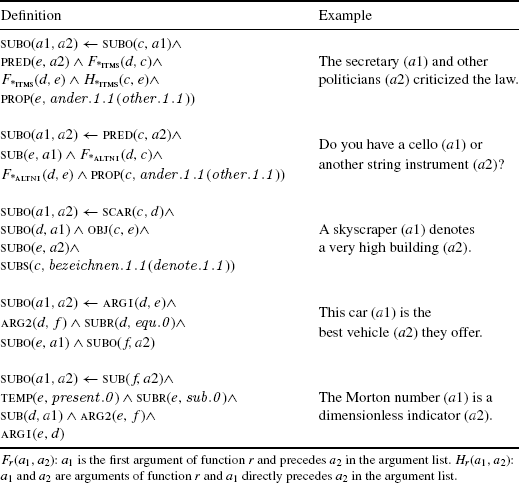
11.6 Architecture
In this section, we shortly give an overview of the total hyponymy extraction process.
The entire validation process is illustrated in Figure 11.2.
Figure 11.2 Activity diagram for the hyponym acquisition process.
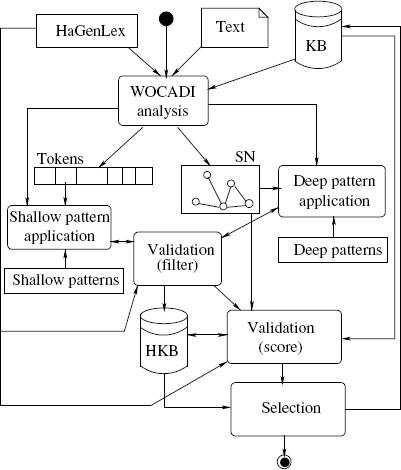
A deep extraction rule consists of a conclusion sub0(a1, a2) (sub0: hyponymy/instance-of/troponymy relation) and a premise that is a semantic network where two of the nodes are labeled with the variables a1 and a2. The pattern network is tried to be matched to the sentence network. The variables can be bound to arbitrary concepts. The instantiated conclusion, where a1 and a2 are replaced by the concepts they were bound to, is the extracted hypothesis. Several example rules are given in Table 11.1. The extraction rules are in part manually specified and in part learn automatically from a collection of annotated semantic networks employing the Minimum Description Length Principle [26], basically following the approach of Cook and Holder [12].
Table 11.1 A Selection of Deep Patterns.