Appendix A
TPM Command Reference
Commands to the TPM go through an interface known as the TSS. There are two types of commands that go to the TSS: those that are known to be secure, and those that are not needed to be secure. Commands that need not be secure are not usually implemented in the TPM and are found in Appendix B, “TSS Command Reference.” These include bind and verify signature. Commands that must be secure, and that therefore must be implemented in hardware, are prefixed with TPM.
Beyond this breakdown, there are several different kinds of commands. Some of them are designed to be used during setup of the system, some are designed to be used by the TSS to load and evict keys as necessary, some are designed to be used by an administrator, and some are designed to be used by application developers. There is no reason that the functions cannot be used by application developers, but they will not be as useful to them.
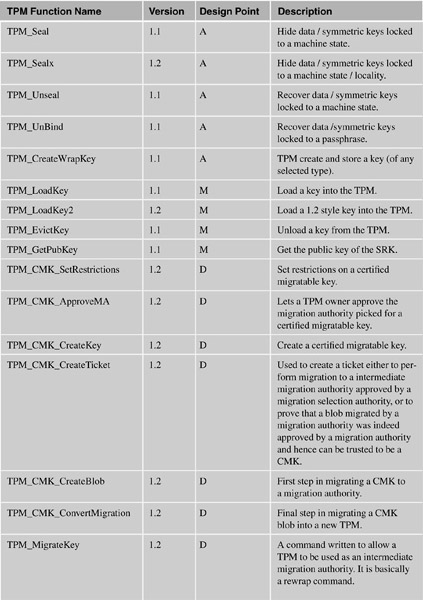
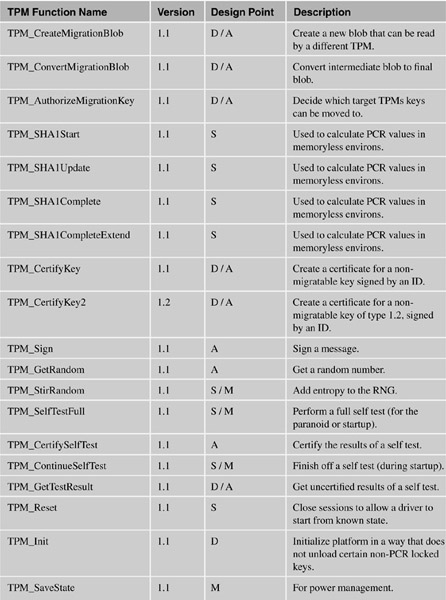
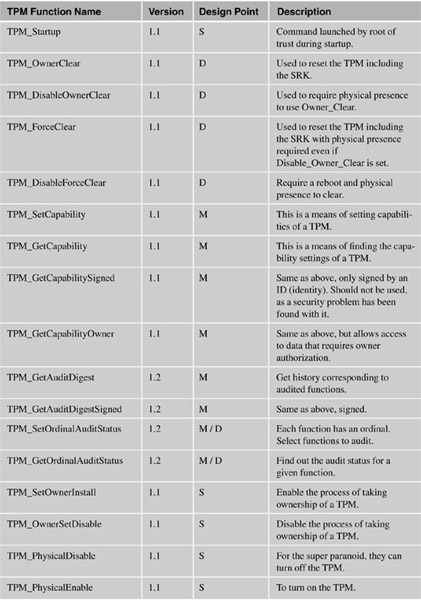
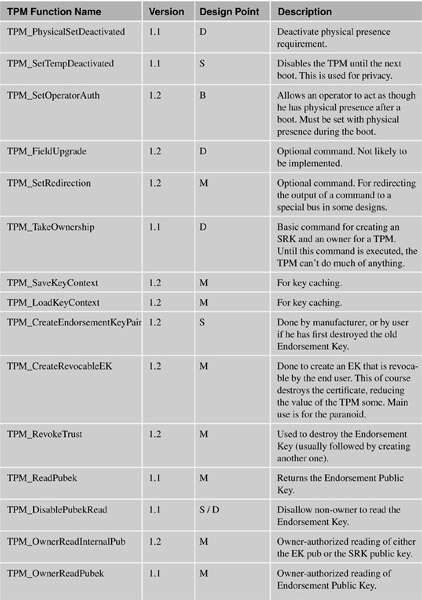
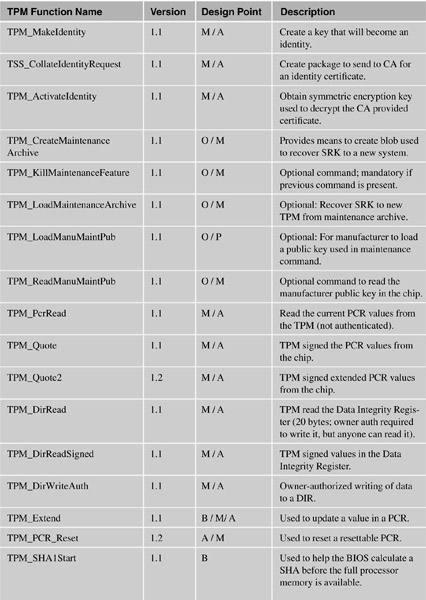
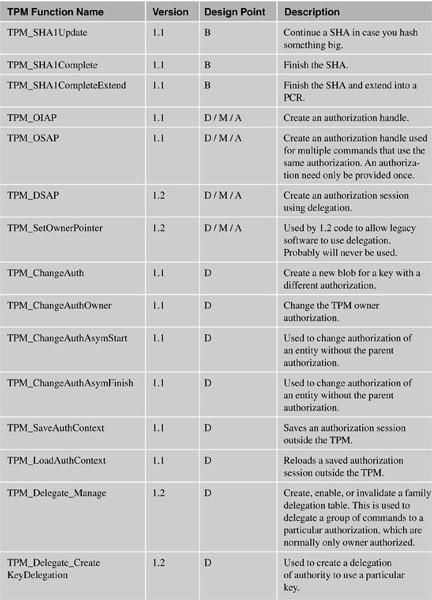
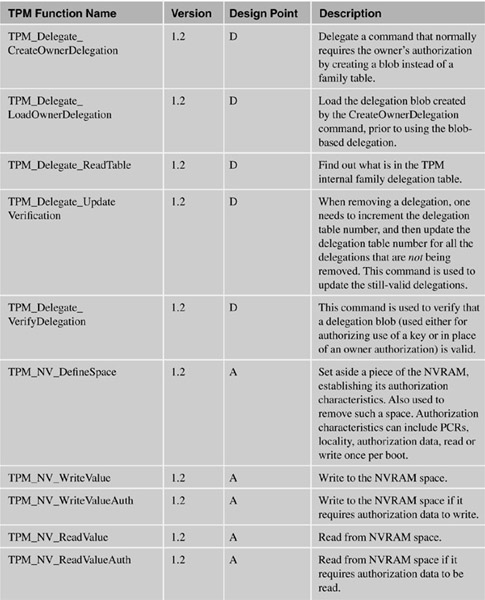
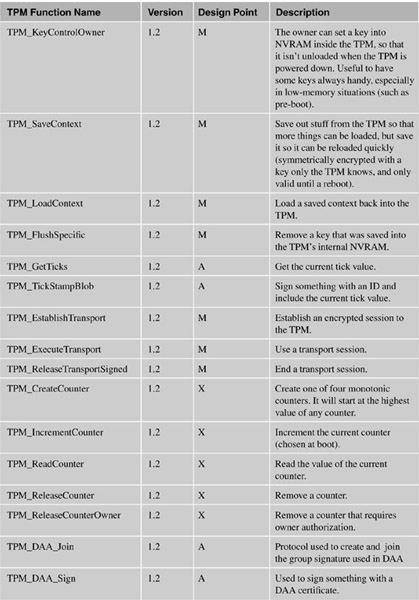
The following table lists the functions and categorizes them by their design point:
A = Application developer (or referenced in applications in this document).
B = For the BIOS.
S = Setup.
M = Middleware (such as loading/unloading keys as necessary).
D = Administration.
O = Optional command. These are unlikely to actually appear in any chip.
P = Command that would only be used by the manufacturer of the PC.
X = System or OS only.