Forensics Analysis of Android Mobile VoIP Apps
T. Dargahi*; A. Dehghantanha†; M. Conti‡ * Islamic Azad University, Tehran, Iran
† University of Salford, Salford, United Kingdom
‡ University of Padua, Padua, Italy
Abstract
Voice over Internet Protocol (VoIP) applications (apps) provide convenient and low-cost means for users to communicate and share information with each other in real-time. Day by day, the popularity of such apps is increasing, and people produce and share a huge amount of data, including their personal and sensitive information. This might lead to several privacy issues, such as revealing user contacts, private messages, or personal photos. Therefore, having an up-to-date forensic understanding of these apps is necessary.
This chapter presents analysis of forensically valuable remnants of three popular Mobile VoIP (mVoIP) apps on Google Play store, namely: Viber, Skype, and WhatsApp Messenger, in order to figure out to what extent these apps reveal forensically valuable information about the users activities. We performed a thorough investigative study of these three mVoIP apps on smartphone devices. Our experimental results show that several artifacts, such as messages, contact details, phone numbers, images, and video files, are recoverable from the smartphone device that is equipped with these mVoIP apps.
Keywords
Android forensics; mVoIP; Viber; Skype; WhatsApp Messenger; Digital forensics
1 Introduction
In recent years, we have witnessed a rapid increase in the use of Voice over Internet Protocol (VoIP) services as an online communication method on mobile devices. This is not surprising due to the increasing proliferation of smartphones: it has been predicted that by 2019 the number of smartphone users will be more than 2.6 billion [1]. These days people use their smartphone devices not only for making voice calls and exchanging SMS, but also for obtaining several services that are offered due to the ubiquitous access to Internet, such as mobile banking, and location-based services. Meantime, the use of VoIP applications, which could be delivered easily through mobile VoIP applications (mVoIP apps), would enable people to interact, share information, and become socialized at a very low cost compared to most of the traditional communication techniques. However, such applications could also be exploited by criminals or be targeted by cybercriminals (e.g., with malware infection to steal financial data) [2, 3]. For these reasons, mobile devices (including smartphones) attracted a lot of attention from the security research community [4], in particular from the perspective of malware [5–12], security enforcement [13–16], and authentication mechanisms [17–19].
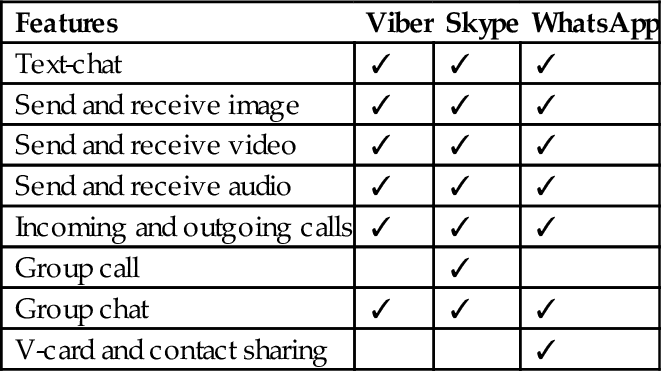
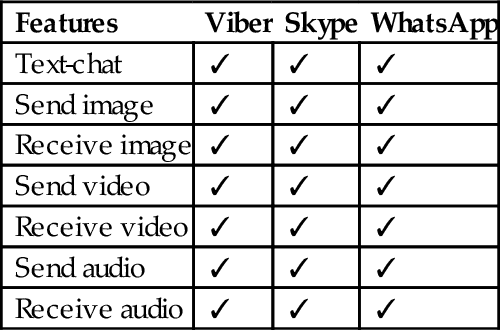
Smartphones are a common source of evidence in both criminal investigations and civil litigations [20–25]. However, the constant evolution and nature (e.g., closed source operating system and diverse range of proprietary hardware) of mobile devices and mobile apps complicates forensic investigations [26]. Among the existing smartphone operating systems in the market, Android dominated the market with more than 80% of the total market share in 2015 Q2 [27, 28]. Therefore Android popularity attracted several researchers to focus on investigating several different security aspects of Android, ranging from user identification [29, 30], feasibility of encryption methods on Android [31], cloud storage apps forensics [32], and social networking apps forensics [3]. Due to the increasing use of mVoIP apps for malicious activities on different platforms including Android, forensic investigation of such apps needs an extensive coverage [33, 34], and therefore in this chapter, we provide an investigative study of the three popular VoIP apps for Android on Google Play (see Table 1), namely: Viber [35], Skype [36], and WhatsApp [37]. The features of these VoIP apps are summarized in Table 2. In particular, we aim to answer the following question: “What artifacts of forensic value can be recovered from the use of Viber, Skype, and WhatsApp Android apps?”
2 Related Work
These days, several trusted and untrusted providers launch various categories of applications for mobile devices. This has led to the ever increasing trend in using mobile devices in order to benefit from the services offered by these applications. This tendency motivated the forensic community to concentrate on forensic investigation of the mobile devices. In this regard Dezfoli et al. [26] perused the future trends in digital investigation and determined that mobile phone forensics is receiving more and more attention by the community and is one of the fastest growing fields. In [38], the authors provided a comprehensive discussion on the nature of digital evidence on mobile devices, along with a complete guide on forensic techniques to handle, preserve, extract, and analyze evidence from mobile devices. Moreover, they presented examples of commercial forensic tools that can be used to obtain data from mobile phones, such as Access Data Forensic Toolkit (FTK), Cellebrite Physical, XACT, along with the case example of the adopted Digital Forensic Framework (DDF) plug-in. In the same line of study, Mohtasebi and Dehghantanha [39] presented a unified framework for investigating different types of smartphone devices. Parvez et al. [40] proposed a forensics framework for investigating Samsung phones. Several researchers have proposed various frameworks for the investigation of Nokia mobile devices and Firefox OS [25, 41].
A comparison of forensic evidence recovery techniques for a Windows Mobile smartphone demonstrates that there are different techniques to acquire and decode information of potential forensic interest from a Windows Mobile smartphone [42]. Furthermore, forensic examination of the Windows Mobile device database (the pim.vol) file confirmed that pim.vol contains information related to contacts, call history, speed-dial settings, appointments, and tasks [43]. Moreover, in [44], the authors provided a number of possible methods of acquiring and examining data on Windows Mobile devices, as well as the locations of potentially useful data, such as text messages, multimedia, email, Web browsing artifacts, and Registry entries. They also used MobileSpy monitoring software as a case example to highlight the importance of forensic analysis. They showed that the existence of such a malicious monitoring software on a Windows phone could be detectable on the device being investigated by forensics analyst. In another recent study, Yang et al. [45] carried out an investigative study on two popular Windows instant messaging apps, i.e., Facebook and Skype. The authors showed that several artifacts are recoverable, such as contact lists, conversations, and transferred files.
A research project published at the DFRWS 2010 Annual Conference discussed technical issues that are in place when capturing Android physical memory [46]. A critical review of 7 years of mobile device forensics [47] demonstrated that there are several research studies in the area of Android device forensics in the literature. However, very few of them support the varying levels of Android memory investigation. Lessard and Kessler [48] showed that it is possible to acquire a logical image of Android-based smartphones, such as Samsung Galaxy, using either a logical method or a physical method. The logical acquisition technique consists of obtaining a binary image of the device’s memory, which requires root access to the device. More so, Vidas et al. [49] discussed an acquisition methodology based on overwriting the “Recovery” partition on the Android device’s SD card with specialized forensic acquisition software. Likewise, Canlar et al. [21] proposed LiveSD Forensics, which is an on-device live data acquisition approach for Windows Mobile devices. They proposed a method to obtain artifacts from both the Random-Access Memory (RAM) and the Electronically Erasable Programmable Read Only Memory (EEPROM). In [50], the authors proposed a methodology for the collection and analysis of evidential data on Android devices, which used the principles of Martini and Choo’s cloud forensics framework [51]. The steps within this methodology are as follows: the collection of the physical image of the device partitions with the aid of a live OS bootloader, and the examination of app files in private and external storage, app databases, and accounts data for all apps of interest, on the android device. Using this methodology, in [52], the authors carried out an analysis of seven popular Android apps within three categories: storage (Dropbox, OneDrive, Box and ownCloud), note-taking (Evernote and OneNote), and password syncing (Universal Password Manager, UPM). Such analysis proves the validity of their proposed methodology.
In order to facilitate the forensic investigation of mobile devices that are rapidly changing in their structure, Do et al. [53] proposed a forensically sound adversary model. Azfar et al. [54] considered this adversary model as a template to map a potential adversary’s capabilities and constraints, in order to evaluate the usefulness of such a model by carrying out a forensic analysis of five popular Android social apps (Twitter, POF Dating, Snapchat, Fling, and Pinterest). They showed that useful artifacts are recoverable using this model, including databases, user account information, contact lists, images, and profile pictures. They could also discover timestamps for notifications and tweets, as well as a Facebook authentication token string used by the apps.
There is also a vast interest of digital investigators in studying the instant messaging artifacts in the stream of research in this area of digital forensics. The first claimed work to carry out a forensic analysis of Skype on the Android platform [55] investigated both the NAND and RAM flash memories in different scenarios. Their obtained results showed that chat and call patterns can be found in both of NAND and RAM flash memories of mobile devices, regardless of whether the Skype account has been signed out, signed in, or even after deleting the call history. In [34, 56], the authors showed that, while conducting recoveries of digital evidences relating to VoIP applications in computer systems, the Skype information is recoverable from the physical memory. Moreover, [57] presents another forensic analysis of several instant messaging applications including Skype and WhatsApp focusing on encryption algorithms used by these applications. Similar work has also been conducted by forensically analyzing WhatsApp on Android platforms [58, 59]. In the same line of study, a forensic analysis of four popular social networking applications (Facebook, Twitter, LinkedIn, and Google+) have been carried out which showed that artifacts useful as evidence in a potential criminal investigation are recoverable from smartphone devices using such applications [3]. Moreover, Yang et al. suggested an approach for forensics investigation of instant messaging applications on Windows 8.1 and applied it to detecting remnants of Facebook Instant Messaging and Skype application. Another important research direction that has always been a concern for digital investigators in investigation of instant messaging applications is privacy [60–62]. Ntantogian et al. [63] evaluated 13 Android mobile applications focusing on privacy. They tried to recover artifacts that provide information relating to authentication credentials. They showed that the users’ credentials are recoverable in the majority of the applications. Moreover, they determined specific patterns for the location of such credentials within a memory dump. In another research study [64], Farden et al. explored the privacy of user data with regards to mobile apps usage by evaluating the privacy risks that are inherent when using popular mobile dating Apps. They showed that in almost half of the investigated applications, the chat messages are recoverable, and in some cases details of other nearby users could also be extracted. Likewise, Azfar et al. [65] provided a forensic taxonomy of Android mHealth apps, by examining 40 popular Android mHealth apps. Their findings could potentially help facilitate forensic analysis of those particular mobile health applications.
In this paper we thoroughly analyze forensics remnants of three popular instant messaging applications, namely Viber, Skype, and WhatsApp on Android platform to provide a guideline for forensics practitioners in conducting similar investigations. Compared to previous studies, this research is delving into forensically valuable evidences in the context of Android platform and provides a comparative study of different VoIP applications remnants. Moreover, it is furthering forensics attention to lesser studied Viber and WhatsApp applications forensics.
3 Experimental Setup
Our investigative methodology is based on the digital forensic framework proposed by Martini and Choo [51]. In this study, we first identified the potential evidence sources and set up the experimental environment (Section 3.1). Thereafter, we carry out logical acquisition in order to collect evidential data (Section 3.2). Finally, by analyzing the collected data, we investigate possible remnant artifacts (Section 3.3). We further demonstrated and discussed the experimental results in Section 4, and presented the conclusions drawn from our investigation in Section 5; both of which exemplify the third and fourth steps of the framework methodology [51], i.e., “Examination and Analysis” and “Reporting and Presentation,” in which the results of the forensic study should be analyzed and presented appropriately.
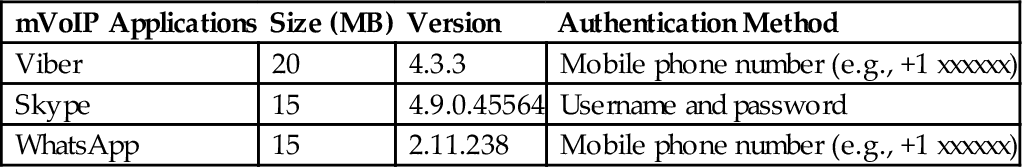
Since without rooting the smartphone device, we would not be able to access that without a rooting the smartphone device, we would not be able to access some of the stored files (we will explain in Section 3.2), we utilized a rooted Android phone, i.e., Samsung Galaxy S3 GT-i9300, in order to conduct our experiments. We set up and configured necessary workstations and tools (including both software and hardware), as listed in Table 3. Moreover, Table 4 reports the authentication methods required for our considered mVoIP applications and their details.
Table 3
Adopted Forensic Tools
| Tool | Version | Details |
| Android platform phone | Samsung S3 GT-i9300, Firmware version 3.0.31 | Mobile device used for this study |
| mVoIP applications | Viber 4.3.3 | Applications that are investigated |
| Skype 4.9.0.45564 | ||
| WhatsApp 2.11.238 | ||
| AccessData FTK Imager | V 3.1.4.6 | Used to explore the acquired logical image (internal memory) of the phone |
| SQLite database browser | 2.0bl | Visual tool that is used to explore the database extracted from each application after identifying the folders using AccessData FTK Imager |
| Internet evidence finder timeline | IEF v6.3 | Provides a view of each artifact on a visual timeline without any need to convert artifacts like timestamps |
| Root-Kit | Frameware CF-Auto-Root-m0 m0xx-gti9300 | Frameware is used to root the device |
| Odin3 | V 3.07 | Enables uploading of the root-kit frameware to the Android device |
| Epoch & Unix timestamp converter | Used to convert the timestamp found in hex format |
Table 4
Application Details and Authentication Methods on the Supported Android 4.3 Platform
| mVoIP Applications | Size (MB) | Version | Authentication Method |
| Viber | 20 | 4.3.3 | Mobile phone number (e.g., +1 xxxxxx) |
| Skype | 15 | 4.9.0.45564 | Username and password |
| 15 | 2.11.238 | Mobile phone number (e.g., +1 xxxxxx) |
Our examination and analysis process consist of three phases, which we explain in the following.
3.1 Phase I: Setup Phase—First Iteration
The first phase of our study is to identify and preserve the source of evidence, which is the first iteration. In this phase, we downloaded three mVoIP applications from the Google Play Store and installed them on a Samsung Galaxy S3 GT-i9300 smartphone. For WhatsApp and Viber applications, an active mobile SIM is required to activate the application, while Skype could be activated by the username and password of the registered account (see Table 4). For each application, we performed several activities, as described in Table 5, continuously for 1 month before the logical acquisition.
3.2 Phase II: Logical Acquisition
The smartphone device that we used for the experiments, i.e., Samsung Galaxy S3 GT-i9300 Firmware version 3.0.31, was originally not rooted. However, without a root access on the phone, many data files would be inaccessible. Therefore, we used the Odin3 (version 3.07) tool [66] to root the device by uploading the rook-kit frameware (CF-Auto-Root-m0-m0xx-gti9300) to the device. The installed root-kit gives the user root access, i.e., the user has the privilege control over the OS, which allows the user to attain privileged control within the Android’s subsystem, and bypass the limitation placed on the device by the manufacturer. The root access grants the user the privilege to access a certain protected directory that holds some of the artifacts needed for this experiment (e.g., [root]/data/directories). The needed directory is then backed up and later accessed with the use of other tools mentioned earlier (see Table 3). The procedure that we adopted in our data acquisition is forensically sound according to [49]; however, there are other methods to acquire a logical image on Android devices without having to root the device. After rooting the phone, the bit-by-bit physical acquisition of dd image is acquired using the following SSH command: ‘sshroot@(Device IP Address) dd if=/dev/block/mmcblk0p12 | of=(Location on your computer). The “mmcblk0p12” (which might be different in several devices) is the internal memory block of the Android device, which is 16GB and so, it takes hours to be fully acquired.
This phase of the experiments leads to acquisition of the logical image of the Android device, which is considered to be the most crucial phase in mobile forensics investigation process, as the generated hash values play a vital role when presenting the case in court of law [67].
3.3 Phase III: Identification and Analysis—Second Iteration
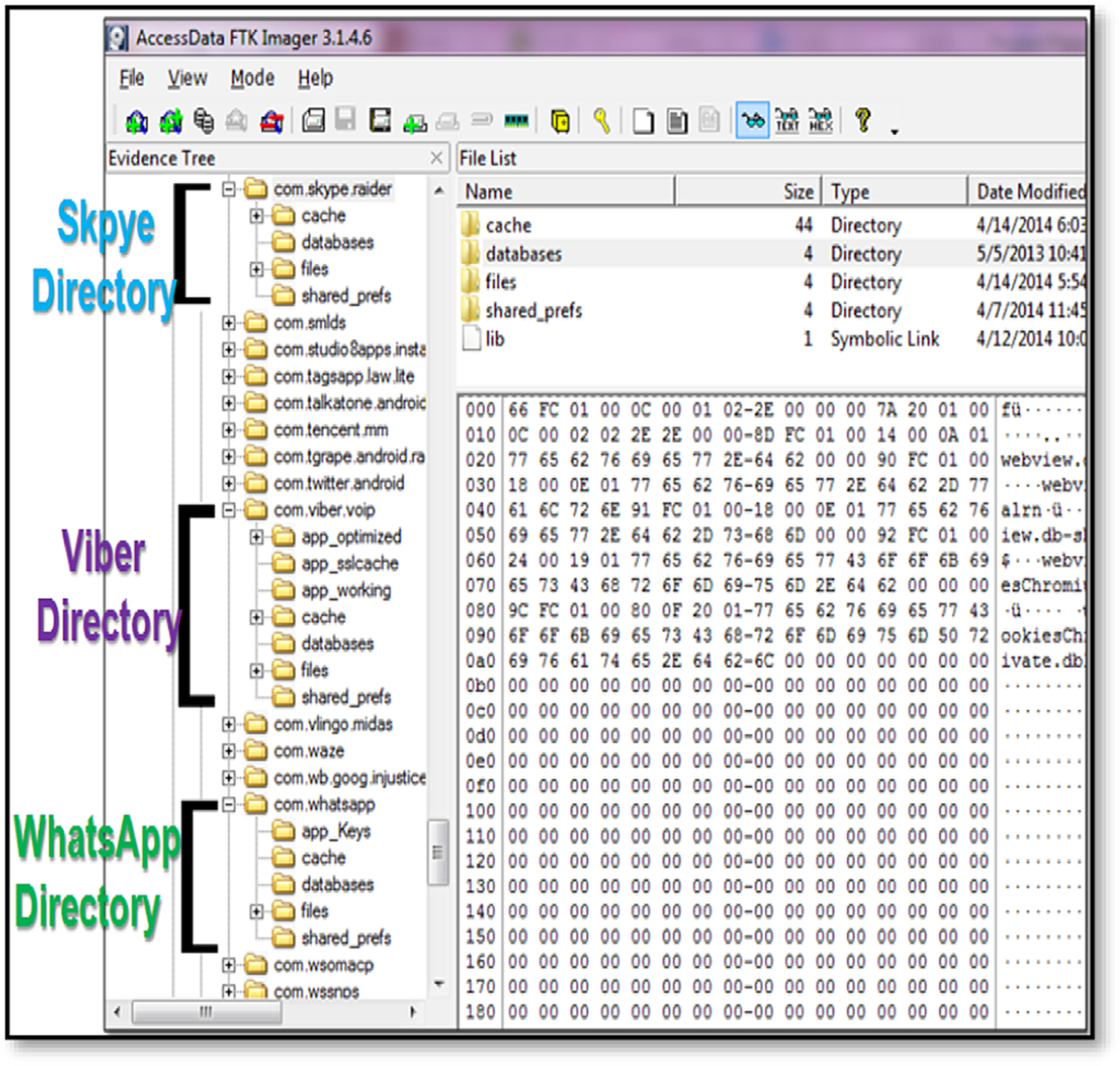
This third phase of the experiment includes identification of folders and files on the logical image acquired in the previous phase. Examination and analysis of the files in order to check the existence of artifacts such as timestamps, location, GPS coordination, contact info, text-chat, SMS, file location, and any significant data that could be relevant to the research area. We conducted forensic examinations manually, with the aid of the tools listed in Table 3. After acquiring the logical image, as described in Phase II, we used “AccessData FTK Imager” to analyze the acquired dd image which resulted in the creation of the directory default path. This allows us to access all the files in each directory, and therefore navigating to each one of the files. Fig. 1 shows the three folders of our three under investigation applications, Viber, Skype, and WhatsApp Messenger. After identifying these folders, in the next step, we need to carry out a deep inspection on each application’s database to know whether we can find any potential evidentiary artifact.
4 Results and Discussion
This section describes the potential artifacts found in each mVoIP application’s directory. Furthermore, we discuss the evidentiary values of the artifacts found for each of the mVoIP applications.
4.1 Viber Artifacts
This section describes the Viber artifacts found in both manual forensic analysis and using IEF tool. We found two unique database directories after examining dd image with the FTK imager for Viber application, which are:
• [root]/data/com.viber.voip/databases/viber_ data.db
• [root]/data/com.viber.voip/databases/viber_ messages.db
The Viber application has two databases: viber_ data.db, which contains the same information as wa.db in WhatsApp; and viber_ messages.db, which has the same information as msgstore.db in WhatsApp application. Once again, using a rooted device enabled us to access the database information in plaintext format. The viber_ data.db file contains data related to the outgoing calls, Viber contact names and numbers. In this experiment, we considered no blocked numbers; however, in case of having some blocked numbers, they would be recoverable as well. All these potential artifacts have evidentiary value relevant to a forensic investigation. On the other hand, the viber_ messages.db file stores geographical location information, contacts, and all the sent or received messages in a chat database. Through performing a forensic examination on this database, one would be able to determine the message exchange and also the actual source and destination of each exchanged message. With the aid of the IEF forensic tool, it is possible to determine whether a particular message was either sent or received by a particular sender or recipient. These artifacts are useful in helping a forensic investigator to determine if a particular suspect is worth taking to court.
4.2 Skype Artifacts
In order to examine the Skype application, after obtaining the dd image in the same way as Viber and WhatsApp, we used the IEF tool. We discovered that, Skype stores information in an SQLite database called main.db, and the file directory is: [root]/data/com.skype.raider/files/SkypeID/main.db, in which the “SkypeID” indicates a particular user account. The database contains information about a user’s account such as messages, calls, group chat, voicemails, contacts, SMS messages, and file transfers. We analyzed the main.db with the SQLite viewer. The timestamp was in Unix epoch time but later converted using the converting tool. Recoverable artifacts from the Skype contact lists include the Skype name, full name, birthday, gender, country, mobile number, email address, and registered date timestamp. Text-chat artifacts include the text message, message type, status, chat ID, and recipient ID. The call related artifacts that could be recovered are: the local user details, remote user details, call duration, and whether the call was incoming or outgoing. The artifacts related to file transfer that we could recover are: timestamp, file size (bytes), and status. Voicemail related artifacts include: the caller’s ID, voicemail size, and status. Finally, IP location related artifacts included the userID, IP address, and timestamp.
Most people actually believe that by physically deleting or clearing chat histories, the Skype logs will be deleted, and the data associated with a particular account cannot be recovered. In mobile devices, evidential data that contains such recoverable artifacts can prove fruitful and provide a rich source of evidence for investigating crimes related to Skype. The artifacts showing an incoming and an outgoing call have timestamps that are also captured along with the call duration. With such evidence, a suspect cannot deny initiating or engaging in such a call. This would give forensic examiners a stronger convincing power in the court of law when handling a case. Moreover, it is possible to recover full contact details of the Skype owner, i.e., full name, date of birth, phone number (if any), date of Skype creation, and email; this makes it easy for the suspect in question to be tracked down. The IP address reflects the “externally visible” IP address of the device where Skype is running, i.e., the IP address of the outermost NAT gateway connecting the device to the Internet. The IP address plays a significant role in terms of determining the geographical location of parties involved in the crime. This artifact can be useful for attribution as it indicates the IP address that the device used to connect to the Internet. This may help tie a subject to a particular IP address and activity originating from that address. Having found artifacts like name, email, mobile number, date of birth, gender, and country, it would be easy for a forensic investigator to further carry out the investigation based on what has been found and also to geographically point to where the relevant subjects reside.
4.3 WhatsApp Artifacts
In this section, we describe the WhatsApp Messenger artifacts that we found in this investigation. In fact, by examining the dd image with the FTK imager tool, we found out three unique directories: two of them are databases, while one is a directory path.
• [root]/data/com.whatsapp/files/Avatars/60xxxx@s.whatsapp.net
• [root]/data/com.whatsapp/databases/wa.db
• [root]/data/com.whatsapp/databases/msgstore.db
We could find the avatar icon of each contact in the WhatsApp application, along with user related MD5 and SHA1 hashes, which have evidentiary value, since they can be directly linked to a particular WhatsApp account, and hence can be used to identify the user who is using this account. Alongside the avatar pictures, the name and phone number of the user are also valuable to forensic specialists.
Since we used a rooted device in the experiments, the database appeared in plain text format. We discovered that the records and logs of all the activities carried out by the user that are listed in Table 5 are stored in two different database files: wa.db and msgstore.db. The wa.db file contains all the information relating to the contacts including the contact names, contact phone numbers, and WhatsApp status. These artifacts can be of great value to actually track down suspects, for example, a certain WhatsApp status update may betray information relating to a criminal activity. Having these kinds of artifacts, a digital forensic specialist would be able to potentially relate the status to an actual incident and back up their case accordingly. On the other hand, the msgstore.db contains artifacts with timestamps relating to sent and received text-chat messages, images, videos, and audios. By analyzing the same database using IEF tool, we could obtain the source and the destination of each message in order to detect the actual sender and receiver of each message.
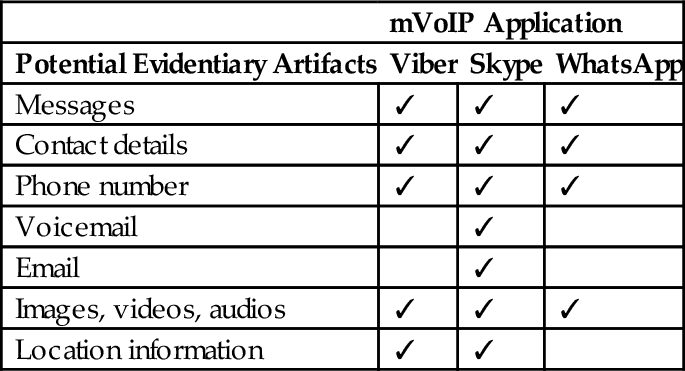
We summarized the results acquired from our investigation in Table 6. Both WhatsApp Messenger and Viber share almost the same potential evidentiary artifacts, however in WhatsApp Messenger, there is neither call duration, nor GPS coordination. Skype leaves more interesting artifacts, such as both local and private IP addresses which are capable of facilitating further investigation on a particular case.
Table 6
Summary of Potential Found Evidentiary Artifacts
| mVoIP Application | |||
| Potential Evidentiary Artifacts | Viber | Skype | |
| Messages | ✓ | ✓ | ✓ |
| Contact details | ✓ | ✓ | ✓ |
| Phone number | ✓ | ✓ | ✓ |
| Voicemail | ✓ | ||
| ✓ | |||
| Images, videos, audios | ✓ | ✓ | ✓ |
| Location information | ✓ | ✓ | |
So far only a few research studies have explored and addressed the forensic recovery and analysis of activities carried out on social network and instant messaging applications on smartphones. These studies provide limited information in terms of logical acquisition and artifacts recovery. On the contrary, our study explored the forensic acquisition, examination, and analysis of the logical image of a smartphone. Our experiment consisted of: (1) installation of three top-rated mVoIP applications, (2) carrying out the usual user activities on each of these applications, followed by the acquisition of the logical image using a forensically sound approach, and (3) performing a manual forensic analysis on each of the installed mVoIP applications. When carrying out such a digital forensic examination, however, there could be some potential obstacles that could make accurate data recovery difficult. For example, there are many varieties of lock screen apps, app lock, SMS, and picture locks; some of which encrypt the data stored on the mobile device, and also lock the device interface [68]. This could be an issue for a digital forensic specialist when examining such a device.
5 Conclusion and Future Work
In this chapter, we carried out a forensic analysis of the most popular mVoIP applications, i.e., Viber, Skype, and WhatsApp Messenger when running on an Android smartphone. Artifacts listed in Table 6 can provide vital evidence that can open up a case or offer a wealth of information for further investigation when dealing with crime related to mobile devices and mobile applications.
This study successfully applies a methodology adapted from an existing digital forensics framework, which uses various techniques from the existing literature, in order to perform a forensic analysis of Viber, Skype, and WhatsApp Messenger applications on an Android platform. We showed that potential evidentiary artifacts can be found on Android devices, which have forensic value to be presented in the court of law by a forensic investigator when handling a case related to cyber terrorism or cybercrime conspiracies. A possible future research direction could be a comprehensive research on different mobile operating system platforms, considering another mVoIP apps. This would provide vital information for digital forensic specialists.