Chapter 9
Network Security
This chapter covers the following official Network+ objectives:
 Explain common security concepts.
Explain common security concepts. Compare and contrast common types of attacks.
Compare and contrast common types of attacks. Given a scenario, apply network hardening techniques.
Given a scenario, apply network hardening techniques. Compare and contrast remote-access methods and security implications.
Compare and contrast remote-access methods and security implications. Explain the importance of physical security.
Explain the importance of physical security.
This chapter covers CompTIA Network+ objectives 4.1, 4.2, 4.3, 4.4, and 4.5. For more information on the official Network+ exam topics, see the “About the Network+ Exam” section in the Introduction.
Network security is one of the toughest areas of IT to be responsible for. It seems as if a new threat surfaces on a regular basis and that you are constantly needing to learn new things just a half a step ahead of potential problems. This chapter focuses on some of the elements administrators and technicians use to keep their networks as secure as possible.
Common Security Concepts
 Explain common security concepts.
Explain common security concepts.
There are three concepts you will see throughout this chapter and probably implied in every security-related book you will ever read: confidentiality, integrity, and availability, often referred to as the CIA triad of security. All security measures should affect one or more of these areas. Confidentiality means preventing unauthorized users from accessing data: passwords, encryption, and access control all support confidentiality. Integrity means ensuring that data has not been altered: hashing and message authentication codes are the most common methods of accomplishing this task (as well as ensuring nonrepudiation with digital signatures). Simply making sure that the data and systems are available for authorized users is what availability is all about: data backups, redundant systems, and disaster recovery plans all support fault tolerance and increased availability.
Threats can come from anywhere. They can include external entities such as bored individuals wanting to inflict harm to any system they can find access to and yours just happened to let them in, or internal entities such as disgruntled employees unhappy they were passed over for a promotion and feeling as if they have a right to cause harm. Often, the internal threats are the hardest to prevent since these users are already granted access to some resources and have an advantage over those outside the organization.
Vulnerabilities are discovered on a regular basis and, as an administrator, you must stay current on information related to discovered problems and be aware of common vulnerabilities and exposures (CVEs): a list of publicly available security flaws that you should be familiar with as an administrator (see https://cve.mitre.org/). When a hole is found in a web browser or other software, and miscreants begin exploiting it the very day it is discovered by the developer (bypassing the one- to two-day response time many software providers need to put out a patch after the hole has been found), it is known as an exploit attack or zero-day attack. Zero-day attacks are incredibly difficult to respond to. If attackers learn of the weakness the same day as the developer, they have the ability to exploit it until a patch is released. Often, the only thing you, as a security administrator, can do between the discovery of the exploit and the release of the patch is to turn off the service. Although this approach can be a costly undertaking in terms of productivity, it is the only way to keep the network safe.
ExamAlert
Be ready to identify types of attacks and common vulnerabilities and exposures (CVEs) such as the one just described. You can expect questions about these types of attacks on the Network+ exam.
Access Control
Access control describes the mechanisms used to filter network traffic to determine who is and who is not allowed to access the network and network resources. Firewalls, proxy servers, routers, and individual computers all can maintain access control to some degree by protecting the edges of the network. Because the security strategy limits who can and cannot access the network and its resources, it is easy to understand why access control plays a critical role. Several types of access control strategies exist, as discussed in the following sections.
ExamAlert
Be sure that you can identify the purpose and types of access control.
Mandatory Access Control
Mandatory access control (MAC) is the most secure form of access control. In systems configured to use mandatory access control, administrators dictate who can access and modify data, systems, and resources. MAC systems are commonly used in military installations, financial institutions, and, because of new privacy laws, medical institutions.
MAC secures information and resources by assigning sensitivity labels or attributes to objects and users. When users request access to an object, their sensitivity level is compared to the object’s. A label is a feature applied to files, directories, and other resources in the system. It is similar to a confidentiality stamp. When a label is placed on a file, it describes the level of security for that specific file. It permits access by files, users, programs, and so on that have a similar or higher security setting.
Discretionary Access Control
Unlike mandatory access control, discretionary access control (DAC) is not enforced from the administrator or operating system. Instead, access is controlled by an object’s owner. For example, if a secretary creates a folder, he decides who will have access to that folder. This access is configured using permissions and an access control list (ACL).
DAC uses an ACL to determine access. The ACL is a table that informs the operating system of the rights each user has to a particular system object, such as a file, a folder, or a printer. Each object has a security attribute that identifies its ACL. The list has an entry for each system user with access privileges. The most common privileges include the ability to read a file (or all the files in a folder), to write to the file or files, and to execute the file (if it is an executable file or program).
Microsoft Windows servers/clients, Linux, UNIX, and macOS are among the operating systems that use ACLs. The list is implemented differently by each operating system.
In Windows Server products, an ACL is associated with each system object. Each ACL has one or more access control entries (ACEs) consisting of the name of a user or group of users. The user can also be a role name, such as “secretary” or “research.” For each of these users, groups, or roles, the access privileges are stated in a string of bits called an access mask. Generally, the system administrator or the object owner creates the ACL for an object.
Note
A server on a network that has the responsibility of being a repository for accounts (user/computer) is often referred to as a network controller. A good example is a domain controller on a Microsoft Active Directory–based network.
Rule-Based Access Control
Rule-based access control (RBAC) controls access to objects according to established rules. The configuration and security settings established on a router or firewall are a good example.
When a firewall is configured, rules are set up to control access to the network. Requests are reviewed to see if the requestor meets the criteria to be allowed access through the firewall. For instance, if a firewall is configured to reject all addresses in the 192.166.x.x IP address range, and the requestor’s IP is in that range, the request would be denied.
In a practical application, RBAC is a variation on MAC. Administrators typically configure the firewall or other device to allow or deny access. The owner or another user does not specify the conditions of acceptance, and safeguards ensure that an average user cannot change settings on the devices.
Role-Based Access Control
Note
Both rule-based and role-based access control use the acronym RBAC.
In role-based access control (RBAC), access decisions are determined by the roles that individual users have within the organization. Role-based access requires the administrator to have a thorough understanding of how a particular organization operates, the number of users, and each user’s exact function in that organization.
ExamAlert
Because the CompTIA objectives specifically call out role-based access control, be sure you know that with RBAC access decisions are determined by the roles that individual users have within the organization.
Because access rights are grouped by role name, the use of resources is restricted to individuals who are authorized to assume the associated role. For example, within a school system, the role of teacher can include access to certain data, including test banks, research material, and memos. School administrators might have access to employee records, financial data, planning projects, and more.
The use of roles to control access can be an effective means of developing and enforcing enterprise-specific security policies and for streamlining the security management process.
Roles should receive only the privilege level necessary to do the job associated with that role. This general security principle is known as the least privilege concept. When people are hired in an organization, their roles are clearly defined. A network administrator creates a user account for a new employee and places that user account in a group with people who have the same role in the organization.
Least privilege is often too restrictive to be practical in business. For instance, using teachers as an example, some more experienced teachers might have more responsibility than others and might require increased access to a particular network object. Customizing access to each individual is a time-consuming process.
ExamAlert
Once just a Security+ objective and concept, this topic has now been added to the Network+ objectives as well. Because you might be asked about the concept of least privilege, know that it refers to assigning network users the privilege level necessary to do the job associated with their role—nothing more and nothing less.
Closely related to least privilege is the concept of a zero trust network. As the name implies, it simply means that you don’t automatically trust anyone and instead always authenticate and authorize. Everything must be verified explicitly, data protection is held to utmost ideal, and all sessions are encrypted end to end.
Defense in Depth
Defense in depth is based on the premise that implementing security at different levels or layers to form a complete security strategy provides better protection and greater resiliency than implementing an individual security defense. This level of defense can be accomplished in a number of different ways; some of the most popular are through the use of network segmentation, screened subnet, separation of duties, network access control, and honeypots. Each variant of defense in depth is discussed in the sections that follow.
Network Segmentation
Dividing one network into smaller subnetworks enables you to optimize it in a number of ways. The segmentation is accomplished with switches and VLANs, and the separation can be done to isolate such things as heavy load systems or certain protocols. If you move them to their own subnetwork, the result should be performance increases for other parts of the network.
Note
One popular approach is using virtual machines (VMs) to segment or separate systems (software) from the main OS (host versus guest) and the rest of the network through virtual switches.
Screened Subnet
An important firewall-related concept is that of the screened subnet. This concept was formerly known as a demilitarized zone (DMZ) and sometimes called a perimeter network. A screened subnet is part of a network where you place servers that must be accessible by sources both outside and inside your network. However, the screened subnet is not connected directly to either network, and it must always be accessed through the firewall. The military term DMZ was used previously because it describes an area that has little or no enforcement or policing.
Using screened subnets gives your firewall configuration an extra level of flexibility, protection, and complexity. Figure 9.1 shows a screened subnet (DMZ) configuration.

FIGURE 9.1 A screened subnet (DMZ) configuration
By using a screened subnet, you can create an additional step that makes it more difficult for an intruder to gain access to the internal network. In Figure 9.1, for example, an intruder who tried to come in through Interface 1 would have to spoof a request from either the web server or proxy server into Interface 2 before it could be forwarded to the internal network. Although it is not impossible for an intruder to gain access to the internal network through a screened subnet, it is difficult.
ExamAlert
Be prepared to identify the purpose of a screened subnet and that this concept was previously known as a DMZ.
Separation of Duties
Separation of duties policies are designed to reduce the risk of fraud and to prevent other losses in an organization. A good policy will require more than one person to accomplish key processes. This may mean that the person who processes an order from a customer isn’t the same person who generates the invoice or deals with the billing.
Separation of duties helps prevent various problems, such as an individual embezzling money from a company. To embezzle funds successfully, an individual would need to recruit others to commit an act of collusion—that is, an agreement between two or more parties established for the purpose of committing deception or fraud. Collusion, when part of a crime, is also a criminal act in and of itself.
In addition, separation of duties policies can help prevent accidents from occurring in an organization. Suppose that you’re managing a software development project. You want someone to perform a quality assurance test on a new piece of code before it’s put into production. Establishing a clear separation of duties prevents development code from entering production status until quality testing is accomplished.
Many banks and financial institutions require multiple steps and approvals to transfer money. These policies help reduce errors and minimize the likelihood of fraud.
Honeypots
When we talk about network security, honeypots and honeynets are often mentioned. Honeypots are a rather clever approach to network security but perhaps a bit expensive. A honeypot is a system set up as a decoy to attract and deflect attacks from hackers. The server decoy appears to have everything a regular server does—OS, applications, and network services. The attacker thinks she is accessing a real network server, but she is in a network trap.
The honeypot has two key purposes. It can give administrators valuable information on the types of attacks being carried out. In turn, the honeypot can secure the real production servers according to what it learns. Also, the honeypot deflects attention from working servers, allowing them to function without being attacked.
A honeypot can do the following:
 Deflect the attention of attackers from production servers
Deflect the attention of attackers from production servers Deter attackers if they suspect their actions may be monitored with a honeypot
Deter attackers if they suspect their actions may be monitored with a honeypot Allow administrators to learn from the attacks to protect the real servers
Allow administrators to learn from the attacks to protect the real servers Identify the source of attacks, whether from inside the network or outside
Identify the source of attacks, whether from inside the network or outside
ExamAlert
Think of a honeypot as a trap that allows the intruder in but does not allow access to sensitive data.
One step up from the honeypot is the honeynet. The honeynet is an entire network set up to monitor attacks from outsiders. All traffic into and out of the network is carefully tracked and documented. This information is shared with network professionals to help isolate the types of attacks launched against networks and to proactively manage those security risks. Honeynets function as a production network, using network services, applications, and more. Attackers don’t know that they are actually accessing a monitored network.
RADIUS and TACACS+
Among the potential issues network administrators face when implementing remote access are utilization and the load on the remote-access server. As a network’s remote-access implementation grows, reliance on a single remote-access server might be impossible, and additional servers might be required. Remote Authentication Dial-In User Service (RADIUS) can help in this scenario.
ExamAlert
RADIUS is a protocol that enables a single server to become responsible for all remote-access authentication, authorization, and auditing (or accounting) services.
RADIUS functions as a client/server system. The remote user dials in to the remote-access server, which acts as a RADIUS client, or network access server (NAS), and connects to a RADIUS server. The RADIUS server performs authentication, authorization, and auditing (or accounting) functions and returns the information to the RADIUS client (which is a remote-access server running RADIUS client software); the connection is either established or rejected based on the information received.
Terminal Access Controller Access Control System (TACACS) is a security protocol designed to provide centralized validation of users who are attempting to gain access to a router or NAS. Like RADIUS, TACACS is a set of security protocols designed to provide AAA of remote users. Terminal Access Controller Access Control System Plus (TACACS+) is a proprietary version of TACACS from Cisco and is the implementation commonly in use in networks today. TACACS+ uses TCP port 49 by default.
Although both RADIUS and TACACS+ offer AAA services for remote users, some noticeable differences exist:
 TACACS+ relies on TCP for connection-oriented delivery. RADIUS uses connectionless UDP for data delivery.
TACACS+ relies on TCP for connection-oriented delivery. RADIUS uses connectionless UDP for data delivery. RADIUS combines authentication and authorization, whereas TACACS+ can separate their functions.
RADIUS combines authentication and authorization, whereas TACACS+ can separate their functions.
ExamAlert
Both RADIUS and TACACS+ provide authentication, authorization, and accounting services. One notable difference between TACACS+ and RADIUS is that TACACS+ relies on the connection-oriented TCP, whereas RADIUS uses the connectionless UDP.
Kerberos Authentication
Kerberos is an Internet Engineering Task Force (IETF) standard for providing authentication. It is an integral part of network security. Networks, including the Internet, can connect people from all over the world. When data travels from one point to another across a network, it can be lost, stolen, corrupted, or misused. Much of the data sent over networks is sensitive, whether it is medical, financial, or otherwise. A key consideration for those responsible for the network is maintaining the confidentiality of the data. In the networking world, Kerberos plays a significant role in data confidentiality.
In a traditional authentication strategy, a username and password are used to access network resources. In a secure environment, it might be necessary to provide a username and password combination to access each network service or resource. For example, a user might be prompted to type in her username and password when accessing a database, and again for the printer, and again for Internet access. This is a time-consuming process, and it can also present a security risk. Each time the password is entered, there is a chance that someone will see it being entered. If the password is sent over the network without encryption, it might be viewed by malicious eavesdroppers.
Kerberos was designed to fix such problems by using a method requiring only a single sign-on (SSO). This single sign-on enables a user to log in to a system and access multiple systems or resources without the need to repeatedly reenter the username and password. Additionally, Kerberos is designed to have entities authenticate themselves by demonstrating possession of secret information.
Kerberos is one part of a strategic security solution that provides secure authentication services to users, applications, and network devices by eliminating the insecurities caused by passwords stored or transmitted across the network. Kerberos is used primarily to eliminate the possibility of a network “eavesdropper” tapping into data over the network—particularly usernames and passwords. Kerberos ensures data integrity and blocks tampering on the network. It employs message privacy (encryption) to ensure that messages are not visible to eavesdroppers on the network.
For the network user, Kerberos eliminates the need to repeatedly demonstrate possession of private or secret information.
ExamAlert
Kerberos is a nonproprietary protocol and is used for cross-platform authentication. It’s the main authentication protocol used with Windows servers.
Kerberos is designed to provide strong authentication for client/server applications by using secret key cryptography. Cryptography is used to ensure that a client can prove its identity to a server (and vice versa) across an unsecure network connection. After a client and server have used Kerberos to prove their identity, they can also encrypt all their communications to ensure privacy and data integrity.
ExamAlert
Kerberos enables secure authentication over an unsecure network such as the Internet.
The key to understanding Kerberos is to understand its secret key cryptography. Kerberos uses symmetric key cryptography, in which both client and server use the same encryption key to cipher and decipher data.
In secret key cryptography, a plain-text message can be converted into cipher text (encrypted data) and then converted back into plain text using one key. Thus, two devices share a secret key to encrypt and decrypt their communications. Figure 9.2 shows the symmetric key process.
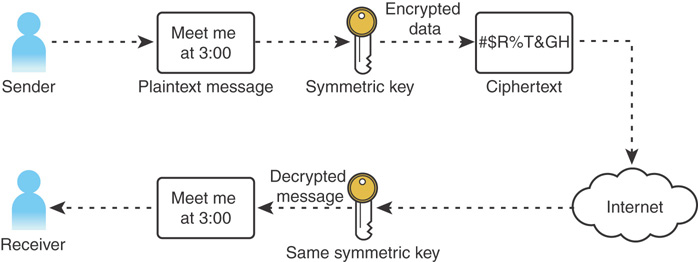
FIGURE 9.2 The symmetric key process
ExamAlert
Another cryptography method in use is asymmetric key cryptography, or public key cryptography. In this method, a device has both a public and a private key. The private key is never shared. The public key is used to encrypt the communication, and the private key is used for decrypting.
Kerberos authentication works by assigning a unique key, called a ticket, to each client that successfully authenticates to a server. The ticket is encrypted and contains the user’s password, which is used to verify the user’s identity when a particular network service is requested. Each ticket is time stamped. It expires after a period of time, and a new one is issued. Kerberos works in the same way that you go to a movie. First, you go to the ticket counter, tell the person what movie you want to see, and get your ticket. After that, you go to a turnstile and hand the ticket to someone else, and then you’re “in.” In simplistic terms, that’s Kerberos.
ExamAlert
You should know that the security tokens used in Kerberos are known as tickets.
Local Authentication
Most of the time, the goal is to authenticate the user using a centralized authentication server or service of some type. When that cannot be done—such as when there is no Internet connectivity available—authentication is done locally by the operating system using values stored within it. In Windows, for example, the Local Authentication Subsystem (LASS) performs this function and allows users access to the system after their stored username and password variables match.
Lightweight Directory Access Protocol
Lightweight Directory Access Protocol (LDAP) provides a mechanism to access and query directory services systems. In the context of the Network+ exam, these directory services systems are most likely to be UNIX based or Microsoft Active Directory based. Although LDAP supports command-line queries executed directly against the directory database, most LDAP interactions are via utilities such as an authentication program (network logon) or locating a resource in the directory through a search utility.
ExamAlert
Know that LDAP, by default, uses port 389.
Using Certificates
A public key infrastructure (PKI) is a collection of software, standards, and policies combined to enable users from the Internet or other unsecured public networks to securely exchange data. PKI uses a public and private cryptographic key pair obtained and shared through a trusted authority. Services and components work together to develop the PKI. Some of the key components of a PKI include the following:
 Certificates: Certificates are electronic credentials that validate users, computers, or devices on the network. They are digitally signed statements that associate the credentials of a public key to the identity of the person, device, or service that holds the corresponding private key.
Certificates: Certificates are electronic credentials that validate users, computers, or devices on the network. They are digitally signed statements that associate the credentials of a public key to the identity of the person, device, or service that holds the corresponding private key. Certificate authorities (CAs): CAs issue and manage certificates. They validate the identity of a network device or user requesting data. CAs can be either independent third parties, known as public CAs, or they can be organizations running their own certificate-issuing server software, known as private CAs.
Certificate authorities (CAs): CAs issue and manage certificates. They validate the identity of a network device or user requesting data. CAs can be either independent third parties, known as public CAs, or they can be organizations running their own certificate-issuing server software, known as private CAs. Certificate templates: These templates are used to customize certificates issued by a certificate server. This customization includes a set of rules and settings created on the CA and used for incoming certificate requests.
Certificate templates: These templates are used to customize certificates issued by a certificate server. This customization includes a set of rules and settings created on the CA and used for incoming certificate requests. Certificate revocation list (CRL): This list identifies certificates that were revoked before they reached the certificate expiration date. Certificates are often revoked because of security concerns, such as a compromised certificate.
Certificate revocation list (CRL): This list identifies certificates that were revoked before they reached the certificate expiration date. Certificates are often revoked because of security concerns, such as a compromised certificate.
Auditing and Logging
Auditing is the process of monitoring occurrences and keeping a log of what has occurred on a system. A system administrator determines which events should be audited. Tracking events and attempts to access the system helps prevent unauthorized access and provides a record that administrators can analyze to make security changes as necessary. This record, or log, also provides administrators with solid evidence if they need to look into improper user conduct.
Caution
Be sure that you can identify the purpose of authentication, authorization, and accounting.
The first step in auditing is to identify what system events to monitor. After the system events are identified, in a Windows environment, the administrator can choose to monitor the success or failure of a system event. For instance, if “logon” is the event being audited, the administrator might choose to log all unsuccessful logon attempts, which might indicate that someone is attempting to gain unauthorized access. Conversely, the administrator can choose to audit all successful attempts to monitor when a particular user or user group is logging on. Some administrators prefer to log both events. However, overly ambitious audit policies can reduce overall system performance.
Multifactor Authentication Factors
Multifactor authentication is defined as having two or more access methods included as part of the authentication process; for example, using both smartcards and passwords. An ATM card and PIN are another common example representing multifactor authentication (in this case, two-factor authentication), as opposed to just one (which constitutes single-factor authentication). The ATM card is something you have, and the PIN is something you know.
The factors used in authentication systems or methods are based on one or more of these five factors:
 Something you know, such as a password or PIN
Something you know, such as a password or PIN Something you have, such as a smartcard, token, or identification device
Something you have, such as a smartcard, token, or identification device Something you are, such as your fingerprints or retinal pattern (often called biometrics)
Something you are, such as your fingerprints or retinal pattern (often called biometrics) Somewhere you are (based on geolocation)
Somewhere you are (based on geolocation) Something you do, such as an action you must take to complete authentication
Something you do, such as an action you must take to complete authentication
ExamAlert
Be able to identify the five types of factors used in multifactor authentication.
Additional Access Control Methods
Today, there are many ways to establish access into networks. You could fill an entire tome with a discussion of the possibilities. What follows are some of the more important ones to know for this exam (others appear on other CompTIA exams, such as Security+).
802.1X
The IEEE standard 802.1X defines port-based security for wireless network access control. As such, it offers a means of authentication and defines the Extensible Authentication Protocol (EAP) over IEEE 802, which is often known as EAP over LAN (EAPOL). The biggest benefit of using 802.1X is that the access points and the switches do not need to do the authentication but instead rely on the authentication server to do the work.
ExamAlert
Remember that IEEE 802.1X authentication allows only authorized devices to connect to the network. The most secure form of IEEE 802.1X authentication is certificate-based authentication.
Extensible Authentication Protocol (EAP)
Choosing the correct authentication protocol for remote clients is an important part of designing a secure remote-access strategy. After they are authenticated, users have access to the network and servers. Extensible Authentication Protocol (EAP) provides a framework for authentication that is often used with wireless networks. Among the EAP types adopted by the WPA/WPA2 standard are PEAP, EAP-FAST, and EAP-TLS. EAP was developed in response to an increasing demand for authentication methods that use other types of security devices, such as token cards, smartcards, and digital certificates.
To simplify network setup, a number of small office/home office (SOHO) routers use a series of EAP messages to allow new hosts to join the network and use WPA/WPA2. Known as Wi-Fi Protected Setup (WPS), this setup often requires the user to do something to complete the enrollment process: press a button on the router within a short time period, enter a PIN, or bring the new device close by (so that near-field communication can take place).
Note
WPA3 uses the Simultaneous Authentication of Equals (SAE) to replace WPA2’s preshared key (PSK) exchange protocol.
Cisco, RSA, and Microsoft worked together to create Protected Extensible Authentication Protocol (PEAP). There is now native support for it in Windows (which previously favored EAP-TLS). Although many consider PEAP and EAP-TLS to be similar, PEAP is more secure because it establishes an encrypted channel between the server and the client.
EAP-FAST (Flexible Authentication via Secure Tunneling) was designed by Cisco to allow for the use of certificates to establish a TLS tunnel in which client credentials are verified.
To put EAP implementations in a chronological order, think EAP-TLS, EAP-FAST, and then PEAP. In between came EAP-TTLS, a form of EAP-TLS that adds tunneling (Extensible Authentication Protocol—Tunneled Transport Layer Security). Of all the choices, PEAP is the one with more vendors than just Cisco and thus is currently favored for use today.
Network Access Control (NAC)
Network access control (NAC) is a method to restrict access to the network based on identity or posture (discussed later in this chapter). This method was created by Cisco to enforce privileges and make decisions on a client device based on information gathered from it (such as the vendor and version of the antivirus software running). If the wanted information is not found (such as that the antivirus definitions are a year old), the client can be placed in a quarantine network area to keep it from infecting the rest of the network. It can also be placed in a guest network and/or allowed to run nonpersistent (versus persistent) agents.
A posture assessment is any evaluation of a system’s security based on settings and applications found. In addition to looking at such values as settings in the Registry or dates of files, NACs can also check 802.1X values—the group of networking protocols associated with authentication of devices attempting to connect to the network. 802.1X works with EAP.
ExamAlert
As you prepare for the exam, be sure that you can identify posture assessment as any evaluation of a system’s security based on settings and applications found.
MAC Filtering
Another name for a network card or network adapter is a network controller. Every controller has a unique MAC address associated with it. Filtering network traffic using a system’s MAC address typically is done using an ACL. This list keeps track of all MAC addresses and is configured to allow or deny access to certain systems based on the list. As an example, look at the MAC ACL from a router. Figure 9.3 shows the MAC ACL screen. Specific MAC addresses can be either denied or accepted, depending on the configuration. It would be possible, for example, to configure it so that only the system with the MAC address of 02-00-54-55-4E-01 can authenticate to the router.
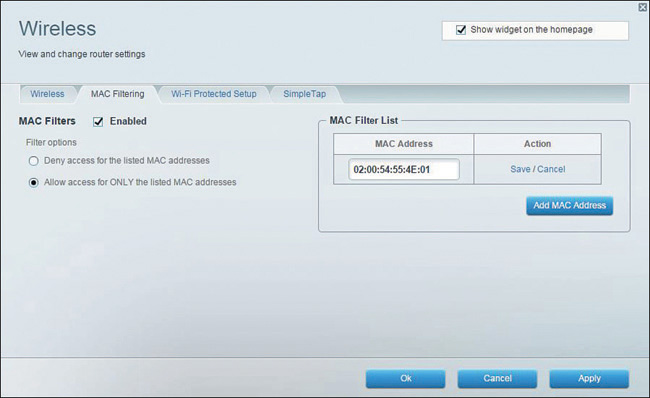
FIGURE 9.3 A MAC ACL
Note
When administrators are configuring security for wireless networks, filtering by MAC address is a common practice. Typically, in MAC filtering security, MAC addresses can be added to an “allow” ACL or “deny” ACL.
Risk Management
Risk management involves recognizing and acknowledging that risks exist and then determining what to do about them. Sometimes, the best solution is to do nothing. If, for example, there is a risk that some data could be lost in the event of a fire but the value placed on that data is below the cost of protecting it from that harm, the economically feasible solution could be to accept the risk and do nothing further. In most cases, acceptance alone is not enough and two likely approaches are mitigation (trying to minimize the risk) and/or transference (shifting a part of the risk to another party such as an insurance provider).
To determine how to manage risk, assessments are usually employed. An assessment can be done on threats, vulnerabilities, or business operations (process assessment and vendor assessment).
Penetration Testing
It is becoming more common for companies to hire penetration testers to test their system’s defenses. Essentially, a penetration tester will use the same techniques that a hacker would use to find any flaws in a system’s security. These flaws may be discovered by means other than directly accessing the system, such as collecting information from public databases, talking to employees/partners, dumpster diving, and social engineering. This approach is known as passive reconnaissance. In contrast, active reconnaissance directly focuses on the system (port scans, traceroute information, network mapping, and so forth) to identify weaknesses that could be used to launch an attack.
When you’re doing penetration testing, it is important to have a scope document outlining the extent of the testing that is to be done. It is equally important to have permission from an administrator who can authorize such testing—in writing—enabling the testing to be conducted.
One weakness a good penetration test looks for is escalation of privilege; that is, a hole created when code is executed with higher privileges than those of the user running it. By breaking out of the executing code, the users are left with higher privileges than they should have.
Three types of penetration testing are black box/unknown environment (the tester has absolutely no knowledge of the system and is functioning in the same manner as an outside attacker), white box/known environment (the tester has significant knowledge of the system, which simulates an attack from an insider—a rogue employee), and gray box/partially known environment (a middle ground between the first two types of testing. In gray box testing, the tester has some limited knowledge of the target system). While the “box” analogy is used to describe the environment, “hats” have often been used to describe the person doing the testing, but that terminology is now being replaced by level of authorization. Therefore, a white hat tester is equivalent to an authorized tester, a black hat tester to an unauthorized tester, and a gray hat tester to a semi-authorized tester.
Note
With so many security-related topics now appearing on the Network+ exam, you have a good head start on Security+ certification study after you successfully finish taking this exam.
Security Information and Event Management
Security information and event management (SIEM) products provide notifications and real-time analysis of security alerts and can help you head off problems quickly. Chapter 8, “Network Operations,” discussed event management and looking at log files, including the security log.
SIEM tools collect, correlate, and display data feeds that support response activities. A SIEM can take individual benign events and tie them together to reveal more details about what occurred and why it’s of concern.
Dashboards are an important element in SIEM solutions, presenting data (and analysis) in actionable format. Most SIEM packages allow organizations to customize their dashboard(s) based on their needs and requirements. One need of any SIEM is to be able to interpret (and visualize) data coming from different sources and, thus, different formats. Normalizing logs involves extracting and processing entries to put them into a readable and structured format that can be displayed and acted upon.
Common Networking Attacks
 Compare and contrast common types of attacks.
Compare and contrast common types of attacks.
Malicious software, or malware, is a serious problem in today’s computing environments. It is often assumed that malware is composed of viruses. Although this typically is true, many other forms of malware by definition are not viruses, but are equally undesirable. Although we commonly associate them with coming from the outside, do not overlook the possibility for them to come from inside threats as well (particularly malicious employees who feel slighted because they did not get a raise or recognition they feel they deserve and have now become an insider threat).
Malware encompasses many types of malicious software and all were intended by their developer to have an adverse effect on the network. The following sections look at some of the more malevolent types.
Denial-of-Service and Distributed Denial-of-Service Attacks
Denial-of-service (DoS) attacks are designed to tie up network bandwidth and resources and eventually bring the entire network to a halt. This type of attack is done simply by flooding a network with more traffic than it can handle. When more than one computer is used in the attack, it is technically known as a distributed DoS (DDoS) attack. These attacks typically use a botnet to launch a command and control attack through a traffic spike. Almost every attack of this type today is DDoS, and we will use DoS to mean both.
A DoS attack is not designed to steal data but rather to cripple a network and, in doing so, cost a company huge amounts of money. It is possible, in fact, for the attack to be an unintentional, or friendly, DoS attack coming from the inside. Just as with friendly fire in combat, it matters not that the attack was unintentional; it does just as much damage.
The effects of DoS attacks include the following:
 Saturating network resources, which then renders those services unusable
Saturating network resources, which then renders those services unusable Flooding the network media, preventing communication between computers on the network
Flooding the network media, preventing communication between computers on the network Causing user downtime because of an inability to access required services
Causing user downtime because of an inability to access required services Causing potentially huge financial losses for an organization because of network and service downtime
Causing potentially huge financial losses for an organization because of network and service downtime
Types of DoS Attacks
Several types of DoS attacks exist, and each seems to target a different area. For instance, they might target bandwidth, network service, memory, CPU, or hard drive space. When a server or other system is overrun by malicious requests, one or more of these core resources breaks down, causing the system to crash or stop responding. A permanent DoS attack continues for more than a short period of time and requires you to change your routing, IP addresses, or other configurations to get around it.
Fraggle
In a Fraggle attack, spoofed UDP packets are sent to a network’s broadcast address. These packets are directed to specific ports, such as port 7 or port 19, and, after they are connected, can flood the system.
Smurfing
The Smurf attack is similar to a Fraggle attack. However, a ping request is sent to a broadcast network address, with the sending address spoofed so that many ping replies overload the victim and prevent it from processing the replies.
Ping of Death
In a ping of death attack, an oversized Internet Control Message Protocol (ICMP) datagram is used to crash IP devices that were manufactured before 1996.
SYN Flood
In a typical TCP session, communication between two computers is initially established by a three-way handshake, referred to as a SYN, SYN/ACK, ACK. At the start of a session, the client sends a SYN message to the server. The server acknowledges the request by sending a SYN/ACK message back to the client. The connection is established when the client responds with an ACK message.
In a SYN attack, the victim is overwhelmed with a flood of SYN packets. Every SYN packet forces the targeted server to produce a SYN/ACK response and then wait for the ACK acknowledgment. However, the attacker doesn’t respond with an ACK, or spoofs its destination IP address with a nonexistent address so that no ACK response occurs. The result is that the server begins filling up with half-open connections. When all the server’s available resources are tied up on half-open connections, it stops acknowledging new incoming SYN requests, including legitimate ones.
Buffer Overflow
A buffer overflow is a type of DoS attack that occurs when more data is put into a buffer (typically a memory buffer) than it can hold, thereby overflowing it (as the name implies).
Distributed Reflective DoS
A distributed reflective DoS (DRDoS) attack is also called an amplification attack, and it targets public UDP servers. Two of the most common protocols/servers that a DRDoS attack usually goes after are Domain Name Service (DNS) and Network Time Protocol (NTP) servers, but Simple Network Management Protocol (SNMP), NetBIOS, and other User Datagram Protocol (UDP) protocols are also susceptible.
ExamAlert
As you study for the exam, be sure to focus on the difference between DoS and DDoS and know that a botnet is formed by many bots (infected systems) and controlled by a command and control server to carry out a DDoS attack.
ICMP Flood
An ICMP flood, also known as a ping flood, is a DoS attack in which large numbers of ICMP messages are sent to a computer system to overwhelm it. The result is a failure of the TCP/IP protocol stack, which cannot tend to other TCP/IP requests.
Other Common Attacks
This section details some of the more common attacks used today.
ExamAlert
Know all the common types of attacks detailed throughout this section. The Network+ exam is extremely likely to ensure your knowledge here is what an administrator should know.
Social Engineering
Social engineering is a common form of cracking. It can be used by both outsiders and people within an organization. Social engineering is a hacker term for tricking people into revealing their password or some form of security information. It might include trying to get users to send passwords or other information over email, following someone closely into a secured area (known as tailgating), walking in with them (known as piggybacking), looking over someone’s shoulder at their screen (known as shoulder surfing), or any other method that tricks users into divulging information. Social engineering is an attack that attempts to take advantage of human behavior.
Logic Bomb
Software programs or code snippets that execute when a certain predefined event occurs are known as logic bombs. Such a bomb may send a note to an attacker when a user is logged on to the Internet and is accessing a certain application, for example. This message could inform the attacker that the user is ready for an attack and open a backdoor. Similarly, a programmer could create a program that always makes sure her name appears on the payroll roster; if it doesn’t, then key files begin to be erased. Any code that is hidden within an application and causes something unexpected to happen constitutes a logic bomb.
Rogue DHCP
A rogue DHCP server added to a network has the potential to issue an address to a client isolating it on an unauthorized network where its data can be captured. Although it sounds like a bad thing, DHCP snooping is just the opposite. It is the capability for a switch to look at packets and drop DHCP traffic that it determines to be unacceptable based on the defined rules. The purpose is to prevent rogue DHCP servers from offering IP addresses to DHCP clients.
Rogue Access Points and Evil Twins
A rogue access point is a wireless access point that has been placed on a network without the administrator’s knowledge. The result is that it is possible to remotely access the rogue access point because it likely does not adhere to company security policies. So, all security can be compromised by a cheap wireless router placed on the corporate network. An evil twin attack is one in which a rogue wireless access point poses as a legitimate wireless service provider to intercept information that users transmit.
Advertising Wireless Weaknesses
Attacks that advertise wireless weaknesses start with war driving—driving around with a mobile device looking for open wireless access points with which to communicate and looking for weak implementations that can be cracked (called WEP cracking or WPA cracking). They then lead to war chalking—those who discover a way in to the network leave signals (often written in chalk) on, or outside, the premise to notify others that the vulnerability is there. The marks can be on the sidewalk, the side of the building, a nearby signpost, and so on.
Phishing
Often users receive a variety of emails offering products, services, information, or opportunities. Unsolicited email of this type is called phishing (pronounced “fishing” ). This technique involves a bogus offer sent to hundreds of thousands or even millions of email addresses. The strategy plays the odds. For every 1,000 emails sent, perhaps one person replies. Phishing can be dangerous because users can be tricked into divulging personal information such as credit card numbers or bank account information. Today, phishing is performed in several ways. Phishing websites and phone calls are also designed to steal money or personal information.
Ransomware
With ransomware, software—often delivered through a Trojan horse—takes control of a system and demands that a third party be paid. The “control” can be accomplished by encrypting the hard drive, by changing user password information, or via any of a number of other creative ways. Users are usually assured that by paying the extortion amount (the ransom), they will be given the code needed to revert their systems to normal operations.
DNS Poisoning
With DNS poisoning, the DNS server is given information about a name server that it thinks is legitimate when it isn’t. This type of attack can send users to a website other than the one to which they wanted to go, reroute mail, or do any other type of redirection wherein data from a DNS server is used to determine a destination. Another name for this is DNS spoofing, and fast flux is one of the most popular techniques. Botnets use it to hide the delivery sites behind a changing network of compromised hosts that act as proxies.
ARP Cache Poisoning
Address Resolution Protocol (ARP) poisoning tries to convince the network that the attacker’s MAC address is the one associated with an IP address so that traffic sent to that IP address is wrongly sent to the attacker’s machine.
Spoofing
Spoofing is a technique in which the real source of a transmission, file, or email is concealed or replaced with a fake source. This technique enables an attacker, for example, to misrepresent the original source of a file available for download. Then he can trick users into accepting a file from an untrusted source, believing it is coming from a trusted source. MAC spoofing is the act of faking the MAC address of a machine—faking its physical identity. While the real MAC address cannot be changed, it is possible for drivers to give values provided to them and fool a system into believing that the NIC it is talking to has the MAC address of a recognized/authorized host. IP spoofing does a similar action with the IP address rather than the MAC address.
Deauthentication
Deauthentication is also known as a disassociation attack. With this type of attack, the intruder sends a frame to the AP with a spoofed address to make it look as if it came from the victim but disconnects the user from the network. Because the victim is unable to keep a connection with the AP, this attack increases the chances of the victim choosing to use another AP—a rogue one or one in a hotel or other venue that he has to pay extra to use. The Federal Trade Commission has filed suits against a number of hotels for launching attacks of this type and generating revenue by requiring their guests to pay for “premium” services rather than being able to use the free Wi-Fi.
Brute Force
There are a number of ways to ascertain a password, but one of the most common is a brute-force attack in which one value after another is guessed until the right value is found. Although that could take forever if done manually, software programs can take lots of values in a remarkably short period of time. Wi-Fi Protected Setup (WPS) attacks, for example, have become much more common since the technology is susceptible to brute-force attacks used to guess the user’s PIN. When an attacker gains access, the attacker is then on the Wi-Fi network.
On-Path Attack
In an on-path attack (previously known as a man-in-the-middle attack), the intruder places himself between the sending and receiving devices and captures the communication as it passes by. The interception of the data is invisible to those sending and receiving the data. The intruder can capture the network data and manipulate it, change it, examine it, and then send it on. Wireless communications are particularly susceptible to this type of attack. A rogue access point, a wireless AP that has been installed without permission, is an example of an on-path attack. If the attack is done with FTP (using the port command), it is known as an FTP bounce attack.
VLAN Hopping
VLAN hopping, as the name implies, is an exploit of resources on a virtual LAN that is made possible because the resources exist on said virtual LAN. There is more than one method by which this occurs, but in all of them, the result is the same: an attacking host on a VLAN gains access to resources on other VLANs that are not supposed to be accessible to them (becoming a compromised system). Again, regardless of the method employed, the solution is to properly configure the switches to keep this from happening.
ExamAlert
A compromised system is any that has been adversely impacted (intentionally or unintentionally) by an untrusted source. The compromise can relate to confidentiality, integrity, or availability (CIA).
ARP Spoofing
With ARP spoofing (also known as ARP poisoning), the Media Access Control (MAC) address of the data is faked. When this value is faked, it is possible to make it look as if the data came from a network that it did not. This technique can be used to gain access to the network, to fool the router into sending data here that was intended for another host, or to launch a DoS attack. In all cases, the address being faked is an address of a legitimate user, and that makes it possible to get around such measures as allow/deny lists.
Vulnerabilities and Prevention
The threat from malicious code is a real concern. You need to take precautions to protect your systems. Although you might not eliminate the threat, you can significantly reduce it.
One of the primary tools used in the fight against malicious software is antivirus/antimalware software. Antimalware software (which includes antivirus software and more) is available from a number of companies, and each offers similar features and capabilities. You can find solutions that are host based, cloud/server based, or network based. Common features and characteristics of antivirus software are as follows:
 Real-time protection: An installed antivirus program should continuously monitor the system looking for viruses. If a program is downloaded, an application opened, or a suspicious email received, the real-time virus monitor detects and removes the threat. The virus application sits in the background, largely unnoticed by the user.
Real-time protection: An installed antivirus program should continuously monitor the system looking for viruses. If a program is downloaded, an application opened, or a suspicious email received, the real-time virus monitor detects and removes the threat. The virus application sits in the background, largely unnoticed by the user. Virus scanning: An antivirus program must scan selected drives and disks, either locally or remotely. You can manually run scanning or schedule it to run at a particular time.
Virus scanning: An antivirus program must scan selected drives and disks, either locally or remotely. You can manually run scanning or schedule it to run at a particular time. Scheduling: It is a best practice to schedule virus scanning to occur automatically at a predetermined time. In a network environment, this time typically is off hours, when the overhead of the scanning process won’t impact users.
Scheduling: It is a best practice to schedule virus scanning to occur automatically at a predetermined time. In a network environment, this time typically is off hours, when the overhead of the scanning process won’t impact users. Live updates: New viruses and malicious software are released with alarming frequency. It is recommended that the antivirus software be configured to regularly receive virus updates.
Live updates: New viruses and malicious software are released with alarming frequency. It is recommended that the antivirus software be configured to regularly receive virus updates. Email vetting: Emails represent one of the primary sources of virus delivery. It is essential to use antivirus software that provides email scanning for both inbound and outbound email.
Email vetting: Emails represent one of the primary sources of virus delivery. It is essential to use antivirus software that provides email scanning for both inbound and outbound email. Centralized management: If antivirus software or antimalware is used in a network environment, it is a good idea to use software that supports managing the virus program from the server. Virus updates and configurations need to be made only on the server, not on each client station.
Centralized management: If antivirus software or antimalware is used in a network environment, it is a good idea to use software that supports managing the virus program from the server. Virus updates and configurations need to be made only on the server, not on each client station.
Managing the threat from viruses is considered a proactive measure, with antivirus software only part of the solution. A complete security protection strategy requires many aspects to help limit the risk of malware, viruses, and other threats:
 Develop in-house policies and rules: In a corporate environment or even a small office, you need to establish what information can be placed on a system. For example, should users download programs from the Internet? Can users bring in their own storage media, such as USB flash drives? Is there a corporate BYOD policy restricting the use of personal smartphones and other mobile devices?
Develop in-house policies and rules: In a corporate environment or even a small office, you need to establish what information can be placed on a system. For example, should users download programs from the Internet? Can users bring in their own storage media, such as USB flash drives? Is there a corporate BYOD policy restricting the use of personal smartphones and other mobile devices? Monitor virus threats: With new viruses coming out all the time, you need to check whether new viruses have been released and what they are designed to do.
Monitor virus threats: With new viruses coming out all the time, you need to check whether new viruses have been released and what they are designed to do. Educate users: One of the keys to a complete antivirus solution is to train users in virus prevention and recognition techniques. If users know what to look for, they can prevent a virus from entering the system or network. Back up copies of important documents. Keep in mind that no solution is absolute, so care should be taken to ensure that the data is backed up. In the event of a malicious attack, redundant information is available in a secure location.
Educate users: One of the keys to a complete antivirus solution is to train users in virus prevention and recognition techniques. If users know what to look for, they can prevent a virus from entering the system or network. Back up copies of important documents. Keep in mind that no solution is absolute, so care should be taken to ensure that the data is backed up. In the event of a malicious attack, redundant information is available in a secure location. Automate virus scanning and updates: You can configure today’s antivirus software to automatically scan and update itself. Because such tasks can be forgotten and overlooked, it is recommended that you have these processes scheduled to run at predetermined times.
Automate virus scanning and updates: You can configure today’s antivirus software to automatically scan and update itself. Because such tasks can be forgotten and overlooked, it is recommended that you have these processes scheduled to run at predetermined times. Don’t run unnecessary services: Know every service that is running on your network and the reason for it. If you can avoid running the service, equate it with putting another lock on the door and do so.
Don’t run unnecessary services: Know every service that is running on your network and the reason for it. If you can avoid running the service, equate it with putting another lock on the door and do so. Keep track of open ports: Just as you don’t want unnecessary services running, you don’t want unnecessary ports left open. Every one of them is an unguarded door through which a miscreant can enter.
Keep track of open ports: Just as you don’t want unnecessary services running, you don’t want unnecessary ports left open. Every one of them is an unguarded door through which a miscreant can enter. Avoid unencrypted channels and clear-text credentials: The days when these were acceptable have passed. Continuing to use them is tantamount to inviting an attack.
Avoid unencrypted channels and clear-text credentials: The days when these were acceptable have passed. Continuing to use them is tantamount to inviting an attack. Shun unsecure protocols: Once upon a time, clear-text passwords were okay to use because risks of anyone getting on your network who should not were minimal. During those days, it was okay to use unsecure protocols as well because the priority was on ease of use as opposed to data protection. These practices went out of acceptance decades ago, so you must—in the interest of security—be careful with the following unsecure protocols: Telnet, HTTP, SLIP, FTP, TFTP, and SNMP (v1 and v2). Secure alternatives—offering the same functionality but adding acceptable levels of security—are available for each. Where possible, opt instead for SSH, SNMPv3, TLS/SSL, SFTP, HTTPS, and IPSec.
Shun unsecure protocols: Once upon a time, clear-text passwords were okay to use because risks of anyone getting on your network who should not were minimal. During those days, it was okay to use unsecure protocols as well because the priority was on ease of use as opposed to data protection. These practices went out of acceptance decades ago, so you must—in the interest of security—be careful with the following unsecure protocols: Telnet, HTTP, SLIP, FTP, TFTP, and SNMP (v1 and v2). Secure alternatives—offering the same functionality but adding acceptable levels of security—are available for each. Where possible, opt instead for SSH, SNMPv3, TLS/SSL, SFTP, HTTPS, and IPSec. Install patches and updates: All applications, including productivity software, virus checkers, and especially the operating system, release patches and updates often, designed to address potential security weaknesses. Administrators must keep an eye out for these patches and install them when they are released. Pay particular attention to unpatched/legacy systems and keep them as secure as possible.
Install patches and updates: All applications, including productivity software, virus checkers, and especially the operating system, release patches and updates often, designed to address potential security weaknesses. Administrators must keep an eye out for these patches and install them when they are released. Pay particular attention to unpatched/legacy systems and keep them as secure as possible.
One of the best tools to use when dealing with problems is knowledge. In several locations, CompTIA stresses that user education is important, but even more important is that administrators know what is going on and keep learning from what is going on now and what has gone on in the past. As an example, TEMPEST is the name of a project commenced by the U.S. government in the late 1950s that all administrators should be familiar with. TEMPEST was concerned with reducing electronic noise from devices that would divulge intelligence about systems and information. This program has become a standard for computer systems certification. TEMPEST shielding protection means that a computer system doesn’t emit any significant amounts of electromagnetic interference (EMI) or radio frequency interference (RFI) (RF emanation). For a device to be approved as a TEMPEST, it must undergo extensive testing, done to exacting standards that the U.S. government dictates. Today, control zones and white noise are used to accomplish the shielding. TEMPEST-certified equipment often costs twice as much as non-TEMPEST equipment.
ExamAlert
Know some of the ways to prevent networking attacks and mitigate vulnerabilities.
Network Hardening and Physical Security
 Given a scenario, apply network hardening techniques.
Given a scenario, apply network hardening techniques. Explain the importance of physical security.
Explain the importance of physical security.
ExamAlert
Remember that the first of the two objectives this section covers begins with “Given a scenario.” This means that you may receive a drag-and-drop, matching, or “live OS” scenario where you have to click through to complete a specific objective-based task.
Having great network security does little good if everything can be compromised by someone walking in your office, picking up your server, and walking out the front door with it. Physical security of the premises is equally important to an overall security implementation.
Ideally, your systems should have a minimum of three physical barriers:
 The external entrance to the building, referred to as a perimeter, which is protected by one or more detection methods. Detection methods usually involve a camera and motion detection. The protection of the perimeter can be accomplished with burglar alarms, external walls, fencing, surveillance, and so on. This type of protection should be used with an access list, which should exist to specifically identify who can enter a facility and can be verified by a security guard or someone in authority. An access control vestibule (previously known as a mantrap) can be used to limit access to only one or two people going into the facility at a time. A properly developed vestibule includes bulletproof glass, high-strength doors, and locks. In high-security and military environments, an armed guard, as well as video surveillance (IP cameras and CCTVs), should be used at the access control vestibule. After a person is inside the facility, additional security and authentication may be required for further entrance.
The external entrance to the building, referred to as a perimeter, which is protected by one or more detection methods. Detection methods usually involve a camera and motion detection. The protection of the perimeter can be accomplished with burglar alarms, external walls, fencing, surveillance, and so on. This type of protection should be used with an access list, which should exist to specifically identify who can enter a facility and can be verified by a security guard or someone in authority. An access control vestibule (previously known as a mantrap) can be used to limit access to only one or two people going into the facility at a time. A properly developed vestibule includes bulletproof glass, high-strength doors, and locks. In high-security and military environments, an armed guard, as well as video surveillance (IP cameras and CCTVs), should be used at the access control vestibule. After a person is inside the facility, additional security and authentication may be required for further entrance. A locked door with door access controls protecting the computer center and network closets. You should also rely on such access control hardware as badge readers (also known as ID badge readers, proximity readers), key fobs, or keys to gain access. Biometrics, such as fingerprint or retinal scans, can be used for authentication.
A locked door with door access controls protecting the computer center and network closets. You should also rely on such access control hardware as badge readers (also known as ID badge readers, proximity readers), key fobs, or keys to gain access. Biometrics, such as fingerprint or retinal scans, can be used for authentication. The entrance to the computer room itself. This entrance should be another locked door that is carefully monitored and protected by keypads and cipher locks. Although you try to keep as many intruders out with the other two barriers, many who enter the building could be posing as someone they are not—heating and air-conditioning technicians, representatives of the landlord, and so on. Although these pretenses can get them past the first two barriers, they should still be stopped by the locked computer room door. If they do manage to gain entry, locking racks, locking cabinets, and even smart lockers (secure storage and distribution systems with computer and sensors built in) should be used to protect hardware and keep it from being absconded.
The entrance to the computer room itself. This entrance should be another locked door that is carefully monitored and protected by keypads and cipher locks. Although you try to keep as many intruders out with the other two barriers, many who enter the building could be posing as someone they are not—heating and air-conditioning technicians, representatives of the landlord, and so on. Although these pretenses can get them past the first two barriers, they should still be stopped by the locked computer room door. If they do manage to gain entry, locking racks, locking cabinets, and even smart lockers (secure storage and distribution systems with computer and sensors built in) should be used to protect hardware and keep it from being absconded. Assets should have asset tags (also known as tracking tags) or tamper tags attached to them that have unique identifiers for each client device in your environment (usually just incrementing numbers corresponding to values in a database) to help you identify and manage your IT assets. Additionally, tamper detection devices should be installed to protect against unauthorized chassis cover and component removal.
Assets should have asset tags (also known as tracking tags) or tamper tags attached to them that have unique identifiers for each client device in your environment (usually just incrementing numbers corresponding to values in a database) to help you identify and manage your IT assets. Additionally, tamper detection devices should be installed to protect against unauthorized chassis cover and component removal.
The objective of any physical barrier is to prevent access to computers and network systems. The most effective physical barrier implementations require that more than one physical barrier be crossed to gain access. This type of approach is called a multiple barrier system.
ExamAlert
Physical security is a recent addition to the Network+ exam. Be sure that you are familiar with the topics discussed here.
One step to never overlook in the security equation is that of employee training. All employees should be trained to look out for social engineering techniques that could be tried on them, the importance of the assets (data and hardware), and that security—also associated with job security—is everyone’s responsibility.
Disposing of Assets
Almost every asset reaches the end of its life at some point in time. Whether that asset is a workstation, a hard drive, a piece of backup media, or something else altogether, care needs to be taken when disposing of it to reduce the risk of sensitive data falling into the wrong hands. As an example, consider that the capacity of a flash drive (also known as a thumb drive, USB drive, jump drive, etc.) is now greater than that of many hard drives only a few years ago and many users now store all of their files on a small drive that they transport with them.
A policy should be created, and implemented, governing the disposal of all assets that hold data. Options of what can be done include performing factory resets (for laptops, tablets, and similar devices), wiping the data, and sanitizing the device before disposal. Sanitizing is simply removing the data and the traces of it; this is usually done with storage devices, such as hard drives, and is often referred to as purging. Wiping goes further than purging and is also known as overwriting (or shredding). With wiping, the data that was there is first replaced with something else and then removed. That way, if the data is somehow recovered, what comes back is the overwritten data rather than the original data. The simplest overwrite technique writes a pattern of zeros over the original data.
Implementing Physical Security
Physical security is a combination of good sense and procedure. The purpose of physical security is to restrict access to network equipment only to people who need it.
The extent to which physical security measures can be implemented to protect network devices and data depends largely on their location. For instance, if a server is installed in a cabinet located in a general office area, the only practical physical protection is to make sure that the cabinet door is locked and that access to keys for the cabinet is controlled. Using other antitheft devices might be practical, but that depends on the location of the cabinet.
However, if your server equipment is located in a cupboard or dedicated room, access restrictions for the room are easier to implement and can be more effective. Again, access should be limited only to those who need it. Depending on the size of the room, this factor might introduce a number of other factors.
Servers and other key networking components are those to which you need to apply the greatest level of physical security. Nowadays, most organizations choose to locate servers in a cupboard or a specific room.
Access to the server room should be tightly controlled, and all access doors must be secured by some method, whether it is a lock and key or a retinal scanning system. Each method of server room access control has certain characteristics. Whatever the method of server room access, it should follow one common principle: control. Some access control methods provide more control than others.
Lock and Key
If access is controlled by lock and key, the number of people with a key should be restricted to only those people who need access. Spare keys should be stored in a safe location, and access to them should be controlled.
Following are some of the features of lock-and-key security:
 Inexpensive: Even a good lock system costs only a few hundred dollars.
Inexpensive: Even a good lock system costs only a few hundred dollars. Easy to maintain: With no back-end systems and no configuration, using a lock and key is the easiest access control method.
Easy to maintain: With no back-end systems and no configuration, using a lock and key is the easiest access control method. Less control than other methods: Keys can be lost, copied, and loaned to other people. There is no record of access to the server room and no way to prove that the key holder is entitled to enter.
Less control than other methods: Keys can be lost, copied, and loaned to other people. There is no record of access to the server room and no way to prove that the key holder is entitled to enter.
Tip
If you use a lock and key for security, make sure that all copies of the original key are stamped DO NOT COPY. That way, it is more difficult for someone to get a copy because reputable key cutters will not make copies of such keys.
Swipe Card and PIN Access
If budgets and policies permit, swipe card and PIN entry systems are good choices for managing physical access to a server room. Swipe card systems use a credit card–sized plastic card read by a reader on the outside of the door. To enter the server room, you must swipe the card (run it through the reader), at which point it is read by the reader, which validates it. Usually, the swipe card’s use to enter the room is logged by the card system, making it possible for the logs to be checked. In higher-security installations, it is common to have a swipe card reader on the inside of the room as well so that a person’s exit can be recorded.
Although swipe card systems have relatively few disadvantages, they do need specialized equipment so that they can be coded with users’ information. They also have the same drawbacks as keys in that they can be lost or loaned to other people. However, the advantage that swipe cards have over key systems is that swipe cards are hard to copy.
PIN pads can be used alone or with a swipe card system. PIN pads have the advantage of not needing any kind of card or key that can be lost. For the budget conscious, PIN pad systems that do not have any logging or monitoring capability can be purchased for a reasonable price. Following are some of the characteristics of swipe card and PIN pad systems:
 Moderately expensive: Some systems, particularly those with management capabilities, are quite expensive.
Moderately expensive: Some systems, particularly those with management capabilities, are quite expensive. Enhanced controls and logging: Each time people enter the server room, they must key in a number or use a swipe card. This process enables systems to log who enters and when.
Enhanced controls and logging: Each time people enter the server room, they must key in a number or use a swipe card. This process enables systems to log who enters and when. Some additional knowledge required: Swipe card systems need special software and hardware that can configure the cards. Someone has to learn how to configure them.
Some additional knowledge required: Swipe card systems need special software and hardware that can configure the cards. Someone has to learn how to configure them.
Biometrics
Although they might still seem like the realm of James Bond, biometric security systems are becoming far more common. Biometric systems work by using some unique characteristic of a person’s identity—such as a fingerprint, a palm print, or a retina scan—to validate that person’s identity.
Although the price of biometric systems has been falling over recent years, they are not widely deployed in small to midsized networks. Not only are the systems themselves expensive, but also their installation, configuration, and maintenance must be considered. Following are some of the characteristics of biometric access control systems:
 Very effective: Because each person entering the room must supply proof-of-person evidence, verification of the person entering the server area is as close to 100 percent reliable as you can get.
Very effective: Because each person entering the room must supply proof-of-person evidence, verification of the person entering the server area is as close to 100 percent reliable as you can get. Nothing to lose: Because there are no cards or keys, nothing can be lost.
Nothing to lose: Because there are no cards or keys, nothing can be lost. Expensive: Biometric security systems and their attendant scanners and software are still relatively expensive and can be afforded only by organizations that have a larger budget; however, prices are sure to drop as more people turn to this method of access control.
Expensive: Biometric security systems and their attendant scanners and software are still relatively expensive and can be afforded only by organizations that have a larger budget; however, prices are sure to drop as more people turn to this method of access control.
Two-Factor and Multifactor Authentication
When two or more access methods are included as part of the authentication process, you’re implementing a multifactor system. A system that uses any two items—such as smartcards and passwords—is referred to as a two-factor authentication system. A multifactor system can consist of a two-factor system, a three-factor system, and so on. As long as more than one factor is involved in the authentication process, it is considered a multifactor system.
For obvious reasons, the two or more factors employed should not be from the same category. Although you do increase difficulty in gaining system access by requiring the user to enter two sets of username/password combinations, it is preferred to pair a single username/password combination with a biometric identifier or other check.
Note
Be sure that you understand that two-factor authentication is a subset of multifactor authentication.
Secured Versus Unsecured Protocols
As you know, any network needs a number of protocols to function. This includes both LAN and WAN protocols. Not all protocols are created the same, however. Some are designed for secure transfer, whereas others are not. Table 9.1 lists several protocols and describes their use.
TABLE 9.1 Protocol Summary
Protocol |
Name |
Description |
|---|---|---|
FTP |
File Transfer Protocol |
A protocol for uploading and downloading files to and from a remote host. It also accommodates basic file management tasks. FTP uses ports 20 and 21. |
SFTP |
Secure File Transfer Protocol |
A protocol for securely uploading and downloading files to and from a remote host. It is based on SSH security. SFTP uses port 22. |
HTTP |
Hypertext Transfer Protocol |
A protocol for retrieving files from a web server. Data is sent in clear text. HTTP uses port 80. |
HTTPS |
Hypertext Transfer Protocol Secure |
A secure protocol for retrieving files from a web server. HTTPS uses SSL to encrypt data between the client and host. HTTPS uses port 443. |
Telnet |
Telnet |
A protocol that enables sessions to be opened on a remote host. Telnet is not considered secure. Telnet uses port 23. |
SSH |
Secure Shell |
A secure alternative to Telnet that enables secure sessions to be opened on a remote host. SSH uses port 22. |
TLS |
Transport Layer Security |
A cryptographic protocol whose purpose is to verify that secure communications between a server and a client remain secure. TLS is an enhancement/replacement for SSL. |
ISAKMP |
Internet Security Association and Key Management Protocol |
A protocol that provides an independent framework for authentication and key exchange. The actual implementation is usually done by IPSec but could be handled by any implementation capable of negotiating, modifying, and deleting security associations. |
RSH |
A UNIX utility used to run commands on a remote machine |
A utility that has been replaced by SSH because RSH sends all data in clear text. |
SCP |
Secure Copy Protocol |
A protocol that enables files to be securely copied between two systems. It uses SSH technology to provide encryption services. |
RCP |
Remote Copy Protocol |
A protocol that copies files between systems, but transport is not secured. |
SNMPv1/2 |
Simple Network Management Protocol versions 1 and 2 |
A network monitoring system used to monitor the network’s condition. Both SNMPv1 and v2 are not secured. |
SNMPv3 |
Simple Network Management Protocol version 3 |
An enhanced SNMP service offering both encryption and authentication services. |
IPSec |
IP security |
IP security that encrypts data during communication between two computers. |
SLIP |
Serial Line Interface Protocol |
A protocol that provides basic encapsulation of the IP protocol over serial and modem connections. |
ExamAlert
You will most certainly be asked questions on secure protocols and when they might be used. Review Table 9.1 before taking the Network+ exam
Hardening Best Practices
In addition to physically securing network devices and opting to run secure protocols in favor of unsecured ones, an administrator should take the following best practices steps to further network hardening:
 Utilize Secure SNMP: The Simple Network Management Protocol (SNMP) collects a lot of data that could be of value to someone looking to compromise a network. Secure SNMP, utilizing SNMPv3, protects the data more by moving from ports 161 and 162 to 10161 and 10162 and enables secure authentication and communication between the SNMP manager and agent.
Utilize Secure SNMP: The Simple Network Management Protocol (SNMP) collects a lot of data that could be of value to someone looking to compromise a network. Secure SNMP, utilizing SNMPv3, protects the data more by moving from ports 161 and 162 to 10161 and 10162 and enables secure authentication and communication between the SNMP manager and agent. Configure Router Advertisement guard: With IPv6, routers will send out multicast messages (router advertisements) to announce their availability and associated information. This information is used by Neighbor Discovery Protocol (NDP) to detect what is available and configure accordingly. A problem is that the messages are unsecured, making them susceptible to spoofing. To increase security, you can configure IPv6 Router Advertisement (RA) guard to protect the network against RA messages generated by unauthorized routers (rogues) trying to join the network.
Configure Router Advertisement guard: With IPv6, routers will send out multicast messages (router advertisements) to announce their availability and associated information. This information is used by Neighbor Discovery Protocol (NDP) to detect what is available and configure accordingly. A problem is that the messages are unsecured, making them susceptible to spoofing. To increase security, you can configure IPv6 Router Advertisement (RA) guard to protect the network against RA messages generated by unauthorized routers (rogues) trying to join the network. Employ Port Security and Dynamic ARP: Port security works at Layer 2 of the OSI model and allows an administrator to configure switch ports so that only certain MAC addresses can use the port. This is a common feature on both Cisco’s Catalyst as well as Juniper’s EX Series switches and essentially differentiates so-called dumb switches from managed (or intelligent) switches. Similarly, Dynamic ARP Inspection (DAI) works with these and other smart switches to protect ports from ARP spoofing.
Employ Port Security and Dynamic ARP: Port security works at Layer 2 of the OSI model and allows an administrator to configure switch ports so that only certain MAC addresses can use the port. This is a common feature on both Cisco’s Catalyst as well as Juniper’s EX Series switches and essentially differentiates so-called dumb switches from managed (or intelligent) switches. Similarly, Dynamic ARP Inspection (DAI) works with these and other smart switches to protect ports from ARP spoofing. Implement Control Plane Policing: Many routers and switches include a Control Plane Policing feature that enables you to configure a quality of service (QoS) filter to protect against DoS attacks. When enabled, the control plane (CP) can continue to forward packets despite an attack or abnormally heavy traffic load on the router/switch.
Implement Control Plane Policing: Many routers and switches include a Control Plane Policing feature that enables you to configure a quality of service (QoS) filter to protect against DoS attacks. When enabled, the control plane (CP) can continue to forward packets despite an attack or abnormally heavy traffic load on the router/switch. Use private VLANs: Also known as port isolation, creating a private VLAN is a method of restricting switch ports (now called private ports) so that they can communicate only with a particular uplink. The private VLAN usually has numerous private ports and only one uplink, which is usually connected to a router, or firewall.
Use private VLANs: Also known as port isolation, creating a private VLAN is a method of restricting switch ports (now called private ports) so that they can communicate only with a particular uplink. The private VLAN usually has numerous private ports and only one uplink, which is usually connected to a router, or firewall. Disable unneeded ports: Disabling unnecessary services (mentioned next) increases security by removing doors that someone could use to enter the server. Similarly, IP ports that are not needed for devices also represent doors that could be used to sneak in. It is highly recommended that unused ports be disabled to increase security along with device ports (both physical and virtual ports).
Disable unneeded ports: Disabling unnecessary services (mentioned next) increases security by removing doors that someone could use to enter the server. Similarly, IP ports that are not needed for devices also represent doors that could be used to sneak in. It is highly recommended that unused ports be disabled to increase security along with device ports (both physical and virtual ports). Disable unneeded services: Every unnecessary service that is running on a server is akin to another door on a warehouse that someone unauthorized may choose to sneak in. Just as an effective way to secure a warehouse is to reduce the number of doors to only those needed, so too is it recommended that a server be secured by removing (disabling) services not in use.
Disable unneeded services: Every unnecessary service that is running on a server is akin to another door on a warehouse that someone unauthorized may choose to sneak in. Just as an effective way to secure a warehouse is to reduce the number of doors to only those needed, so too is it recommended that a server be secured by removing (disabling) services not in use. Change default passwords: The easiest way for any unauthorized individual to access a device is to use the default credentials. Many routers, for example, come configured with an “admin” account and a simple value for the password (“admin,” “password,” and so on). Anyone owning one of those routers knows those values and could use them to access any other of the same make if the values have not been changed. To make it more difficult for unauthorized users to access your devices, change those default usernames and passwords as soon as you start using them.
Change default passwords: The easiest way for any unauthorized individual to access a device is to use the default credentials. Many routers, for example, come configured with an “admin” account and a simple value for the password (“admin,” “password,” and so on). Anyone owning one of those routers knows those values and could use them to access any other of the same make if the values have not been changed. To make it more difficult for unauthorized users to access your devices, change those default usernames and passwords as soon as you start using them. Avoid common passwords and increase complexity: It is a good thing to preach password security to users, but often administrators are guilty of using too-simplistic passwords on network devices such as routers, switches, and the like. Given the large number of devices in question, sometimes the same passwords are also used on multiple devices. Common sense tells every administrator that this approach is wrong, but often it is done anyway with the hope that no miscreant will try to gain unauthorized access. Don’t be that administrator: use complex passwords, with notable length, and use a different password for each device, increasing the overall security of your network.
Avoid common passwords and increase complexity: It is a good thing to preach password security to users, but often administrators are guilty of using too-simplistic passwords on network devices such as routers, switches, and the like. Given the large number of devices in question, sometimes the same passwords are also used on multiple devices. Common sense tells every administrator that this approach is wrong, but often it is done anyway with the hope that no miscreant will try to gain unauthorized access. Don’t be that administrator: use complex passwords, with notable length, and use a different password for each device, increasing the overall security of your network. Enable DHCP snooping: As was mentioned when discussing rogue DHCP servers earlier in this chapter, DHCP snooping is a good thing. It provides a way for a switch to look at packets and drop DHCP traffic that it determines to be unacceptable based on a set of defined rules to prevent rogue DHCP servers from offering IP addresses to clients.
Enable DHCP snooping: As was mentioned when discussing rogue DHCP servers earlier in this chapter, DHCP snooping is a good thing. It provides a way for a switch to look at packets and drop DHCP traffic that it determines to be unacceptable based on a set of defined rules to prevent rogue DHCP servers from offering IP addresses to clients. Change the default VLAN: On switches, the native VLAN is the only VLAN that is not tagged in a trunk. This means that native VLAN frames are transmitted unchanged. By default, the native VLAN is port 1, and that default represents a weakness in that it is something known about your network that an attacker could use. To strengthen security, albeit a small amount, you can change the native VLAN to another port. The command or commands used to do so are dependent on the vendor and model of your switch but can be easily found online.
Change the default VLAN: On switches, the native VLAN is the only VLAN that is not tagged in a trunk. This means that native VLAN frames are transmitted unchanged. By default, the native VLAN is port 1, and that default represents a weakness in that it is something known about your network that an attacker could use. To strengthen security, albeit a small amount, you can change the native VLAN to another port. The command or commands used to do so are dependent on the vendor and model of your switch but can be easily found online. Utilize patch and firmware management: There is a reason why each firmware update is written. Sometimes, it is to optimize the device or make it more compatible with other devices. Other times, it is to fix security issues and/or head off identified problems. Keep firmware on your production machines current after first testing the upgrades on lab machines and verifying that you’re not introducing any unwanted problems by installing. Just as firmware upgrades are intended to strengthen or solve problems, patches and updates do the same with software (including operating systems). Test each release on a lab machine(s) to make sure you are not adding to network woes, and then keep your software current to harden it.
Utilize patch and firmware management: There is a reason why each firmware update is written. Sometimes, it is to optimize the device or make it more compatible with other devices. Other times, it is to fix security issues and/or head off identified problems. Keep firmware on your production machines current after first testing the upgrades on lab machines and verifying that you’re not introducing any unwanted problems by installing. Just as firmware upgrades are intended to strengthen or solve problems, patches and updates do the same with software (including operating systems). Test each release on a lab machine(s) to make sure you are not adding to network woes, and then keep your software current to harden it. Put an access control list in place: Discussed at length in this chapter, access control is necessary to limit who can access resources to only those who should have access and thus protect those resources. Access control lists (ACLs) enable devices in your network to ignore requests from specified users or systems or to grant them access to certain network capabilities. You may find that a certain IP address is constantly scanning your network, and you can block this IP address at the router and the IP address will automatically be rejected any time it attempts to utilize your network.
Put an access control list in place: Discussed at length in this chapter, access control is necessary to limit who can access resources to only those who should have access and thus protect those resources. Access control lists (ACLs) enable devices in your network to ignore requests from specified users or systems or to grant them access to certain network capabilities. You may find that a certain IP address is constantly scanning your network, and you can block this IP address at the router and the IP address will automatically be rejected any time it attempts to utilize your network. Apply role-based access: It is recommended that role-based access be applied where possible. The difference between this approach and others was discussed earlier in this chapter.
Apply role-based access: It is recommended that role-based access be applied where possible. The difference between this approach and others was discussed earlier in this chapter. Enforce firewall rules: Firewall rules are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rule’s criteria: block the connection (explicit deny), accept the connection, or allow the connection if conditions are met (such as it being secured). It is this last condition that is the most difficult to configure, and conditions usually end with an implicit deny clause. An implicit deny clause means that if the proviso in question has not been explicitly granted, access is denied.
Enforce firewall rules: Firewall rules are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rule’s criteria: block the connection (explicit deny), accept the connection, or allow the connection if conditions are met (such as it being secured). It is this last condition that is the most difficult to configure, and conditions usually end with an implicit deny clause. An implicit deny clause means that if the proviso in question has not been explicitly granted, access is denied.
Note
Where it exists, an explicit deny takes precedence over all other settings
 Verify file hashes: File hashing is used to verify that the contents of files are unaltered. A hash is often created on a file before it is downloaded and then hashed after the download so the two values can be compared to make sure the contents are the same. When downloading files—particularly upgrades, patches, and updates—check hash values and use this one test to keep from installing those entities that have had Trojan horses attached to them.
Verify file hashes: File hashing is used to verify that the contents of files are unaltered. A hash is often created on a file before it is downloaded and then hashed after the download so the two values can be compared to make sure the contents are the same. When downloading files—particularly upgrades, patches, and updates—check hash values and use this one test to keep from installing those entities that have had Trojan horses attached to them. Generate new keys: Keys are used as a part of the encryption process, particularly with public key infrastructure (PKI), to encrypt and decrypt messages. The longer you use the same key, the longer the opportunity becomes for someone to crack that key. To increase security, generate new keys on a regular basis: The commands to do so will differ based on the utility that you are creating the keys for.
Generate new keys: Keys are used as a part of the encryption process, particularly with public key infrastructure (PKI), to encrypt and decrypt messages. The longer you use the same key, the longer the opportunity becomes for someone to crack that key. To increase security, generate new keys on a regular basis: The commands to do so will differ based on the utility that you are creating the keys for.
ExamAlert
Most of the items appearing in the preceding list are the topics beneath objective 4.3; make sure you know them for the exam.
Wireless Security
Wireless systems transmit data through the air and can be much more difficult to secure than those dependent on wires that can be physically protected. The growth of wireless systems in every workplace and home creates many opportunities for attackers looking for signals that can be easily intercepted. This section discusses various types of wireless systems that you’ll likely encounter and some of the security issues associated with this technology.
MAC Filtering
To increase wireless security, some APs enable you to configure MAC address filtering and guest access. MAC address filtering enables you to limit access to only those specified hosts. Guest access uses a different password and network name and enables visitors to use the Internet without having access to the rest of the network (thus avoiding your data and computers).
ExamAlert
Make sure that you understand the purpose of MAC address filtering and that this works the same whether the network is wired or wireless.
Antenna Placement and Power Levels
Antenna placement can be crucial in allowing clients to reach the access point. There isn’t a universal solution to this issue, and it depends on the environment in which the access point is placed. As a general rule, the greater the distance the signal must travel, the more it will attenuate, but you can lose a signal quickly over a short distance as well if the building materials reflect or absorb the signal. You should try to avoid placing access points near metal (which includes appliances) or near the ground. Placing them in the center of the area to be served and high enough to get around most obstacles is recommended. On the chance that the signal is actually traveling too far, some access points include power level controls, which allow you to reduce the amount of output provided. Both a heat map and a site survey can be used to optimize wireless antenna placement.
Isolation
As the name implies, isolation is the process of keeping something from communicating with others. This can be done on a wireless network with a single client (wireless client isolation) or a guest network (guest network isolation). With the latter, the guest user cannot see any other connected devices even though they are logged in to the network. Most wireless routers allow for creating a private network in each frequency and thus enabling temporary users (guests) to access the Internet and their own files without jeopardizing the rest of the network’s resources.
Preshared Keys
During the authentication process, keyed security measures are applied before communication can take place. On many APs, authentication can be set to either shared key authentication or open authentication. The default setting for older APs typically is open authentication. Open authentication enables access with only the SSID and/or the correct WEP key for the AP. The problem with open authentication is that if you do not have other protection or authentication mechanisms in place, your wireless network is totally open to intruders. When set to shared key mode, the client must meet security requirements before communication with the AP can occur.
Shared key mode requires that a WEP key be configured on both the client system and the AP. This makes authentication with WEP-Shared mandatory, so it is more secure for wireless transmission. WPA-PSK, the acronym for Wi-Fi Protected Access with Preshared Key, is a stronger form of encryption in which keys are automatically changed and authenticated between devices after a specified period of time or after a specified number of packets have been transmitted.
Note
One implementation of WPA is known as WPA2 Personal. This implementation uses a preshared key (PSK), whereas WPA2 Enterprise needs an authentication server. WPA3 is a newer standard in use today, and it uses Simultaneous Authentication of Equals (SAE) instead of PSK, enabling users to choose easier-to-remember passwords. An additional benefit is that by using forward secrecy, WPA3 does not compromise traffic already transmitted even if the password itself becomes compromised.
Geofencing
Any wireless technology, but usually GPS and sometimes RFID, can be used to create a virtual geographic boundary. This boundary is called a geofence. After that boundary is defined, software can be used to trigger a response when a device enters or leaves that area. A section of a supermarket, for example, can be configured to text a coupon code to iPhones for a percentage off milk purchases to any phone coming within 10 feet of the dairy section.
Similar technology can be used to take attendance in a classroom, at a meeting location, and so on. Because events can be triggered for not only entering a zone but also leaving it, this technology could be used to send a message to parents if a child leaves the virtually defined neighborhood, and so on. Still in its infancy, geofencing technology is expected to grow in acceptance and application over the next few years.
ExamAlert
Remember that the goal of geofencing is to have a defined boundary and then be able to respond to what either enters or leaves that area.
Captive Portal
As you might recall from Chapter 6, “Wireless Solutions and Issues,” most public networks, including Wi-Fi hotspots, use a captive portal, which requires users to agree to some condition before they use the network or Internet. The condition could be to agree to the acceptable use policy, payment charges for the time they are using the network, and so forth.
One of the most popular implementations of captive portals is a Cisco application in its Identity Services Engine. However, there have been vulnerabilities identified with it, which enable attackers to intercept clear-text values.
IoT Access Considerations
With so many sensors being added to networks today, the Internet of Things (IoT) opens up a can of networking opportunities, but each comes with its own set of security issues. From the standpoint of a network administrator, it is critical that you treat these devices the same as any other resource connected to the network, constantly keep abreast of discovered security vulnerabilities, and patch when/where needed.
Remote-Access Methods
 Compare and contrast remote-access methods and security implications.
Compare and contrast remote-access methods and security implications.
Several protocols are associated with remote-control access that you should be aware of: Remote Desktop Protocol (RDP), Secure Shell (SSH), Virtual Network Computing (VNC), and Telnet. RDP is used in a Windows environment and is now called Remote Desktop Services (RDS). It provides a way for a client system to connect to a server, such as Windows Server, and, by using RDP, operate on the server as if they were local client applications. Such a configuration is known as thin client computing, whereby client systems use the resources of the server instead of their local processing power.
Windows products (server as well as client) have built-in support for Remote Desktop Connections. The underlying protocol used to manage the connection is RDP. RDP is a low-bandwidth protocol used to send mouse movements, keystrokes, and bitmap images of the screen on the server to the client computer. RDP does not actually send data over the connection—only screenshots and client keystrokes. RDP uses TCP and UDP port 3389.
Building on RDP, a Remote Desktop Gateway offers an RDP-type of HTTPS VPN service over TCP 443 and UDP 3391. This allows users from outside the corporate firewall to connect to internal network resources (such as a work computer) from a remote device (Windows PC, Mac, tablet, smartphone, etc.) using Microsoft’s Remote Desktop connection. The benefit of a remote desktop gateway is that it increases security by encapsulating the session with TLS and does not require a VPN.
SSH is a tunneling protocol originally created for UNIX/Linux systems. It uses encryption to establish a secure connection between two systems and provides alternative, security-equivalent applications for such utilities as Telnet, File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP), and other communications-oriented applications. Although it is available with Windows and other operating systems, it is the preferred method of security for Telnet and other clear-text-oriented programs in the UNIX/Linux environment. SSH uses port 22 and TCP for connections.
Virtual Network Computing (VNC) enables remote login, in which clients can access their own desktops while being physically away from their computers. By default, it uses port 5900, and it is not considered overly secure.
Telnet enables sessions to be opened on a remote host and is one of the oldest TCP/IP protocols still in use today. On most systems, Telnet is blocked because of problems with security (it truly does not have any), and SSH is considered a secure alternative to Telnet that enables secure sessions to be opened on the remote host.
ExamAlert
Be sure that you know the ports associated with RDP (3389), Telnet (23), FTP (20, 21), VNC (5900), and SSH (22).
ExamAlert
The protocols described in this chapter enable access to remote systems and enable users to run applications on the system, using that system’s resources. Only the user interface, keystrokes, and mouse movements transfer between the client system and the remote computer.
Remote File Access
File Transfer Protocol (FTP) is an application that allows connections to FTP servers for file uploads and downloads. FTP is a common application that uses ports 20 and 21 by default. It is used to transfer files between hosts on the Internet but is inherently insecure. A number of options have been released to try to create a more secure protocol, including FTP over SSL (FTPS), which adds support for SSL cryptography, and SSH File Transfer Protocol (SFTP), which is also known as Secure FTP.
An alternative utility for copying files is Secure Copy (SCP), which uses port 22 by default and combines an old remote copy program (RCP) from the first days of TCP/IP with SSH.
On the opposite end of the spectrum from a security standpoint is the Trivial File Transfer Protocol (TFTP), which can be configured to transfer files between hosts without any user interaction (unattended mode). It should be avoided anywhere there are more secure alternatives.
VPNs
A virtual private network (VPN) encapsulates encrypted data inside another datagram that contains routing information. The connection between two computers establishes a switched connection dedicated to the two computers. The encrypted data is encapsulated inside Point-to-Point Protocol (PPP), and that connection is used to deliver the data.
A VPN enables users with an Internet connection to use the infrastructure of the public network to connect to the main network and access resources as if they were logged on to the network locally. It also enables two networks to be connected to each other securely.
To put it more simply, a VPN extends a LAN by establishing a remote connection using a public network such as the Internet. A VPN provides a point-to-point dedicated link between two points over a public IP network. For many companies, the VPN link provides the perfect method to expand their networking capabilities and reduce their costs. By using the public network (Internet), a company does not need to rely on expensive private leased lines to provide corporate network access to its remote users. Using the Internet to facilitate the remote connection, the VPN enables network connectivity over a possibly long physical distance. In this respect, a VPN is a form of wide-area network (WAN).
Note
Many companies use a VPN to provide a cost-effective method to establish a connection between remote clients and a private network. There are other times a VPN link is handy. You can also use a VPN to connect one private LAN to another, known as LAN-to-LAN internetworking. For security reasons, you can use a VPN to provide controlled access within an intranet. As an exercise, try drawing what the VPN would look like in these two scenarios.
Components of the VPN Connection
A VPN enables anyone with an Internet connection to use the infrastructure of the public network to dial in to the main network and access resources as if the user were locally logged on to the network. It also enables two networks to securely connect to each other.
Many elements are involved in establishing a VPN connection, including the following:
 VPN client: This computer initiates the connection to the VPN server.
VPN client: This computer initiates the connection to the VPN server. VPN server: This server authenticates connections from VPN clients.
VPN server: This server authenticates connections from VPN clients. Access method: As mentioned, a VPN is most often established over a public network such as the Internet; however, some VPN implementations use a private intranet. The network used must be IP based.
Access method: As mentioned, a VPN is most often established over a public network such as the Internet; however, some VPN implementations use a private intranet. The network used must be IP based. VPN protocols: These protocols are required to establish, manage, and secure data over the VPN connection. Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP) are commonly associated with VPN connections. These protocols enable authentication and encryption in VPNs. Authentication enables VPN clients and servers to correctly establish the identity of people on the network. Encryption enables potentially sensitive data to be guarded from the general public.
VPN protocols: These protocols are required to establish, manage, and secure data over the VPN connection. Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP) are commonly associated with VPN connections. These protocols enable authentication and encryption in VPNs. Authentication enables VPN clients and servers to correctly establish the identity of people on the network. Encryption enables potentially sensitive data to be guarded from the general public.
VPNs have become popular because they enable the public Internet to be safely used as a WAN connectivity solution.
ExamAlert
VPNs support analog modems, Integrated Services Digital Network (ISDN) wireless connections, and dedicated broadband connections, such as cable and digital subscriber line (DSL). Remember these details for the exam.
VPN Connection Types
Two types of client-to-site VPN connections are possible: full tunnel and split tunnel. When full tunnel is used, all requests through the VPN are encrypted regardless of where the service is hosted, and it is not possible to access local network resources. With split tunnel, all incoming requests are encrypted over the VPN, but traffic going to sites outside the client network (including Zoom, Office 365, Google) does not go through the VPN server. Full tunnel is more secure and generally recommended.
When a choice between the two exists, it is recommended that you use full tunnel if you are connecting from an untrusted network such as in a coffee shop or hotel. While split tunnel may be necessary if there is a need to access both local resources and the organization’s resources, you should always recognize that it is less secure, so a better option is to disconnect from the VPN first before accessing those other sites.
VPN Pros and Cons
As with any technology, VPN has both pros and cons. Fortunately with VPN technology, these are clear cut, and even the cons typically do not prevent an organization from using VPNs in its networks. Using a VPN offers two primary benefits:
 Cost: If you use the infrastructure of the Internet, you do not need to spend money on dedicated private connections to link remote clients to the private network. Furthermore, when you use the public network, you do not need to hire support personnel to support those private links.
Cost: If you use the infrastructure of the Internet, you do not need to spend money on dedicated private connections to link remote clients to the private network. Furthermore, when you use the public network, you do not need to hire support personnel to support those private links. Easy scalability: VPNs make it easy to expand the network. Employees who have a laptop with wireless capability can simply log on to the Internet and establish the connection to the private network.
Easy scalability: VPNs make it easy to expand the network. Employees who have a laptop with wireless capability can simply log on to the Internet and establish the connection to the private network.
Table 9.2 outlines some of the advantages and potential disadvantages of using a VPN.
TABLE 9.2 Pros and Cons of Using a VPN
Advantage |
Description |
|---|---|
Reduced cost |
When you use the Internet, you do not need to rent dedicated lines between remote clients and a private network. In addition, a VPN can replace remote-access servers and long-distance dial-up network connections that were commonly used in the past by business travelers who needed access to their company intranet. This way, you eliminate long-distance phone charges. |
Network scalability |
The cost to an organization to build a dedicated private network may be reasonable at first, but it increases exponentially as the organization grows. The Internet enables an organization to grow its remote client base without having to increase or modify an internal network infrastructure. |
Reduced support |
Using the Internet, organizations do not need to employ support personnel to manage a VPN infrastructure. |
Simplicity |
With a VPN, a network administrator can easily add remote clients. All authentication work is managed from the VPN authentication server, and client systems can be easily configured for automatic VPN access. |
Disadvantage |
Description |
Security |
Using a VPN, data is sent over a public network, so data security is a concern. VPNs use security protocols to address this shortcoming, but VPN administrators must understand data security over public networks to ensure that data is not tampered with or stolen. |
Reliability |
The reliability of the VPN communication depends on the public network and is not under an organization’s direct control. Instead, the solution relies on an Internet service provider (ISP) and its quality of service (QoS). |
IPSec
The IP Security (IPSec) protocol is designed to provide secure communications between systems. This includes system-to-system communication in the same network, as well as communication to systems on external networks. IPSec is an IP layer security protocol that can both encrypt and authenticate network transmissions. In a nutshell, IPSec is composed of two separate protocols: Authentication Header (AH) and Encapsulating Security Payload (ESP). AH provides the authentication and integrity checking for data packets, and ESP provides encryption services.
ExamAlert
IPSec relies on two underlying protocols: AH and ESP. AH provides authentication services, and ESP provides encryption services.
Using both AH and ESP, data traveling between systems can be secured, ensuring that transmissions cannot be viewed, accessed, or modified by those who should not have access to them. It might seem that protection on an internal network is less necessary than on an external network; however, much of the data you send across networks has little or no protection, allowing unwanted eyes to see it.
Note
The Internet Engineering Task Force (IETF) created IPSec, which you can use on both IPv4 and IPv6 networks.
IPSec provides three key security services:
 Data verification: Verifies that the data received is from the intended source
Data verification: Verifies that the data received is from the intended source Protection from data tampering: Ensures that the data has not been tampered with or changed between the sending and receiving devices
Protection from data tampering: Ensures that the data has not been tampered with or changed between the sending and receiving devices Private transactions: Ensures that the data sent between the sending and receiving devices is unreadable by any other devices
Private transactions: Ensures that the data sent between the sending and receiving devices is unreadable by any other devices
IPSec operates at the network layer of the Open Systems Interconnection (OSI) reference model and provides security for protocols that operate at the higher layers. Thus, by using IPSec, you can secure practically all TCP/IP-related communications.
SSL/TLS/DTLS
Security is often provided by working with the Transport Layer Security (TLS) protocol (which has replaced Secure Sockets Layer in most implementations). SSL VPN, also marketed as WebVPN and OpenVPN, can be used to connect locations that would run into trouble with firewalls and NAT when used with IPSec. It is known as an SSL VPN whether the encryption is done with TLS or truly with the older SSL.
Note
SSL was first created for use with the Netscape web browser and is used with a limited number of TCP/IP protocols (such as HTTP and FTP). TLS is not only an enhancement to SSL but also a replacement for it, working with almost every TCP/IP protocol. Because of this, TLS is popular with VPNs and VoIP applications. Just as the term Kleenex is often used to represent any paper tissue, whether or not it is made by Kimberly-Clark, SSL is often the term used to signify the confidentiality function, whether it is actually SSL in use or TLS (the latest version of which is 1.2).
The Datagram Transport Layer Security (DTLS) protocol is a derivation of SSL/TLS by the OpenSSL project; it provides the same security services but strives to increase reliability.
The National Institute of Standards and Technology (NIST) publishes the Guide to SSL VPNs, which you can access at https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-113.pdf.
Site-to-Site and Client-to-Site
The scope of a VPN tunnel can vary, with the two most common variations being site-to-site and client-to-site (also known as host-to-site). A third variation is host-to-host, but it is really a special implementation of site-to-site. In a site-to-site implementation, as the name implies, whole networks are connected together. An example would be divisions of a large company. Because the networks are supporting the VPN, each gateway does the work, and the individual clients do not need to have any VPN.
In a client-to-site scenario, individual clients (such as telecommuters or travelers) connect to the network remotely. Because the individual client makes a direct connection to the network, each client doing so must have VPN client software installed.
ExamAlert
Be sure that you understand that site-to-site and client-to-site are the two most common types of VPNs.
Virtual Desktops
What is called a virtual desktop can differ from vendor to vendor, but generally it is a preconfigured image of an operating system and applications wherein the desktop environment is separated from the physical device used to access it. The virtual desktop can be accessed remotely (thin clients were mentioned earlier in this section), and any endpoint device (laptop, tablet, smartphone, etc.) can be used.
Upon connecting, the virtual desktop provider installs the necessary client software on the endpoint device, and the user then interacts with that software on the device with it looking like a physical workstation. Depending on the type of implementation and configuration, users may or may not be able to save changes or permanently install applications, but they experience their desktop the same way every time they log in, no matter which device they are logging in from.
Virtual desktops differ from virtual machines in that the operating system for the virtual desktop lives in the data center, and not the endpoint. Typically, the virtual desktop is running within a virtual machine housed at the cloud host data center.
HTTPS/Management URL
HTTP Secure (HTTPS) is the protocol used for “secure” web pages that users should see when they must enter personal information such as credit card numbers, passwords, and other identifiers. It combines HTTP with SSL/TLS to provide encrypted communication. The default port is 443, and the URL begins with https:// instead of http://.
HTTPS is the common protocol used for management URLs to perform tasks such as checking server status, changing router settings, and so on.
Authentication and Authorization Considerations
When implementing remote access, administrators must recognize that they are increasing risk. The safest network to secure is one without users. The next safest is one in which all users must physically be present within a confined area. Once you open the network up to users from anywhere, you increase the risks of harm to data and security violations. In all cases, administrators should attempt to mitigate these risks as much as possible, and this is particularly true when it comes to authentication and authorization.
Throughout much of this chapter, the discussion has been on security and how to increase it, and thus, there is little new to add here other than to reiterate the importance of authenticating users (using multifactor authentication) and focusing on the CIA security triad—confidentiality, integrity, and availability. You should take every reasonable measure to prevent unauthorized users from accessing data, and, similarly, you should take every reasonable step to make sure that the data and systems are available for authorized users all the time.
Out-of-Band Management
When a dedicated channel is established for managing network devices, it is known as out-of-band management. A connection can be established via a console router, or modem, and this can be used to ensure management connectivity independent of the status of in-band network connectivity (which would include serial port connections, VNC, and SSH). Out-of-band management lets administrators monitor, access, and manage network infrastructure devices remotely and securely, even when everything else is down.
What’s Next?
The final chapter of this book, “Network Troubleshooting,” focuses on all areas of network troubleshooting, including troubleshooting best practices and some of the tools and utilities you use to assist in the troubleshooting process.
No matter how well a network is designed and how many preventive maintenance schedules are in place, troubleshooting is always necessary. Consequently, network administrators must develop those troubleshooting skills.
