Chapter 17
Opportunistic Networks
In this chapter, we will briefly describe the main features of an emerging class of next generation wireless networks, namely, opportunistic networks. After presenting the state of the art in opportunistic networking and related technologies, we will describe representative use cases. Finally, we will present a short overview of the main envisioned technological evolutions, and of the challenges to be faced by opportunistic network designers.
17.1 Opportunistic Networks: State of the Art
An opportunistic network is a short-range wireless network characterized by a very sparse network topology—see Figure 17.1: if one takes a snapshot of the network at an arbitrary time instant, what is typically observed is a large fraction of isolated nodes, and a small fraction of nodes having active links with a few other nodes in the network. From a networking perspective, what is lacking in the network topology is connectivity, that is, the possibility for a node in the network to establish a (possibly multi-hop) communication path with all the other nodes. However, network connectivity—or at least, as we will see, a weak form of connectivity—can be achieved by exploiting the temporal dimension and node mobility: since nodes in an opportunistic network move, isolated nodes can get in touch with other nodes as time goes by. Similarly, a node A which is currently in touch with node B might later get in touch with another node C, and so on—see Figure 17.1. So, if messages circulating in the network are stored in the node buffers for a long enough time interval, it is indeed possible to establish multi-hop communication paths between nodes in the network by exploiting these relatively seldom communication opportunities—whence the name of the network—achieving network-wide communications.
Figure 17.1 Typical opportunistic network architecture.
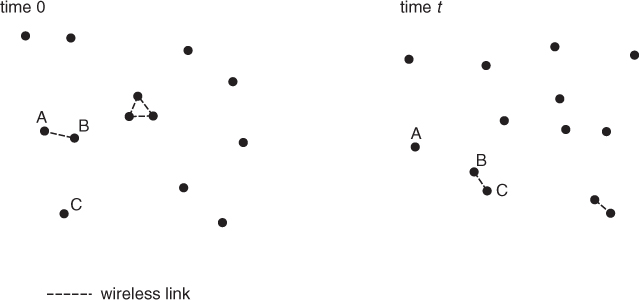
Since the communication mechanism described above—called store, carry, and forward, see Chapter 18—relies on node mobility to physically carry around and forward messages within the network, and human/animal/vehicular mobility is several orders of magnitude slower than the speed of radio signal propagation in the air, which is comparable to the speed of light, it is clear that the delays in communicating a message from source to destination are much higher than those typical of other types of networks. Hence, applications running in opportunistic networks must be able to tolerate very large delays—in the order of minutes or hours—which explains why opportunistic networks are also called delay-tolerant networks (DTNs).
Unlike the other types of next generation wireless networks considered so far in this book, opportunistic networks are not related to a specific wireless technology, but rather are a class of mobile networks characterized by the above-described specific topological property of being extremely sparse. This means that, depending on the scenario, the radio technology used to establish wireless links between nodes can be different: it can be a WLAN technology such as WiFi, a PAN technology such as Bluetooth, or a vehicular or wireless sensor communication technology if some of the members of the opportunistic network are vehicles and/or wireless sensor nodes. It is indeed the case that in some scenarios different technologies coexist, and are alternately used to establish peer-to-peer wireless links: the most typical case in this respect is that of a smart phone with both WiFi and a Bluetooth interface and which can use either interface to establish a wireless link with another cell phone.
One type of opportunistic network that has recently attracted a lot of attention in the research community is the one which is dynamically formed by individuals carrying advanced personal communication devices (PCDs) capable of establishing direct wireless links, such as smart phones, PDAs, etc. This type of opportunistic network is known as a pocket-switched network (PSN) in the literature (Hui et al. 2005), and is considered very interesting under both the mobility analysis/characterization viewpoint and the potential application viewpoint. In fact, since members of a PSN are people, characterization of human mobility patterns can be used to improve the PSN performance. Furthermore, PSNs can potentially enable novel participatory and social networking applications based on opportunistic communications, as described in the next section.
It is important to observe that, while most nodes in an opportunistic network are mobile, there might exist application scenarios in which some of the nodes in the network are fixed and act as data collection and/or message relay points. An important example of this class of opportunistic networks is DieselNet, an opportunistic network composed of 40 radio-equipped public buses in the city of Amherst, Massachusetts (Group 2007). In DieselNet, some of the bus stops are equipped with wireless collection points called throwboxes that act as message relays, thus speeding up the message propagation process in the network. Another example is that of a very sparse wireless sensor network composed of mobile sensor nodes (e.g., sensor nodes attached to animals), where fixed data gathering stations can be installed in strategic locations (e.g., at a water source).
From a technological viewpoint, some of the short-range wireless technologies that can be used in opportunistic networks are mature (e.g., WiFi and Bluetooth for PSN applications), some are close to fully ripening (e.g., ZigBee for WSN-related applications), while others are in an advanced development stage (e.g., IEEE 802.11p/DSRC (Dedicated Short-Range Communications) for vehicular-related applications). A summary of the main features of wireless technologies for opportunistic network communications is given in Table 17.1.
Table 17.1 Short-range wireless technologies for opportunistic network communications

17.2 Opportunistic Networks: User Scenarios
In this section, we report some representative user scenarios for opportunistic networks in the domain of PSN, WSN, and vehicular network applications.
17.2.1 User Scenarios in PSNs
Suppose traveler Bob has just arrived at an airport in a foreign country, and he would like to take a taxi to the Hotel Wonderland where he is staying. If possible, Bob would like to share the ride with other travelers staying at the same hotel, and thus to share the costs of the taxi ride. With PSNs, Bob could disseminate a message expressing his interest in going to the Hotel Wonderland by taxi. Due to the very dense population of PCD-equipped individuals typically found in an airport—highlighting that, in some cases, a part of an opportunistic network can indeed be relatively dense—Bob's expression of interest is likely to be disseminated quickly in the airport. So, in a few minutes since issuing the message, Bob could get a reply from other travelers interested in taking a taxi to the Hotel Wonderland, and who maybe are currently still waiting to claim their baggage. Another possible reply to Bob's expression of interest message might be a notification from a local shuttle service that a shared shuttle service to the Hotel Wonderland is available, together with directions on how to reach the shuttle stop. After getting the replies, Bob could decide to wait for the other travelers, or inform them that he was going instead to take the taxi by himself or the cheaper shuttle service.
Note that a smart transportation service like this one could be realized also through the Internet, for instance, by accessing a web server collecting travelers' posts about their transportation needs. However, this would require users to have Internet access enabled on their cell phones, which comes at a cost, especially considering that many subscription plans have rather high rates for accessing the Internet when roaming. If PSNs are used instead, no connection to the Internet is required, and also relatively cheap cell phones with a Bluetooth interface and no Internet connection can be used to access the smart transportation service.
Another possible use of PSNs is in the aftermath of disasters. Suppose an earthquake hit the city of Futuria, and the communication infrastructure—including the cellular network—is compromised. PSNs can be used during the hours/days needed to restore the communication infrastructure to enable exchange of information between survivors, members of the rescue teams, etc. For instance, a person living in Woodland Street who survived the earthquake could take some pictures with her cell phone to show the situation concerning the buildings and roads in the vicinity, and disseminate this information on the PSN. In a few minutes, the information could be delivered to a member of a rescue team, who would then share this information with other members of the team and local authorities to gain a better understanding of the situation. Alternatively, another person living in Woodland Street currently located in Central Avenue, where he works, might disseminate on the PSN an enquiry for any information relating to the situation in Woodland Street. After a few minutes, he might start to receive text messages and pictures reporting the situation in Woodland Street, from which he can see that his house survived the earthquake.
17.2.2 User Scenarios in WSNs
Suppose a WSN is used to monitor the health status and movement of wild animals. A small fraction of the monitored animals are equipped with radios. Furthermore, a set of fixed base stations with satellite Internet connection is located in selected feeding grounds and near water sources. When two radio-equipped animals move into each other's transmission range, they exchange summaries of their movement/health status in the last time period. This way, the data generated by an animal can reach the remote user monitoring the animals through the Internet in two ways: directly, when the tracked animal visits one of the regions covered by a base station; or through a multi-hop path, if the animal's movement/health status summary is delivered to a base station by another, recently met animal.
Note that this scenario, similar, for example, to that of the well-known ZebraNet experiment (Martonosi et al. 2004), is well within the realm of opportunistic networks when the density of radio-equipped animals is relatively low, and eventual communication of tracked data to the base stations is achieved through exploitation of animal movements.
17.2.3 User Scenarios in Vehicular Networks
Consider an advanced urban traffic monitoring system whose purpose is to give local authorities and vehicle drivers a real-time picture of the current traffic status in a city. Traffic status is tracked in real time both through fixed cameras at selected points and through traffic reports generated by the vehicles themselves. In particular, a set of traffic checkpoints is defined within the road network by the traffic authorities, and communicated to the traveling vehicles through the communication infrastructure—composed, for instance, of a set of sparsely deployed IEEE 802.11p RSUs. When traveling, vehicles automatically detect whether they have just passed a checkpoint and, if so, they compute the time elapsed since the passing time at the previous checkpoint. The computed traveling time, together with the ID of the two checkpoints, constitutes a traffic report, which is delivered to the traffic monitoring service through the communication infrastructure, for example, when the vehicle gets in touch with one of the RSUs. If the density of RSUs is not too sparse, or in case multi-hop forwarding of traffic reports is allowed, traffic reports reach the traffic monitoring service center in a few seconds, thus enabling a real-time assessment of the situation. A traffic monitoring service similar to the one described above has been recently proposed in the IPERMOB project (Consortium 2010).
The previously described scenario, at least the part concerning communication of traffic reports to the monitoring service center, displays all the features of opportunistic networks: a network composed of relatively sparse mobile nodes (we can expect that DSRC-equipped vehicles will be a minority of all circulating vehicles for several years to come), complemented with a few fixed collection points (RSUs); data generated by the vehicles is eventually delivered to the monitoring service center through a RSU, with a possibly faster data delivery process in case vehicle-to-vehicle forwarding of traffic reports is realized.
17.3 Opportunistic Networks: Perspectives
While opportunistic networks are considered a very promising type of next generation wireless network, technological and network design challenges are still to be satisfactorily addressed before these networks can be considered a feasible and practical solution.
In terms of technology, we are currently in a situation where some of the short-range wireless technologies exploited for opportunistic communications are mature, while others—especially in vehicular applications—are still to mature. However, where the radio technology is mature, the problem of designing energy-efficient solutions is still to be faced. Curiously, in those situations where energy consumption is not an issue, such as in vehicular applications, the communication technology is relatively less mature.
For instance, considering PSNs, it is well known that the energy drain of a smart phone when the WiFi or Bluetooth interfaces are active is very high, leading to a very short battery life if these interfaces are continuously kept active. Thus, applications for opportunistic networks should be designed taking into account that short-range radio interfaces are not necessarily active, possibly leading to missed communication opportunity detection. This means that energy efficiency should be carefully traded off against a lower likelihood of detecting communication opportunities, which are the fundamental building blocks of any opportunistic networking protocol. Another possible way of addressing the problem of energy efficiency is through improved hardware design of the short-range radio interfaces, possibly integrating them better with the other interfaces present in the smart phone.
It is important to observe that efficient use of the battery is a prerequisite for the success of opportunistic network-based applications: a user is likely to be willing to use these applications if the perceived “added value” they provide is not overwhelmed by the increase in energy consumption; if running an opportunistic network application—even a very exciting one—drains the battery in a few hours, it is likely that most users will end up not using it.
Another major challenge facing the opportunistic network designer is related to the design and realization of networking protocols explicitly designed for opportunistic networks. So far, most research efforts have been devoted to optimizing the performance of well-known networking primitives such as unicast, broadcast, multicast, and so on, in opportunistic networks. However, these primitives appear to be unsuitable for an effective design of opportunistic network applications such as those described in the previous section. Consider for instance the airport scenario. What networking primitive should be used to propagate Bob's message within the airport PSN? Unicast is not suitable, since there is no specific destination that Bob is aware of to which the message should be sent. Similarly for broadcast, since it is not even clear who the members of the airport PSN are at a given time; furthermore, most of the airport PSN members are likely not to be interested in Bob's message. Multicast could be a reasonable choice, but it is quite unlikely that a multicast group composed of “all the users staying at the Hotel Wonderland” could be distributively built and efficiently maintained in such a dynamic setting.
The example above highlights the need to design radically different networking primitives for opportunistic networks, which are designed, for instance, to deliver a message to all users sharing similar interests (staying at the Hotel Wonderland in the airport example) or to all users of a community (those living on Woodland Street in the earthquake example), and so on.
Finally, security and privacy issues are still to be addressed, especially in PSNs. Most existing opportunistic networking solutions exploit information about a user's mobility pattern, social ties, and so on, to optimize the spreading of messages and information within the network. While these solutions achieve their goal in terms of improved network performance, it is very unlikely that users will be willing to expose such sensitive information to potential strangers to run opportunistic network applications. Hence, techniques should be designed to enable a secure and privacy-preserving spreading of information within opportunistic networks.
17.4 Further Reading
This chapter is just a short introduction to opportunistic networks and related technologies. The reader interested in gaining a better understanding of this topic is referred to the books and surveys available in the literature, such as Zhang (2006), Farrell and Cahill (2006), Harras (n.d.), and Denko (2008).
Consortium I 2010 http://www.ipermob.org.
Denko M 2008 Mobile Opportunistic Networks: Architectures, Protocols and Applications. Auerbach Publications, Boca Raton, FL.
Farrell S and Cahill V 2006 Delay- and Disruption-Tolerant Networking. Artech House, London.
Group PR 2007 http://prisms.cs.umass.edu/dome/umassdieselnet.
Harras K n.d. Challenged Networks: Protocol and Architectural Challenges in Delay and Disruption Tolerant Networks. VDM, Saarbr.
Hui P, Chaintreau A, Scott J, Gass R, Crowcroft J and Diot C 2005 Pocket-switched networks and human mobility in conference environments. Proceeding of the ACM Workshop on Delay-Tolerant Networks.
Martonosi M, Lyon S, Peh LS, Poor V, Rubenstein D, Sadler C, Juang P, Liu T, Wang Y and Zhang P 2004 http://www.princeton.edu/mrm/zebranet.html.
Zhang Z 2006 Routing in intermittently connected mobile ad hoc networks and delay tolerant networks: Overview and challenges. IEEE Communications Surveys & Tutorials 8, 24–37.
