4 Data Mining and E-banking Security
Manu Bala, Seema Baghla, and Gaurav Gupta
Contents
4.1.4 Current Security Systems for E-banking
4.2.2 Data Mining Applications
4.4.3 Implementation Using SPSS Software
4.1 Introduction
4.1.1 E-banking
“Web managing” an account empowers a client to carry out money exchanges through the bank’s site. This is also called “virtual managing” or “anyplace managing” an account [1]. It resembles moving the bank to one’s PC at one’s preferred place and time. Most customers who select web-based banking to manage their money normally identify advantages, like paying electronic bills in instalments. The e-banking services in India can be classified as below [1]:
- 1. Informational e-banking: In informational e-banking services, the server is the administrator of the banking system, and the bank’s features, and items are promoted by the administrator itself. Risk-associated web management of the accounts involves the banking server itself [1].
- 2. Communicative e-banking: The bank and its clients communicate with each other using communicative e-banking, such as email, enterprise resource planning (ERP) system, requesting account operations, and using advanced applications, such as artificial intelligence, to access their personal records [1].
- 3. Transactional e-banking: Clients can carry out transactions and exchanges with the bank, using transactional e-banking services. Transactional e-banking services include account transactional information, paying various bills and invoices, interactions with other banks for fund transfers, etc. [1].
4.1.2 Security in E-banking
The security of data in e-banking primarily consists of three basic aspects, namely accessibility, responsibility, and secrecy. These aspects of e-banking security issues address particular concerns, such as trust of the client being lost, resulting in the client leaving the bank [2]. The main issue related to security is to keep the customer’s username and passcode safe, to avoid any phishing attack incurring a loss to the customer, safeguarding the customer’s e-banking details, even during a crash of the bank server [2].
E-banking basically involves electronic management of a client’s account in order to help the client make e-transactions, using the bank’s website and applications, benefitting the client and allowing a boost in e-business activities. E-banking services have been characterized by different banking platforms. The following salient points list out the importance and highlights of e-banking services:
- To combine the services of banking and develop innovative services.
- To encourage clients to perform transactions and make purchases through the internet, leading to savings in time and monetary charges.
- To make almost all of the exchanges electronically, without the need to physically contact any organizations.
- To manage and administer the accounting systems of the client by using data innovation, involving using a third-party banking service [3].
The common e-banking services come under following categories [2, 3]:
- Electronic charge introductions and instalment payments.
- Fund transfers.
- Recording of client’s bank transactions.
- Online purchases and bill payments.
- Loan-related applications, such as loan repayments, loan re-imbursements etc.
- Support for clients with different levels of e-banking requirements for financial transactions and expertise.
- E-money exchange services.
- E-ticket booking services.
- E-bill payment services.
- E-shopping services, etc.
E-banking basically involves the use of data innovation by banking systems to encourage the use of online financial and transaction services, to save time and money incurred for various financial transactions, with proper planning for the security and ease-of-use by the client. The system estimates the client’s e-banking usage capabilities and then matches it with the e-capabilities of the banking systems. Physical approaches to banking services will then be used only by older customers or by customers who do not have the knowledge or experience to operate the e-banking system. Sometimes, it can become a major issue to determine which system best suits each customer.
Customers are rapidly switching to e-banking and are more satisfied by e-banking services rather than by physical banking [3]. The business has much greater potential for growth, due to very fast money transfer systems. ATM services are the best way for customers to withdraw the money without any interface or interruptions in service, from any location at any time [3]. E-banking normally includes services such as using ATMs, credit cards, smart cards, debit-cum-shopping cards, mobile, internet, telephone banking, and electronic fund transfer systems, such as national electronic fund transfer (NEFT), real time gross settlement (RTGS), immediate payment service (IMPS), etc.
4.1.3 Attacks on E-banking
Hackers basically use a number of ways to break into the bank’s secure framework. It is of utmost importance to focus on security against such attacks. For the design of a secure e-banking system, an understanding of the various types of attacks that can be carried out on the e-banking systems is very important and must take the highest priority to achieve success of an efficient e-banking system. The following list points out the various types of attack possible on e-banking frameworks:
- a) Port Scanners
Port scanners can be used by attackers to compromise the security systems of the bank’s frameworks. Attackers learn about various sections of the bank’s framework, and use various strategies to draw and track customer data. The programming based port scanners are used by attackers to accumulate and trap secure customer data and misuse it [3]. - b) Bundle Sniffers
Bundle sniffers track and trap client’s personal data and transaction records by utilizing a link between the client’s system and the internet. To block sniffers, a secure layer is used by the developers to provide more secure banking systems that does not allow sniffers to trap sensitive information [3]. - c) Secret Word Cracking
Various unscrambling procedures have been adopted by hackers, using secret word breaking. If the e-banking framework does not require good passwords, these attackers can exploit system security weaknesses. So, clients using regular text make it straightforward for a secret word cracker to access a framework and to obtain important information on the client [3]. A strong password, with different combinations of words, numerals, and special symbols, can be used to avoid or at least reduce this kind of attack. - d) Trojans
Some hackers use Trojans to obtain a client’s personal information from banking servers and database frameworks. Through Trojans, the e-banking platform screen data, texts, data exchanges, etc. can be trapped and used for malicious transactions, leading ultimately to banking frauds [3]. - e) Server Bugs
Server bugs are basically a virus attack on the e-banking website server. These can be found and easily fixed, based on the architecture of the security system designed to restrict the hacker. The banking framework directors must be capable of detecting and removing server bugs within the least amount of time [3]. - f) Password Cracking
Hackers use these kinds of attack to obtain the password for the e-banking login. Some of the hash table and password decryption techniques are used, such as brute force secret key assaults. Hash tables use procedures to un-scramble passcodes to disclose the whole of the client’s personal login data [3]. Using this approach, the hackers use techniques to obtain the user ID and passcode for a particular e-banking website. - g) Keystroke catching/logging
Keystroke logging is used by fraudsters to obtain passwords. The risk of being subjected to keystroke logging is more noteworthy on PCs shared by various individuals.
4.1.4 Current Security Systems for E-banking
Security log audits have been used to avoid various attacks. These are also used to detect the possible attackers, so as to protect the system, control data traffic, and pursue legal modalities [3]. The security system checks the sharing of data from individuals by applying security checks and audits to avoid fraudulent, logging in, or and making financial transactions etc. [3].
The security ID in present e-banking services is of utmost importance nowadays. Each client or customer is provided with a secret user ID (“user ID”) and secret key or password (involving a complex combination of small and capital letters, numerals, and special symbols, up to 20 characters long) with which to access e-banking services for various kinds of activity. Various options are given to secure accounts with high levels of security, with provisions such as biometrics, one-time passwords (OTP), or email authentication. Customers can use security check procedures, such as security questions, pass code, or even requests for special permissions for sizeable transactions. The following list describes some of the highly secured options available to e-banking customers.
- OTP (One-time password): The client can enrol for a high-security method by associating their mobile (cell) phone number and/or email address, or any other messaging method to the account. The client obtains a security code in the form of an OTP on the respective messaging facility and uses that code for the transaction. If the account is falsely accessed by a would-be hacker, that person will not be able to carry out any financial transaction from the account without the OTP, thus securing the account against malicious attack.
- QRP (Quick-response protocol): This is basically a verification framework. This framework allows the financial transaction only if it receives a secret key obtained on the mobile phone, which is camera enabled. The transaction will only be possible with the confirmation token or key received on the mobile phone.
- Security Question: Each client account can be enabled with a security question for both transaction as well as for recovery of the account, in situations where the user has forgotten the password. For each transaction, the user needs to answer a security question; after a maximum of two failed attempts, the account becomes temporarily suspended, avoiding any malicious attack.
- SMS Keeping Money: Push-and-draw SMS facility can also be enabled on the client’s account, using the mobile phone number. This is known as mobile banking. “Push” messages are sent to the client’s mobile number regarding any transaction by the client who merely enrols for this security feature on mobile banking by paying a small charge per quarter. “Draw” messages are used by customers to know the status of the account, such as balances, by sending SMS to a specific helpline number, as requested by the customer, from time to time.
4.2 Data Mining
Data mining (DM) has been used to extract usable information from various datasets [1, 3]. Important aspects of data mining include data preprocessing, using cleaning and missing-value treatment of data, integration of data, transformation of data, pattern evaluation and representation of data in usable form, etc. [2]. This is basically one of the tasks in the knowledge discovery process of databases as shown in Figure 4.1.

Using clustering algorithms, similar records are generally combined together to simplify the large database maintaining multi-dimensional records. The purpose of the present work is to find out where the security problem arises and how it can be avoided [1].
4.2.1 Data Mining Techniques [2 –5]
- Association: This process is used to detect co-occurring sets of attributes and basic rules, managing the relationships between data and attributes. Association occurs by creating relationships between different attributes in a large customer database.
- Clustering: Similar records are generally combined to simplify the large database, having multi-dimensional records. These are then used to create data segments that exhibit similarity within a group of points.
- Classification: Classification, which is a conventional DM strategy, is based on system information. In this case, attributes are classified into different categories.
- Sequential patterns: Sequential patterns are used to find the statistically significant patterns, where values can take on a particular order. These patterns are also related with the association rule.
- Regression: Regression is used to identify a relationship among different variables. Generally, this approach is based upon segmentation.
- Segmentation: Segmentation is the process of taking the data and dividing it up and grouping similar data together based on the chosen parameters so that it can be used more efficiently within marketing and operations. The customer bases that respond in a similar strategy are grouped together. Data segmentation gives companies the ability to identify high-opportunity groups within their customer database and can help better communication to targeted groups.
- Prediction: These techniques are applied for predictions, based on some sort of data or application. Regression analysis can be done for developing relationships between various variables.
4.2.2 Data Mining Applications
- Banking/Financing: Data mining has been used to maintain the banking and financial transaction of the client. The transactions include purchasing data, surfing data, selling data, money-exchange data, etc. [3].
- Advertise Basket Analysis: Data mining has also been used to record the details of the customer’s purchasing information at the retailer’s end. This analysis has been used by the retailers to obtain information about the customer’s loyalty and to understand the specific purchasing patterns of the customer [4].
- Producing Engineering Learning: Data mining has also been helpful for engineering learning, to understand the connections between inventory, price, and customers, that have shown interest in a particular product [4, 5].
- Customer Relationship Management (CRM): CRM is a procedure to develop a more efficient relationship and to understand the customer’s behavior by gathering data and further examining the collected data. Data mining principles, such as information mining, can be used to extract the precise collection of the required information, and used for further examination, so as to improve the response of businesses [6].
- Client Segmentation: This is a method to classify clients, based on particular priorities, such as buying patterns, product class, typical amount spent, and method of payment. The priorities of the clients can be used to classify them and, accordingly, to target them for improving the businesses. Data mining principles has been used to find some ways to avoid clients moving to other businesses, and to impress the customers to continue offering their business by offering attractive loyalty schemes, in the form of customized offers [7].
- Monetary Banking: Data mining and information mining principles can be used for managing an account to record and classify specific information on the customers [7]
- Criminal Investigation: Data mining applications can also be used in criminology to identify wrongdoing behaviour of suspects and criminals. Data mining strategies can be applied to such arrangements, by making use of precise information in large datasets datasets, developing intricate patterns of behaviour.
4.3 Related Work
Jayasree and Balan (2013) [1] described a comprehensive study on various data-mining techniques in the banking sector. The authors provided information about knowledge discovery in database processes and suggested that data mining applications and principles could be used for various applications in the banking sector. Jain and Srivastav (2013) [2] studied classification and prediction techniques for implementation in data mining algorithms, and explained the use of data mining techniques to obtain the information by descriptive partitioning of the data and by utilizing stored data, in order to build predictive models.
Ramageri (2014) [3] compared different data-mining techniques to identify their strengths and weaknesses with respect to growth in various business types. The author used various data mining techniques and algorithms to find the patterns to decide future business trends. Pakojwar and Uke (2014) [4] developed an algorithm for assessing security in online banking services, using data mining, and concluded that the banks should execute some new methods with which to verify the client’s identity and to securely provide a safe e-banking platform.
Amutha (2016) [5] proposed a method to examine the information gathered from some source, with the assistance of different statistical measures like straightforward rate examination, midpoints, F-statistic, and the chi-squared test. The author suggested that statistical techniques could be used to securely improve the customer transaction analysis. Rajput (2015) [6] investigated customer’s views about their experience on e-banking services, using a questionnaires with closed-ended questions and Likert types of inquiries for data collection.
Rani (2012) [7] presented a method to study perception towards e-banking in Ferozepur district of Punjab State, India, on the basis of data collected using a questionnaire. By considering the customers’ opinions, it was concluded that 60% of people showed positive responses. Omariba et al. (2012) [8] presented a study on e-banking privacy and security, and examined e-banking security, and issues of protection and assaults on e-banking accounts.
Stojanovic and Krstic (2017) [9] explained the challenges and methodologies of e-banking risk management. The authors explained the ‘electronic money management’ method for innovatively managing the account by utilizing the principles of data innovation. The authors developed a method to determine the risks associated with e-banking. Ali et al. (2016) [10] discussed various cyber threats in e-banking services. The authors discussed various effects on customers’ behavior toward e-banking, and investigated the impacts of digital dangers in e-banking web management. The authors explained how different cyber threat effects on e-banking increase awareness among the customers, and advocated the need to increase awareness among the customers when using online banking.
Shanab et al. (2015) [11] discussed various frauds and security infractions associated with e-banking. The authors explained the use of biometric data, image verification, and fingerprints for securing a bank account, and proposed that the customer must be informed and made aware of safe e-banking behavior, emphasizing money transfer risks. Devadiga et al. (2017) [12] proposed a steganography- and cryptography-based e-banking security system. The proposed method was based on storing the encrypted details in an image used to carry out the transaction. Thereafter, data mining techniques have been used to note any deviations in customers’ transaction pattern or behavior.
Nwogu (2014) [13] proposed an improved e-banking security system, based on three-level security. Biometric identification-based protocols were used by the author for secure banking, who used advanced encryption standards, along with biometric identification, and concluded that biometric identification was more secure than other security tools, providing access to a more secure e-banking server rather than to customers’ computers. Reddy and Reddy (2015) [14] discussed the effects of the customers’ perception and satisfaction toward e-banking systems. The authors said that the use of information and communication technology (ICT) has led to improvements in the e-banking systems, and proposed that the purchaser discernment between the comfort and ease-of-use of different e-saving money administrations be measured. Consumer loyalty level toward e-banking had been distinguished.
Roozbahani et al. (2015) [15] explained the effect of the use of e-payment tools on e-banking on customer satisfaction. They reviewed various methods and concluded that the e-payment methods could be used to help operation of e-instalment devices and thus to improve consumer loyalty. The authors analyzed the survey data in two ways, namely (1) SPSS programming and (2) the Pearson’s correlation test. Fozia (2013) [16] developed a system for secure e-management of a client’s accounts, with this system using the client’s transaction data and e-banking platform operational data to assess the risk of security infringement of the system in private e-banking operations. Fozia (2013) concluded that the secure e-management would help to identify the client’s requirements and to ensure greater security of their account.
Jham (2016) [17] discussed the fact that banks have tried to satisfy their customers by providing the best e-services, with this paper concentrating on the utilization of internet-based savings and transactions by the bank’s existing customers. The impact of the customer’s acknowledgement of internet management of account administration has also been studied. Kshirsagar and Dole (2014) [18] presented a comparison of various data mining methods to identify crime detection, involving the detection of both transactional and application domains. Such detection is important, not only for governmental bodies, but also for business organizations all over the world.
4.4 Methodology
A questionnaire using a Likert scale was used to gather information on e-banking from the respondents. Basically, the Likert scale was used to measure opinions. On this scale, respondents were asked to rate their opinions on an Excel sheet. After collecting the information, the data collected were analyzed, using SPSS software.
4.4.1 Algorithm
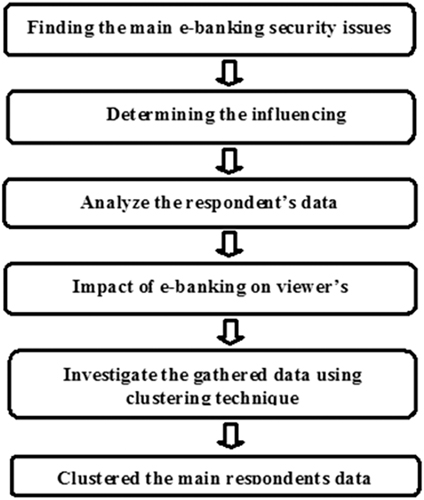
- Identify the main e-banking security issues: The main factors by which e-banking security problems arise, and how, are reported.
- Identify the influencing factors: The major client factors determining satisfaction with e-banking security are the age, gender, and the location (urban/rural) of the client. Data on these factors were gathered from the various respondents
- Analyze the respondents’ data: The impact of the influencing factors was analyzed, with regard to the satisfaction of the respondents with e-banking.
- Determine the impact of e-banking platforms on respondents’ satisfaction: The impact of e-banking was statistically analyzed with respect to clients’ satisfaction. Significant and highly significant values were denoted as “*” and “**”, respectively.
- Investigate the collected data, using clustering: The main influencing factors were grouped using the clustering technique. The respondent’s data is further clustered for analysis and draw meaningful inferences.
The flowchart of the work is shown in Figure 4.2.
4.4.2 Questionnaire Data Set
NAME
ROLE:
CUSTOMERS □ E-CUSTOMERS □
AGE:
18–30 □ 30–60 □ >60□
GENDER:
MALE □ FEMALE □
AREA:
RURAL □ URBAN □
TYPE:
CUSTOMERS □ E-CUSTOMERS □
The subsequent statements relate to your attitude toward e-banking. Please point out your response to each question, on the Likert scale, of Strongly Agree (SA), Agree (A), Neutral (N), Disagree (D), and Strongly Disagree (SD) [5] as described in Table 4.1.
TABLE 4.1
Likert Scale in Questionnaire

4.4.3 Implementation Using SPSS Software
After collecting the information from the questionnaires, the data collected were analyzed using the t-test, using the SPSS software tool. SPSS has been used to operate spreadsheets from MS Excel or plain text files, and relational Structure Query Language (SQL) databases as well. Figure 4.3 shows the data, relating to answers to the 20 questions (v1 to v20) on the questionnaire, from 100 customers. The columns refer to customers’ data and the rows refer to the individual customers.

Data analysis view opens the data from all the questionnaires and displays the complete data in two sheets. Figure 4.4 shows menu options: Select Analyse > compare means> independent sample t-test. These options open the mean values along with statistical comparison, using the t-test.

The independent t-test has been used to analyze the data, and Figure 4.5 shows how the variables are grouped together. After grouping, each of the variables is tested to determine statistical comparisons of all the values between customers and e-customers.

Figure 4.6 shows a group-statistics table and a viewer window. The system contains the menu and toolbars. The window is divided into two parts: a structured outline tree on the left and the output elements shown on the right side, i.e., a structured table of contents.
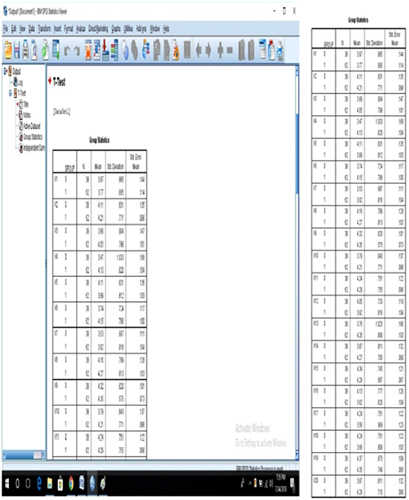
Figure 4.7 shows the output of the independent t-tests. Using the t-tests, the independent-sample means of the same continuous, dependent variable between two mutually exclusive groups (customers and e-customers) are compared.

SPSS provides some procedures for marketing applications, such as analysis, segmentation, and testing. It helps to improve interpretation of the results from the independent t-tests. Figure 4.8 shows the direct marketing option.

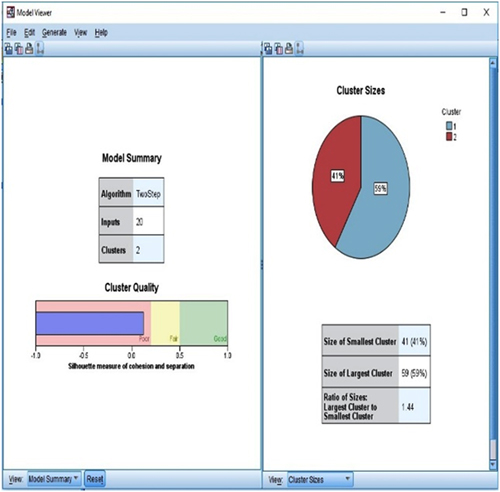
After carrying out the analyses, there is then a need to carry out clustering on the basis of ten inputs, as shown in Figure 4.9.

Figure 4.10 shows the data inputted given to the designated system. The interface also provides information regarding the clustering of similar data.
4.5 Results and Discussions
The primary aim of the present work is to obtain meaningful information from the data collected, using a well-design questionnaire related to security in e-banking. Table 4.2 shows the responses of customers and e-customers, along with the t-test values.
TABLE 4.2
Perception of Respondents (1=Strongly Agree, 5=Strongly Disagree)

Firstly, the data collected through the questionnaires were examined and ambiguities removed, using pre-processing of the data. The collected data are basically the customer’s perception. Table 4.3 shows the ten factors found to be significant with reference to e-banking security, using the statistical independent t-test. Table 4.3 explains that the responses to questions, such as “Avoid trusting e-services to manage money”, “Unexpected system failure and framework”, “Security providers (cyber security, information storage, assurance of data safeguards, without any fraud)”, “Not being able to maintain security”, were found to be highly significant between customers and e-customers, as indicated by “**” in t-values.
TABLE 4.3
Significant Factors (1=Strongly Agree, 5=Strongly Disagree)

The results for all these parameters reflected the awareness of respondents to the security issues in e-banking. They still did not have trust in the e-banking system and were afraid to use internet banking in case they lost their money. Responses to other questions, such as “Threats from hackers through encryption of login”, “E-banking not being able to maintain security”, “E-banking security always updated to protect any theft or fraudulent activity”, “Timeliness of data through internet helps to save the account from any malicious attack. Bank quickly resolves problems customer encounters with own online transactions”, “Increased comfort and time saving” were found to be significantly different between customers and e-customers, as indicated by “*” in their t-values. All these parameters reflect security issues.
4.6 Conclusions
Data mining methods have been used to assess e-banking security concerns. Data from customers and e-customers were collected using a questionnaire and analyzed to identify customers’ perception of security issues in e-banking. The dataset was obtained by collecting completed questionnaires filled in by 100 respondents. Clustering technique was used to find out the significant and highly significant values between customers and e-customers, using the statistical t-test. The system was analyzed using SPSS software. In this work, the customers’ perception of the e-banking security has been analyzed. Ultimately, the responses were studied and important influencing factors have been identified statistically. From the results, it has been found that e-customers are most worried about the security issues in e-banking mainly cyber security issues, information protection, fraudsters draining the login data and delayed response of the bank in case of malicious online activities.
4.7 Future Scope
- Data from 100 respondents was collected in the present study. In future, data from web portals and other data sources can be collected to draw more meaningful conclusions from larger and more representative samples.
- Three respondent factors (age, gender, and location) were considered during the present study. In future studies, more factors should be taken into account to provide more detailed and generally applicable results.
- Using the present work, the user is only able to either like or dislike the particular facility provided by the e-banking system based on three respondent factors. In future “any suggestions” can also be applied, based on a larger number of factors.
- Further data mining software should be used, such as Rapid Miner, Orange, or KEEL.
Bibliography
- 1. V. Jayasree, V. S. Balan, “A review on data mining in banking sector”, American Journal of Applied Sciences, 10(10), pp. 1160–1165, 2013.
- 2. N. Jain, V. Srivastava, “Data mining techniques: A survey paper”, International Journal of Research in Engineering and Technology, 2(11), pp. 116–119, 2013.
- 3. B. M. Ramageri, “Data mining techniques and applications”, Indian Journal of Computer Science and Engineering, 1(4), pp. 301–305, 2014.
- 4. S. Pakojwar, N. J. Uke, “Security in online banking services-A comparative study”, International Journal of Innovative Research in Science, Engineering and Technology, 3(10), pp. 16850–16857, 2014.
- 5. D. Amutha, “A study of consumer awareness towards E-Banking”, International Journal of Economics and Management Sciences, 5(4), pp. 350–353, 2016.
- 6. U. S. Rajput, “Customer perception on e-banking service”, Pacific Business Review International, 8(4), pp. 85–94, 2015.
- 7. M. Rani, “A study on the customer perception towards e-banking in Ferozepur district”, International Journal of Multidisciplinary Research, 2(1), pp. 108–118, 2012.
- 8. Z. B. Omariba, N. B. Masese, G. Wanyembi, “Security and privacy of electronic banking”, International Journal of Computer Science Issues, 9(4), pp. 432–446, 2012.
- 9. D. Stojanovic, M. Krstic, “Modern approaches and challenges of risk management in electronic banking”, International Scientific Conference Science and Higher Education in Function of Sustainable Development, 2(7), pp. 41–48, 2017.
- 10. L. Ali, F. Ali, P. Surendran, B. Thomas, “The effects of cyber threat on customer’s behavior in e-banking services”, International Journal of E-Education, E-Management and E-Learning, 7(1), pp. 70–78, 2016.
- 11. E. A. Shanab, S. Matalqa, “Security and fraud issues of E-Banking”, International Journal of Computer Networks and Applications, 2(4), pp. 179–187, 2015.
- 12. N. Devadiga, H. Kothari, H. Jain, S. Sankhe, “E-banking security using cryptography, steganography and data mining”, International Journal of Computer and Applications, 164(9), pp. 26–30, 2017.
- 13. E. R. Nwogu, “Improving the security of the internet banking system using three-level security implementation”, International Journal of Computer Science and Information Technology & Security, 4(6), pp. 167–176, 2014.
- 14. D. N. V. K. Reddy, M. S. Reddy, “A study on customer’s perception and satisfaction towards electronic banking in Khammam district”, IOSR Journal of Business and Management, 17(12), pp. 20–27, 2015.
- 15. F. S. Roozbahani, S. N. Hojjati, R. Azad, “The role of e-payment tools and e-banking in customer satisfaction”, International Journal of Advanced Networking and Applications, 7(2), pp. 2640–2649, 2015.
- 16. M. Fozia, “A comparative study of customer perception towards e-banking services provided by selected private & public sector bank in India”, International Journal of Scientific and Research Publication, 3(9), pp. 283–292, 2013.
- 17. V. Jham, “Customer satisfaction with internet banking: Exploring the mediating role of trust”, Journal of Emerging Trends in Economics and Management Sciences, 7(2), pp. 75–87, 2016.
- 18. A. Kshirsagar, L. Dole, “A review on data mining methods for identity crime detection”, International Journal of Electrical, Economics and Computer Systems, 2(1), pp. 51–55, 2014.
