30
–––––––––––––––––––––––
Scalable Service Composition in Pervasive Computing
Joanna Siebert and Jiannong Cao
30.1 INTRODUCTION
Nowadays, a majority of the appliances in physical environments around us are embedded with computing capabilities. Also, devices with communicating capabilities are growing in numbers and becoming more powerful. How to coordinate these smart devices and make them serve people in a less obtrusive manner has become one of the main research concerns in pervasive computing. In the vision of pervasive computing [34], the environment built on the physical world with embedded computing devices is a medium that provides a user with all the functionality he or she needs. Such a functionality of a computational entity whose execution satisfies the requestor's requirement is called a service.
This chapter is concerned with scalable service composition in pervasive computing environments (PvCEs). Service composition refers to the process of finding the best suited service providers in the environment, identifying and combining component functionalities to compose a higher-level functionality. It also provides the means to perform the requested functionality and to make services better suited by adapting to changes in the request and in the environment. The motivation behind the research on service composition in PvCEs derives from the huge gap between the high-level requirements from pervasive computing applications and the complexity of the PvCEs. In order to allow the massive deployment of service providers in PvCEs and its efficient composition, we need new architectures and techniques. Scalability of the service composition indicates the ability of the mechanisms to maintain the performance even if more service providers are present in the environment and when composed requests become more complex.
In this chapter, we present a review of recent research on scalable service composition in pervasive computing. The chapter is organized as follows. In Section 30.2, we analyze the functionalities of a service composition framework and present the background on scalable service composition in PvCE. In Section 30.3, we present the principles and the corresponding techniques for achieving scalable service composition with the evaluation of their advantages and disadvantages. Finally, in Section 30.4, we conclude the chapter with a discussion of the future directions of scalable service composition in PvCE research.
30.2 SERVICE COMPOSITION FRAMEWORK
Service composition in pervasive computing fills in the gap between users and service providers embedded in PvCEs. Service composition mechanisms facilitate interaction between entities in PvCEs and free users from tedious and redundant administrative and configuration works. Therefore, service composition research is critical to the success of pervasive computing. Scalability is a primary consideration in the design of mechanisms for service composition in pervasive computing systems. Mechanisms that work well in a small and relatively static system are not suitable for growing and dynamic systems.
30.2.1 Service Composition Mechanisms
In this section, we shall discuss the framework and the major components of a service composition system. As described in Figure 30.1, the service composition framework has two operational modules —the functional module and the execution module. Basic functions include means to specify the requirement by users and service descriptions by service providers, specifying the composition plan, and selecting the best suited service providers. The execution functionalities include service monitoring and adaptation policies to suit the user need under dynamic environment changes. The lowest layer of a service composition framework consists of the PvCE. Selection of service providers is facilitated by the use of various protocols designed for different composition models. Users, human or devices alike, can specify the composition plan and access services using different primitives. Service composition systems require scalability supports as well as measures to deal with dynamicity of the environments. We consider all the horizontal boxes as core components of a generic service composition system and the vertical boxes as essential system support service components. Different protocols may choose to implement the system support modules depending on the application and user requirements. Below, we describe the issues associated with different parts of the framework.
30.2.1.1 PvCE We define PvCE as a medium that provides users with all the functionality they need to satisfy their requirements. It is built on objects in the physical world with embedded computing devices interconnected according to the underlying communication network. Functionalities provided by devices embedded in PvCE are exposed as services. A service instance is software deployed on the device. It exists to be invoked or to be interacted with. Abstract descriptions of service instances are classified into service types. In PvCE, many service providers can provide the same functionality. Also, there may be no atomic service provider that can meet the requirement. Moreover, service providers can enter and leave the environment dynamically.
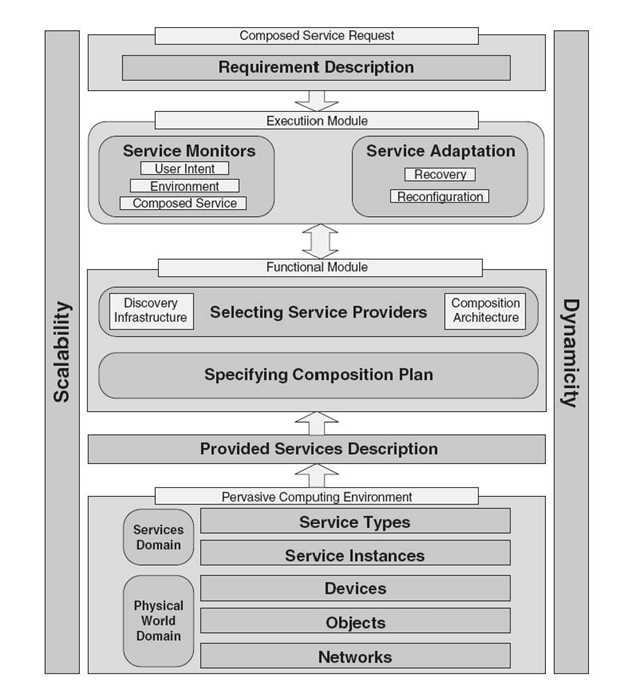
Figure30.1 Service composition framework.
30.2.1.2 Provided Services Description Smart objects may deliver functionalities for other objects and become service providers. Therefore, the service providers will provide description of their atomic services. Sometimes [1], they also specify composition plans in which they can take part. Existing service composition approaches are characterized by different expressiveness of the language used to describe the provided services.
30.2.1.3 Requirement Description In the meantime, the service requester can also express the requirement in a service specification language. Regarding the way that requested services are defined, we observe two approaches: low-level description and high-level description. In low-level description [1‒13], requested service is specified as a workflow, given the set of atomic services to be composed. In high - level description, the requested service is specified as a goal to be achieved [3, 12, 13].
30.2.1.4 Specifying the Composition Plan Next, the service composition system tries to provide the needed functionalities by composing the available functionalities that are exposed by service providers. It tries to generate one or several composition plans with the service providers available in the environment. Since PvCEs are saturated with service providers, often there can be several ways to satisfy the same requirement. In order to create the composition plan, diverse techniques can be used. In the most common approach [1‒5, 9‒11, 13‒15], a composite service is broken down into a sequence of interactions between atomic services. The system generates a customized composition plan that describes how various services should interact with one another as well as with the requestor.
30.2.1.5 Selecting Service Providers While many similar service providers are available to a requestor, it is important to determine which service provider should be used. It is challenging to find service providers for requestors efficiently and accurately. Service provider selection is a process of choosing a service provideramong discovered candidates. Many service providers can expose the same or similar functionalities. In that case, the services can be ranked based on the information provided from the nonfunctional attributes. In pervasive environments, this evaluation depends strongly on many criteria like the application context, the ability to interact with other service providers chosen to satisfy the requirement, the quality of the network, and the nonfunctional service quality of service (QoS) properties. In the majority of the solutions, selection is done by the service requestor [16‒19]. After receiving a full or partial list of available services, a user chooses a service based on service information and additional information, such as context. However, too much user involvement causes inconvenience. It may be distracting for a user to examine many candidates for service providers and to compare them. The second group of approaches is protocol - based selection, in which protocols may select services for a user [20]. The advantage of protocol-based selection is that it decreases user distraction. However, it is difficult to design a protocol selection that will reflect the actual useR's will since predefined selection criteria may not apply to all cases. A balance between protocol selection and user selection is needed. One way to achieve this is to enhance protocol-based service selection with context information [1‒3, 5‒15, 20‒23]. In addition to that, more desirable service providers can be identified and proposed to the user by considering the QoS of service providers [1, 4, 9‒11].
30.2.1.6 Service Adaptation Service providers may leave environments due to mobility, unexpected power off, or failures. In a PvCE, even when once the initial composition is identified and a service provisioning is established, the dynamicity of the environment may require change of the composed solution, which is called service recovery. In addition to dynamicity of the environment, the context in which composed services are deployed changes dynamically. For example, user intent may change during execution of the service. Moreover, the requirement may be changed according to new environment conditions. Composed service must adapt to such changes. Reconfiguration of composed service refers to the capability of a service to adapt to changing user needs and environment conditions.
30.2.1.7 Service Monitors In order to successfully perform recovery or reconfiguration of the composed service, first, the system needs to decide when it is necessary to invoke such functions. In general, recovery and reconfiguration should be invoked upon detected changes regarding user intent (new needs), environment (new opportunities), or currently executed composed service (failure handling). This function is provided by service monitors.
30.2.2 Scalability in PvCEs
When designing mechanisms for service composition in PvCE, issues of scalability and dynamicity must be taken into consideration. Both environment and users are impacted by the scale and dynamicity of PvCE. Due to increased interactions, users experience the problem of distraction. Also, in saturated PvCE, the response time becomes an issue. Increased interactions are also a problem to be tackled from the point of view of environments, where service providers must handle messages generated by different composed service requests. Moreover, with the increase of service providers, heterogeneity is more likely. Because computing resources are embedded in a physical environment, the distance between service providers and users becomes an issue.
This implies that algorithms and techniques should be different for PvCEs than they are for small-scale and static computing systems. There is a need for efficient mechanisms to perform service composition that will scale well and manage well dynamic and large-scale PvCE.
30.2.2.1 Dynamicity Support Dynamicity of the environments is one of the major challenges in pervasive computing, and to handle it efficiently, service recovery mechanisms are necessary. For example, users with their mobile phones may walk out of a room while their mobile phones were providing a service in collaboration with other devices in this room, or the users 'mobile phones may no longer be available due to power limitations. In scenarios of one of atomic services in a composed service becoming suddenly unavailable, the challenge is to recompose the service as quickly as possible considering the new state of the environment. The majority of the proposed solutions to the service composition problem assume static service composition. In this approach, if one of the services fails, service composition needs to start over again. Dynamic service composition approaches [9‒13, 25] support replanning of the composed service during the execution of the composition. Services can be replaced, added, or removed without starting the service composition processes over. Dynamic service composition is more difficult to implement than static service composition since every service provider of the composed service is being monitored and should be replaced immediately in case of failure.
30.2.2.2 Scalability Support Scalable service composition is the main consideration when designing PvCE. We measure scale of the environment along several dimensions—scale of services and service providers, scale of service requests, and scale of interactions in the environment. First, we are concerned with the number of service providers as well as the number and granularity of service types. Scale of environments varies, from small personal networks, through smart spaces and smart cities to all Earth connected into the Internet of Things. Within each environment, the number of embedded services grows. Moreover, the scale of the request, such as the size of the request, the number of requests, and the number of users is important as well. An additional consideration is the distance between collaborating services, as well as distance between users and services. There are more and more interactions between users and computing environments.
In fact, all the mechanisms in service composition frameworks should be designed with a goal to achieve scalability. However, it is most critical in the case of mechanisms that depend on the knowledge of the environment state, such as service selection. Since in large-scale, dynamic PvCE we assume that service requestors do not know what services are available in the environment and service providers may join and leave the environment at runtime, collecting knowledge about the environment state is very expensive. Therefore, in the next section, we will mostly focus on selecting service providers in service composition.
30.3 APPROACHES AND TECHNIQUES FOR SCALABLE SERVICE COMPOSITION IN PVCE
In the previous section, we have presented mechanisms in the service composition framework followed by issues introduced by scalability considerations. In this section, we focus on techniques to achieve scalability to address these issues. We will show how to build scalable service composition mechanisms for PvCE.
30.3.1 Approaches to Achieve Scalability
An important part of the service composition framework presented in the previous section is identifying appropriate service providers to contribute to the composed service. Depending on the environment characteristics, different approaches can be chosen when designing techniques for selecting service providers. Service composition mechanisms in this respect adopt either a centralized, decentralized, or hybrid architecture. They are presented in Figures 30.2‒30.4. These approaches detail how the knowledge about the environment (such as knowledge about service providers) is managed. Specifically, they differ from each other with respect to if global knowledge is necessary and how many entities collect any knowledge about the environment. In addition to three approaches presented in Figures 30.2‒30.4, we will also discuss a localized version of the decentralized approach to service composition.
30.3.1.1 Centralized Approach Many works [1, 2, 5, 14, 15] for PvCE propose centralized solutions to service composition. This category of works depends on the existence of a centralized directory of services, namely, they rely on one or more central entities to maintain the global service information in order to make composition decisions. Service requestors submit requirements to the directory and the directory makes a decision on the list of services that should be returned to the requestors. This approach works well for environments that are well managed and are relatively stable. However, the assumption on centralized control becomes impractical in scenarios with dynamic arrivals and departures of service providers, which requires frequent updates of the central entities, resulting in large system overhead. Moreover, relying on central entities to maintain global knowledge leads to inability of the system to serve the request when the central manager is compromised.
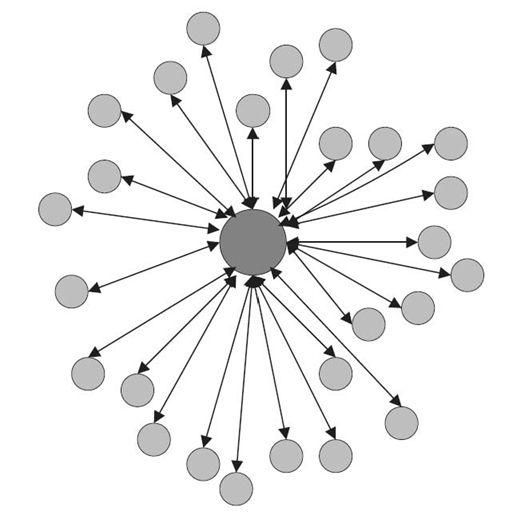
Figure 30.2 Centralized approach.
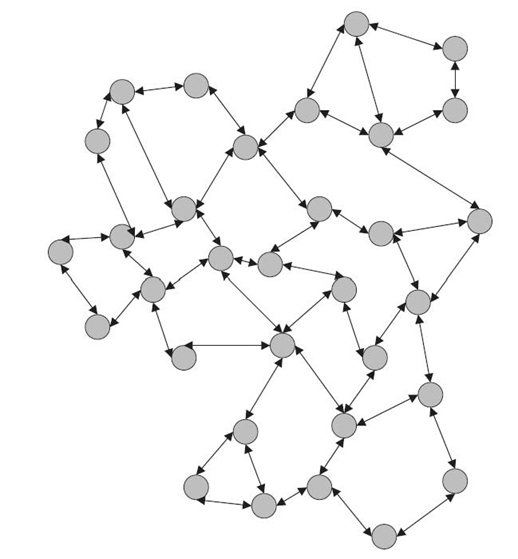
FIGURE 30.3 Decentralized approach.
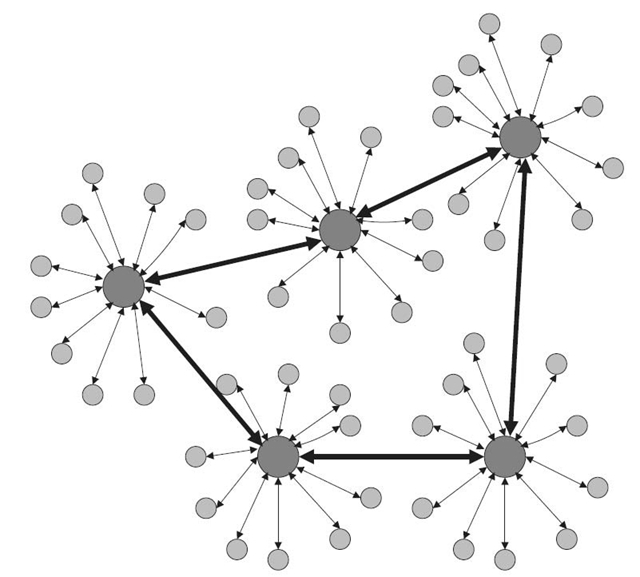
Figure30.4 Hybrid approach.
30.3.1.2 Decentralized Approach The next category of distributed service composition approaches removes the need for a service directory and provides a fully distributed search for needed services. In Reference 24, a hierarchical task graph-based approach to do service composition in ad hoc environments has been proposed. A composite service is represented as a task graph and subtrees of the graph are computed in a distributed manner. This approach assumes that the service requestor is one of the services and relies on this node to coordinate service composition. The coordinator uses global search across the whole network to do composition. The same domain of the problem was studied in Reference 25. It is different from Reference 24 in terms of the way of electing the coordinator. For each composite request, a coordinator is selected from within a set of nodes. The service requestor delegates the responsibility of composition to the elected coordinator. The elected coordinator utilizes distributed service discovery architecture and subsequently integrates and executes services needed for a composite request. However, many decentralized approaches still rely on global information. Even if there is no central directory, there is still need for a coordinator to collect global information. One category of decentralized approaches that do not rely on global information is localized algorithms.
Localized scalability is an important issue in service composition. It is often better to identify service providers that are closer to the user and there is no need to know the environment status in other parts of the PvCE. Therefore, localized algorithms can benefit from the scalable service composition in PvCE. They can significantly decrease the communication cost as well as response delay.
In general, a localized algorithm is a distributed algorithm where each node decides on its own behavior based on the information received from only nodes in its immediate neighborhood.
We have proposed a localized approach to the service composition process in Reference 26. Our work is based on the analysis of the requirements of the fully decentralized service composition: (1) There should be no special entity to manage the service composition process; (2) service providers can communicate only with their local neighbors, not all other service providers; and (3) no service provider knows the full global information or gathers it.
Our approach starts at lower levels of hierarchy and decisions arise from joint involvement of entities. Service providers distributed in the physical environment utilize localized interactions to satisfy the given requested composite service. In this approach, it is necessary for service providers to collaborate with their neighbors. We assume that all service providers in the environment can access a whiteboard showing the user-specified service description, which is a set of component functionalities together with composition relationships. Our problem is to construct the composite service in a distributed manner, through localized interactions between service providers. We transform this problem to a subgraph isomorphism problem, which is proven to be NP-complete.
Unlike previous algorithms that rely on global knowledge, in our algorithm, each device only maintains local state information about its physical neighbors. As a result, service providers will build an overlay network graph that satisfies the requirement with the QoS comparable to the centralized approach. We propose an algorithm for the devices to cooperatively construct the requested services through localized interactions. Device candidates decide with whom to cooperate based only on the information of the devices within its physical neighborhood. Our idea is to grow sections of composed service from available services. First, the service provider identifies what service type it needs to interlock with through his or her output and then searches for an appropriate service provider with matching input type. It is possible that service provider forms a section with another section. By merging pieces with each other, eventually, a global solution emerges.
30.3.1.3 Hybrid Approach In order to address deficiencies of centralized approaches, some works exploiting the hybrid approach have already been proposed. As the first step toward decentralization of service composition, they introduce a distributed directory of services. For example, in Reference 27, a hierarchical directory has been proposed. The resource-poor devices depend on resource-rich devices to support service discovery and composition.
In the rest of this section, we compare the approaches discussed above in terms of their scalability. We further characterize them by the knowledge that algorithms rely on. In the centralized approach, an algorithm relies on global information to make composition decisions, while the decentralized and hybrid approaches can be designed either based on global or local information. The localized approach is an example of a decentralized algorithm with local information. In this section, we only compare the centralized approach as an example of an algorithm requiring global information against the localized approach, which requires local information only.
Our comparison is in two dimensions, network size and request complexity. They describe the ability of the service composition mechanism to manage an increasing number of service providers and of atomic services in the request, with minimal effort given in number of messages and response delay [26].
30.3.1.4 Network Size Network size in the service composition in PvCE is bounded by the number of service providers as well as their distribution in the physical environment. To discuss the impact of the network size on the scalability of service composition approaches, we consider the number of messages necessary to find the first response and the time necessary to find the first answer.
Localized service composition mechanisms require fewer messages than centralized approaches for finding the first result. This is because the centralized directory needs to pull the request from the network, which includes generating and forwarding messages for sending the request and receiving the response, while the localized approach takes advantage of localized interactions: does not collect global information and considers only some limited neighborhood. Moreover, the localized approach scales very well with the growing size of the network, while centralized mechanisms impose larger cost when the network grows.
Similar observations can be made for the time necessary to find the first answer, according to the size of the network. The localized mechanism performs better than the centralized mechanism. Since in the centralized approach messages are flooded in the network, the collision effect causes increase in delay. The localized approach experiences a lower rate of collisions due to forwarding node selection. Similar to message cost, the localized approach scales better than the centralized approach due to considering only the local neighborhood.
30.3.1.5 Request Complexity The size of the request influences scalability of the service composition mechanisms as well. We discuss the influence of the request complexity on the number of messages generated and the time necessary to find the first answer by the service composition protocol.
Although the localized mechanism avoids flooding the network with messages, the number of messages generated increases with the complexity of the request. In this respect, the centralized approach is more scalable. Since the centralized mechanism collects global information, it collects the same amount of information for a different request complexity and incurs only a little additional cost for computing the result, while the cost of the localized mechanism depends on the complexity result.
With respect to the time necessary to find the first answer, according to the size of the request, the localized approach performs better than centralized for finding the first result. This is possible due to the localized nature of discovery of services to be composed. If service providers are close to each other, they can compose service faster than it takes for the central entity to collect information from the environment. With respect to scalability, the performance of localized and decentralized approaches is similar. The centralized approach requires longer time for more complex requests. Although the time for collecting the information from the environment is similar for different requests, however, the centralized mechanism will need additional time for evaluating the information and for making a decision.
30.3.2 Techniques for Achieving Scalability
We discuss further three main techniques for achieving scalability in service composition. We show not only how to select service providers for the composed service but also how to recover from the failed composed service. The service replication objective is to provide several copies of services that are kept consistent. In case of service failure, copies can be used. In accordance with the service locality principle, a service provider that is nearer should be used. Environment partitioning is a principle in which PvCE is split into parts that can operate independently to a large extent, such as smart houses and smart classrooms.
30.3.2.1 Service Replication Service composition mechanisms must provide a consistent view of service providers available in the network. They must be scalable and resilient to changes in the network's status. Service redundancy allows fast recovery of service composition. Service redundancy can apply to redundant service providers or redundant composition plans. Redundant service providers act as duplicates to failed services. Redundant composition plans allow choosing a completely different solution to the user request.
There are two main categories of methods in redundancy-based service recovery. The persistence-based method [28] assumes that the failure causes no further problems in the composed service. The failing service provider is ignored and has to provide its own recovery actions if it wants to join the composition again. The relocation-based method [29] migrates service from a failing service provider to a different one.
Repair and reconfiguration are also objectives of composition plan adaptation works, which focus on action that modifies the composition plan in a way that changes composition plan behavior in response to the change of context considered relevant to that composition plan. Reconfiguration is an adaptation that is triggered by the change of context related to the user's need, such as the need for new services or the replacement of an original service. Repair is triggered by changes in the environment during execution of the composed service. A service that is bound to a task might become unavailable and the composition plan needs to adapt to compensate the failure.
The composition plan adaptations can be done in many methods. One of them is specifying all the possible adaptations in the composition plan itself [21]. However, this method is not flexible since the composition plan must be changed every time a new adaptation is needed. It is only suitable for a composition plan that does not change often.
Another method is utilizing the abstract composition plan concept [30]. The abstract composition plan allows for adaptation in the abstract composition plan by determining the actual implementation of services in the abstract composition plan at execution time based on the context. In this method, the abstract composition plan contains one or more abstract activities that are replaced by one of the concrete implementations, which are predefined, to customize the service for the user. A variability point defines a part of the composition plan to which the service is selected and bound during execution. Flexibility of utilizing the abstract composition plan is limited, but it ensures that the adapted composition plan gives the expected result and is suitable for a rigid composition plan such as the hospital workflow presented as their scenario. Taking into account the resource context, this method may require the executing task to restart if the resource becomes unavailable.
Adapting the composition plan instance [31] is yet another method. Each service in the functional model is attached to a set of service versions that can be added at runtime. During execution, either the original service is executed or is replaced by one of the available versions based on various types of sensed context and the predefined adaptation rules. Therefore, the adaptation in this method takes place at the instance level and the service is bound during execution. This is the more flexible method but requires runtime service discovery and that the list of available services be maintained.
These adaptation levels imply a different composition plan management. Composition plan instance adaptation can be handled easier, while the adaptation in the concrete definition requires the handling of the running composition plan instances. Late binding, in which the services in the composition plan are bound to the services as the execution proceeds to each service in the composition plan instance, provides more flexibility but requires runtime service discovery and that the list of available services be maintained.
30.3.2.2 Service Locality In service composition for PvCE, service locality refers to the distance between the services used in composition, and it is required that it should be as small as possible. Composition locality is an important factor when the tasks include services that need to interact with each other and if they are embedded on different service providers in the network. To minimize such cost of composition, all atomic services in the composed service need to be located as close to each other as possible. Localized approaches naturally tend to select compositions with a high degree of composition locality. Service locality can also be achieved by caching of service descriptions.
30.3.2.3 Environment Partitioning Works in traditional areas of identifying service providers as well as service recovery share a common feature, which is the globalized nature of algorithms. As mentioned earlier, in a globalized algorithm, at least one node needs to maintain global network information. This is unsuitable for highly dynamic and large-scale environments. Gathering such global information creates huge communication overhead, especially with frequent changes of topology. Moreover, global knowledge is not always necessary. Splitting service environment into parts that operate independently increases scalability of the service composition mechanisms. This can be achieved by deployment of cooperating directories within the network. A distributed set of directories is deployed over base stations, and the directories are responsible for a spatial region. The traffic generated by the service discovery process is kept to a minimum, and consumption of resources, in particular energy, is minimized.
30.4 CONCLUSIONS
As discussed in this chapter, service composition concerns several functionalities for bridging the gap between users and services embedded in PvCE. In particular, scalable service composition is concerned with the ability of the service composition mechanism to manage an increasing scale of service providers and service requests with minimal effort given in the number of messages and response delay. The growing scale of the environments as well as their dynamicity make it more difficult to manage information about available service providers. Traditional centralized approaches that rely on a special node collecting global information become unsuitable for such environments. Techniques that adopt decentralized and more specifically localized architectures are proposed to address scalability issues. Further, service replication, service locality, and environment partitioning are important principles to achieve scalability of the service composition mechanism.
Several issues are still worth investigating. One core challenge that remains more or less unexplored is how we can further utilize localized algorithms for service composition in PvCEs. Developing localized algorithms can be the key to address the challenges posed by the dynamic and ad hoc nature of pervasive systems. Pervasive devices must coordinate locally with peer devices to achieve some global objective with respect to service composition.
REFERENCES
[1] S.B. Mokhtar, N. Georgantas, and V. Issarny, “Cocoa: Conversation-based service composition in pervasive computing environments,” Proceedings of the IEEE International Conference on Pervasive Services, 2006.
[2] Z. Song, Y. Labrou, and R. Masuoka, “Dynamic service discovery and management in task computing,” in Mobiquitous, pp. 310‒318, 2004.
[3] C. Hesselman, A. Tokmakoff, P. Pawar, and S. Iacob, “Discovery and composition of services for context-aware system,” Proceedings of the 1st European Conference on Smart Sensing and Context, 2006.
[4] A. Mingkhwan, P. Fergus, O. Abuelma Atti, M. Merabti, B. Askwith, and M.B. Hanneghan, “Dynamic service composition in home appliance networks,” Multimedia Tools and Applications, 29: 257‒284, 2006.
[5] H. Pourreza and P. Graham, “On the fly service composition for local interaction environments,” in IEEE International Conference on Pervasive Computing and Communications Workshops, p. 393, IEEE Computer Society, 2006.
[6] A. Qasem, J. Hein, and H. Munoz-Avila, “Efficient source discovery and service composition for ubiquitous computing environments,” Workshop on Semantic Web Technology for Mobile and Ubiquitous Applications, 2004.
[7] M. Sheshagiri, N.M. Sadeh, and F. Gandon, “Using semantic web services for context-aware mobile applications,” Second International Conference on Mobile Systems (MobiSys 2004), Applications, and Services—Workshop on Context Awareness, 2004.
[8] T. Cottenier and T. Elrad, “Adaptive embedded services for pervasive computing,” Workshop on Building Software for Pervasive Computing—ACM SIGPLAN conf. on Object-Oriented Programming, Systems, Languages, and Applications, 2005.
[9] W.L.C. Lee, S. Ko, S. Lee, and A. Helal, “Context-aware service composition for mobile network environments,” International Conference on Ubiquitous Intelligence and Computing, 2007.
[10] G. Kaefer, R. Schmid, G. Prochart, and R. Weiss, “Framework for dynamic resource-constrained service composition for mobile ad hoc networks,” UBICOMP, Workshop on System Support for Ubiquitous Computing, 2006.
[11] U. Bellur and N.C. Narendra, “Towards service orientation in pervasive computing systems,” in Proceedings of the International Conference on Information Technology: Coding and Computing, pp. 289‒295, 2005.
[12] A. Ranganathan and R.H. Campbell, “Autonomic pervasive computing based on planning,” in International Conference on Autonomic Computing, pp. 80‒87, 2004.
[13] A. Ranganathan and S. McFaddin, “Using workflows to coordinate web services in pervasive computing environments,” in Proceedings of the IEEE International Conference on Web Services, pp. 288‒295, 2004.
[14] M. Vallee, F. Ramparany, and L. Vercouter, “Flexible composition of smart device services,” in International Conference on Pervasive Systems and Computing, pp 165‒171, CSREA Press, 2005.
[15] A. Bottaro, J. Bourcier, C. Escoffier, and P. Lalanda, “Autonomic context-aware service composition,” 2nd IEEE International Conference on Pervasive Services, 2007.
[16] E. Guttman and C. Perkins, “Service location protocol,” version 2, 1999.
[17] S. Helal, N. Desai, V. Verma, and C. Lee, “Konark—A service discovery and delivery protocol for ad hoc networks,” Proceedings of the 3rd IEEE Conference on Wireless Communication Networks, 2003.
[18] Sun Microsystems, Jini Technology Core Platform Specification, v. 2.1.2.2003. Available at http://river.apache.org/doc/spec-index.html.
[19] UPnP Forum, UPnP Device Architecture 1.0.2008. Available at http://upnp.org/specs/ arch/UPnP-arch-DeviceArchitecture-v1.0.pdf.
[20] M. Nidd, “Service discovery in DEAPspace,” IEEE Personal Communications, 8: 39‒45, 2001.
[21] M. Wieland, P. Kaczmarczyk, and D. Nicklas, “Context integration for smart workflows,” Proceedings of the 6th Annual IEEE International Conference on Pervasive Computing and Communications, IEEE Computer Society, 2008.
[22] S.Y. Lee, J.Y. Lee, and B.I. Lee, “Service composition techniques using data mining for ubiquitous computing environments,” International Journal of Computer Science and Network Security, 6 (9): 110‒117, 2006.
[23] Q. Ni, “Service composition in ontology enabled service oriented architecture for pervasive computing,” Workshop on Ubiquitous Computing and e-Research, 2005.
[24] T.D.C. Little, B. Prithwish, and K. Wang, “A novel approach for execution of distributed tasks on mobile ad hoc networks,” IEEE WCNC, 2002.
[25] D. Chakraborty, A. Joshi, T. Finin, and Y. Yesha, “Service composition for mobile environments,” Mobile Networks and Applications, Special Issue on Mobile Services, 10: 435‒451, 2005.
[26] J. Siebert, J.N. Cao, L. Cheng, E. Wei, C. Chen, and J. Ma, “Decentralized service composition in pervasive computing environments,” International Wireless Communications and Mobile Computing Conference, 2010.
[27] S. Kalasapur, M. Kumar, and B.Z. Shirazi, “Dynamic service composition in pervasive computing,” IEEE Transactions on Parallel and Distributed Systems, 18: 907‒918, 2007.
[28] C. Dabrowski and K. Mills, “Understanding self- healing in service-discovery systems,” in WOSS '02: Proceedings of the 1st Workshop on Self-Healing Systems, pp. 15‒20, ACM, 2002.
[29] J. Albrecht, D. Oppenheimer, A. Vahdat, and D.A. Patterson, “Design and implementation trade-offs for wide-area resource discovery,” ACM Transactions on Internet Technology, 8: 1‒44, 2008.
[30] N.C. Narendra, B. Umesh, S.K. Nandy, and K. Kalapriya, “Functional and architectural adaptation in pervasive computing environments,” in Proceedings of the 3rd International Workshop on Middleware for Pervasive and Ad-Hoc Computing, ACM, 2005.
[31] T. Chaari, D. Ejigu, F. Laforest, and V.M. Scuturici, “A comprehensive approach to model and use context for adapting applications in pervasive environments,” Journal of Systems and Software, 80: 1973‒1992, 2007.
[32] M. Satyanarayanan, “Pervasive computing vision and challenges,” IEEE Personal Communications, 8: 10‒17, 2001.
