Application security is becoming more and more important. As the cloud is becoming the de-facto standard for infrastructure in large companies, we can't rely on the fact that the data is confined in a single data centre.
Usually, when someone starts a new business, the main focus is to build the product from the functional point of view. Security is not the main focus and usually gets overlooked.
This is a very dangerous practice and we are going to amend that by letting the reader know the main security threats that could compromise our application.
The main four big security points to develop applications in a secure manner are as follows:
- Injection
- Cross-site scripting
- Cross-site request forgery token protection
- Open redirects
At the end of this section, we will be able to identify the main vulnerabilities, but we won't be armored against a malicious attacker. In general, a software engineer should be up to date with the security as much as they are up to date with new technologies. No matter how good the product you build is, if it is not secure, someone will find out and take the advantage of it.
As we stated before, security is an ongoing subject in application development. No matter what type of software you are building, there will always be security implications around it.
The best way I've found during my professional career to be up to date with security around web development without being a full-time dedicated security engineer is to follow the OWASP project. OWASP stands for Open Web Application Security Project and they produce quite an interesting document (among others) on a yearly basis called OWASP Top 10.
In the previous section, we identified the four main security issues that a software developer can face and all of them are mentioned in the following sections.
Injection is, by far, the most dangerous attack that we could be exposed to. Specifically, a SQL injection is the most common form of injection that affects applications and it consists of an attacker forcing a SQL code in one of our application queries, leading to a different query that could compromise the data of our company.
There are other types of injections, but we are going to focus on SQL injection, as pretty much every application in the modern world uses a relational database.
SQL injection consists of the injection or manipulation of SQL queries in our application through the input from non-validated sources, such as a web form or any other data source with arbitrary input of text.
Let's consider the following example:
SELECT * FROM users WHERE username = 'username' AND password = 'password'
This query will give us the user that corresponds to a given name and password. In order to build the query from the client's input, we can consider doing something similar to the following code as a good idea:
var express = require('express');
var app = express();
var mysql = require('mysql');
var connection = mysql.createConnection({
host : 'localhost',
user : 'me',
password : 'secret',
database : 'test_db'
});
app.get('/login', function(req, res) {
var username = req.param("username");
var password = req.param("password");
connection.connect();
var query = "SELECT * FROM users WHERE username = '" + username + "' AND password = '" + password + "'";
connection.query(query, function(err, rows, fields) {
if (err) throw err;
res.send(rows);
});
connection.end();
});
app.listen(3000, function() {
console.log("Application running in port 3000.");
});At first sight, it looks like an easy program that accesses the database called test_db and issues a query to check whether there is a user that matches the username and password and renders it back to the client so that if we open the browser and try to browse to the http://localhost:3000/login?username=david&password=mypassword URL, the browser will render a JSON object with the result of the following query:
SELECT * FROM users WHERE username = 'david' AND password = 'mypassword'
Nothing strange yet, but what happens if the customer tries to hack us?
Take a look at the following input:
http://localhost:3000/login?username=' OR 1=1 --&password=mypassword
As you can see, the query generated by it is the following code:
SELECT * FROM users WHERE username = '' OR 1=1 -- AND password = 'mypassword'
In SQL, the -- character sequence is used to comment the rest of the line so that the effective query would be as follows:
SELECT * FROM users WHERE username='' OR 1=1
This query returns the full list of users, and if our software is using the result of this query to resolve whether the user should be logged in or not, we are in some serious problems. We have just granted access to our system to someone who does not even know a valid username.
This is one of the many examples on how SQL injection can affect us.
In this case, it is pretty obvious that we are concatenating untrusted data (coming from the user) into our query, but believe me, when the software gets more complicated, it is not always easy to identify.
A way to avoid SQL injection is through the usage of prepared statements.
Applications interact with users mainly through forms. These forms usually contain free text input fields that could lead to an attack.
The easiest way to prevent corrupted data from getting into our server is through input validation, which as the name suggests, consists of validating the input from the user to avoid the situation described earlier.
There are two types of input validation, as follows:
- White listing
- Black listing
Black listing is a dangerous technique. In majority of cases, trying to define what is incorrect in the input takes a lot more effort than simply defining what we expect.
The recommended approach is (and will always be) to white list the data coming from the user, validating it through the use of a regular expression: we know how a phone number looks like, we also know how a username should look like, and so on.
Input validation is not always easy. If you have ever come across the validation of an e-mail, you will know what I am talking about: the regular expression to validate an e-mail is anything but simple.
The fact that there is not an easy way to validate some data should not restrict us from doing it as the omission of input validation could lead to a serious security flaw.
Input validation is not the silver bullet for SQL injections, but it also helps with other security threats such as cross-site scripting.
In the query from the previous section, we do something quite dangerous: concatenate user input into our query.
One of the solutions could be to use some sort of escaping library that will sanitize the input from the user, as follows:
app.get('/login', function(req, res) {
var username = req.param("username");
var password = req.param("password");
connection.connect();
var query = "SELECT * FROM users WHERE username = '" + connection.escape(username) + "' AND password = '" + connection.escape(password) + "'";
connection.query(query, function(err, rows, fields) {
if (err) throw err;
res.send(rows);
});
connection.end();
});In this case, the mysql library used provides a suite of methods to escape strings. Let's see how it works:
var mysql = require('mysql');
var connection = mysql.createConnection({
host: 'localhost',
username: 'root',
password: 'root'
});
console.log(connection.escape("' OR 1=1 --"))The small script from earlier escapes the string provided as username in the previous example, the result is ' OR 1=1 --.
As you can see, the
escape() method has replaced the dangerous characters, sanitizing the input from the user.
Cross-site scripting, also known as XSS, is a security vulnerability that mainly affects web applications. It is one of the most common security issues and the implications can be huge for the customer as potentially, someone could steal the user identity with this attack.
The attack is an injection code put into a third-party website that could steal data from the client's browser. There are a few ways of doing it, but by far, the most common is by unescaped input from the client.
In few websites on the Internet, users can add comments containing arbitrary input. This arbitrary input can contain script tags that load a JavaScript from a remote server that can steal the session cookie (or other types of valuable information), letting the attacker replicate the user session on a remote machine.
There are two main types of XSS attacks: persistent and non-persistent.
The persistent type of XSS consists of storing the XSS attack by crafting a particular string of text that resolves into the attack once it is displayed to the user in the website. This code could be injected via an arbitrary input text that is stored in the database (such as a comment in a forum).
The non-persistent type of XSS is when the attack is inserted into a non-persistent part of the application due to bad data handling.
Let's take a look at the following screenshot:
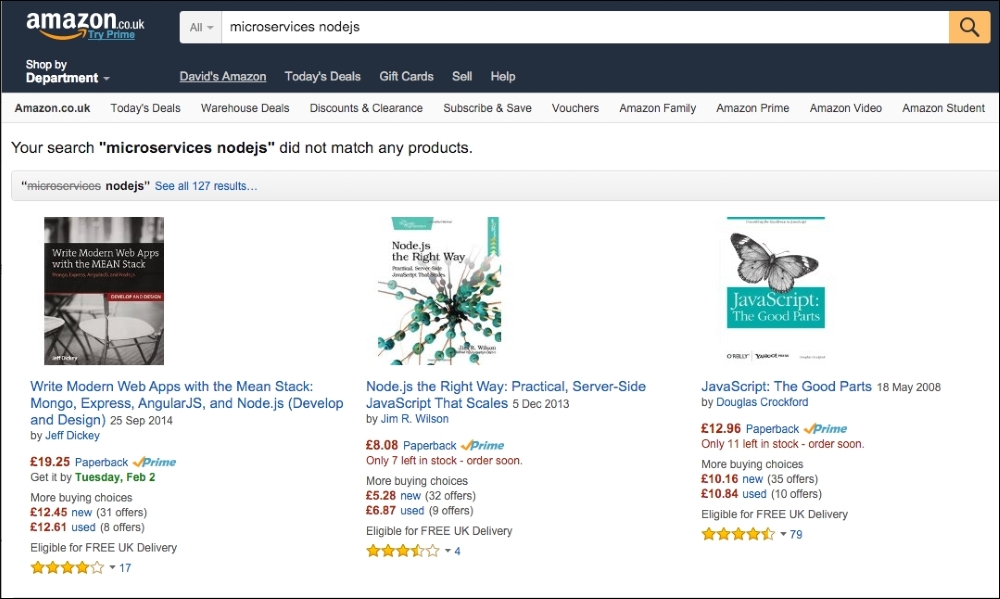
As you can see, we have searched for a book (this book) in http://www.amazon.co.uk/. It does not produce any output (as the book is not published yet), but it specifies that Your search "microservices nodejs" did not match any products, which is somehow using the input from the web browser as output. Even more, when I clicked on search, Amazon redirected me to the following URL:
http://www.amazon.co.uk/s/ref=nb_sb_noss?url=search-alias%3Daps&field-keywords=microservices+nodejs
We know Amazon is secure, but if it was sensible to XSS attacks, we could have modified the value of the field-keywords parameter to craft a request that injected a script tag in the content, leading to the attacker being able to steal the session cookie that could result in some serious problems for the website.
A way to protect against this attack is output encoding. We have done it before, when we used connection.escape() in the Input validation section of this chapter. In fairness, we should be validating all the data entered from the user and encoding all the outputs that come from third parties. This includes the input entered by the user, as well as sources of information coming from outside of the system.
When narrowing the problem to web development, we have to be aware of the three different areas where output encoding is needed:
- CSS
- JavaScript
- HTML
The most problematic two are JavaScript and HTML, where an attacker could easily steal information without too much effort.
Generally, no matter which framework we use for building our app, it always has functions to encode the output.
Cross-site request forgery (CSRF) is the reverse of cross-site request scripting. In cross-site request scripting, the problem is in the client trusting the data coming from the server. With cross-site request forgery, the problem is that the server trusts the data coming from the client.
After stealing the session cookie, the attacker can not only steal information from the user, but can also modify the information of the account associated with the cookie.
This is done by posting the data to the server via HTTP requests.
HTTP classifies its requests in methods. A method is basically used to specify what is the operation to be carried by the request. The most interesting four methods are the following ones:
GET: This gets the data from the server. It should not modify any persistent data.POST: This creates a resource in the server.PUT: This updates a resource in the server.DELETE: This deletes a resource from the server.
There are more methods (such as PATCH or CONNECT), but let's focus on these four. As you can see, three of these four methods modify data from the server, and a user with a valid session could potentially steal data, create payments, order goods, and so on.
A way to avoid the cross-site request forgery attack is by protecting the POST, PUT and DELETE endpoints with a cross-site request token.
Take a look at the following HTML form:
<form action="/register" method="post"> <input name="email" type="text" /> <input name="password" type="password" /> </form>
This form describes a perfectly valid situation: a user registering on our website; very simple, but still valid and flawed.
We are specifying a URL and the list of expected parameters so that an attacker can register hundreds or thousands of accounts within a span of minutes, with a small script that issues a POST request with the two parameters (email and password) in the body.
Now, look at the following form:
<form action="/register" method="post"> <input name="email" type="text" /> <input name="password" type="password" /> <input name="csrftoken" type="hidden" value="as7d6fasd678f5a5sf5asf" /> </form>
You can see the difference: there is an extra hidden parameter called csrftoken.
This parameter is a random string that is generated every time a form is rendered so that we can add this extra parameter to every form.
Once the form is submitted, the csrftoken parameter is validated to only let go through the requests with a valid token and generate a new token to be rendered on the page again.
Sometimes, our application might need to redirect the user to a certain URL. For example, when hitting a private URL without a valid authentication, the user will usually be redirected to the login page:
http://www.mysite.com/my-private-page
This could result into a redirect to the following:
http://www.mysite.com/login?redirect=/my-private-page
This sounds legit. The user is sent to the login page, and once he provides a valid set of credentials, it is redirected to /my-private-page.
What happens if someone tries to steal the account of our user?
Look at the following request:
http://www.mysite.com/login?redirect=http://myslte.com
This is a crafted request that will redirect the user to myslte.com instead of mysite.com (note the l instead of i).
Someone could make myslte.com look like the login page of mysite.com and steal your user's password and username by distributing the preceding URL in the social media as the users will be redirected to a malicious page.
The solution for the preceding problem is quite simple: don't redirect the user to untrusted third-party websites.
Again, the best way of doing such task is white listing the target hosts for redirects. Basically, we don't let our software redirect our customers to unknown websites.
One of the most effective ways to reduce security flaws in our applications is through a systematic and informed code review process. The problem with code reviews is that they always end up being a dump area for opinions and personal preferences that usually not only won't improve the quality of the code, but will also lead to last minute changes that could expose vulnerabilities in our application.
A dedicated stage in the product development life cycle for a security code review helps to drastically reduce the amount of bugs delivered to production.
The problem that the software engineers have is that their mind is trained to build things that work well, but they don't have the mindset to find defects, especially around the things that they build. This is why you should not be testing your own code (any further than the test carried on when developing), and even less, security testing your application.
However, we usually work in teams and that enables us to review someone else's code, but we have to do it in an effective manner.
Code reviews require as much brain power as needed to write software, especially if you are reviewing a complex code. You should never spend more than two hours reviewing the same functionality, otherwise important flaws will be missed and attention to detail will decrease to a worrying level.
This is not a big problem in microservices-based architectures as the functionality should be small enough to be read in a reasonable period of time, especially if you talked to the author about what he was trying to build.
You should always follow a two phase review, as follows:
- Review the code quickly to get the big picture: how it works, what technology it uses that you are not familiar with, does it do what it is supposed to do, and so on
- Review the code following a checklist of items to look for
This list of items has to be decided upfront and depends on the nature of the software that your company is building.
Usually, the list of items to check around the code security concerns during a code review is quite big, but we can narrow it down to the following components:
If we check this list, we will be able to identify the biggest issues around security in our apps.
