Chapter 6
Reducing Risk and Exceeding Compliance
All I want is compliance with my wishes, after reasonable discussion.
—Winston Churchill
This chapter focuses on various forms of compliance. Compliance by definition is to meet governing regulatory or contractual requirements. Requirements can come from an organization’s leadership, such as a corporate-mandated policy, which would be considered a policy based on corporate compliance. Another possible requirement is meeting a legal obligation, which would be government-based regulatory or statutory compliance. Lastly, a compliance requirement can be industry compliance, meaning leadership sets the goal to meet a general recommendation. Not being compliant with a government-required policy will lead to fines and potentially jailtime. Not being compliant with industry recommendations will lead to gaps in security practices. Gaps will become failures in security. This is why many organizations include industry-recommended guidelines and government-required policies within their mandated corporate policy. Enforcing good security practices leads to a reduction of risk.
Note
Compliance is not security. Security is the practice of implementing effective technical controls to protect assets, while compliance is focused only on meeting governing, regulatory, or contractual requirements. Anything outside of those requirements is not considered, which is why SOCs need to look beyond compliance when setting their baseline for security standards—and is why this chapter’s title states “Exceeding Compliance.” To exceed compliance, your security baseline must focus on being secure!
Chapter 1, “Introducing Security Operations and the SOC,” emphasized that security best practices are made up of the right combination of people, process, and technology. An example of a people-focused best practice would be found within industry certification programs, such as the CISSP teaching proper security practices. An example of a process-oriented best practice resource would be a guideline such as those released by NIST. An example of a technical-focused resource would be Common Criteria, an international standard for computer security certification. When I consult with customers, I typically find that they have security technology in place as well as people with responsibility over that technology, meaning the customers have some level of people and technology. A common area of weakness in many organizations is a lack of processes or very weak processes made up of dated procedures or policies. Without up-to-date policies and procedures, situations develop where security events are captured by existing technology, but procedures are not followed regarding proper use of technology, causing events to be overlooked. Outdated policies and procedures cause vulnerabilities in an organization’s security practice and become the weakest link leading to exploitation.
This chapter describes how to develop and maintain strong policies and procedures and introduces industry recommendations for policies and procedures found in standards, frameworks, and guidelines. Policies and procedures are requirements developed and enforced internally by an organization. Standards, frameworks, and guidelines are not required by law to be followed and usually are referenced externally by organization leadership, such as an industry best practice for a topic, but can be a best practice developed in-house as well. Many organizations use standards, frameworks, and guidelines as templates for creating policies and procedures, which I’ll cover how to do in this chapter. The successful use of policies and procedures will depend on your organization’s business objectives, what is required by local and federal government agencies, and what threats could impact the business. This chapter also covers common required compliance based on government or service requirements.
Why Exceeding Compliance
I use the term “Exceeding Compliance” in the title of this chapter even though compliance can only be met or not met. My intent for this chapter is to cover how to develop strong policies and procedures using industry standards, frameworks, and guidelines to establish part of a strong baseline for security. The remaining parts of your security baseline will be addressed using security-focused services such as tabletop exercises, assessments, and penetration testing, which are also topics that I will cover. The combination of building compliance and security-focused capabilities within your security practice will dramatically reduce the risk of future exploitation of your people, process, and technology as far as the entity enforcing compliance is concerned.
Note
Many organizations can operate while not compliant with internal policies or external laws or regulations as long as they have a plan to eventually become compliant. Sometimes the allowed time to remediate is months or even years!
Policies
Policies are high-level mandatory rules that an organization sets in place. Think of a policy as the objective for a security goal. Common language for a policy is using a term such as “Acceptable Use” meaning what actions are and are not accepted. Because a policy is an objective, it is developed with the intent to not change often. Any specific details should be left out, such as naming a specific technology or person or specifying how tasks are performed, because they can change as the organization evolves over time. Details for a policy are ideal for being developed into procedures, as covered later in this chapter.
An example policy statement is “Only employee-issued devices will be used within the employee network.” In this example, the vision is stated; however, details such as how this policy is enforced are left out. This policy can survive changes in people, process, and technology because it’s a goal lacking specific details. Another example is “All employees must use multifactor authentication to access the corporate network.” Again, the details are left out regarding which authentication factors are eligible, which technologies are to be used, and how this policy will be enforced, all of which are details better addressed in procedures.
Note
SANs provides an excellent resource for different policy templates at https://www.sans.org/security-resources/policies.
Let’s break down how to properly construct a policy by looking at an example. The different parts of this policy example will also be similar to what is included in developing other formal documents such as standards and procedures. None of these steps are required, but including them in your policy documentation is highly recommended and encouraged. Some sections are not needed if the details they cover are found in other sections. I, however, recommended using dedicated concept sections (more commonly called indexing) to simplify finding the location of each topic covered in a policy. This allows a reader to quickly identify areas of interest in the policy, which is particularly important when introducing new policies with major impact that will cause concern for employees. Employees will need a way to reference the policy and better understand how it impacts them or they will not accept the change. I will talk more about this concept when I address tasks that must be completed as you deploy new policies or make changes to existing policies.
Policy Overview
A policy starts with an overview. An overview can explain the history of the policy or situation prior to the policy being established, the scope of the policy—how and to whom or what it applies, when the policy applies, the intended audience that is expected to review the policy, and prerequisites or other details needed to comprehend the policy’s meaning. Some of these items can be omitted if other sections of the policy cover the topic, such as a section dedicated to describing the history of the document. However, a concept may be stated more than once in a policy—the overview may include items that are repeated later in the policy because the overview is intended to be an introduction to the policy topic, which might require the reader to understand certain details before proceeding to any other topics within the policy. There is a lot of flexibility for developing an overview, but keep in mind that as the first part of the policy, the overview sets the tone for the rest of the document. Also keep in mind that the overview may be the only part of the policy that some people review.
Policy Overview Example
The following is a sample policy overview.
Overview
<COMPANY or SECURITY TEAM>’s intentions for publishing <POLICY> are not to impose restrictions that are contrary to <COMPANY>’s established culture of openness, trust, and integrity. <COMPANY or SECURITY TEAM> is committed to protecting employees, partners, and <COMPANY> from illegal or damaging actions by individuals, either knowingly or unknowingly.
Internet/Intranet/Extranet-related systems, including but not limited to computer equipment, mobile devices, software, operating systems, storage media, network accounts providing electronic mail, usage of WWW, and file transfer, are the property of <COMPANY. These systems are to be used for business purposes in serving the interests of the company and customers in the course of normal operations. Please review Human Resources policies for further details.
Effective security is a team effort involving the participation and support of every <COMPANY employee and affiliate who deals with information and/or information systems. It is the responsibility of every <COMPANY user to know these guidelines, and to conduct their activities accordingly.
The first part of this example policy overview highlights the intent of the policy. In this case, the policy is designed to protect employees, partners, and the company from illegal or damaging actions. The first part of this overview also emphasizes the security team has not designed this policy to impact the culture of the organization. These two points establish a baseline for the thought process during the development of this policy.
The second part of this policy overview defines the scope related to various types of technology and usage of technology. Rather than explaining the details of each technology, this section refers to another human resources policy for additional details regarding what is defined as “business purpose in serving the interest of the company and customers.” It is common practice to cross reference other policies in this manner.
The final part of this policy overview explains not only who is required to follow the policy but also how following this policy impacts every individual at this organization. The policy requires all users to understand guidelines associated with the impacted systems of this policy. Rather than referring to another policy, this last statement refers to guidelines, which are different than a policy and contain more details. Referring to industry guidelines is also common practice, as is referencing other more detailed sources such as procedures. For example, a policy could require two-factor authentication and reference a procedure that provides details on how the policy should be executed in terms of which technologies, people, and steps should be taken to meet the policy requirements.
Other overview items that could have been included in this example policy are statements about the creation or revisions of the policy, who was involved with creating it, who is sponsoring this policy, who to contact with questions, and other items that help the reader better understand the policy as they review the other sections that follow the policy overview. For this example policy, you will find many of the statements that were left out of the overview are addressed in other sections of the policy.
Policy Purpose
The purpose of a policy explains why the policy exists. Sometimes, a policy exists to meet a mandatory requirement. Some examples could be a policy enforcing HIPAA requirements to protect user privacy, meeting business goals such as reducing operational costs, or even meeting another policy requirement. Other times a policy’s purpose is to reduce risk, meaning that conforming to the policy will reduce the chance of some unwanted action(s) from occurring. An example is banning the use of USB drives in order to prevent the release of confidential data of the company, its partners, and customers. The policy purpose is critical because it answers questions regarding why this policy must be met.
Policy Purpose Example
The following statement is an example of a policy purpose.
Purpose
The purpose of this policy is to outline the acceptable usage of <SOMETHING> at <COMPANY>. These rules have been established to protect the employee, customers, and <COMPANY>. Inappropriate use exposes <COMPANY> to risks including cyberattacks, malware, and compromise of systems and services, any of which can result in legal issues.
This example purpose explains that the reason for this policy is to protect users, the customer, and company from various types of threats. A different tactic could take the approach of meeting a compliance requirement, which would also result in similar goals of risk reduction. For example, the purpose could state the intent is to be compliant with a guideline such as the Center for Internet Security (CIS) Top 20 Critical Security Controls. The purpose of the CIS Top 20 Critical Security Controls is protecting systems from cyberthreats, which has the same purpose as protecting users from various types of threats as stated in this policy purpose example. Specifying a purpose or referencing another source such as a guideline that has the same purpose are both common practices for language included within a policy’s purpose section.
Policy Scope
A policy’s scope defines what is and what is not included in coverage of the policy. The scope can include types of people, technology, and behavior as well as what is associated with each of these items. An example is listing employees and those that interact with employees. For this example scope statement, coverage would not include guests unless the guests have interacted with an employee but it would include employees and contractors. A scope should be developed in a whitelist format, meaning the policy must specify only what is covered and assume anything else is not covered. Using a blacklist approach such as “all nonemployee assets” would not be recommended because a nonemployee asset could be almost anything. It is better to specify more specific categories whenever possible, such as “nonemployee mobile devices, tablets, or IT equipment.”
Policy Scope Example
The following is an example policy scope.
Scope
This policy applies to employees, contractors, consultants, guests, and other users within <COMPANY>, including all personnel affiliated with third parties. This policy applies to all equipment used by such people that is owned or leased by <COMPANY>.
Policy Statement
The policy statement is where the details (the meat and potatoes) of the policy are explained. Policy statements are written in a high-level format and can reference other sources, such as procedures, as a way to explain what is required to properly meet the goals of the policy. A policy can state multiple items and group content based on similar concepts. For example, all topics that cover protecting information could fall under a section titled “Security and Proprietary Information.” Grouping concepts within a policy works well; however, recommended practice dictates that you split up a policy into more-focused policies if too many categories are needed to properly cover the policy concept.
Policy Statement Example
An example policy for “Security and Proprietary Information” follows. This example shows only one group within the policy, with sections 1.1.0–1.1.4. If the policy has other groups, they could be presented as sections 1.2.0–1.2X, 1.3.0–1.3.X, and so forth.
Policy: Security and Proprietary Information
1.1.0. All computing devices that connect to the <COMPANY> managed internal network must comply with <COMPANY> access policy.
1.1.1. System-level and user passwords must comply with <COMPANY> password policy. Providing access to passwords to another individual is prohibited.
1.1.2. All computing systems must be secured using a password-protected screensaver with automatic activation feature set to 5 minutes or less.
1.1.3. Any postings by employees of <COMPANY> to external or internal media must contain a disclaimer stating the opinions expressed are strictly their own and do not represent <COMPANY>, unless otherwise permitted to do so on behalf of <COMPANY>.
1.1.4. Employees must use caution when opening email attachments from unknown senders.
This policy example has one topic group focused on information security, which could by itself be the complete policy or could be a topic group within a larger policy. Notice that none of the parts of this policy provide details on how a requirement is met. Also, notice that none of these statements would likely need to be modified as the organization changes, because the concepts are broad enough to adapt to change. Lastly, notice that consequences for not meeting this policy are not listed in this section. Consequences come in the next section, policy compliance.
Unlike the preceding policy statement example, which covers what is permitted, a policy statement can also be written regarding actions that are not authorized. For example, a policy for “unacceptable usage of company assets” would state various activities that are a violation of the company policy. Part of a policy covering unwanted behavior could state that no employee is ever permitted to engage in illegal activities. The options for what can exist in a policy are endless and should be based on a specific overall objective that is backed by leadership.
Policy statements can be very broad or very specific. Broad policies are ideal to give guidance and accommodate many different possible situations, while a specific policy is more direct, but anything outside of the specific defined criteria would not be a violation. I recommend layering both types so that when a specific policy doesn’t catch a violation, a broader policy is put in place to step in. For example, a specific policy could state “Users are required to change their passwords every 180 days.” A broad policy could state “It is the policy of this organization to secure credential information for all assets from unauthorized use or disclosure.” The specific policy requires users to take a specific action to reduce the risk of password compromise, but it doesn’t cover all actions users must or must not take to secure passwords. For example, if a user shares their password with an outside party, that would not be a violation of the specific policy example, but it would violate the broad policy that covers anything that endangers the security of credential information, including the action of sharing a password. Prohibiting the sharing of passwords would likely be covered in separate specific policy, but if the policy writers overlook including that provision, the broad policy a covers the void.
Note
I recommend reviewing policy statements with a legal professional to ensure that they don’t include any language that could be construed as illegal in the country in which your organization operates. Certain policy restrictions or requirements that are intended to secure your organization might also be considered, for example, a violation of employee privacy rights.
Policy Compliance
The policy compliance section states how the policy will be validated, what are the potential exceptions to the policy and the possible outcomes if someone fails to comply with the policy. This section is important not only to explain the validation process of a policy, but also to identify who is responsible for validating compliance and where to seek requests for exceptions. Will the InfoSec team enforce validation of the policy using detection tools, monitoring techniques, etc., or is it up to the user? Will a specific group have the authority to grant an exception to the policy? This section should answer these questions, though it shouldn’t specify individuals who are enforcing the policy or how to contact them. Those details can change often and thus should be included in a procedure that can be referenced by the policy. An example resource could be “IT Security” or “The Security Operations Center,” which both are generic enough to accommodate change within those groups. If a specific contact must be included, it is best to use a generic contact method, such as [email protected], that is tied to the current team within the IT security team.
Policy compliance must also state what will occur if the policy is not met. An example of good use of language for noncompliant behavior could be “Any employee found to have violated this policy may be subject to disciplinary action, up to and including termination of employment.” This example provides the opportunity for the policy violator’s manager and/or human resources to determine the specific outcome if a policy is not met.
Related Standards, Policies, Guidelines, and Processes
This section is ideal for referencing other sources related to the policy. Sources can include other policies that align with this policy’s goals, sources that are referenced within this policy such as another larger policy, related procedures that would define in more detail what would be required to enforce this policy, related disciplinary and legal details, or anything else that would make sense to associate with this policy.
Definitions and Terms
For the definitions and terms section, include any definitions and references that will help the reader understand the policy. For example, if the topic of phishing is covered within the policy, a reference to the definition of phishing should be included in this section, not only to explain what phishing is, but also to explain how the term is used within this policy. Some concepts can be interpreted in different ways, and this section can help clarify which definition is being referenced. For example, if the policy covers a denial-of-service (DoS) concept, it might be appropriate to explain in this section if the denial-of-service example leverages a large volume of systems (known as a volumetric DoS attack) or exploits a vulnerability within a protocol to cause the system to become unavailable, which is a different type of DoS attack. Best practice is to consider the audience of a policy and include definitions for any terms that a reader might be unfamiliar with or terms that would need more clarity to understand how they are being used. A reference symbol such as * could be placed next to any term in the policy that the reader could seek out in this section for more clarification.
History
This section lists when the document was created and when any updates have been made. It is ideal to include the date of the change, who made the change, and a summary of the change. All three of these pieces of information are important to help validate how often changes are made and who to question about any changes. Recommended practice dictates changing the version of the policy and tracking version updates within this section, including the changes that were made to the new version.
Note
I recommend seeking templates and consulting when developing policies rather than developing policy details from scratch. Using trusted references not only provides external checks and balances to what is being enforced but also reduces the likelihood of developing ineffective processes that will not be well accepted by the impacted parties. I also recommend crossreferencing sources if they are available, such as “see <Guideline> for details” or “in compliance with <Guideline>,” regarding the purpose of the statement being made.
Launching a New Policy
The previous eight sections covered a practical layout for developing a policy. The specific sections that you include in any particular policy will depend on the type of policy and the intended audience. Regardless of the chosen format, it is critical that all policies are backed by leadership to ensure they are properly supported and enforced. Leadership that sponsors a policy is ideally part of the C-level team, meaning the CEO, CSO, or another position that has enough authority to provide required support to properly execute the policy as well as enforce any disciplinary actions that occur if the policy is not followed. Support can include budget for people, process, and technology.
Prior to launching a new policy, make sure to identify prerequisites to sustain the new policy, such as budget, to avoid a situation where expected results are unattainable. For example, if a policy requires multifactor authentication for physical access to doors but the existing doors do not have a method to provide multifactor authentication, that would be an obvious policy failure that will continue to be a failure until budget and resources are made available to acquire and deliver authentication technology for each physical door. It is common for policies to be launched with the expectation that the current state of the organization does not meet the requirements; however, provide a set time to correct the missing policy elements before any violation is considered. I have seen many requests for proposals from customers based on policies they are being asked to enforce before a specific date such as the end of the year.
Steps for Launching a New Policy
Launching a new policy should include the following three general steps to inform the organization about the changes associated with the new policy:
Distribute the policy. For a policy to be legally enforceable in relation to employees, the employer must bring it to the attention of all employees. Each employee that is impacted by the policy should be provided a copy of the policy, either in electronic form, hard copy, or both. Employees need to have easy access to any policy that impacts them, again either electronically, such as an intranet resource, or in hard copy, such as in a department policy manual.
Obtain acknowledgment of receipt. It is important to have each impacted employee sign and date an acknowledgment stating they received, read, and understood the policy and were afforded an opportunity to ask questions about it. File a copy of the acknowledgment in the employee’s personnel file in the event you require it at a future date. There will always be a handful of employees who don’t (or won’t) sign such acknowledgments; in those cases, two management members can themselves sign an acknowledgment stating that they gave “the person” a copy of the policy but “the person” refused to sign the acknowledgment.
Provide advance notice. If the new or changed policy significantly affects or changes any employment rights or benefits, such as vacation rights, you need to give employees advance notice of the policy implementation and a grace period for the change to take effect. Otherwise, the change can amount to “constructive dismissal.” Constructive dismissal occurs when the employer unilaterally changes a fundamental term(s) or condition(s) of employment, effectively breaching the employment contract. The employee can either accept the change, essentially agreeing to the new contract, or refuse to accept the change, accept the employer’s termination of the contract, and sue the employer for wrongful dismissal. Just what amounts to a fundamental change and the length of the required advance notice depends on the circumstances. In general, however, the more significant the change, or the longer the employee’s service, the longer the advance notice of the change that’s required.
How each of these three actions is carried out will depend on the impact the policy has on the associated parties. Minor policy changes or new policies with minor impact require far less advanced notice than a major policy change or a new policy with major impact. I find it common for the distribution of electronic or physical documentation for minor policy changes or new policies with minor impact to occur during an annual policy reminder session, training, or notification that includes the combination of various minor changes, rather than bothering employees with documentation for every minor policy change or new policy with minor impact. Acknowledgment of receipt can be a required action item following the policy reminder session, training, or notification, allowing for the acceptance of all policy changes at once as well as any new policies.
Policy Enforcement
Another important policy concept is that a policy must be monitored to validate that the policy is being followed; otherwise, policy violations will go unnoticed. I remember working for a government agency that had a policy stating, “All contractor laptops must be scanned before accessing the network.” That policy was displayed on physical signs around the office; however, it was up to the contractor or sponsor of the contractor to notify security that a contractor’s device needed to be scanned. This poor practice led to many contractor laptops connecting to the network without being scanned because the organization loosely monitored and enforced the policy. I also don’t recall if any repercussion existed if a contractor was caught not having their laptop scanned outside of it being considered “frowned upon,” which further drove the behavior to ignore this policy. This example shows why it is highly recommended to include in your policy template a policy compliance section that states who is responsible for monitoring and enforcing the policy as well as the consequences of a failure to comply with the policy.
Although a policy compliance section states how the policy will be validated, this doesn’t solve the problem of ensuring the policy is being enforced once it goes live. Who is responsible for looking for violations? When a violation is identified, who makes the determination that the action is or is not a clear violation of the policy? Looking back at my example of a broad policy, “It is the policy of this organization to secure credential information for all assets from unauthorized use or disclosure,” I gave the example of an employee sharing his or her password as a violation. Suppose the employee gave the password to a contractor who was authorized to access the system on the date of the alleged policy violation. The employee could argue that providing the password to the contractor on that day was authorized and therefore no policy violation occurred. The employer could argue that it is a violation because the contractor continues to know the password after the date the contractor was authorized to access the system. If there isn’t another policy that requires contractors to be provided a temporary password, it is possible an employee would share a password while a contractor is authorized and technically would not be violating the policy. Which argument is correct? It depends on how your organization enforces policies.
Enforcing a policy starts with enabling the people responsible for validating a policy with the proper authority and training. These people are typically the managers and supervisors who manage the affected employees, but can also be a third-party validator. Training needs to include how to handle violations. When a violation occurs, the appropriate disciplinary penalty needs to be imposed consistently and warnings of consequences need to be provided regarding future violations.
Policy violations need to be tracked. Chapter 8, “Threat Hunting and Incident Response,” covers case management concepts. Case management also applies to tracking policy violations. The goal is to document when a violation occurs to gain an understanding of how successful the policy is, validate if changes need to be made due to excessive violations, and track parties involved for possible disciplinary actions. If tracking shows a number of requested exceptions for a policy, the risk management team will need to adjust the policy based on the recorded feedback. If an employee is found to have a history of policy violations, action will need to be taken to reduce future violations. All of these outcomes require a tracking system to document and adapt to policy violations.
Another, more formal approach to enforcing and adapting policies is to use an official certification and accreditation program.
Certification and Accreditation
A formal way to enforce policies is through a certification and accreditation process. The certifier is the party responsible for assessing if policy elements are being met. This practice is common for meeting formal certification programs such as PCI DSS (discussed later in the chapter), but can also be part of the process to enforce organization-driven policies. For certification programs, organizations will use a third-party certifier to validate that the processes, systems, products, events, or skills meet some existing standard. For general polices, an organization can authorize one or more people within the organization to certify if a policy is or is not met. This team is typically part of the compliance team.
Accreditation means a formal declaration by the certifier that what the certifier was reviewing meets all requirements. If an organization is looking to meet a formal certification program, once the organization passes all checks by the certifier, the organization can be accredited as being compliant. The entity that declares accreditation not only is confirming that the organization has met all requirements, but also is owning all responsibilities for everything that it has accredited. If a violation is found post accreditation, the accreditor might be liable, depending on the situation. The same concept applies to an accreditation given by the compliance team within an organization.
Regarding general policies, somebody with authority needs to be able to declare an accreditation when polices are met. For example, if there are minimal security requirements that must be put in place before a server is allowed to connect to the network, somebody needs to know how to validate that those security controls are in place, representing the certifier, and somebody needs to formally approve the system is ready to go live, representing the accreditor. Without these two processes, polices will not be enforced because no one will know how to validate against a policy and no one will be concerned about breaking a policy because no formal validation is put in place.
Note
One extremely important value obtained from using a certification and accreditation program is that it addresses risk. Security policies are designed to reduce the risk of threats. If a certifier finds that a policy is not being followed, the certifier can identify why and recommend controls that would enforce policy compliance. Even though compliance doesn’t take into consideration all risks, enforcing certification and accreditation of your policies will accommodate all risks associated with any policies being validated.
When it comes to the success of a policy, determining how the policy is executed by the organization is critical. Procedures fill in the missing details for policies. This brings us to the topic of procedures.
Procedures
Procedures are the details that support what a policy is designed to accomplish. Procedures are more specific than policies and will change as people, process, and technology adapt to changes within the business. Think of procedures as the step-by-step requirements to accomplish a policy. Looking back at the previous policy scenarios, an example procedure to match the policy “Employees are permitted to use only company-issued devices on the company network” would explain the details of what is considered an employee-issued device. For this example, let’s say an employee-issued device is only one that is provided by the employer and running approved software. The procedure document would define this as well as explain how validation of an employee-issued device could be achieved either by verifying a hidden certificate or by adding the MAC address of the device to a whitelist that includes the MAC addresses of all corporate-issued assets. The procedure document would also need to explain details such as how acceptable devices are distributed, how they are validated as they connect to and are used within the network, who should receive requests for exceptions, and what will occur if a violation is identified. Notice that many of the details in this example procedure document will likely change, making the maintenance process of the procedure documentation just as critical as its original creation. Changes to procedures should be captured in updated versions of the associated procedures, while the policy being supported should remain untouched. I find that when an organization has failures in processes, the cause typically is not how the documents were created but rather a failure in documentation maintenance and training.
Procedure Document
The format of a procedure document can vary as long as the required steps are included to properly execute all required tasks. Topics included in a procedure document should cover the purpose of the procedure, what is required to perform the desired tasks, when tasks should be performed, who is responsible for the tasks, and any other required steps that must be performed to properly execute the procedure. Let’s look at an example procedure document for registering a website.
Procedure for Website Registrar at <COMPANY>:
The website register must record the following information and provide the results to [email protected] within 30 days of launching a new website. A notification from the service provider will be provided regarding the status of the request to the email provided.
List of all domain names that are registered
The renewal dates for each domain name
Names of all hosting services
Any services that expire with expiration dates
Associated costs and the responsible department
Name and job title of the requestor
Email of the requestor
Purpose of the website
It is the responsibility of the registration requestor for all maintenance of the registered website. Network services at <COMPANY> shall provide notification of the expiration date of the website registration to the requestor 90 days prior to the expiration, after which it is the responsibility of the requestor to renew the website prior to the expiration date. Any expired websites must have the owners submit a new request for website registry.
This example procedure document lists the specific details regarding what is required to register a website within the company. All details are required to be sent to [email protected], which will respond with status updates as the request is being processed. Responsibilities for both the requestor and organization are listed, including expectations for notification of the website expiring as well as who should renew the website. The steps provided in this document are clear enough that any employee who wants to register a website within the organization can follow the procedure to properly submit a request. Other procedure sections would likely be included with this example procedure section, including a section covering procedures for deploying content on the website, securing the website, and performing other website-related tasks. These topics could all be grouped under one large procedure document for deploying websites at the company, or each topic could be a separate procedure document that references other documents as users need to request, stand up, and maintain a website at the company. Also, all of these procedures could fall under one or more policies, such as a policy for “deploying websites at <COMPANY>.”
One theme I have continued to emphasize is that there isn’t a set rule for developing policies and procedures. While this flexibility is great for accommodating creativity and the many dynamics found within an organization, having an open-ended format for building process documentation can cause confusion when an organization attempts to build and validate well-thought-out policies and procedures. I find that many organizations don’t know how to validate their new or existing policies and procedures or identify gaps and are therefore unsure if their policies and procedures are effective. One recommended approach to testing an organization’s policies and procedures is to perform a tabletop exercise. In the next section I will walk you through developing and executing a successful tabletop exercise. This will allow you to validate and improve your processes.
Tabletop Exercise
A tabletop exercise is a hypothetical scenario–based walkthrough of how an organization would respond to a security incident. The purpose of a tabletop exercise is to test the people, process, and technology conceptually without having these resources perform the actual response. Other services such as penetration testing are ideal when real-world testing of a policy is desired.
An example of a tabletop exercise is one that tests how an organization would respond to a ransomware pandemic. Ransomware doesn’t just appear on an endpoint, meaning a tabletop exercise would consider all aspects of this situation from response to recovery. For this scenario, the following are sample questions that the team performing the tabletop exercise could be asked:
Who is responsible for receiving the notification from the end user that malware has been identified on the user’s system?
What endpoint applications exist that could identify and alert IT of malware like ransomware?
What tools exist to determine the type of malware being identified?
Which team monitors endpoints and how does that team respond to events?
When malware is identified, how is the situation scoped and contained?
What remediation actions would take place and who would perform those steps?
What forensic steps would be taken to identify how the malware was installed on the endpoint?
What vulnerability and security assessment actions would follow this situation to ensure that other systems are not affected by the malware or vulnerability that led to the malware infection?
Who would be responsible for any public or internal messaging explaining the impact from this malware?
Which specific team members would be part of the response team? Who are their backups?
What response time and result would be considered a success or a failure?
How does the organization’s current expected response align with desired successful responses?
What gaps in people, process, and technology exist that would impact a successful response to this threat?
Which members of the HR, management, and legal teams would be involved for any required disciplinary actions resulting from this incident?
As you can see from the list of example questions, a tabletop exercise can be very involved and require many hours to properly execute. You should also notice that members from different parts of the organization are required to thoroughly validate the people, process, and technology that would be evaluated during a tabletop exercise. This brings up the question of who should be involved in a tabletop exercise. The short answer is, it depends. The following section outlines different options for delivering tabletop exercises, which require different people to be involved with the exercises.
Tabletop Exercise Options
There are different approaches to executing a tabletop exercise. One approach is to run the same scenario for different groups within the organization, which means performing multiple smaller tabletop exercises. For the ransomware example, the organization could first work with desktop support to capture how they would respond to a ransomware situation. Next, the organization could meet with the network security team and run the same ransomware scenario, but with a focus on their impact on the overall incident response. Using this smaller-group approach is ideal for keeping the exercise focused with fewer people involved and possibly reducing concern that other teams would influence or impact how a specific team would respond during the tabletop exercise.
Another approach to delivering a tabletop exercise is to include managers from each department and obtain input from all departments during the same meeting. This approach allows each department to contribute while the scenario is being covered, rather than requiring the team delivering the tabletop exercise to combine the responses of all the individual group exercises into a single tabletop exercise results document. This also allows for real-time debate as current and potential future responses based on changes occurring post table top exercise are analyzed. Some concerns when including all teams within an organization are the size of the meeting, the time required to hear feedback from all included members within the tabletop exercise, and the potential for conflict between departments. Limiting the tabletop exercise to only department managers can mitigate these and other problems; however, department managers might not know the details required to answer a question during the tabletop exercise. For example, a manager might not know the specific technology that would be used, but would know which member of his or her team would be able to answer such questions. Using the manager-led tabletop exercise format would require managers to take any unanswered questions back to their team and later provide a response.
Tabletop Exercise Execution
The best format for a tabletop exercise typically depends on the scenario that is being tested. However, the following tips apply generally to executing a successful tabletop exercise, paraphrased from the CSO article, “6 Tips for Effective Security Tabletop Testing” by Bob Violino:
Take time to prepare for the exercise: Invest time in developing the objectives and the scope and selecting the proper participants. Planning is often the most time-consuming phase but will pay off regarding the success of the exercise. Having the wrong people involved or a scope that is too narrow or too broad will not only produce poor results but also cause those involved to believe their time was wasted, leading to a lack of support for any recommended adjustments following the tabletop exercise.
Involve multiple parties from different departments: Security is the responsibility of every person in an organization. That means the response to an incident will impact many different departments. The best tabletop exercise results come from involving all parties that would be impacted and could provide value or cause complications during the incident response.
Establish the ground rules up-front: A tabletop exercise represents walking through stressful situations. Some people might want to speak openly regardless of whether the topic is positive or negative, while others might not want to participate unless called upon. Not addressing the different personalities in the room will lead to frustration and loss in support for the results of the exercise. Make sure to set expectations up-front for required participation, what is and is not permitted to be discussed during the exercise, what can and cannot be talked about after the meeting, and any other ground rules to ensure a successful use of everybody’s time.
Leverage external resources if available: Tabletop exercise services have been used by many organizations, and best practice documentation is available. Hiring a consultant that provides tabletop exercise services can be valuable because the consultant offers an external, unbiased voice and has experience executing successful tabletop exercises. If your team has never delivered a tabletop exercise, it is recommended to seek external support and learn from the best practices of others before performing your own internal exercises.
Broader is likely better: Discussion of some tabletop exercise topics can either go very deep into details or remain broad. Keeping the discussion broad likely is better unless the team involved in the tabletop exercise believes the topic being covered requires specific details. For most tabletop exercises, details can be captured by the expert after the tabletop exercise, allowing for all topics to remain broad and for all team members to be engaged (versus the risk of only hearing from specific experts). Keeping conversations broad also shortens the duration of the tabletop exercise because details are not addressed until after the meeting.
Use realistic scenarios: The purpose of a tabletop exercise is to evaluate the response to a potential future situation. All scenarios need to be as realistic as possible in order to produce a realistic result.
Tabletop Exercise Format
It is recommended to include certain topics within the tabletop exercise document that is used during and referenced after the exercise is performed. First, an introduction should explain the purpose of the exercise. A goals section should be included (or goals should also be listed in the introduction section) so that the expected outcome is clear. All details about the meeting need to be documented, including the date, facilitator, and all participants. All processes that are evaluated should also be listed, including desired policies and procedures that might not exist but are planned to be developed, with the current status noted. The tabletop exercise scribes need to document each scenario, including its target capabilities being tested, objectives for the exercise, and details regarding how the organization would respond if the situation occurred. Documentation of recommended remediation may or may not be included depending on whether the purpose of the tabletop exercise is to just evaluate processes or to also include corrective actions. All of this needs to be included in the tabletop exercise post event documentation.
I am often asked which tabletop scenarios are best for an organization to run through. Again, my answer is it depends on your business, as no single threat list fits all organizations. The tabletop exercise scenario list for an organization that runs an online business will be very different than one for a school. If you need a general guideline for scenarios, I highly suggest considering using playbook templates. Chapter 8, “Threat Hunting and Incident Response,” and Chapter 10, “Data Orchestration,” both provide a deep look at playbooks. In both chapters, I will run through different playbook examples provided by the Incident Response Consortium (IRC) at https://www.incidentresponse.com/playbooks/. Figure 6-1 shows the gallery of free playbooks available from IRC, which include recommended steps for different parts of responding to specific threats. Playbook templates are a great resource for building a template for your tabletop exercise, but I highly recommend prioritizing the threats you expect to impact your organization versus running through random playbook templates.
FIGURE 6-1 Incident Response Consortium Playbook Options
Tabletop Exercise Template Example
This section presents an example of a tabletop exercise template. If you decide to use a playbook template to develop your tabletop exercise template, you can use this example as a way to structure what questions you will ask based on the steps recommended in the playbook template. For example, if a malware outbreak playbook suggests informing IT about the situation, you would include a question such as “Who would be informed when a malware outbreak event is identified?” The same process would apply as you evaluate your SOC service playbooks against a tabletop exercise. Playbooks will be covered in more detail in Chapters 8 and 10.
The following is a sample tabletop exercise template for disaster planning featuring many of these suggested sections.
Disaster Planning Guide for <COMPANY>
This forum is used to design and facilitate a tabletop exercise (TTX) as well as provide appropriate documentation of performance and findings during the exercise.
The TTX involves administrative staff, management, and other key personnel in an informal group discussion focused on a hypothetical situation.
The purpose of the TTX is to evaluate existing plans, policies, and procedures without incurring signification costs and time commitment required to deploy and test actual resources. A TTX allows participants to work through a problem in a controlled environment in compressed or simulated time without the pressures of an operations-based exercise.
It is recommended that the TTX be completed on a regular basis for potential threats that have been identified by the SOC and leadership.
Goals:
Participants in a TTX will:
Identify strengths and opportunities for improvement
Enhance understanding of new concepts
Change attitudes and perspectives
Conduct Characteristics:
Requires an experienced person to facilitate the TTX
Promotes in-depth discussions
Involves slow-paced problem solving in simulated/compressed time
Date/Facilitator/Participants:
Plans, Policies, Procedures referenced during TTX:
Scenario 1:
Overview
The time of occurrence and impacted system
Identified objectives for operational period
Identified tasks that need to be performed to meet objectives
Response from team members regarding current capabilities
Scenario 2 (Repeat):
Tabletop Exercise Evaluation:
Identified areas of strength
Identified opportunities for improvement
Identified roles of CUSTOMER in the TTX
Identify any changes that may result from the TTX
Note
The Center for Internet Security (CIS) offers tabletop exercise templates. One example can be found at https://www.cisecurity.org/wp-content/uploads/2018/10/Six-tabletop-exercises-FINAL.pdf.
Another approach to validating policies and procedures outside of performing a tabletop exercise is to compare what would be performed by an organization against what is considered industry best practice. This leads us to the topic of standards, guidelines, and frameworks, all of which can be reference points for what should be included in your organization’s policies and procedures. Standards, guidelines, and frameworks are also useful for referencing what steps should be taken during a tabletop exercise so that existing policy and procedures can be compared against what the industry would recommend should be done when addressing a scenario.
Note
Many organizations incorporate standards, guidelines, and frameworks into their policies and procedures rather than building policies and procedures from scratch.
Standards, Guidelines, and Frameworks
Chapter 1 introduced the concepts of standards, guidelines, and frameworks. Although organizations are not legally obligated to follow standards, guidelines, and frameworks, many are highly recommended as security best practices and often used as templates for developing policies and procedures as well as meeting various forms of compliance. There are many resources that provide their interpretation of best practices, which can cause confusion when seeking out advice for improving an organization’s security. When considering the merits of a specific resource, it is recommended to evaluate the reputation of the organization that created the resource, what was considered when the standard, guideline, or framework was developed, the target audience for the resource, when the resource was created, and if any vulnerabilities or other issues have been documented in reference to the use of the resource. Common practices for verifying the usefulness of a resource include speaking with your counterparts at other organizations in the same field of business to get their opinions as well as researching the company that is offering the resource.
Note
In some cases, the leadership of an organization may adopt a certain standard, guideline, or framework as a policy, which means the standard, guideline, or framework must be followed regardless if it is dated or potentially no longer relevant. This could cause problems and introduce vulnerabilities depending on what is being required. For example, if a policy requires to follow a resource that approves only older software on a system, updating or patching the software on that system might violate the policy and put the system at risk! I recommend leadership of an organization to speak with technical experts regarding potential impact of change to reduce the risk of policies causing negative impact to the organization.
Next I will review some of the most commonly used security standards, guidelines, and frameworks, all of which were introduced in previous chapters. Many of these resources will have overlapping concepts, which should be expected because they are all attempting to provide industry best practices for various security topics. Keep in mind that it is common for people, process, and technology to change faster than external resources such as the following can adapt to, which could lead to introducing vulnerabilities even if the recommended resource is followed. This is why you should validate the resource’s creation and maintenance date as well as how relevant the resource is to your organization’s goals prior to leveraging the resource. The same concept applies when developing policies and procedures that reference external sources. With proper validation, standards, guidelines, and frameworks can be excellent resources for assisting with developing policies and procedures. Remember that meeting compliance doesn’t mean you are meeting a best practice for a security baseline. You will need to exceed compliance requirements using a more holistic view of security.
NIST Cybersecurity Framework
Introduced in Chapter 1, the NIST Cybersecurity Framework (CSF) is one of the most popular frameworks consisting of standards, guidelines, and best practices for dealing with cybersecurity-related risk. Chapter 1 also introduced the NIST Framework Core and five framework Functions, as shown in Figure 6-2.

FIGURE 6-2 NIST Cybersecurity Framework Core Structure
As a refresher from Chapter 1, each of the five functions of the NIST Framework Core has a high-level view on one aspect of security. Anything under the Identify function would represent steps used to manage risk to systems, people, assets, data, and capabilities. The Protect function would cover topics that develop and implement people, process, and technology to reduce risk proactively and ensure delivery of critical services. Reactive risk recovery topics would fall under the Recover function since they cover actions that follow an incident, including topics covering how to restore and resist future compromise. Detect and Respond functions cover topics that involve how an organization identifies and responds to incidents.
Using the NIST Cybersecurity Framework
The CSF tiers provide context on how an organization views cybersecurity risk and the processes in place to manage that risk. The NIST CSF approach to grouping topics enables an organization to pick an area of interest and review targeted recommendations to best understand what NIST would consider best practices for people, process, and technology. Tiers cover an increasing degree of rigor and sophistication in cybersecurity risk management practices. The tiers approach helps determine the extent to which cybersecurity risk management is informed by business needs and is integrated into an organization’s overall risk management practices. This approach also considers an organization’s current risk management practices, threat environment, legal and regulatory requirements, information sharing practices, business/mission objectives, supply chain cybersecurity requirements, and organizational constraints. Understanding the maturity of a recommendation is critical not only to identity an organization’s current capacities but also to set goals and milestones to improve the associated people, process, and technology against what is being recommended by NIST.
The NIST CSF can be used by first identifying the capability that you want to assess against what NIST views as industry best practices. You can use the NIST capability assessment process to understand where your capability stands today based on its current maturity level as well as identify goals for improvement based on gaps identified during the assessment process. The NIST CSF uses a tier model to categorize different maturity levels of capabilities, where the fourth tier represents the most mature capabilities. It is ideal to target all capabilities to reach NIST’s highest tier in maturity, but some capabilities may not need to reach this level. For those situations, a lower tier can be set as the target profile during the evaluation process.
NIST Tiers
The following list breaks down each tier of the NIST Cybersecurity Framework. Each higher tier assumes capabilities from a previous tier plus additional improvements. Some of your capabilities might fall between tiers, making it a judgment call as to where your capabilities would be documented according to the NIST recommendations.
Note
It is left to the reviewer’s discretion to determine at which tier an organization’s current capabilities should be classified. This could lead to a false sense of security or false positives if poor judgment is used when determining current capability tier ranking.
Partial (Tier 1): Organizational cybersecurity risk management process is not formalized and risk is managed in an ad hoc approach and sometimes reactive manner. There is very limited awareness of cybersecurity risk at the organization level. The organization does not understand its role in the larger ecosystem with respect to collaborating with or receiving information from external resources.
Risk Informed (Tier 2): Risk management practices are approved by management but might not be established as organization-wide policy. There is some awareness of cybersecurity risk at the organizational level, but an organization-wide approach to managing cybersecurity risk has not been established. There is some collaboration with external sources via receiving and sharing security information; however, it is limited and not a repeatable collaboration.
Repeatable (Tier 3): The organization’s risk management practices are formally approved and expressed as policy. Cybersecurity practices are regularly updated based on business/mission requirements and the changing threat and technology landscape. There is an organization-wide approach to managing cybersecurity risk. This includes well-defined policies and procedures, which are periodically reviewed and updated. The organization leverages and contributes to external resources through established collaboration relationships. This leads to an awareness of the organization’s understanding of existing risks based on industry standards, guidelines, and frameworks.
Adaptive (Tier 4): The organization adapts its cybersecurity practices based on previous and current cybersecurity activities, including lessons learned and predictive indicators. Through a process of continuous improvement incorporating advanced cybersecurity technologies and practices, the organization actively adapts to a changing threat and technology landscape and responds in a timely and effective manner to evolving, sophisticated threats. The relationship between the organization and cybersecurity goals is clearly defined and understood and considered when decisions are made. The organization has adopted external partnerships that are essential to decisions regarding understanding and responding to the current threat landscape.
An organization can use the NIST Cybersecurity Framework as part of its systematic process for identifying, assessing, and managing cybersecurity risk. The best approach is to match existing capabilities against what is recommended by NIST and identify at which tier your organization’s current capabilities should be pegged. When evaluating a capability, you need to consider the entire lifecycle of the capability, including how the capability is planned, designed, deployed, run, and decommissioned. During the lifecycle of a capability, its maturity rating can be evaluated at any point against the NIST tier structure to better understand its current state of maturity. For example, the tier level of a capability should increase as you plan a new capability, deploy it, and eventually tune it so it provides maximum value. In this example, you would want to continuously update how the capability’s tier or maturity is documented rather than document it during the planning phase and never adjust its perceived maturity as it goes live and provides more value to the organization.
NIST CSF Capability Assessment
NIST CSF tiers are a way to understand the maturity of a capability. A capability, however, must be evaluated to understand which NIST tier it falls within. You cannot assume all of your capabilities are at maximum maturity, or Tier 4 in the NIST CSF. You must continuously evaluate your capabilities with the goal to improve their maturity, which is represented as an increase in NIST CSF tier status. Using the NIST CSF to assess an organization’s capabilities not only enables the organization to map each capability to a NIST Tier to better understand the organization’s current strengths and weakness but enable the organization for a roadmap to improvement.
The following steps illustrate how an organization could use the Framework to create a new cybersecurity program or improve an existing program:
Step 1. Prioritize and Scope: In this step, the organization must identify organization or mission objectives along with high-level organizational priorities. NIST offers many recommendations for your organization to follow, some of which will be more relevant to your organization than others. It is up to your reviewer to determine the order of how the people, process, and technology are evaluated by NIST based on various business and technology factors related to the organization.
Step 2. Orient: Identify all related systems and assets, regulatory requirements, and overall risk approach to what is being assessed.
Step 3. Create a Current Profile: Document which NIST Framework Core Categories and Subcategories (introduced in Chapter 1) are currently being achieved.
Step 4. Conduct a Risk Assessment: Assess existing capabilities to determine gaps in what is identified as achieved and missing. The topic of performing an assessment will be covered later in this chapter in the section “Risk Assessment.”
Step 5. Create a Target Profile: Create a target profile that focuses on the CSF Categories and Subcategories assessment and describes the desired cybersecurity outcomes.
Step 6. Determine, Analyze, and Prioritize Gaps: Compare the current profile against the target profile to determine what changes in people, process, and technology will help the organization achieve the desired target profile.
Step 7. Implement Action Plan: Prioritize and execute on actions needed to achieve the target profile.
Keep in mind that the NIST CSF tier approach is a way to measure a capability’s maturity and that the assessment process places each capability within a tier. It is up to the organization to determine the desired tier the capability being evaluated should be functioning at as well as to set that tier as the target profile. All capabilities do not need a target profile of Tier 4, Adaptive, but any critical capability is ideal for Tier 4 performance.
An example of using the NIST CSF to validate industry best practices would be to view the Identify (ID) function, Asset Management category, and ID.AM-2 subcategory that specifies “Software platforms and application within the organization are inventoried.” What also makes the NIST CSF a valuable option is that it references other industry guidelines to support its recommendations. For example, the “Informative References” column for the NIST CSF ID.AM-2 subcategory points to the following industry guidelines that align with this recommendation: CIS CSC 2; COBIT 5 BAI09.01, BAI09.02, BAI09.05; ISA 62443-2-1:2009 4.2.3.4; ISA 62443-3-3:2013 SR 7.8; ISO/IEC 27001:2013 A.8.1.1, A.8.1.2, A.12.5.1; and NIST SP 800-53 Rev. 4 CM-8, PM-5. I recommend viewing the other recommendations in an “Informative References” section of any NIST CSF best practice to better understand the security control based on seeing more than one guideline’s view of the same topic. During your assessment of NIST CSF ID.AM-2, you would identify which tier (1 through 4) represents your organization’s capability to manage the inventory of its software platforms and applications. Check out the full NIST CSF to review the various topics that you can use to assess your security capabilities for people, process, and technology.
Note
The NIST Cybersecurity Framework is available free of charge at https://doi.org/10.6028/NIST.CSWP.04162018.
ISO/IEC 27005
The International Organization for Standardization (ISO) creates documents that provide requirements, specifications, guidelines, or characteristics that can be used consistently to ensure that materials, products, processes, and services are fit for their purpose. Part of ISO’s value is its family of standards that provide best practices for various cybersecurity concepts.
One popular publication is ISO/IEC 27005, Information technology – Security techniques – Information security risk management, which offers guidelines for information security risk management. As shown in Figure 6-3, the ISO/IEC 27005 steps for managing information security risk include establishing context; conducting a risk assessment by identifying, analyzing, and evaluating risk; and then treating the risk. Ongoing activities during these steps include communication, consultation, monitoring, and review. Any organization can use the details provided in ISO/IEC 27005 to help improve how it handles information security risk management through auditing against ISO recommendations or performing a tabletop exercise and using ISO recommendations as the source against which to compare existing practices.
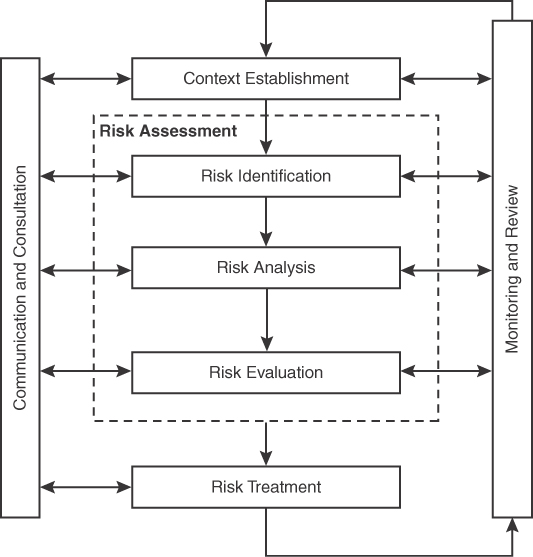
FIGURE 6-3 ISO/IEC 27005 Information Security Risk Management Process
An example use case from the ISO/IEC 27005 publication is section 7.2 under “Context establishment,” which focuses on a suggested information security risk management approach. ISO recommends using the appropriate risk management approach that addresses basic criteria such as risk evaluation criteria, impact criteria, and risk acceptance criteria. Additionally, ISO recommends that resources should be able to perform risk assessments as well as establish risk treatment plans, define and implement policies and procedures, monitor controls, and monitor the information security risk management process. Section 7.2 remains high level, making it an ideal resource for developing a risk management policy. Other sections of ISO/IEC 27005 provide more details that can help organizations develop supporting procedures for new or existing policies; however, procedures should always contain specific details that relate to your organization.
There are many other information security topics covered by ISO guidelines. For example, ISO/IEC 27034 provides guidance on information security to those specifying, designing, and programming or procuring, implementing, and using application systems. An application system normally consists of a user interface, business logic, and a database of some sort. ISO/IEC 27002 is extremely popular and an internationally recognized standard code of practice for information security controls. ISO offers hundreds of papers covering various IT topics, which you can search through at https://www.iso.org.
Note
Another great resource to learn more about ISO security guidelines is https://www.iso27001security.com.
CIS Controls
The Center for Internet Security (CIS) provides best practice solutions for cyber defense and builds and leads industry groups to enable an environment of trust within the cyber community. One CIS resource that is extremely popular is the CIS Controls, security best practices that provide specific and actionable ways to reduce the risk of exploitation. The CIS Controls are derived from the most common attack patterns highlighted in leading threat reports and vetted across a broad community of industry security professionals. Members associated with vetting the CIS Controls include the NSA Red and Blue Teams, U.S. Department of Energy Nuclear Energy Labs, and various law enforcement agencies, which all give creditability to this resource.
The CIS Controls are broken down into the following three categories, depicted in Figure 6-4 (based on CIS Controls Version 7.1, the current version at the time of writing):
Basic CIS Controls: Anything basic should be considered security table stakes, meaning all organizations should have some form of the recommendations in the basic category applied to their processes. Example basic recommendation categories include identifying what’s on the network and dealing with vulnerabilities.
Foundational CIS Controls: Defenses against threat categories such as malware defense or protecting an organization’s DMZ or network boundary.
Organizational CIS Controls: Controls that impact the entire organization, such as incident response.
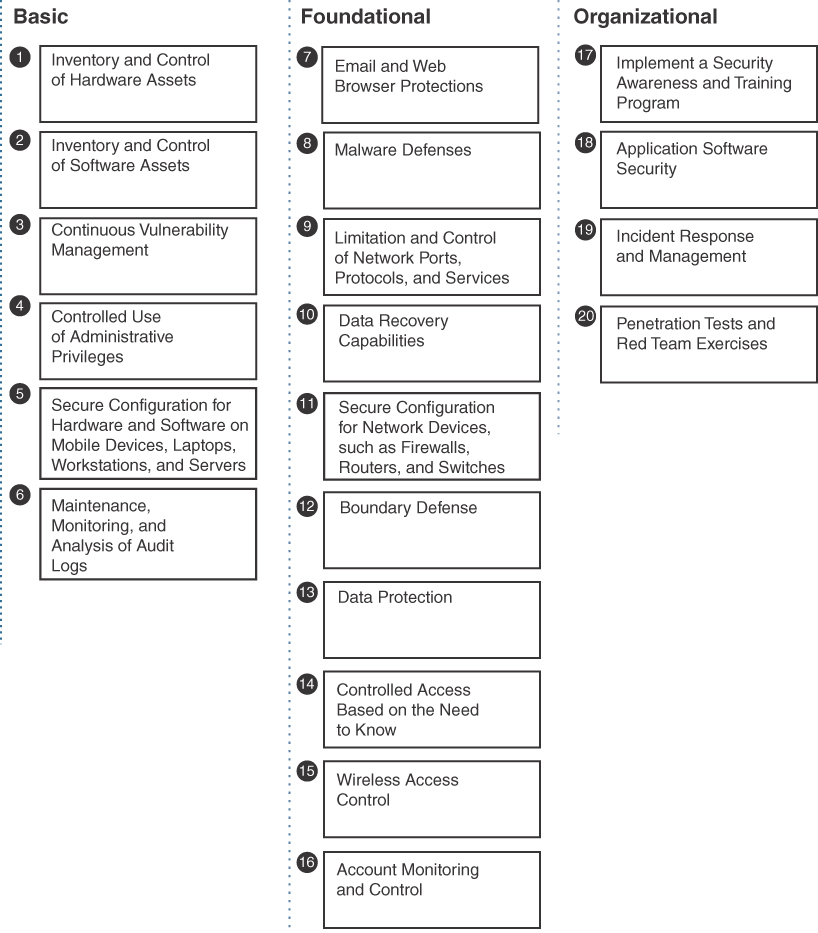
FIGURE 6-4 CIS Controls Version 7.1
CIS takes into consideration the type of organization that would use its recommendations based on the organization’s size and expected funding. For example, a small restaurant would likely not be able to invest in an expensive vulnerability management tool to evaluate a few endpoints used within its business. CIS uses a three-tier grouping system to identify which type of organization should consider the recommendations being offered. Figure 6-5 shows how CIS defines its system for grouping the different types of organizations expected to use the CIS Controls resource.

FIGURE 6-5 CIS Controls Organization Grouping
A sample use of the CIS Controls is referencing CIS Sub-Control 2.2, which states “Ensure Software is Supported by Vendor.” This recommendation is classified as an “identify” security function and applies to all three organization groups, which means any size organization should follow this recommendation. The explanation section of this Sub-Control further defines this recommendation as only using authorized software according to the vendor and listing any unauthorized software as unsupported and a potential risk.
Any size organization can benefit from referencing the CIS Controls. They are short, tactical, and well-vetted by industry experts.
Note
You can download the CIS Controls at https://learn.cisecurity.org/cis-controls-download.
ISACA COBIT 2019
ISACA is an independent, nonprofit, global association that develops guidelines for information system best practices. One of its most popular offerings is the COBIT 2019 Business Framework for Governance and Management of Enterprise IT. COBIT 2019 offers detailed enabler guides that focus on governance and management best practices. COBIT 2019 also has professional guides targeting implementation, information security best practices, guidance on assurance, risk management, and other security topics. COBIT 2019 is available only to members, for a small fee. Learn more about COBIT 2019 and other ISACA offerings at https://www.isaca.org.
FIRST CSIRT Services Framework
The Forum of Incident Response and Security Teams (FIRST) is the global forum of incident response and security teams. FIRST offers various standards, publications, and best practice guides that are designed to provide best practices for various cybersecurity concepts. One popular offering from FIRST is the Computer Security Incident Response Team (CSIRT) Services Framework. The CSIRT Services Framework is a high-level document describing a collection of cybersecurity services and associated functions other security teams can learn from. The CSIRT Services Framework is essentially a guideline for best practices for incident response.
The CSIRT Services Framework Version 2.1 is composed of four elements: service areas, services, functions, and sub-functions: The five service areas are Information Security Event Management, Information Security Incident Management, Vulnerability Management, Situational Awareness, and Knowledge Transfer. Each service area has services, which in turn have different functions and sub-functions. For example, the Information Security Incident Management service area has a service named Artifact and forensic evidence analysis, which contains four functions: media or surface analysis, reverse engineering, runtime and/or dynamic analysis, and comparative analysis. Each service, function, and sub-function has a section describing what it is, a section describing its purpose, and a section describing its outcome (measurable results of implementing it). Each function also has a list of sub-functions, if applicable. For example, function 6.3.2, reverse engineering, has four sub-functions, which are static analysis, code reverse engineering, potential behavior analysis and description, and potential signature design.
The CSIRT Services Framework Version 2.1 can provide value by enabling you to review your policies and procedures against what is listed as best practice for every service area and its associated topics. You can download the latest version of the framework from https://www.first.org/standards/frameworks/.
Note
FIRST also has a great framework resource for product incident response teams (PSIRT); see https://www.first.org/standards/frameworks/.
Exceeding Compliance
It is common practice to use any of the standards, guidelines, and frameworks previously discussed (and others) as reference points for developing and testing your people, process, and technology and as templates for building policies and procedures. Using resources such as a tabletop exercise or leveraging standards, guidelines, and frameworks is great but might not provide enough details to help you generate specific areas of improvement or best understand your specific needs.
As stated at the beginning of the chapter, it is important to understand that compliance is something you either meet or do not meet. It is also important to understand that compliance does not consider all aspects of security, meaning any risk that falls outside of compliance is not taken into account in an audit for compliance. This is why you must establish a baseline for security that exceeds what is required for meeting compliance. To do this, you first need to meet compliance using a formal testing process known as an audit. Once your organization passes an audit, you identify where it may still have risk outside of compliance by using assessments and penetration testing. Next, let’s look at how to meet compliance by using audits.
Audits
Audits are the process to validate that policies are properly enforced. Policies will include everything from regulations to what a organization’s leadership deems is required. Audits alone are not designed to evaluate the security posture of the organization. Audits focus only on what is in scope for meeting compliance and are designed to be tactical rather than generic. An example would be auditing for compliance with a specific policy, such as a policy that prohibits unauthorized devices from being attached to the network. The audit would test only for unauthorized devices and not consider any other vulnerabilities. Keeping the audit focused simplifies execution and expected results, which leads to a quick benefit from the service. The downside of keeping the audit scope limited and focused would be overlooking other vulnerabilities. This can lead to a false sense of security even though the criteria for the audit were met.
Other services such as assessments and penetration testing should be used when evaluating the overall security of an organization. Reserve audits for more tactical evaluations such as meeting compliance for a specific policy. The format used for an audit depends on what is being assessed.
Audit Example
You should leverage any document that lists requirements to meet what is being audited, such as the targeted policy, and evaluate if capabilities are met. In some cases, it might make sense to use a pass/fail approach, while other cases might require more detailed information. The following is an example template that could be used for auditing a firewall.
Firewall Audit
The organization should have a firewall or equivalent deployed to protect its internal network and devices against unauthorized access. [Full / Partial / None]
The password on the firewall should be changed from the default setting to an alternative strong password. [Changed / Not Changed]
The firewall password should meet the following:
8 characters or longer [Pass / Fail]
Not the same as the username [Pass / Fail]
Does not contain any identical characters next to each other [Pass / Fail]
Is not made of up of only a dictionary word [Pass / Fail]
Includes upper- and lowercase letters and at least three numbers or special characters [Pass / Fail]
Has not been reused within a predetermined time period [Pass / Fail]
Does not contain the manufacture’s name [Pass / Fail]
Each rule set on the firewall must be approved by an authorized individual and documented, including an explanation of the business need for the rule. [Pass / Fail]
Unapproved or vulnerable services should be blocked at the gateway firewall. [Pass / Fail]
Any permissive firewall rules that are no longer required should be disabled. [Pass / Fail]
All exceptions to firewall rules must have a documented expiration date. All exceptions that exceed the expiration date must be removed. [Pass / Fail]
The firewall’s administration settings should not be accessible from the Internet. [Pass / Fail]
The previous audit example shows a checklist approach to auditing a firewall. Each question provides answer options for the auditor to select to determine the appropriate response. Another approach to formatting the responses for this document would be to provide an open response section for each question, allowing the auditor to provide a much more detailed response about his or her findings, in addition to choosing from a predefined selection of choices. Another approach for this document would be to use a scoring system, where each question is worth a value, and then the auditor would add up all the values to generate a score. Any of these approaches work as long as the results successfully establish a repeatable evaluation of the people, process, and technology being audited.
Internal Audits
It is common practice to use audits to validate if specific policies or recommended standards, guidelines, or frameworks are being met within the organization. Audits are also used to validate if required industry regulations such as PCI DSS or HIPAA are being met, as described later in this chapter. The team responsible for performing an audit could be part of the SOC, part of a dedicated compliance team, or a partnership between one or more groups. Many organizations have a dedicated group that performs audits and is led by the chief compliance officer (CCO), who is responsible for overseeing compliance within an organization as well as ensuring compliance with laws, regulatory requirements, policies, and procedures. The CCO is considered the subject matter expert and has the responsibility of establishing standards and implementing procedures to ensure compliance programs are effective in identifying, detecting, and correcting noncompliance with laws and regulations as they apply to the organization. Because the CCO sits on the board, he or she must provide assurance to other senior management that compliance is met as well as develop strategies and responses for any compliance-related complications. This is accomplished by using a combination of audit services and other assessment tools.
Note
It is highly recommended to seek the CCO’s support for the SOC program and to incorporate the CCO’s objectives within the SOC goals. CCO support will gain SOC visibility at the executive level as well as allow the SOC to leverage budget associated with the organization’s compliance goals.
External Auditors
Most required industry compliance will have an external team that represents either the government or industry service that mandates the compliance and is responsible for validating if your organization falls within compliance. External auditors might charge a fee and require periodic auditing in order for your organization to be authorized to use a service or certain type of data. You can recruit your own external auditors to validate your current capabilities prior to the scheduled external audit or use internal services for audit preparation. For example, if your organization accepts credit cards as a form of payment, then your organization must comply with PCI DSS. There are companies that can assist with helping you prepare for the official PCI DSS audit and it is highly recommended that you use only external auditors that are approved by the PCI Security Standards Council to ensure a quality service when auditing for PCI DSS. The same concept would apply regarding seeking auditing services for any other type of compliance. You want to ensure the service provider is an authorized auditor for the subject you want to have evaluated.
When you consider external audit services, the following are some general questions you should ask when evaluating a potential audit service provider:
How does your service validate that it meets the latest version of the topic(s) being audited?
What guarantees does your service provide if a topic considered compliant is found by another auditor to be noncompliant?
What are the scope and costs for your services?
What technology and steps are included within your services?
What resources and access permissions are required for your service to be performed?
What risk is associated with using your service?
How long should the organization wait until performing another audit?
Do you provide recommendations or remediation services for items that fail the audit?
Audit Tools
Another option you can use to audit for various types of compliance is to leverage cloud or on-premises auditing tools. Auditing tools can provide a template of questions your internal auditors can use to perform auditing services or provide some scanning capacities to gather and assess targets for compliance. An example is using LogicGate’s risk management tools that offer compliance audit capabilities, including assessing for PCI DSS. Some network and security tools might also offer a compliance widget or report to help assist with gathering data for compliance; for example, a firewall might include compliance reports for NIST standards. You can also ask your trusted technology vendors if they offer mappings to popular standards, guidelines, and frameworks. Figure 6-6 shows an example of mapping the Cisco security products to the NIST Cybersecurity Framework. As with auditing services, recommended practice dictates that you validate the tool as an acceptable source for auditing the topic of interest to avoid having inaccurate results. Some vendors might claim to meet audit requirements but would actually only partially meet or outright fail if audited by an authorized service provider.

FIGURE 6-6 Mapping of Cisco Security Products to the NIST Cybersecurity Framework
Audits focus only on specific subtopics found within the topic being evaluated. You need to consider evaluating the entire organization for vulnerabilities regardless of whether the potential vulnerability is related to your organization’s compliance requirements. This is how you exceed compliance: addressing risk beyond what is required to be compliant. The process you can use to evaluate for all vulnerabilities and risk is to perform an assessment and penetration test. First, let’s review the concept of assessments.
Assessments
An assessment goes beyond what is evaluated by an audit by considering any vulnerability found within the scope of what is being assessed. For example, an audit against a policy for identifying unauthorized systems connected to the network would only validate what is connected to the network. An assessment of devices connected to the network would further evaluate the risk associated with each device such as if the device has potential vulnerabilities, what risk each device poses to the organization, and other vulnerabilities in the people, process, and technology associated with devices connecting to the network.
Note
Assessments are security-focused while audits are compliance-focused. Best practice is to use both to exceed compliance by ensuring you meet compliance as well as address risk outside of what is required to be compliant.
Assessment Types
Different types of assessments can be performed. A threat assessment looks at anything that could contribute to a disruption of normal services and operations. The following is a sample format for a threat assessment report.
Threat Assessment
Threat |
Caused by Human/Nature |
Strength of Threat |
Motivation Factor |
Disgruntled employee |
Human |
Medium |
High |
A vulnerability assessment focuses on identifying, quantifying, and rating weaknesses or gaps within your systems. The following is an example format for a vulnerability assessment report.
Vulnerability Assessment
Asset |
Vulnerability |
Severity |
Exposure |
Rating |
Website |
Incomplete SQL code |
High |
High |
5 |
A risk assessment is focused on measuring the probability of a security breach occurring and the magnitude of the risk. This approach can provide results in a qualitative view (high, medium, low) or a quantitative view such as on a scale of 1 to 5. The following is an example format for a risk assessment report.
Risk Assessment
Risk |
Likelihood of Occurrence |
Existing Controls |
Proposed Mitigation Measures |
Virus attack |
High |
Antivirus |
Improve Internet usage policy. Install anti-malware that is based on behavior and anomaly detection capabilities. |
An impact assessment identifies how and the extent to which your business will be affected by a security breach. The following is an example format for an impact assessment report.
Impact Assessment
Risk |
Business Impact |
Customer Impact |
Financial Impact |
Regulatory Impact |
Virus attack |
High |
Medium |
High |
Low |
It is recommended to use all four assessment methods to evaluate your people, process, and technology. Assessment reports can break up data into sections that focus on these four assessment types or include different columns that cover results from each assessment method. The previous examples could be combined into one large report or be part of a spreadsheet that covers all related topics.
Note
The U.S. Federal Risk and Authorization Management Program (FedRAMP) offers a great resource for developing a security assessment report at https://www.fedramp.gov/developing-a-securityassessment-report/.
It is common for the scope of an assessment to be much broader than an audit and for assessments to be performed more frequently than audits. Assessments can include various types of people, process, and technology, and performing assessments is commonly one of the services offered by a SOC. Chapter 3, “SOC Services,” covered different types of SOC services, including performing assessments.
Assessment Results
The results of an assessment are used to develop a vulnerability report that includes a list of potential vulnerabilities and details about each. A commonly included detail is the estimated risk associated with the potential vulnerability, to help the organization prioritize which risk to address first. The most common method used in vulnerability reports to help organizations rank the associated risk with an identified vulnerability is the Common Vulnerability Scoring System (CVSS) from FIRST. Essentially, a CVSS score provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity. The CVSS is widely accepted in the security industry, and popular security assessment solution providers such as Rapid7, Core Security, and Tenable offer the same CVSS scoring references within their products. You can calculate the associated risk of a vulnerability manually by referencing the CVSS; however, most security solutions will do the calculations for you and rank the vulnerabilities with a scoring or color-coding system. Table 6-1 provides a sample vulnerability report featuring the results from assessing a website, USB devices, and a server. Chapter 9, “Vulnerability Management,” covers the CVSS in much more detail.
Note
You can learn more about how a CVSS score is generated at https://www.first.org/cvss/specificationdocument.
TABLE 6-1 Example Vulnerability Report
Asset |
Vulnerability |
Severity |
Exposure |
Rating |
Website |
Incomplete SQL codes left by a freelance web designer leading to SQL injection attacks |
HIGH |
HIGH |
5 |
USB devices |
Default operating system configuration allows all programs to run automatically |
HIGH |
MEDIUM |
4 |
Server |
Missing patch permits unauthenticated command prompt |
HIGH |
MEDIUM |
4 |
Assessment Template
Different assessments will vary regarding the focus of what the outcome report will contain. A vulnerability assessment report will focus on the different vulnerabilities found and their associated severity, such as shown in Table 6-1. A risk assessment report can include vulnerability data, but the report will be more focused on general risk, including quantitative and qualitative computations. A threat assessment report can contain both risk and vulnerability data, but the focus will be on specific types of threats and how they could potentially impact the organization. An impact assessment report will be focused on your organization’s assets and business and explain what to expect if certain types of events were to occur. There are many specific details that could be included depending on the desired outcome for the assessment service. My recommendation is to reference industry guidelines regarding what should be included in the type of assessment report you are looking to perform. An example of a guideline is the MITRE Threat Assessment and Remediation Analysis (TARA), found at https://www.mitre.org/sites/default/files/pdf/pr-11-4982-tara-methodology-description-version-1.pdf, which is a great reference point for a threat-focused assessment.
In addition to the specifics to the type of assessment being delivered, a final assessment report should include general topics, including an executive summary, purpose, list of technologies used, list of who was involved, and a summary of what was found. The next section is an example template for a risk-focused assessment. Many of the sections are common across all assessment reports regardless of the focus. Use this template as a reference for developing your assessment reports. I have left each section blank regarding example input and instead included descriptions about how to fill out each section.
Executive Summary
[Briefly summarize the scope and results of the risk assessment. Highlight high-risk findings and comment on required management actions.]
Detailed Assessment
1. Introduction
[Provide an overview of the project and what was done. This will prepare the reader for understanding everything to follow. This is not a complete summary, such as what was done in the executive summary.]
1.1. Purpose
[Describe the purpose of the risk assessment in context of the organization’s overall security program.]
1.2. Scope of this risk assessment
[Describe the scope of the risk assessment, including system components, elements, users, field site locations (if any), and any other details about the system to be considered in the assessment.]
2. Risk Assessment Approach
[Describe the steps that were taken during the assessment.]
2.1. Participants
Role |
Participant |
System Owner |
|
System Custodian |
|
Security Administrator |
|
Database Administrator |
|
Network Manager |
|
Risk Assessment Team |
2.2. Techniques Used
Technique |
Description |
[List techniques used; e.g., questionnaires, tools.] |
[Describe the technique used and how it assisted in performing the risk assessment.] |
2.3. Risk Model
[Describe the risk model used in performing the risk assessment. For an example risk model, refer NIST SP 800-30 Rev 1.]
3. System Characterization
[Describe the technology that was assessed.]
3.1. Technology Components
Component |
Description |
Applications |
[Describe key technology components, including commercial software.] |
Databases |
|
Operating systems |
|
Networks |
|
Interconnections |
|
Protocols |
3.2. Physical Location(s)
Location |
Description |
[Include locations included in scope.] |
3.3. Data Used By System
Data |
Description |
[Detail data elements included in scope] |
[Describe characteristics of data elements] |
3.4. Users
Users |
Description |
[Detail categories of users.] |
[Describe how users access the system and their intended use of the system.] |
3.5. Flow Diagram
[Provide connectivity diagram or system input and output flowchart to delineate the scope of this risk assessment effort.]
4. Vulnerability Statement
[Compile and list potential vulnerabilities applicable to the system assessed.]
Vulnerability |
Description |
[List vulnerabilities.] |
[Describe vulnerability and its impact.] |
5. Threat Statement
[Compile and list the potential threat sources applicable to the system assessed.]
Threat Source |
Threat Actions |
[List threat sources.] |
[List and/or describe actions that can be taken by threat source; e.g., identity theft, spoofing, system intrusion.] |
6. Risk Assessment Results
[List the observations (vulnerability/threat source pairs). Each observation should include
Observation number and brief description of observation (e.g., Observation 1: User system passwords can be guessed or cracked)
Discussion of the threat source and vulnerability pair
Identification of existing mitigating security controls
Likelihood discussion and evaluation (e.g., High, Medium, or Low likelihood)
Impact analysis discussion and evaluation (e.g., High, Medium, or Low impact)
Risk rating based on the risk-level matrix (e.g., High, Medium, or Low risk level)
Recommended controls or alternative options for reducing the risk]
Item Number |
Observation |
Threat-Source/Vulnerability |
Existing Controls |
Likelihood |
Impact |
Risk Rating |
Recommended Controls |
|
|
|
|
|
|
|
|
Vulnerability Scanners
One of the most common tools used for assessing vulnerabilities is a vulnerability scanner. Vulnerabilities will be included in all assessment report types since vulnerabilities represent potential attack vectors. You will need to include vulnerability scanning as part of your assessment process. Vulnerability scanners can be automated to perform periodic or on-demand assessments, depending on how they are used. The quality of the results will depend on many factors, including the data seen by the scanner and how the scanner evaluates a target. For example, a credential-based vulnerability scanner would be able to log into an endpoint device and assess the device without its results being impacted by the endpoint device’s enabled security tools such as a host firewall. A non-credential-based scanner would not be able to log into the endpoint, limiting its results to what can be seen and not blocked by enabled security tools such as the host firewall. Chapter 9 covers vulnerability management best practices in more details, including how to use vulnerability scanners to address risk and how to understand the data the scanners produce. Use the steps from Chapter 9 to leverage a vulnerability scanner as part of your assessment process.
Note
Best practice dictates using both credentialed and non-credentialed scanning when assessing devices. Credentialed assessments provide more accurate results, but non-credentialed assessments are closer to what a potential attacker would have access to. Both approaches provide their own form of value and should be leveraged equally.
Assessment Program Weaknesses
One important concept regarding assessments is that they lack validation of the results. They show “potential” risk rather than actual validated risk. The results being considered potential risk can occur based on how the assessment is performed. Many times, the tools used for an assessment capture data and compare it against a list of known vulnerabilities rather than actually attempting to exploit the vulnerability. This approach can lead to false negatives due to other elements that are not evaluated but are essential to truly understanding the nature of the potential vulnerability. For example, a vulnerability scan may find that a server has many vulnerabilities; however, the server might exist within a contained lab environment and not be a real threat to the organization, or the vulnerabilities that were found might be based on limited data captured by the assessment tool due to the server’s existing enabled security that limits what can be evaluated by the assessment tool. The best way to test any potential vulnerability to ensure that it is really a risk is to attempt to exploit it. Exploiting potential vulnerabilities is part of a penetration testing service.
Note
Assessments and penetration testing are services that help your organization consider risk that extends beyond what is addressed by meeting compliance requirements.
Penetration Test
A penetration test, also referred to as a pentest, goes beyond an assessment by performing the same steps that an adversary would perform to exploit an identified vulnerability. It is common for an assessment to report many more potential vulnerabilities than a penetration test of the same scope actually discovers due to how both approaches validate a target. By following the steps used by an attacker, a pentest truly qualifies whether a target is vulnerable to a real-world attack and, if so, at what level. A pentest typically has a higher cost and more risk associated with its services than an assessment, but a pentest tends to produce more accurate results. I specifically use the language “tends to produce more accurate results” because the actual results received will depend on the scoping and expected goals. I have seen organizations invest thousands of dollars in penetration testing services that result in very little actionable outcomes. My goal in this section is to address some of those pitfalls that lead to poor penetration testing results.
Note
You should first perform an assessment and apply risk reduction steps before performing a penetration test, which helps to maximize the value of the penetration test.
NIST Special Publication 800-115
NIST SP 800-115, introduced in Chapter 3, identifies four phases of a penetration test: planning, discovery, attack, and reporting. The following is a summary of those phases.
Note
NIST SP 800-115, Technical Guide to Information Security Testing and Assessment, is available at https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-115.pdf. I recommend at least perusing the table of contents to discover the full scope of what it has to offer for conducting penetration tests and assessments.
Phase 1: Planning
The planning phase involves establishing the rules and the scope of the penetration test and obtaining necessary approval for the penetration test before executing it. It is highly recommended to obtain approval from the highest level of leadership to ensure that all steps are authorized, in the event that something goes wrong. I have seen situations where a manager approved a penetration test that executive leadership was unaware of and the pentesting caused system failures. Both the manager and service provider were blamed for the system outages even though the penetration testers performed services within the agreed-upon scope of work. In the industry, having this approval is known as the “get out of jail free card.” Make sure your get out of jail free card is signed by a C-level executive!
Phase 2: Discovery
The discovery phase is made up of two parts. First, all network ports and services that fall within scope are identified to develop a list of potential targets. Other techniques might be used, such as dumpster diving, with the goal of gathering information and building a potential target list. These data collection steps fall under the category target reconnaissance and are the most time consuming but also the most valuable work. The more quality data that is discovered and collected about a target, the better the capability to identify potential targets to exploit. Some example tools you can use to conduct target reconnaissance are NMAP and masscan to perform port scanning; Shodan to research web-facing resources such as websites, web cameras, and network-enabled IoT devices; and searching social media sources such as LinkedIn and Facebook for details on people that work within the target network.
The second part of the discovery phase is analyzing the potential targets for vulnerabilities. Vulnerability analysis is commonly performed by comparing the services, applications, and operating systems for potential targets against a vulnerability database or using a tester’s own knowledge of vulnerabilities. Tools such as Metasploit from Rapid7 provide a database of known exploits, where you simply type in an identified vulnerability and find various weaponized exploits tied to the weakness. Figure 6-7 shows an example of searching for Apache Struts vulnerabilities within Metasploit. Notice how the number of available exploits expands beyond what can be displayed on the screen!

FIGURE 6-7 Various Apache Struts Exploits in Metasploit
Phase 3: Attack
Once targets are confirmed, the actual exploitation occurs during the attack phase. Remember that exploitation does not necessarily mean something bad has already occurred. Exploitation can open the path for malicious actions such as pushing a remote-access tool (RAT), ransomware, or other forms of malware to the system. An example of exploitation could be running an Armitage/Metasploit weaponized attack against a system that is vulnerable to an exploitation of Struts, as shown in Figure 6-8. The example shows a system has an open shell, meaning the attacker has full access to the compromised system. From this point, the attacker can perform a number of actions, including using this compromised system as a gateway into the network to perform a new attack against internal systems. In the example, the attacker showcases his or her level of access by running the whoami command.
FIGURE 6-8 Using Armitage to Exploit a Struts Vulnerability
In other cases, the action of exploitation causes negative results, such as exploitation of a website to take it offline, known as a denial-of-service attack. Another example could be overloading the memory of a switch to cause it to fall back into a hub-like state, allowing an attacker to view all traffic within that device. From a penetration testing viewpoint, using the Cyber Kill Chain is a good way to view the steps that would be involved with exploiting a target and delivering something, which are the same steps penetration testers and real attackers would use against a target. As a refresher from Chapter 1, Figure 6-9 depicts the Cyber Kill Chain. The attack phase of the NIST penetration testing process corresponds to the Delivery, Exploitation, Installation, and Command and Control phases of the Cyber Kill Chain.
FIGURE 6-9 Cyber Kill Chain Attack Lifecycle
Note
Kali Linux and BackBox are great free penetration operating system builds you can download and use for penetration testing efforts. Metasploit is a great resource you can test your attacks against in a free and legal manner.
Phase 4: Reporting
The results of the attack phase are documented in the final phase, the reporting phase. Reporting should also include steps from the other phases so the entire penetration testing process is documented. The language used in a report is extremely important, meaning you must know your target audience and consider the impact that will result based on who reviews the report. I have seen people lose their jobs based on negative feedback about their work or how they were blamed for the results of the penetration testing exercise. I recommend at a minimum that your penetration testing report contain the following information:
Vulnerabilities: What was found during the penetration test? List all vulnerabilities along with details about what they are.
Impact: What is the potential negative impact that could occur if a real attacker were to take advantage of a vulnerability found during the penetration testing exercise?
Likelihood: How hard is it to exploit an identified vulnerability? Do you need root access or connectivity to the internal network, or can anybody from anywhere access and exploit the vulnerability?
Risk evaluation: How do the identified vulnerabilities impact the overall business?
Recommendation: What is recommended to reduce the risk of the identified vulnerabilities?
References: Who was involved in the penetration testing exercise?
Additional details: Make sure to include any appendices, glossary items, tools used, and other details that would help the reader follow the penetration test report.
Note
SANS offers great resources for templates for penetration testing reports, at https://pen-testing.sans.org/resources/downloads.
Figure 6-10 shows a diagram of the NIST SP 800-115 four-stage penetration testing methodology, which is a high-level view of performing a penetration testing exercise.

FIGURE 6-10 NIST 800-115 Four-Stage Penetration Testing Methodology
Additional NIST SP 800-115 Guidance
NIST SP 800-115 provides much more detail as you read further into the document. For example, the attack stage of the NIST four-stage penetration testing methodology is further broken down into four steps, as shown in Figure 6-11. The first step is to gain access to the target, also known as establishing a foothold. It is possible that the current privilege level will be limited based on how the access was accomplished, so the next step would be to attempt to escalate privileges to a higher level, such as administrator-level access. Once the highest level of system access is achieved, the third step is to browse the system to discover mechanisms to gain access to other systems. The final step represents the results of the exploit, which might be installing a backdoor, removing data (or documenting the potential to do so), or repeating the process against other internal systems. This cycle is repeated until enough results are generated that can be recorded during the reporting stage of the NIST penetration testing methodology.

FIGURE 6-11 NIST 800-115 Attack Phase Details for Penetration Testing
Note
There are many other penetration testing resources available, including popular certification programs that train and test on core penetration testing skills, such as the Certified Ethical Hacker (CEH) certification program offered by EC-Council and the Offensive Security Certified Professional (OSCP) certification program.
Penetration Testing Types
Different types of penetration testing services are available and are differentiated based on the agreed-upon scope of the testing. It is common practice to scope a penetration test in a known environment, unknown environment, or partially known environment (prehistorically called white, black, or gray format). The following are definitions of each approach:
Known Enviroment: All information about the target is provided to the penetration tester. This includes its IP address, what software is running, who accesses the system, and other relevant information. A white-scoped penetration test is commonly performed by system owners responsible for the security of their systems.
Unknown Enviroment: No information about the target is provided to the penetration tester. It is up to the penetration tester to research anything within scope and discover any potential target as well as attack the target using any method within scope of the service.
Partially Known Enviroment: Some information about the target is provided to the penetration tester while other details are not. It is common to provide details that an attacker would find if they performed reconnaissance of a target, to reduce the time and cost of the penetration test. It is close to impossible to prevent adversaries from gathering intelligence about your organization using certain sources for their reconnaissance efforts, so some data exposure should be expected.
I recommend leveraging gray penetration testing services whenever using an external paid resource. You can assume and expect that adversaries are capable of researching your organization. Paying the penetration testing service to research your organization during a black-scoped penetration test can quickly increase the cost of the service while providing limited value.
Penetration Testing Planning
Beyond considering the type of penetration test to conduct, penetration testing planning includes other aspects to consider. The following list provides questions that need to be answered as you plan to perform a penetration test or request external penetration testing services. These questions would also need to be answered within any statement of work for a penetration testing service.
What is the scope of the penetration test?
What are the priorities for the penetration test?
Who is authorized to conduct the penetration test?
What are the data handling requirements?
What are the penetration test’s logistics?
Will the penetration test be internal or external?
How should sensitive data be handled?
What should occur in the event of an incident?
My recommendation is to develop the requirements for your penetration test and identify potential service providers or develop an internal team to provide the service. To ensure the service will meet your scope, you need to have a scoping meeting, where you meet with the penetration testing team and review the scope of work to ensure all parties understand what needs to be done and what is considered a successful service engagement.
The most important aspect of the service is what is delivered, commonly referred to as the penetration testing report. To ensure that the final penetration testing report contains everything you desire from the service provider, you need to specify everything that needs to be included in your scope of work. The scope of work is essential for identifying what is expected from the penetration testing team.
Penetration Testing Scope Template
Much like an assessment report, a penetration testing report should be based on the focus of the service. A report for a web application–focused penetration test will look different from a report for a social engineering–focused penetration test. There are industry guidelines for the deliverable report for the various forms of penetration testing services. Offensive Security (creators of Kali Linux) provides a good example of a penetration testing report at https://www.offensive-security.com/reports/sample-penetration-testing-report.pdf.
Earlier in this chapter, I pointed out that the value of a penetration test is based on the quality of the scope of work. It is absolutely critical to ensure the scope matches the desired outcome or you will not receive what you expect from the services. For example, I once delivered a penetration test in which I got access to the target’s network using social engineering, meaning I attacked the people’s trust and tricked them into giving me sensitive information. The organization, however, was expecting a technical penetration test, meaning they were only concerned about threats to their Internet-facing technology. The penetration testing scope of work did not specify the organization’s desired outcome, which led to my service meeting the scope but the results not satisfying the customer.
To help you avoid receiving an undesired outcome from a penetration test, I have provided a template for a scope of work. Use this template as a method to summarize the questions that I provided in the “Penetration Testing Planning” section of this chapter; also pay attention to the additional information I have included in the penetration scope template. The more details you include regarding what you expect from the service, the better results you should receive from the service, assuming the penetration testing team meets what you request in your scope statement.
Penetration Testing Scope Statement
[Provide an overview of the purpose for the service request and expected outcome.]
Penetration Test Pre-Planning
[Provide details about what needs to be done prior to the penetration test. Who needs to be notified? What technologies need to be available? What other actions need to be taken prior to the start of the penetration test?]
Team Location(s) |
Organization Location(s) |
Client Personnel Aware of Testing |
Resources Provided to Pentest Team |
Pentest Technologies Used |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
High-Level Work Schedule: Project Scope
Description of Work/Pentest Boundaries |
Assumptions and Constraints |
What is tested? What are the social engineering test boundaries? What is acceptable? What are the boundaries of physical security tests? What are the restrictions on invasive pentest attacks? What type of corporate policies affect your test? [Response] |
[Response] |
Milestones |
Due Dates |
[Response] |
[Response] |
ID |
Activity |
Resource |
Labor |
Material |
Total Cost |
|||||||
Hours |
Rate |
Total |
Units |
Cost |
Total |
|||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
Appropriate Authorization (Including Third-Party Authorization)
[List anybody who is authorized to perform the penetration test. Anybody outside of these people are considered not authorized and would be representing a real threat to the organization.]
Name |
Title/Organization |
Description of Authorization and Consent (Identify Reference Documents) |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
[Response] |
Reconnaissance Pentest Activities
[Provide any requirements for reconnaissance activities. For gray or white penetration testing, certain reconnaissance action items can be removed, and the results can be provided to the penetration testing team. This will reduce the cost of the services based on the assumption that certain reconnaissance details are publicly available to real threats.]
Pentest Scanning Activities
[Provide any requirements for evaluating targets.]
Scanning Test Deliverable Name |
Scanning Test Deliverable Description |
[Response] |
[Response] |
[Response] |
[Response] |
Gaining Access Activities
[Provide what is permitted once access to a target is possible.]
Gaining Access Activity Name |
Gaining Access Activity Description |
[Response] |
[Response] |
[Response] |
[Response] |
Maintaining Access Activities
[Provide what is permitted to maintain access on a target, commonly called establishing a foothold.]
Maintaining Access Activity Name |
Maintaining Access Activity Description |
[Response] |
[Response] |
[Response] |
[Response] |
Covering Tracks Activities
[Provide what is within scope for removing the footprint caused during the previous exploitation steps.]
Covering Tracks Activity Name |
Covering Tracks Activity Description |
[Response] |
[Response] |
[Response] |
[Response] |
Pentest Analysis and Report Planning
[Provide an explanation regarding what outcome and details need to be included in the penetration test final report. Include whether you require recommendations for risk reduction, screenshots of the tasks performed, or any other details regarding what will enable your organization to use the report to improve its security.]
Describe Plan for Analyzing and Reporting Pentest Results |
[Response] |
All compliance concepts covered in this chapter thus far have been based on policy and procedures, also known as an organization’s process. Processes are developed at the discretion of the organization and made into a required rule or policy that must be followed based on the details in any supporting procedure documentation. There are certain compliance requirements that are mandatory, regardless of whether the organization has a policy in place to enforce it. Not meeting certain types of required industry compliance can result in fines and other negative outcomes. The final topic for this chapter is reviewing required industry compliance.
Industry Compliance
Most industries are required to comply with specific laws, standards, and/or regulations mandated by legislatures, government agencies, or industry regulators. Violations of government requirements are considered breaking the law, with repercussions ranging from fines to jail time. The reason behind government-enforced laws is to protect those that are associated with what is being protected, which is a good thing. For example, HIPAA protects people’s privacy, particularly their health information. If a company in the health care industry fails to protect its customers’ privacy, HIPAA requirements can be enforced by the government with strong repercussions if they are not followed, forcing the proper security controls to be put in place.
Industry services also have similar goals for enforcing requirements. Industry regulators don’t have the power to assess legal penalties; however, they have other methods to encourage following their policies, including reduction of allowed services as well as requirements for passing audits before services are reinstated. For example, most people have credit cards, which if stolen would mean access to their protected data. When people use credit cards to purchase something, they want to have confidence that their data will not be used inappropriately. If a company fails to protect a customer’s credit card data, it’s the buyer that is exposed to risk because their financial and other personal data is what is impacted.
Laws such as HIPAA as well as industry service requirements such as PCI DSS force any affected organization to enforce security best practices to protect the people that could be impacted by a breach, which in the example of PCI DSS are the customers using their credit cards with a vendor, and with HIPAA is the customers’ privacy. Without these requirements, organizations would use less secure methods to protect credit card and privacy data, causing an increase in data theft and a decrease in customer trust of the credit card network and health care services that contain private data.
Compliance Requirements
There are a handful of government-enforced laws and industry requirements that your organization will need to be aware of depending on your line of business. It is also good to know when other organizations must meet an industry compliance requirement as well. Looking back at the PCI DSS example, I once received my credit card receipt at a restaurant and saw that my entire credit card number was printed on it, a violation of PCI DSS. I could’ve reported the violation to my credit card company, but I chose to inform the manager about the issue. According to PCI DSS, the restaurant should have printed only the last four digits of my credit card number on the receipt, sufficient to enable me to confirm the credit card number charged is the one I used; however, the remaining data is protected. I recommend including considerations of who you do business with based on if they meet required industry compliance.
Note
It is common practice for organizations to advertise that they meet various types of industry compliance, with the goal of gaining the confidence of potential customers. For example, an organization might advertise on its website that it follows secured supply chain or software development best practices when creating products.
The following are some of the most commonly required industry compliance standards and laws that your organization, or organizations you do business with, may be required to follow:
PCI: The PCI Data Security Standards help protect the safety of that data. They set the operational and technical requirements for organizations accepting or processing payment transactions, and for software developers and manufacturers of applications and devices used in those transactions.
Note
Learn more about PCI at https://www.pcisecuritystandards.org/pci_security/maintaining_payment_security.
HIPAA: The Health Insurance Portability and Accountability Act of 1996 developed regulations for protecting the privacy and security of health information. This rule applies to health plans, health care clearinghouses, and any health care provider who transmits health information in electronic form, including business associates. The HIPAA Security Rule is broken down into safeguard categories. Technical safeguards evaluate technology that is in contact with HIPAA-protected data. HIPAA also references other guidelines within its technical safeguards, such as what can be found within various NIST standards for what it considers acceptable encryption standards. Physical safeguards target risk to physically accessing HIPAA-protected data and systems with HIPAA data. Topics include inventory of hardware and physical security concepts. Administrative safeguards address policies and procedures and bring privacy rules and security rules together. For example, conducting risk assessments allows an organization to address vulnerabilities in both physical and technical systems. Other administrative topics include developing policies and procedures according to industry-recommended best practices.
The U.S. Department of Health and Human Services offers various checklists at HHS.gov that you can use to audit your organization for HIPAA compliance. It is up to your organization to validate and meet HIPAA compliance requirements to avoid fines and other negative outcomes.
Note
You can download HHS’s summary of the HIPAA Privacy Rule at https://www.hhs.gov/sites/default/files/ocr/privacy/hipaa/understanding/summary/privacysummary.pdf.
SOX: Sarbanes-Oxley Act of 2002, better known as SOX, focuses on corporate fraud by requiring all publicly held companies to enact internal checks and balances and procedures for financial reporting. CEOs and CFOs are directly responsible for the accuracy, documentation, and submission of all financial reports and can be penalized for failure to comply regardless of whether it is intentional or not. SOX also has data security requirements, including use of SOX-compliant software. It is up to your organization to identify if you have SOX obligations and, if so, to meet compliance requirements.
FISMA: The Federal Information Security Modernization Act of 2014 protects U.S. government data and compliance with it is mandatory for all U.S. federal agencies as well as contractors that wish to do business with a U.S. federal agency. To comply with FISMA, organizations must follow FIPS 199, FIPS 200, and the NIST 800 series guidelines. The top areas of focus that must be met are as follows: maintain an information system inventory; categorization of systems based on risk; develop and maintain a security plan; adhere to NIST SP 800-53 security controls; conduct risk assessments according to NIST SP 800-30; and have annual certification and accreditation of systems. Penalties for failing compliance can include censure by Congress, a reduction in federal funding, and reputational damage. If you work for the U.S. government or plan to do business with a U.S. government entity, you must follow FISMA compliance requirements.
Note
Learn more about FISMA at https://www.dhs.gov/cisa/federal-information-security-modernization-act.
FedRAMP: The Federal Risk and Authorization Management Program is another U.S. government-wide program and compliance with it is required for any government agency leveraging cloud technology. FedRAMP provides steps for performing security assessments, authorization, and continuous monitoring of cloud products and services. FedRAMP, like FISMA, uses the NIST SP 800-53 security controls for its blueprint. Cloud services must have their security assessed and be granted an Agency Authority to Operate (ATO) or Provisional Authority to Operate (P-ATO) in order to be accepted by a government agency, unless a special exception is granted. If you work for a U.S. government agency or plan to do business with a government agency using cloud-based technology, you need to follow FedRAMP requirements.
Note
You can learn more about FedRAMP at https://www.fedramp.gov/faqs/.
Data sovereignty laws: Data sovereignty is a country-specific requirement mandating that data is subject to the laws of the country in which it is collected or processed as well as must remain within its borders. Many countries have had data sovereignty laws for decades; however, new privacy laws are making data sovereignty requirements more public. Countries such as Russia, China, Germany, France, Indonesia, and Vietnam require that their citizens’ data must be stored on physical services within the country’s borders, meaning data can’t exist in a cloud service outside the physical country. The reason for these laws is that countries are concerned about data being misused when it leaves their borders because, technically, they are no longer legally able to protect such data. An example where data sovereignty will come into play is cloud services that have data warehouses located around the world. Organizations that must meet their government’s data sovereignty requirements will need evidence that their data will be stored only within data warehouses residing within their country or they will not be permitted to use the cloud service. It is up to the organization to identify and adhere to any data sovereignty requirements, which will vary from country to country.
Industry-specific compliance requirements: Your organization might be required to comply with one or more requirements specific to its industry. As an example of a compliance requirement specific to the energy industry, I’ll briefly mention NERC CIP. The North American Electric Reliability Corporation (NERC) has been in charge of maintaining the operations and functions of bulk power systems, more commonly called the electric grid, since the early 1960s. In 2008, NERC developed the Critical Infrastructure Protection (CIP) compliance framework, made up of 11 control families, to mitigate cybersecurity attacks on the electric grid. There are useful general recommendations as well as those that are very specific to the security of bulk power systems. The framework can be found at https://www.nerc.com/pa/Stand/Pages/CIPStandards.aspx.
Note
I included NERC CIP as an example of a very specific industry compliance requirement. Industries such as manufacturing, education, and government also have industry-specific certifications. PCI DSS is a specific service requirement, meaning you only need to follow PCI DSS if you are involved with credit card services. I recommend consulting with a compliance specialist if you are unaware of all compliance requirements your organization is obligated to follow.
Summary
Meeting compliance is essential to any successful cybersecurity program. This chapter started by describing how to develop and maintain policies and procedures, which are the ingredients of an organization’s process. Next, it covered how to evaluate existing policies and procedures through the use of a tabletop exercise. You then learned how standards, guidelines, and frameworks are resources that your organization can use to build or tune your policies and procedures; although following such resources is not required, they often represent industry best practices. Next, this chapter looked at how to meet compliance using audits as well as how to exceed compliance by focusing on all risk using assessments and penetration testing. Finally, this chapter surveyed several common legal and industry-based compliance requirements that might apply to your organization, depending on the nature of its operations.
Remember that compliance can only be met or not met in perspective of the entity enforcing the compliance; however, meeting compliance does not mean you are secure. Many organizations will continue to operate while they are not compliant as long as they have a plan in place to eventually become compliant, which not only increases the risk of compromise but also demonstrates a lack of focus for meeting what needs to be considered the bare minimal effort to be secure. Exceeding compliance means to not only meet compliance, but also to evaluate all risk, with a focus on actually securing the organization. Make sure to include both meeting compliance and security goals as part of how you establish your security baseline. This will result in your organization not only exceeding compliance, but also reducing the risk of a future compromise within your people, process, and technology.
Chapter 7 dives into an extremely useful resource for securing your organization against attacks, known as threat intelligence.
References
Archieve360 Team. (2019, February 14). Data Sovereignty and the GDPR; Do You Know Where Your Data Is? Archive360. https://www.archive360.com/blog/data-sovereignty-and-the-gdpr-do-you-know-where-your-data-is
California Association of Health facilities. (n.d.). Discussion Based Tabletop Exercise: Design Template & Documentation. CAHF. http://www.ndltca.org/image/cache/Tabletop_Exercise_Template.pdf
CIS. (2018, October 18). Tabletop Exercises: Six Scenarios to Help Prepare Your Cybersecurity Team. CIS. https://www.cisecurity.org/wp-content/uploads/2018/10/Six-tabletop-exercises-FINAL.pdf
FIRST.org, Inc. (2019, November). Computer Security Incident Response Team (CSIRT) Services Framework Version 2.1.0. FIRST.org, Inc. https://www.first.org/standards/frameworks/csirts/FIRST_CSIRT_Services_Framework_v2.1.0.pdf
Gitanjali, M. (2018, May 2). A Security Assessment Template for Small Businesses: Evaluate Your IT Security. GetApp. https://lab.getapp.com/security-assessment-template-for-small-businesses/
LaBoissonnière, L. (2018, February 2). Be Diligent: 5 Practical Steps to Enforceable Workplace Policies. McInnes Cooper. https://www.mcinnescooper.com/publications/be-diligent-5-practical-steps-to-enforceable-workplace-policies/
National Institute of Standards and Technology. (2018, April 16) Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1. NIST. https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
North American Electric Reliability Corporation. Critical Infrastructure Protection (CIP) Standards. NERC. https://www.nerc.com/pa/Stand/Pages/CIPStandards.aspx
Oltsik, J. (2018, January 11). Research Suggests Cybersecurity Skills Shortage Is Getting Worse. CSO. https://www.csoonline.com/article/3247708/security/research-suggests-cybersecurity-skills-shortage-is-getting-worse.html
SANS. (2020). Security Policy Templates. SANS. https://www.sans.org/information-security-policy/
Vlallno, B. (2014, October 27). 6 Tips for Effective Security Tabletop Testing. CSO. https://www.csoonline.com/article/2838365/planning-for-a-security-emergency-from-the-tabletop-down.html
