Chapter 2. Security, Privacy Policies, and Procedures
This chapter covers the following topics:
Policy and Process Life Cycle Management: This section discusses the effects that new business, new technologies, environmental changes, and regulatory requirements have on policy and process life cycle management.
Support Legal Compliance and Advocacy: This section covers partnering with human resources, legal, management, and other entities to support legal compliance.
Common Business Documents to Support Security: The documents discussed in this section include risk assessments/statements of applicability, business impact analyses, interoperability agreements, interconnection security agreements, memorandums of understanding, service-level agreements, operating-level agreements, non-disclosure agreements, business partnership agreements, and master service agreements.
Security Requirements for Contracts: Topics include requests for proposal, requests for quote, requests for information, and agreements.
General Privacy Principles for Sensitive Information: This section explains personally identifiable information and details the privacy principles that are important for protecting PII.
Policies Containing Standard Security Practices: The components discussed include separation of duties, job rotation, mandatory vacation, the principle of least privilege, incident response, forensic tasks, employment and termination procedures, continuous monitoring, training and awareness for users, auditing requirements and frequency, and information classification.
This chapter covers CAS-003 objective 1.2.
IT governance documents should be implemented to ensure that organizational assets are protected as well as possible. This chapter explains how the process and policy life cycles are managed and how to support legal compliance. It also discusses business documents and contracts that are commonly used to support security. It covers general privacy principles. Finally, it discusses the development of policies containing standard security practices.
Policy and Process Life Cycle Management
In a top-down approach, management initiates, supports, and directs the security program. In a bottom-up approach, staff members develop a security program prior to receiving direction and support from management. A top-down approach is much more efficient than a bottom-up approach because management’s support is one of the most important components of a security program. Using the top-down approach can help ensure that an organization’s policies align with its strategic goals.
In the context of organizational security, a policy is a course or principle of action adopted by an organization, and a process is a series of actions taken to achieve a particular end. A procedure is a series of actions conducted in a certain order or manner. Policies, procedures, and processes determine all major decisions and actions within an organization, and all organizational tasks operate within the boundaries set by policies, procedures, and processes.
To understand the relationship between the three, policies are written first to guide the creation of procedures and processes. Processes then provide a high-level view of tasks within the processes. Procedures are the detailed steps involved to complete the process.
Let’s look at an example. Say that an organization adopts a particular policy for processing accounts payable. The process designed around this policy details the high-level tasks that must occur, which may include receiving the bill, inputting the bill, authorizing the payment, printing the check, signing the check, and mailing the check. The procedures written would include each separate step involved in each task in the process.
Policies should be written based on the following life cycle:

Step 1. Develop the policy.
Step 2. Perform quality control.
Step 3. Obtain approval of the policy.
Step 4. Publish the policy.
Step 5. Periodically review the policy.
Step 6. Archive the policy when no longer needed or applicable.
During this life cycle, the quality control should be performed prior to obtaining approval to ensure that the policy complies with laws, regulations, and standards. When the policy is published, the organization must ensure that the affected personnel are properly educated on the new policy. The new policy should be incorporated into any training received by these personnel. Each policy should at minimum be reviewed annually. If policies must be changed, version control should be implemented to ensure that the most current version of a policy is being used across the enterprise. When a policy is outdated, it should be archived.
Policies should be reviewed often and on a regular schedule. Certain business, technology, risk, and environment changes should always trigger a review of policies, including adoption of a new technology, merger with another organization, and identification of a new attack method.
For example, suppose that employees request remote access to corporate email and shared drives. If remote access has never been offered but the need to improve productivity and rapidly respond to customer demands means staff now require remote access, the organization should analyze the need to determine whether it is valid. Then, if the organization decides to allow remote access, the organization’s security professionals should plan and develop security policies based on the assumption that external environments have active hostile threats.
Policies that should be considered include password policies, data classification policies, wireless and VPN policies, remote access policies, and device access policies. Most organizations develop password and data classification policies first.
A process is a collection of related activities that produce a specific service or product (that is, serve a particular goal) for the organization. Change management and risk management are examples of processes.
Once a policy is written, the appropriate processes should be written based on the following life cycle:

Step 1. Analyze
Step 2. Design
Step 3. Implement
Step 4. Monitor
Step 5. Retire
During this life cycle, step 1 is the time to analyze the policy, and step 2 is the time to design the process based on the policy. When the new process is implemented, all personnel involved in the process should be informed of how the process works. The process should be monitored regularly and may be modified as issues arise or as the base policy has been updated. Keep in mind that processes are created based on the policy. If a new policy is adopted, then a new process is needed. If a policy is edited or archived, then the process for the policy should also be edited or retired.
Once the policy and associated processes are documented, procedures must be written. Procedures embody all the detailed actions that personnel are required to follow and are the closest to the computers and other devices. Procedures often include step-by-step lists on how policies and processes are implemented.
Once an organization has analyzed the business, technology, risk, and environment changes to develop and update policies, the organization must take the next step: Develop and update its processes and procedures in light of the new or updated policies and environment and business changes. Procedures might have to be changed, for example, if the organization upgrades to the latest version of the backup software it uses. Most software upgrades involve analyzing the current procedures and determining how they should be changed. As another example, say that management decides to use more outside contractors to complete work. The organization may need to add a new process within the organization for reviewing the quality of the outside contractor’s work. As a final example, suppose that an organization decides to purchase several Linux servers to replace the current Microsoft file servers. While the high-level policies will remain the same, the procedures for meeting those high-level policies will have to be changed.
If an organization’s marketing department needs to provide more real-time interaction with its partners and consumers and decides to move forward with a presence on multiple social networking sites for sharing information, the organization would need to establish a specific set of trained people who can release information on the organization’s behalf and provide other personnel with procedures and processes for sharing the information.
Some of the processes and procedures that should be considered include the change management process, the configuration management process, network access procedures, wireless access procedures, and database administration procedures. But remember that procedures and processes should be created or changed only after the appropriate policies are adopted. The policies will guide the development of the processes and procedures.
Internal organizational drivers are the basis on which policies and processes are developed. Organizations should ensure that policies and processes are designed or reviewed when new business or business changes occur, new technologies are launched, environmental changes occur, or regulatory requirements change.
New Business
New business occurs when an organization launches or purchases a new area of business. Business changes are changes dictated by the nature of an organization’s business and are often driven by consumer demands. As a change occurs, an organization must ensure that it understands the change and its implication for the security posture of the organization. Organizations should take a proactive stance when it comes to these changes. Don’t wait for problems. Anticipate the changes and deploy mitigation techniques to help prevent them!
Suppose a business decides to launch a new endeavor whereby consumers can now directly purchase the products that were previously only sold to large retail stores. A new business policy will need to be written based on this new model, and a new process will need to be designed to handle the new business.
Security professionals are integral to any projects wherein new business is starting or business changes are occurring because the security professionals ensure that security controls are considered. Security professionals should ensure that all risks associated with the new business or business change are documented, analyzed, and reported to management. They must also document any suggested security controls that will mitigate these risks.
New Technologies
Technology changes are driven by new technological developments that force organizations to adopt new technologies. Again, organizations must ensure that they understand the changes and their implications for the security posture of the organization.
Suppose a business decides to allow personnel to implement a bring your own device (BYOD) policy. Security professionals should work to ensure that the policy defines the parameters wherein BYOD will be allowed or denied. In addition, the process would need to be written and would likely include obtaining formal approval of a device, assessing the security posture of the device, and granting the device full or limited access based on the device’s security posture.
Security professionals are integral to the inclusion or usage of any new technologies because they ensure that security controls will be considered. Security professionals should ensure that all risks associated with new technology are documented, analyzed, and reported to management. They must also suggest and document security controls to mitigate these risks.
Environmental Changes
Environmental changes are divided into two categories: those motivated by the culture in an organization and those motivated by the environment of the industry. As with new business or technologies, organizations must ensure that they understand the changes and their implications for the security posture of the organization.
Suppose a business decides to implement a new policy that provides a certain amount of “green space” for each of its facilities. Management would need to develop a process whereby these green spaces could be completed and maintained. It would likely include purchasing the land, designing the plan for the land, implementing the new green space, and maintaining the green space.
Regulatory Requirements
Regulatory requirements are any requirements that must be documented and followed based on laws and regulations. Standards can also be used as part of the regulatory environment but are not strictly enforced as laws and regulations. As with new business or technologies or environmental changes, organizations must ensure that they understand the regulations and their implications to the security posture of the organization.
The International Organization for Standardization (ISO) has developed a series of standards that are meant to aid organizations in the development of security policies. Other regulatory bodies include local, state, federal, and other government bodies.
Let’s look at an example. Suppose an organization is rewriting its security policies and has halted the rewriting progress because the executives believe that the organization’s major vendors have a good handle on compliance and regulatory standards. The executive-level managers are allowing vendors to play a large role in writing the organization’s policy. However, the IT director decides that while vendor support is important, it is critical that the company write the policy objectively because vendors may not always put the organization’s interests first. The IT director should make the following recommendations to senior staff:
Consult legal and regulatory requirements.
Draft a general organizational policy.
Specify functional implementation policies.
Establish necessary standards, procedures, baselines, and guidelines.
As you can see from this example, you don’t have to memorize the specific standards. However, you need to understand how organizations apply them, how they are revised, and how they can be customized to fit organizational needs.
Emerging Risks
Emerging risks are any risks that have emerged due to the recent security landscape. Often risks are not identified for new technologies, devices, and applications until after one of them has been deployed. Organizations should write policies and procedures to ensure that security professionals are doing the proper research to understand emerging risks. Emerging risks is an area that can be particularly dependent upon patch management. Often vendors will try to quickly release security fixes for any emerging risks.
Suppose an organization decides to deploy a new Internet of Things (IoT) device. Several weeks into the deployment, the vendor announces a security flaw that allows attackers to take over the device functionality. As a result, they release a security patch that addresses this issue. If the appropriate policies are in place, the organization’s security professionals should be monitoring the vendor for announcements regarding patch management and should deploy the patch once it can be properly tested.
Support Legal Compliance and Advocacy
An organization should involve its human resources department, legal department or legal counsel, senior management, and other internal and external entities in its legal compliance and advocacy program. Legal compliance ensures that an organization follows relevant laws, regulations, and business rules. Legal advocacy is the process carried out by or for an organization that aims to influence public policy and resource allocation decisions in political, economic, and social systems and institutions.
Human resources involvement ensures that the organization is addressing all employment laws and regulations to protect its employees. Human resources professionals can help guide an organization’s security policies to ensure that individual rights are upheld while at the same time protecting organizational assets and liability. For example, an organization should ensure that a screen is displayed at login that informs users of the employer’s rights to monitor, seize, and search organizational devices to reduce the likelihood of related legal issues. Then, if a technician must take an employee’s workstation into custody in response to an investigation, the organization is protected. Both the HR and legal departments should be involved in creating the statement that will be displayed to ensure that it includes all appropriate information.
Note
Applicable laws are covered in Chapter 1, “Business and Industry Influences and Associated Security Risks.” To learn about specific laws that could affect an organization, refer to the section “Legal Requirements.”
Common Business Documents to Support Security
Security professionals need to use many common business documents to support the implementation and management of organizational security. Understanding these business documents helps ensure that all areas of security risk are addressed and the appropriate policies, procedures, and processes are developed.
Risk Assessment (RA)
A risk assessment (RA) is a tool used in risk management to identify vulnerabilities and threats, assess the impacts of those vulnerabilities and threats, and determine which controls to implement. Risk assessment or analysis has four main steps:

Step 1. Identify assets and asset value.
Step 2. Identify vulnerabilities and threats.
Step 3. Calculate threat probability and business impact.
Step 4. Balance threat impact with countermeasure cost.
Prior to starting a risk assessment, management and the risk assessment team must determine which assets and threats to consider. This process involves determining the size of the project. The risk assessment team must then provide a report to management on the value of the assets considered. Next, management reviews and finalizes the asset list, adding and removing assets as it sees fit, and then determines the budget for the risk assessment project.
If a risk assessment is not supported and directed by senior management, it will not be successful. Management must define the purpose and scope of a risk assessment and allocate personnel, time, and monetary resources for the project.
Note
To learn more about risk assessment, refer to Chapter 3, “Risk Mitigation Strategies and Controls.”
The statement of applicability (SOA) identifies the controls chosen by an organization and explains how and why the controls are appropriate. The SOA is derived from the output of the risk assessment. If ISO 27001 compliance is important for an organization, its SOA must directly relate the selected controls to the original risks they are intended to mitigate.
The SOA should make reference to the policies, procedures, or other documentation or systems through which the selected control will actually manifest. It is also good practice to document why controls not selected were excluded.
Business Impact Analysis (BIA)
A business impact analysis (BIA) is a functional analysis that occurs as part of business continuity and disaster recovery. Performing a thorough BIA will help business units understand the impact of a disaster. The resulting document that is produced from a BIA lists the critical and necessary business functions, their resource dependencies, and their level of criticality to the overall organization.
Interoperability Agreement (IA)
An interoperability agreement (IA) is an agreement between two or more organizations to work together to allow information exchange. The most common implementation of these agreements occurs between sister companies that are owned by the same large corporation. While the companies may be structured and managed differently, they may share systems, telecommunications, software, and data to allow consolidation and better utilization of resources. IAs are considered binding agreements.
Do not confuse an interoperability agreement with a reciprocal agreement. Whereas an IA covers normal operations, a reciprocal agreement is an agreement between two organizations that have similar technological needs and infrastructures. In a reciprocal agreement, each organization agrees to act as an alternate location for the other if the primary facilities of either of the organizations are rendered unusable. Unfortunately, in most cases, these agreements cannot be legally enforced.
Interconnection Security Agreement (ISA)
An interconnection security agreement (ISA) is an agreement between two organizations that own and operate connected IT systems to document the technical requirements of the interconnection. In most cases, the security control needs of each organization are spelled out in detail in the agreement to ensure that there is no misunderstanding. The ISA also supports a memorandum of understanding (described next) between the organizations.
For example, if an organization has completed the connection of its network to a national high-speed network, and local businesses in the area are seeking sponsorship with the organization to connect to the high-speed network by directly connecting through the organization’s network, using an ISA would be the best way to document the technical requirements of the connection.
Memorandum of Understanding (MOU)
A memorandum of understanding (MOU) is an agreement between two or more organizations that details a common line of action. MOUs are often used in cases where parties either do not have a legal commitment or in situations where the parties cannot create a legally enforceable agreement. In some cases, it is referred to as a letter of intent.
Service-Level Agreement (SLA)
A service-level agreement (SLA) is an agreement about the ability of the support system to respond to problems within a certain time frame while providing an agreed level of service. SLAs can be internal between departments or external with a service provider. Agreeing on the quickness with which various problems are addressed introduces some predictability to the response to problems, which ultimately supports the maintenance of access to resources. Most service contracts are accompanied by an SLA, which may include security priorities, responsibilities, guarantees, and warranties.
For example, an SLA is the best choice when a new third-party vendor, such as a cloud computing provider, has been selected to maintain and manage an organization’s systems. An SLA is also a good choice when an organization needs to provide 24-hour support for certain internal services and decides to use a third-party provider for shifts for which the organization does not have internal personnel on duty.
Operating-Level Agreement (OLA)
An operating-level agreement (OLA) is an internal organizational document that details the relationships that exist between departments to support business activities. OLAs are often used with SLAs. A good example of an OLA is an agreement between the IT department and the accounting department in which the IT department agrees to be responsible for the backup services of the accounting server, while the day-to-day operations of the accounting server are maintained by accounting personnel.
Non-Disclosure Agreement (NDA)
A non-disclosure agreement (NDA) is an agreement between two parties that defines what information is considered confidential and cannot be shared outside the two parties. An organization may implement NDAs with personnel regarding the intellectual property of the organization. NDAs can also be used when two organizations work together to develop a new product. Because certain information must be shared to make the partnership successful, NDAs are signed to ensure that each partner’s data is protected.
While an NDA cannot ensure that confidential data is not shared, it usually provides details on the repercussions for the offending party, including but not limited to fines, jail time, and forfeiture of rights. For example, an organization should decide to implement an NDA when it wants to legally ensure that no sensitive information is compromised through a project with a third party or in a cloud-computing environment.
An example of an NDA in use is the one you sign when you take the CompTIA Advanced Security Practitioner exam. You must digitally sign an NDA that clearly states that you are not allowed to share any details regarding the contents of the exam except that which is expressly given in the CompTIA blueprint available on its website. Failure to comply with this NDA can result in forfeiture of your CompTIA credential and being banned from taking future CompTIA certification exams.
Business Partnership Agreement (BPA)
A business partnership agreement (BPA) is an agreement between two business partners that establishes the conditions of the partner relationship. A BPA usually includes the responsibilities of each partner, profit/loss sharing details, resource sharing details, and data sharing details.
For example, if an organization has entered into a marketing agreement with a marketing firm whereby the organization will share some of its customer information with the marketing firm, the terms should be spelled out in a BPA. The BPA should state any boundaries for the contract, such as allowing the marketing firm to only contact customers of the organization who explicitly agreed to being contacted by third parties.
BPAs should include any organizational policies that might affect the partner and its personnel. If your organization has a security policy regarding USB flash drives, any BPAs with partners that may have personnel working onsite should include the details of the USB flash drive security policy.
Master Service Agreement (MSA)
A master service agreement (MSA) is a contract between two parties in which both parties agree to most of the terms that will govern future transactions or future agreements. This agreement is ideal if an organization will have a long-term relationship with a vendor or provider. An MSA provides risk allocation strategy that outlines the risk and responsibility of contractors and employees included in the agreement for each contract’s duration. It also provides indemnification that allows one party to hold harmless or safeguard another party against existing or future losses. The indemnifying party agrees to pay for damages it has caused or may cause in the future, regardless of which party is at fault; these damages include legal fees and costs associated with litigation.
An MSA usually includes a statement of work (SOW), which outlines the specific work to be executed by the vendor for the client. It includes the work activities, the deliverables, and the time line for work to be accomplished.
Security Requirements for Contracts
Contracts with third parties are a normal part of business. Because security has become such a concern for most organizations and government entities, contracts now include sections that explicitly detail the security requirements for the vendor. Organizations should consult with legal counsel to ensure that the contracts they execute include the appropriate security requirements to satisfy not only the organizations’ needs but also any government regulations and laws.
An organization may want to consider including provisions such as the following as part of any contracts:

Required policies, practices, and procedures related to handling organizational data
Training or certification requirements for any third-party personnel
Background investigation or security clearance requirements for any third-party personnel
Required security reviews of third-party devices
Physical security requirements for any third-party personnel
Laws and regulations that will affect the contract
Security professionals should research security requirements for contracts, including RFPs, RFQs, RFIs, and other agreements.
Request for Proposal (RFP)

An RFP is a bidding-process document issued by an organization that gives details of a commodity, a service, or an asset that the organization wants to purchase. Potential suppliers use the RFP as a guideline for submitting a formal proposal.
Suppose that two members of senior management can better understand what each vendor does and what solutions they can provide after three vendors submit their requested documentation. But now the managers want to see the intricacies of how these solutions can adequately match the requirements needed by the firm. The managers should submit an RFP to the three submitting firms to obtain this information.
Request for Quote (RFQ)

An RFQ (sometimes called an invitation for bid [IFB]) is a bidding-process document that invites suppliers to bid on specific products or services. RFQs often include item or service specifications. An RFQ is suitable for sourcing products that are standardized or produced in repetitive quantities, such as desktop computers, RAM modules, or other devices.
Suppose that a security administrator of a small private firm is researching and putting together a proposal to purchase an intrusion prevention system (IPS). A specific brand and model has been selected, but the security administrator needs to gather cost information for that product. The security administrator should prepare an RFQ to perform a cost analysis report. The RFQ would include information such as payment terms.
Request for Information (RFI)

An RFI is a bidding-process document that collects written information about the capabilities of various suppliers. An RFI may be used prior to an RFP or RFQ, if needed, but can also be used after these if the RFP or RFQ does not obtain enough specification information.
Suppose that a security administrator of a large private firm is researching and putting together a proposal to purchase an IPS. The specific IPS type has not been selected, and the security administrator needs to gather information from several vendors to determine a specific product. An RFI would assist in choosing a specific brand and model.
Now let’s look at an example where the RFI comes after the RFP or RFQ. Say that three members of senior management have been working together to solicit bids for a series of firewall products for a major installation in the firm’s new office. After reviewing RFQs received from three vendors, the three managers have not gained any real data regarding the specifications about any of the solutions and want that data before the procurement continues. To get back on track in this procurement process, the managers should contact the three submitting vendor firms and have them submit supporting RFIs to provide more detailed information about their product solutions.
Agreement or Contract

Organizations use other types of agreements with third parties besides those already discussed. Even though many of these agreements are not as formal as RFPs, RFQs, or RFIs, it is still important for an organization to address any security requirements in an agreement to ensure that the third party is aware of the requirements. This includes any types of contracts an organization uses to perform business, including purchase orders, sales agreements, manufacturing agreements, and so on.
General Privacy Principles for Sensitive Information
When considering technology and its use today, privacy is a major concern of users. This privacy concern usually involves three areas: which personal information can be shared with whom, whether messages can be exchanged confidentially, and whether and how a user can send messages anonymously. Privacy is an integral part of an organization’s security measures.
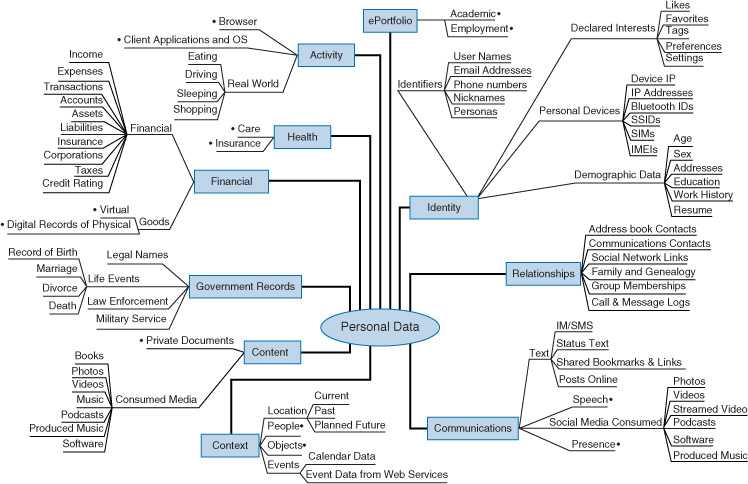
As part of the security measures that organizations must take to protect privacy, personally identifiable information (PII) must be understood, identified, and protected.
PII is any piece of data that can be used alone or with other information to identify a single person. Any PII that an organization collects must be protected in the strongest manner possible. PII includes full name, identification numbers (including driver’s license number and Social Security number), date of birth, place of birth, biometric data, financial account numbers (both bank account and credit card numbers), and digital identities (including social media names and tags).
Keep in mind that different countries and levels of government can have different qualifiers for identifying PII. Security professionals must ensure that they understand international, national, state, and local regulations and laws regarding PII. As the theft of this data becomes even more prevalent, you can expect more laws to be enacted that will affect your job.

Figure 2-1 lists examples of PII.
Support the Development of Policies Containing Standard Security Practices
Organizational policies must be implemented to support all aspects of security. Experienced security professionals should ensure that organizational security policies include separation of duties, job rotation, mandatory vacation, least privilege, incident response, forensic tasks, employment and termination procedures, continuous monitoring, training and awareness for users, and auditing requirements and frequency.
Separation of Duties
Separation of duties is a preventive administrative control to keep in mind when designing an organization’s authentication and authorization policies. Separation of duties prevents fraud by distributing tasks and their associated rights and privileges among users. This helps to deter fraud and collusion because when an organization implements adequate separation of duties, collusion between two or more personnel would be required to carry out fraud against the organization. A good example of separation duties is authorizing one person to manage backup procedures and another to manage restore procedures.
Separation of duties is associated with dual controls and split knowledge. With dual controls, two or more users are authorized and required to perform certain functions. For example, a retail establishment might require two managers to open the safe. Split knowledge ensures that no single user has all the information needed to perform a particular task. An example of split knowledge is the military’s requiring two individuals to each enter a unique combination to authorize missile firing.
Separation of duties ensures that one person is not capable of compromising organizational security. Any activities that are identified as high risk should be divided into individual tasks, which can then be allocated to different personnel or departments.
When an organization adopts a policy which specifies that the systems administrator cannot be present during a system audit, separation of duties is the guiding principle.
Let’s look at an example of the violation of separation of duties. Say that an organization’s internal audit department investigates a possible breach of security. One of the auditors interviews three employees:
A clerk who works in the accounts receivable office and is in charge of entering data into the finance system
An administrative assistant who works in the accounts payable office and is in charge of approving purchase orders
The finance department manager, who can perform the functions of both the clerk and the administrative assistant
To avoid future security breaches, the auditor should suggest that the manager should only be able to review the data and approve purchase orders.
Job Rotation
From a security perspective, job rotation refers to the detective administrative control where multiple users are trained to perform the duties of a position to help prevent fraud by any individual employee. The idea is that by making multiple people familiar with the legitimate functions of the position, the likelihood increases that unusual activities by any one person will be noticed. Job rotation is often used in conjunction with mandatory vacations. Beyond the security aspects of job rotation, additional benefits include:
Trained backup in case of emergencies
Protection against fraud
Cross-training of employees
Mandatory Vacation
With mandatory vacations, all personnel are required to take time off, allowing other personnel to fill their positions while gone. This detective administrative control enhances the opportunity to discover unusual activity.
Some of the security benefits of using mandatory vacations include having the replacement employee:
Run the same applications as the vacationing employee
Perform tasks in a different order from the vacationing employee
Perform the job from a different workstation than the vacationing employee
Replacement employees should avoid running scripts that were created by the vacationing employee. A replacement employee should either develop his or her own script or manually complete the tasks in the script.
Least Privilege
The principle of least privilege requires that a user or process be given only the minimum access privilege needed to perform a particular task. The main purpose of this principle is to ensure that users have access to only the resources they need and are authorized to perform only the tasks they need to perform. To properly implement the least privilege principle, organizations must identify all users’ jobs and restrict users to only the identified privileges.
The need-to-know principle is closely associated with the concept of least privilege. Although least privilege seeks to reduce access to a minimum, the need-to-know principle actually defines the minimums for each job or business function. Excessive privileges become a problem when a user has more rights, privileges, and permissions than needed to do his job. Excessive privileges are hard to control in large enterprise environments.
A common implementation of the least privilege and need-to-know principles is when a systems administrator is issued both an administrative-level account and a normal user account. In most day-to-day functions, the administrator should use her normal user account. When the systems administrator needs to perform administrative-level tasks, she should use the administrative-level account. If the administrator uses her administrative-level account while performing routine tasks, she risks compromising the security of the system and user accountability.

Organizational rules that support the principle of least privilege include the following:
Keep the number of administrative accounts to a minimum.
Administrators should use normal user accounts when performing routine operations.
Permissions on tools that are likely to be used by attackers should be as restrictive as possible.
To more easily support the least privilege and need-to-know principles, users should be divided into groups to facilitate the confinement of information to a single group or area. This process is referred to as compartmentalization.
The default level of access should be no access. An organization should give users access only to resources required to do their jobs, and that access should require manual implementation after the requirement is verified by a supervisor.
Discretionary access control (DAC) and role-based access control (RBAC) are examples of systems based on a user’s need to know. Ensuring least privilege requires that the user’s job be identified and each user be granted the lowest clearance required for his or her tasks. Another example is the implementation of views in a database. Need-to-know requires that the operator have the minimum knowledge of the system necessary to perform his or her task.
If an administrator reviews a recent security audit and determines that two users in finance also have access to the human resource data, this could be an example of a violation of the principle of least privilege if either of the identified users works only in the finance department. Users should only be granted access to data necessary to complete their duties. While some users may require access to data outside their department, this is not the norm and should always be fully investigated.
Incident Response
Security events are inevitable. The response to an event has a great impact on how damaging the event will be to the organization. Incident response policies should be formally designed, well communicated, and followed. They should specifically address cyber attacks against an organization’s IT systems.
Steps in the incident response system can include the following (see Figure 2-2):

Step 1. Detect: The first step is to detect the incident. All detective controls, such as auditing, discussed in Chapter 3, are designed to provide this capability. The worst sort of incident is one that goes unnoticed.
Step 2. Respond: The response to the incident should be appropriate for the type of incident. Denial-of-service (DoS) attacks against a web server would require a quicker and different response than a missing mouse in the server room. An organization should establish standard responses and response times ahead of time.
Step 3. Report: All incidents should be reported within a time frame that reflects the seriousness of the incident. In many cases, establishing a list of incident types and the person to contact when each type of incident occurs is helpful. Attention to detail at this early stage, while time-sensitive information is still available, is critical.
Step 4. Recover: Recovery involves a reaction designed to make the network or system affected functional again. Exactly what that means depends on the circumstances and the recovery measures that are available. For example, if fault-tolerance measures are in place, the recovery might consist of simply allowing one server in a cluster to fail over to another. In other cases, it could mean restoring the server from a recent backup. The main goal of this step is to make all resources available again.
Step 5. Remediate: This step involves eliminating any residual danger or damage to the network that still might exist. For example, in the case of a virus outbreak, it could mean scanning all systems to root out any additional affected machines. These measures are designed to make a more detailed mitigation when time allows.
Step 6. Review: The final step is to review each incident to discover what can be learned from it. Changes to procedures might be called for. It is important to share lessons learned with all personnel who might encounter the same type of incident again. Complete documentation and analysis are the goals of this step.
The actual investigation of an incident occurs during the respond, report, and recover steps. Following appropriate forensic and digital investigation processes during an investigation can help ensure that evidence is preserved.
Incident response is vital to every organization to ensure that any security incidents are detected, contained, and investigated. Incident response is the beginning of any investigation. After an incident has been discovered, incident response personnel perform specific tasks. During the entire incident response, the incident response team must ensure that it follows proper procedures to ensure that evidence is preserved.
As part of incident response, security professionals must understand the difference between events and incidents. The incident response team must have the appropriate incident response procedures in place to ensure that an incident is handled, but the procedures must not hinder any forensic investigations that might be needed to ensure that parties are held responsible for any illegal actions. Security professionals must understand the rules of engagement and the authorization and scope of any incident investigation.
Events Versus Incidents
In regard to incident response, a basic difference exists between events and incidents. An event is a change of state. Whereas events include both negative and positive events, incident response focuses more on negative events—events that have been deemed to negatively impact the organization. An incident is a series of events that negatively impact an organization’s operations and security. For example, an attempt to log on to the server is an event. If a system is breached because of a series of attempts to log on to the server, then an incident has occurred.
Events can be detected only if an organization has established the proper auditing and security mechanisms to monitor activity. A single negative event might occur. For example, the auditing log might show that an invalid login attempt occurred. By itself, this login attempt is not a security concern. However, if many invalid login attempts occur over a period of a few hours, the organization might be undergoing an attack. The initial invalid login is considered an event, but the series of invalid login attempts over a few hours would be an incident, especially if it is discovered that the invalid login attempts all originated from the same IP address.
Rules of Engagement, Authorization, and Scope
An organization ought to document the rules of engagement, authorization, and scope for the incident response team. The rules of engagement define which actions are acceptable and unacceptable if an incident has occurred. The authorization and scope provide the incident response team with the authority to perform an investigation and with the allowable scope of any investigation the team must undertake.
The rules of engagement act as a guideline for the incident response team to ensure that it does not cross the line from enticement into entrapment. Enticement occurs when the opportunity for illegal actions is provided (luring), but the attacker makes his own decision to perform the action. Entrapment involves encouraging someone to commit a crime that the individual might have had no intention of committing. Enticement is legal but does raise ethical arguments and might not be admissible in court. Entrapment is illegal.
Forensic Tasks
Computer investigations require different procedures than regular investigations because the time frame for the investigator is compressed, and an expert might be required to assist in the investigation. Also, computer information is intangible and often requires extra care to ensure that the data is retained in its original format. Finally, the evidence in a computer crime can be very difficult to gather.
After a decision has been made to investigate a computer crime, you should follow standardized procedures, including the following:
Identify what type of system is to be seized.
Identify the search and seizure team members.
Determine the risk of the suspect destroying evidence.
After law enforcement has been informed of a computer crime, the organization’s investigator’s constraints are increased. Turning over the investigation to law enforcement to ensure that evidence is preserved properly might be necessary.
When investigating a computer crime, evidentiary rules must be addressed. Computer evidence should prove a fact that is material to the case and must be reliable. The chain of custody must be maintained. Computer evidence is less likely to be admitted in court as evidence if the process for producing it has not been documented.

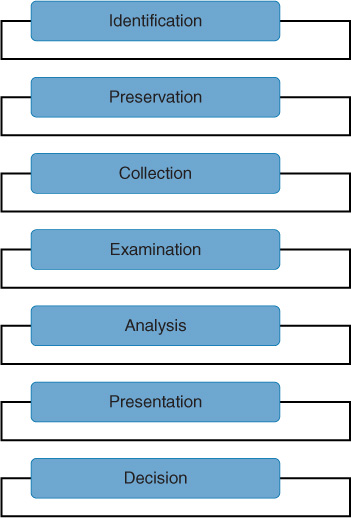
A forensic investigation involves the following steps:
Step 1. Identification
Step 2. Preservation
Step 3. Collection
Step 4. Examination
Step 5. Analysis
Step 6. Presentation
Step 7. Decision
Figure 2-3 illustrates the forensic investigation process.
Forensic investigations are discussed in more detail in Chapter 11, “Incident Response and Recovery.”
Employment and Termination Procedures
Personnel are responsible for the vast majority of security issues within an organization. For this reason, it is vital that an organization implement the appropriate personnel security policies. Organizational personnel security policies should include screening, hiring, and termination policies.
Personnel screening should occur prior to the offer of employment and might include a criminal background check, work history, background investigations, credit history, driving records, substance-abuse testing, and education and licensing verification. Screening needs should be determined based on the organization’s needs and the prospective hire’s employment level.
Personnel hiring procedures should include signing all the appropriate documents, including government-required documentation, no expectation of privacy statements, and NDAs. An organization usually has a personnel handbook and other hiring information that must be communicated to a new employee. The hiring process should include a formal verification that the employee has completed all the training. Employee IDs and passwords are then issued.
Personnel termination must be handled differently based on whether the termination is friendly or unfriendly. Procedures defined by the human resources department can ensure that organizational property is returned, user access is removed at the appropriate time, and exit interviews are completed. With unfriendly terminations, organizational procedures must be proactive to prevent damage to organizational assets. Therefore, unfriendly termination procedures should include system and facility access termination prior to employee termination notification as well as security escort from the premises.
Management must also ensure that appropriate security policies are in place during employment. Separation of duties, mandatory vacations, and job rotation are covered earlier in this chapter. Some positions might require employment agreements to protect the organization and its assets even after the employee is no longer with the organization. These agreements can include NDAs, non-compete clauses, and code of conduct and ethics agreements.
Continuous Monitoring
Before continuous monitoring can be successful, an organization must ensure that the operational baselines are captured. After all, an organization cannot recognize abnormal patterns of behavior if it does not know what “normal” is. Periodically these baselines should also be revisited to ensure that they have not changed. For example, if a single web server is upgraded to a web server farm, a new performance baseline should be captured.
Security professionals must ensure that the organization’s security posture is maintained at all times. This requires continuous monitoring. Auditing and security logs should be reviewed on a regular schedule. Performance metrics should be compared to baselines. Even simple acts such as normal user login/logout times should be monitored. If a user suddenly starts logging in and out at irregular times, the user’s supervisor should be alerted to ensure that the user is authorized. Organizations must always be diligent in monitoring the security of their enterprise.
Training and Awareness for Users
Security awareness training, security training, and security education are three terms that are often used interchangeably, but these are actually three different things. Awareness training reinforces the fact that valuable resources must be protected by implementing security measures. Security training involves teaching personnel the skills they need to perform their jobs in a secure manner. Awareness training and security training are usually combined as security awareness training, which improves user awareness of security and ensures that users can be held accountable for their actions. Security education is more independent and is targeted at security professionals who require security expertise to act as in-house experts for managing security programs. So, awareness training addresses the what, security training addresses the how, and security education addresses the why.
Security awareness training should be developed based on the audience. In addition, trainers must understand the corporate culture and how it affects security. For example, in a small customer-focused bank, bank employees may be encouraged to develop friendships with bank clientele. In this case, security awareness training must consider the risks that come with close relationships with clients.

The audiences you need to consider when designing training include high-level management, middle management, technical personnel, and other staff. For high-level management, security awareness training must provide a clear understanding of potential risks and threats, effects of security issues on organizational reputation and financial standing, and any applicable laws and regulations that pertain to the organization’s security program. Middle management training should discuss policies, standards, baselines, guidelines, and procedures, particularly how these components map to the individual departments. Also, middle management must understand their responsibilities regarding security. Technical staff should receive technical training on configuring and maintaining security controls, including how to recognize an attack when it occurs. In addition, technical staff should be encouraged to pursue industry certifications and higher education degrees. Other staff need to understand their responsibilities regarding security so that they perform their day-to-day tasks in a secure manner. With these staff, providing real-world examples to emphasize proper security procedures is effective.
Targeted security training is important to ensure that users at all levels understand their security duties within the organization. Let’s look at an example. Say that a manager is attending an all-day training session. He is overdue on entering bonus and payroll information for subordinates and feels that the best way to get the changes entered is to log into the payroll system and activate desktop sharing with a trusted subordinate. The manager grants the subordinate control of the desktop, thereby giving the subordinate full access to the payroll system. The subordinate does not have authorization to be in the payroll system. Another employee reports the incident to the security team. The most appropriate method for dealing with this issue going forward is to provide targeted security awareness training and impose termination for repeat violators.
Personnel should sign a document indicating that they have completed the training and understand all the topics. Although the initial training should occur when someone is hired, security awareness training should be considered a continuous process, with future training sessions occurring annually at a minimum.
It is important for organizations to constantly ensure that procedures are properly followed. If an organization discovers that personnel are not following proper procedures of any kind, the organization should review the procedures to ensure that they are correct. Then the personnel should be given the appropriate training so that the proper procedures are followed.
For example, if there has been a recent security breach leading to the release of sensitive customer information, the organization must ensure that staff are trained appropriately to improve security and reduce the risk of disclosing customer data. In this case, the primary focus of the privacy compliance training program should be to explain to personnel how customer data is gathered, used, disclosed, and managed.
It is also important that security audits be performed periodically. For example, say that an organization’s security audit has uncovered a lack of security controls with respect to employees’ account management. Specifically, the audit reveals that accounts are not disabled in a timely manner after an employee departs the organization. The company policy states that an employee’s account should be disabled within eight hours of termination. However, the audit shows that 10% of the accounts were not disabled until seven days after a dismissed employee departed. Furthermore, 5% of the accounts are still active. Security professionals should review the termination policy with the organization’s managers to ensure prompt reporting of employee terminations. It may be necessary to establish a formal procedure for reporting terminations to ensure that accounts are disabled when appropriate.
Auditing Requirements and Frequency
Auditing and reporting ensure that users are held accountable for their actions, but an auditing mechanism can only report on events that it is configured to monitor. Organizations must find a balance between auditing important events and activities and ensuring that device performance is maintained at an acceptable level. Also, organizations must ensure that any monitoring that occurs is in compliance with all applicable laws.

Audit trails detect computer penetrations and reveal actions that identify misuse. As a security professional, you should use audit trails to review patterns of access to individual objects. To identify abnormal patterns of behavior, you should first identify normal patterns of behavior. Also, you should establish the clipping level, which is a baseline of user errors above which violations will be recorded. A common clipping level that is used is three failed login attempts. Any failed login attempt above the limit of three would be considered malicious. In most cases, a lockout policy would lock out a user’s account after this clipping level was reached.
Information Classification and Life Cycle
Data should be classified based on its value to the organization and its sensitivity to disclosure. As mentioned earlier in this chapter, assigning a value to data allows an organization to determine the resources that should be used to protect the data. Resources that are used to protect data include personnel resources, monetary resources, and access control resources. Classifying data as it relates to confidentiality, integrity, and availability (CIA) allows you to apply different protective measures.
After data is classified, the data can be segmented based on the level of protection it needs. The classification levels ensure that data is handled and protected in the most cost-effective manner possible. An organization should determine the classification levels it uses based on the needs of the organization. A number of commercial business and military and government information classifications are commonly used.
The information life cycle should also be based on the classification of the data. Organizations are required to retain certain information, particularly financial data, based on local, state, or government laws and regulations.
Commercial Business Classifications

Commercial businesses usually classify data using four main classification levels, listed here from the highest sensitivity level to the lowest:
Confidential
Private
Sensitive
Public
Data that is confidential includes trade secrets, intellectual data, application programming code, and other data that could seriously affect the organization if unauthorized disclosure occurred. Data at this level would be available only to personnel in the organization whose work relates to the data’s subject. Access to confidential data usually requires authorization for each access. Confidential data is exempt from disclosure under the Freedom of Information Act. In most cases, the only way for external entities to have authorized access to confidential data is as follows:
After signing a confidentiality agreement
When complying with a court order
As part of a government project or contract procurement agreement
Data that is private includes any information related to personnel—including human resources records, medical records, and salary information—that is used only within the organization. Data that is sensitive includes organizational financial information and requires extra measures to ensure its CIA and accuracy. Public data is data that would not cause a negative impact on the organization.
Military and Government Classifications

Military and government entities usually classify data using five main classification levels, listed here from the highest sensitivity level to the lowest:
Top secret
Secret
Confidential
Sensitive but unclassified
Unclassified
Data that is top secret includes weapons blueprints, technology specifications, spy satellite information, and other military information that could gravely damage national security if disclosed. Data that is secret includes deployment plans, missile placement, and other information that could seriously damage national security if disclosed. Data that is confidential includes patents, trade secrets, and other information that could seriously affect the government if unauthorized disclosure occurred. Data that is sensitive but unclassified includes medical or other personal data that might not cause serious damage to national security but could cause citizens to question the reputation of the government. Military and government information that does not fall into any of the other four categories is considered unclassified and usually has to be granted to the public based on the Freedom of Information Act.
Information Life Cycle
All organizations need procedures in place for the retention and destruction of data. Data retention and destruction must follow all local, state, and government regulations and laws. Documenting proper procedures ensures that information is maintained for the required time to prevent financial fines and possible incarceration of high-level organizational officers. These procedures must include both the retention period, including longer retention periods for legal holds, and the destruction process.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple choices for exam preparation: the exercises here and the practice exams in the Pearson IT Certification test engine.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 2-1 lists these key topics and the page number on which each is found.

Table 2-1 Key Topics for Chapter 2
Key Topic Element |
Description |
Page Number |
List |
Policy life cycle |
66 |
List |
Process life cycle |
66 |
Paragraph |
Risk assessment description and steps |
71 |
List |
Contract security provisions |
75 |
Paragraph |
RFP |
76 |
Paragraph |
RFQ |
76 |
Paragraph |
RFI |
76 |
Paragraph |
Agreements |
77 |
Different types of PII |
78 |
|
List |
Least privilege rules |
81 |
List |
Incident response steps |
81 |
List |
Forensic investigation steps |
84 |
Paragraph |
Security awareness training audiences |
87 |
Paragraph |
Auditing guidelines |
88 |
List |
Commercial business classifications |
89 |
List |
Military and government classifications |
90 |
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
business impact analysis (BIA)
business partnership agreement (BPA)
interconnection security agreement (ISA)
interoperability agreement (IA)
master service agreement (MSA)
memorandum of understanding (MOU)
non-disclosure agreement (NDA)
operating-level agreement (OLA)
personally identifiable information (PII)
statement of applicability (SOA)
Review Questions
1. Your organization has recently been the victim of fraud perpetrated by a single employee. After a thorough analysis has been completed of the event, security experts recommend that security controls be established to require multiple employees to complete a task. Which control should you implement, based on the expert recommendations?
mandatory vacation
separation of duties
least privilege
continuous monitoring
2. Your company has recently decided to switch Internet service providers. The new provider has provided a document that lists all the guaranteed performance levels of the new connection. Which document contains this information?
SLA
ISA
MOU
IA
3. Your organization has signed a new contract to provide database services to another company. The partner company has requested that the appropriate privacy protections be in place within your organization. Which document should be used to ensure data privacy?
ISA
IA
NDA
PII
4. Your organization has recently undergone major restructuring. During this time, a new chief security officer (CSO) was hired. He has asked you to make recommendations for the implementation of organizational security policies. Which of the following should you not recommend?
All personnel are required to use their vacation time.
All personnel should be cross-trained and should rotate to multiple positions throughout the year.
All high-level transactions should require a minimum of two personnel to complete.
The principle of least privilege should be implemented only for all high-level positions.
5. What is the primary concern of PII?
availability
confidentiality
integrity
authentication
6. Which of the following is an example of an incident?
an invalid user account’s login attempt
account lockout for a single user account
several invalid password attempts for multiple users
a user attempting to access a folder to which he does not have access
7. What is the first step of a risk assessment?
Balance threat impact with countermeasure cost.
Calculate threat probability and business impact.
Identify vulnerabilities and threats.
Identify assets and asset value.
8. During a recent security audit, your organization provided the auditor with an SOA. What was the purpose of this document?
to identify the controls chosen by an organization and explain how and why the controls are appropriate
to document the performance levels that are guaranteed
to document risks
to prevent the disclosure of confidential information
9. Which document requires that a vendor reply with a formal bid proposal?
RFI
RFP
RFQ
agreement
10. Your company has decided to deploy network access control (NAC) on the enterprise to ensure that all devices comply with corporate security policies. Which of the following should be done first?
Develop the process for NAC.
Develop the procedures for NAC.
Develop the policy for NAC.
Implement NAC.