CHAPTER 1
Introduction to Security
This chapter covers the following subjects:
![]() Security 101: School is in session. This section discusses some of the basic principles of information security such as CIA and AAA, some basic threats, and various ways to mitigate those threats.
Security 101: School is in session. This section discusses some of the basic principles of information security such as CIA and AAA, some basic threats, and various ways to mitigate those threats.
![]() Think Like a Hacker: “To know your Enemy, you must become your Enemy” (Sun Tzu). However, sometimes the hacker is your adversary, sometimes not. This section describes the various hats worn in the hacker society, as well as the other actors on the security stage and their attributes.
Think Like a Hacker: “To know your Enemy, you must become your Enemy” (Sun Tzu). However, sometimes the hacker is your adversary, sometimes not. This section describes the various hats worn in the hacker society, as well as the other actors on the security stage and their attributes.
![]() Threat Actor Types and Attributes: From script kiddies to hacktivists to nation states, the stage is filled with different individuals and entities you will defend against. Their motives might be pure, they might not—this section describes the other attackers you should know.
Threat Actor Types and Attributes: From script kiddies to hacktivists to nation states, the stage is filled with different individuals and entities you will defend against. Their motives might be pure, they might not—this section describes the other attackers you should know.
Welcome! Before we launch into heavy-duty security, I’d like to go over some foundation-level security concepts. I recommend that everyone read this chapter, but if you are a seasoned professional, you might opt to scan or skip it. For those of you new to the IT security field, this chapter (and the rest of the book) acts as the basis of your IT sleuthing career.
It is so important in today’s organizations to protect information and information systems from unauthorized access and to prevent the modification, disruption, or destruction of data unless it is approved by the organization. That in a nutshell is information security. Companies consider it so important that many IT directors have transformed into full-fledged executives—chief information officer (CIO), chief security officer (CSO), or chief technology officer (CTO). But let’s not get ahead of ourselves! This book is for persons wanting to embark on, or continue along, the path as a security administrator. Many other names are given to that particular position, but we’ll stick with that one for the sake of continuity throughout this book.
This entire book is all about information security; it’s about locating risks and vulnerabilities to your information, and eliminating those risks, or at least reducing them to a point acceptable to your organization.
This first chapter talks about some basic fundamental security concepts and teaches you to think like a hacker but act like an administrator.
Let’s begin!
Foundation Topics
Security 101
The first thing we need to get out of the way is that nothing is ever completely or truly secure. People might give clever definitions of something that could be completely secure, but it is a utopia—something that can be imagined but never achieved. There is always a way around or through any security precaution that we construct.
Now that it’s understood that there is no perfect scenario, we can move on to some security basics that can help to build a solid foundation upon which proper mitigating of security risks can begin.
The CIA of Computer Security
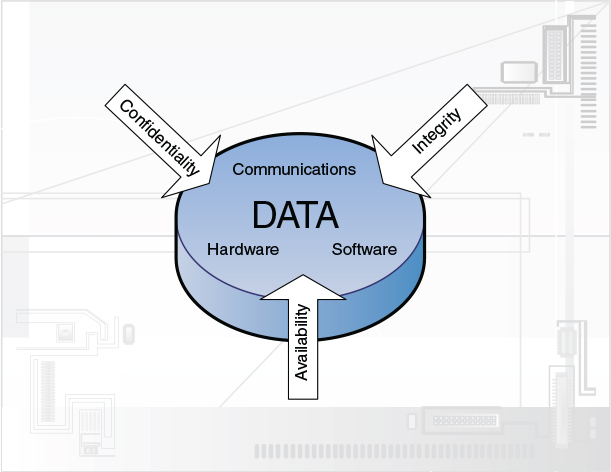
No, we’re not talking about the acronym associated with national security, but computers can indeed be the victim of covert operations. To defend against the worst, IT people attempt to adhere to three core principles of information security: confidentiality, integrity, and availability. Collectively, these three are known as the CIA triad as illustrated in Figure 1-1.

By employing the concepts of confidentiality, integrity, and availability to its data, an organization can properly secure its hardware, software, and communications. Let’s discuss each of the three items of the CIA triad in a little more depth.

![]() Confidentiality: This concept centers on preventing the disclosure of information to unauthorized persons. For the public it signifies Social Security numbers (or other country-specific identification), driver’s license information, bank accounts and passwords, and so on. For organizations this can include all the preceding information, but it actually denotes the confidentiality of data. To make data confidential, the organization must work hard to make sure that it can be accessed only by authorized individuals. This book spends a good amount of time discussing and showing how to accomplish this. For example, when you use a credit card number at a store or online, the number should be encrypted with a strong cipher so that the card number cannot be compromised. Next time you buy something over the Internet, take a look at how the credit card number is being kept confidential. As a security professional, confidentiality should be your number one goal. In keeping data confidential, you remove threats, absorb vulnerabilities, and reduce risk.
Confidentiality: This concept centers on preventing the disclosure of information to unauthorized persons. For the public it signifies Social Security numbers (or other country-specific identification), driver’s license information, bank accounts and passwords, and so on. For organizations this can include all the preceding information, but it actually denotes the confidentiality of data. To make data confidential, the organization must work hard to make sure that it can be accessed only by authorized individuals. This book spends a good amount of time discussing and showing how to accomplish this. For example, when you use a credit card number at a store or online, the number should be encrypted with a strong cipher so that the card number cannot be compromised. Next time you buy something over the Internet, take a look at how the credit card number is being kept confidential. As a security professional, confidentiality should be your number one goal. In keeping data confidential, you remove threats, absorb vulnerabilities, and reduce risk.
![]() Integrity: This means that data has not been tampered with. Authorization is necessary before data can be modified in any way; this is done to protect the data’s integrity. For example, if a person were to delete a required file, either maliciously or inadvertently, the integrity of that file will have been violated. There should have been permissions in place to stop the person from deleting the file. Here’s a tip for you: Some organizations do not delete data—ever!
Integrity: This means that data has not been tampered with. Authorization is necessary before data can be modified in any way; this is done to protect the data’s integrity. For example, if a person were to delete a required file, either maliciously or inadvertently, the integrity of that file will have been violated. There should have been permissions in place to stop the person from deleting the file. Here’s a tip for you: Some organizations do not delete data—ever!
![]() Availability: Securing computers and networks can be a strain on resources. Availability means that data is obtainable regardless of how information is stored, accessed, or protected. It also means that data should be available regardless of the malicious attack that might be perpetrated on it.
Availability: Securing computers and networks can be a strain on resources. Availability means that data is obtainable regardless of how information is stored, accessed, or protected. It also means that data should be available regardless of the malicious attack that might be perpetrated on it.
These three principles should be applied when dealing with the security of hardware, software, or communications. They should be foremost in the mind of a security administrator.
Another acronym to live by is the AAA of computer security: authentication, authorization, and accounting.

![]() Authentication: When a person’s identity is established with proof and confirmed by a system. Typically, this requires a digital identity of some sort, a username/password, biometric data, or other authentication scheme.
Authentication: When a person’s identity is established with proof and confirmed by a system. Typically, this requires a digital identity of some sort, a username/password, biometric data, or other authentication scheme.
![]() Authorization: When a user is given access to certain data or areas of a building. Authorization happens after authentication and can be determined in several ways, including permissions, access control lists, time-of-day restrictions, and other login and physical restrictions.
Authorization: When a user is given access to certain data or areas of a building. Authorization happens after authentication and can be determined in several ways, including permissions, access control lists, time-of-day restrictions, and other login and physical restrictions.
![]() Accounting: The tracking of data, computer usage, and network resources. Often it means logging, auditing, and monitoring of the data and resources. Accountability is quickly becoming more important in today’s secure networks. Part of this concept is the burden of proof. You as the security person must provide proof if you believe that someone committed an unauthorized action. When you have indisputable proof of something users have done and they cannot deny it, it is known as non-repudiation.
Accounting: The tracking of data, computer usage, and network resources. Often it means logging, auditing, and monitoring of the data and resources. Accountability is quickly becoming more important in today’s secure networks. Part of this concept is the burden of proof. You as the security person must provide proof if you believe that someone committed an unauthorized action. When you have indisputable proof of something users have done and they cannot deny it, it is known as non-repudiation.
This AAA concept should also be applied to any security plan you develop. But it goes further than this. There are authentication protocols based on the concept of AAA such as RADIUS and TACACS+, which we cover in more depth in Chapter 10, “Physical Security and Authentication Models.” Because of this, AAA is also referred to as a protocol. The details of AAA are set in stone within several RFC documents that can be downloaded from the following link: http://tools.ietf.org/wg/aaa/.
The Basics of Information Security
Information security is the act of protecting data and information systems from unauthorized access, unlawful modification and disruption, disclosure, corruption, and destruction. We discuss how to implement information security throughout the entire book, but for now let’s talk about several basic types of threats you need to be aware of to be an effective security administrator:
![]() Malicious software: Known as malware, this includes computer viruses, worms, Trojan horses, spyware, rootkits, adware, ransomware, crypto-malware, and other types of unwanted software. Everyone has heard of a scenario in which a user’s computer was compromised to some extent due to malicious software.
Malicious software: Known as malware, this includes computer viruses, worms, Trojan horses, spyware, rootkits, adware, ransomware, crypto-malware, and other types of unwanted software. Everyone has heard of a scenario in which a user’s computer was compromised to some extent due to malicious software.
![]() Unauthorized access: Access to computer resources and data without consent of the owner. It might include approaching the system, trespassing, communicating, storing and retrieving data, intercepting data, or any other methods that would interfere with a computer’s normal work. Access to data must be controlled to ensure privacy. Improper administrative access falls into this category as well.
Unauthorized access: Access to computer resources and data without consent of the owner. It might include approaching the system, trespassing, communicating, storing and retrieving data, intercepting data, or any other methods that would interfere with a computer’s normal work. Access to data must be controlled to ensure privacy. Improper administrative access falls into this category as well.
![]() System failure: Computer crashes or individual application failure. This can happen due to several reasons, including user error, malicious activity, or hardware failure.
System failure: Computer crashes or individual application failure. This can happen due to several reasons, including user error, malicious activity, or hardware failure.
![]() Social engineering: The act of manipulating users into revealing confidential information or performing other actions detrimental to the users. Almost everyone gets e-mails nowadays from unknown entities making false claims or asking for personal information (or money!); this is one example of social engineering.
Social engineering: The act of manipulating users into revealing confidential information or performing other actions detrimental to the users. Almost everyone gets e-mails nowadays from unknown entities making false claims or asking for personal information (or money!); this is one example of social engineering.
Many information security technologies and concepts can protect against, or help recover from, the preceding threats. The question is, does your organization have the resources to implement them? Even on a low budget the answer is usually “yes.” It all starts with planning, which is effectively free.
In general, a security administrator should create a proactive security plan that usually starts with the implementation of security controls. When creating the security plan, some IT professionals divide the plan into three categories of controls as follows:
![]() Physical: Things such as alarm systems, surveillance cameras, locks, ID cards, security guards, and so on.
Physical: Things such as alarm systems, surveillance cameras, locks, ID cards, security guards, and so on.
![]() Technical: Items such as smart cards, access control lists (ACLs), encryption, and network authentication.
Technical: Items such as smart cards, access control lists (ACLs), encryption, and network authentication.
![]() Administrative: Various policies and procedures, security awareness training, contingency planning, and disaster recovery plans (DRPs). Administrative controls can also be broken down into two subsections: procedural controls and legal/regulatory controls.
Administrative: Various policies and procedures, security awareness training, contingency planning, and disaster recovery plans (DRPs). Administrative controls can also be broken down into two subsections: procedural controls and legal/regulatory controls.
Note
We’ll expand on these and other security controls in Chapter 12, “Vulnerability and Risk Assessment.”
These information security controls are used to protect the confidentiality, integrity, and availability, or “CIA” of data.
More specifically, several ways to prevent and help recover from the previous threats include
![]() User awareness: The wiser the user, the less chance of security breaches. Employee training and education, easily accessible and understandable policies, security awareness e-mails, and online security resources all help to provide user awareness. These methods can help to protect from all the threats mentioned previously. Although it can only go so far while remaining cost-effective and productive, educating the user can be an excellent method when attempting to protect against security attacks.
User awareness: The wiser the user, the less chance of security breaches. Employee training and education, easily accessible and understandable policies, security awareness e-mails, and online security resources all help to provide user awareness. These methods can help to protect from all the threats mentioned previously. Although it can only go so far while remaining cost-effective and productive, educating the user can be an excellent method when attempting to protect against security attacks.
![]() Authentication: Verifying a person’s identity helps to protect against unauthorized access. Authentication is a preventative measure that can be broken down into five categories:
Authentication: Verifying a person’s identity helps to protect against unauthorized access. Authentication is a preventative measure that can be broken down into five categories:
— Something the user knows; for example, a password or PIN
— Something the user has; for example, a smart card or other security token
— Something the user is; for example, the biometric reading of a fingerprint or retina scan
— Something a user does; for example, voice recognition or a written signature
— Somewhere a user is; for example, a GPS-tracked individual, or when a system is authenticated through geographic location
![]() Anti-malware software: Anti-malware protects a computer from the various forms of malware and, if necessary, detects and removes them. Types include antivirus and anti-spyware software. Well-known examples include programs from Symantec and McAfee, as well as Microsoft’s Windows Defender. Nowadays, a lot of the software named “antivirus” can protect against spyware and other types of malware as well.
Anti-malware software: Anti-malware protects a computer from the various forms of malware and, if necessary, detects and removes them. Types include antivirus and anti-spyware software. Well-known examples include programs from Symantec and McAfee, as well as Microsoft’s Windows Defender. Nowadays, a lot of the software named “antivirus” can protect against spyware and other types of malware as well.
![]() Data backups: Backups won’t stop damage to data, but they can enable you to recover data after an attack or other compromise, or system failure. From programs such as Windows Backup and Restore, Windows File History, and Bacula to enterprise-level programs such as Veritas Backup Exec and the various cloud-based solutions, data backup is an important part of security. Note that fault-tolerant methods such as RAID 1, 5, 6, and 10 are good preventative measures against hardware failure but might not offer protection from data corruption or erasure. For more information on RAID, see Chapter 16, “Redundancy and Disaster Recovery.”
Data backups: Backups won’t stop damage to data, but they can enable you to recover data after an attack or other compromise, or system failure. From programs such as Windows Backup and Restore, Windows File History, and Bacula to enterprise-level programs such as Veritas Backup Exec and the various cloud-based solutions, data backup is an important part of security. Note that fault-tolerant methods such as RAID 1, 5, 6, and 10 are good preventative measures against hardware failure but might not offer protection from data corruption or erasure. For more information on RAID, see Chapter 16, “Redundancy and Disaster Recovery.”
![]() Encryption: This involves changing information using an algorithm (known as a cipher) to make that information unreadable to anyone except users who possess the proper “key.” Examples of this include wireless sessions encrypted with Advanced Encryption Standard (AES), web pages encrypted with HTTP Secure (HTTPS), and e-mails encrypted with Secure/Multipurpose Internet Mail Extensions (S/MIME) or Pretty Good Privacy (PGP).
Encryption: This involves changing information using an algorithm (known as a cipher) to make that information unreadable to anyone except users who possess the proper “key.” Examples of this include wireless sessions encrypted with Advanced Encryption Standard (AES), web pages encrypted with HTTP Secure (HTTPS), and e-mails encrypted with Secure/Multipurpose Internet Mail Extensions (S/MIME) or Pretty Good Privacy (PGP).
![]() Data removal: Proper data removal goes far beyond file deletion or the formatting of digital media. The problem with file deletion/formatting is data remanence, or the residue, left behind, from which re-creation of files can be accomplished by some less-than-reputable people with smart tools. Companies typically employ one of three options when met with the prospect of data removal: clearing, purging (also known as sanitizing), and destruction. We talk more about these in Chapter 18, “Policies and Procedures.”
Data removal: Proper data removal goes far beyond file deletion or the formatting of digital media. The problem with file deletion/formatting is data remanence, or the residue, left behind, from which re-creation of files can be accomplished by some less-than-reputable people with smart tools. Companies typically employ one of three options when met with the prospect of data removal: clearing, purging (also known as sanitizing), and destruction. We talk more about these in Chapter 18, “Policies and Procedures.”
By combining a well-thought-out security plan with strong individual security methods, a security professional can effectively stop threats before they become realities, or at the least, in worst-case scenarios, recover from them quickly and efficiently. The strongest security plans take many or all of these methods and combine them in a layering strategy known as defense in depth, which can be defined as the building up and layering of security measures that protect data throughout the entire life cycle starting from inception, on through usage, storage, and network transfer, and finally to disposal.
Think Like a Hacker
I’m not condoning any malicious activity, but to think like a hacker, you have to understand the hacker. A good hacker understands the mind of a security administrator, making computer and network security a difficult proposition. But the converse is true as well—the smart security person is aware of hackers and their methods.
So, ask yourself, why do people decide to become hackers? In the minds of some malicious individuals, it may simply be because users are there to be taken advantage of! Another common answer is greed—in this case the act of hacking for illegal monetary gain. Other attackers have an agenda, or believe in a cause. Some want to get free access to movies and music. Finally, some just want to cause mayhem and anarchy. Consider this when you secure your organization’s computers—they just might be a target! Of course, people use different names to classify these types of individuals: hacker, cracker, cyber-criminal, and so on. It doesn’t matter what you call them, but the accepted term in most network security circles is hacker—which we will use throughout this book.
Now consider this: Not all hackers are malicious. That’s right! There are different types of hackers. Various names are used by different organizations, but some of the common labels include the following:
![]() White hats: These people are non-malicious; for example, an IT person who attempts to “hack” into a computer system before it goes live to test the system. Generally, the person attempting the hack has a contractual agreement with the owner of the resource to be hacked. White hats often are involved in something known as ethical hacking. An ethical hacker is an expert at breaking into systems and can attack systems on behalf of the system’s owner and with the owner’s consent. The ethical hacker uses penetration testing and intrusion testing to attempt to gain access to a target network or system.
White hats: These people are non-malicious; for example, an IT person who attempts to “hack” into a computer system before it goes live to test the system. Generally, the person attempting the hack has a contractual agreement with the owner of the resource to be hacked. White hats often are involved in something known as ethical hacking. An ethical hacker is an expert at breaking into systems and can attack systems on behalf of the system’s owner and with the owner’s consent. The ethical hacker uses penetration testing and intrusion testing to attempt to gain access to a target network or system.
![]() Black hats: These are malicious individuals who attempt to break into computers and computer networks without authorization. Black hats are the ones who attempt identity theft, piracy, credit card fraud, and so on. Penalties for this type of activity are severe, and black hats know it; keep this in mind if and when you come into contact with one of these seedy individuals—they can be brutal, especially when cornered. Of course, many vendors try to make the term “black hat” into something cuter and less dangerous. But for the purposes of this book and your job security, we need to speak plainly, so here we will consider a black hat to be a malicious individual.
Black hats: These are malicious individuals who attempt to break into computers and computer networks without authorization. Black hats are the ones who attempt identity theft, piracy, credit card fraud, and so on. Penalties for this type of activity are severe, and black hats know it; keep this in mind if and when you come into contact with one of these seedy individuals—they can be brutal, especially when cornered. Of course, many vendors try to make the term “black hat” into something cuter and less dangerous. But for the purposes of this book and your job security, we need to speak plainly, so here we will consider a black hat to be a malicious individual.
![]() Gray hats: These are possibly the most inexplicable people on the planet. They are individuals who do not have any affiliation with a company but risk breaking the law by attempting to hack a system and then notify the administrator of the system that they were successful in doing so—just to let them know! Not to do anything malicious (other than breaking in…). Some gray hats offer to fix security vulnerabilities at a price, but these types are also known as green hats or mercenaries.
Gray hats: These are possibly the most inexplicable people on the planet. They are individuals who do not have any affiliation with a company but risk breaking the law by attempting to hack a system and then notify the administrator of the system that they were successful in doing so—just to let them know! Not to do anything malicious (other than breaking in…). Some gray hats offer to fix security vulnerabilities at a price, but these types are also known as green hats or mercenaries.
![]() Blue hats: These are individuals who are asked to attempt to hack into a system by an organization, but the organization does not employ them. The organization relies on the fact that the person simply enjoys hacking into systems. Usually, this type of scenario occurs when testing systems.
Blue hats: These are individuals who are asked to attempt to hack into a system by an organization, but the organization does not employ them. The organization relies on the fact that the person simply enjoys hacking into systems. Usually, this type of scenario occurs when testing systems.
![]() Elite: Elite hackers are the ones who first find out about vulnerabilities. Only 1 out of an estimated 10,000 hackers wears the Elite hat—and I say that figuratively. The credit for their discoveries is usually appropriated by someone else more interested in fame. Many of these types of individuals don’t usually care about “credit due” and are more interested in anonymity—perhaps a wise choice. You do not want to get on an Elite hacker’s bad side; they could crumple most networks and programs within hours if they so desired.
Elite: Elite hackers are the ones who first find out about vulnerabilities. Only 1 out of an estimated 10,000 hackers wears the Elite hat—and I say that figuratively. The credit for their discoveries is usually appropriated by someone else more interested in fame. Many of these types of individuals don’t usually care about “credit due” and are more interested in anonymity—perhaps a wise choice. You do not want to get on an Elite hacker’s bad side; they could crumple most networks and programs within hours if they so desired.
I mentioned before that no system is truly secure (and I use the term “system” loosely). Hackers know this and count on it. There’s always a way to circumnavigate a defense. It’s a constant battle in which administrators and attackers are consistently building and breaking down better and better mouse traps. The scales are always tipping back and forth; a hacker develops a way to break into a system, then an administrator finds a way to block that attack, then the hacker looks for an alternative method, and so on. This seems to reek of the chicken and the egg—which came first? Answer: You have to take it on a case-by-case basis. The last few sentences of banter are there for one reason—to convince you that you need to be on your toes; that you need to review logs often; that you need to employ as many security precautions as possible; that you need to keep abreast of the latest attacks and ways to mitigate risk; and that you must never underestimate the power and resilience of a hacker.
Threat Actor Types and Attributes
The security arena has other types of personas as well. It’s important to understand the types of attackers that you might encounter and their characteristics and personality traits. Keep in mind that these “actors” can find ways to access systems and networks just by searching the Internet. So, some attacks can be perpetrated by people with little knowledge of computers and technology. Other actors have increased knowledge—and with knowledge comes power—the type of power you want to be ready for in advance. However, all levels of attackers can be dangerous. Let’s describe several of the actors now.
The first of these personas is the script kiddie. This is an unsophisticated individual with little or no skills when it comes to technology. The person uses code that was written by others and is freely accessible on the Internet. For example, a script kiddie might copy a malicious PHP script directly from one website to another; only the knowledge of “copy and paste” is required. It’s a derogatory term that is often associated with juveniles. Though the processes they use are simple, script kiddies can knowingly (and even unwittingly) inflict incredible amounts of damage to insecure systems. These people almost never have internal knowledge of a system and typically have a limited amount of resources, so the amount, sophistication, and extent of their attacks is constrained. They are often thrill-seekers and are motivated by a need to increase their reputation in the script-kiddie world.
Next is the hacktivist—a combination of the terms hack and activist. As with the term hacker, the name of hacktivist is often applied to different kinds of activities; from hacking for social change, to hacking to promote political agendas, to full-blown cyberterrorism. Due to the ambiguity of the term, a hacktivist could be inside the company or attack from the outside and will have a varying amount of resources and funding. However, the hacktivist is usually far more competent than a script kiddie.
Cyber-criminals might work on their own, or they might be part of organized crime—a centralized enterprise run by people motivated mainly by money. Individuals who are part of an organized crime group are often well-funded and can have a high level of sophistication.
Individuals might also carry out cyberattacks for governments and nation states. In this case, a government—and its processes—is known as an advanced persistent threat (APT), though this term can also refer to the set of computer-attacking processes themselves. Often, an APT entity has the highest level of resources, including open-source intelligence (OSINT) and covert sources of intelligence. This, coupled with extreme motivation, makes the APT one of the most dangerous foes.
Companies should be prepared for insiders and competitors as well. In fact, they might be one and the same. An inside threat can be one of the deadliest to servers and networks, especially if the person is a systems administrator or has security clearance at the organization.
You should know these actors and their motivations, but in the end, it doesn’t matter too much what you call the attacker. Be ready to prevent the basic attacks and the advanced attacks and treat them all with respect.
Note
For the bulk of this book I will simply use the term attacker to represent any individual or group that perpetrates an attack on any type of technology.
Chapter Review Activities
Use the features in this section to study and review the topics in this chapter.
Review Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 1-1 lists a reference of these key topics and the page number on which each is found.

Table 1-1 Key Topics for Chapter 1
Key Topic Element |
Description |
Page Number |
The CIA of computer security |
||
Bulleted list |
Definitions of confidentiality, integrity, and availability |
|
Bulleted list |
Definitions of authentication, authorization, and accounting |
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
information security, confidentiality, integrity, availability, authentication, authorization, accounting, non-repudiation, defense in depth, white hat, ethical hacker, black hat, script kiddie, hacktivist, organized crime, advanced persistent threat (APT)
Review Questions
Answer the following review questions. Check your answers with the correct answers that follow.
1. In information security, what are the three main goals? (Select the three best answers.)
A. Auditing
B. Integrity
C. Non-repudiation
D. Confidentiality
E. Risk Assessment
F. Availability
2. To protect against malicious attacks, what should you think like?
A. Hacker
B. Network admin
C. Spoofer
D. Auditor
3. Tom sends out many e-mails containing secure information to other companies. What concept should be implemented to prove that Tom did indeed send the e-mails?
A. Authenticity
B. Non-repudiation
C. Confidentiality
D. Integrity
4. Which of the following does the A in CIA stand for when it comes to IT security? (Select the best answer.)
A. Accountability
B. Assessment
C. Availability
D. Auditing
5. Which of the following is the greatest risk when it comes to removable storage?
A. Integrity of data
B. Availability of data
C. Confidentiality of data
D. Accountability of data
6. When it comes to information security, what is the I in CIA?
A. Insurrection
B. Information
C. Indigestion
D. Integrity
7. You are developing a security plan for your organization. Which of the following is an example of a physical control?
A. Password
B. DRP
C. ID card
D. Encryption
8. A user receives an e-mail but the e-mail client software says that the digital signature is invalid and the sender of the e-mail cannot be verified. The would-be recipient is concerned about which of the following concepts?
A. Confidentiality
B. Integrity
C. Remediation
D. Availability
9. Cloud environments often reuse the same physical hardware (such as hard drives) for multiple customers. These hard drives are used and reused when customer virtual machines are created and deleted over time. What security concern does this bring up implications for?
A. Availability of virtual machines
B. Integrity of data
C. Data confidentiality
D. Hardware integrity
10. Which of the following individuals uses code with little knowledge of how it works?
A. Hacktivist
B. Script kiddie
C. APT
D. Insider
11. When is a system completely secure?
A. When it is updated
B. When it is assessed for vulnerabilities
C. When all anomalies have been removed
D. Never
Answers and Explanations
1. B, D, and F. Confidentiality, integrity, and availability (known as CIA, the CIA triad, and the security triangle) are the three main goals when it comes to information security. Another goal within information security is accountability.
2. A. To protect against malicious attacks, think like a hacker. Then, protect and secure like a network security administrator.
3. B. You should use non-repudiation to prevent Tom from denying that he sent the e-mails.
4. C. Availability is what the A in CIA stands for, as in “the availability of data.” Together the acronym stands for confidentiality, integrity, and availability. Although accountability is important and is often included as a fourth component of the CIA triad, it is not the best answer. Assessment and auditing are both important concepts when checking for vulnerabilities and reviewing and logging, but they are not considered to be part of the CIA triad.
5. C. For removable storage, the confidentiality of data is the greatest risk because removable storage can easily be removed from the building and shared with others. Although the other factors of the CIA triad are important, any theft of removable storage can destroy the confidentiality of data, and that makes it the greatest risk.
6. D. The I in CIA stands for integrity. The acronym CIA stands for confidentiality, integrity, and availability. Accountability is also a core principle of information security.
7. C. An ID card is an example of a physical security control. Passwords and encryption are examples of technical controls. A disaster recovery plan (DRP) is an example of an administrative control.
8. B. The recipient should be concerned about the integrity of the message. If the e-mail client application cannot verify the digital signature of the sender of the e-mail, then there is a chance that the e-mail either was intercepted or is coming from a separate dangerous source. Remember, integrity means the reliability of the data, and whether or not it has been modified or compromised by a third party before arriving at its final destination.
9. C. There is a concern about data confidentiality with cloud computing because multiple customers are sharing physical hard drive space. A good portion of customers run their cloud-based systems in virtual machines. Some virtual machines could run on the very same hard drive (or very same array of hard drives). If one of the customers had the notion, he could attempt to break through the barriers between virtual machines, which if not secured properly, would not be very difficult to do.
10. B. A script kiddie uses code and probably doesn’t understand how it works and what the repercussions will be. Other actors such as hackers, hacktivists, insiders, and so on will usually have a higher level of sophistication when it comes to technology. An advanced persistent threat (APT) is a group of technical processes or the entity that implements those processes. An APT is just that—advanced—and is on the other side of the spectrum from the script kiddie.
11. D. A system can never truly be completely secure. The scales are always tipping back and forth; a hacker develops a way to break into a system, then an administrator finds a way to block that attack, and then the hacker looks for an alternative method. It goes on and on; be ready to wage the eternal battle!