Chapter 6
Cybersecurity Considerations When Working from Home
IN THIS CHAPTER
![]() Understanding that remote working creates security risks
Understanding that remote working creates security risks
![]() Understanding various types of risks created by — or made worse by — remote working
Understanding various types of risks created by — or made worse by — remote working
![]() Learning how to address risks when working from home
Learning how to address risks when working from home
In early 2020, the spread of a new, deadly and highly contagious disease — COVID-19 — began to facilitate a worldwide change in the way many people work. For the first time in generations, the need to stop a global pandemic led to governments enforcing lockdowns that prohibited people from working together in offices. Unlike during all prior such lockdowns in human history, however, technological advances made over the past few decades meant that many people who would otherwise have been unable to work, could, in fact, continue to do their jobs — albeit remotely.
Naturally, the sudden transition of a tremendous number of in-office workers to remote workers, and on such short notice, translated into a whole host of cybersecurity challenges. In addition, while many business leaders initially thought that the remote-working phase would be short-lived, that was not to be the case. Remote working in some fashion is here to stay, and, therefore, in the second edition of this book, I dedicate a chapter to discussing cybersecurity issues related specifically to working from home.
Network Security Concerns
A major cybersecurity concern with working remotely involves the networks from which remote employees access sensitive data. If those networks aren’t properly secured, two really bad things can occur:
- Someone may steal sensitive information — and neither the employee, nor the employer, may ever know that it happened.
- Malware or a hacker may compromise some user’s device and leapfrog from it to other corporate devices and networks — and, once inside corporate resources, wreak havoc in any one or more of many possible ways.
Why are remote-worker networks often unsafe?
Businesses often have much better firewalls than those offered in consumer products — and most remote workers are using consumer-grade routers and no additional firewalls. Should your employer really be trusting its cybersecurity to the router you bought for $19.99 on Black Friday five years ago? Likewise, most consumers have no idea how to configure their routers or firewalls, and utilize only basic options. Even when they are more sophisticated, people rarely deploy true intrusion detection systems and other security technologies at home. Such offerings are simply not available in inexpensive routers.
Businesses often have all sorts of security technologies deployed at their perimeters. An organization’s firewalls, for example, may block certain types of outbound requests, and data loss prevention systems may stop emails that contain sensitive materials that appear to have been inadvertently attached to the messages. Remote workers rarely, if ever, have such security functionality available from their routers. On that note, how many employers even know what routers their employees are using when their employees work from home, never mind know if those routers have had their firmware kept up to date? Do managers of businesses really know if an employee working from home has properly conducted vulnerability scans?
Besides the issue of the router’s patch level and firmware, how many employers have verified that their employees have properly secured their personal home-based Wi-Fi access points? And how many employers know who else is using the home network — and for what they are using it? Kids downloading games can easily infect computers with malware, and malware can spread via network connections.
While some have suggested that employers can utilize a full tunneling virtual private network (VPN) to address such risks — such a VPN would force all Internet traffic from the user to the employer’s network and would route all Internet requests through the employer’s security systems at the perimeter. Doing so is often highly risky as it essentially means that malware and other cyber-problems present on the employee’s home network can potentially propagate to the employer’s network. It also means that if something goes wrong with the employer’s connectivity, the employee cannot work — even remotely.
How can you address such risks?
Ideally, your employer should provide you with a second router that connects to your home router — the second router would effectively form a separate work environment, with a different network segment, that is logically (somewhat) isolated from all of the other devices on the network.
If properly set up, the work network will be able to initiate outbound requests to the Internet, but your home network will not be able to initiate requests to the work network. One way to do this is shown in Figure 6-1. This type of configuration is better than using one router, but still not ideal as the work network can still communicate with the home network. While, in theory, there are ways to ensure that such a configuration is still secure, the opportunity increases for making configuration mistakes undermining security. Ideally, therefore, use two internal routers as shown Figure 6-2. It should be noted however, that deploying the third network segment as shown in Figure 6-2 can complicate printing and various other tasks, but as printers are inexpensive and do not take up a lot of space, ask your employer to supply you with a work-related printer.
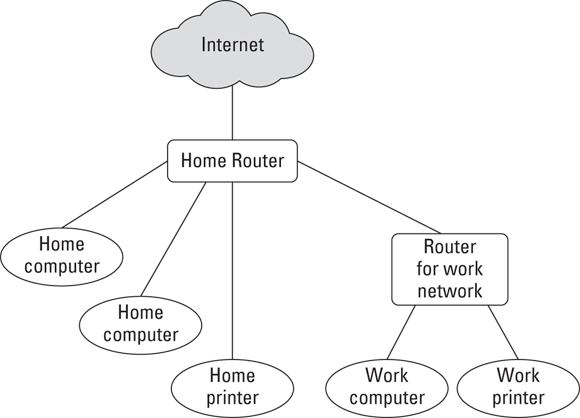
FIGURE 6-1: Network setup in which the work router communicates through the home router.
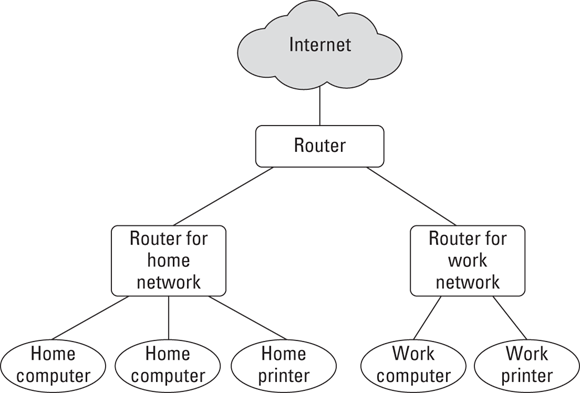
FIGURE 6-2: Network setup using separate routers for work and home.
Ideally, employees should also use computers owned by their employers — both for legal reasons (to prevent various privacy-related matters if private devices are used) and to prevent data leaks and prevent corporate data from ending up on computers that could be used by others and/or connected to insecure networks. In a perfect world, the only devices that ever connect to a work network are those owned by the employer.
Device Security Concerns
Insecure devices can lead to the same problems as insecure networks — data can potentially be pilfered and/or hackers can penetrate the organization and wreak havoc of all sorts. As I mention in the previous section, ideally, all devices used for work should be owned and managed by your employer. There are many reasons for this:
- Employers should know what is on workers’ devices so that workers can work efficiently and with minimal distractions and without potential spyware or the like capturing data or otherwise performing nefarious actions.
- Employers can be liable if they ask an employee to install an app on the employee’s personal device and the app creates vulnerabilities or otherwise causes problems, such as conflicting with other software on the device.
- If an employee suddenly leaves the organization and has work-related data on a personal device, that data may remain intact and put the employer at risk intentionally or inadvertently. The same holds true of the device is stolen from the employee. Likewise, in a more extreme case, if an employee were to die, who knows where the employee’s laptop containing sensitive work-related information will end up.
That said, issuing employer devices for employees to use from home is not always a practical possibility.
Location Cybersecurity
While we often think of the technology handing data as being the primary factor impacting the security of that data, the reality is that other factors play at least as great a role. As described throughout this book, people themselves are a significant factor. Another important element is the location in which systems are used and data is accessed. This factor has dramatically increased in significance as a result of the migration from in office working to remote working, which means that location-based dangers are more important than ever to understand.
Shoulder surfing
One of the greatest risks created by employees working remotely to the security and privacy of employer data is actually a quite old-fashioned danger. If an employee works in a place in which other people or cameras can see sensitive information as it is displayed on the screen of the user’s device, the confidentiality of the data may be compromised.
Such a problem is known colloquially as shoulder surfing. It is hardly a new concept, but it still remains a problem. Especially when large numbers of workers are expected to work outside of their usual professional workspaces. So, ideally, if you are going to work from home, do exactly that — work from home — and not from coffee shops, public parks, or the like.
Also, if possible, work in an environment that is configured in such a manner that your significant others and/or kids are not able to view sensitive information either. If need be, employers may even purchase furniture or equipment to help you ensure such privacy.
Eavesdropping
Similar risks apply in regard to voice communication — don’t discuss sensitive information over the phone or other voice communication system from a location in which other people can hear you. This may sound obvious, but prior to the pandemic, I heard many sensitive work-related calls transpiring on buses to and from New York City, while the bus-riding employee was oblivious to the fact that they were compromising the privacy of information that was clearly intended not to become public.
Theft
Home offices are rarely as well secured as professional office spaces, and public locations — such as parks, libraries, and coffee shops — are even less secure. Remote workers, therefore, often stand a greater chance of having a laptop stolen from them than do their counterparts whose devices never leave their normal at-work offices.
Human errors
It is important to understand that if people are repetitively interrupted, they are more likely to make mistakes than if that were not the case, and mistakes, of course, can easily lead to data leaks. If you are working remotely, create a workspace where you can keep disruptions to a minimum. Of course, remote working locations are often much more problematic than professional offices in such regard — especially during a pandemic when children are home all day and attend school virtually. So, seek to create a workspace in which you can work efficiently while staying focused and keeping data as private as is reasonably possible.
Video Conferencing Cybersecurity
As a result of the transition from in-office work to remote work that began in 2020 as a result of the COVID-19 pandemic, the use of video call and video conferencing technology has skyrocketed, with the number of people who regularly make work-related video calls from outside of their official places of work growing by orders of magnitude in just a short period of time. With the sudden and rapid adoption of such a transformative and unfamiliar technology comes risks, and, in the case of video conferencing, those risks include serious risks to information security and privacy.
Keep private stuff out of camera view
When you video conference, make sure you do not have any sensitive information or other private material on display in your camera’s frame. Keep in mind that mirrors and reflective surfaces in frame can also allow people in a video conference to see materials that are technically out of the camera’s view. If the preceding two points sound obvious, feel free to search online for how many significant cases are known of people not being careful as such.
Keep video conferences secure from unauthorized visitors
Video conferencing cybersecurity is about much more than just keeping sensitive data out of frame. In fact, the tremendous number of security violations that occurred during the earlier months of the COVID-19 pandemic — in which unauthorized parties regularly joined Zoom meetings and wreaked havoc — led to the creation and proliferation of a new term: Zoom bombing. To reduce the chances that your video communications will be Zoom bombed, consider the following advice:
- Never use video conferencing for secret conversations. No modern commercial video conferencing services are appropriate for truly secret conversations. Remember, video conferencing software, like all other software packages, may have exploitable vulnerabilities within it.
- Password-protect your sessions. If unauthorized users try to join your video calls without authorization, they will find doing so challenging, as without the password to your calls, they will not be able to easily join you.
- Create a new room name for every meeting. Some video call services allow you to use the same meeting room name over and over. Do not do so, as this makes it much easier for someone who obtains information about one of your calls to join another call.
- Use a waiting room. Many popular video-conferencing apps allow you to automatically redirect all participants into a virtual waiting room after they join the call. You, the host, get to decide who gets admitted from the waiting room into the actual call meeting room; you can usually either admit everyone in one shot, or select participants individually to admit into the session. You may also have the option of having pre-registered participants placed directly into the meeting room upon their joining the session, but forcing unknown parties seeking to join to wait for admission from the waiting room.
- Lock your sessions. Once all of the expected participants have joined a session, or after some period of time after the start of a session if some such folks have not joined, lock the session so that no additional parties can join.
- “Throw the bums out.” Periodically scan the list of who is participating in your meeting. If you see anyone who does not belong, remove them immediately! Likewise, if an authorized participant is causing problems during a video call session, consider removing them as well. If you locked the session, you should only need to review the list of participants once — right after you lock the session. Of course, if you have cohosts, your locking may be undone by them, so make sure to scan the participant list periodically.
- Disable private chatting. If possible, disable the ability of participants to private message one another via the video conferencing app. If they want to chat, let them use their regular chat apps.
- Do not allow general participants to share their screens. Unless there is a need for a particular party in a virtual meeting to share their device’s screen with other participants, either disable screen sharing altogether or set screen sharing to be available to only yourself, the host.
- Do not overshare meeting login information on social media. When possible — and I know that it is not always possible — do not share on public social platforms any login details for meetings. Instead, if necessary, advertise about the meeting, but require people to sign up for it, check the list of registered participants, and email the relevant login information to the folks who both signed up and you want to attend. And, in any event, private meetings should never be announced on public social media.
Social Engineering Issues
People who work from home, in environments separate from those in which their colleagues do their own jobs, are more likely to fall for some types of social engineering attacks than are people who work together, in person, with their colleagues. People in distinct locations cannot as easily verify the authenticity of a request. A homebound CFO who receives a request from a CEO to issue a payment, for example, cannot simply walk to the office next door and ask the CEO in person if the request is legitimate.
In addition, as we saw during the early weeks of the COVID-19 pandemic, many businesses that were forced to suddenly convert to a remote work model did not have the chance to properly prepare for such a situation, and as a result, various technologies that they had in place in their professional offices to reduce the likelihood of users being exposed to social engineering attacks were not successfully extended to remote locations prior to the commencement of remote work.
Regulatory Issues
The fact that people need to work remotely due to the rapid spreading of a dangerous virus does not negate the requirements of various laws and other regulations related to information security and privacy. Businesses subject to Europe’s General Data Protection Regulation (GDPR), for example, still must ensure that remote working does not undermine efforts to protect the privacy of personal information. Likewise, the fact that a medical facility might have allowed its clerical staff to work remotely on tasks such as billing insurance companies for services, does not excuse it from compliance with the relevant data protection requirements of the Health Insurance Portability and Accountability Act of 1996 (HIPAA). U.S. Securities and Exchange Commission (SEC) rules still apply as well — so insider information cannot be allowed to leak, or otherwise be provided even to authorized parties at inappropriate times. The same holds true for other regulations and industry guidelines.
Make sure your remote working program is not going to get you or others into regulatory hot water.

 In addition, because the work network router is supplied by your employer, your employer can select an appropriately equipped and remotely manageable device — and can keep it updated and patched.
In addition, because the work network router is supplied by your employer, your employer can select an appropriately equipped and remotely manageable device — and can keep it updated and patched. In any case, all computing devices — whether laptops, tablets, and/or smartphones — need appropriate security software installed, enabled, and kept up to date. Such devices should also have the ability to be remotely wiped if lost or stolen, and all relevant data on them must be both encrypted and appropriately backed up.
In any case, all computing devices — whether laptops, tablets, and/or smartphones — need appropriate security software installed, enabled, and kept up to date. Such devices should also have the ability to be remotely wiped if lost or stolen, and all relevant data on them must be both encrypted and appropriately backed up. When participating in a video conference from home in which your camera and/or microphone are on (for even part of the time), make sure that any and all other people in the home are aware that you are engaging in such a session. Warn them that you are sharing your camera feed and microphone, and that if they speak near you or walk near you, they may be heard or seen by others. Sadly, there have been many embarrassing incidents in which people walked half naked into the field of view of someone else’s video conference session.
When participating in a video conference from home in which your camera and/or microphone are on (for even part of the time), make sure that any and all other people in the home are aware that you are engaging in such a session. Warn them that you are sharing your camera feed and microphone, and that if they speak near you or walk near you, they may be heard or seen by others. Sadly, there have been many embarrassing incidents in which people walked half naked into the field of view of someone else’s video conference session.