What You Should Do Right Now
Privacy is not a new concept; it existed long before the current digital age. It is a natural reaction of individuals to maintain their rights in public and to be left alone. As you saw in Chapter 1, the legal right to privacy is constitutionally protected in most democratic societies. However, the recent revelations of mass surveillance programs in addition to the new bills issued in the United Kingdom and United States against protecting users’ privacy cast doubt on whether your privacy is protected when online.
In today’s digital age, information gathering is fast, easy, and less expensive than in the past. Huge technological advancements in computing technology make it easy to collect vast volumes of data and store it for later analysis.
With buzz words such as hacking and cybersecurity appearing in the press regularly and being common topics of conversation among everyday technology users, information security and privacy are at, or at least should be, at the forefront of people’s minds.
In this chapter, we will present technical tips and best practices to assure your digital privacy when surfing the Web, sending e-mails, shopping online, banking online, and using social networking web sites. The practices covered in this chapter offer the first line of defense against online privacy threats. Advanced techniques in encryption, Windows hardening, data concealments, and many more will be covered thoroughly in the remaining chapters.
To better understand how you can maintain your online privacy, we’ll first introduce the types of computer security threats that you face online.
Types of Computer Security Risks
The Internet is full of risks! Whenever you go online, there is a possibility that you will encounter a risk. There are different types of computer threats with varying associations of damaging effects. For example, some threats may damage or corrupt your installed operating system and force you to reinstall it. Another type may steal your credentials and saved passwords. Still other threats may not bring any harm to your PC; instead, they will track your online activities and invade your privacy.
Today, criminals are smarter than ever before, and malicious programs are more sophisticated. Modern malware can infect a target PC and remain undetected for a long time. The motive behind the majority of cyber-attacks nowadays is not to damage your machine but instead to steal your money, to access your private information, or to acquire your logon credentials.
In this section, we will briefly talk about the main types of security risks that you may encounter when going online.
Malware
Malware is short for “malicious software” and is any software employed to bring damage to computing devices (computers, smartphones, etc.) or the stored content (data or applications). Malware corruption can manifest in different ways, such as formatting your hard disk, deleting or corrupting files, stealing saved login information, gathering sensitive information (your files and private photos), or simply displaying unwanted advertisements on your screen. Many malware variants are stealthy and operate silently without the user’s knowledge or awareness. Malware is a term used to refer to many types of malicious software such as computer viruses, worms, Trojan horses, spyware, ransomware, scareware, and adware.
Hacking
Hacking is the process of invading your privacy by gaining unauthorized access to your computing device. Hackers usually scan your machines for vulnerabilities (such as unpatched Windows updates) and gain access through them. After gaining access, they may install a keylogger or a Trojan horse to maintain their access, to begin stealing information, or to spy on user activities.
Pharming
Pharming is a cyber-attack intended to redirect users from a legitimate web site to a fraudulent site without their knowledge. Pharming can be conducted either by changing the hosts file on a victim’s computer or by poisoning the Domain Name System (DNS) server records with false information to lead users to unwanted destinations. DNS servers are computers responsible for resolving Internet names into their real Internet Protocol (IP) addresses.
If the Windows hosts file gets infected with malware, it can change its contents and insert redirects, so when the user types the legitimate URL, the browser may then redirect to a malicious web site that has the same look and feel. When the user enters his or her username and password, the malicious web site will receive them instead of the original one, thus resulting in a compromised user account and credentials.
To mitigate such attacks, you can prevent hosts file modifications by following these steps:
Navigate to the %SYSTEMDRIVE%WindowsSsystem32driversetc folder (SYSTEMDRIVE is where you installed Windows, usually at C:).
Right-click the hosts file, select Properties, and select the Read-only attribute; finally click OK (see Figure 2-1).

Figure 2-1. Changing hosts file attributes to Read-only to avoid pharming attacks on Windows machines
Phishing
Phishing messages come in different shapes, such as SMS messages, e-mails, and web site links (URLs), all of which are designed to look genuine and use the same format as the legitimate company. Phishing aims to collect user-sensitive details (such as banking information, passwords, and credit card details) by tricking the end user into handing the information to the attacker. Phishing is covered in detail later in this chapter.
Ransomware
Ransomware is computer malware that installs silently on the user machine. Its objective is to deny access to user files, sometimes encrypting the entire hard disk drive and even all the attached external disk drives. It then demands that the user pay a ransom to get the malware creator to remove the restriction so the user can regain access to the system and stored assets.
Most ransomware hits devices through phishing e-mails and pop-up advertisements. There are three major types of ransomware.
The first one locks the system in a way that is not difficult for a technical person to reverse; it displays a message requesting payment to unlock it.
The second type encrypts the whole disk drive, including any removable storage, and demand a ransom to decrypt it (but there’s no guarantee of getting any data back).
The third is a variant that pretends to be ransomware but is actually trickware, which can easily be removed. Figure 2-2 shows an example that was mounted against the iPad and iPhone.

Figure 2-2. Sample trickware mounted against Apple devices
Victims of ransomware usually pay the ransom through the bitcoin digital currency (more on bitcoins in Chapter 4).
Ransomware usually comes hidden in a legitimate file. When the user installs the legitimate program, the ransomware gets installed as well without the user’s knowledge.
Ransomware is now the number-one security concern for organizations. As the number of attacks increase, it has become a global problem that threatens both individuals and companies. According to CNN, cyber-criminals collected $209 million in the first three months of 2016, meaning that at the end of 2016 this number may reach $1 billion. This number may be even bigger than that, though, because some victims may choose to pay and not report the crime. 1
Adware and Spyware
Adware is used to collect information about you and your machine. It usually comes with free software or useful plug-ins or search bars for web browsers; once installed, it begins tracking your online activities and may then send it to outside parties. Many free games and free system utilities contain adware. As we already said in Chapter 1, few users read the end-user license agreements (EULAs) and simply click the “I agree” button without knowing that the freeware may contain adware (which is clearly stated in their EULAs).
Spyware in the form of a keylogger will seek to steal everything you type on your keyboard (usernames and passwords) and send it to its operator. Some spyware can facilitate installing a virus on your operating system, rendering it inoperable. Other forms can do this via the in-house/in-home Wi-Fi connection, communicating any acquired credentials and information into the hands of an awaiting actor.
Trojan
This type of malware can infect computer silently. It usually installs itself as part of a legitimate software installation. In fact, many Trojans work stealthily in the background and are undetectable by antivirus programs. Most of the popular banking threats come from a Trojan family like Zeus and SpyEye. Trojans can potentially gain access to all your system functions including the camera and microphone . They also have the ability to delete files and monitor your online activities and keystrokes or even to detect other Trojans that may be installed by other criminals and then to remove them, making the new resident Trojan the only active variant on the target system.
Virus
Computer viruses have been around now for at least two decades and are one of the oldest traditional risks known since the early days of personal computers. They have morphed through many variations of dangerous profiles. A virus is a malicious program that infects a target PC or its content with the objective to make the computer inoperable, thus possibly forcing drastic action like a reformat to return to its normal state. Some viruses cause more damage such as stealing your contact list and credentials and facilitating unauthorized access to your machine. Nowadays, viruses are not widely used because they have been replaced with other types of malware that enable attackers to generate revenue from their attacks such as ransomware.
Worms
The Morris worm, or Internet worm, was one of the first to be seen in the wild. In November 1988, it was distributed via the Internet and caused significant damage to the infected systems. This is now another type of old-school attack that is still widely used. However, unlike viruses, which aim to destroy or compromise the OS, the worm works to spread from one machine to another through internal networks or the Internet. Many types of worms attack the e-mail client (e.g., Microsoft Outlook or Thunderbird) and copy themselves to all contacts in the address book to further distribute their infection to new locations. Worms can make computers run slowly because they can consume your disk space and Internet bandwidth. Worm propagations can cause tremendous lost in revenue for companies when spread inside a company’s intranet.
Wi-Fi Eavesdropping
No matter whether you are at home, at work, or at a public access point, hackers can intercept communication communicated through unprotected wireless networks and access points. Such attacks can result in intercepting all your online communications, including your usernames and passwords, and of course may provide access to your online banking details.
Scareware
Scareware is a form of malicious software that uses social engineering to cause shock, anxiety, or the perception of a threat in order to manipulate users into buying unwanted software. 2 For example, scareware can report to a user that his or her machine is full of spyware and other infections and he or she must act promptly and purchase an anti-malware solution (which is fake!). The idea here is to trick the user into purchasing something unnecessarily in order to take his or her money.
Distributed Denial-of-Service Attacks
A distributed denial-of-service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. Attackers build networks of infected computers, which could be millions of machines, known as botnets, by spreading malicious software through e-mails, web sites, and social media . Once infected, these machines can be controlled remotely by a bot master, without their owners’ knowledge, and used like an army to launch an attack against any target.
Botnets can generate huge floods of traffic to overwhelm a target. These floods can be generated in multiple ways, such as sending more connection requests than a server can handle, manipulating the TCP flags (like the well-known Christmas Tree attack did), or having computers send the victim huge amounts of random data to use up the target’s bandwidth.
Cyber-criminals don’t have to make their own malware these days; they can purchase ready-made malware in the form of crime wave as a service (CaaS) that is ready to launch DDoS attacks against any web site they choose. An underground black market (we will talk about this later in the book) offers the Bot Malware Kit, which can be used to infect a large number of computers, create a botnet, and launch a DDoS attack for only $200. 3
Rootkits
A rootkit is a dangerous type of malware; it can potentially gain full access (administrative access) over the system and has the ability to prevent normal detection programs (antivirus and anti-rootkit programs) from noticing its presence. Some dangerous rootkits attack at the hardware level (firmware rootkit ), and removal may require hardware replacement or specialized intervention.
Juice Jacking
In this attack, an intruder will steal your private data through the USB charging port of your smartphone, tablet, or laptop when you connect your device to a public power-charging station such as the ones available in airports, conferences, and restaurants. Malware can also get installed using this technique. To counter such risks, do not charge your computing device in public charging stations; use personal power bank units instead.
Install Antivirus and Other Security Solutions
Installing an antivirus program is considered the first line of defense for any computer user. However, keep in mind that having an antivirus solution does not mean you are covered on the whole Internet security front. Unfortunately, some antivirus products try to give the impression (for marketing purposes) that they will completely cover all security holes once installed.
Traditional antivirus programs are useful against classical threats such as viruses, worms, some types of malware, phishing , and spam. But the end user may still need a specialist solution against spyware and ransomware in addition to a firewall solution for maximum protection. The majority of commercial antivirus solutions come with an integrated firewall; each product has its own configuration manual to explain how to use it. In this section, we will demonstrate how to use a free dedicated firewall from Comodo. All personal firewalls use the same configuration terms, so this should help you to configure yours easily. For now, we’ll start by talking about computer antivirus software.
How to Select Your Antivirus Program
Antivirus software usually uses three basic methods for detecting, blocking, and removing viruses.
Signature-based detection
Heuristics detection
Rootkit detection
Most personal antivirus solutions use a combination of signature-based detection and heuristic technology. Although most antivirus programs have a similar approach for detecting malicious software, some are better than others. To help you select the best one, we have created a number of criteria that should be met by your future antivirus solution.
The antivirus program should detect and remove malware of all kinds (including ransomware or any other financial malware).
It should be able to detect phishing attacks and dangerous web sites and deny access to them.
It should be able to integrate with major e-mail clients (such as Microsoft Outlook and Thunderbird) to scan incoming and outgoing e-mails automatically in addition to filtering spam e-mails.
It should be compatible with the currently installed operating system and programs.
It should come equipped with a personal firewall.
It should update itself automatically.
It should be efficient in terms of discovering zero-day malware and updating its virus signature database instantly.
If the antivirus has the ability to detect rootkits, this is an excellent extended feature.
It should have a lower number of false positive alerts or false alarms (this happens when antivirus software recognizes legitimate software as malware).
It should be able to protect your browser from outside attacks.
It should have a DNS protection feature (more about DNS in Chapter 4).
It should be lightweight and not consume high computing resources when scanning files or working in the background.
It should not renew its license automatically without explicit approval.
It should be affordable to you.
Microsoft has a free antivirus solution that provides protection against different types of computer malware called Microsoft Security Essentials (MSE). MSE has received generally positive reviews for its simple user interface, low resource usage, and freeware license. MSE can be installed on Windows 7; however, modern versions of Windows (Windows 8, Windows RT, Windows 8.1, Windows RT 8.1, and Windows 10) have Windows Defender built into Windows that helps guard your PC against viruses and other malware. Windows Defender surpasses MSE for having enhanced protection against rootkits and bootkits. If you’re looking to protect an older PC running Windows 7, you can use Microsoft Security Essentials ( http://windows.microsoft.com/mse/ ).
The main disadvantage of both MSE and the modern Windows Defender is the lack of a personal firewall. Despite this fact, these products are excellent choices for Windows. With regard to the firewall issue, you can install a separate solution from Comodo, as you are going to see later.
Note
Install antivirus alongside Windows Defender. Windows Defender will automatically disable itself when you install a third-party antivirus program and then reenable itself again if you decide later to uninstall that third-party antivirus program. It’s designed to get out of the way.
Other free antivirus solutions offer good basic protection for your Windows PC, as shown in Table 2-1.
Table 2-1. Some Free Antivirus Solutions
Antivirus | Main Feature | URL |
|---|---|---|
360 Total Security | Its virus definition signature is based on four antivirus engines (360 Cloud Scan Engine, 360 QVMII AI Engine, Avira, and Bitdefender). | https://www.360totalsecurity.com/en/features/360-total-security/ |
Avast | This captures emerging threats (real-time analysis of unknown files). | |
AVG AntiVirus Free | This provides basic protection against viruses and other malware. |
If you want to purchase a paid antivirus solution (always recommended as they offer more comprehensive protection), you can always check the Independent IT-Security Institute web site at https://www.av-test.org/en/ , which conducts regular tests to find the best antivirus solution for different operating systems (including smartphones) according to specific technical and security criteria.
Anti-exploit
An antivirus program by itself is no longer an adequate security measure on its own. Emerging threats require you to install additional solutions for full protection. Anti-exploit programs help you survive against sophisticated attacks such as Flash and Silverlight exploits and Browser vulnerabilities. Anti-exploit tools also provide protection against zero-day malware.
The Enhanced Mitigation Experience Toolkit (EMET), available at https://www.microsoft.com/en-us/download/details.aspx?id=50766 , is a free product from Microsoft. EMET anticipates the most common techniques that adversaries might use in compromising a computer and helps protect by diverting, terminating, blocking, and invalidating those actions. EMET helps protect your computer systems even before new and undiscovered threats are formally addressed by security updates and anti-malware software.
Anti-spyware
Running anti-spyware software for computer safety is considered to be just as important as having antivirus software. Spyware is a kind of malware that tracks your online activities and sends it to third parties. The more dangerous spyware can steal everything you type on your keyboard and send it to its creator. Antivirus solutions have the ability to detect different kinds of spyware; however, it is advisable that you have a dedicated solution for spyware removal for maximum protection.
Spybot S&D ( https://www.safer-networking.org ) is a popular free program used to detect and remove different kinds of adware, malware, and spyware from your computer system. Spybot S&D (the free edition) is not an antivirus tool. It can, however, run alongside antivirus software to enhance the security of your PC. The paid edition comes supplied with antivirus functionality.
Anti-malware
As we said previously, malware includes all types of malicious software that can damage your operating system and stored files. Every day a large number of malware programs are launched online. The security solutions we already talked about can stop many types of malware, but it is recommended that you have a dedicated solution to stop malware attacks only. Spybot S&D (the free edition) comes with an anti-malware functionality, but there is another famous program for detecting malware called Malwarebytes ( https://www.malwarebytes.com ). The free edition can detect and remove malware and advanced threats in addition to removing rootkits and repairing the files they damage. Malwarebytes doesn’t require advanced configuration. Install it and you are ready to go, making it a preferable solution for beginners.
Warning
It is not recommended that you install Spybot and Malwarebytes at the same time because they both have anti-malware functionality.
Firewalls
A firewall monitors and controls the incoming and outgoing network traffic and helps you to screen out hackers, viruses, and worms that try to reach your computer over the Internet. All Windows versions, beginning from Windows XP SP2, have a firewall built in and turned on by default. However, this firewall has some limitations compared with third-party firewalls. (For example, it monitors incoming traffic only, while letting outgoing traffic flow freely; also it does not offer an easy-to-use interface for its advanced features.) You can access Windows Firewall (in all Windows versions) from Control Panel ➤ Windows Firewall.
The primary function of a firewall is to block unrequested incoming and outgoing connections. It allows you to set access permissions for each program on your computer. When one of these programs tries to connect to the Internet, your firewall will block it and launch a warning message unless it recognizes the program and verifies that you have given it permission to make that sort of connection. By doing this, your firewall prevents any currently installed malware from connecting to the outside world to spread viruses or to communicate with hackers to invade your machine.
Tip
To better configure the advanced features of the built-in Windows Firewall, you can install a tiny program called Windows Firewall Notifier ( https://wfn.codeplex.com ) that helps you to better visualize Windows Firewall functions.
The majority of the paid versions of antivirus solutions come equipped with a personal firewall, but if you opt to install a free edition, then you need to have a dedicated personal firewall installed on your machine. There are many free firewall solutions for Windows; however, configuring a firewall could be a daunting task for beginners, so it is better to install one that is easy to configure and provides maximum protection. The free Comodo firewall has such characteristics.
Because of the importance of a robust firewall on every computer accessing the Internet, we will describe how to set up and configure the Comodo firewall in some detail. Before beginning the installation of Comodo firewall , though, make sure that your current antivirus software doesn’t have its own firewall activated as part of it. Also, make sure to deactivate the built-in Windows Firewall.
Install the Comodo firewall by following these steps:
Download the Comodo firewall from https://www.comodo.com/home/internet-security/firewall.php . The current version of the Comodo firewall is 10. After downloading the program, execute the installer to begin the installation wizard. The first screen in the wizard asks you to select your installation language. In our case, we are selecting English. Then click the I AGREE button to move to the next step.
Comodo may ask you to set Yahoo as your default home page and search engine. In our case, we are unchecking this option. Click Next to continue.
The next wizard has two tabs. The first one asks whether you want to send anonymous program usage information and whether you want to use cloud-based behavior analysis. Uncheck both options.
The next tab asks you whether you want to install the additional components, which are Comodo GeekBuddy (for technical support) and Comodo Dragon Web Browser. In this case, we are unchecking both. Now click the Install button to begin installing the firewall (107MB). This may take some time depending on your Internet connection speed.
Upon finishing, the final wizard window will ask you to enter your e-mail if you want to receive offers and news from Comodo. In our case, we are selecting not to receive anything. Click the Finish button. Restart your computer to finish the installation.
After Windows restarts, Comodo will detect your current network connection and ask you about your location. In this case, select “I am at Home.”
The Comodo firewall desktop icon appears in the system tray. To access the firewall settings, double-click this icon.
Note The default settings of Comodo are suitable for most users; however, we prefer to use custom rules in order for interactive protection to investigate all incoming and outgoing connections.
Once Comodo’s main interface appears, click Settings (see Figure 2-4).

Figure 2-4. Comodo program main interface
Go to Firewall ➤ Firewall Settings and check Enable Firewall (Recommended). From the drop-down menu, select Custom Ruleset. Finally, click the OK button to accept the new settings (see Figure 2-5).

Figure 2-5. Modifying the firewall settings to become a custom ruleset for interactive protection
After implementing the new setting, every time the Comodo firewall receives a connection request, it activates a pop-up firewall alert prompting you to either allow or block access to your system to and from the Internet (see Figure 2-6).

Figure 2-6. Example of Comodo firewall alert when trying to access the Internet using Mozilla Firefox
It is advisable to be strict in allowing programs to connect to the Internet. Do not hesitate to stop any suspicious program from connecting to the Internet. If you suspect any program, you can simply click its icon to open the Properties window and learn more about the process or program requesting access (see Figure 2-7).

Figure 2-7. Investigating iexplore.exe by clicking its process name in the Comodo alert message
You can further configure application rules and change the rules for previously running applications by going to Settings ➤ Firewall ➤ Application Rules. From here you can see the list of firewall application rules currently activated on this system. Select any one (by selecting its check box) and then click Edit to further customize its online behavior (e.g., allowing outbound traffic while denying inbound traffic) (see Figure 2-8).

Figure 2-8. Configuring specific application firewall rules (Firefox in this case)
The Comodo firewall comes with a default host intrusion prevention system (HIPS ) ruleset that works “out of the box,” providing extremely high levels of protection without any user intervention. For example, HIPS automatically protects system-critical files, folders, and registry keys to prevent unauthorized modifications by malicious programs. Advanced users looking to take a firmer grip on their security posture can quickly create custom policies and rulesets using the powerful rules interface.
We will not delve more into how to configure the Comodo firewall. We cover its basic usage here to impress upon you the importance of having a firewall on your computer. You can find everything you want to know about the Comodo firewall in the help section of the product online page ( http://help.comodo.com ). We highly encourage you to have a firewall installed on your PC before going online because there are many threats that cannot be stopped by regular antivirus/anti-malware software.
Tips to Use Antivirus Software Efficiently
Here are some tips to follow in order to achieve the maximum efficiency when using your antivirus software:
Do not install two antivirus programs at the same time. They may be in conflict, slow down your machine, or cause instability problems in your computer.
Make sure your antivirus program is updating itself automatically. If you are suddenly disconnected from the Internet, make sure to update it manually when you have your connection back.
Perform or schedule a full scan for the entire system. Antivirus programs usually perform automatic scans; however, this scan doesn’t cover all system areas (only critical locations), so it is advisable to run a full system scan each week for maximum protection.
Be cautious before executing any software downloaded from the Internet. It is better to execute such programs on an isolated virtual machine before installing them on your work PC.
Do not open e-mail attachments before scanning them using your antivirus program. Executable programs and scripts should not be opened at all when sent through e-mails.
Do not insert removable media (such as USB stick drives, DVDs, CDs, external hard disks, and SD cards) from unknown sources into your computer. Many viruses reside on such removable media and can infect your computer even when you have an antivirus program installed.
Passwords
People’s choice of passwords continues to pose a huge security risk. Recent data breaches of user personal data and account passwords show that a large number of users are still using risky passwords to secure their accounts. According to SplashData’s 2015 “Worst Passwords List” (compiled from more than 2 million leaked passwords during the year), the two most commonly used passwords by online users were 123456 and password, both of which have remained at the top of the list since it first started in 2011. The report also shows that despite many users attempting to create more secure passwords, the majority are based on simple patterns that would be easily guessed by hackers. Examples include 1234567890, 1qaz2wsx (the first two columns of the main keys on a standard keyboard), and qwertyuiop (the top row of keys on a standard keyboard); these all appeared in the top 25 list.
In this section, we will give guidelines and tools for creating strong passwords.
Create Secure Passwords
Here are some tips to create secure passwords:
The password should be at least 15 characters in length for maximum security.
The password should contain at least one lowercase letter, one uppercase letter, one number, and one symbol (e.g., # % &).
The password shouldn’t be your username or even part of it.
Do not use your spouse’s, family member names (including your name), or pet’s name as part of your password.
Do not share the same password between your spouse or friends (have two e-mails with the same password).
Do not use your gender or birth date/place as part of your password.
Do not use places names for your password (country, city, street name, school, or university name).
Do not use famous people’s names as your password (e.g., famous movie actors, political leaders, public figures, singers).
Avoid sequences when creating passwords (consecutive letters, numbers, or keys on the keyboard such as 123456 or asdfghjkl).
Do not use the same passwords for two different accounts (e.g., your bank account password and your private e-mail password should not be the same).
Change your password once every three months.
Do not use the same password again (e.g., when you change your e-mail password, do not return and use any password you were using during the last year).
Do not use dictionary words as your password or part of it.
Do not use real words from foreign languages as your password.
Use a password manager to organize and protect passwords, generate random passwords, and automatically log into web sites.
Don’t store your passwords in an unencrypted text file or Microsoft Excel spreadsheet or any other file type that is not encrypted. Also, never write down your password on paper. If you want to take your password with you and you are afraid that you may forget it (because it is complex), then use a portable password manager and keep it on your smartphone or on your USB stick drive.
Do not let your web browser save your entered passwords.
Do not use tools to automatically generate your password for top important accounts (e.g., bank accounts and medical record accounts). For such important accounts, follow the rules already mentioned and create something from your mind.
Do not send your password if someone requests it from you. Many social engineering attacks involve making users trust the attacker and getting them to share their passwords.
Whenever you hear about a data breach in press, instantly change your affected account password.
Do not ever type your password on a computer that does not belong to you.
Password Generation Tools
Obviously, it is important to change your passwords continually and to use strong, complex passwords that can be difficult or impossible to crack using brute-force , dictionary, or guessing attacks. Many users may fail to create such complex passwords or may simply repeat and use a portion of the old password to create the new one, which is considered an insecure practice. In this section, we will give you some tools and services that can help you to generate strong and complex passwords.
Free Password Generator ( https://www.securesafepro.com/pasgen.html ) is a free, lightweight tool for generating secure and complex passwords. It has a portable version and can run on all Windows versions.
PWGen ( http://pwgen-win.sourceforge.net ) is an open source professional password generator capable of generating large numbers of cryptographically secure “classical” passwords, pronounceable passwords, pattern-based passwords, and passphrases consisting of words from word lists. It uses a “random pool” technique based on strong cryptography to generate random data from indeterministic user inputs (keystrokes , mouse handling) and volatile system parameters. It also has some interesting features because it can encrypt, decrypt, and clear the clipboard so that no information is intercepted when copying passwords out of this program.
Many web sites offer online password generation services. However, we prefer not to use such services because your password can be intercepted while traveling to your PC (even though some of these services encrypt the password before sending it to you or simply use a script to run locally on the user’s client machine).
Tip
Most password manager tools contain a password generation utility. So, you can opt to use one tool for both generating your secure passwords and storing them directly in a safe encrypted database.
Now you may wonder that after you have successfully created your strong passwords, how can you keep them all in a safe location? The next section will answer this.
Password Managers
As you already saw, the majority of users use weak passwords and repeat using them across different web sites. This bad practice happens because humans have difficulty remembering long, complex passwords, especially if they have many accounts with different passwords. The solution for this problem is to use a password manager.
A password manager allows you to store all your online accounts’ login details in one place. When you want to log in to any service/web site, all you have to do is copy the username/password to the login form. A password manager encrypts the database that contains your login information and protects it with a master password. This is the only password you have to remember.
It is always preferable to use open source tools, especially when dealing with security software. Open source tools can be audited for backdoors , thus providing confidence to its users. The following sections highlight open source password managers that also have a password generation feature.
KeePass Password Safe
KeePass Password Safe ( http://keepass.info ) is a free open source password manager. You can take a look at its full source and check whether the encryption algorithms are implemented correctly. KeePass has a portable version so you can run it from your USB stick. It has been ported onto different platforms such as macOS, iOS, Linux, and Android.
Master Password
Master Password ( https://ssl.masterpasswordapp.com ) has a unique approach to generating user passwords. Its passwords aren’t stored in an encrypted database or uploaded to a secure cloud service. Instead, they are generated on the fly using the following parameters: your name, the site you are going to use the password for, and your master password (which is the main password used to log in to the Master Password program). This unique approach to password creation/management guarantees that your passwords will not get intercepted as you synchronize your account between devices (for example, your smartphone and PC). In addition, you do not need any repository to store these passwords. All you need to do is install the Master Password tool on each device you want to use and then enter your name and site names and you are ready to go (see Figure 2-10).

Figure 2-10. Sample password generated using the Master Password tool
Password Safe
Password Safe ( https://www.pwsafe.org ) is an open source program that allows you to easily and quickly generate, store, organize, retrieve, and use complex new passwords, using password policies that you control. The original version was designed by renowned security expert Bruce Schneier. Password Safe is designed to be extremely hard to crack using brute-force attacks, and it encrypts all user data in memory when using it.
You can copy a username and password from your saved entries by right-clicking the entry, without needing to access and view the record itself.
The password managers introduced in this section are all offline (except for Master Password, which uses a stateless approach) and store users’ passwords in a safe location on the device being used. We still find that storing user passwords on your own computing device or a USB memory stick is the most secure solution for keeping such important information away from outside interception.
In addition to storing your credentials safely, password managers can make you more resistant to many types of keyloggers because they can securely send your password directly to the form fields in your browser without needing the user to type usernames or passwords for the keylogger to pick up. Password manager software is considered a type of encryption software, and it can be vulnerable to different attack types (both hardware and software based). We will cover these attacks and suggest countermeasures in Chapter 5.
Warning
Password managers don’t completely protect against keyloggers that actually scan the forms in web browsers. It also cannot protect you against malware that has direct access to your computer clipboard.
Secure Your Online Browsing
Your web browser is your window to the entire world. From here you can log in to your social media accounts, access your bank account, buy products and services, and check your e-mails, in addition to anything else you do online. The wealth of information that exists in web browsers makes them attractive for cyber-criminals. Thus, it is necessary to tweak your browser security settings to make it less vulnerable to outside attacks.
There are many desktop browsers ; the market share is mainly divided between Microsoft Internet Explorer (IE), Mozilla Firefox, Safari, Opera, and Google Chrome. IE and its successor Edge come preinstalled on the Windows OS; however, we always encourage users to use open source software to assure maximum security when working online. Mozilla Firefox is still considered the only true open source browser among the main browsers already mentioned, so in this book we will cover using this browser only.
In this section, we will give useful basic tips to secure your online browsing. In Chapter 4, we will cover advanced configuration for Firefox to harden it against online threats.
Turn On Private Browsing
Most modern web browsers have a privacy feature called private browsing that lets you browse web sites without your history being tracked locally on your computer. When this is enabled in Firefox, Firefox will not record your visited pages, cookies , temporary files, and searches. Firefox will also activate tracking protection , which will block parts of web sites that try to track your browsing history across multiple sites.
To enable private browsing in Firefox, go to the Firefox menu at the top-right corner of your browser window and then click New Private Window (see Figure 2-11). You can also use the Ctrl+Shift+P keyboard shortcut to access it directly.

Figure 2-11. Setting New Private Window in the Firefox browser
A new Firefox window will appear showing you what is saved and what is not saved while browsing in this mode.
As we said, Firefox will also enable tracking protection, which blocks common advertising trackers , social sharing trackers, and analytics trackers. If you want Firefox to be more aggressive in blocking all trackers, you can enable this feature from the Firefox menu (see Figure 2-11). Select Options, go to the Privacy tab, click the Change Block List button, and select “Disconnect.me strict protection. Blocks known trackers. Some sites may not function properly.” Finally, click Save Changes (see Figure 2-12).

Figure 2-12. Enabling aggressive tracking protection to block all online trackers using Mozilla Firefox
Keep in mind that activating strict protection may break the functionality of some web sites, so if this happens and you want to disable protection for a specific web site, click the little shield icon in the address bar and then click “Disable protection for this session” (see Figure 2-13).

Figure 2-13. Disabling tracking for a specific web site when you are in private mode
Read Web Site Privacy Policies
When you join a social networking web site or buy something online, you are asked to agree to the terms of use and to read and agree to the privacy policy agreement before proceeding. Such policy agreements will usually contain information on how the web site will collect data from your computer and how the web site will share it. Because the privacy policy agreement is long and full of legal terms, people tend not to read it at all.
Another misconception about privacy policies is that users assume having a privacy policy on a web site means that their personal information is protected. In truth, many privacy policy agreements contain terms that violate users’ rights to privacy.
We always encourage you to read the privacy policy agreement in full (for critical services and software) or at least the important sections of it to be aware of any violation against your personal data. To make things simpler for you, just look out for these key items while reading:
What type of information will the site/software collect about you?
Will your personally identifiable information (PII) or anonymous information be shared with third-party affiliates?
Will your information will be disclosed overseas?
Can you opt out from this agreement later?
Where will your information be stored ?
Who has access to your information (check all possible parties, including law enforcement and security services)?
Can you access the service later to update or delete your personal information ?
Can you make a privacy complaint?
When will your information be discarded or deleted? Some sites store information for specific periods of time, while some store your information indefinitely.
What kind of security measures will protect your information?
Focus on everything written in capital letters.
Use Ctrl+F to conduct a search for the following keywords in the agreement: third party, affiliate, opt out, arbitration, contents, advertisers. When finding any of these words, read the corresponding section carefully.
When signing your agreement, make sure that https:// appears in the browser bar to indicate a secure connection.
These tips will help you read the privacy policy agreement quickly, but they may not prevent you from signing a bad agreement; nevertheless, it’s still better than signing an agreement without reading it!
Disable Location Information
Sure, it sounds like a great idea to check into your favorite bar or restaurant on Facebook, Yelp, Google+, and more, but a simple click with your smartphone could unknowingly put you in trouble. Major social networking web sites give you the ability to “check in” and reveal your current location on a map. For example, many people “check in” with their Facebook account at home to announce some events (e.g., a birthday party), which will reveal the user address publicly. The same person can later announce he or she is at a restaurant or going on a vacation; for thieves, this means an empty home ready for robbery.
Robbery is not the only danger of revealing your location through the check-in feature; your child’s safety can be at risk. If your child also performs regular check-ins, this will reveal the current location of your family members and will simplify attacking them if you or they become a target someday. It is highly advisable to deactivate location services in your social networking app, teach your children to do the same, and ask them not to reveal their location using written status updates either.
To disable the location service in the Facebook app (on Android ), open the Facebook app, tap the menu button, and select Account Settings ➤ Location ➤ Location Services ➤ Turn it OFF.
Each version of Android, iOS, and Windows Phone has its own settings to disable location services. As a rule of thumb, you can search for disable location services X (substitute your operating system version or phone model for the X) to find a detailed guide on how to disable it on your phone/tablet.
Another important feature that must be turned off on your smartphone is recording geotagging information, which contains the GPS coordination of your current location when a photo has been taken. This feature is sometimes useful, but, for instance, it could reveal your address information if you take pictures in your home or work office.
The GPS information stored with your shots is part of the Exchangeable Image File (EXIF) data. This is metadata about the image file itself and does not appears to the naked eye; it contains different technical metadata information such as the time and date of each photo and the camera used to take it (see Figure 2-14).
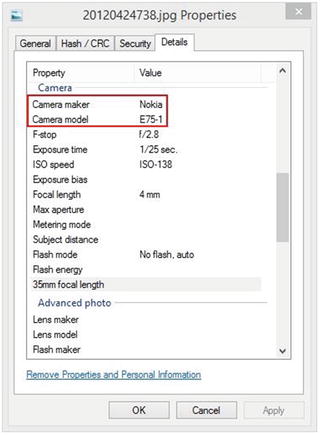
Figure 2-14. Metadata of a JPEG image showing mobile phone and camera type that took the shot
You can disable the “location tag ” on your smartphone, thus preventing it from recording your current geolocation on all future shots. To do this on an Android phone, turn on the camera, go to Settings ➤ Location tags, and turn it off (see Figure 2-15).

Figure 2-15. Disabling “Location tags” on Android smartphones
On iOS, go into Settings, tap Privacy, and then tap Location Services; toggle the Camera option to off. If you cannot find the specified setting on your smartphone, search for disable location tags in X (with your smartphone or OS type instead of the X).
Some social networking web sites strip out geolocation information and other metadata automatically before publishing it online. Twitter and Facebook do so, but some web sites do not. So, to stay in the safe zone, always turn location tags off and read the next section to learn how to remove metadata of different digital file types.
Remove Metadata from Digital Files
Metadata is a data about data. In technical terms, it contains hidden descriptive information about the file it belongs to. For example, some metadata included in a document file might include author name, date/time created, and comments.
From a privacy perspective, users are mainly concerned about the metadata that exists in digital images, but keep in mind that metadata exists in almost all digital files such as documents, video and audio files, and web pages. Metadata usually comes stored in the digital file; however, some file types store it in a separate file.
There are three types of image metadata.
Technical metadata: This data is usually generated by the capturing camera. It contains information such as camera type and brand name, date/time when the photo was captured, geolocation information (if enabled) of the captured image, and the ID number of the device.
Descriptive metadata : This data is added by the user using a specific software program to add details about the captured images. For example, the user can add the photographer name, comments, title, and caption, among other things.
Administrative data: This data is added manually by the image creator to protect the photo; such data may contain copyright information and the contact address for licensing.
EXIF is a standard that specifies the format for images, sound, and ancillary tags used by digital cameras (including smartphones), scanners, and other systems handling image and sound files recorded by digital cameras. 4
EXIF data is embedded within the image file and works with JPEG images only. EXIF metadata can contain geolocation metadata in addition to a wide array of technical information.
Other metadata standards include the Extensible Metadata Platform (XMP) and the International Press Telecommunications Council (IPTC). XMP is a metadata standard developed by Adobe Systems. It’s based on XML and was designed to allow the exchange of standardized and custom metadata for digital documents and data sets. Hence, it’s a format that can be used to describe any kind of asset, not limited to pictures (e.g., support video, audio, and PDF files).
IPTC is an older meta-information format, which is slowly being phased out in favor of XMP . The newer IPTCCore specification uses the XMP format. IPTC information can be found in JPEG, TIFF, PNG, MIFF, PS, PDF, PSD, XCF, and DNG images. 5
It is advisable to check the metadata of all images before uploading it to the Internet to avoid leaking private information about yourself and the device. There are many freeware tools that can view and edit a digital file’s metadata; we’ll begin with digital images.
Exif Pilot ( www.colorpilot.com/exif.html ) is a free EXIF editor that allows you to view, edit, and remove EXIF, EXIF GPS, IPTC, and XMP data in addition to adding new tags and importing and exporting EXIF and IPTC to/from text and Microsoft Excel files (see Figure 2-16).

Figure 2-16. Using Exif Pilot to view and edit EXIF/IPTC tags
Other free tools that can be used to remove image metadata are GIMP ( https://www.gimp.org ) and XnView ( www.xnview.com/en/ ).
Windows comes supplied with a built-in function that allows you to view and remove some metadata associated with documents and digital images. However, keep in mind that Windows may not be able to remove all EXIF tags, so if you intend on sharing important files, always use the suggested third-party tools already mentioned.
To remove EXIF using Windows, right-click the image, select Properties, and go to the Details tab. At the bottom, click Remove Properties and Personal Information to open the EXIF removal tool. The tool lets you either create a copy of the image with all metadata removed or pick and choose which properties to erase from the selected file (see Figure 2-17).

Figure 2-17. Removing EXIF metadata using the Windows built-in function
As we already said, Microsoft Office documents, PDF files, and audio and video files all have metadata associated with them. We will cover how to remove them quickly in a moment.
To clear metadata from PDF files, Adobe has a feature called Sanitize Document. After clicking it, you can remove all hidden metadata from the intended PDF file (see Figure 2-18).

Figure 2-18. Clearing PDF file metadata
Please note that not all versions of Adobe Reader support the sanitization feature. If your currently installed version does not support it, you can use a third-party tool for this purpose such as ImageMagick ( https://www.imagemagick.org/script/index.php ) or Pdf Metadata Editor ( http://broken-by.me/pdf-metadata-editor/ ).
To view/edit and remove audio file metadata, use Mp3tag ( www.mp3tag.de/en/ ). This is a powerful and easy-to-use tool to edit the metadata of audio files. It supports batch tag-editing of ID3v1, ID3v2.3, ID3v2.4, iTunes MP4, WMA, Vorbis Comments, and APE tags for multiple files at once, covering a variety of audio formats.
To remove a video file’s metadata, use MediaInfo ( https://mediaarea.net/en/MediaInfo ).
To remove metadata from Microsoft Office documents, do the following: for Microsoft Office 2010, 2013, and 2016, you can check the document metadata by selecting File and then going to the Info tab. The Properties panel will be on the right side; from here you can remove document metadata by clicking the Properties button and selecting Advanced Properties (see Figure 2-19).

Figure 2-19. Removing Microsoft Office document metadata
In Microsoft Office 2007, you need to click the Microsoft Office button and then select Prepare ➤ Properties to edit the document metadata.
Another issue you need to consider when sending Microsoft Office documents to outside parties is deleting other hidden metadata. Fortunately, Microsoft Office provides a functionality for deleting hidden metadata. You can access this feature in Microsoft Word 2013/2010/2016 from File ➤ Info ➤ Check for Issues ➤ Inspect Document. In Microsoft Word 2007, you can access this feature by clicking the Office button and selecting ➤ Prepare ➤ Inspect Document.
Make Sure to Log Out
Whenever log in to your social networking account, your e-mail, or an online retail account, make sure to log out when finished. Web sites usually put the login/logout links at the top of the web site. If you are using Firefox in private mode, it will log you out automatically when you close it. Giant companies like Facebook and Google can track your online activities and link them back to your real identity (on Facebook or Google ID ) easily when you remain logged in while you browse the Internet or conduct regular searches. The same thing happens to smartphone applications; the majority of users remain logged in to their Facebook app while browsing the Internet on their mobile device. This practice is bad and will reveal much about your personality and online habits, as we mentioned in Chapter 1.
How to Know Whether a Web Site Is Secure
Millions of dollars are spent daily on web sites such as Google, Amazon, and eBay. These giant companies use the latest technology to protect their assets and customers from cyber-criminals , but when comes to new web sites and online stores, you should be careful that the web site is secure before giving any information or making any purchase. The following are some quick tips that you can use to tell whether a site is secure.
Check the Web Site SSL Certificate
SSL certificates are small data files that digitally bind a cryptographic key to web site details. When installed on a web server, the certificate activates a padlock and the Hypertext Transfer Protocol Secure (HTTPS) and allows a secure connection between the company server and the client machines. Upon installing the SSL certificate, the URL of the web site will begin with https:// instead of http:// (the s stands for “secure”).
To get an SSL certificate, a company must undergo a validation process. There are different levels of validation. Some require only a valid domain name; others require more information about the company behind the certificate. The lowest validation level requires that you prove that you have the right to use the domain name that you are trying to secure (usually done through checking the Whois record of your domain). This type of validation is not secure because an attacker could buy an SSL certificate and bind it to a web site dedicated to conducting phishing attacks.
A more stringent validation will require (in addition to domain validation) you to submit official documents about your company such as a business license/certificate, public records filing for a new business entity, certificate of payment of business tax, or any official documents that can validate your business legitimately. This kind of validation is called extended validation (EV) and uses the highest level of authentication and a rigorous verification process. You can tell when a site is using an EV certificate because the address bar will be green, and the security status bar will reveal detailed information about the company operating the web site when you hover the mouse over it (see Figure 2-20). EV certificates incorporate some of the highest standards for identity assurance to establish the legitimacy of online entities.

Figure 2-20. Sample web site protected with EV SSL certificate
Check the Domain Name
Cyber-criminals create web sites that are identical to an existing one and try to trick people into logging in or purchasing items from it. These web sites are designed to look completely legitimate and like an existing web site.
It is highly advisable to type the URL of your intended web site directly in the address bar of your browser instead of clicking links that come in e-mails, especially e-mails that ask you to update your bank, PayPal, or online store account details. For example, a criminal could buy the domain name Go0gle.com and set up a web site that looks just like the Google.com home page. Then the user could buy an ordinary SSL certificate (that only needs domain name validation) and try to trick users into signing in to their Google account to receive a prize by sending the fake URL through phishing e-mails. When the user clicks the fake URL and accesses his or her Google account, his or her credentials will travel to the attackers, and the fake web site will forward the user to the real Google web site to avoid raising suspicion.
Legitimate Web Sites Do Not Have Pop-Ups
Most reputable retailers don’t use pop-ups; they know that customers strongly dislike them and that using pop-up ads may turn customers away.
Know That Legitimate Web Sites Do Not Send Spam
Reputable web sites don’t send you spam e-mail unless you specifically signed up to get information from them or their partners. Be cautious and do not click links in spam e-mails .
Check the Physical Address
Reputable retailers usually put their physical address and phone number on the Contact Us page or in the footer or header of the web site.
Other Indicators of Fake Retailer Web Sites
Here are some other indicators:
If you are shopping for products online and find a store that offers very low-priced items, be suspicious. Such web sites could be a scam to steal your money.
Always look for a return policy and shipping policy . Reputable retailers have such documents clearly on their web sites.
Fake web sites usually do not accept credit cards; they ask for debit cards or for checks. This is because they want to stay anonymous and do not have a legitimate presence to make agreements with credit card companies to accept online purchases.
The overall design of the web site should be consistent and professionally developed. Broken pages and inconsistent colors or themes across pages should raise suspicion about the web site. Credible web sites have excellent design and support mobile devices.
Do Not Install Pirated Software
As software prices increase, many users illegally download pirated software from the Internet to save costs. Such software usually comes with an executable program named Crack or Patch to unlock the pirated program trial version and make it work like the paid one. Running executable programs to unlock legitimate software is dangerous, especially because many pirated program instructions ask the user to turn off antivirus software to avoid any conflict while installing. The pirated software might be disguised malware that will install silently upon executing it. This will effectively jeopardize your personal security.
Another risk is disabling updates . Users are forced to stop automatic updates of pirated software to avoid being discovered by the developer company. For example, when you install a cracked version of Windows or any security solution (e.g., an antivirus solution), you may not be able to update it regularly like the original version. This will leave your software or OS vulnerable to different risks.
If you prefer to use freeware programs downloaded from the Internet, it is highly advisable to use your antivirus solution to scan them before executing them. To become more confident, you can scan the downloaded program with free scan services, which comes in handy when you want to scan a specific file/program using multiple antivirus engines.
VirusTotal ( https://www.virustotal.com ) is a free service that analyzes suspicious files and URLs and facilitates the quick detection of viruses, worms, Trojans, and all kinds of malware. All you need to do is enter the web site URL you want to check or to upload the file/program to see whether it is clear from malware threats.
Update Everything
Be careful to configure Windows to install automatic updates ; your web browser and antivirus should both update automatically.
To configure Windows (applicable to Windows 7 and 8) to install updates automatically, go to Control Panel ➤ System. On the bottom left, click Windows Update. On the left side, click “Change settings,” and from the drop-down menu, select “Install updates automatically (recommended)” (see Figure 2-21).

Figure 2-21. Configuring Windows 8 to install updates automatically
In Windows 10, automatic updates are enabled by default.
E-mail Security
E-mail is the most used service through the Internet; it is widely used for both business and private communications. Using it unwisely or without appropriate protection can make you susceptible to different online threats. Here are some important tips to consider when using your e-mail service:
Do not access your primary e-mail account using free, open Wi-Fi access points in public places.
Use encryption when using an e-mail client (e.g., Mozilla Thunderbird) and make sure to encrypt the connection between your computer and e-mail server.
Create multiple e-mail accounts. Dedicate one e-mail to sign up for free offers and services, keep one for private use, and use another for your daily work. There are many providers that offer free e-mail services; Google and AOL are among them.
Do not use free e-mail service for mission-critical work. Giant free e-mail service providers such as Google (Gmail) and Microsoft (Live) scan e-mail contents to deliver targeted advertisements to their users.
Encrypt all your mission-critical e-mails. Chapter 5 will cover e-mail encryption .
Do not publish your primary e-mail address online; instead, use another account for public use.
Make sure that your antivirus solution can scan inbound and outbound e-mails in your e-mail client and can stop spam and phishing scams .
Do not open e-mail attachments from unknown senders. If a friend on your contact list sent you an e-mail with an attachment, make sure to scan it first for malicious software.
Beware of phishing scams that use fraudulent e-mails and fake web sites, masquerading as legitimate businesses, to trick unsuspecting users into revealing private account or login information. To be safe, if you receive an e-mail from a business that includes a link to a web site, make certain to type the web site URL in the address bar manually. We will cover phishing in more detail in the next section.
Do not send sensitive documents (e.g., a Social Security number, a copy of your passport, credit card information, medical records) via e-mail without appropriate encryption.
Do not reply to spam e-mails. If you reply, the spammers will know that your e-mail is valid, and they will target you with more spam and maybe phishing attacks.
Do not use your personal e-mail account for your work because most business organizations have Internet usage policies that allow them to monitor all Internet traffic passing through the organization’s internal network. If you use your personal e-mail account for business work, they will have the right to access your e-mail and check its content. On the other hand, if you forward some sensitive business documents to your personal e-mail, your company could take legal action if it suspects you of corporate espionage or misuse of sensitive in-house information.
Social Engineering
Social engineering is a kind of attack that uses psychological tricks (social tricks) over the phone or uses a computing device to convince someone to handle sensitive information about himself or herself or an organization and its computer systems (see Figure 2-22).

Figure 2-22. Social engineering attack life cycle
Hackers exploit a human’s natural tendency to trust in order to acquire sensitive information in order to gain access to computing systems and information. There are many techniques already employed to conduct social engineering attacks; the most common type is phishing.
Phishing
The United States Computer Emergency Readiness Team (US-CERT) defines phishing as follows:
“…an attempt by an individual or group to solicit personal information from unsuspecting users by employing social engineering techniques. Phishing emails are crafted to appear as if they have been sent from a legitimate organization or known individual. These emails often attempt to entice users to click on a link that will take the user to a fraudulent website that appears legitimate. The user then may be asked to provide personal information, such as account usernames and passwords, that can further expose them to future compromises. Additionally, these fraudulent websites may contain malicious code.” 6
What Does a Phishing E-mail Message Look Like?
Certain characteristics distinguish phishing e-mails from legitimate ones. Here is a list of the main ones:
Many phishing e-mails use urgent or threatening language in the subject line (e.g., they threaten you about account closure if you do not act promptly). Such e-mails ask you to send your details, fill in online forms, or click a link to renew your subscription or to update your personal details. This could be for your e-mail service, bank account, or any of your social networking accounts.
They make job offers or talk about work-from-home opportunities with high salary and simple requirements.
They offer prizes, like a lottery. Some phishing e-mails say that your e-mail won the lottery and you must send your personal details, including bank account, to receive the funds or tax repayment.
They offer business deals with promises of great profits.
They are business e-mails with programs or executable code attached to them. Businesses usually do not send programs to execute on client machines.
Some immigration firms claim an ability to give you a U.S. visa or other country’s visa and request your personal details or ask for a tiny payment to submit the application for you.
Phishing e-mails usually contain grammatical errors and seem unprofessionally written.
Phishing e-mail addresses come from a different domain name than the company presents. For example, an e-mail sent from a free service (Google or Outlook) asking you to update your PayPal account details is a phishing scam.
They contain links that take you to web sites other than the company they are pretending to represent.
Whenever you suspect an e-mail to be a scam , do not reply to it. To check whether it is a phishing e-mail, rest your mouse (but don’t click) on the links contained in the e-mail to see whether the address matches the link that was typed in the message or the sender domain name.
Some attackers may use short URL services to mask the real phishing URL sent to the user. Services like Bitly ( https://bitly.com ) and TinyURL ( https://tinyurl.com ) allow users to shorten any URL. If you suspect that a short URL could be a scam, you can expand it using a free online service like the one at http://checkshorturl.com to see the destination.
You can also check whether the link is safe before clicking it by using free online services such as Norton Web Safe ( https://safeweb.norton.com ) and ScanURL ( http://scanurl.net ).
Phishing is not only limited to e-mails or a digital medium; many phishing attacks are done through phone calls. Phishers will say anything to cheat people out of money. They seem friendly and usually have some previous information about you. They call you by your first name and ask about your life and family to gain your trust. Many of them claim to work for companies you already deal with; others may first send you an e-mail asking you to call them later on their free phone line.
Phishing attacks can also target employees in giant companies. A good example is when an attacker tries to gain some sensitive information about a specific person. If the attacker knows the targeted person’s phone number, he or she can pretend to be that person and call the targeted user’s mobile phone operator technical support and ask for an account reset because he or she forgot the online password. If the trick is successful, the attacker can access the targeted user’s online account and gain sensitive information about him or her that can be used to impersonate him or her or to launch further attacks.
Here are some countermeasure steps against phishing attacks:
Do not give your credit card , bank details, or other sensitive personal information over phone calls or through e-mails. Some phishers may have part of your personal information and ask you to confirm it; beware of this trick and do not give any information or confirm your details.
Refuse to answer calls from telemarketing people. Some of them could be genuine; however, it is preferable to avoid them for security purposes.
Do not give information to charity organizations that you do not know. Some attackers may pretend to be working in a charity to steal your money or to gain more information about you.
Do not give information about the company you work for. This also includes revealing information about it online (e.g., on social networking sites ).
Pay attention to the URL of a web site. A phishing web site may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (.com becomes .org or .info).
Do not click hyperlinks or links attached in the suspected phishing e-mail, especially when you want to check your bank account. Always type the bank URL directly in the web browser address bar.
Check your bank account regularly to make sure it is safe and no illegal transactions have been made.
If you suspect that a phishing e-mail could be a legitimate one, try to contact the company behind the e-mail directly using its web site’s Contact Us page. Do not use the Contact Us e-mail or link supplied as part of the suspected e-mail because it could be false and part of the phishing attack.
Do not install programs or download files sent as attachments in e-mails from unknown senders.
Do not access your important accounts on public computers , and use a virtual keyboard where applicable.
Always discard pop-up screens and never enter information using them.
Make sure the web site you deal with to enter your personal information is protected by an SSL certificate (HTTPS).
Phishing is not limited to one avenue. Although most phishing attacks target bank accounts, there are many that target social networking sites and other companies such as eBay and PayPal.
Consider the anti-phishing working group at www.antiphishing.org for a list of previously recorded phishing attacks. ISIT Phishing ( http://isitphishing.org ) checks phishing URLs using heuristic technology coupled with machine learning.
Enhance the security of your computer by keeping your antivirus software up-to-date, update your Windows machine continuously, and do not ignore any warning raised by your web browser or e-mail service provider about any a suspected phishing e-mail/web site.
Organizations should invest in educating their employees about cyber-security attacks. If employees learn how to protect their data and the company’s confidential data, they’ll be able to recognize a social engineering attempt and mitigate its consequences.
Business organizations should have a data classification policy, where only the employees who really need to access sensitive data are given access to it.
If you suspect that you are a victim of a phishing attack, contact the Federal Trade Commission and raise a complaint at https://www.ftc.gov/complaint . You can report identity theft at the same page if you suspect that someone or a company is misusing your private data. You can also file a complaint on the FBI web site at https://www.ic3.gov/complaint/default.aspx .
Other Social Engineering Attack Types
Social engineering attacks are a preferred method to gain access to sensitive information in a relatively easy way compared with technical attacks such as brute-force or man-in-the-middle attacks. Phishing is the most common technique currently used to trick users into handing over their sensitive information; however, there are other techniques used to perform social engineering attacks. The following are the most popular:
Shoulder surfing : This is trying to gain sensitive information from users while they perform their regular tasks. For example, it means capturing user passwords by watching them type them on the keyboard.
Dumpster diving : This attack tries to gain sensitive information from materials thrown in the trash. Many organizations discard different types of papers without proper shredding (e.g., calendar of meetings, users list, system usage manuals). In fact, some organizations get rid of old computers without properly destroying them or securely wiping data on the hard disk. An attacker can gain important information by looking in the garbage or recovering data from old computers’ hard disks.
Role-playing : In this kind of attack, an attacker will impersonate technical support staff at some company and try to take sensitive information from users to gain illegal access to their accounts.
Keyloggers/Trojan horses: Here, an attacker tricks the user into installing malicious software on his or her machine (e.g., through an e-mail attachment or freeware downloaded from the Internet). The installed tool will record everything the user types on the keyboard and send it back to its operator.
OSINT: Open source intelligence (OSINT) is where attackers investigate publicly published information about a specific company or person to gain intelligence. Different tools exist to perform these attacks such as Maltego ( https://www.paterva.com/web7/ ) and Social-Engineer Toolkit (SET) ( https://github.com/trustedsec/social-engineer-toolkit ).
As you can see, there are different kinds of social engineering (SE) attacks, and all try to gain unauthorized access through exploiting the “human factor,” which remains the weakest element in computer security. Educating users about SE risks is still the best countermeasure technique against such attacks.
Secure Home Wi-Fi Settings
Most individual users connect to the Internet using a dedicated router (usually an ADSL router ). All home computing devices and appliances are connected using this single device. Most users prefer to use a wireless connection instead of cables. A wireless connection is easy to set up and does not require physical space. However, a wireless connection is promiscuous and should be considered less secure than its wired equivalent of communication and, if not correctly secured, may be intercepted and compromised more easily by outside hackers. In this section, we will give you simple guidelines to secure your home Wi-Fi network settings to become less vulnerable to outside attacks.
First, you need to access your router’s settings page. This usually done by typing a router control panel address in your browser and then entering the default username and password at the prompt. The default comes supplied with your router manual (e.g., D-Link uses http://192.168.1.1 to access its settings).
After you are at the router’s settings page, you must change your router administrator password. Most routers use the default login admin and the password password. Change the default password to something difficult to crack.
Change the Network SSID Name
Each router comes with a default name (SSD or wireless network name ), which is usually the name of the manufacturer (e.g., D-Link). Changing this name to something else (don’t use your personal information; use something ordinary and not related to you personally) will help you to prevent outsiders from knowing which router belongs to you.
You can also hide your Wi-Fi SSID completely. (Router settings allow you to hide your Wi-Fi network from prying outsiders. Note that once you do this, you’ll stop seeing the network pop up in your own devices’ Wi-Fi lists, and you’ll need to type the SSID into each device you want to connect to.)
Warning
Even after hiding your network name and not broadcasting your network presence, hackers can use some tools to capture your network even when it is in the hidden state. Tools such as InSSIDed ( www.metageek.com/support/downloads/#downloadInssider ), WirelessNetView ( www.nirsoft.net/utils/wireless_network_view.html ), and Homedale ( www.the-sz.com/products/homedale/ ) can capture hidden wireless networks.
Enable Wi-Fi Encryption
When you are at your router’s settings page, go to Wireless setup ➤ Wireless security and select a strong encryption standard to secure your Wi-Fi transmission. For instance, WPA2 is the most secure one (see Figure 2-25). Finally, enter a passphrase to protect your Wi-Fi connection (this passphrase is used by all devices that want to use your Wi-Fi connection; it is different from the first password used to secure your router’s settings area).

Figure 2-25. Enabling strong encryption standard for Wi-Fi connection using D-Link router
Filter MAC Addresses
All computing devices (laptops, tablets, desktops, and smartphones) have a MAC address . This is a unique address hard-coded on the network interface card of each device capable of interacting with the Internet. You can go into your router settings (usually the MAC filter area) and type in the MAC addresses of only those devices you want to allow on the network. This will effectively help you to restrict access to your local network.
Warning
Please bear in mind that hackers can spoof MAC addresses and gain full access to your Wi-Fi network. They can achieve this by sniffing your device MAC address using a free tool like Nmap ( https://nmap.org ) and then spoofing the MAC address on their attacking device using a free tool like Technitium MAC Address Changer ( https://technitium.com/tmac/ ).
Update Firmware
Make sure to update your router firmware continually. Manufacturers release updates to counter future vulnerabilities, and leaving your router without an update is a security hole.
Cover Your Laptop Webcam
This tip is from FBI director James Comey, who recently recommended that we all cover our webcams with tape for security reasons. Comey believes that doing so is a simple step for people to “take responsibility for their own safety and security.” 7
Do Not Post Your Selfie Pictures
Taking pictures of yourself ( selfie s) while raising your fingers (displaying the peace sign, for example) in the photo can pose a real security risk to your privacy. Nowadays, smartphone cameras are so accurate and can produce pictures with so much detail that these pictures can be magnified using special computer programs to extract user fingerprints.
Professional hackers can harvest the Internet for such pictures and then extract user fingerprint s to use in different criminal scenarios. Creating false passports or security access cards is one of them.
So, if you have pictures posted online where your finger appears clearly, delete them immediately to avoid identity theft.
Back Up Your Data
Backing up is a way to protect your sensitive data when a failure happens to your computing device. It is essential to have at least three copies of your data off-site and to protect these copies with a password so you can retrieve your important data in the case of system failure, virus attack, or natural disaster.
Most business organizations have backup plans already in place. They back up their data daily and in some instances after each transaction to assure a high level of security and trust.
Individual users can either back up their data to the cloud or use tapes and external hard disk drives for this purpose. We prefer to use external disk drives and tapes to back up our confidential data. This is the safest method because storing data in the cloud, especially sensitive information, may not always be a good choice for security-conscious people.
Note
Consider using an iStorage FIPS-140/2 password-protected device to secure all of your backup files and important data assets.
For individuals, it is essential to maintain a backup schedule of your important files. It is recommended that you have at least two copies stored on two different backup media (e.g., one stored on tape and another on an external hard drive). Backup media should be stored in a secure, safe location and must be protected with a strong password (review our password creation guidelines). There are many free backup software applications for Windows systems. The following are the most popular ones:
Comodo Backup ( https://www.comodo.com/home/backup-online-storage/comodo-backup.php ): This is a free backup solution that is easy to use by ordinary computer users; it walks you through a wizard and asks you exactly what you want to do. It can back up data to a local drive, optical media like a CD/DVD/BD disc, network folder, external drive, or FTP server; it can also be sent to a recipient over e-mail. The backup can be divided into pieces and protected with a password. Recovering data is easy and needs only a few clicks.
Cobian Backup ( www.cobiansoft.com/cobianbackup.htm ): This is a multithreaded program that can be used to schedule and back up your files and directories from their original locations to other directories/drives on the same computer or other computer in your network. FTP backup is also supported in both directions (download and upload). Cobian works silently in the background to check your backup schedule and perform the required tasks.
These backup programs do not have the ability to perform a backup on specific programs. For instance, e-mail clients such as Thunderbird and the Mozilla Firefox browser contain important information that must be backed up on a regular basis. MozBackup ( http://mozbackup.jasnapaka.com ) is a simple utility for creating backups of Mozilla Firefox, Mozilla Thunderbird, Mozilla Sunbird, Flock, SeaMonkey, Mozilla Suite, Spicebird, Songbird, and Netscape profiles. It allows you to back up and restore bookmarks, mail, contacts, history, extensions, passwords, cache data, and so on. It’s an easy way to do Firefox and Thunderbird backup.
Web Sites That Create a False Identity
Some web sites may ask you to provide personal information about yourself to register with or use their services. The Internet is a hostile place, and you cannot guarantee that a web site that requests this information is 100 percent secure or respecting the law and not handing such information to third-party affiliates. There are many web sites that generate alternate valid personal information that you can use to register with the web sites that you do not trust 100 percent.
A fake identity generator can generate everything you need to become a new digital citizen. This includes phone, web site, e-mail, username, password, account security questions, fake credit card and Social Security numbers, occupation, company, physical traits, and more. Here is a list of the most popular identity generation web sites:
Using a fake identity generator is against the law when providing personal details for legitimate web sites. It is strongly advised to limit this usage to web sites that you do not trust and noncritical services that ask for personal details without an acceptable reason.
Warning
Hackers misuse fake ID generation tools to gain unauthorized access to sensitive data. According to the BBC, Facebook user Aaron Thompson exposed an online thief who gained access to his account simply by sending the support team a fake passport to unlock the account. 8
The trick was successful, and the attacker gained unauthorized access to a legitimate Facebook account. This clearly shows you the danger of using a fake ID and false government paper in the digital world to hack into honest people’s accounts.
Best Practices When Using Social Networking Sites
Social media is a part of our daily lives. Often, when we talk about social media, we tend to think of Facebook, Twitter, and LinkedIn. People tend to post many details about their personal lives on social media sites. These services attract cyber-criminals who aim to perform malicious actions such as identity theft and footprinting users to direct customized attacks against them later.
Covering all the privacy settings of the main social media sites is a daunting task and requires a book on its own. However, there are general guidelines that can be followed to create a balance between using social media sites and keeping your information confidential.
Facebook is the biggest and most popular social media site, so we will cover its security settings in some detail. First, you need to access your Facebook settings by clicking the downward arrow in the top-right corner of the screen and then clicking Settings (see Figure 2-26). You must be logged in to your account to access this page.

Figure 2-26. Accessing the Facebook settings page
This will open General Account Settings page of your Facebook profile, where you can download a copy of your Facebook data. On the left side of the page, click Security to access the Facebook security panel.
Security Section
The Login Alerts setting allows you to get an alert (e-mail or SMS) when anyone logs into your account from an unrecognized device or browser.
The Two-Factor Authentication setting enables two-factor authentication (you need a security code generated automatically) when logging in to your Facebook account using a new browser. You have the following options to receive this security code:
You can receive an SMS message on your cell phone.
You can use a Universal 2nd Factor (U2F) security key to log in through USB or NFC.
You can use Code Generator in your Facebook mobile app to reset your password or to generate Login Approval security codes.
You can use recovery code (pregenerated security codes; you can keep them with you on paper) to access your account when you do not have your mobile phone with you.
The Where You’re Logged In setting allows you to see all the places where you are currently logged in. You can also terminate the session of any device currently logged into your account that you do not recognize.
The Deactivate Your Account setting will disable your profile and remove your name and photo from most things you’ve shared on Facebook. Some information may still be visible to others, such as your name in their friends list and messages you sent. You can reactivate the account at any time you want.
There are other settings, but they are all self-explanatory.
Privacy Section
The next section that you should access and configure properly is the Privacy settings (which resides below the Security section on the left side of the Settings page). This section shows you the basic privacy settings and helps you make sure that your profile and the content you share are viewable only by the audience you select (see Figure 2-27).

Figure 2-27. Accessing the Privacy section in the Facebook settings
The “Who can see my stuff?” group of settings lets you edit who can see your future posts. It is recommended that you set the default sharing option to Friends.
The “Who can look me up?” group of settings allows other people to look you up using your e-mail address and phone number. It also determines whether search engines from outside Facebook can link to your Facebook profile directly. This setting is important because it will determine how outsiders can find you online; select the best privacy setting commensurate to your needs.
The next important section is Timeline and Tagging Settings. It contains the following settings:
The “Who can add things to my Timeline?” group has two settings. The first one is “Who can post on your Timeline?” The recommended setting is “Only me.” The next one is “Review posts friends tag you in before they appear on your Timeline?” The recommended setting is Enabled.
“Who can see things on my Timeline?” has three settings. The first one is “Review what other people see on your Timeline.” This tool lets you see what your Timeline looks like to the public or a specific friend. The second setting is “Who can see posts you’ve been tagged in on your Timeline?” The recommended setting is Friends. The third one is “Who can see what others post on your Timeline?” The recommended setting is Friends.
“How can I manage tags people add and tagging suggestions?” has three settings. The first one is “Review tags people add to your own posts before the tags appear on Facebook?” The recommended setting is Enabled. This is an important privacy option because if someone adds a tag to one of your posts, his or her entire list of friends will see the post and not just the friends you’ve selected. Enabling this option will allow you to review the tag first. The recommended option for the next two settings is Friends.
The last groups of settings we are going to cover is the Mobile section; click it on the left side of the Settings page.
Enter a mobile phone and verify it. This setting is important to protect your account from theft attempts. If your browser is not recognized, you will receive a confirmation code via text message to log in to your Facebook account.
We covered the Facebook security settings in some detail because of Facebook’s widespread usage, but keep in mind that social media sites exist to simplify sharing and making connections between people online. It is essential to use such services wisely and avoid releasing your personal information or work details online. Make sure to activate Two-Factor Authentication and have some sort of second authentication (e.g., your mobile phone and password) for maximum security. It is also advisable to keep your browser, antivirus, and anti-malware programs up-to-date. Do not use the same password twice on Facebook and remember to log out when you’re done.
Remember what we said in Chapter 1: anything that goes online will remain there, even after deleting it. Be cautious before posting anything online, especially your personal pictures and private data.
Note
You can view your Facebook account activity log by going to https://www.facebook.com/me/allactivity .
Protect Your Children Online
Today, most kids these days are well versed in the tech-savvy art of computing. Most children own a smartphone or a tablet and use it to access the Internet. As we’ve already mentioned many times, the Internet is a dangerous place to let kids surf without proper advice and precautionary measures. For instance, it is crucial to educate your kids about Internet threats to help them enjoy the Web safely and keep your family protected in today’s digital age.
Internet Dangers for Kids
Here’s a list of possible Internet dangers for kids:
Pornography: Viewing porn pictures and movies by kids may affect their look on life and will change their sexual attitudes and beliefs. This can have a huge negative impact on your child’s social life and health .
Cyber-criminals/cyber-bullying: People may trick your children in giving sensitive information about their family to conduct different crimes later.
Gaming: Many online games involve playing with other unknown people online. In addition, these games can include sexual content, violence, and crude language. You can see the same dangers in public chat rooms.
Social media sites: Most kids have social media accounts (especially on Facebook), and posting personal pictures and revealing geolocation positions online can pose a great danger to kids and their entire family. Social media sites facilitate making friends online, but you cannot trust all people online in today’s digital age, and your kids may easily fall victim to cyber-criminals.
Health effects: Using a computer for long hours will affect a kid’s health. The risk of eye strain, wrist strain, and other injuries increases when using computers for long hours. It is crucial to limit the amount of time your kids spend on computing devices.
Internet addiction: This has become a modern heath problem. Spending long hours online will heavily affect your kid’s personal life (offline life).
This does not mean your child may encounter these threats when going online. However, knowing about the dangers can help you and your kids make smart decisions online.
Now, we’ll give some countermeasures to protect your kids online.
Teach Your Kid About Internet Dangers
It is important to have a discussion with your kids and teach them about Internet safety. Your kids certainly do not know what is waiting them when going online; it is your responsibility to educate them well on how to use the Internet following safety rules.
Here is a list of rules that your children should understand and agree to follow when using the Internet:
They will not post personal information about their parents or any family members online without clear consent from their parent. This includes home address, parents’ work address and contact information, geolocation information, and anything else that is considered private.
If they come across something inappropriate online, they should immediately inform their parents or guardian and close the page (e.g., seeing porn material).
They should not make friends online or chat with strangers without their parental consent.
They will not post pictures/videos about family to social media sites without parents’ consent.
They will not respond to e-mails or chat messages that pop up from unknown people; they always must inform an adult to check such issues.
They will not install games or freeware on their computing device.
They should understand that anything that goes online will remain there, even after deleting it.
They will not use the Internet extensively and must follow their parents’ advice on the amount of time they can spend online daily.
They should not share their passwords with others, even their close friends, and must store these passwords in a location that their parents can access (e.g., a password manager).
Written rules and discussions are effective means to communicate with your kids; however, some technical measures will also help you enforce these rules.
Parental Control Software
Parental control software helps parents to monitor and track their children’s online activity. You should block dangerous sites and protect kids from online bullying or even the potential of an approach from a pedophile. There is software already available for this purpose; many of them are free and have excellent features. The following are the most popular ones.
Microsoft Family Safety Account
For Windows 8 and 10, you can sign up for a family safety account. You can have multiple accounts (one for each child) and link them all to your family account ( https://account.microsoft.com/account/ManageMyAccount ). All you need to have is one Microsoft account (ID) and to sign in with it on your Windows PC. To activate this option in Windows 10, follow these steps:
Click the Windows 10 Start menu and select Settings (see Figure 2-28).

Figure 2-28. Accessing Settings in Windows 10
The Settings window appears; select Accounts.
Make sure you are signed into your Microsoft account (see Figure 2-29).

Figure 2-29. Making sure you are signed into your Microsoft account
In the left panel, click “Family & other people.” After that, click “Add a family member.”
A pop-up window appears. Select the option “Add a child” and enter the child’s e-mail. Click the Next button (see Figure 2-30).

Figure 2-30. Adding a child account to your existing Microsoft account to activate parental controls on Windows 10
The next window asks you to confirm your choice; click the Confirm button.
The final window informs you that an invitation has been sent to your child’s e-mail. To activate parental control on the child’s account, your child needs to accept the invitation (see Figure 2-31) and then access his or her Windows account using this registered e-mail (Microsoft e-mail, Outlook, Live, or Hotmail).

Figure 2-31. Invitation sent to child account to activate parental control
Now, after your child has been successfully added to your family, you can access the Family Safety web site at https://familysafety.microsoft.com and log in with your Microsoft account credentials to view reports and edit the family safety settings for each child. You can also review the privacy settings for each child, add another child, and add another parent (e.g., your spouse) to monitor your child’s activities.
Configuring a Windows safety account offers great features for parents to monitor their kids’ online activity.
Parents can add a small amount of money to a kid’s Microsoft account to facilitate online shopping with small limits. No credit card is needed when your child wants to make online purchases, and Microsoft will set age limits on their purchases.
If your kids are using a Windows mobile phone, parents can track them online and see where they are.
Microsoft will generate online activity reports about all your kids’ online activity. It can also block their access to specific apps, games, and web sites.
It will also limit how much time your children can stay online.
It is highly advisable to use the Microsoft family safety account for your children; it is supported in modern Windows versions and offers a comprehensive solution to protect your children online.
If you do not like the Microsoft approach to protect your children’s safety online, you can use third-party software for this purpose. There are many parental applications available, and some have great features for free. You can always search for parental software and compare their features. We will mention one free popular solution in the next section.
K9 Web Protection
This is a free Internet filter and parental control application for your home Windows or Mac computer. Its main features include blocking web sites, forcing safe searches on all major search engines, setting a time restriction on computer usage, and protecting against adult and malicious web sites. You need to register to get the free license to use this software. You can find K9 Web Protection at www1.k9webprotection.com .
Bear in mind that parental controls cannot block everything bad online, but they can help you to better monitor your children’s activities online and assure that your discussion with them about Internet dangers is properly understood and followed.
Set Up a Family-Safe DNS
Another technical method to prevent viewing porn and malicious web sites is to use a safe DNS service. DNS works transparently in the background to convert human-readable web site names into computer-readable numerical IP addresses. By setting a safe DNS on your Windows PC, you can assure, to a large extent, that bad web sites will not open when your kids use the Internet.
There are many family-safe DNS providers; we will demonstrate how to use a popular free service called OpenDNS Family Shield, which comes preconfigured to block adult content without user intervention. Later we will show you how to use a simple program that can change between different safe DNS providers.
To configure your Windows to use OpenDNS Family Shield, follow these steps:
Go to Control Panel ➤ Network and Sharing Center and click “Change adapter settings” on the left side. Right-click the network connection you’re using and select Properties.
Highlight Internet Protocol Version 4 (TCP/IPv4) and click Properties.
Select “Use the following DNS server addresses” and type the OpenDNS addresses 208.67.222.222 and 208.67.220.220 in the “Preferred DNS server” and “Alternate DNS server” fields (see Figure 2-32).

Figure 2-32. Using a custom DNS server for your current connection
Click OK, then Close, and then Close again. Finally, close the Network Connections window.
There are other family-safe DNS providers that offer similar services in blocking adult content and fraudulent web sites. Examples include Yandex.DNS ( https://dns.yandex.com ) and Norton ConnectSafe ( https://dns.norton.com ). Configuring Windows to use the DNS of these services is like what you already did previously. However, there is a tool that can simplify this process and change between different DNS services automatically.
DNS Angel (see Figure 2-34) is a portable freeware application for changing the DNS setting automatically in Windows. You can download it from www.sordum.org/8127/dns-angel-v1-4/ .

Figure 2-34. DNS Angel used to change between different DNS services automatically on Windows
Warning
You can configure your router to use a safe DNS. This will effectively allow you to use the same settings on all connected devices on your local network. However, local DNS settings in Windows will override the one inserted in your router, so if your tech-savvy kid changes the DNS setting on the local machine, this will override the one used on your router. To prevent your children from changing the DNS setting on Windows, create a limited user account for them without administrator access.
Track Yourself Online
It is important to track yourself online on a regular basis. This helps you to find where you are showing up online and what others are saying about you. This section covers the free online services that can help you with this.
Google Alerts
Google Alerts is a notification service offered by Google; it works by sending an e-mail to the user when it finds new results such as web pages, newspaper articles, blogs, or scientific research that matches the user’s entered search terms . You must be logged into your Google account to create a new alert.
You can set up a new alert at https://www.google.com/alerts . In the box at the top, enter a topic you want to follow. You can create as many alerts as you like and adjust the settings to be notified on a daily, weekly, or “as it happens” basis (see Figure 2-35).

Figure 2-35. Setting up Google Alerts to get notified when your search terms are mentioned online
The free people search engine at https://pipl.com is another web site to search about yourself and other people online. It allows you to search by name, address, or e-mail and has the most comprehensive database of people profiles online.
Auditing Facebook Profile
Many users have been using Facebook for a long time. Some people have thousands of likes and posts on their Timelines. Humans have a tendency to forget their previous online actions, though. For instance, any person who previously posted his or her political opinion or comment (aggressively) may find that it will be more suitable to hide previous online actions for many reasons. Performing a check on every post and action conducted on Facebook is a daunting task, especially if the user has been active on Facebook for a long time.
Stalkscan ( http://stalkscan.com/en/ ) is a free online service that allows anyone to look up any Facebook user’s public information. It is a great auditing tool for Facebook profiles and allows any person to see previously posted images, comments, events attended in the past in addition to future events planning to attend, places where they “checked in,” and everything they “like” online (posts, video, pictures, etc.).
This tool shows you just how easy it is to find any public information on Facebook, so be careful before posting anything publicly online.
Check Whether Someone Has Taken Your Personal Picture
Sometimes you may encounter a case where someone took your personal pictures (or your child’s pictures) from your Facebook profile and used them on a profile or blog without your consent or even used them for the wrong reasons. Reverse Image Search helps you to find any photo you have uploaded to the Internet along with a list of all other web sites where this photo appears.
TinEye ( https://www.tineye.com ) is a reverse search engine with more than 17.4 billion images indexed (at the time of writing). You can upload the image you want to search for online or simply enter its URL, and TinEye will find all the locations and web sites where this image is located.
Google has a similar service to search for images online. To use it, follow these steps:
Go to https://images.google.com .
In the search bar, click the camera icon (see Figure 2-36).

Figure 2-36. Using a Google image search to find all instances of a selected picture online
You can either upload a picture from your computer or enter its URL to search for it.
Google will return every instance of that image it can find.
Another free service to conduct an image search is https://www.imageraider.com . This web site allows you to search popular search engines like Google, Bing, and Yandex to find all web sites using your photos.
A good practice when publishing personal photos online is to watermark them. This allows you to prove ownership of your photos. There are many tools and online services that offer watermarking for free. https://www.watermarquee.com offers free online watermarking, as does Picasa (retired but available) at http://filehippo.com/download_picasa .
Check Your Data Breach Status
Almost every week the press announces a data breach that hit a major web site. To tighten your security, it is essential to check whether your account was among the ones that got breached. Fortunately, there are many free services to check whether your account was compromised.
https://haveibeenpwned.com is a free resource for anyone to quickly assess whether they may have been put at risk because of an online account being compromised or “pwned” in a data breach. It is run by security researcher Troy Hunt, who tracks data breaches. To use this web site, enter the e-mail address or username in the search box to check whether you have an account that has been compromised in a data breach.
You can also sign up for alerts tied to your e-mail address so you can be notified as soon as another breach is detected by clicking “Notify me” at the top of the page.
https://breachalarm.com offers a similar service; it allows you to check anonymously if your password has been posted online and sign up for e-mail notifications about future password hacks that affect you.
It is highly advisable whenever you hear about a data breach in the press and you have accounts at a company that has been breached that you change your affected account’s password. Checking the previously mentioned sites to see whether your account was stolen is a good thing, but it is important to act promptly and change your affected account’s password. Remember, do not use the same password on two different accounts.
Delete All Your Online Profiles
If you decide to delete your online presence from the Internet and return to the “offline age,” there is a free service that can help you achieve this. Deseat.me is a service that lets you see all the web sites you’re signed up for and asks if you’d like to delete them or unsubscribe . It asks for your e-mail address and password so it can scan for the sites you’re signed up to. The sign-in must done using a Google account (using Google’s OAuth protocol); this makes this service limited because it requires users to have a Google e-mail address that is used for all their online accounts. This will result in discarding online accounts where the user registered using a non-Google e-mail account like Microsoft or AOL account.
Another value-add security service that can help you to find all major web sites that you may have accounts at is http://backgroundchecks.org/justdeleteme/ . It is not like Deseat.me in terms of searching for online accounts automatically. This service is a directory of direct links to delete your account from web services. It offers a direct link and some information on how to disable your account for each listed online service.
Remove the Offending Content
Sometimes your personal information is made available to the public without your consent, or it may happen that someone writes something inappropriate or false about you that may affect your reputation and you want to remove it. Removing the offending content or even personal data is not an easy task online. The nature of the Internet allows the information to be replicated quickly. (For example, posting a photo to your Facebook Timeline will make it appear on all your friends’ feeds, and if some of your friends share it using the public state, it can replicate and appears in the timeline of millions of people.)
Removing yourself completely from the Internet is extremely difficult, and no one can guarantee 100 percent successful removal. However, you can minimize your online footprint in many ways and remove offending content.
We already covered how to delete yourself from major social media sites, but remember, you may have been using some less famous sites in the past and forgotten about it. The same thing applies to shopping web sites (e.g., Amazon and eBay). Your information is still available and must be deleted to minimize your online footprint.
To delete old accounts, you need to handle each one separately. Each one should have an option in the settings area to cancel, remove, and deactivate your current account. If you have problems deleting it, you can search the Internet for information on how to remove it using how to remove my X account (replace the X with your account provider name). For example, use how to remove my Reddit account and Google will return detailed instructions accordingly.
If you cannot delete your account or the account providers don’t supply such an option, change your real information to something fake or random.
Data collection sites are another threat to your online privacy. These web sites gather your information from primary sources, such as public records from government entities, social media sites , Whois records of registered domain names, and any source that is publicly available. They sell this information to interested third parties and to advertisement companies. There are plenty of data collection web sites (Intelius, LexisNexis, PeopleFinders, Spoke, WhitePages, BeenVerified, DOBSearch, Pipl, Radaris, Mylife, Wink, LookUp, PeekYou, and Waatp, to name a few!), and removing yourself from them is a daunting task. This is why we always emphasize thinking twice before posting personal information about yourself online. For instance, we will give an example of how to remove yourself from one of these web sites. Unfortunately, not all data collection sites have similar removal procedures. You need to check each one’s privacy policy agreement to see how you can remove yourself from it.
To remove your record from the Intelius database, go to https://www.intelius.com/optout.php . Fill in the form and submit your details (you need to provide an acceptable ID to validate your ownership of the data you want to remove).
There are some companies that will offer to delete your personal information from the Internet for a price. We will not endorse anyone for this task; you can always search online about such companies and compare their features and prices.
If someone has written something bad or offensive about you and you want to remove it, you need to follow different procedures than what you have already learned about. For instance, if you encounter a blog post about you and it contains inaccurate information that may damage your personal or business reputation, you can ask the web site that publishes it to remove it. Here is a list of methods you can use to remove false, unlawful, and damaging information from the Internet:
Most web sites that allow its users to post their opinions or to make online reviews about products and services have set guidelines (often called community and review guidelines) that must be followed by all users when posting content. If someone violates their policies, you can “flag” or “report” the content to the site moderator, who will act to see whether this content is violating the site’s terms of use. For example, Amazon allows its users to report abuse about any item review if you find it inappropriate (see Figure 2-37).

Figure 2-37. Users can report abuse about any customer review posted on Amazon.com if inappropriate
If you have images or other copyright content that has been copied and used elsewhere without your consent, you can ask the web sites that host this content to remove it. If they do not respond, you can file a complaint according to the Digital Millennium Copyright Act, which preserves your rights when it comes to content that belongs to you.
You can make direct contact with the web site owner asking to remove the damaging content. Of course, you should have a legal reason for this. It is advisable to contact the people in charge, not the person who wrote the damaging post. You can find out who is responsible for a web site by going to its About Us and Contact Us page. If you do not find the proper contact you are searching for, you can send your e-mail to the site webmaster (check to get the webmaster contact information at www.whois.com/whois/ ).
If the content contains your sensitive information , you have the right to get it removed. Google allows users to remove their personal content from its search results. To see the Google removal policy, check this page: https://support.google.com/websearch/answer/2744324 . To remove information from Google, go to https://support.google.com/legal/troubleshooter/1114905 . You can check what Google accepts you to remove (see Figure 2-39). To remove nude pictures of yourself from Google search results, visit https://support.google.com/websearch/troubleshooter/3111061#ts=2889054%2C2889099%2C2889064%2C3143868%2C6256340%2C6256363 .

Figure 2-39. Information that can be removed by Google
If you have personal old information published online and you successfully manage to remove it but it still appears in Google search results (because Google cached it), you can ask Google to remove this old content by filling out the form at https://www.google.com/webmasters/tools/removals?pli=1 .
The final method to lower the impact of offending content about you is to push such content from Google’s first-page results. You can achieve this by posting content online and optimizing it with proper search engine optimization techniques to make it appear in the first Google result page.
Note
Remember, you cannot fight over someone’s opinion because you simply do not like what he or she said about you. The freedom of speech is protected in democratic countries, and you cannot do anything about this.
Cloud Storage Security
More and more companies are adopting cloud storage solutions to reduce the costs of storing and processing data locally. Cloud storage solutions help employees access data anytime and from anywhere using any device type with low IT overhead. As more enterprises shift their data to the cloud, companies should take considerable steps to improve their cloud storage security and keep their sensitive data secure.
With the wide adoption of cloud storage solutions and the reduction of its costs, individuals also are more willing to save their sensitive data in the cloud. To secure cloud storage accounts, the following security measures should be implemented:
Use strong passwords to secure your cloud accounts. These passwords should be stored in a safe location (e.g., using password manager software). At the beginning of this chapter, we thoroughly covered how to create and store passwords.
Enable two-factor authentication to access your cloud account. For example, use a password and your phone to receive a security code.
Use antivirus/anti-exploit software and keep them up-to-date along with your Windows OS.
Cloud storage providers allow you to share specific files with your friends/colleagues. When you provide access permission, take care to revoke this access when sharing is no longer needed. It is advisable to give other people read-only access permission.
Storing your data in the cloud does not mean it is 100 percent secure. It is highly advisable to keep a backup copy of all data in a safe location off-site.
Do not upload anything to the cloud without encrypting it first locally! Some cloud storage providers offer the encryption feature to encrypt/decrypt your data while in the cloud before granting you access. This is not suitable for paranoid security people, as cryptographic keys will be stored by the cloud provider and can be compromised or taken by other third parties (e.g., intelligence agencies), which will put your data at risk. In Chapter 5 we will teach you everything you need to know to secure your data through encryption techniques.
Even after encrypting your data, it is not preferable to use cloud storage to store sensitive data.
Encrypt the connection between your machine and the cloud storage provider, and do not use a public Wi-Fi connection to upload your data to the cloud without proper encryption (e.g., using a VPN connection; more on that in Chapter 4).
Do not upload business documents to free cloud storage or free file-sharing services. Some employees may make this mistake and upload sensitive business data to cloud providers that don’t meet minimum security standards. This will effectively put company data at risk.
Always read the privacy policy and terms of service agreement of the cloud provider to make sure that no terms are violating your privacy when using the service.
When it comes to security, remember that technology depends on human factors to make it work well. Be careful to not reveal sensitive data about your accounts (e.g., via social engineering attacks) and do not give applications installed on your mobile phone access to your confidential data.
Note
MyPermissions ( https://mypermissions.org ) is an app that allows you to know how many apps have access to your personal information on your smartphone.
On August 31, 2014, a hacker’s invasion of dozens of celebrities’ iCloud accounts led to the embarrassing leak of nude photos of about 100 celebrity women and one man. The hacker took advantage of a security flaw in Apple’s online backup service, iCloud. Many online services lock someone out after several unsuccessful attempts to log in, but Apple’s Find My iPhone app and iCloud did not. That has been changed by Apple in the aftermath of the nude celebrity photo scandal.
The attack was successful because most celebrities were using weak passwords and using the same password to secure their iCloud account and Find My iPhone app. The hacker first found the Find My iPhone app password and then used the same password to access the iCloud account. 9
Internet of Things Security
Network-connected devices such as mechanical equipment, computing devices, and other services that can access and share data across the Internet constitute the Internet of Things (IoT). Nowadays, everything is connected to the Internet, from refrigerators to air-conditioning systems to coffee makers While these IoT devices can make our lives easier, they also create new security risks if compromised by malicious hackers.
Poorly secured IoT devices such as web cameras, baby monitors, and other home appliances can pose a great risk to individuals and the nation. As we already mentioned in Chapter 1, on October 21, 2016, a series of distributed denial-of-service (DDoS) attacks caused a widespread disruption of legitimate Internet activity in the United States. This huge attack was caused by exploiting vulnerabilities in a large number of IoT devices across the globe.
While the benefits of IoT are undeniable, the reality is that security is not keeping up with the pace of innovation. To enjoy the benefit of IoT devices, a set of security measures must be implemented by individuals and companies to avoid turning the IoT innovation into a catastrophe.
Do not connect your device to the Internet unless there is a need for this. For example, if connecting your refrigerator to the Internet does not bring additional benefits to you, disconnect it. It is also advisable to turn such devices off when you are not going to use them frequently (e.g., turning off router when you are on a vacation).
Isolate IoT devices in a separate network. Create a new virtual network and let your IoT devices use it. This will effectively help you to isolate your computing devices (which contains your personal data) from other home appliance devices.
Use a strong, complex password for each IoT device. Do not use the same password on two devices.
Change the device’s default username and password. IoT devices come with default usernames and passwords known by hackers; you must change these before connecting your device to the Internet.
Many IoT devices rely on cloud storage providers to store their data in the cloud. Make sure to read the device manual carefully and know what kind of data is going to the cloud. Enable encryption of the data before the device uploads it to the cloud. If you suspect that your data is not secure, do not use this device type and trade it for something else more secure.
Businesses should prevent their employees from bringing their IoT devices to work. Wearable IoT devices such as smart watches, head-mounted displays, and others can impose a security risk on sensitive company data.
Read the manual of the IoT device before connecting it to the Internet. Most devices allow you to enable encryption, which can add an additional layer of security to your device.
Keep your IoT device up-to-date by visiting the device settings; you can also register your device on the manufacturer’s web site to get regular updates. The device manufacturer may discover a security flaw and launch a patch to close the security hole. Make sure to close it before hackers exploit it.
Disable Universal Plug and Play (UPnP) . UPnP allows devices on your home network to discover each other; this allows outside hackers to take control of your local network if they successfully manage to compromise one device. UPnP can be easily disabled in your router settings.
If your IoT device supports Telnet and SSH services, make sure to disable them. This will prevent hackers and malware from gaining access to your device through such services.
Secure your Wi-Fi network as we already mentioned previously because most IoT devices will connect through a wireless connection.
Purchase IoT devices from companies with a reputation for providing secure devices.
IoT adoption will increase in both speed and scope and will impact virtually all sectors of our society. It is crucial to study the features of IoT devices before buying them, especially the security features (in terms of the amount of sensitive data collected and the costs of remedying the security vulnerabilities). You should also make sure to configure the IoT device properly, as we already mentioned, to strengthen it against outside attacks.
Physical Security Threats and Countermeasures
No matter how much effort you spend to secure your digital devices by following all the precautionary steps already mentioned, you could still find everything vanished before your eyes if your computing device or hardware gets stolen or unauthorized physical access to it took place while it was unattended. Physical threats are not only from theft; other threats include natural disasters, breakage, power surges, poured coffee over the computer, and anything else that can damage your computing equipment and prevent you from accessing the information stored on it.
Performing an IT security risk assessment should be an important part of any company’s IT security precautions. It helps businesses to understand and quantify the risks to IT and the possible consequences each could have.
To counter such threats, business should create a plan to act promptly when something goes wrong. To begin, a company’s IT staff members should first list all its IT equipment, then they should assess the risk to each individual item, and finally they should access each item’s importance in terms of how much damage it will bring to the company if a failure takes place.
IT equipment includes the following and more:
Computers (desktops)
Portable devices (laptops, netbooks, tablets, personal digital assistants, USB [flash] drives, compact discs, smartphones)
Servers
Backup storage devices (tapes, external HDD)
Printers and multifunctional devices (MFDs)
Photocopier and photo printer
Projectors
Digital camera
Digital duplicator
Telephone handset
Internet-connecting devices such as routers, switches, hubs, wireless access points
Now you should assess how the following risks would affect each item already mentioned; this will also help you to assess each item’s importance on the overall business functions and continuity.
Theft and loss of hardware devices
Damaged equipment because of excessive heat, high humidity, water, or any liquids
Damaged equipment (computers may fall on the ground and become damaged)
Natural disaster (fire, flood, earthquake, tornados)
Software failure
Intentional destruction of data (e.g., vandalism and arson)
Malware attacks (e.g., ransomware that encrypts disk drives and prevents access to stored data)
Your next step is to risk-assess the potential of these occurrences and the impact for each incident and overall business continuity. This will help you create a complete scenario on what is tolerable and what is not.
Individuals also suffer from physical threats. Theft and hardware defects can prevent them from accessing data stored on computing devices. For example, laptops that are left unattended without being secured by a cable lock can be quickly stolen. In today’s digital age, most individuals carry at least one portable computing device with them. To secure mobile devices, use these tips:
When using your laptop in public places, secure it by using a cable lock attached to a heavy object (e.g., desk, table, lighten column in gardens).
Do not leave your office without locking it when you have portable devices left inside it.
Do not store your company’s sensitive files on your computing device without proper permission, and make sure to encrypt everything if you can store such data on your device.
Do not store your sensitive/personal data on mobile devices without proper encryption. For instance, if you take personal pictures with your mobile phone, make sure to shift this data to your computer at home on a regular basis.
Use a password to protect your mobile device from unauthorized access.
Do not leave your device unattended in public places.
Do not turn your Bluetooth connection on in public places, and if necessary, run it for a short period of time to receive or send urgent files.
Turn off Wi-Fi when you are not using it. Be careful when using public hotspots and encrypt your connection using VPN.
Keep a written record of the make, model, serial number , MAC address, and other pertinent information about your portable device in case it gets stolen.
Disposing of Old Computers
There is a large amount of computer equipment that is simply thrown away because people don’t have the time to get it ready to donate or the equipment is no longer desirable to any consumers. You should make sure that your computing device’s hard disk is wiped securely and does not contain any sensitive data that can be recovered later using forensic analysis techniques.
Most ordinary computer users do not know that deleting files from a hard disk, emptying the Recycle Bin, and even formatting the hard disk drive will not erase the data completely. There are many recovery tools that can be employed to recover this data. For instance, use these tips before selling or throwing away your old computing device:
Ensure you destroy data stored on a disk completely using specialized software (also known as disk wiping). Data on the disk includes your main visible data and remnants of data left after deleting old files. Both should be cleaned completely.
For Windows machines, you can turn on BitLocker encryption of all disk partitions, set a complex password, and then format the disk. This will make recovering data near impossible. We will show you how to use encryption techniques in Chapter 5.
Use physical destruction techniques to destroy the hard disk drive/solid-state drive when you want to achieve the maximum security possible.
The security risks of recovering sensitive data from disk drives are applicable to more than just computers because there is a lot of IT office equipment that stores and processes data; recovering such data can impose great security risk on companies if it falls into the wrong hands. An example is an office copier or multifunction printer; whenever documents are copied or sent to the printer, they are backed up to a hard drive inside the copier. This isn’t a problem, but if the printer suffers from a technical problem and needs to be sent for maintenance (or simply resold or sent for parts) and if the data stored (or remnants of it) in the printer’s hard drive is not erased securely, this will effectively expose your sensitive documents that were previously printed to danger.
Mobile phones also store a considerable amount of sensitive information about their users. When getting rid of your old device, it’s important to take steps to help ensure that no sensitive data is left for recovery.
All smartphones have a setting that allows you to return the device to its factory reset. This will wipe all data stored on your device. To know how to do this for your device, search for the topic on the device manufacturer’s web site or consult the device manual.
Warning
Do not trust the reset function. This does not assure the removal of all the stored and potentially sensitive data objects.
The second thing you need to erase in your smartphone is the SD card; you can remove the SD card from the phone, attach it to your computer, and erase it securely using one of the tools already mentioned to erase data on a computer’s hard drive.
Note
Data destruction techniques in Windows will be covered in the next chapter.
Educate Yourself About Cybersecurity
As technology becomes more intertwined with our daily lives, it provides convenience but also increases our exposure to threats and risks. No one can predict to what heights such risks can reach. There are many security threats online that are still impossible to detect by security software. You, the user, are still the first and last line of defense against cyber-criminals trying to access your private data.
The importance of educating yourself about cybersecurity cannot be stressed enough; the more you know and understand about this domain, the better your chances of staying protected are. Your cyber-knowledge is essential to your safety and privacy on the Internet. The following resources will help you to stay up-to-date with the latest online threats and will broaden your knowledge about the subject. Of course, you can always search online for anything you came across and do not fully understand.
Read specialized books about cyber-security and digital privacy. It is preferable to read books that offer practical guidelines with adequate theoretical information. A great example is the book you are reading right now!
Watch cybersecurity online courses ; there are many for free, and they offer excellent content suitable for ordinary Internet users. Check out the author’s portal for a list of such courses: www.darknessgate.com/category/technical-training .
Check out Internet resources. Many web sites offer detailed information and best practices on how to protect yourself online. The following list includes some of them:
Stay up-to-date on the latest recent online threats (this may not be practical for nonexperienced users). The following web sites offer such services:
Use Free and Open Source Software
As software prices become higher, some people may tend to install illegal programs (patched and cracked programs) on their computers to reduce costs. We already discussed the danger of installing illegal software, as the majority contains malware and other software that can track user activities online and even send keystrokes to malware operators.
This book will cover the Windows OS only when talking about operating system tools and functions. It is not practical to advise you to use an open source OS like Linux to save the cost of Windows! However, what most users care about when buying new software are the programs (productivity programs) that they are going to use to get their job done. There is plenty of free and open source software (FOSS) that can replace paid software. Microsoft Office and other drawing programs from third-party companies can be easily replaced with something free and open source instead of installing illegal software with security risks. Table 2-2 lists the main free alternatives to Windows commercial programs needed by most users.
Table 2-2. Free Alternative Software for Windows
Program Name | URL | Task |
|---|---|---|
FreeOffice | Alternative to Microsoft Office | |
LibreOffice | Alternative to Microsoft Office | |
PeaZip | File archiver utility | |
PortableApps | +300 apps covering all areas | |
GnuCash | Personal and small-business financial accounting software | |
Thunderbird | Free e-mail application | |
GIMP | GNU image-editing program | |
Pidgin | Instant messaging |
Summary
This was a long chapter full of advice on how to deal with today’s online threats. We began by talking about the importance of installing security software on user computers. There are many products out there that perform great functions; however, they are not all equal in protection. We gave you some selection criteria to help you select the best solution according to your current needs.
Selecting a strong and complex password is vital to protecting your digital accounts. Unfortunately, many people still underestimate its importance. We focused on this and gave guidelines and tips.
The first thing most computer users do after logging into their machines is to open the web browser to access the Internet. Your web browser knows a lot about you, and we gave fast tips to secure your browsing sessions. In later chapters we will cover more techniques for safe browsing.
We also talked about e-mail security and social engineering attacks. Such attacks have become more sophisticated, and many people and companies’ employees have fallen victim to them.
Children’s online security is vital to parents, so we covered practical tips and suggested tools to monitor and protect children from cyber-threats.
Cloud storage, Internet of Things devices (IoT), and physical threats create risks for your sensitive data and online activities; we mentioned threats and suggested countermeasures to mitigate such threats.
We ended this chapter by stressing the importance of educating yourself to become more computer security literate. Being properly educated can only help in making an informed decision when figuring out how to properly protect your digital assets.
Cybersecurity is no longer buried far away in the tech section of newspapers and web sites. It has become first-page headline news and will remain so for the foreseeable future. Computer security is concerned with protecting computing systems and the data that stores and processes it. Without proper knowledge of the main areas of computer security, businesses cannot do their jobs, and individuals cannot benefit from the technology revolution to enjoy their modern lives.
Protection is never 100 percent, but knowledge is everything. In the coming chapters, we will delve more into the technical side of digital privacy to teach you how you can use a plethora of tools and techniques to protect your personal information and prevent identity theft against the ever-evolving cyber-threats.
Bibliography
National Resource Centre for Free and Open Source Software (NRCFOSS), “Benefits of using FOSS.” http://nrcfoss.org.in/resources/benefits-of-using-foss .
State of California Department of Justice, “Online Privacy.” https://oag.ca.gov/privacy/online-privacy .
Dmitri Vitaliev, “Digital Security & Privacy for Human Rights Defenders.” Frontlinedefenders.org, February 23, 2016. https://www.frontlinedefenders.org/en/resource-publication/digital-security-privacy-human-rights-defenders .
Notes
David Fitzpatrick and Drew Griffin, “Cyber-Extortion Losses Skyrocket, Says FBI.” CNN.com, April 15, 2016. http://money.cnn.com/2016/04/15/technology/ransomware-cyber-security/ ).
Luis Ayala, Cybersecurity Lexicon. New York: Apress, 2016. p. 139.
Betanews, “Want to launch your own DDoS attacks on a website? $200 will get you everything you need.” Betanews, July 23, 2014. http://betanews.com/2014/07/23/want-to-launch-your-own-ddos-attacks-on-a-website-200-will-get-you-everything-you-need/ .
Camera & Imaging Products Association, “CIPA DC- 008-Translation- 2016.” July 2016. www.cipa.jp/std/documents/e/DC-008-Translation-2016-E.pdf .
The Sudbury Neutrino Observatory Institute (SNOI), “IPTC Tags.” April 7, 2015. www.sno.phy.queensu.ca/~phil/exiftool/TagNames/IPTC.html .
US-CERT, “Report Phishing Sites.” https://www.us-cert.gov/report-phishing .
Violet Blue, “The FBI recommends you cover your laptop’s webcam, for good reason.” Engadget. https://www.engadget.com/2016/09/23/the-fbi-recommends-you-cover-your-laptops-webcam-good-reasons/ .
BBC, “Facebook ‘hack’ victim exposes passport scam.” BBC, June 29, 2016. www.bbc.com/news/technology-36661557 .
Alan Duke, "5 Things to know about the celebrity nude photo hacking scandal.” CNN, October 12, 2014. http://edition.cnn.com/2014/09/02/showbiz/hacked-nude-photos-five-things/ .






