6 A Review of the Internet of Things (IoT)
Rohit Kumar, Gaurav Bathla, and Hramanjot Kaur
Contents
6.3.1 Layer-Specific Architectures
6.3.1.6 Fog and Cloud-based Architecture Layers
6.3.2 Domain-Specific Architectures
6.3.2.1 CloudThings Architecture
6.3.2.2 Industrial IoT Architecture
6.3.2.3 Smart and Connected Communities (SCC) IoT Architecture
6.3.2.43 G-PLC (Power Line Communication) Architecture
6.3.2.5 Software-Defined Network (SDN)-Based Architectures
6.3.2.6 MobilityFirst Architecture
6.3.3 Industry-Defined Architectures
6.3.3.4 Microsoft Architecture
6.3.4 Association of Industry-Defined Architectures
6.1 Introduction
The Internet of Things (IoT) has attracted much interest recently and this technology has grown and developed in leaps and bounds. IoT has penetrated deep into human life and has been immensely beneficial, with applications ranging from automobile automation to health care. The phrase “IoT” was first created by authors in 1999 [1], when Kevin Ashton was working on an intelligent network consisting of sensor devices, wireless devices, actuators, robotic arms, etc. In the modern era the term IoT can be defined with the equation:
|
|
According to the report and statement published by International Telecommunication Union (ITU) in 2005 [3], IoT will be a major driving force and will facilitate the construction of smart and intelligent sensory networks, connecting the globe. IoT has also been a key driving force with respect to supportive technology for pervasive (ubiquitous) computing, and the impact of IoT can be seen in mobile devices, smart watches, digital cameras, tablets, etc. [4]. The penetration of IoT has led to an immense increase in data traffic across the IoT networks, which will increase manifold in the near future; according to Cisco data, the traffic on IoT-based networks in 2019 was 70% higher than in 2014, when the growth of traffic was only 40% in the year 2009 [5]. Similarly, it is forecast that the number of connections from one device to another will increase at the rate of 43% from 2014 onwards [6]. This increase can be credited to the fact that IoT has been involved in a large number of scenarios and devices, e.g., radio-frequency identification (RFID) tags, wireless sensors, actuators, Bluetooth-enabled devices, intelligent driving systems and cars, smart homes, and many more technologies. Looking at the bright future of IoT, companies like Intel, IBM, Cisco, etc., have developed their specific reference-based architecture for IoT. Due to specific applications and vendors’ motives, a single standard reference model for IoT has not been finalized [8]. In this chapter, IoT core concepts and different architectures will be presented and discussed. In Section 6.1, the core elements of the IoT network are presented in tabular form; following on from a description of IoT basics in Section 6.2, in Section 6.3, IoT-specific features are presented and, in Section 6.4, consideration of various architectures is summarized. Section 6.5 presents a comparative analysis of the different architectures, and Section 6.6 describes the main conclusions of IoT development.
6.2 Basic Elements of IoT
To understand the most important aspects of IoT, the reader should have a good understanding of the foundation blocks of this emerging technology. Implementation of IoT requires an understanding of various simple fundamentals, as depicted in Table 6.1. These include sensors, things or devices, actuators, networks, gateways, cloud infrastructure, and RFID tags [9].
TABLE 6.1
Fundamental Elements of IoT
Elements of IoT |
Description |
Sensors |
Sensors are the primary means of data collection and monitoring from the given environment |
Actuators |
Actuators perform actions and help in performing operations and data collection without human involvement. |
Gateways |
They act as a bridge across different IoT components and ensure smooth information flow. |
Network infrastructure (NI) |
IoT is essentially a computational communication network and encompasses all major components of conventional computer networks, like routers, gateways etc. |
Cloud infrastructure (CI) |
IoT can be easily integrated with Cloud-based networks for better storage capability and computational capabilities. |
RFID |
Radio-frequency identifiers (RFID) and other bar-code-like technologies, which can help in object detection with ease. |
6.3 Architecture
This section showcases the various architectures introduced by researchers for the IoT. Many architectures exist in the literature, that have been proposed in the past by various researchers during the rise of IoT technology. These architectures can be classified as :
- Layer-specific architectures.
- Domain-specific architectures.
- Industry-defined architectures.
Further classification of the aforesaid architectures is presented in Fig. 6.1.

6.3.1 Layer-Specific Architectures
Categorization of IoT on the basis of layers is shown in Fig. 6.2.

6.3.1.13 -Layer Architecture
This is the elementary design for the Internet of Things. According to [10], it includes three layers, which are explained as:
- i. Perception Layer, also known as the sensor layer or the recognition layer [11], is the bottom layer of IoT architecture. This layer interconnects the real objects and devices via basic elements of IoT (explained in Table 6.1). The main functionalities of the perception layer are:
- To connect real objects with an IoT-based system.
- To calculate, assemble, and handle the state-of-the-art information associated with the objects via smart gadgets.
- To pass the data, after processing, on to the upper layer by the use of layer interfaces.
- ii. Network Layer is the central layer of IoT architecture, and is also known as the transmission layer or gateway layer [12]. The network layer is the primarily focused layer in IoT architecture, as it basically builds the assimilation of various devices (gateway, hub, switches, or cloud infrastructure, etc.), as well as various data transmission technologies (like Bluetooth, long-term evolution (LTE), WiMax, etc.).The objectives of the network layer are:
- To obtain the processed information that is handed over by the perception layer.
- To regulate the routes for transferring this information to different IoT devices through interconnected networks (e.g., WiFi, Router, Access point, Bluetooth etc.).
- iii. Application Layer is the uppermost layer in the IoT architecture [13]. It is also known as the business layer and performs the following major functions:
- To receive the information transmitted from the network layer.
- To use these data for distribution among the required services [10].
Regardless of the benefits, like straightforwardness, effortless problem identification, flexibility, and management functionalities, the absence of security in this layer is a crucial drawback [14]. The network layer and application layer perform complex functions, For instance, alongside finding the routes and sending the information, the network layer should also offer other data services such as data fusion and computation, etc. In addition to providing customer services, this layer must also provide information services, like information analytics and mining etc. [13, 15].
6.3.1.24 -Layer Architecture
The author of [16] defines a layer as performing a task intermediate between the network and application layers. This service layer is held accountable for delivering services in the Internet of Things. Based on this concept, the IoT researchers have introduced a Service-oriented Architecture (SoA) [13, 15]. The main functions provided by four-layer architecture are:
- The IoT based on SOA conceals the needless details from the product builder and controls the decrease in product building time.
- It helps to organize workflow in an easy way.
It builds a method for advertising the saleable products more easily and allows it to be completed in a very short time (Fig. 6.3).

6.3.1.35 -Layer Architecture
A five-layer IoT architecture was proposed by the authors in [18] and is depicted in Fig. 6.2. The main objectives of all the layers under this model are discussed below:
- i. Perception layer is mainly associated with physical objects. This layer observes and collects the data about physical objects (e.g., humidity and temperature of the environment, location and motion of the objects, etc.) and further transmits information to the next upper layer.
- ii. Transmission layer is used to achieve the security objective and assists in reliable transmission of information to the next upper layer.
- iii. Middleware layer is concerned with information storage but it also processes the data and takes appropriate actions, based on the results.
- iv. Application layer achieves the functionality of application management, such as smart grids, smart healthcare, smart home, smart farming, etc.
- v. Business layer, the uppermost layer, supports data analytics, on the basis of which it plans further actions [19].
In [8], the five-layer architecture is described, in which the five layers are:
- i. Perception layer, which is the bottommost layer, and it perceives the data.
- ii. Transport layer has the same functions as the network layer in the three-layer model, i.e. it transmits the perceived information from perception layer (or from devices) to the application layer.
- iii. Processing layer stores, analyzes, and processes the data to identify some definite pattern which can be exploited for use by the business layer, which manages the entire IoT.
- iv. Application layer manages the applications.
- v. Business layer carries out the data analysis.
6.3.1.46 -Layer Architecture
A six-layer architecture was introduced in [20], based on the earlier-defined 4-layer model, but possessing two new layers. These are:
- i. Media access control (MAC) layer, which assists in observing and controlling gadgets. It also helps in saving the energy of the devices by allowing them to sleep in their idle time.
- ii. Processing and storage layer, which assists by carrying out the queries, analyzing and storing the information and providing security features[19].
A six-layered architecture for IoT was proposed by the authors in [21] is shown in Fig. 6.2, Roles of each layer are described as follows:
- i. Focus layer is mainly focused on the recognition of devices, and it takes account of the multiple facets of the system under observation.
- ii. Cognizance layer determines the sensing competence (for this purpose, sensors or actuators are deployed) and it gathers data from the physical objects that are observed in the previous layer.
- iii. Transmission layer allows the sending of perceived information received from the cognizance layer to the subsequent layer.
- iv. Application layer achieves the collection and classification of the data according to the requirement of the desired zone.
- v. Infrastructure layer assists with the features which are linked with service-oriented architecture, such as cloud and cognitive computing, geographic information system (GIS) mapping, big data, and data storage functionality.
- vi. Competence business layer works to scrutinize the commercial networks of the Internet of Things systems. It also provides privacy and this layer is also concerned with the business models, as well as profit models, in an efficient manner.
6.3.1.57 -Layer Architecture
By considering the physical objects or devices in the surrounding environment, researchers projected a seven-layer architecture [22] as shown in Fig. 6.2. This enhanced architecture has some special features. The users can consider different aspects that influence the sensing potential of actuators and sensors, etc. Various roles and functionalities of these layers are described [21]:
- i. Application layer gathers the data about a specific task, based on the client’s requirements.
- ii. Application support and management layer is accountable for handling the IoT gadgets along with their operation, as well as operating the security.
- iii. Services layer focuses on providing the various necessary services to the consumers, focusing on activities provided on the development side.
- iv. Communication layer is used to provide an interface for communicating the information from the sensing layer to the services layer.
- v. Network layer assists the gadgets by processing and then sending the information through the internet.
- vi. Hardware layer is used for assimilation of various hardware objects required for deployment on the IoT platform.
- vii. Environment layer determines the possibility of detecting physical objects (such as moving vehicles, humans, etc.) or other aspects of the environment, e.g., humidity or temperature, of a place etc.
6.3.1.6 Fog and Cloud-based Architecture Layers
In [8], the authors presented a Fog architecture based on [23], which is composed of six layers as shown in Fig. 6.2. In Fog architecture, four layers, namely observing, pre-processing, storing, and security layers, were inserted between the physical layer and the transport layer, before the information is passed to the cloud. As mentioned in [21], the functionalities of these layers can be described as:
- i. Physical layer is focused on the examination of objects.
- ii. Monitoring layer is responsible for observing the factors, like services and assets, by the consumers, and varied reactions.
- iii. Pre-processing layer is responsible for various operations like managing, filtering, and analyzing the information.
- iv. Storage layer is accountable for storage and distribution of the gathered information, whenever required.
- v. Security layer works on the fundamental security aspects of the information, by preventing it from unauthorized access.
- vi. Transport layer is the uppermost layer of the fog architecture that allows transmission of data.
Cloud-based architecture is the one which provides the feature of centralized access over the information, using a cloud-based information-handling system, which allows the IoT system to possess a cloud-centric architecture. It is gaining popularity day-by-day in IoT systems because of its intelligent type of sensing of the information and of producing results in the form of information from IoT gadgets. In cloud-based architecture, the cloud is situated between the application and the network layers [21].
6.3.2 Domain-Specific Architectures
6.3.2.1 CloudThings Architecture
In [24], an IoT-based scenario is described which uses the smart home. In this concern, a new architecture, named CloudThings, was presented as a cloud-centric IoT platform. The CloudThings architecture makes use of the following services:
- PaaS: Platform as a Service
- IaaS: Infrastructure as a Service
- SaaS: Software as a Service
Collaboration between the IoT and the cloud denotes a realistic way through which one can easily smoothen the development of an application. Yet, there is a need for dealing with the heterogeneous nature of the IoT physical (or dynamic) things [14].
6.3.2.2 Industrial IoT Architecture
The associated architecture is depicted in Fig. 6.4, which is meant for green Industrial IoT. Its components are:

- i. Sense entities domain: To increase the energy savings, nodes and smart devices are organized in the sense entities field and they are categorized as:
- Control nodes (CNs).
- Sense nodes (SNs).
- Gateway nodes (GNs).
- ii. Constrained RESTful Network: RESTful web services are hosted by the network, with the sense entities becoming connected with the Cloud Server.
- iii. Cloud Server: This provides the Virtual Environment for the objects which are further transmitted to the applications server. It also processes and computes the extracted information.
- iv. User applications: Through the application server interfaces, clients can interact with the application server, even though they do not have access to the server side codes. The administration node can grant direct access to the clients [25].
6.3.2.3 Smart and Connected Communities (SCC) IoT Architecture
In [27], the authors proposed an IoT-based SCC (Smart and Connected Communities) architecture. This IoT architecture consists of four different layers, and is specifically designed for smart cities as illustrated in Fig. 6.5.

- i. Responding layer (or sensing layer) is the outermost layer of SCC IoT architecture. It is the perceiving layer, with which smart gadgets communicate with the IoT system. It performs the functions of perceiving and transmitting the information further to the interconnecting layers.
- ii. Interconnecting layer performs functions similar to those the human nervous system carry out in the human body. It is the connecting layer and its main purpose is data exchange and transfer between different gadgets and diverse domains.
- iii. Data layer is considered to be the brain of the smart cities, responding to requests from services of the service layer, such as smart lighting system in bad weather, With the assistance of the knowledge base and real-time analysis of data, the intelligent decision system automatically takes the required decisions and carries out the actions. It is used to back-up large amounts of mixed and insignificant information, and representing it in a significant manner, for knowledge management, decision-making processes, etc..
- iv. Service layer, also known as the application layer, provides a variety of essential services for small cities. This layer offers the interface between the IoT system and consumers. The services depend on the service supporting system.
6.3.2.43 G-PLC (Power Line Communication) Architecture
In [28], 3G-PLC-based IoT architecture is proposed, which collaborates with complex communication systems, namely:
- i. 3G network
- ii. Power Line Communication (PLC) network.
Increasing the number of nodes is the primary objective for using the 3G-PLS network. To accomplish this, IoT framework layers are integrated with the purpose of discovering a new 3G-PLC IoT-based architecture.
Benefits: The advantages of this proposed architecture are:
- Improved services as related to backhaul network opponents.
- Lower cost of network structure.
Limitation: However, this architecture has a major limitation, lacking the incorporation of network heterogeneity [14].
6.3.2.5 Software-Defined Network (SDN)-Based Architectures
In [29], the author designed a SDN-based IoT architecture. The motive behind implementation of this architecture was to enable various IoT tasks in a heterogeneous wireless network environment with high-level Quality-of-Service (QoS).
Benefits: This proposed architecture presents various benefits such as:
- Flexibility.
- Effectiveness in terms of data flow.
- Efficient resource management.
Many existing studies have also revealed that wireless SDN-based architecture can assist in achieving the objectives of IoT in terms of improved scalability, quality of service, context-aware semantic information retrieval, and simple, fast placement of resources.
Limitation: This architecture lacks the organization of the layer created by the controller as it is hard to supervise heterogeneous IoT networks.
6.3.2.6 MobilityFirst Architecture
In [30], a name-specific Future Internet Architecture (FIA), known as MobilityFirst, was introduced by the authors to assist in resolving many problems concerned with cellular (mobile) phones, when these phones were acting as gateways to the Wireless Sensor Networks (WSN) in IoT. The ability of the network is measured and matched to the sensor information speed at a given location.
Benefits:
- Ad hoc services
- High security
Limitation: The absence of motivation processes for mobile providers to use the system is a prime limitation [14].
6.3.3 Industry-Defined Architectures
6.3.3.1 Cisco Architecture
It follows an Edge model. Fig. 6.6 illustrates the IoT reference architecture and its different levels. The data flow follows a bidirectional approach in IoT:

- In a control pattern, control information flows from the top to the bottom.
- In a monitoring pattern, the control information flows from the bottom to the top.
The processing layer in a 5-layer model is composed of three layers, where data fusion, like gathering information from all the devices, is handled by the data abstraction layer, storage is performed by the data communication layer, and real processing is achieved by the edge computing layer. Level 3 activities aim to carry out large-scale information analysis and transformation. For instance, a sensor device generates the data samples throughout the year at Level 1 a number of times throughout the day. Despite generating this large amount of information, the collected information was never analyzed. Just because of the slow processing of the majority of IoT solutions, analyzing the data will be difficult. Architecture which uses the cloud to carry out analysis will face different problems in the future, because of excessive data.
The approach followed by Cisco is called edge computing. It will solve the issue, by calculating in real time [8, 31, 32], such as, by transmitting the videos from security cameras (as they are worthless) in place of processed video of an event, it will be productive. Another example is in the banking systems, where edge computing is used for detection of fraudulent transactions in ATMs. Cisco promotes its gateways as edge computing devices and it is making trends. Early calculations were also possible with Cisco edge computing; after processing, these analytics are sent to the cloud. Acting on this information, which is near-source, some calculations allow continuous operation, even if the network is not active [8].
6.3.3.2 IBM Architecture
This cloud-computing architecture has been transformed to another model, along with some enhancements, such as device control and management [34]. In that aspect, the layers, in which they are expert with respect to the seven-layer model, is explained here. Much of the IBM architecture for IoT deals with middleware, rather than the whole architecture. Considering the power of IBM’s Watsons IoT [35] with Cisco’s edge computing, as shown in Fig. 6.7, the architecture components are categorized into the following major components:

- Connect: The Connect component ensures secure device connectivity (via Gateway), control of gadgets, and communication with third-party services. It is also responsible for device management, as gadgets with device organization agents can execute device organization actions, which can be triggered by the Watson IoT Platform dashboard or the device organization Application Programming Interface (API)
- Information management: Information management handles the storing, archiving, metadata management, streaming data, and parsing and managing of the structured and unstructured data. By using the Watson IoT Platform Last Event Cache API, the last event that was sent by a device can be retrieved.
- Analytics: This covers a lot of functionality, such as covering social data analytics, machine data analytics, and cultured text analytics for incident data. It is basically intended for applications with millions of records per second, i.e., high-speed applications. Organizations can anticipate more efficiently when there is a greater probability of an event happening by analyzing real-time information from the sensors. In addition, with this high-end data analytics, predictive, cognitive, and real-time data analytics can be carried out.
- Risk management: This module ensures leverage of the correct and secure information from the right sources. It performs the functions like e-information protection, auditing, key management, firmware updates, and managing specific security etc. In other words, this layer manages the integrity of the device [8]. By referring to Watson IoT Platform cloud analytics, directive conditions are specified that are dependent on real-time gadget data and that trigger alarms and elective actions when they occur [8, 35].
6.3.3.3 INTEL Architecture
The INTEL System Architecture Specification (SAS) features two versions [37]:
- Version 1.0: For Connecting the Unconnected. It allows the system builders to securely connect and manage legacy gadgets, using an IoT gateway,
- Version 2.0: For Smart and Connected Things. It specifies how to integrate a variety of smart and connected things, ranging from battery-powered devices to ultra-high-performance devices. It is future- concerned architecture, i.e., it assists seamless cyber physical models.
Fig. 6.8 illustrated a SAS-based layered architecture where:
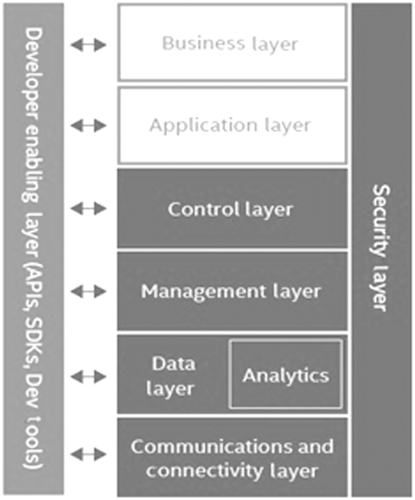
- The used entity is represented by the white block,
- The run time layer is represented by dark blue blocks and
- The developers are represented by light blue blocks.
The main objectives of the eight layers shown in Fig. 6.8 are:
- Control layer, with the help of policy and control APIs, offers the capability to detach the organization and control. It can take the gadgets away off-premises for cloud-based platform/remote control, which is a basic need of an SDN.
- Business layer accesses other layers in the solution through the application layer.
- Security layer provides protection to all the layers [8, 37].
6.3.3.4 Microsoft Architecture
The architecture recommended by Microsoft in [38] for IoT applications is cloud native, micro-service, and serverless based. Microsoft recommended that sub-systems communicate over HTTPS/REST, using JSON (as it is human readable), though binary protocols should be used for high-performance needs. The architecture also supports a hybrid cloud and an edge-compute strategy, i.e. some data processing is expected to happen on-premises. It is recommended to use an orchestrator, such as Azure Managed Kubernetes or Service Fabric, to scale individual subsystems horizontally, or PaaS services, e.g., Azure App Services, that offer built-in horizontal scale capabilities.
6.3.3.4.1 Subsystems of Microsoft Architecture for IoT
An IoT application consists of the following subsystems:
- Devices (and/or on-premises edge gateways) that are able to securely index with the cloud and offer connectivity options for transmitting and reception of information with the cloud.
- Cloud Gateway (IoT hub) is a service to safely receive the information and to offer gadget management options.
- Stream Processors that consume the data, assimilate with business processes, and save the data into storage.
- User Interface to envision telemetry data and enable gadget management.
- Data Transformation permits reforming, retransforming, and recombination of telemetry data sent from devices.
- Machine Learning offers various algorithms, which are executed, based on a dataset of previous telemetry data, so that predictive maintenance scenarios are enabled.
- User Management involves part of management which allows different roles and responsibilities among various users by dividing different functionality among them (Fig. 6.9).

6.3.3.5 Google Architecture
Google reference architecture for IoT, introduced by the Google Cloud platform, is shown in Fig. 6.10.

6.3.3.5.1 Basic Components of Google Architecture for IoT
The system is divided into the following three components:
- Device/Gadget includes firmware that can directly interact with the world and create a link to a network for interaction among themselves.
- Gateway assists different gadgets to communicate with cloud services.
- Cloud allows data from a device to be uploaded onto the cloud, where data from different devices, as well as other business-transactional data, are also available for combining and further processing [39].
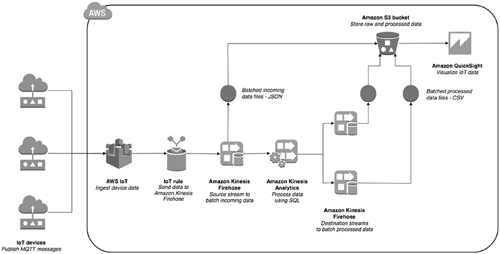
6.3.3.6 AWS IoT Architecture
Amazon Web Services (AWS) reference Architecture for IoT was a controlled cloud platform in Amazon IoT solutions.
Its main features are:
- It helps web-connected gadgets to communicate with cloud applications and other gadgets securely, thus providing a secure device gateway, authentication, and authorization for proven exchanged data.
- Registration for the identification of gadgets.
- Thing Shadows for storage and retrieval of existing state data.
- Rules engine for communication between gadgets and AWS services.
- Amazon has the most comprehensive service among the cloud providers, so that using the AWS IoT inherently provides you with other benefits.
- With the built-in Kibana integration, this platform becomes highly scalable, resulting in IoT applications that gather, handle, analyze, and respond to information generated. In addition, the on-the-spot registration automatically registers new certificates as part of the initial interaction between the device and AWS IoT, speeding up batch deployments.
- AWS IoT enables integration with the rest of the AWS services, like AWS Lambda, Amazon Dynamo DB, Amazon Kinesis, Amazon S3, and Amazon SNS.
- The AWS IoT offers four different interfaces for creating and interacting with things (Fig. 6.11). These are:
- i. Command line interface
- ii. API
- iii. AWS SDKs
- iv. Device SDK [41].
6.3.4 Association of Industry-Defined Architectures
The author of [42] carried out a survey to find the top IoT companies. The author collected the data from different sources like company websites, Twitter, IoT Analytics, Google, and LinkedIn, as described in Table 6.2.
TABLE 6.2
Comparison of Top 5 IoT Companies [42]
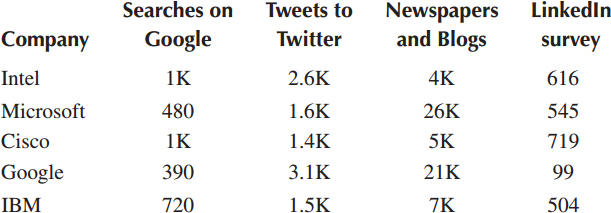
Based on the facts and figures represented in the Table, it is quite obvious that Intel had taken over from Google in 2015 in terms of the number of searches. A survey of the number of employees was conducted of companies that carry “IoT” as their tag, so the growth of the top 5 IoT companies was shown in the form of a bar graph (Fig. 6.12).

6.4 Conclusion
Much technological advance has been carried out in the field of IoT but still we are lagging behind with respect to a standard architecture. There is no standard architecture defined up to now so, to gain the appropriate facts about IoT architectures, this review presents the state-of-the-art of various architectures, classified on the basis of the number of layers, domains, and those of industry-defined structures. This paper also compares the industry-defined architectures. However, we are still lacking information on various domains like noise detection, agriculture, etc., which can be explored further.
Bibliography
- 1. T.D. Nguyen, J.Y. Khan, and D.T. Ngo . 2016. “Energy Harvested Roadside IEEE 802.15.4 Wireless Sensor Networks for IoT Applications.” Ad Hoc Networks. doi:10.1016/j.adhoc.2016.12.003.
- 2. M. Bilal . 2017. “A Review of Internet of Things Architecture, Technologies and Analysis Smartphone-Based Attacks Against 3D printers.” arXiv, arXiv:1708.04560 [Online]. Available: https://arxiv.org/abs/1708.04560. [Accessed September 22, 2018].
- 3. International Telecommunications Union. 2005. ITU Internet Reports 2005: The Internet of Things, Executive Summary, Geneva: ITU.
- 4. I. Ungurean, N. Gaitan, and V.G. Gaitan . 2014. “An IoT Architecture for Things from Industrial Environment.” In: 10th International Conference on Communications (COMM), Bucharest, pp. 1–4.
- 5. “Cisco Visual Networking Index: Forecast and Methodology, 2014–2019.” Cisco, 2015 May 27. http://www.cisco.com/c/en/us/solutions/collateral/service-provider/ip-ngn-ip-next-generation-network/white_paper_c11-481360.pdf.
- 6. K. Rose, S. Eldridge, and L. Chapin, 2015 October. “The Internet OF THINGS: An OVERVIEW- Understanding the Issues and Challenges of a More Connected World.” The Internet Society (ISOC).
- 7. Melanie Swan . 2012. “Sensor Mania! The Internet of Things, Wearable Computing, Objective Metrics, and the Quantified Self 2.0.” Journal of Sensor and Actuator Networks, doi:10.3390/jsan1030217.
- 8. N.M. Masoodhu Banu and C. Sujatha . 2017. “IoT Architecture a Comparative Study.” In: International Journal of Pure and Applied Mathematics, 117(8), pp. 45–49. doi:10.12732/ijpam.v117i8.10.
- 9. N.M. Kumar and P.K. Mallick . 2018. “The Internet of Things: Insights into the Building Blocks, Component Interactions, and Architecture Layers.” In: International Conference on Computational Intelligence and Data Science (ICCIDS).
- 10. J. Lin, W. Yu, N. Zhang, X. Yang, H. Zhang, and W. Zhao . 2017 October. “A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications.” IEEE Internet of Things Journal, 4(5), pp. 1125–1142.
- 11. H. Suo, J. Wan, C. Zou, and J. Liu . 2012. “Security in the Internet of Things: A Review.” In: Computer Science and Electronics Engineering (ICCSEE), 2012 International Conference on, pp. 648–651.
- 12. M. Leo, F. Battisti, M. Carli, and A. Neri . 2014 November. “A Federated Architecture Approach for Internet of Things Security.” In: Proceedings Of 2014 EURO Med Telco Conference (EMTC).
- 13. A. Al-Fuqaha, M. Guizani, M. Mohammadi, M. Aledhari, and M. Ayyash . 2015. “Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications.” IEEE Communications Surveys and Tutorials, 17(4), pp. 2347–2376. Fourth quarter.
- 14. I. Yaqoob et al., 2017 June. “Internet of Things Architecture: Recent Advances, Taxonomy, Requirements, and Open Challenges.” IEEE Wireless Communications, 24(3), pp. 10–16.
- 15. L.D. Xu, W. He, and S. Li, 2014 November. “Internet of Things in Industries: A Survey.” IEEE Transactions on Industrial Informatics, 10(4), pp. 2233–2243.
- 16. P.P. Ray . 2016. “A Survey on Internet of Things Architectures.” Journal of King Saud University – Computer and Information Sciences. doi:10.1016/j.jksuci.2016.10.003.
- 17. “Digital Service Innovation and Smart Technologies: Developing Digital Strategies Based on Industry 4.0 and Product Service Systems for the Renewal Energy Sector: Scientific Figure on ResearchGate.” Available: https://www.researchgate.net/Service-oriented-architecture-for-IoT-adapted-from-Li-et-al-2015_fig5_309807447. [Accessed September 23, 2018].
- 18. R. Khan, S.U. Khan, R. Zaheer, and S. Khan . 2012. “Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges.” In: 10th International Conference on Frontiers of Information Technology.
- 19. T. Ara, P.G. Shah, and M. Prabhakar . 2016 December. “ Internet of Things Architecture and Applications: A Survey.” Indian Journal of Science and Technology, 9(45), pp. 0974–5645. doi:10.17485/ijst/2016/v9i45/106507.
- 20. I.B. Thingom . 2015. “Internet of Things: Design of a New Layered Architecture and Study of Some Existing Issues.” IOSR Journal of Computer Engineering (IOSR-JCE ), 1, pp. 26–30.
- 21. N.M. Kumar and P.K. Mallick . 2018. “The Internet of Things: Insights into the Building Blocks, Component Interactions, and Architecture Layers.” In: International Conference on Computational Intelligence and Data Science (ICCIDS).
- 22. D. Darwish . 2015. “Improved Layered Architecture for Internet of Things.” International Journal of Computing Academic Research (IJCAR), 4, pp. 214–223.
- 23. P. Sethi and S.R. Sarangi, “Internet of Things: Architectures, Protocols, and Applications.” Journal of Electrical and Computer Engineering. doi:10.1155/2017/9324035.
- 24. J. Zhou et al., 2013. “Cloudthings: A Common Architecture for Integrating the Internet of Things with Cloud Computing.” In: IEEE 17th International Conference Computer Supported Cooperative Work in Design, pp. 651–657.
- 25. K. Wang, Y. Wang, Y. Sun, S. Guo, and J. Wu . 2016. “Green Industrial Internet of Things Architecture: An Energy-Efficient Perspective.” IEEE Communications Magazine, 54(12), pp. 48–54. doi:10.1109/MCOM.2016.1600399CM.
- 26. Green Industrial Internet of Things Architecture: An Energy-Efficient Perspective: Scientific Figure on ResearchGate.” Available: https://www.researchgate.net/figure/Energy-efficient-IIoT-architecture_fig1_311750469. [Accessed September 23, 2018].
- 27. Y. Sun, H. Song, A.J. Jara, and R. Bie . 2016. “Internet of Things and Big Data Analytics for Smart and Connected Communities.” IEEE Access, 4, pp. 766–773. doi:10.1109/ACCESS.2016.2529723.
- 28. H.-C. Hsieh and C.-H. Lai . 2011. “Internet of Things Architecture Based on Integrated PLC and 3G Communication Networks.” In: IEEE 17th International Conference Parallel and Distributed Systems, pp. 853–856.
- 29. Z. Qin et al., 2014. “A Software Defined Networking Architecture for the Internet-of-Things.” In: IEEE Network Operations and Management Symposium, pp. 1–9, May 2014.
- 30. J. Li et al., 2013. “A Mobile Phone Based WSN Infrastructure for Iot Over Future Internet Architecture.” In: Green Computing and Communications IEEE and Internet of Things, and IEEE International Conference Cyber, Physical and Social Computing, pp. 426–433.
- 31. “The Internet of Things Reference Model, Whitepaper from Cisco.” 2014.
- 32. Z. Javeed . 2018, May. “Edge Analytics, the Pros and Cons of Immediate, Local Insight.” [Online]. Available: https://www.talend.com/resources/edge-analytics-pros-cons-immediate-local-insight/. [Accessed September 22, 2018].
- 33. “Development of an Architecture for a Tele-Medicine-Based Longterm Monitoring System: Scientific Figure on ResearchGate.” Available: https://www.researchgate.net/The-visual-representation-of-Internet-of-Things-Model-shows-7-layers-from-1-the_fig8_315892029. [Accessed September 23, 2018].
- 34. A. Gerber. 2017 August 7. “Simplify the Development of Your IoT Solutions with IoT Architectures, IBM Document.”
- 35. “Watson IoT Platform Feature Overview, IBM Cloud.” 2018 [Online]. Available: https://console.bluemix.net/docs/services/IoT/feature_overview.html#feature_overview.
- 36. “Webcast: IoT Use-Cases with IBM Watson IoT Platform.” Mario Noioso, 2016 May 11. Available: https://marionoioso.com/2016/11/05/webcast-iot-use-cases-with-ibm-watson-iot-platform/.
- 37. “The Intel IoT Platform, Architecture Specification White Paper.”
- 38. “Microsoft, Azure IoT Reference Architecture, Microsoft.” 2018. Available: https://azure.microsoft.com [Online]. https://azure.microsoft.com/en-us/blog/getting-started-with-the-new-azure-iot-suite-remote-monitoring-preconfigured-solution/.
- 39. “Overview of Internet of Things.” 2018 Available: https://cloud.google.com/ [Online]. https://cloud.google.com/solutions/iot-overview [Accessed September 29, 2018].
- 40. “Google Cloud IoT.” 2018 Available: https://cloud.google.com/ [Online]. Available: https://cloud.google.com/solutions/iot/ [Accessed September 29, 2018].
- 41. “9 Platforms That Have Revolutionised the World of Things Connectivity — Part 1.” [Online]. Available: https://itnext.io/9-platforms-that-have-revolutionised-the-world-of-things-connectivity-part-1-2664624d6f65. [Accessed September 29, 2018].
- 42. K.L. Lueth . 2015. “The top 20 Internet of Things companies right now: Intel overtakes Google.” IoT Analytics, February 24. [Online]. Available: https://iot-analytics.com/20-internet-of-things-companies/.
- 43. Kavita Taneja, Harmunish Taneja, and Rohit Kumar . 2018. “Multi-Channel Medium Access Control Protocols: Review and Comparison.” Journal of Information and Optimization Sciences, 39(1), pp. 239–247.
- 44. Harmanjot Kaur and Rohit Kumar . 2019. “A Survey on Internet of Things (IoT):Layer-Specific, Domain-Specific and Industry-Defined Architectures.” Advances in Computational Intelligence and Communication Technology, pp. 260–270.
