Chapter 1
Comparing and Contrasting Different Types of Social Engineering Techniques
This chapter covers the following topics related to Objective 1.1 (Compare and contrast different types of social engineering techniques) of the CompTIA Security+ SY0-601 certification exam:
Phishing
Smishing
Vishing
Spam
Spam over internet messaging (SPIM)
Spear phishing
Dumpster diving
Shoulder surfing
Pharming
Tailgating
Eliciting information
Whaling
Prepending
Identity fraud
Invoice scams
Credential harvesting
Reconnaissance
Hoax
Impersonation
Watering hole attack
Typo squatting
Pretexting
Influence campaigns (hybrid warfare and social media)
Principles of social engineering and reasons for effectiveness (including Authority, Intimidation, Consensus, Scarcity, Familiarity, Trust, and Urgency)
Social engineering attacks leverage the weakest link, which is typically the human user. If an attacker can get a user to reveal information, it is much easier for the attacker to cause harm than it is by using some other method of reconnaissance. Social engineering can be accomplished through email or misdirection of web pages, prompting a user to click something that leads to the attacker gaining information. Social engineering can also be done in person by an insider or an outside entity or over the phone.
This chapter delves into the methods and techniques that social engineers can employ to gain access to buildings and systems and obtain company data and personal information. It also covers the various ways that these social engineers can be defeated.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read this entire chapter thoroughly or jump to the “Chapter Review Activities” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 1-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 1-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
|---|---|
Social Engineering Fundamentals |
1–9 |
User Security Awareness Education |
10 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. An attacker sends a targeted email with a malicious attachment to a user in your company. This attacker researched public information about the user to send a “more personal” and targeted email to the user. Which of the following is this type of attack?
Spear phishing
Typo squatting
Pharming
None of these answers are correct.
2. Which of the following is an example of a tool that can be used specifically to perform social engineering attacks?
Maltego
SET
The Harvester
Recon-NG
3. Which of the following best describes the difference between smishing and vishing?
Vishing is a social engineering attack in which the attacker calls the user over the phone and then persuades the user to reveal sensitive information or perform a given action. Smishing is a type of phishing campaign using SMS text messages instead of email.
Vishing is a social engineering attack in which the attacker leaves a voicemail and then persuades the user to reveal sensitive information or perform a given action. Smishing is a type of typo squatting and pharming campaign using Bluetooth.
Vishing is a social engineering attack in which the attacker leaves a voicemail and then persuades the user to reveal sensitive information or perform a given action. Smishing is a type of typo squatting and pharming campaign using short Internet messaging systems.
None of these answers are correct.
4. A(n) ______ is a small space that can usually only fit one person, used to combat tailgating.
tunnel-gap
tunnel-trap
piggyback
access control vestibule
5. Which of the following best describes pretexting?
Impersonation
Social engineering
Whaling
Pharming
6. Which of the following refers to the act of incorporating malicious ads on trusted websites, which results in users’ browsers being inadvertently redirected to sites hosting malware?
Malvertising
Pharming
Active ad exploitation
Whaling
7. Which of the following is true about spear phishing?
Spear phishing attacks use the Windows Administrative Center.
Spear phishing attacks are phishing attempts that are constructed in a very specific way and directly targeted to specific individuals or companies.
Spear phishing, whaling, and phishing are the same type of attack.
Spear phishing attacks use the Windows PowerShell.
8. Derek is the CEO of a Fortune 500 company. He received an email with a malicious attachment. Once Derek clicked on the attachment, malware was installed on his system. Which of the following best describes this attack?
Smishing
Vishing
Whaling
Pretexting
9. Which of the following is true about social engineering motivation techniques?
Social proof can be used to create a feeling of urgency in a decision-making context. It is possible to use specific language in an interaction to present a sense of urgency and manipulate the victim.
Scarcity can be used to create a feeling of urgency in a decision-making context. It is possible to use specific language in an interaction to present a sense of urgency and manipulate the victim.
Scarcity cannot be used to create a feeling of urgency in a decision-making context. It is possible to use specific language in an interaction to present a sense of urgency and manipulate your victim.
Social proof cannot be used in an interrogation because it is illegal. It is not legal to use specific language in an interaction to present a sense of urgency and manipulate your victim.
10. Which of the following recommendations can be used in user security awareness education?
Adhere to the organization’s clean desk policy, which states that all documents, electronics, personally owned devices, and other items be put away (or locked away) when the user is not at his or her desk, or other work area.
Always screen your email and phone calls carefully and keep a log of events. This is also known as communications vetting.
Use encryption when possible to protect emails, phone calls, and data.
All of these answers are correct.
Foundation Topics
Social Engineering Fundamentals
Let’s discuss a low note in our society. Because that is what information security–based social engineering is—a low form of behavior, but an effective one. It is estimated that 1 out of 10 people is conned every year through social engineering methods, and as many as half of them don’t even know it has occurred. It’s glorified in the movies, but in real life it can have devastating consequences to an organization and to innocent individuals.
Social engineering is the act of manipulating users into revealing confidential information or performing other actions detrimental to the user. Examples of social engineering are common in everyday life. A basic example would be a person asking for your username and password over the phone; often the person uses flattery to gain information. Malicious people use various forms of social engineering in an attempt to steal whatever you have of value: your money, information, identity, confidential company data, or IT equipment.
A primary example is attackers leveraging normal user behavior. Suppose that you are a security professional who is in charge of the network firewalls and other security infrastructure equipment in your company. An attacker could post a job offer for a very lucrative position and make it very attractive to you, the victim. Suppose the job description lists benefits and compensation far beyond what you are already making at your company. You decide to apply for the position. The criminal (attacker) then schedules an interview with you. Because you are likely to “show off” your skills and work, the attacker may be able to get you to explain how you have configured the firewalls and other network infrastructure devices for your company. You might disclose information about the firewalls used in your network, how you have configured them, how they were designed, and so on. Your answers give the attacker a lot of knowledge about the organization without requiring the attacker to perform any type of scanning or reconnaissance on the network.
Let’s take a look at another example: suppose that you are a security guard and a pregnant woman comes to you saying that she is feeling sick and that she needs a bathroom immediately. You are courteous and escort her to the bathroom inside your premises, where she then uses her laptop to connect to your Wi-Fi or put a wireless rogue access point (AP) to lure some of your users to connect to such an AP. We are good and kind people (most of the time) and will continue to be the weakest link in the cybersecurity world because this human nature becomes our weakness.
Social engineers will rely on information. For example, open-source intelligence (OSINT) is a way that attackers can gain knowledge about a target. OSINT includes media, public government data, commercial data, and academic publications. You will learn additional details about OSINT in Chapter 5, “Understanding Different Threat Actors, Vectors, and Intelligence Sources.”
Tip
You can find several references to tools that can be used for OSINT reconnaissance at my GitHub repository: https://github.com/The-Art-of-Hacking/h4cker. This GitHub repository has thousands of cybersecurity references that can be very helpful for this certification and many others.
The main reason that social engineering succeeds is a lack of user awareness. But social engineering can also be effective in environments in which the IT personnel have little training, and in public areas—for example, public buildings with shared office space. Let’s discuss some of the more common types of social engineering.
Common social engineering techniques include the following:
Phishing and spear phishing
Smishing
Vishing
Spam
Spam over Internet messaging (SPIM)
Dumpster diving
Shoulder surfing
Pharming
Tailgating
Eliciting information
Whaling
Prepending
Identity fraud
Invoice scams
Credential harvesting
Reconnaissance
Hoax
Impersonation or pretexting
Eavesdropping
Baiting
Watering hole attack
Typo squatting

Phishing and Spear Phishing
Phishing is the attempt at fraudulently obtaining private information. A phisher usually masquerades as someone else, perhaps another entity. There are two main differences between phishing and pretexting. Pretexting is the act of impersonating or “spoofing” someone else’s identity. For example, an attacker could impersonate an employee of a company or a business partner to attempt to steal sensitive data from the victim. Phishing is usually done by electronic communication, not in person. Second, little information about the target is necessary. A phisher might target thousands of individuals without much concern as to their background. An example of phishing would be an email that requests verification of private information. The email probably leads to a malicious website designed to lure people into a false sense of security to fraudulently obtain information. The website often looks like a legitimate website. A common phishing technique is to pose as a vendor (such as an online retailer or domain registrar) and send the target email confirmations of orders that they supposedly placed.
This is a triple-whammy. First, the orders are obviously fake; a person might say, “Hey, wait! I didn’t place these orders!” and perhaps click the link(s) in the email, leading the person to the false web page. Second, if a person thinks it’s a legitimate order (perhaps the person does many orders, and the fraudulent one looks like another legitimate one), the person might click a link to track the order, again leading to the bogus web page. Third, once at the web page, the person is asked to enter credentials for an account (which then leads to credit card fraud and ID theft), and in addition to that the page might have Trojans and other malicious scripts that are delivered to the unsuspecting person on exit. Sheesh, talk about cyberbullying!
Generally, no information about the target is necessary for a phishing attack. However, some “phishermen” actually target specific groups of people or even specific individuals. This is known as spear phishing. And when an attacker targets key stakeholders and senior executives (CEOs, CFOs, and so on), it is known as whaling. Whaling attacks are much more detailed and require that the attacker know a good deal of information about the target (much of which is freely available on the Internet).
Many different types of social engineering are often lumped into what is referred to as phishing, but actual phishing for private information is normally limited to email and websites.
Several open-source tools can help automate or accelerate a social engineering attack (including sending phishing and spear phishing emails). An example of these tools (and one of the most popular) is the Social Engineering Toolkit (SET). Example 1-1 demonstrates how attackers can use SET to send spear phishing emails to a victim and either select existing payloads or create their own.
Example 1-1 The Social Engineering Toolkit
[---] The Social-Engineer Toolkit (SET) [---]
[---] Created by: David Kennedy (ReL1K) [---]
Version: 8.0.3
Codename: 'Maverick'
[---] Follow us on Twitter: @TrustedSec [---]
[---] Follow me on Twitter: @HackingDave [---]
[---] Homepage: https://www.trustedsec.com [---]
Welcome to the Social-Engineer Toolkit (SET).
The one stop shop for all of your SE needs.
The Social-Engineer Toolkit is a product of TrustedSec.
Visit: https://www.trustedsec.com
It's easy to update using the PenTesters Framework! (PTF)
Visit https://github.com/trustedsec/ptf to update all your tools!
Select from the menu:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) Third Party Modules
99) Return back to the main menu.
set> 1
The Spearphishing module allows you to specially craft email messages
and send them to a large (or small) number of people with attached
fileformat malicious payloads. If you want to spoof your email
address, be sure "Sendmail" is installed (apt-get install sendmail)
and change the config/set_config SENDMAIL=OFF flag to SENDMAIL=ON.
There are two options, one is getting your feet wet and letting SET
do everything for you (option 1), the second is to create your own
FileFormat payload and use it in your own attack. Either way, good
luck and enjoy!
1) Perform a Mass Email Attack
2) Create a FileFormat Payload
3) Create a Social-Engineering Template
99) Return to Main Menu
set:phishing>1
/usr/share/metasploit-framework/
Select the file format exploit you want.
The default is the PDF embedded EXE.
********** PAYLOADS **********
1) SET Custom Written DLL Hijacking Attack Vector (RAR, ZIP)
2) SET Custom Written Document UNC LM SMB Capture Attack
3) MS15-100 Microsoft Windows Media Center MCL Vulnerability
4) MS14-017 Microsoft Word RTF Object Confusion (2014-04-01)
5) Microsoft Windows CreateSizedDIBSECTION Stack Buffer Overflow
6) Microsoft Word RTF pFragments Stack Buffer Overflow (MS10-087)
7) Adobe Flash Player "Button" Remote Code Execution
8) Adobe CoolType SING Table "uniqueName" Overflow
9) Adobe Flash Player "newfunction" Invalid Pointer Use
10) Adobe Collab.collectEmailInfo Buffer Overflow
11) Adobe Collab.getIcon Buffer Overflow
12) Adobe JBIG2Decode Memory Corruption Exploit
13) Adobe PDF Embedded EXE Social Engineering
14) Adobe util.printf() Buffer Overflow
15) Custom EXE to VBA (sent via RAR) (RAR required)
16) Adobe U3D CLODProgressiveMeshDeclaration Array Overrun
17) Adobe PDF Embedded EXE Social Engineering (NOJS)
18) Foxit PDF Reader v4.1.1 Title Stack Buffer Overflow
19) Apple QuickTime PICT PnSize Buffer Overflow
20) Nuance PDF Reader v6.0 Launch Stack Buffer Overflow
21) Adobe Reader u3D Memory Corruption Vulnerability
22) MSCOMCTL ActiveX Buffer Overflow (ms12-027)
set:payloads>
Note
SET and other penetration testing tools are not covered in the exam. The instance provided in Example 1-1 is for your reference only. SET and similar tools can be installed in different Linux distributions. Some of the most popular Linux distributions for security penetration testing are Kali Linux, Parrot Security, and Black Arch.
To defend against this, users should install a phishing filter or add-on and enable it on the web browser. Also, a person should be trained to realize that institutions will not call or email requesting private information. If people are not sure, they should hang up the phone or simply delete the email. A quick way to find out whether an email is phishing for information is to hover over a link. You will see a URL domain name that is far different from that of the institution that the phisher is claiming to be, probably a URL located in a distant country. Many of these phishers are also probably engaging in spy-phishing: a combination of spyware and phishing that effectively makes use of spyware applications. A spyware application of this sort is downloaded to the target, which then enables additional phishing attempts that go beyond the initial phishing website.

Smishing
Because phishing has been an effective tactic for threat actors, they have found ways other than using email to fool their victims into following malicious links or activating malware from emails. A number of phishing campaigns have used Short Message Service (SMS) to send malware or malicious links to mobile devices. This social engineering technique is also known as smishing (short for SMS phishing).
One example of SMS phishing is the Bitcoin-related SMS scams that have surfaced in recent years. Numerous victims have received messages instructing them to click links to confirm their accounts and claim Bitcoins. When a user clicks such a link, he or she might be fooled into entering sensitive information on that attacker’s site.

Vishing
Phishing attacks can also be accomplished by telephone conversations. Phone or voice phishing, known as vishing, works in the same manner as phishing but is initiated by a phone call (often using VoIP systems). Vishing is typically used to steal sensitive information such as Social Security numbers, credit card numbers, or other information used in identity theft schemes. Attackers might impersonate and spoof caller ID to obfuscate themselves when performing voice phishing attacks.
In many vishing attacks, the phone call often sounds like a prerecorded message from a legitimate institution (bank, online retailer, donation collector, and so on). The message asks the unsuspecting person for confidential information such as name, bank account numbers, codes, and so on—all under the guise of needing to verify information for the person’s protection. It’s really the opposite, of course, and many people are caught unaware by these types of scams every day. Through the use of automated systems (such as the ones telemarketers use), vishing can be perpetuated on large groups of people with little effort.
Note
A similar technique using automated systems is known as war-dialing. This type of attack occurs when a device (modem or other system) is used to scan a list of telephone numbers and dial them in search of computer systems and fax machines. The technique sifts out the phone numbers associated with voice lines and the numbers associated with computers. The result is a list that can later be used by other attackers for various purposes.
Spam and Spam over Internet Messaging (SPIM)
Spam has traditionally been the term used to describe unwanted and unsolicited email messages. However, email messages are not the only way that attackers or malicious users send spam. Users may also receive spam (numerous messages) via social media sites and instant/Internet messaging applications. For instance, you can be talking to other security professionals over a Discord server and someone may hop on the server and send dozens of unwanted messages, sometimes protesting against something. A better example is receiving unwanted messages and scam offers via your Facebook Messenger, WhatsApp, Keybase, Signal, WeChat, Telegram, or any other instant messaging application.
Tip
Several free services enable you to obtain DNS-based blocking lists of spammers, as well as ways that you can report spam events. An example is SpamCop (https://www.spamcop.net).

Dumpster Diving
When a person literally scavenges for private information in garbage and recycling containers, that is known as dumpster diving. Any sensitive documents should be stored in a safe place as long as possible. When they are no longer necessary, they should be shredded. (Some organizations incinerate their documents.) Information might be found not only on paper but also on hard drives or removable media. Chapter 15, “Understanding the Importance of Physical Security Controls,” covers proper recycling and/or destruction of hard drives in more detail.

Shoulder Surfing
Shoulder surfing occurs when a person uses direct observation to find out a target’s password, PIN, or other such authentication information. The simple resolution for this type of behavior is for the user to shield the screen with privacy screens or filters, keypads, or other authentication-requesting devices. A more aggressive approach is to courteously ask the suspected shoulder surfer to move along. Also, private information should never be left on a desk or out in the open. Computers should be locked or logged off when the user is not in the immediate area. From a more technical perspective, password masking can be implemented (if not already), where typed passwords appear only as asterisks or dots on the screen. Always check if your systems, applications, and devices use password masking. Some lesser devices (such as SOHO routers) may not implement password masking by default, and that might go against company policy due to the inherent lack of security. Shoulder surfing, along with eavesdropping, and dumpster diving are examples of no-tech hacking.

Pharming
Pharming is the term used to describe a threat actor redirecting a victim from a valid website or resource to a malicious one that could be made to appear as the valid site to the user. From there, an attempt is made to extract confidential information from the user or to install malware in the victim’s system. Pharming can be done by altering the hosts file on a victim’s system, through DNS poisoning, or by exploiting a vulnerability in a DNS server.
Figure 1-1 illustrates the mechanics of how pharming works.
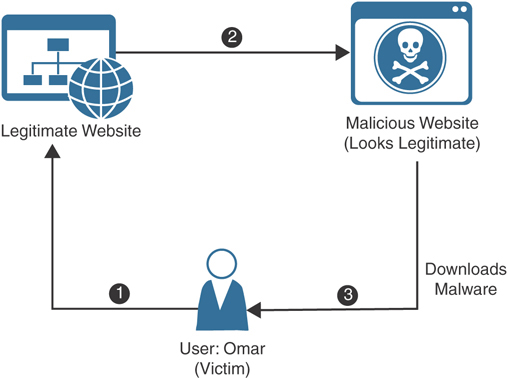
FIGURE 1-1 Pharming Example
The following steps are illustrated in Figure 1-1:
The user (Omar) visits a legitimate website and clicks a legitimate link.
Omar’s system is compromised, the hosts file is modified, and Omar is redirected to a malicious site that appears to be legitimate. (This could also be accomplished by compromising a DNS server or spoofing a DNS reply.)
Malware is downloaded and installed on Omar’s system.

Piggybacking or Tailgating
When an unauthorized person tags along with an authorized person to gain entry to a restricted area—usually with the person’s consent—that person is piggybacking. Tailgating is essentially the same with one difference: it is usually without the authorized person’s consent. Both of these attacks can be defeated through the use of access control vestibules (formerly known as mantraps). An access control vestibule is a small space that can usually fit only one person. It has two sets of interlocking doors; the first set must be closed before the other will open, creating a sort of waiting room where people are identified (and cannot escape!). This technique is often used in server rooms and data centers. Multifactor authentication is often used in conjunction with an access control vestibule; for example, using a proximity card and PIN at the first door and using a biometric scan at the second. An access control vestibule is an example of a preventive security control. Turnstiles, double entry doors, and security guards are other less expensive (and less effective) solutions to the problem of piggybacking and tailgating and help address confidentiality in general.

Eliciting Information
Key components of social engineering are how someone influences, interrogates, and impersonates others. In short, eliciting information is the act of gaining knowledge or information from people. In most cases, an attacker gets information from the victim without directly asking for that particular information.
How an attacker interrogates and interacts with a victim is crucial for the success of the social engineering campaign. An interrogator can ask good open-ended questions to learn about an individual’s viewpoints, values, and goals. The interrogator can then use any information revealed to continue to gather additional information or to obtain information from another victim.
It is also possible for an interrogator to use closed-ended questions to get more control of the conversation and to lead the conversation or to stop the conversation. Asking too many questions can cause the victim to shut down the interaction, and asking too few questions might seem awkward. Successful social engineering interrogators use a narrowing approach in their questioning to gain the most information from the victim.
Interrogators pay close attention to the following:
The victim’s posture or body language
The coloring of the victim’s skin, such as the victim’s face color becoming pale or red
The direction of the victim’s head and eyes
Movement of the victim’s hands and feet
The victim’s mouth and lip expressions
The pitch and rate of the victim’s voice, as well as changes in the voice
The victim’s words, including their length, the number of syllables, dysfunctions, and pauses
With pretexting—or impersonation—an attacker presents as someone else in order to gain access to information. In some cases, this type of social engineering attack can be very simple, such as quickly pretending to be someone else within an organization; in other cases, it can involve creating a whole new identity and then using that identity to manipulate the receipt of information. Social engineers might use pretexting to impersonate individuals in certain jobs and roles, even if they do not have experience in those jobs or roles.
For example, a social engineer might impersonate an IT support worker and provide unsolicited help to a user. Impersonating IT staff can be very effective because if you ask someone if he or she has a technical problem, it is quite likely that the victim will think about it and say something like, “Yes, as a matter of fact…yesterday, this weird thing happened to my computer.” Impersonating IT staff can give an attacker physical access to systems in the organization. The attacker who has physical access can use a USB stick containing custom scripts to compromise a computer within seconds.

Whaling
Whaling is similar to phishing and spear phishing; however, with whaling, the attack is targeted at high-profile business executives and key individuals in a corporation. So, what is the difference between whaling and spear phishing? Like threat actors conducting spear phishing attacks, threat actors conducting whaling attacks also create emails and web pages to serve malware or collect sensitive information; however, the whaling attackers’ emails and pages have a more official or serious look and feel. Whaling emails are designed to look like critical business emails or something from someone who has legitimate authority, either externally or even internally in the company itself. In whaling attacks, web pages are designed to specifically address high-profile victims. In a regular phishing attack, the email might be a faked warning from a bank or service provider. In whaling attacks, the email or a web page would be created with a more serious executive-level form. The content is created to target an upper manager, such as the CEO, or an individual who might have credentials for valuable accounts within the organization. In summary, a whaling attack takes additional steps to target and entice higher-profile victims.
The main goal in whaling attacks is to steal sensitive information or compromise the victim’s system and then target other key high-profile victims.
Attackers could use multifaceted attacks (also known as combined social engineering attacks). For instance, an attacker could send a spear-phishing email to a victim and then follow up with a phone call. This makes the attack even more effective.

Prepending
You can often configure your email servers or email cloud services to prepend a message in the email subject line to identify emails that are coming from outside of the organization. This technique is also known as prepending. For example, the subject line of an email could read something like this:
Subject: "[EXTERNAL] Order Update"

Identity Fraud
Social engineering has been used by many threat actors and scammers to steal sensitive information to then open new bank accounts, make purchases, and get tax refunds, among many other scenarios. The United States Federal Trade Commission (FTC) created an educational website to help you report and recover from identity theft at https://www.identitytheft.gov. Other countries have similar websites and resources.
As stated by the United States FTC, “There are many ways that you might discover that someone is using your information. You might get a notice from the IRS or find unfamiliar accounts on your credit report. You might notice strange withdrawals from your bank account, get bills that aren’t yours, or get calls about debts that you don’t owe.”

Invoice Scams
Many scammers continue to send unsolicited emails and other messages to victims that include “an invoice” (as a malicious attachment) for something that they have not purchased. For instance, a scammer might send you a targeted email message including an invoice for something that you most likely have purchased in the past. The scammer may look for information about you (using OSINT) and then send a targeted email with such an invoice. For example, the attacker/scammer may have found your LinkedIn profile and then will send an email with a fake invoice from LinkedIn. Because you use that service, you might be more susceptible to click on that attachment and, subsequently, for your system to get compromised.

Credential Harvesting
Nowadays, you hear about a new breach pretty much on a daily basis. In many cases, attackers dump user credentials in sites like Pastebin, GitHub, and many others. Consequently, it is easier for attackers to compromise systems because users reuse their usernames and passwords to authenticate to other sites and systems. Credential harvesting (often called account harvesting) refers to the attacking technique or activities of grabbing legitimate usernames and even passwords to gain access to systems to steal information or to use them for malicious purposes.

Reconnaissance
Threat actors obtain many details about their victims before launching an attack. They can do this by actively performing scans of systems and networks (active reconnaissance). However, threat actors can also leverage open-source intelligence (OSINT) or human intelligence (HUMINT) to potentially obtain sensitive information from a target without the need of using active scans or sending any packets to the targeted network and underlying systems (this is referred to as passive reconnaissance).
Tip
The MITRE Corporation (MITRE) is a United States government-funded research organization. It has created different standards and frameworks that are used by many organizations and cybersecurity professionals. MITRE created a set of matrices (called the MITRE ATT&CK) that document the tactics and techniques attackers use to compromise networks and systems. As part of the same effort, MITRE maintains a list of tactics and techniques used by attackers to gather information about their victims before compromising their systems and networks (PRE-ATT&CK). MITRE’s ATT&CK can be accessed at https://attack.mitre.org and PRE-ATT&CK can be accessed at https://attack.mitre.org/matrices/enterprise/pre/.

Hoaxes
A hoax is the attempt at deceiving people into believing something that is false. The differences between hoaxes and phishing can be quite gray. However, hoaxes can come in person or through other means of communication, whereas phishing is generally relegated to e-communication and phone. Although phishing can occur at any time, and with the specific goal of obtaining private information, a hoax can often be perpetuated on holidays or other special days and could be carried out simply for fun. Regardless, hoaxes can use up valuable organization resources: email replies, Internet bandwidth used, time spent, and so on. An example of a “harmless” hoax was Google’s supposed name change to “Topeka” on April Fools’ Day 2010. An example of a financially harmful hoax was the supposed assassination of Bill Gates on April Fools’ Day 2003. This hoax led to stock market fluctuations and loss of profit in Asia. Some companies place a time limit on jokes and hoaxes indicating that the affected person has become nonproductive; for example, 3 percent of the workday.
Pretexting, malicious insider attempts, diversion theft, phishing, and hoaxes are all known as confidence tricks, thus the term con, and are committed by “bunko” artists. However, there are even lower ways to get access to people’s information; these often are used with the previous methods. They include shoulder surfing, eavesdropping, dumpster diving, baiting, and piggybacking.

Impersonation or Pretexting
Pretexting is a type of social engineering attack in which a person invents a scenario, or pretext, in the hope of persuading a victim to divulge information. Preparation and some prior information are often needed before attempting a pretext; impersonation is often a key element. By impersonating the appropriate personnel or third-party entities, a person performing a pretext hopes to obtain records about an organization, its data, and its personnel. IT people and employees should always be on the lookout for impersonators and always ask for identification. If there is any doubt, the issue should be escalated to your supervisor and/or a call should be made to the authorities.
Eavesdropping
Eavesdropping is a strategy in which a person uses direct observation to “listen” in to a conversation. This could be a person hiding around the corner or a person tapping into a phone conversation. Soundproof rooms are often employed to stop eavesdropping, and encrypted phone sessions can also be implemented.
Baiting
Baiting is a strategy in which a malicious individual leaves malware-infected removable media such as a USB drive or optical disc lying around in plain view. It might have an interesting logo or distinctive look about it. When a person takes it and connects it to his or her computer, the malware infects the computer and attempts to take control of it and/or the network the computer is a member of.

Watering Hole Attack
The watering hole attack is a strategy that targets users based on the common websites that they frequent. The attacker loads malware beforehand on one or more websites in the hopes that the user will access those sites and activate the malware, ultimately infecting the user’s system and possibly spreading through the network. To figure out the browsing habits of users, the attacker might guess or use direct observation. So, this attack may also build on other social engineering methods such as eavesdropping, pretexting, and phishing.
Popular websites such as Google, Microsoft, and so on will be difficult to infect with malware. It’s the smaller websites that the attacker will go after. For example, let’s consider a company that manufactures widgets. Chances are that the company will need to purchase plastic and other resources to build the widgets. It follows that users will connect to suppliers’ websites often via the Internet or possibly an intranet. Typically, suppliers’ websites are known for a lack of security and make excellent targets. If many users in the company go to these same websites, and often, it’s just a matter of time before one clicks on the wrong website element or gets tricked in another manner. Then malware gets installed to the client computer and possibly spreads throughout the company. An attacker might also redirect users to other websites where more hardcore malware (such as ransomware) or other scams are located.
The problem is that you, as a security administrator, can’t actively prevent the malware on the targeted websites. You can suggest prevention methods to those companies—such as software patches and secure coding—but can’t force them into action. So, you should focus on localized prevention methods including training users, reducing web browser functionality, blocking known malicious websites based on threat intelligence, and monitoring in the form of antimalware software and IDS/IPS.

Typo Squatting
Typo squatting (or typosquatting) is a technique used by adversaries that leverages human error when typing a URL in their web browser. For instance, users often enter typos (or a wrong URL) for a given website. Let’s suppose you want to go to google.com, but instead typed gogle.com. An attacker can register the “gogle.com” domain and impersonate the real website and host malware or perform any other malicious technique to compromise your system.

Influence Campaigns, Principles of Social Engineering, and Reasons for Effectiveness
The following are several motivation techniques used by social engineers:
Authority: A social engineer shows confidence and perhaps authority—whether legal, organizational, or social authority.
Intimidation: Attackers can use intimidation to manipulate their victims to perform some action or to reveal sensitive information.
Consensus: Consensus, or “social proof,” is a psychological phenomenon in which an individual is not able to determine the appropriate mode of behavior. For example, you might see others acting or doing something in a certain way and might assume that it is appropriate. Social engineers might use this tactic when an individual enters an unfamiliar situation that he or she doesn’t know how to deal with. Social engineers might manipulate multiple people at once by using this technique.
Scarcity: It is possible to use scarcity to create a feeling of urgency in a decision-making context. Specific language can be used to heighten urgency and manipulate victims. Salespeople often use scarcity to manipulate clients (for example, telling a customer that an offer is for today only or that there are limited supplies). Social engineers use similar techniques.
Familiarity: Individuals can be influenced by things or people they like or are familiar with. Social engineers take advantage of these human vulnerabilities to manipulate their victims.
Trust: Attackers take advantage of the trust a person has in another person or organization in order to influence them to perform some action or reveal sensitive information.
Urgency: It is possible to manipulate a person with a sense of immediate urgency to prompt him or her to act promptly. Using urgency, social engineers force their victims to act quickly to avoid or rectify a perceived dangerous or painful situation.
Tip
Nowadays, threat actors use automated bots in social media sites like Twitter and Facebook to influence the sentiment of a given user. These bots are used to try to manipulate public sentiment on contentious issues including political events, gun control, abortion, and many more. Hybrid warfare is a subject that was originally employed by the armed forces. However, attackers nowadays use hybrid warfare techniques in cyber and influential campaigns to manipulate people to believe something that may not be true by using different types of propaganda that are often shared in social media sites.

User Security Awareness Education
The user could be the single most exploitable resource of a company. I think that the previous section about social engineering provides a good argument to support that opinion. People aren’t computers. Some might be compared to robots (perhaps unfairly), but no matter how logical and disciplined a person might be, there is always the potential for human error. So, until firewalls are developed for people’s brains, education becomes the best method to prevent social engineering attacks and malware infection, not to mention user error.
As an IT manager, I have always made it a point to incorporate technology and security training for as many employees as possible. This would include classroom/conference room training, written materials, digital courses, even funny posters in the cafeteria. I’d use whatever platform I could to get the point across. The key is to make it accessible to the user and to make it interesting and fun.
There are several roadblocks when it comes to user training. The first is organizational acceptance. Are the executives of a company on board with the idea? As time moves on, we see that more and more executives include user education as a matter of course. However, if you come across an individual who is against the idea because of a “lack” of budgeting or time, you can simply show that person a news article about one of the many successful attacks that have occurred recently. Then show a case study of the amount of time and money that the affected company lost due to the attack, and—in most cases—how easily it could have been prevented. Then, there are the employees to be trained themselves. Some will put up a fight when it comes to education. Again, the secret ingredient here is to pique the interest of the users. Get them involved, make it fun, create a reward system, and use your imagination. Some organizations employ IT trainers on a full-time basis or as consultants. Good IT trainers know how to get through to the typical employee. Other organizations will offer incentives for attending training, or penalties for not attending—though statistics show that incentives usually work better than penalties.
You can also attempt role-playing. I’m not talking about a role-playing game such as Dungeons & Dragons! Rather, having the employees act out different organizational roles, such as system administrators, privileged users, executive users, data owners, system owners, and of course, typical end users. Throw in the hacker and/or con artist as the “bad guy” role and you can really teach in a fun way. Create scenarios where people can learn in a tangible way how attacks are carried out and how they can be prevented. Quiz the employees, but keep it light. The idea is for employees to expand their knowledge into other areas of the company—a sort of table-top job rotation, so to speak. Develop the situations and solutions properly, and the whole organization becomes a stronger and more secure unit, thanks to you. Come on, you know you always aspired to be a Dungeon Master!
Finally, there is the time factor. People have projects and tasks to complete and usually aren’t even given enough time for that! Where does the time for training come from? This is when the mindset of loyalty to the company comes in—and Human Resources can usually be helpful in cultivating that mindset. The whole outlook should be based on the idea of overall efficiency and benefits to the company and individual. By sitting in on security training, the user will save time over the long term and will ultimately become a more knowledgeable person.
Anyway, for the Security+ certification, how the training gets accomplished isn’t as important as what is covered in training. The following is a basic list of rules you can convey when training employees:
Never, under any circumstances, give out any authentication details such as passwords, PINs, company ID, tokens, smart cards, and so on.
Always shield keypads and screens when entering authentication information.
Adhere to the organization’s clean desk policy, which states that all documents, electronics, personally owned devices, and other items be put away (or locked away) when you are not at your desk, or other work area.
Always screen your email and phone calls carefully and keep a log of events. This is also known as communications vetting.
Use encryption when possible to protect emails, phone calls, and data.
If there is any doubt as to the legitimacy of a person, email, or phone call, document the situation and escalate it to your supervisor, security, or the authorities.
Never pick up, and make use of, any unknown removable media.
Always shred any sensitive information destined for the garbage or recycling.
Always comply with company policy when it comes to data handling and disposal. For example, if a hard drive, USB flash drive, memory stick, or optical disc is no longer being used, make sure it is disposed of properly. If you are not sure, contact the IT department or facilities department of the organization to find out if it should be recycled, or destroyed.
Always track and expedite shipments.
Be extremely careful when using a web browser. Double-check everything that is typed before pressing Enter or clicking Go. Don’t click on anything unless you know exactly what it is. Web-based attacks account for a huge percentage of damage to organizations.
When training employees, try to keep them interested; infuse some fun and be silly if you want to. For instance, the first bullet said to never give out authentication details. Pundits tell us to never say never. Well, if it’s okay for them, then it’s okay for us. And in this case, it’s vital to the health of your organization—not to mention you. You see what I mean? Or, if you don’t want to be silly, then consider imparting some real examples. Use examples of social engineering so that your trainees can make the connection between actual social engineering methods and their defenses. Make them understand that social engineers don’t care how powerful an organization’s firewall is or how many armed guards the company has. They get past technology and other types of security by exploiting the weaknesses inherent in human nature.
Chapter Review Activities
Use the features in this section to study and review the topics in this chapter.
Review Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 1-2 lists a reference of these key topics and the page number on which each is found.

Table 1-2 Key Topics for Chapter 1
Key Topic Element |
Description |
Page Number |
|---|---|---|
Section |
Phishing and Spear Phishing |
9 |
Section |
Smishing |
12 |
Section |
Vishing |
12 |
Section |
Spam and Spam over Internet Messaging (SPIM) |
13 |
Section |
Dumpster Diving |
13 |
Section |
Shoulder Surfing |
14 |
Section |
Pharming |
14 |
Section |
Piggybacking and Tailgaiting |
15 |
Section |
Eliciting Information |
15 |
Section |
Whaling |
16 |
Section |
Prepending |
17 |
Section |
Identity Fraud |
17 |
Section |
Invoice Scams |
17 |
Section |
Credential Harvesting |
18 |
Section |
Reconnaissance |
18 |
Section |
Hoaxes |
19 |
Section |
Impersonation or Pretexting |
19 |
Section |
Watering Hole Attack |
20 |
Section |
Typo Squatting |
20 |
Section |
Influence Campaigns, Principles of Social Engineering, and Reasons for Effectiveness |
21 |
Section |
User Security Awareness Education |
22 |
List |
Rules you can convey when training employees |
23 |
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Review Questions
Answer the following review questions. Check your answers with the answer key in Appendix A.
1. You go out the back door of your building and notice someone looking through your company’s trash. If this person were trying to acquire sensitive information, what would this attack be known as?
2. User education can help to defend against which type of attacks?
3. You can often configure your email servers or email cloud services to add a message in the email subject line to identify emails that are coming from outside of the organization. This technique is also known as __________.
4. What is the most common reason that social engineering succeeds?
5. In which two environments would social engineering attacks be most effective?
6. What is a social engineering technique used by adversaries that leverages user errors (“typos”) when entering a given URL in their web browser for a given website?
7. A man pretending to be a data communications repair technician enters your building and states that there is networking trouble and he needs access to the server room. What is this an example of?
8. Turnstiles, double entry doors, and security guards are all preventive measures for what kind of social engineering?
9. What is the social engineering technique where the attacker redirects the victim from a valid website or resource to a malicious one that could be made to appear as the valid site to the user?
10. Why would you implement password masking and privacy screens/filters?
