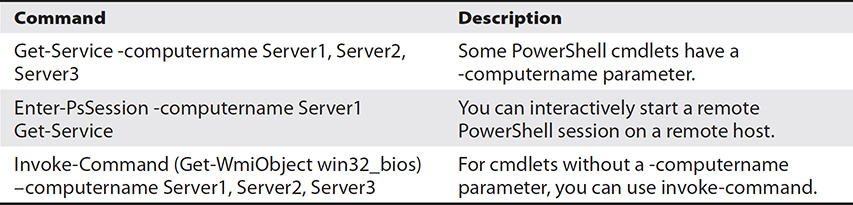
Table 3-5 PowerShell Remote Management Examples
Additionally, PowerShell Desired State Configuration (DSC) enables administrators to configure and manage Windows and Linux hosts centrally using a declarative syntax, as shown in the following example:

This would be placed in a PowerShell script. It ensures that the Windows IIS web server is installed, and if not, it will be. PowerShell DSC can even be used to manage cloud virtual machines.
Automating Server Administration with Scripting
Scripting provides a method of automating server administration by placing commands in one or more script files and then invoking the script file or having the script invoked automatically during the machine bootstrap process. Scripts can automate just about anything, such as server or service startup, shutdown, logging in to remote hosts, and user account management. There are four widely used script types, listed in Table 3-6.
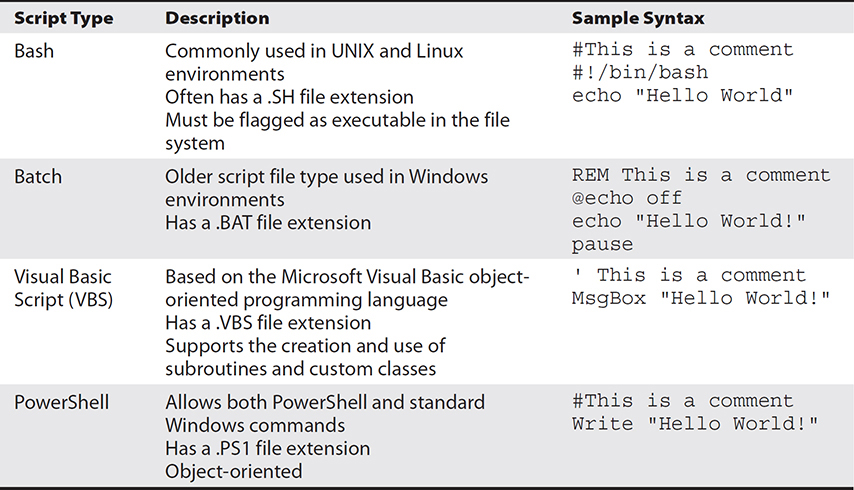
Table 3-6 Common Mail Protocols
Scripts can reference environment variables, such as the currently logged on username. When you’re reading and writing variables in PowerShell, the variable name must be prefixed with a dollar sign ($). You can also set the data type of a variable, such as an integer, a string value, an array, or a date time value. Data types vary depending on the type of scripting language being used. Consider the following PowerShell examples with their descriptive comments:
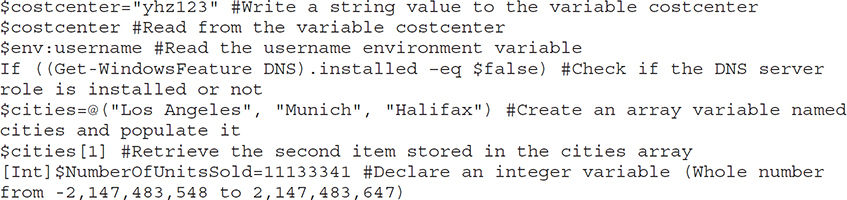
You can execute script commands repetitively in a loop until a certain condition is met. There are various looping constructs, including a while loop, which executes until a condition is met, and a for loop, which is normally used when you know how many times the loop should execute. The following PowerShell example uses a for loop to display city names stored in the array variable $cities:
ForEach ($city in $cities){$city}
Server Documentation
If you’ve ever done IT consulting, you know that accurate and readily available documentation saves everybody time and money. Troubleshooting a server that isn’t performing well takes much longer when you know nothing about how the server is configured. Vendor service manuals are a great troubleshooting starting point when it comes to hardware misconfigurations.
Each server needs documentation and a change log, and, ideally, this is all automated and inventoried in a database somewhere that is easily searched. Aside from OEM hardware and software service manuals, we need to know how these technological solutions have been put in place in a specific environment. How companies implement technology is sensitive information. This is a big part of reconnaissance when malicious users try to learn about a network to identify vulnerabilities. That’s why it’s important to keep this documentation under lock and key, and encrypt any files containing this stuff.
Asset Life Cycle
On-premises servers, and even cloud servers running critical IT systems, are assets in the sense that we must apply a risk-management framework to them to protect them throughout their useful life. Here’s an example of a server life cycle:
1. Provision servers and their IT workloads.
• Procurement of servers on-premises or the cloud
2. Configure servers and their IT workloads.
• Manually or automatic
3. Manage servers and their IT workloads.
• Security
• Patching
• Compliance with laws/regulations
• Change management policy and forms
4. Monitor servers and their IT workloads.
• Ensure peak performance
• Provide centralized monitoring and logging
5. Decommission servers when they have reached end of life.
• Proper disposal techniques
• Physical destruction
• Sanitize/wipe media
6. Upgrade or functionally replace IT workloads.
Asset Inventory
Until the 1990s, very few automated asset inventory options were available for IT environments. Long were the days spent crouching under desks and behind server racks to inventory equipment physically and to document configuration settings.
These days, all of this can be automated and is readily accessible for small, medium-sized, and large enterprises. Even so, physical equipment still needs to be labeled or inscribed for tracking purposes. Inventorying servers falls into two categories: hardware and software.
Hardware Inventory
We can’t troubleshoot, optimize, or upgrade something if we don’t know what we have to begin with—we have no reference point! Even virtual machines have “virtual hardware.” This can be very useful when you’re optimizing and troubleshooting, both of which are covered later in the book.
Server items that may be inventoried include the following:
• Make, model, and serial number
• Whether the physical server is owned or leased
• Motherboard and device serial numbers
• Physical or digital asset tag (on a sticker or stored in the BIOS)
• RAM
• Storage
• Network interfaces
• Other peripherals
• Printers
• USB devices other than storage
• Monitor displays
Here are some reasons for creating a detailed and accurate hardware inventory:
• Inventory audits
• Asset tracking
• Determine asset use
• Asset repair and warranty
• Asset recall
• Asset security
Solutions provided by Spiceworks, Altiris, or Microsoft System Center Configuration Manager (SCCM) (see Figure 3-15), for example, provide ways to inventory devices on a large scale, such as in a data center. Inventory solutions may or may not have a software agent running within the OS; more detail is available when an agent is used, since it knows everything about that specific server. Inventory scanning schedules determine whether inventory data is up-to-date. Running queries or reports against inventory data stored in a database makes managing server assets easier.
Figure 3-15 SCCM hardware inventory for a Windows computer
In a data center with thousands of pieces of IT equipment, inventorying and monitoring are easier when radiofrequency identification (RFID) tags are used. RFID mobile reading devices scan items with RFID tags in close proximity—so, for instance, rack-mounted servers could have RFID tags adhered to the front of the servers for ease in scanning.
Software Inventory
Knowing the specific versions of operating systems, drivers, and application software in use is critical. Let’s say, for example, that a software vendor has released a critical security update that needs to be applied immediately. If you don’t know how many servers are running the affected software, you can’t even determine the scope of the work required! Software license compliance is also important; licenses can be inventoried and you can reconcile this against purchased licenses (this is called a true up).
Similar to hardware inventory, software inventory can and should be automated on a scheduled basis. Using the same type of enterprise tools used for hardware inventory (Spiceworks, Altiris, and SCCM, to name a few) allows for automation. You can then run queries and reports against inventoried software. As another example, you may want to know how many instances of a version of a certain server OS are running on your network to ensure license compliance, or you may want to know how many devices do not have the required configuration to support an application, in which case new hardware may need to be procured.
Service Level Agreements
A service level agreement (SLA) is a contract outlining expected service from a service provider to a service consumer. This could exist between your company and a public cloud provider, or you might use SLAs within an organization between business units and the services offered by the IT department. When things go wrong, the SLA can be very valuable.
The two most common items found in SLAs are
• Uptime
• This specifies expected availability for IT services.
• Providers are usually obligated to notify clients of scheduled maintenance and downtime.
• Response time
• This specifies how quickly IT services respond when they are needed.
• This can also specify how quickly the provider responds when you need support.
• How long will it take for a problem to be resolved?
• Is support available only during business hours?
When providers fail to meet SLA expectations, they may offer credits of some kind, and you should determine whether there is a maximum number associated with this. It’s a good idea to ensure that the SLA includes a clause for leaving a provider if it chronically fails to meet thresholds documented in the SLA.
All of the responsibility, however, isn’t just on the provider. As an IT service consumer, you may have to adhere to certain rules, such as how servers are configured and used and which updates and software components are allowed on servers.
Other Documentation
Documentation goes beyond just servers. Servers live in a technological ecosystem that affects them, so there are other factors to consider:
• Network infrastructure diagrams Server placement
• Workflow, dataflow, and application architecture diagrams Server involvement in data movement, processing, and storage
• Baseline documentation Normal operating conditions and troubleshooting, including required patches (see Chapter 7)
• Recovery documentation Policies and procedures to return the server to an operational state as quickly as possible (see Chapter 8)
Much can be learned about server and IT workload configurations by checking log files. Most UNIX and Linux variants store log files in the /var directory. Windows logs are accessible using the GUI event viewer tool or PowerShell cmdlets such as Get-eventlog.
If Group Policy is used heavily in your environment, it can be helpful to get a complete report of all Group Policy Objects (GPOs) and their settings. One quick way of achieving this is as follows:
Get-gporeport -all -reporttype html c:gpo_report.html
This example retrieves all GPO settings linked to all AD organizational units (OUs) and puts them into a nicely formatted HTML document.
Maintaining Servers
With inventory in place, server maintenance becomes easier through automated inventory and documentation. Proactive management also includes ensuring that firmware and software patches are delivered in a timely fashion. Then we need reports that can confirm that patches have been successfully applied. Of course, we’ll also know all of this because of frequent software inventory scans on our servers.
Patch Management
UNIX and Linux variants sometimes require a subscription before updates can be applied, just like Windows Server OSs require activation before all updates are available.
There are different types of updates. Some are critical security updates that must be applied right away, while others add additional functionality to software. This also holds true for firmware updates for motherboard BIOS/UEFI, printer firmware, router firmware, and so on.
Imagine a data center with 1000 hypervisor operating systems, which, of course, will need updates on a continuous basis. Instead of each of those 1000 systems downloading the same updates, we can configure centralized update management and then run reports on update compliance.
Windows Server Update Services (WSUS) is a free Microsoft patch-management tool that has been available for years. Microsoft SCCM uses WSUS to manage and deploy patches using the SSCM infrastructure. Updated metadata is synchronized from either Microsoft update servers online or from another WSUS server. Updates can be applied manually or on a scheduled basis to a group of computers.
Deploying and managing non-Microsoft updates in a Windows environment can be done using tools such as Microsoft System Center Updates Publisher (SCUP) or other vendor-specific solutions.
Proactive Maintenance
At this point, you know that hardware and software inventory, patching, and various types of documentation can help ease server management over time, but there are other factors to consider as well.
Sometimes the simplest physical issues can make a big difference with IT computing. Servers need to be kept clear of dust, with no obstructions near intake fans. And they must be kept cool; overheating servers could cause performance degradation (CPU throttling to slow down speed, which reduces heat), or worse—server power-downs.
Speaking of server power-downs, servers should be plugged into uninterruptible power supplies (UPSs) to ensure the graceful shutdown of servers when the power goes out. You’ll find more about UPSs in Chapter 8.
Reactive Maintenance
Despite the best-laid proactive plans, sometimes we have to react quickly to certain events when managing servers. Chapter 8 provides details, but there are a few everyday things you should keep in mind:
• LED indicators on equipment such as servers, UPS systems, and storage arrays
• Indicates problems as well as normal status messages
• Failing disk arrays, RAM errors, problems with batteries or backplanes, and so on
• Error and beep codes
• Vendor equipment with specific error and beep codes
• Warning of some kind, such as imminent drive failure
Hands-on Exercises
Exercise 3-1: Install the Microsoft Windows Server 2019 Operating System
1. Start VMware Workstation Pro and ensure that the Srv2019-1 virtual machine you created in Chapter 2 is open.
2. In the navigation panel on the left, click Edit Virtual Machine Settings. On the left side of the screen, notice that the Network Adapter is configured for NAT. This enables the virtual machine to communicate on your network (and potentially the Internet if you have an Internet connection) while using its own unique IP addressing scheme.
3. Click CD/DVD, and then, on the right, click Use ISO Image File. Click Browse and select the Windows Server 2019 Trial ISO File Downloaded, as per the instructions in Appendix A, and click Open. Within Device Status, check the Connect At Power On option if not already enabled. Click OK.
4. In the navigation panel on the left, click Power On This Virtual Machine, click in the virtual machine screen, and press ENTER when presented with the Press Any Key To Boot From CD Or DVD message.
5. In the Windows Setup dialog box, accept the defaults and click Next.
6. Click Install Now.
7. From the list of operating systems to install, choose the second option, Windows Server 2019 Standard Evaluation (Desktop Experience), and then click Next.
8. Accept the license terms and click Next.
9. On the installation type screen, in the Which Type Of Installation Do You Want? dialog, choose Custom: Install Windows Only (Advanced).
10. You will then see the four virtual hard disks you created in Chapter 2 in Exercise 2-2. Ensure that Disk 0 Unallocated Space is selected, and then click Next.
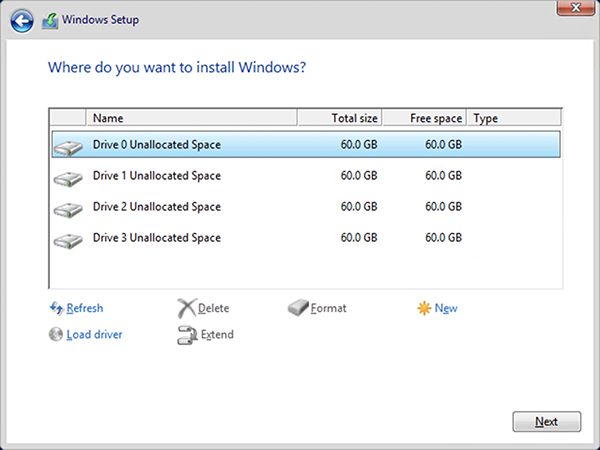
11. Windows begins copying files. This is a good time to get a cup of coffee, but be quick! Depending on your machine, this part of the install may take only 2 or 3 minutes.
12. The installation will reboot your virtual machine automatically and continue the installation. You will be prompted to specify the administrator password. Enter Pa$$w0rd172hfX and click Finish. For production environments, always adhere to organizational security policies related to the use of strong passwords. This password is used only for testing purposes.
13. After a moment the server login screen is displayed. From the VMware VM menu, choose Send Ctrl+Alt+Del and enter the Administrator password, Pa$$w0rd172hfX. Then press ENTER. The server desktop is displayed and the Server Manager tool automatically launches. If you get a network message about finding PCs, devices, and so on, click Yes. If you get a message stating to Try Managing Servers With Windows Admin Center, check the box next to Don’t Show This Message Again and then click the X to close the dialog box.
14. Configure Server Manager not to start automatically: In Server Manager, choose Manage | Server Manager Properties. Check the box that says Do Not Start Server Manager Automatically At Logon. Click OK, and then close Server Manager.
Add a second network adapter for the server
15. From the VMware VM menu, choose Settings.
16. Click Add at the bottom of the screen, choose Network Adapter, and then click Finish.
17. Choose Custom: Specific Virtual Network and choose VMnet5 from the drop-down list. Click OK. If prompted with hints, turn them off and continue. Your virtual machine screen may be blank for a few seconds as the change is put into effect.
Configure a static IP4 address for the server
18. If you can’t see the Windows Start menu icon at the bottom left of the screen, from the VMware View menu, choose Stretch Guest, and then choose Keep Aspect Ratio Stretch. Or, from the Start menu, select Control Panel, and then select Network And Internet. Click Network And Sharing Center.
19. On the left, click Change Adapter Settings. Right-click the Ethernet0 adapter and choose Rename. Type ExternalNAT and then press ENTER.
20. Right-click the Ethernet1 adapter and choose Rename. Type Internal and then press ENTER.

21. Right-click the Internal adapter and choose Properties. Select Internet Protocol Version 4 (TCP/IPv4), and then click the Properties button.
22. Choose Use The Following IP Address and enter the following values:
IP address: 192.168.1.200
Subnet mask: 255.255.255.0
23. Click OK and then click Close.
24. Click the Start menu and type cmd and press ENTER.
25. Enlarge the command prompt window, and then type ipconfig and press ENTER. Notice the IP address information listed for the Internal and ExternalNAT network adapters.
Name the server
26. From the Start menu, choose Server Manager.
27. On the left, click Local Server; on the right, click the blue computer name link, and then click the Change button.
28. For the computer name, type Srv2019-1 and click OK.
29. At the You Must Restart Your Computer To Apply These Changes prompt, click OK, and then click Close. Choose Restart Now. The server will restart.
Create a snapshot of the installation after the computer has restarted in case you need to revert to this configuration in the future
30. From the VMware VM menu, choose Snapshot, Take Snapshot.
31. Type Fresh Installation for the name, and then click Take Snapshot. You may have to wait a few minutes as the snapshot is created. You can track the snapshot creation progress at the bottom left of the VMware Workstation window; it will say “Saving state…” followed by the percent complete.
Create a second virtual machine by cloning the one you just created
32. Shut down your Srv2019-1 virtual machine: from the VM menu, choose Power, and then choose Shut Down Guest.
33. From the VM menu, choose Manage, Clone. Click Next twice.
34. On the Clone Type screen, choose Create A Full Clone. Click Next.
35. Name the clone Srv2019-2 and choose a location on your computer that has plenty of free disk space. Click Finish and then close the dialog box when cloning has completed.
36. Start the Srv2019-1 virtual machine. Switch to the Srv2019-1 tab, and on the left, click Power On This Virtual Machine.
37. Switch to the Srv2019-2 tab, and from the VM menu, choose Settings. Remove the Network Adapter configured with NAT. Click OK and then start the virtual machine.
38. Log in to Srv2019-2 as Administrator with a password of Pa$$w0rd172hfX and change the following:
• In Control Panel, configure IPv4 to obtain the IP address and DNS server address automatically for the Internal network interface.
• Change the computer name by entering Srv2019-2 using Server Manager.
39. When prompted, restart Srv2019-2.
40. After Srv2019-2 has restarted, from the VM menu, choose Snapshot, Take Snapshot. Type Fresh Installation – Server2 for the name and then click Take Snapshot. You may have to wait a few minutes as the snapshot is created.
Exercise 3-2: Install the DNS Server Role in Windows Server 2019
1. Make sure you are logged into your Srv2019-1 virtual machine as the Administrator account with a password of Pa$$w0rd172hfX.
2. Start Windows PowerShell from the Start menu and enter the following command:
install-windowsfeature dns -includemanagementtools
(Note that there should be no space between the – symbol and the includemanagementtools parameter.)
3. After the DNS server role is installed, enter the command
get-windowsfeature *dns*
to ensure that it shows up as being installed (with an X in the box). The asterisks are wildcard symbols that will show any features containing the text dns.
4. Configure the internal server network interface to use itself for DNS name resolution by entering the following command:
set-dnsclientserveraddress -interfacealias internal -serveraddress 127.0.0.1
(Note that there should be no space between the – symbol and the serveraddress parameter.)
5. Configure the external server network interface to use itself for DNS name resolution by entering the following command:
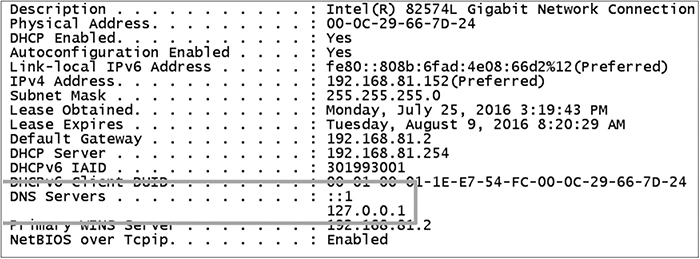
set-dnsclientserveraddress -interfacealias externalnat -serveraddress 127.0.0.1
6. Type ipconfig /all to verify that the DNS server being used by the interfaces is 127.0.0.1, as shown in the following illustration.
7. Verify DNS functionality by typing nslookup and pressing ENTER. Type www.google.com and press ENTER. You should see a list of IP addresses that service google.com. Press ENTER. Type exit and press ENTER to close the PowerShell window.
Exercise 3-3: Configure the DNS Server in Windows Server 2019
1. Make sure you are logged into your Srv2019-1 virtual machine with the Administrator account.
2. Click the Start menu and type DNS in the search bar. When the DNS tool is displayed, press ENTER.
3. In the left navigator of the DNS Manager window, expand your server name, highlight Forward Lookup Zones, and right-click Forward Lookup Zones. Choose New Zone.
4. In the Welcome To The New Zone Wizard, click Next.
5. Accept the default of a Primary Zone, and then click Next.
6. For the Zone name, type fakezone.com and then click Next.
7. Accept the defaults for the rest of the wizard and click Finish.
8. Expand Forward Lookup Zones and click fakezone.com. On the right, notice the default SOA and NS DNS records.
9. A reverse lookup zone should be created for the subnet. On the left, highlight Reverse Lookup Zones, and then right-click Reverse Lookup Zones and choose New Zone. Click Next.
10. Continue through the wizard. Create a Primary IPv4 Reverse Lookup Zone. For the Network ID, type 192.168.1. Accept the defaults for the rest of the wizard and click Finish.
11. Right-click fakezone.com and choose New Host (A or AAAA record).
12. In the New Host window, specify www for the name, and for the IP enter 192.168.1.200. Enable the option Create Associated Pointer (PTR) Record. Click Add Host and then click OK. If the New Host window pops up, click its close box. Click Done.
13. Select fakezone.com on the left, and notice the new A record for www.fakezone.com.
14. Start PowerShell. Type nslookup and press ENTER. Type www.fakezone.com, and press ENTER. You should see the Address (192.168.1.200) returned for the host.
15. Type set type=ptr and press ENTER. Watch for the case and spacing; it’s very unforgiving!
16. Type 192.168.1.200 and press ENTER. It should return the name of www.fakezone.com—this comes from your reverse lookup zone.
17. Type exit and press ENTER.
18. Type get-dnsserver. PowerShell will then return info about the DNS server, including the zones. Keep PowerShell open for the next exercise. Close the DNS Manager window.
Exercise 3-4: Install an Active Directory Server in Windows Server 2019
1. Make sure you are logged into your Srv2019-1 virtual machine with the Administrator account.
2. In PowerShell type the following command:
install-windowsfeature ad-domain-services –includemanagementtools
3. Start the Server Manager GUI tool.
4. Click the flag notification icon in the upper right; you will see a message stating that you must Promote This Server To A Domain Controller. Click the link.
5. Choose Add A New Forest, and within the Deployment Configuration window and for the Root Domain Name, type fakedomain.local. Then click Next.
6. Enter Pa$$w0rd172hfX for the DSRM password and click Next.
7. Accept the defaults for the remainder of the wizard and then click Install. After a few minutes, your server will restart.
8. Log back in using the FakedomainAdministrator account with a password of Pa$$w0rd172hfX.
9. Click the Start button and type Active in the search bar. When Active Directory Users And Computers is displayed, click it. The fakedomain.local AD domain now exists.
10. Click the Start button and type DNS in the search bar. When the DNS tool is displayed, click it.
11. In the DNS Manager window, expand the server name on the left, and then expand Forward Lookup Zones. Notice the fakedomain.local zone.
12. Expand fakedomain.local, and then click _tcp. Notice the four service location records for the domain controller.
13. Start PowerShell from the taskbar and type get-aduser -filter* to verify that AD is accessible via PowerShell. You will see a list of AD user accounts. Close all open windows.
Exercise 3-5: Install the DHCP Server in Windows Server 2019
1. Make sure you are logged into your Srv2019-1 virtual machine with the Administrator account.
2. Start PowerShell from Start menu and type the following:
install-windowsfeature dhcp –includemanagementtools
3. Start Server Manager. Click the flag icon in the upper right. Click Complete DHCP Configuration, click Next, then click Commit, and finally click Close.
4. In PowerShell, type restart-service dhcpserver.
5. Click the Start button and type DHCP in the search bar. When the DHCP tool is displayed, click it.
6. In the left navigator in the DHCP Manager window, expand srv2019-1
.fakedomain.local, select IPv4, right-click IPv4, and choose New Scope. Click Next. If you don’t see the server name immediately, close the DHCP tool and start it again until you do.
7. For the name, type LabScope1 and then click Next.
8. For the starting IP address, enter 192.168.1.50, and for the ending IP address, enter 192.168.1.80. Click Next four times.
9. For the router (default gateway), enter 192.168.1.200 and click Add. Click Next.
10. Click Next three times, and then click Finish.
11. On the Srv2019-2 virtual machine, type the following command and then press ENTER.
ipconfig /release, then ipconfig /renew
12. On Srv2019-1, in the DHCP tool, expand IPv4 and then expand Scope [192.168.1.0] LabScope1. Click Address Leases. You will see that an IP address has been leased to Srv2019-2.
Exercise 3-6: Install the Ubuntu Linux 20.04.1 Operating System
1. Start VMware Workstation Pro and ensure that the Ubuntu-1 virtual machine is selected.
2. In the navigation panel on the left, click Edit Virtual Machine Settings.
3. Notice the Network Adapter on the left. Ensure it is set to use NAT.
4. On the left, click CD/DVD, and on the right, click Use ISO Image File. Click Browse and select the Ubuntu Linux trial ISO file downloaded as per the instructions in Appendix A of this book. Click OK.
5. In the navigation panel on the left, click Power On This Virtual Machine. The virtual machine begins booting from the Linux installation media.
6. From the Ubuntu Linux 20.04.1 Welcome screen, press ENTER to select English.

7. Press ENTER and accept default settings until you reach the Guided Storage Configuration screen. Press TAB until Done is highlighted, and then press ENTER. On the Storage Configuration screen, press ENTER.
8. When prompted to Confirm Destructive Action, press TAB until Continue is highlighted, then press ENTER.
9. Type user one in the Your Name field. Press TAB and then type ubuntu-1 in the Your Server’s Name field. Press TAB and then type uone in the Pick A Username field. Specify and confirm a password of Pa$$w0rd172hfX.
10. Press TAB to highlight Done, then press ENTER. Press the SPACEBAR to enable the Install OpenSSH Server option, then press TAB twice to highlight Done, and then press ENTER.
11. If you receive an option for Feature Server Snaps, continue by selecting Done.
12. Once installation is complete, from the VM menu, choose Settings. On the left click CD/DVD (SATA). On the right, uncheck Connect At Power On. Click OK. Ensure that Reboot is highlighted and press ENTER.
13. After the server reboots, click in the virtual machine screen and press ENTER when you see the Reached Target Cloud-init Target status message.
14. At the Ubuntu1 login prompt, type uone and press ENTER. Type Pa$$w0rd172hfX and press ENTER.
15. Type ip a to view the IPv4 address acquired through DHCP.
16. On Srv2019-1, allow all incoming network traffic from Ubuntu1, and in a command prompt window type the following:
netsh advfirewall firewall add rule name="Allow all traffic from Linux" dir=in action=allow protocol=any remoteip=IP Of Ubuntu1
(Replace IP Of Ubuntu1 with the IP address from step 15.)
17. Create a snapshot of the installation in case you need to revert to this configuration in the future: From the VMware VM menu, choose Snapshot, Take Snapshot. Type Fresh Installation for the name, and then click Take Snapshot. You may have to wait a few minutes as the snapshot is created.
18. Shut down each virtual machine guest by switching to the Virtual Machine tab and choosing VM, Power, Shut Down Guest.
Chapter Review
This chapter focused on how to install, configure, manage, and maintain server operating systems, whether they run on physical hardware or within virtual machines.
Server Roles
The type of workload handled by a server must be planned before server installation, and in some cases, these roles can be co-located on the same server.
DHCP
On DHCP servers, centrally configured IPv4 and IPv6 settings can be deployed to DHCP. DHCP servers use UDP port 67, and DHCP clients use UDP port 68. DHCP scopes contain IP address ranges as well as additional settings such as lease duration, default gateways, DNS servers, reservations, exclusions, and more. Specific DHCP settings can be delivered to certain types of DHCP clients using vendor class identifiers. IPv4 clients that cannot reach DHCP will be auto-configured with an APIPA address with a prefix of 169.254.
Name Resolution
DNS servers are queried by clients on UDP port 53 primarily for name resolution, where an FQDN is supplied and a corresponding IP address is returned. Given an IP address, a DNS server can also perform a reverse lookup to return a name. DNS is a hierarchy of domains, where different DNS servers control different parts of the DNS namespace. The most common type of DNS resource record managed by administrators is an A record (IPv4) that is used for resolving names to IP addresses; the equivalent for IPv6 is an AAAA record.
WINS is used for resolving computer names to IP addresses, but, unlike DNS, it is not a hierarchy, but rather a flat list of NetBIOS computer names.
NTP
NTP is used to synchronize time for network devices from a time source. Connectivity for this protocol occurs over UDP port 123. Stratum 0 NTP devices are a trusted time source. Stratum 1 devices are NTP servers that get their time from a Stratum 0 device. Stratum 2 devices are NTP servers that get their time from Stratum 1 servers, and so on.
Directory Services
A directory service is a network database containing network-related objects such as users, computers, and groups. Often this is replicated among multiple servers to provide high availability and service localization.
Microsoft Active Directory uses domain controllers to house and replicate the directory service database. Clients discover domain controllers via DNS service location records.
Other Server Roles
Web servers use HTTP to transmit HTML web pages to web browser clients. Clients request the pages over TCP port 80 (HTTP) or 443 (HTTPS) and the server responds to the client on a dynamically allocated client port number normally between 49152 and 65535. HTTPS requires a server-side SSL/TLS certificate to secure the connection. Web site developers can build server-side/client-side code for site functionality. Enterprise Web SSO uses an underlying directory service, often in the form of identity federation.
Application servers can consist of multiple components such as a front-end web server and a back-end database that serve a specific business purpose.
File and print servers enable connectivity to these resources over the network and must have properly configured ACLs to allow access. SMTP mail servers transfer mail between SMTP mail hosts; POP and IMAP are message retrieval protocols used by mail client software. IMAP allows synchronization between different devices, unlike POP.
Routing and remote access servers (RRAS) have at least two network interfaces and can be configured for IP routing, NAT, or VPNs.
Virtualization Servers
Hypervisors are software that run virtual machines and manage access to physical hardware. Type 1 hypervisors have direct access to physical hardware; Type 2 hypervisors rely on an underlying operating system to manage hardware access.
Hardware for the hypervisor must be planned relative to the virtual machines and their workloads that it will host. More RAM would be needed to run multiple virtual machines, and some IT workloads such as large database servers will require more resources such as RAM.
Guests are virtual machines running on a hypervisor host, and each is configured with its own set of virtual hardware to accommodate its IT workloads properly. Settings such as dynamic memory can more efficiently use host memory among multiple virtual machines.
Server Installation
Hardware and software compatibility lists must be consulted before installing servers to ensure the smooth installation and running of IT services. Server OSs can be installed from bootable media or over the network, including PXE boot. PXE booting occurs over the network without local media, and services such as Microsoft RIS/WDS provide this functionality.
Server OS images can be used as well, and a server installation from media or an image can be completely automated using answer files or enterprise deployment solutions. A virtual machine deployed on-premises or in the cloud can use virtual machine images (or templates), which enable easy server deployment in mere minutes.
Existing physical servers can use a software agent to read configuration settings, which results in a virtual server through a process called physical-to-virtual (P2V) cloning. Existing virtual machines can be cloned when new virtual machine requirements are similar to the original source server configuration. Virtual machine templates can be used on-premises or in the cloud to provision virtual machines quickly.
Open-source software does not normally incur licensing fees, but technical support does. For proprietary software, there are numerous licensing models such as per-server, per-instance, per-core, per-socket, and per-concurrent user. Node-locked licensing is tied to a specific node. Signature-based licensing is based on digital signatures and is commonly used to verify the authenticity of a gaming or media provider.
Server Administration Methods
Server administration methods include the following:
• Locally at the console
• Remotely using GUI tools such as Microsoft RSAT or RDP
• Remotely using SSH
• Remotely using PowerShell or WinRM
KVM is used to connect to numerous servers where a single keyboard, video display, and mouse is used. KVM enables technicians to switch to different servers for management, whether servers have physical connections to KVM or over IP.
Out-of-band administration provides hardware-level remote access to a host without relying on the OS software running. Common solutions include Dell’s iDRAC and HP’s iLO; the server hardware must support this type of remote administration, and it must be configured with IP settings.
Server technicians can create Bash (.SH), batch (.BAT), Visual Basic (.VBS), or PowerShell (.PS1) scripts to automate server management tasks such as software installation, server or service startup or shutdown, user account management, and more. Data types, variables, and looping construct details and syntax vary slightly across the scripting types.
Server Documentation
Server documentation includes the following:
• OEM service manuals
• Hardware and software inventory
• Log files
• Network/dataflow diagrams
• Service level agreements
• Baseline documentation
• Recovery documentation
The server asset life cycle, from procurement to disposal, must be documented, including configuration changes during the useful life of the server. This data can be crucial for recovery services and should be made highly available through backups or replication to alternate locations. Server configuration documentation must also be kept secure—the last thing you want is malicious users knowing server configuration details.
Server Maintenance
Proactive maintenance includes applying firmware and software updates, ensuring that server room and data center environmental controls are in place, plugging servers into UPS systems, and making sure that a recovery procedure exists in the event of server failure.
Patch management can be centralized and automated using a tool such as WSUS or SSCM for Windows environments. Reports can be run to ensure that updates have been successfully applied.
Reactive maintenance involves viewing log entries, responding to alerts including error codes, server LCD messages, and so on.
Questions
1. Through which methods can on-premises servers communicate with cloud-based virtual machine servers? Choose two.
A. Site-to-site VPN connection
B. IPv6 leased connection
C. Dedicated leased connection
D. PKI
2. Which server role provides centralized IP configuration settings for clients?
A. DNS
B. IIS
C. RDP
D. DHCP
3. You need to configure DHCP to deliver a specific IP address to a specific network printer. What should you configure?
A. DHCP scope
B. DHCP reservation
C. Default gateway
D. PXE
4. Your network consists of Windows 10 computers and Android smartphones. You need to ensure that the Android devices are given IP addresses that place them on their own isolated VLAN. What should you do?
A. Configure a DHCP vendor class identifier.
B. Plug the Android devices into switch ports grouped into a VLAN.
C. Configure a DHCP reservation.
D. Configure a DHCP scope.
5. Your users report that they cannot access Internet resources today, although yesterday this worked fine. At a user station, you notice the IP address begins with 169.254. Why can’t user stations reach the Internet?
A. A DHCP server cannot be reached.
B. An incorrect subnet mask has been specified.
C. An incorrect default gateway has been specified.
D. An incorrect DNS server has been specified.
6. Which Windows command shows DHCP lease information?
A. ipconfig /release
B. arp -a
C. nslookup
D. ipconfig /all
7. What type of DNS record is used to resolve FQDNs to IP addresses?
A. MX
B. PTR
C. A
D. AAAA
8. Which port does a DNS server listen on for client queries?
A. UDP 53
B. TCP 53
C. UDP 3389
D. TCP 3389
9. You install a Windows DNS server named DNS1. Clients on the network are configured to use DNS1 for name resolution. Users report they are able to connect to Internet resources by name. You need to ensure that DNS resolves only internal names. What should you do?
A. Remove the DNS server default forwarders.
B. Remove the DNS server default stub zones.
C. Add DNS server root hints.
D. Remove the DNS server root hints.
10. You need to configure firewall ACLs to allow DNS server zone transfer traffic. Which port should your ACL allow?
A. UDP 53
B. TCP 53
C. UDP 80
D. TCP 80
11. How do WINS and DNS differ?
A. WINS uses a hierarchical naming structure; DNS uses a flat naming structure.
B. WINS uses a flat naming structure; DNS uses a hierarchical naming structure.
C. WINS uses AAAA records for IPv6; DNS uses A records for IPv6.
D. WINS uses UDP port 53 for client queries; DNS uses TCP port 53 for client queries.
12. Your network servers point to NTP time servers connected to reference clocks. Which type of NTP time servers do you have on your network?
A. Stratum 0
B. Stratum 1
C. Stratum 2
D. Stratum 3
13. You are configuring firewall ACLs. You need to ensure that NTP traffic is allowed through. Which port must you specify in your ACL rule?
A. UDP 161
B. TCP 161
C. UDP 123
D. TCP 123
14. Which server role stores network configuration objects in a centralized and replicated database?
A. Directory service
B. CUPS
C. DNS
D. DHCP
15. Your intranet has a web server containing sensitive data. You want to encrypt communications between web browser clients and the web server. What should you do?
A. Issue a PKI certificate for each client web browser. Install the certificates on the web server.
B. Issue a PKI certificate for each client web browser. Install the certificates on each client.
C. Issue a PKI certificate for the web server. Install the certificate on the web server.
D. Issue a PKI certificate for the web server. Install the certificate on each client station.
16. Which file and printer sharing protocol is used by Windows devices?
A. Samba
B. NFS
C. SMB
D. CUPS
17. Your firewall has an ACL that allows inbound traffic destined for TCP port 25 to your company’s DMZ. What type of traffic is this?
A. POP
B. SNMP
C. IMAP
D. SMTP
18. What term is used to refer to a host with at least two network interfaces?
A. NIC teaming
B. Multihomed
C. MultiNICed
D. NIC homing
19. Which term is used to refer to a running virtual machine on a hypervisor?
A. Host
B. Node
C. Device
D. Guest
20. Which type of hypervisor has direct access to physical hardware?
A. Type 1
B. Type 2
C. Type A
D. Type B
21. You need to ensure that your cloud backup solution has guaranteed uptime. What must you have to ensure this?
A. Network diagram
B. Dataflow diagram
C. Service level agreement
D. Change control policy
22. You have a Linux image that will be deployed to numerous virtual machines. The image should be pulled down over the network without providing boot media. Which option should you use?
A. PXE
B. DHCP
C. DISM
D. USB
23. You want data center technicians to be able to scan equipment physically to facilitate hardware inventory gathering. What should you use?
A. Bluetooth
B. RFID
C. Wi-Fi
D. 4G
24. Which PowerShell cmdlet opens an interactive session with a remote host?
A. Invoke-Command
B. All PowerShell cmdlets using the -computername parameter
C. Enter-PSSession
D. Winrs
25. Which of the following are considered out-of-band server management solutions? Choose two.
A. SSH
B. iDRAC
C. iLO
D. RDP
Questions and Answers
1. Through which methods can on-premises servers communicate with cloud-based virtual machine servers? Choose two.
A. Site-to-site VPN connection
B. IPv6 leased connection
C. Dedicated leased connection
D. PKI
A, C. Site-to-site VPNs traverse the Internet and can link local and cloud networks together. Dedicated leased connections do not traverse the Internet and could also be used to link on-premises and cloud networks. B and D are incorrect. IPv6 supersedes IPv4 and has a larger address space as well as security and quality of service improvement, but there is no such thing as an IPv6 leased connection. PKI is a hierarchy of security certificates; it can be used to secure traffic but not to link two networks together.
2. Which server role provides centralized IP configuration settings for clients?
A. DNS
B. IIS
C. RDP
D. DHCP
D. DHCP provides centralized IP settings that DHCP clients can use. A, B, and C are incorrect. DNS is a centralized name lookup service. IIS is Microsoft’s web server product. RDP is Microsoft’s Remote Desktop Protocol.
3. You need to configure DHCP to deliver a specific IP address to a specific network printer. What should you configure?
A. DHCP scope
B. DHCP reservation
C. Default gateway
D. PXE
B. DHCP reservations tie an IP address to a MAC address of a device on the network. A, C, and D are incorrect. DHCP scopes contain address ranges and settings such as DNS server and default gateways. A default gateway sets the IP address(es) of the router(s) interface on the local network and enables traffic to be sent outside of the LAN. PXE is a network booting option often used for machine imaging purposes.
4. Your network consists of Windows 10 computers and Android smartphones. You need to ensure that the Android devices are given IP addresses that place them on their own isolated VLAN. What should you do?
A. Configure a DHCP vendor class identifier.
B. Plug the Android devices into switch ports grouped into a VLAN.
C. Configure a DHCP reservation.
D. Configure a DHCP scope.
A. Vendor class identifiers can determine which type of device is connecting to DHCP and can assign IP settings for that type of device. B, C, and D are incorrect. Android devices do not have Ethernet ports for network cables. DHCP reservations tie an IP address to a device MAC address. DHCP scopes contain IP address ranges and related settings, but the scope applies to all devices by default.
5. Your users report that they cannot access Internet resources today, although yesterday this worked fine. At a user station, you notice the IP address begins with 169.254. Why can’t user stations reach the Internet?
A. A DHCP server cannot be reached.
B. An incorrect subnet mask has been specified.
C. An incorrect default gateway has been specified.
D. An incorrect DNS server has been specified.
A. APIPA addresses are the result of a device not being able to contact a DHCP server. B, C, and D are incorrect. An incorrect subnet mask, default gateway, or DNS server won’t matter if the station is using a 169.254 address prefix.
6. Which Windows command shows DHCP lease information?
A. ipconfig /release
B. arp -a
C. nslookup
D. ipconfig /all
D. The ipconfig /all command shows IP information including that related to DHCP. A, B, and C are incorrect. The ipconfig /release command releases DHCP-acquired IP configurations. The arp -a command shows IP address to MAC address resolution information. nslookup is a DNS diagnostic tool.
7. What type of DNS record is used to resolve FQDNs to IP addresses?
A. MX
B. PTR
C. A
D. AAAA
C. A records, also called host records, resolve FQDNs to IPv4 addresses. A, B, and D are incorrect. MX records are mail exchange records used to locate SMTP mail servers. PTRs are pointer records used in reverse lookup zones to return a name, given an IP address. AAAAs are IPv6 host records.
8. Which port does a DNS server listen on for client queries?
A. UDP 53
B. TCP 53
C. UDP 3389
D. TCP 3389
A. Client DNS queries target the DNS server on UDP port 53. B, C, and D are incorrect. TCP 53 is used for zone transfers between DNS servers. UDP 3389 is not normally used. TCP 3389 is the default RDP port on Windows hosts.
9. You install a Windows DNS server named DNS1. Clients on the network are configured to use DNS1 for name resolution. Users report they are able to connect to Internet resources by name. You need to ensure that DNS resolves only internal names. What should you do?
A. Remove the DNS server default forwarders.
B. Remove the DNS server default stub zones.
C. Add DNS server root hints.
D. Remove the DNS server root hints.
D. DNS server root hints allow for Internet name resolution. A, B, and C are incorrect. There are no forwarders or stub zones by default, and adding DNS server root hints will not resolve the issue.
10. You need to configure firewall ACLs to allow DNS server zone transfer traffic. Which port should your ACL allow?
A. UDP 53
B. TCP 53
C. UDP 80
D. TCP 80
B. TCP port 53 is used for zone transfer traffic between DNS servers. A, C, and D are incorrect. UDP 53 is used for DNS client queries, UDP 80 is not normally used, and TCP 80 is the default HTTP web server port.
11. How do WINS and DNS differ?
A. WINS uses a hierarchical naming structure; DNS uses a flat naming structure.
B. WINS uses a flat naming structure; DNS uses a hierarchical naming structure.
C. WINS uses AAAA records for IPv6; DNS uses A records for IPv6.
D. WINS uses UDP port 53 for client queries; DNS uses TCP port 53 for client queries.
B. WINS simply resolves NetBIOS computer names to IP addresses; there is no hierarchy as there is in DNS. A, C, and D are incorrect. WINS is not hierarchical; DNS is. DNS A records are for IPv4; AAAA records are for IPv6. UDP 53 is used only for DNS client queries; TCP 53 is used for DNS server zone transfers.
12. Your network servers point to NTP time servers connected to reference clocks. Which type of NTP time servers do you have on your network?
A. Stratum 0
B. Stratum 1
C. Stratum 2
D. Stratum 3
C. Stratum 2 NTP servers point to Stratum 1, which in turn uses a reference clock (Stratum 0). A, B, and D are incorrect. Stratum 0 is for reference clocks, Stratum 1 are time servers connected to reference clocks, and Stratum 3 servers point to Stratum 2 time providers.
13. You are configuring firewall ACLs. You need to ensure that NTP traffic is allowed through. Which port must you specify in your ACL rule?
A. UDP 161
B. TCP 161
C. UDP 123
D. TCP 123
C. NTP uses UDP port 123. A, B, and D are incorrect. UDP 161 is for SNMP; TCP 161 and 123 are not normally used.
14. Which server role stores network configuration objects in a centralized and replicated database?
A. Directory service
B. CUPS
C. DNS
D. DHCP
A. A directory service is a centralized and replicated database that stores network objects such as users, groups, and computers. B, C, and D are incorrect. CUPS is the UNIX- and Linux-based print server standard. DNS is used for name resolution. DHCP provides centralized IP settings for DHCP client devices.
15. Your intranet has a web server containing sensitive data. You want to encrypt communications between web browser clients and the web server. What should you do?
A. Issue a PKI certificate for each client web browser. Install the certificates on the web server.
B. Issue a PKI certificate for each client web browser. Install the certificates on each client.
C. Issue a PKI certificate for the web server. Install the certificate on the web server.
D. Issue a PKI certificate for the web server. Install the certificate on each client station.
C. Only the web server requires a PKI certificate. A, B, and D are incorrect. Clients do not need a PKI certificate for secured web server traffic.
16. Which file and printer sharing protocol is used by Windows devices?
A. Samba
B. NFS
C. SMB
D. CUPS
C. Windows file and printer sharing uses the SMB protocol. A, B, and D are incorrect. Samba enables Linux clients to contact Windows SMB shared resources. NFS is the UNIX and Linux file sharing standard. CUPS is the UNIX and Linux print server standard.
17. Your firewall has an ACL that allows inbound traffic destined for TCP port 25 to your company’s DMZ. What type of traffic is this?
A. POP
B. SNMP
C. IMAP
D. SMTP
D. SMTP mail traffic has a destination port of TCP 25. A, B, and C are incorrect. POP uses TCP port 110, SNMP is UDP 161, and IMAP is TCP 143.
18. What term is used to refer to a host with at least two network interfaces?
A. NIC teaming
B. Multihomed
C. MultiNICed
D. NIC homing
B. A host with at least two NICs is said to be multihomed. A, C, and D are incorrect. NIC teaming groups multiple NICs together for bandwidth aggregation or load balancing. MultiNICed and NIC homing are made-up words.
19. Which term is used to refer to a running virtual machine on a hypervisor?
A. Host
B. Node
C. Device
D. Guest
D. A virtual machine is also called a guest. A, B, and C are incorrect. The hypervisor is referred to as the host. A node or device is a network entity that can transmit and receive packets.
20. Which type of hypervisor has direct access to physical hardware?
A. Type 1
B. Type 2
C. Type A
D. Type B
A. Type 1 hypervisors have direct access to hardware without going through an operating system. B, C, and D are incorrect. Type 2 hypervisors go through an existing operating system for hardware access. Types A and B are not used to refer to hypervisors.
21. You need to ensure that your cloud backup solution has guaranteed uptime. What must you have to ensure this?
A. Network diagram
B. Dataflow diagram
C. Service level agreement
D. Change control policy
C. Service level agreements specify details such as guaranteed uptime. A, B, and D are incorrect. Network and dataflow diagrams are useful documentation for troubleshooting, change management, and inventory purposes. A change control policy dictates steps that must be taken to make configuration changes.
22. You have a Linux image that will be deployed to numerous virtual machines. The image should be pulled down over the network without providing boot media. Which option should you use?
A. PXE
B. DHCP
C. DISM
D. USB
A. PXE boots over the network and pulls down a small operating system to the local machine, often for imaging purposes. B, C, and D are incorrect. DHCP is used with PXE, but it does not provide boot and imaging options. DISM is a Windows command line tool that can be used to service Windows image files. Using a USB would mean technicians would have local boot media.
23. You want data center technicians to be able to scan equipment physically to facilitate hardware inventory gathering. What should you use?
A. Bluetooth
B. RFID
C. Wi-Fi
D. 4G
B. RFID enables devices to be scanned with RFID tags for inventory and tracking purposes. A, C, and D are incorrect. Bluetooth, Wi-Fi, and 4G are wireless technologies, but they are not designed specifically for inventory gathering.
24. Which PowerShell cmdlet opens an interactive session with a remote host?
A. Invoke-Command
B. All PowerShell cmdlets using the -computername parameter
C. Enter-PSSession
D. Winrs
C. Interactive PowerShell sessions can be started with Enter-PSSession. A, B, and D are incorrect. Invoke-Command and the -computername parameter for some cmdlets enable remote code execution, but not interactively. Winrs is a Windows command line remote management tool.
25. Which of the following are considered out-of-band server management solutions? Choose two.
A. SSH
B. iDRAC
C. iLO
D. RDP
B, C. Dell’s iDRAC and HP’s iLO are hardware-based, out-of-band remote management solutions. A and D are incorrect. SSH is used to manage any device securely and remotely with an SSH listener. RDP is used to manage Windows computers remotely.


