When you see something that is technically sweet, you go ahead and do it and you argue about what to do about it only after you have had your technical success. That is the way it was with the atomic bomb.
—J. Robert Oppenheimer
Did you know that the US government can legally seize your cash without any court order and charges against you? I didn’t until I read an article1 in The Washington Post about a former Marine pulled over by police when traveling from Texas to California to see his daughters. The police searched his car and found $87,000 in cash in the trunk. The ex-Marine was not arrested or charged with any crime. However, the police still decided to seize the money using a legal procedure called “adoption,” which allows federal authorities to take cash or property they suspect is connected to criminal activity without levying criminal charges. His only “crime” was that he did not trust banks and wanted to carry cash with him. I wouldn’t believe that this is a truthful story, but The Washington Post is one of the sources I still trust.
This story shows that our money is not safe from criminals and governments (the government representatives behaved like criminals in this case), even in the form of cash. Since many people call crypto “cash for the Internet,” what are the perils of using crypto compared to traditional money? Would a similar story be possible with Bitcoin or other cryptos? Of course not. Does it mean crypto is much more secure than cash or electronic payments like plastic cards? Yes and no. Although crypto is a significant step up in security and privacy, it has privacy threats. These are new, often unknown, and poorly studied vulnerabilities, and therefore crypto can be even more dangerous for unsophisticated users than cash or cards. Let’s see how to avoid them.
While working on the GRAFT white paper,2 my first crypto project, I spent a lot of time researching privacy coins. Such coins provide their users with adequate security and protect their identities beyond the “Bitcoin standard .” When people first dive into the exciting world of crypto, they don’t pay much attention to the downsides of blockchain technology. However, start comparing Bitcoin with plastic payment cards, famous for their huge number of security holes. You will be surprised to find that crypto does not withstand the criticism, disproving its much-advertised privacy features. There is a simple explanation for this perception discrepancy.
Bitcoin Is Pseudonymous!
The inventors and first adopters of Bitcoin assumed that the very fact of the decentralized nature of the Bitcoin network and anonymous access to the blockchain would fully protect the user’s privacy. They underestimated the ingenuity of people around crypto, who are not necessarily against the crypto philosophy but maybe just want to make it better by hacking it. That’s the original hackers’ philosophy, by the way – they don’t want to break anything, but they are rather convinced that by exposing vulnerabilities, they will eventually make the product more robust. Yours truly is not an exception, and my books reveal some facts that help make this world a little better.
Comparing Bitcoin and Plastic Payment Card Privacy
Bitcoin | Plastic Payment Cards | |
|---|---|---|
Access | Pseudo-anonymous, i.e., does not require identity disclosure, but the link can be established through blockchain analysis and online surveillance | Requires full identity disclosure |
Transaction traceability | Transaction data is publicly visible, but there is no direct link to user identity available out of the box | Transaction data is not visible to public, but readily available to selected corporations, governments, and hackers |
Ability to enhance privacy | Available through using special tools | Not available |
Absolute privacy | Available through converting funds to privacy-centric coin | Not available |
Making Your Bitcoin Transactions Private
So which technology – Bitcoin or plastic payment cards – provides better privacy? Although there is no simple answer to this question, I still vote for Bitcoin for multiple reasons. First of all, it is decentralized, and no one can stop me from using it! I admit a fundamental flaw in “traditional” crypto like Bitcoin or Ethereum: they make all your money movements public. And it’s possible to establish the link between your wallet and your identity; it’s just a matter of time and effort.
However, it should be noted that there are special tools that allow users to significantly improve their privacy even if they use pseudo-anonymous coins like Bitcoin. There are ways to hide your transactions – from simple methods like generating a new, unique wallet address for each transaction to more sophisticated ways like coin mixers. If you are still in love with Bitcoin, Ethereum, or any other pseudonymous coin (this is not sarcasm, no worries, I get it) and not ready to switch to privacy-centric coins but want to get closer to the real freedom from the big brother, let’s review these relatively simple tools.
Unique Wallet Address per Transaction
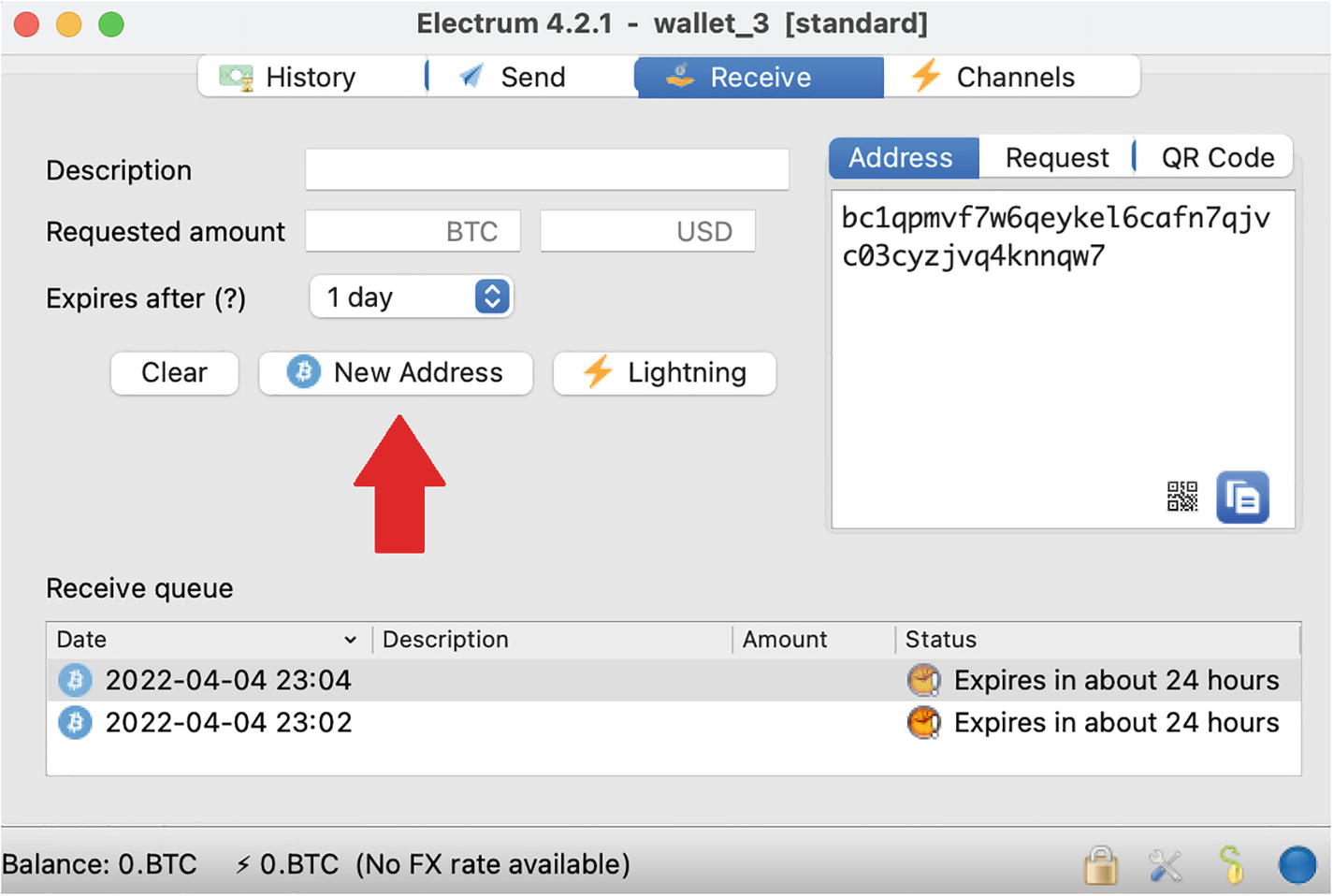
A screenshot of a window titled, Electrum 4.2.1 wallet 3 standard. Four tabs, history, send, receive, and channels are at the top. Labels on the left: description, requested amount, expires after; on the right: address, request, Q R code. A section titled, receive queue is at the bottom.
Generating a new, unique wallet address in the Electrum wallet
What happens if you use unique addresses? It helps keep your incoming transactions unlinked, making establishing your identity a more difficult task. The problem, however, is outgoing transactions. When you send bitcoin, your wallet combines the transaction from multiple inputs, which effectively links those transactions that previously looked unlinked. You can reduce this effect by using multiple wallets, but only to a certain degree. To completely hide your transactions, you need to use other, more powerful methods .
Coin Mixers (Tumblers)
Although the legal status of coin mixing services, or tumblers, is questionable, you should know about them. For some people like journalists or political dissidents, privacy is vital and even more important than any legal concerns. The concept of a coin mixer is simple: instead of sending your coins directly to the recipient, you send them through the mixing service. The mixer “grinds” them to mix the inputs and outputs with other people’s coins and, after some delay, sends the “brand-new” coins to your recipient. The result of such a performance is that it is almost impossible to reliably establish the link between your and your recipient’s wallets.
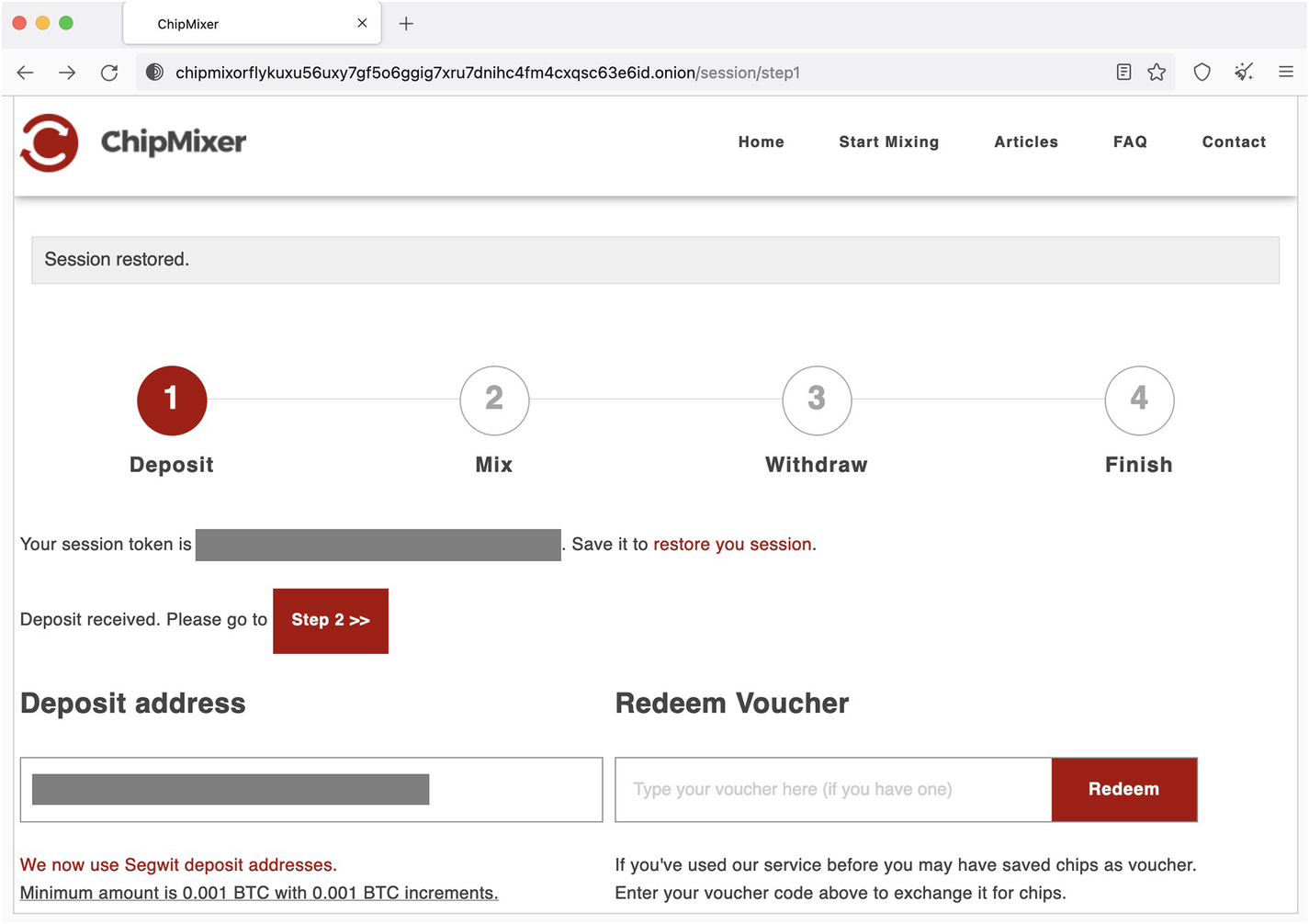
A screenshot of the ChipMixer deposit screen. Five options at the top are home, start mixing, articles, F A Q, and contact. It represents a session with 4 steps: deposit, mix, withdraw, and finish. Two sections, deposit address and redeem voucher are present.
ChipMixer deposit screen
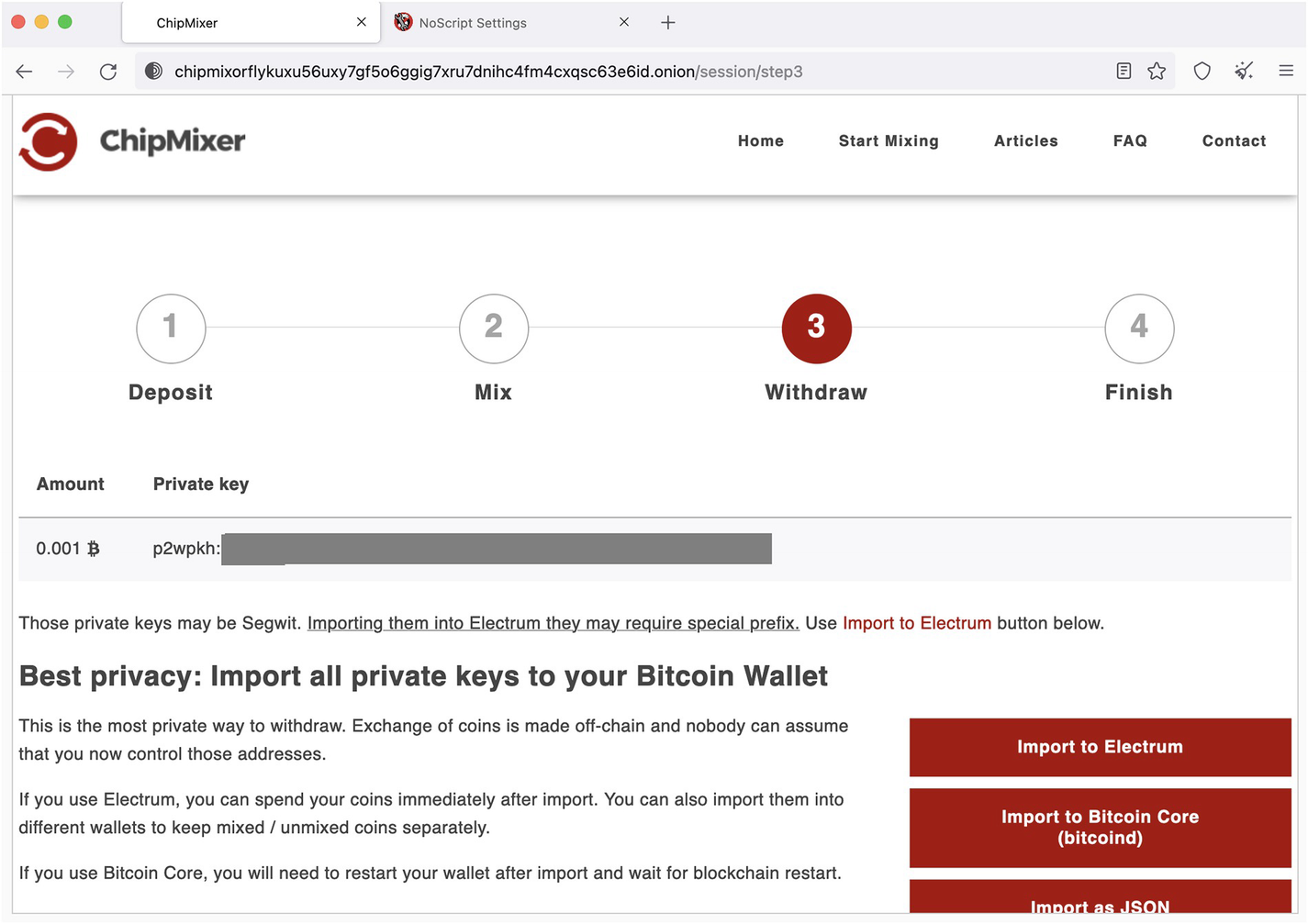
A screenshot of the ChipMixer webpage displays a session with 4 steps: deposit, mix, withdraw (highlighted), and finish. A section titled, Best privacy: Import all private keys to your Bitcoin Wallet is present.
ChipMixer withdrawal through a private key
This way, it works like a “time machine” as you withdraw your funds using transactions that haven’t been done yet but will be done in the future because a private key is not a transaction; it’s just a piece of information that allows you to process transactions. So, at the time of “withdrawal,” you do not withdraw anything until you use this private key to send funds to someone else. In fact, ChipMixer says that “this is the most private way to withdraw. Exchange of coins is made off-chain, and nobody can assume that you now control those addresses.”
Sounds too good to be true! Well, that’s because it’s not exactly too good. The problem is that if someone (ChipMixer in this case) knows your private key, they can still use your funds. So, suppose you don’t send the funds associated with the withdrawal private key immediately to your other wallet. In that case, you should come to terms with the idea that you completely trust ChipMixer (which is highly not recommended).
It’s important to note that most mixers are proprietary, centralized applications. They can be a scam, run away and disappear, go bankrupt, or the government can shut them down. Please think twice before you trust your private keys to them or anyone else! It’s like sharing your bank account credentials. Do it only if you really need it. There is always a risk of losing. At least reduce the risk by dividing large amounts into several transactions.
A screenshot of a window titled, Electrum 4.2.1 my wallet, Imported. Three tabs, history, send, and receive are present at the top. A table displays data under the following column headers: Date, description, amount, and balance.
Exodus wallet with the private key just imported from ChipMixer
With that said, this mixer works fine. Note that they don’t charge any fees! They accept donations, though, in the form of excessive amounts of deposits. For example, if you send 0.0015 BTC, you get a 0.001 BTC chip, and 0.0005 goes to ChipMixer. Another good feature is that they support SegWit (not all wallets have it), which means that withdrawals can be made with lower fees. We will talk about SegWit in a chapter about wa llets.
The Onion Router (TOR)
It starts with the prefix chipmix, which hints that it may be related to the ChipMixer website. And it ends with the suffix .onion. Don’t try to google the .onion Internet domain – it does not exist in the regular World Wide Web as you know it. Onion is the suffix of the darknet (a.k.a. dark web or deep web) address. And that address is pointing to the same site as the https://chipmixer.com/ website but located in the darknet and accessed through the onion cloud or TOR network.
TOR (The Onion Router) is another powerful privacy tool that can complement the previous methods we reviewed. TOR allows fully secure, anonymous, untraceable access to the Internet, especially if you use onion addresses. The onion cloud is the network of servers called relays or nodes located all over the world that ensures anonymity and untraceability of your Internet connection. When you access a website through a TOR browser,4 your computer’s IP address is hidden and cannot be linked to the destination site’s server. Instead, the data between your computer and the website hops through TOR nodes (at least 3) which obfuscates your Internet traffic.
Not all websites are connected to the onion cloud directly, but you can still access regular websites with their standard URL using the TOR browser. For example, if you type https://chipmixer.com/ , it will bring you to the same ChipMixer website. The connection will be through the onion cloud, with an exit point at some random TOR node located anywhere in the world. From that exit node, all the way until the website, the “last mile” will be through the regular “open” Internet. Such a connection is more secure and private than a standard browser like Chrome, but it can still be intercepted and traced. So, to use the full power of the onion cloud, you better use the onion addresses (if they are available ).
VPN (Virtual Private Network)
Is there anything more secure and private than TOR? A VPN (virtual private network) is not more secure than TOR, but it complements its security and privacy and provides a much higher connection speed.
What Is VPN?
Its function is basically similar to TOR: hide your location and Internet identity (IP address). The difference is that a VPN is a centralized service, so your data can be hacked or seized by the government. All VPN operators, of course, state that they don’t retain or disclose any information about your activities, but how can you verify that? Let’s hope nothing like this ever happens, but the first cybersecurity principle is “zero trust,” so don’t assume anyone cares about your privacy more than you do.
How Does VPN work?
It’s straightforward . When you install a VPN client app on your computer or phone, it will route all your Internet connections to the closest VPN server (instead of sending them directly to the websites you are browsing). From there, your connection goes to another server, which can be located in a different part of the world (which you can usually choose). It’s called an exit server, similar to a TOR exit node. What it also does is it is replacing your original IP address with its IP address, making your call efficiently anonymous.
The website you browse does not know who you are and where you are from. They cannot track your activities and cannot establish any link with your other activities on the Internet.
Your ISP – the company such as AT&T that provides you with the Internet access, records all your Internet traffic, sells this data to other companies, and reports it to the government (yes, don’t be surprised!) – won’t be able to know anything about your Internet activities anymore. The only activity they will ever record is your connection to the VPN entry server; that’s it.
Another interesting “side effect” of VPN is that you can pretend to be in a different place by selecting an exit point in a specific country (Figure 5-5). Hackers widely use this to trick websites that track user geolocation and regulate access based on it .
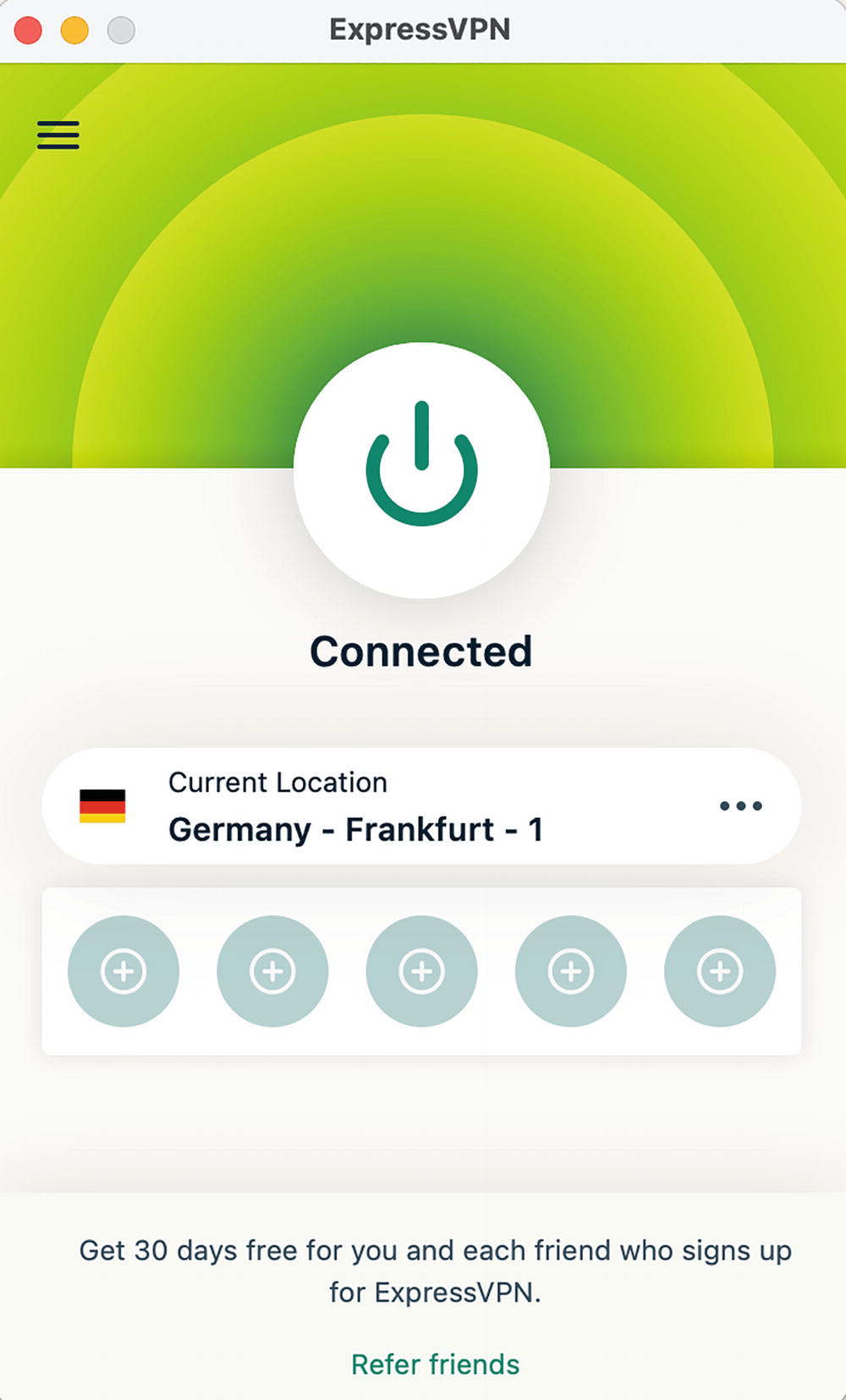
A screenshot of the Express V P N. A power button symbol at the center is labeled connected. Current location, Germany Frankfurt 1.
VPN connection with an exit point in Germany
Note that if you use a standard browser like Chrome, it’s important to enable private browsing (Incognito Browsing in Chrome). Otherwise, your identity can still be established, and your activities can be tracked using metadata submitted by your standard browser. Using a TOR browser, however, is the better option.
If I Use TOR, Should I Use VPN As Well?
The answer is yes. When you use a VPN and TOR, you increase your chance of surviving the surveillance and avoid some hacking attacks. No one even knows that you ever connect to the TOR cloud because VPN hides this fact. If your data leaks from the VPN, you are still protected by TOR and vice versa.
Some good examples of VPN services are ExpressVPN 5 and NordVPN,6 but there are many others. Even though there are some free VPN services theoretically, I have never managed to find one that reliably works. So come to terms with the fact that privacy is not free and find the service that fits your needs and wallet (your regular wallet, not necessarily crypto).
Besides the Case with the Coin Mixer, Should I Use TOR and VPN?
If you want to keep your transactions fully private, you should use your crypto wallet with both a VPN and TOR, or at least a VPN, as this is the easiest one, and it provides additional privacy benefits beyond just crypto.
Using crypto wallets with TOR can be a nontrivial task and may require running a node because not all “light” wallets support TOR. But a VPN is typically a straightforward, one-click user-friendly app that can be installed on any computer and phone. It is transparent for the wallet app, meaning there is nothing you need to configure specifically in the wallet app to use a VPN – just launch the VPN app.
Choose the Right Wallet
There are different types of wallets , such as thin wallets and full node wallets . Crypto wallets rely on external services, either decentralized (including the crypto networks themselves) or centralized (app servers). The very fact that your wallet communicates with a third-party service is a privacy concern because that service can record your IP address and your activity and therefore establish a link between your identity and your financial transactions.
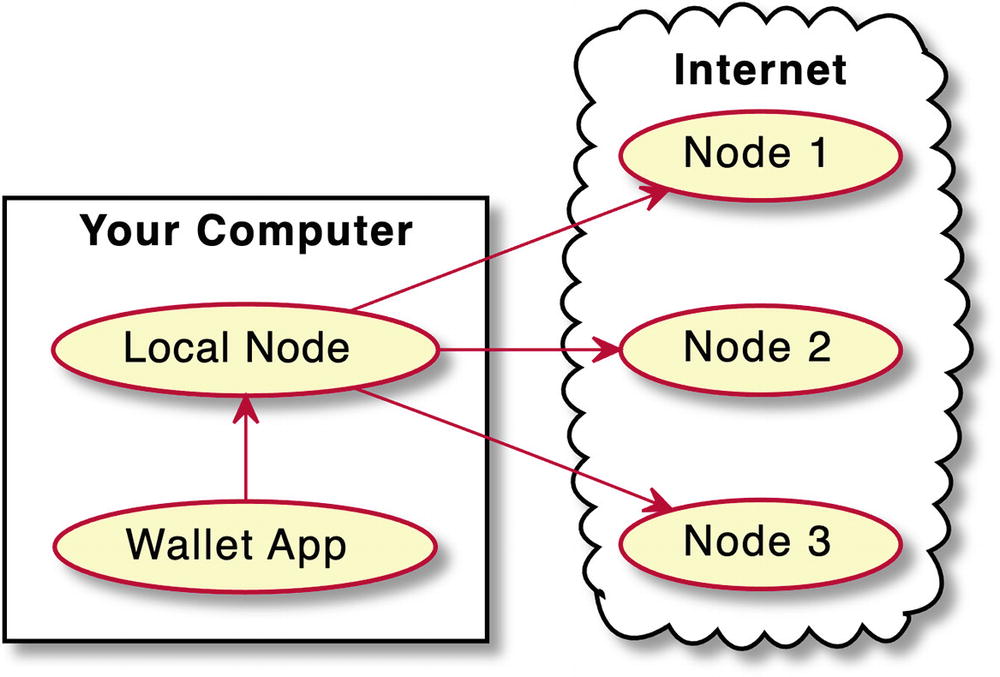
A diagram depicts the full node wallet like Bitcoin Core. The wallet app points to a local node in your computer. Local node points to nodes 1, 2, and 3 on the internet.
Full node wallet like Bitcoin Core
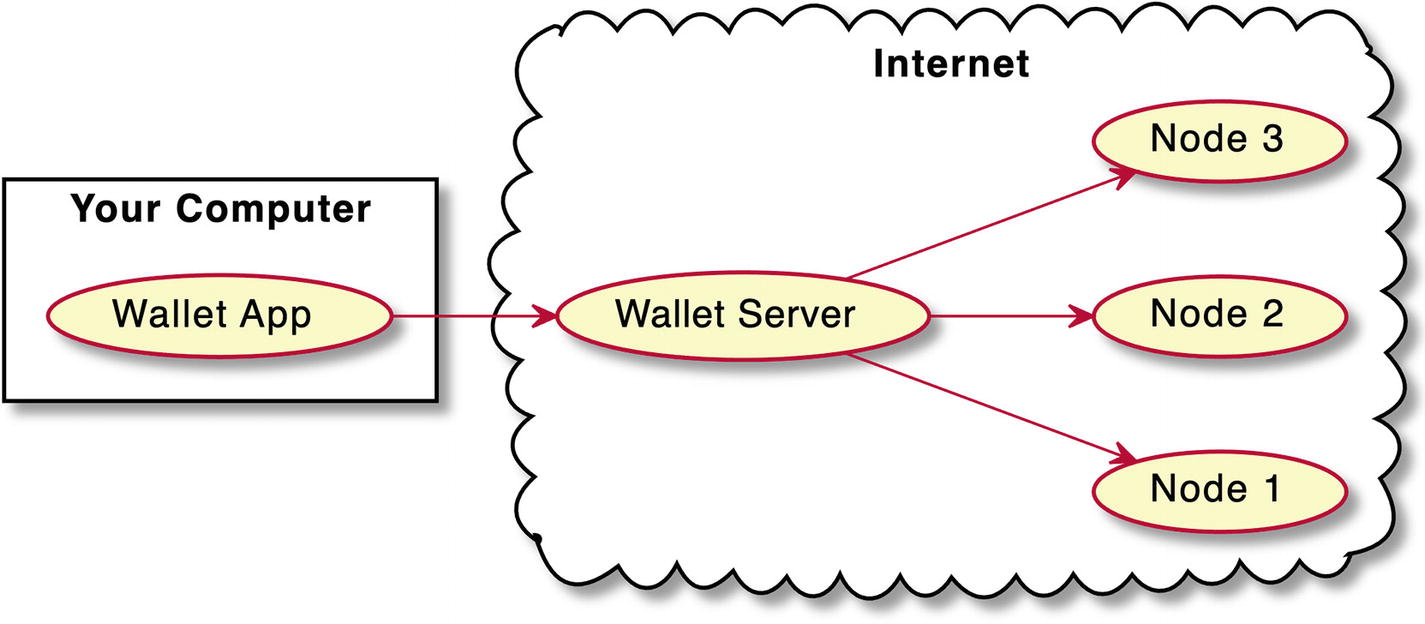
A diagram depicts electrum. The wallet app on your computer points to the wallet server on the internet. The wallet server points to nodes 1, 2, and 3 on the internet.
Thin wallet like Electrum requires a centralized “man in the middle”
The good news is that this “man in the middle” can be you. Electrum provides an option to run such a wallet server on your local machine and connect it to the full Bitcoin node, which you also run locally.7 Such configuration can be helpful if you want to use ChipMixer and other features offered by the Electrum wallet . But if you use a different mixer service and don’t need all these features like hardware wallet support, there is another, less complicated (but less featured) option: Bitcoin Core GUI wallet .8 It contains the full Bitcoin node, so the only thing it depends on is the decentralized Bitcoin network itself. In addition, it is developed as a community project and does not belong to any corporation.
Run Your Wallet with TOR
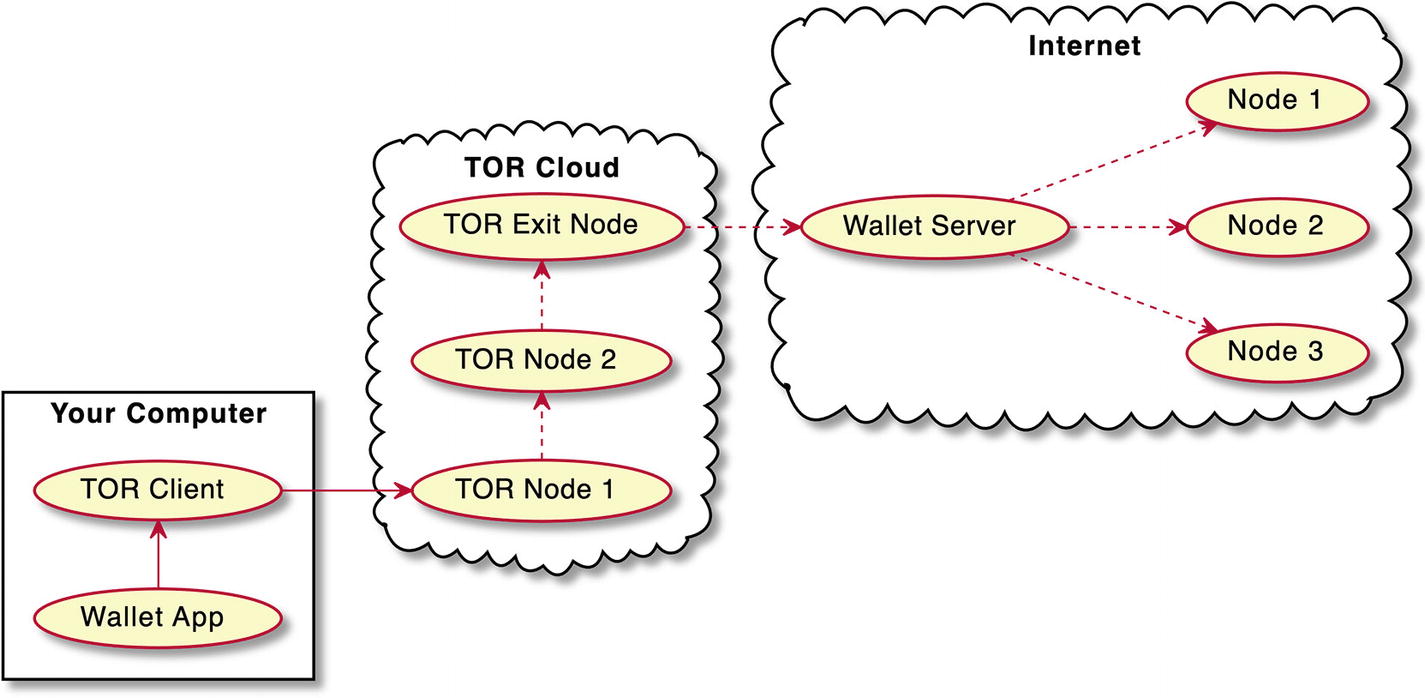
A diagram depicts a thin wallet like electrum on the T O R cloud. The wallet app on your computer points to T O R client. T O R client points to T O R node 1 and this points to T O R node 2. T O R node 2 points to T O R exit node and this points to wallet server on the internet. The wallet server points to nodes 1, 2, and 3 on the internet.
Thin wallet like Electrum on the TOR cloud
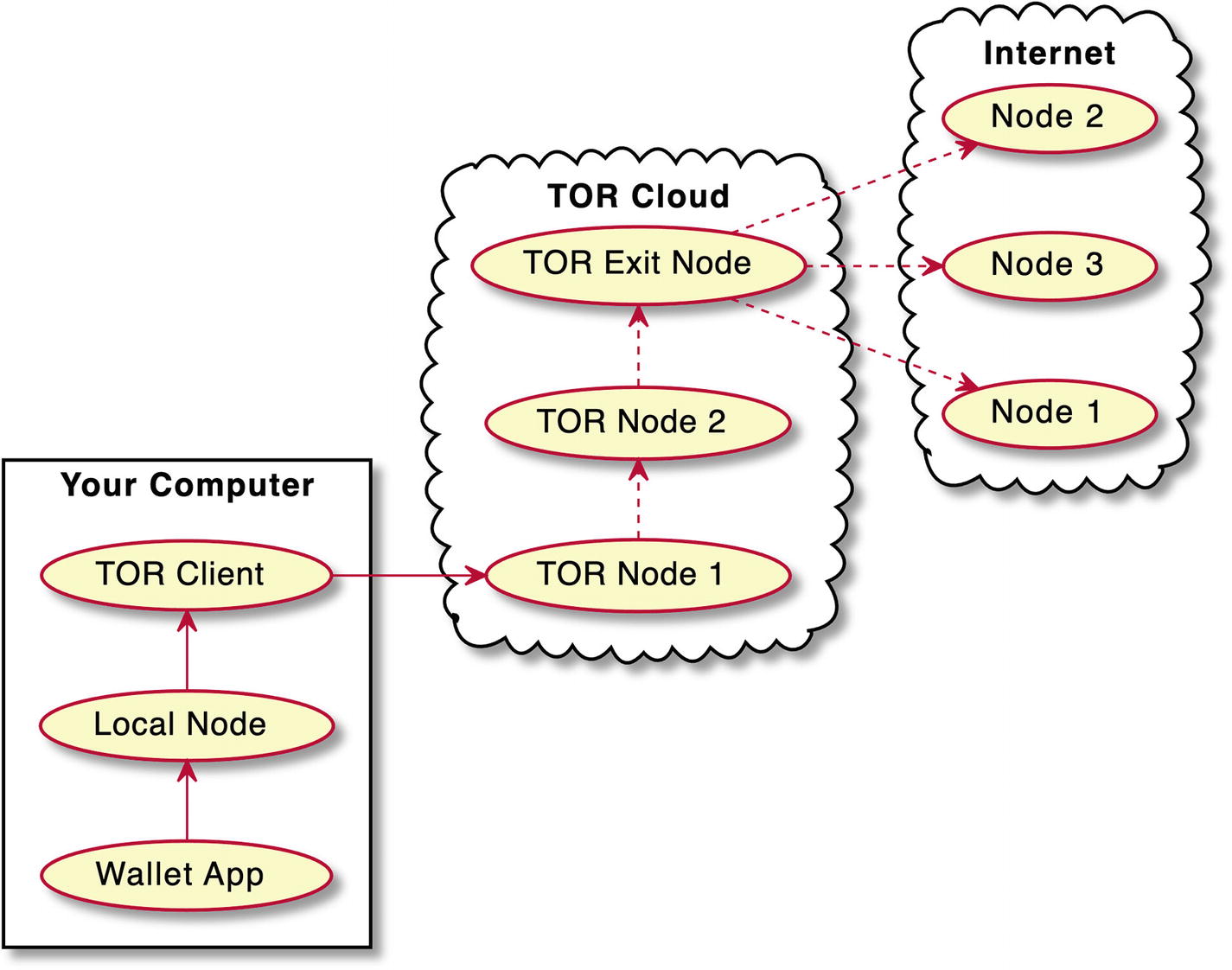
A diagram depicts a full node wallet like Bitcoin core on the T O R cloud. The wallet app on your computer points to local node and this points to T O R client. T O R client points to T O R node 1 and this points to T O R node 2. T O R node 2 points to T O R exit node and this points to wallet server on the internet. The wallet server points to nodes 1, 2, and 3 on the internet.
Full node wallet like Bitcoin Core on the TOR cloud
Install a TOR browser (this is simple; just click download and follow the instructions).
Launch the Bitcoin Core wallet, go to Preferences ➤ Network, and check “Connect through SOCKS5 proxy,” as shown in Figure 5-10. Then restart Bitcoin Core, and make sure that the TOR browser is running.
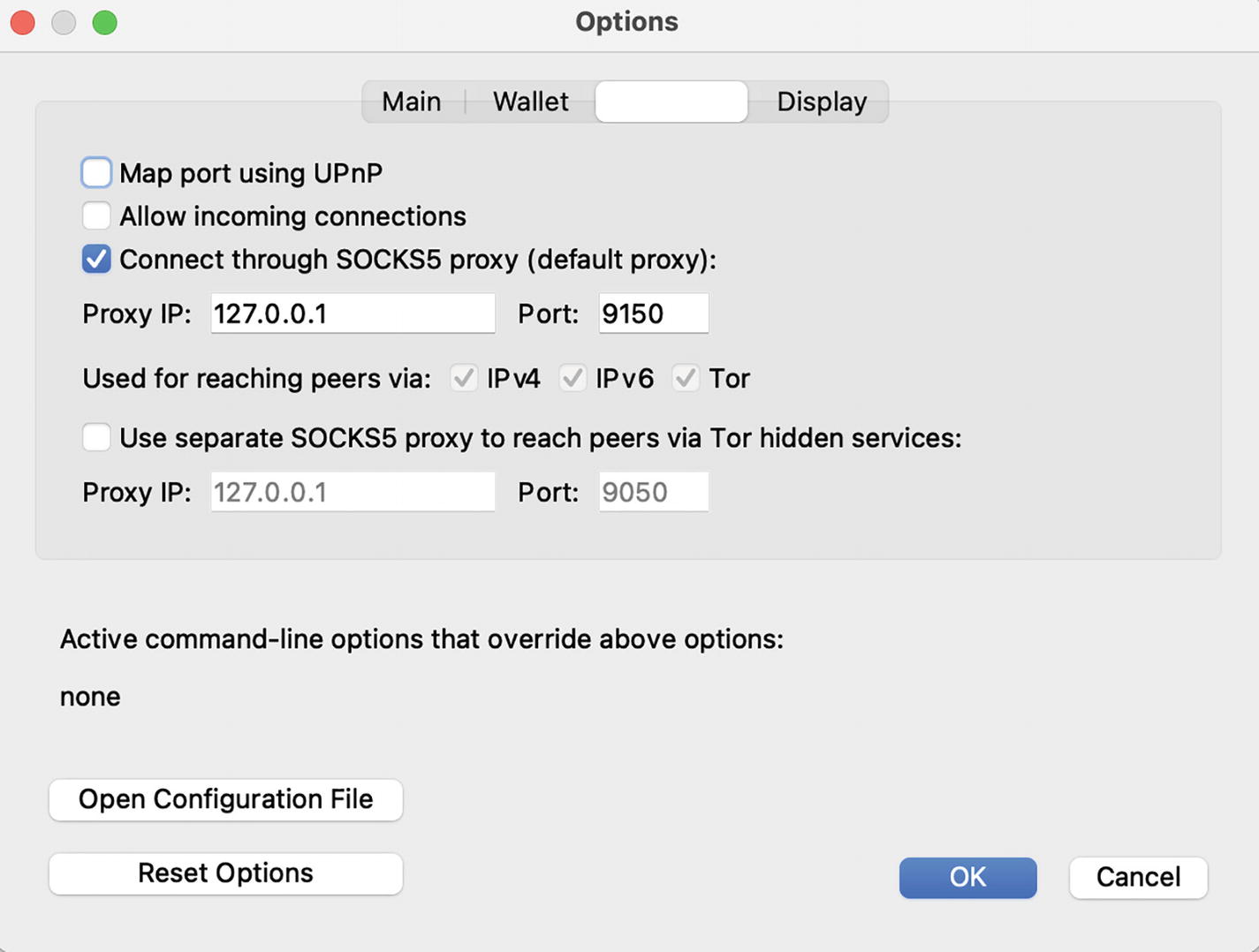
A screenshot depicts the Bitcoin Core wallet configured for the T O R network. Three tabs, Main, Wallet, and Display are at the top. The checkbox, connect through SOCKS5 proxy is selected. Proxy IP, 127.0.0.1. Port, 9150. Two buttons, OK and cancel are at the bottom. OK is selected.
Bitcoin Core wallet configured for the TOR network
Note that the default port number is 9050. If your wallet does not communicate with the network (shows 0 active connections when you tap over the network icon in the bottom right corner), change the port to 9150 and restart the wallet again.
Bitcoin TOR Nodes
With the TOR network enabled , your Bitcoin Core now communicates with Bitcoin nodes through TOR, which hides your IP address from anyone and your activities from your ISP. Your communication, however, can still be traced from the TOR exit node all the way to the Bitcoin nodes, so there is another small step you can take with the privacy of your wallet.
You can tell your Bitcoin Core to connect only to the Bitcoin nodes connected through the TOR cloud. And you already know what it means: these nodes must have onion addresses instead of regular IP addresses.9 When you are connected to Bitcoin nodes through TOR addresses, it closes the loop: your connection is fully “TORified.”
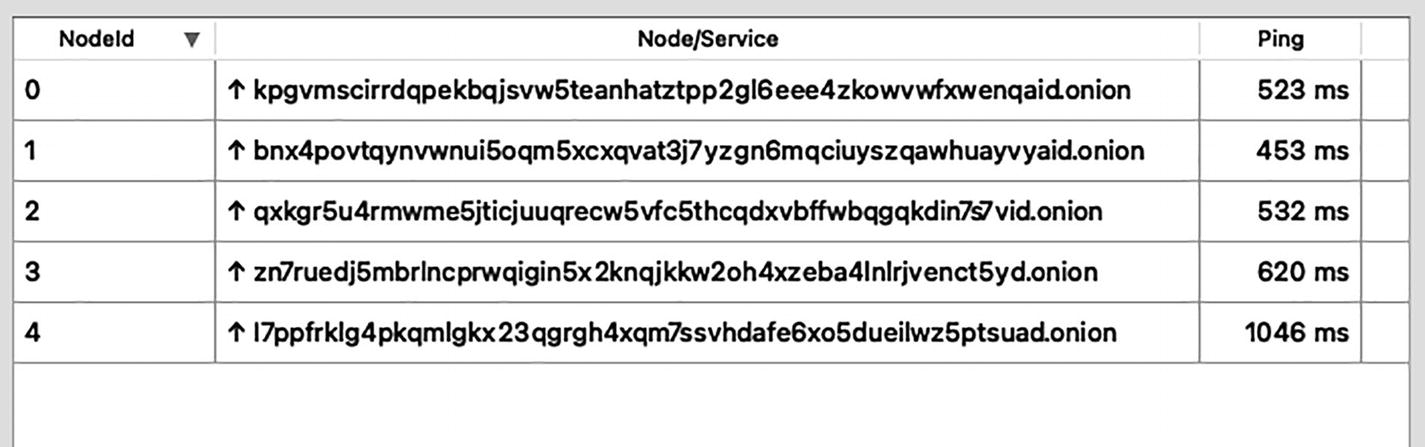
A table of 3 columns and 5 rows depicts the Bitcoin seed nodes. The column headers are N o d e l d, Node or service, and ping.
Bitcoin seed nodes with TOR “onion” addresses instead of IP addresses
What’s Next?
Although there is a common perception of crypto as a stronghold of privacy, you can see that this is not true for most coins and tokens. Pseudonymity provided by Bitcoin and others only creates an appearance of safety, masking the actual state of the crypto privacy. This is dangerous because we have not yet developed instincts that would intuitively protect ourselves in the crypto world, similar to how we manage to navigate the physical realm of cash and plastic cards.
Fortunately, however, there is a solution already: privacy-centric coins. We will see how Monero, the best privacy-centric technology, works in the next chapter. Looking ahead, I’ll just say that if you start using Monero, you can forget most of the tricks you just learned about in this chapter.
