19
University Learning Technology Control and Security: Requires Teamwork to Succeed
Donald Tharp and Greg Chamberlain
19.1 Introduction
Learning technology (interchangeably termed instructional or educational technology) and information technology continue to grow rapidly and expand further into instructional and student support practices at institutions of higher education. Two major issues continue to challenge college and universities’ attempts to facilitate adoption and integrate learning technology as an integral part of their processes. The first issue deals with security across the spectrum of individual institutions regarding people, data, infrastructure, and equipment. The second issue concerns the relationships among those who control and manage learning technology (Weiss 2011). Information technology is focused on normal day-to-day operations of the network and equipment as well as securing data and information. Learning technology focuses on facilitating learning and improving performance through the use of technology. Although related, they are distinctly different both in technology use and the integration planning. Therefore, control (e.g., accountability, responsibility) for strategic planning, integration, and professional development should be accomplished by their respective organizations with clearly defined roles and responsibilities.
Higher education institutions, regardless of size and population, are confronted with daunting challenges in regards to computer security and system maintenance. Schools face a lack of information technology resources (Grajek 2013; Grajek and Pirani 2012), limited information technology staff, software limitations, and significant budget constraints that make providing the same type of security and management as entities such as government institutions or corporations nearly impossible. Additionally, depending on the institution and planning process, the lack of equipment standardization, training, and infrastructure make these challenges even more difficult for higher education administrators to overcome. The successful adoption of learning technology requires the successful integration and security of information technology. In higher education, learning and information technology professionals must be committed, work, and plan as a team for successful integration.
According to Brown, Lauder, and Ashton’s 2008 study conducted in Britain, China, Germany, India, Korea, Singapore, and the United States, in a globalized world economy based heavily on information services and technology higher education is critical in preparing students to enter the workforce (Brown, Lauder, and Ashton 2008). According to the New Media Consortium Horizon Report (Johnson et al. 2014), over the next 12 years the World Bank estimates a 25% increase in higher education attendance. To put this into perspective, in Africa alone by 2025 four universities serving 30,000 students would need to be built per week to accommodate enrollment. With this kind of increasing demand, there is an intensified emphasis on online/e-Learning capabilities reaching out to both urban and rural communities (Jasinski 2007). As learning technology solutions increase educational program delivery capabilities, students increasingly are gaining more convenient access to higher education. Additionally, faculty have a wider array of learning technology tools to choose from, all designed to enhance the student’s learning experience and educational outcomes.
In addition to location-specific college and university programs, distance-learning technology has proven effective in bridging geographic, transportation, and time-related barriers to college coursework. Currently, according to Allen and Seaman (2014), online education offerings are small but growing rapidly; in 2013 at least 33.5% of US higher education students took an online course. Additionally, in rural populated countries (e.g., Australia, India, South Africa, China) Open University types of higher education systems (distance/online) have proven to be cost-effective in filling demand and providing educational opportunities. Unfortunately, how online education is presented to students is inconsistent and quality varies by institution and instructor. However, through the adoption and implementation of standards (e.g., see Allen and Seaman 2014) online education paired with the appropriate technology has become more student-centered and instructionally sound (Woods 2014).
Today over 80% of new jobs created by the knowledge-driven economy require education at university level (Glazer and Grimes 2014). Population growth requires higher education expand to meet the needs of traditional students but there needs to be even greater growth in order to meet nontraditional student needs. Unfortunately, higher education is facing limited resources, budgets cuts, and slowed expansion due to the weak economy. Massive open online courses (MOOCs) provide students with the opportunity to take a course taught by some of the most prestigious faculty in academia, forcing universities to start looking internally at how to reach students locally, nationally, and internationally more efficiently and effectively (MacGregor 2013). Additionally, with the cost of tuition rising beyond the means of most families, it becomes imperative institutions adopt and implement learning technologies and look at ways to reach students, develop faculty expertise with the use of learning technologies, and provide university leadership with the understanding and tools needed to control and manage these learning technologies.
Although higher education’s move towards implementing learning technology is driven by an increasing number of competitors and student demand, its implementation should not be considered a panacea, with excellent outcomes reached each time. Even though technology has become a pervasive part of everyday life, many higher education faculty have resisted embracing learning technology. The implementation of learning technology can range from very successful to abysmal failure (Johnson et al. 2013).
In an effort to increase the likelihood of successful adoption, the selection and integration of technology should be accomplished in a manner consistent with mission and strategy such that learning is enhanced but organizational priorities and identities remain intact (Bonk et al. 1999). These possibilities inform and shape the manner in which we view, support, and lead higher education. Technology integration in higher education should be planned, adopted, securely delivered, and carefully controlled.
To assist the adoption of learning technologies plans, policies, and finances should be considered and implemented to meet the ongoing needs of the institution’s faculty, students, and staff. An institutional mechanism is necessary to help address those needs along with training, professional development, and data and equipment security (Cao and Sakchuctchawan 2011). Normally the higher education institutional mechanism is established via a technology plan. The technology plan provides the basis for the administrative leadership to establish a technology committee focused on learning and information technology integration (Weiss 2011).
The technology committee is critical to the success of the institution’s technology plan. The committee expertise should be focused on resources, infrastructure, people, policies, learning, evaluation, and support (RIPPLES) (Surry 2002). Additionally, according to Rogers (2003), the committee needs to understand the barriers to adoption and the change process. In higher education, adoption barriers include change agents, time, workload impact, technology support, access, and training (Elzarka 2012). The ability to provide leadership with viable technology integration and operational planning falls under the technology committee established by institution leadership (see Figure 19.1).

Figure 19.1 Institution organization.
According to the New Media Consortium Horizon Report (Johnson et al. 2013), technology continues to drive much of the futuristic thinking in academia. Higher education’s ability to keep pace with people’s desire for technology (e.g., information, social media, networks anytime/anywhere) requires reasoned plans and accessible implementation policies and programs. Technology planning is a major undertaking and requires a commitment to the process and understanding of how the institution’s technology fits into the overall strategic plan.
19.2 Educational Master Plan
Establishing a strategic plan is about making choices and in higher education adding another meeting, committee, or team takes time away from doing day-to-day work. This can be compounded when the institution is situated across multiple sites or international boundaries, adding to communication issues and resource allocation, or is too small and under-resourced. For an institution without a strategic plan, developing one requires time, money, and resources, all of which are in short supply (Kerr 1999). Institutions that engage in poor or unfocused planning processes end up with disillusioned faculty, staff, and students, poor use of resources and loss of funding, and a 20% success rate (Hinton 2012). The high rate of failure has been linked to leadership, communication, and inflexibility of the plan and planning process. The lack of teamwork, planning, focus, timing, and support has led to the failure of the UK’s eUniversity (Garrett 2004), Arizona Learning Systems, New York University Online, and AllLearn (Oxford, Yale, and Stanford) (Matthews, Pickar, and Schneid 2007). According to Higher Ed CIO (2011) the two main reasons why strategic planning fails are:
- organizations cannot consistently describe their own strategy
- 66% of information technology departments continue to develop plans that are not aligned to the institution’s strategy.
All too often strategic plans are relegated to shelves, committees established without support, and very little of the plan implemented. In the mid-1990s accreditation standards started shifting from institutional level measures (e.g., fiscal stability, faculty with terminal degrees, number of books in the library) to trying to measure the learning process. To help tighten standards, accreditation organizations and government agencies insisted institutions have a strategic plan meshed with an evaluation plan in order to meet accrediting requirements (Hinton 2012). Additionally, Grajek (2013) relayed the need for strategic priorities and strategically funded technology and how those forces are shaping institutional strategy.
Having a successful strategic plan requires having an implementation (e.g., operational and tactical) plan. It is at those levels where the teamwork and change process is outlined and manifested to foster collaboration and communication to achieve success (e.g., Northwestern University (United States), University of Melbourne (Australia), Nanyang Technology University (Singapore)). According to Rogers (2003), implementing change and strategic plans requires committees/organizations who understand the existing practices, values, and needs of potential adopters.
Educational master plans (EMPs) are developed at many levels: national, regional, state, institutional, and area. An EMP provides leadership and stakeholders with a roadmap guiding the institution(s) towards their future goals. It provides the organization with a policy and planning framework to accommodate growth and help meet future needs (Kerr 1999). It is a dynamic document, typically reviewed and updated at regular intervals. Goals may include access, affordability, equity and quality, and efficient use and allocation of resources. The EMP also looks at social and economic growth and changes (e.g., demands, global change, demographics) and future challenges and opportunities. Priorities are then set and linked to financial support and needs.
A good EMP includes accountability measures to ensure students achieve the desired educational outcomes and post-graduation success. At the heart of the EMP process is strategic planning. Additionally, it provides the foundation for each department or school’s operational and tactical plans (see Figure 19.2). The EMP is where the foundation of learning technology control and security should emanate, allowing those who have established the plan an opportunity to analyze, design, develop, implement, and evaluate learning and information technology in pursuit of improved student outcomes. Both learning technology and information technology bring required capabilities and processes, meaning that both need to be involved in the planning process and prepared to work as a team to avoid being part of the 66% who fail to develop plans linked to institutional strategy.
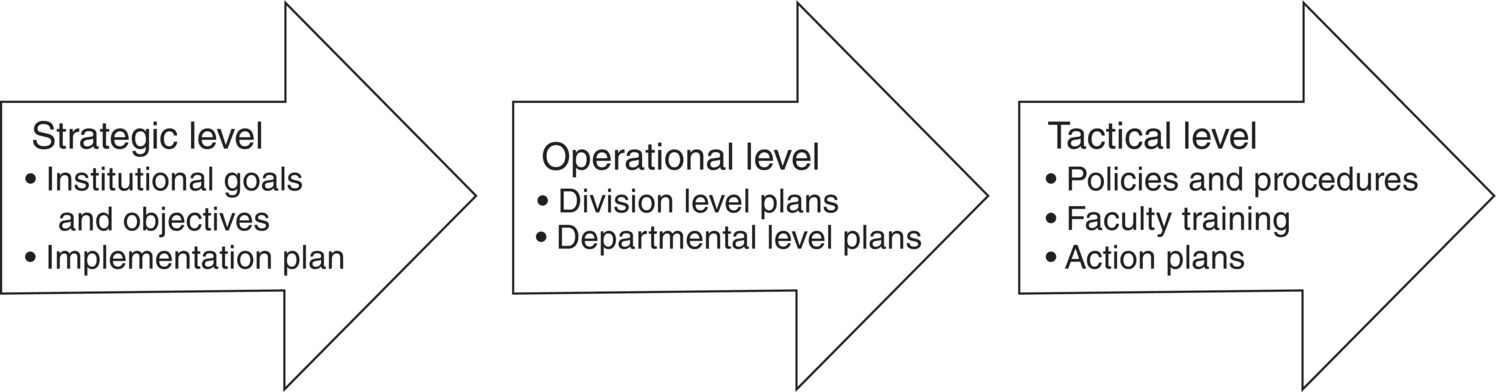
Figure 19.2 Planning levels.
19.3 Strategic Planning
Implementing a sound strategic planning process is critical to the success of higher education and the foundation of the EMP (Pisel 2008). According to Fain (2007), the vast majority of higher education institutions would be more successful if they used a systematic strategic planning process. The planning process is critical in enabling higher education leadership to develop and implement their institutional plan and work through the required change and adoption process (Hannan 2005). The strategic plan includes strategic goals and objectives to give general direction and perspective for organizing the plan along with specific terms for the parts of the plan requiring accountability and measurement. The strategic planning process provides the vision, direction, and goals for the institution. Most often, strategic level goals and objectives form the basis of the strategic plan at higher education institutions; this type of plan is usually developed with participatory input. Participatory input and teamwork helps higher education institutions improve the quality, relevance, and effectiveness of their teaching and research missions (Shawyun 2012).
The strategic plan should be attainable and addressed in phases for the best possible outcome. In this manner one action is completed before the next can be taken, plus finances, personnel, and equipment are aligned to allow efficient use and operation of limited resources. This gives the planning committee members the ability to look cross-functionally to see any conflicts that may arise during implementation. The plan should have short-, mid- and long-term deadlines specifying what will be accomplished and include completion targets. These deadlines provide the basis for implementation and structure for change management tied to operational and tactical planning and execution. Responsible parties should also be identified for each action. The strategic level of planning provides control, should drive resource allocation, and have its roots in the overall education vision.
19.4 Operational Planning
Operational planning takes place at the department organizational level. The best operational plans are the result of a well-defined strategic plan. Operational planning focuses on personnel, equipment, production, and processes. This allows each organization the ability to focus and execute its core educational function. The operational plan provides more detail and a clearer picture of how a team, section, or department will contribute to achieving the institution’s strategic goals.
Institutions that implement solid strategic planning processes provide clear goals and priorities for all stakeholders to understand. The lack of a coherent planning process tends to break the institution down into silos or factions, each with their separate plans and missions, fighting for their own critical resources. This kind of competition contributes to disjointed actions and an overall reduction of efficiency in operations. For example, instead of having a well-organized and advertised e-Learning program where technology is coordinated for both campus and online instruction, each area is advertising and trying to grow its own segment along with what it considers the best technology to accomplish the mission. This results in poor growth, miss-matched technologies, and areas competing against each other across the institution. The advantage for the institution using its strategic plan to allocate resources is that everyone knows in advance which activities have priority and which will be receiving the resources to implement parts of their operational plan.
19.5 Tactical Planning
Tactical planning is directed at the implementation of strategic and operational goals and objectives. It looks at the identified required resources and provides clear direction for the deployment and use of those resources. Tactical means “now”; it takes strategy to action. Tactical planning is developed annually and has three departmental components: (1) action plans, (2) measureable outcomes, and (3) education and training plans for department employees. This is where policies and procedures are necessary to successfully manage, plan, budget, and assess the department’s annual plan. This is also where educational and student support planning is completed. Implementing and following the tactical planning process takes time, work, and discipline. During this phase, flexibility and adaptability are important, providing feedback into the strategic plan as assessment facilitates ongoing success.
Understanding what an EMP is and how the planning processes work helps the entire organization understand how learning and information technology integrate with the higher education environment and is essential to the control and security of learning technologies. Technology planning and implementation works with the institution’s strategic goals and objectives to further the institution’s success. The lack of a plan or a failed implementation leads to institutions with a variety of potentially incompatible and hard-to-support information technology hardware and software, limited faculty development, and a lack of appropriate resource allocation. One or more of these conditions opens up the technology infrastructure to inadequate security implementation and a lack of appropriate assessment, therefore breaking down into a variety of entities vying for control of campus technology.
19.6 Technology
The current generation of “digital natives” (Prensky 2001) is more at ease with online, collaborative, and immersive computing environments due to the increased influence of digital pressures (e.g., Internet, social media, interactive games). The expanded use of distance learning and other learning technologies allows for more adaptive learning environments and resources as a focus in developing higher education strategy in broadening learner access to postsecondary and life-long education. Geographic boundaries and remote locations present few obstacles for most of these technologies, allowing globalized growth of higher education (Wildavsky 2012). Courses are being delivered around the world via computers, mobile devices, and two-way interactive video classrooms, both synchronously and asynchronously. These learning technologies are reshaping how higher education leadership looks to expand their educational reach and institutional revenue opportunities.
Not only are academic institutions from Western countries expanding their footprint into the Middle East and Asia, but also universities in China and India are making their mark on the global ranking tables, offering increased competition for Western institutions.
(Wildavsky 2012)
Increased use of learning technology in the traditional classroom is also changing how instruction is delivered and learning takes place. Institutional use in blended and online learning has increased in Africa with the expansion and development of cheaper and faster Internet access and policies (Carr 2013). Faculty eyes have been opened to the reality of engaging a wider variety of their students and in some cases flipping their classrooms, where the classroom dynamic is reversed (Millard 2012). Students get their lectures via technology outside of the academic environment and work through problems and discussions together in the classroom. Learning technology provides students with more opportunities to learn by doing (e.g., simulation, virtual environments, connecting students on campus and around the world). Because of changing and emerging technologies, technology-experienced younger faculty and the expansion of online teaching, faculty are adapting or having to adapt their classes to keep up.
Younger students and faculty are familiar with technology and willing to experiment, but sustainability and growth of learning technology in higher education requires commitment of time and money for continued success. Technology alone does not enhance pedagogy; successful integration is about how learning technology tools are used and integrated into the teaching and learning process (Georgina and Olson 2008). According to Moser (2007), many faculty lack technical and pedagogical competencies to successfully integrate learning technology into teaching. Additionally, time for higher education faculty is a scarce resource, with a variety of activities competing for their attention (e.g., research, publishing, teaching).
These new technologies also affect campus administration and staff. Marketing and fundraising campaigns are using social-networking tools to link with alumni and business partners. Human resources are implementing programs for course registration, paperless filing, and employee benefits in an attempt to save costs and reduce overheads. In addition, there is an increased need for support services, which include academic assistance (e.g., advising, mentoring, student support centers, counseling) and faculty and staff assistance (e.g., support centers, health, communication, human resources).
Arden Bement, director of the National Science Foundation, once said:
We are entering a second revolution in information technology, one that may well usher in a new technological age that will dwarf, in sheer transformational scope and power, anything we have yet experienced in the current information age.
(Bement 2007)
Although most institutions view the technology advances and changes as positive, they have realized this is a double-edged sword. Adoption of technology, specifically learning technology, must address a variety of barriers to its integration into higher education. Institutions need to plan strategically when addressing learning technology barriers and integrate the plan operationally and tactically to facilitate adoption while trying to avoid technological obsolescence, and all while protecting personnel data, hardware, and software (Moser 2007). This becomes especially significant where institutions are trying to be available at all times and from anywhere.
The technology plan provides the control and cornerstone for helping faculty and administration identify the right uses of technology, which technology to pursue and use, and establish the necessary professional development and support required to succeed. A potentially valuable tool to aid in the planning, adoption, and integration of learning technology in higher education is the RIPPLES model (Surry 2002; Surry, Ensminger, and Haab 2005). According to Jasinski (2007) it is important to consider all seven components of the model for planning and implementation.
The growth of learning and information technologies has “given rise to a generation of students who have never known life without a computer” (Glenn 2008, 18). Learning technologies will continue to expand and reach more people around the world who want an education. Institutions (e.g., administrators, faculty, and staff) will need to keep pace if they want to be part of the growth. To keep pace, learning and information technology must be strategically planned, aligned, and cohesively adopted and integrated.
19.7 Technology Plan: Control
Information and learning technology is a vital component in the support of teaching, learning, research, and administration in higher education. Higher education students, faculty, and staff drive the adoption of technology that supports all areas on their campuses; similar to how they have adopted technology in their personal lives. It becomes incumbent on the technology plan and committee to provide the control for learning technology across the institution. An institution can sometimes succeed without a strategically aligned technology plan, but only under strong leadership, access to resources, and strong alliances across the Institution. However, according to Grajek and Pirani (2012) the technology organizations that enjoyed the greatest success were those whose agendas and plans served the institution’s priorities.
Higher education’s expanded use of technology along with online course growth increases demand for more advanced technology services and capabilities. It takes an organization that is committed to teamwork and willing to listen, learn, and lead in the delivery of learning technology and information resources to succeed in growing and protecting the infrastructure. According to Hawkins and Oblinger (2005), higher education technology is interdependent and nonhierarchical, crosscutting and linking diverse groups, and requiring leaders to work jointly to define a technology strategy based on educational needs rather than cost.
One of the biggest issues with integrating technology is it can fail, leading to frustration for both faculty and students. Failing is inevitable, but part of learning. Additionally, much of the failure can be attributed to how it is organized and aligned strategically. Often technology integration fails when it is decentralized; when each school or department is responsible for their own technology integration and training (Howell, Williams, and Lindsay 2003). According to Meyer (2003) a successful plan should motivate people, improve productivity and security, and enable skill and learning development while considering the benefits and limitations of technologies.
Given the resource requirements of information and learning technology along with the continuous requirement to upgrade software and hardware, even institutions lacking an EMP or strategic plan often have a technology plan. The problem with having a technology plan without an EMP planning process is that the technology plan is created in a vacuum. Having a technology plan that is derived from and integrated with an EMP provides an institution with two significant advantages.
First, an integrated EMP and technology plan provides institutional leadership with a control mechanism to facilitate meeting their mission goals. On today’s campuses information and learning technology impacts or supports in some way almost everything at the institution, whether instruction, student services, facilities, operations, or administration. Whether it is academic or administrative computing, the purpose of the information technology department is to keep operations running securely and smoothly. Learning technology assists in engaging students in the learning process and supports faculty as they seek additional methods to promote active learning in their students. This makes it important for technology planners to work as a team and get to know and understand the campus plan, not just for current operations but also to provide a control capability for new and future demands for technology.
Secondly, the collaborative knowledge a good technology staff can bring to the planning process provides the campus and leadership with an ideal foundation from which to work and establish control over budgeting, purchasing, and integration. The key is to have the right blend of information technology and learning technology personnel working together. Successful integration of technology requires collaboration, networking, and team building (Grajek 2013). Having institutional technology staff participating in EMP planning discussions provides the planning committee with grounded estimates of cost, time needed for implementation, and training needs for new technology initiatives. Additionally, this staff can provide insight into technology issues regarding security and needed control as the plan unfolds.
19.8 Technology Committee: Control and Team
The technology committee serves as the institution’s primary focus for technology vision, policy recommendations, budgeting, and dissemination of information regarding technology. The committee becomes responsible for institutional control of learning and information technology. The committee as directed by the leadership and authority of the EMP takes control of establishing the technology plan and continually addressing information and learning technology as it relates to operations, security, teaching, and learning. As the primary institutional technology control mechanism the committee needs to have representation from across the institution, communicate with stakeholders, be empowered from leadership and have the desire to partner with all facets of the institution. As discussed earlier, Surry’s (2002) RIPPLES model assists the committee to be focused on resources, infrastructure, people, policies, learning, evaluation, and support. Each institution’s committee will be different due to the member make-up, planning process, finances, governance, leadership, and goals established by the institution and committee, but their defining success will be based on their teamwork (Grajek 2013; Weiss 2011).
According to Anderson and Perry (1994) and Armstrong, Simer, and Spaniol (2011), the technology planning committee must be established and attempt to represent the institution’s stakeholders. Similar to the military and corporate environment, the technology committee leader must be empowered by leadership, have a vision of how technology can be used to enhance the instructional and support processes, and know how technology can be beneficial for the staff (Elzarka 2012). There are no set rules on the number of members and designation of a specific leader (e.g., chief information officer (CIO) or learning technology officer (LTO)). It can be any faculty member, administrator, or staff member or even co-shared leaders with the vision on how learning and information technology can solve the needs of the institution, though it must fit the institutional governance structure. At some institutions with multiple campuses and technology requirements, the committee will need to establish guidelines for working with associated members from a distance and have an understanding of each campus’s unique capabilities and requirements. There may be a need to have one small central committee with members from each campus working with campus specific sub-committees.
Necessary for success are leadership (president, provost, or chancellor), empowered members from the faculty, finance, staff, library, information technology leadership (CIO or deputy), and learning technology leadership with at least a three-year commitment. The committee leadership can rotate every year or as necessary per leadership guidance. Members do not have to be technology experts, but having working technology knowledge makes the team a more effective liaison between users and learning and information technology organizations. The four key empowered leadership members are information technology leader, learning technology leader, senior administrative leader, and finance leader. Each brings key elements to the table: the information technology leader is responsible for the day-to-day operations and security of the infrastructure, the learning technology leader is responsible for understanding and assisting in the development of technology enhanced-learning and teaching strategies across the curriculum, the senior administrative leader represents the institution’s senior management and the EMP, and the finance leader is responsible for the budgeting process, especially as it relates to the EMP. The president/chancellor should appoint the chair(s) and provide guidance and oversight.
Although the technology committee may focus on using Surry’s 2002 RIPPLES model (i.e., resources, infrastructure, people, policies, learning, evaluation, support) for reviewing learning and information technology needs across the institution another good tool for administering its activities is the RACI (responsible, accountable, consulted and informed) matrix (Jacka and Keller 2009). The RACI charting or matrixing technique is used to identify activities or decisions, along with the individuals or groups involved in those activities or decisions. The key questions are what has to be done and who must do it? The RACI matrix allows technology committee stakeholders the ability to self-identify their interest matched to the level of their involvement. RACI is useful for translating the committee’s decisions into actions. Activities, deliverables, or tasks are broken down against the roles and coded according to the following:
- responsible: office or individual who bears responsibility to achieve the task
- accountable: office or individual who is accountable for the completion of the deliverable or task and the one who delegates the work to those responsible
- consulted: offices or individuals whose opinions are sought and a dialogue ensues (e.g., subject matter experts)
- informed: offices or individuals are kept informed of the outcome of the task or deliverable and any future revisions, normally just one-way communication.
By clearly articulating responsibilities with tasks, RACI offers a high likelihood stakeholders will buy in to the process and decrease the chances that other groups will complain about being left out of the discussions. The RACI matrix is not a one-time event but an ongoing lifecycle process. As an institution adapts and changes to meet new and changing processes and events the technology committee should modify and adapt to meet those changes (e.g., LMS change, MOOCs, online growth, security issues). The matrix provides a roadmap and available data to make the new and necessary changes through the responsible office (Dyason and Harle 2014).
The primary purpose of the technology committee (team) is to serve as the oversight committee on matters of information technology and learning technology, and to be responsible for setting the strategic technology direction and control for the institution. In order to achieve its stated purpose here are a few examples from US and European technology committees:
- Review, assess, update, and endorse the technology strategic plan based on the EMP.
- Prioritize technology purchases based on the strategic plan (team with learning technology, information technology and finance).
- Review and endorse technology annual budgets.
- Develop, review, and establish institution-wide technology standards and policies.
- Review and approve technology projects (categorize projects into near-, mid-, and far-range goals).
- Investigate new tools and capabilities.
- Establish technology training requirements.
- Campus focal point for distributing technology information to personnel.
- Assess the role of technology in all institutional areas.
- Oversight for technology projects (e.g., user involvement, roll-out plan, testing, agreements).
- Maintain relationships with other institution committees that deal with technology-related issues (e.g., faculty forum, finance, human resources, student records, extended studies, distance learning).
- If part of larger educational and diverse system, establish and maintain relationships dealing with technology.
- Look for economy of scale, share resources where applicable, share research, assessments, and technology successes.
- Most importantly, communicate what is going on to leadership, other committees, and stakeholders (e.g., faculty, staff, students, administration).
To be successful, the technology committee must remember their priority is student learning and institutional success (Kerr 1999). Their job is to establish control of the technology to facilitate the institution’s EMP. According to Rogers (2003), adoption and change takes engagement with people to be successful along with regular and effective communication. The challenge for the technology committee is to understand and encourage change, change management, and technology adoption. This takes dedication, a willingness to reach out to experts when required, and time to learn about the issues coming from all areas of the institution.
19.9 Technology Security
The traditional culture of higher education promotes the free exchange of ideas and research. As technology has evolved so has academia’s dependence on technology and the Internet. Having information readily available to employees and students provides institutions with a tool that can benefit their academic goals and mission. Information has now become the lifeblood of higher education institutions where administration, faculty, staff and students are just a click away from each other. Technology systems and networks link every school and department, and connect us with other institutions, research partners, and educational markets. This openness is what makes protecting higher education technology more difficult than the corporate environment (Bradbury 2013).
Sound technology security at higher education institutions is an essential element in protecting student, faculty, and staff personal information, financial and research data and partnerships, along with enhancing institutional reputation and ensuring compliance with regulations. Educational institutions have adopted technology and started sharing information via computers and networks in order to expand their reach and be cost-effective and more efficient.
One of the hardest things about technology security in higher education is balancing how much security is needed versus maintaining traditional academic freedom; openness and collegial sharing is required to foster research and advance learning. The weakest link in security is people (Mann 2008).
It is easy to understand the necessity of securing computer equipment, mainly because it is a tangible asset with associated costs and value. Understanding the cost to store, access and transmit data is a much more ambiguous and daunting task. The data itself contains value and in reality is more valuable than the equipment residing on campus. Since the institution is responsible for the security and integrity of its information, higher education management has to be proactive, ensuring data and assets are protected.
Since learning and information technology has become the backbone of current and future education it has become important for technology to function seamlessly for the institution as a whole. The challenges facing higher education institutions are complex in nature and vary by country, state, and institution. Higher education’s unique organizational structure of management, administration, faculty, and students has resulted in fragmented networks to handle the academic, research, and business operations. Couple this with academic openness, government regulations, varying amounts of planning, leadership direction, cost, current and emerging technologies, and training, it is no surprise that 15% of data breaches have happened at educational institutions (Bradbury 2013).
When compared to corporations or the defense industry this is a relatively small number of breaches. For any given institution, however, one breach is too many when matched with the potential cost of the loss of records, reputation, repairing and upgrading technology, training, and any lawsuit you face for the loss. It is better to be prepared to face a cyber attack, hacking event, or technology crime than clean up after the incident. In addition, the institution needs to have a plan in place ready to handle such incidents because the occurrence normally engages leadership, information technology, public relations, and legal affairs, a time-consuming and costly process. This should be part of the institution’s technology plan.
Cyber attacks in 2012 cost US companies an average of $8.9 million (Avery 2013). Cyber attacks against businesses of all sizes from both inside and outside the organization are common; businesses need to be prepared for potential threats. Lockheed, a worldwide corporation with 116,000 employees spread across 130 countries, currently runs the US cyber training range and provides cyber security for the Department of Homeland security. Lockheed itself has increasingly been the target of cyber attacks at a growing rate of 20% a year. Lockheed requires employees to take annual information assurance training and tests, log into computers with secure ID cards, and spends millions per year on security. In 2012, despite these efforts to manage risks related to the use, processing, storage, and transmission of data, they had a very sophisticated breach take place. Having gone through this experience and daily occurrences, Lockheed provides a few words of advice: determine what is most important and protect and build defenses and a team based on that.
There are increased attacks on higher education institutions because hackers know higher education institutions are repositories for valuable data, such as advanced health, technology, and science research. The potential availability of faculty, staff, and student personal information is a lucrative target as well. In July 2013, a cyber attack on the University of Delaware resulted in a breach of more than 74,000 individuals’ records, including names, addresses, university IDs, and social security numbers. In October 2013, a data breach at Melbourne University led to the public release of confidential employee records. According to McVicar (2013):
University IT staffs, already stretched thin by increasing workloads, are hard-pressed to keep up with every piece of malicious code and phishing attempt, or even to make sure that software is properly updated and patched.
Major universities are reporting anywhere from 90,000 to over 130,000 hacking attempts a day and growing yearly.
19.10 Higher Education Security Issues
For the majority of higher education institutions, unlike the corporate environment, the most challenging control and security issue they face today is the requirement for an open network where individuals can access it with multiple unmanaged devices while information technology tries to manage security and follow government regulatory compliance rules. The hardware and software threats institutions currently face include malware, phishing, hacking, spam, peer2peer, file sharing, social media and engineering, cyber espionage, mobile, and insider threats—this does not include human errors (e.g., accidental data leaks or misuse). A few of the threats (e.g., hacking, malware) came into being with the growth of the Internet. The rest come as a result of users adopting technologies faster than information technology professionals counter them with new security measures (Glenn 2008).
Besides the need for an open network, higher education technology includes a wide variety of infrastructure equipment, devices (e.g., desktops, laptops, tablets, smart phones), and operating systems (e.g., UNIX, Linux, Windows, Mac OS, iOS, Android, Blackberry). Additionally, due to cost many institutions have adopted open-source software or solutions for learning and content management systems (e.g., Moodle, Sakai, Canvas), and/or linked to companies like Google, who supply a wide variety of educational capabilities but leave security out of the institution’s control. All of these have unique vulnerabilities and capabilities, and a small technology staff often does not have the expertise to manage and secure every item. Additionally, there are open computer labs and kiosks readily available to students with technology knowledge ranging from neophyte to expert and in some cases allowing outsiders to access. The information technology staff must work to keep these online while keeping them secure from theft or malware. Compound this with daily hacker events where the school is being scanned for vulnerabilities from international sources that are smart enough and adept enough to bounce their work around the world, disguising their identities.
In the corporate environment the mission and people of the organization are focused towards a very specific common goal and vision. The leadership, decision-making, and information technology control and security is usually centralized and can be concentrated on training, educating, and protecting its personnel against cyber intrusion.
Higher education works in a more decentralized fashion (Grajek and Pirani 2012) where leadership and decision-making, along with learning and information technology, are responsible for a variety of loosely aligned coalitions. Research functions represent both outside and inside focused and funded operations, and each department or area often has its own agenda for research, outreach, and education. Faculty are trying to teach at the same time as they do research, publish, and mentor students, while administration works to cover daily operations for all those activities. In addition, leadership is trying to grow the institution and garner more dollars. Students, increasingly bringing their own devices (BYOD), are inside the network and have varying degrees of technology understanding and prowess. This myriad of operations in an institution make life hard for even a well-funded, organized, and forward-looking technology team. Managing this is a daunting task, especially if an institution lacks proper planning to help focus at least some of the needed technology energy. Without a comprehensive plan, there is a lack of technology control, and this degrades an institution’s ability to secure and avoid wasting learning and information technology infrastructure, resources, and capabilities (Weiss 2011; Green 2013).
Higher education must invest in a holistic technology plan linked to the EMP in order to build a robust enough network to defend against cyber attacks but also be open enough to collegial exchanges, research, and open-access student learning opportunities. A well-balanced technology committee with learning technology, information technology, senior institution, and financial leaders at the core provides the diversity needed but also the decision-making capability to meet the institution’s mission.
19.11 Securing Technology
The expanding technology use and global growth of education is increasing the demand for more innovative technology solutions. To facilitate the adoption of technology while avoiding disruption of critical operations, loss of intellectual property, loss of trust and reputation, and avoiding federal and state penalties, or worse yet, losing data that becomes a threat to national security, each institution needs a technology plan that addresses security.
Security and control of learning technology is not just a technical issue; similarly information technology security is too important to assign only to the chief information officer. It requires teamwork, leadership, stakeholder involvement, and communication to control and grow learning and information technology. Additionally, institutions need to think differently about technology by thinking more about tools, capabilities, and services (Grajek 2013). This new or updated mindset will traverse through the system and provide a better platform of understanding of technology as an internal and external institutional learning solution.
While teamwork is essential, and utilizing a governance structure that allows for input from all stakeholders is a must, sometimes hard, timely decisions need to be made swiftly. Technology leaders manage areas that rapidly change and therefore decisions are often needed quickly and authoritatively. Many technology proposals and decisions have opposing viewpoints that can stall implementation. An effective technology control structure acknowledges this and allows for the final call to be made by the appropriate technology leader.
The EMP is the groundwork that develops and builds the institution’s path forward in order to meet its aligned mission. The EMP is the result of a team that looked inside and outside the organization, aligned with stakeholders and provides a measure of effectiveness. Similarly, the technology strategic plan merges and integrates learning and information technology into the EMP path.
Leadership (president, chancellor, rector, principal) provides the goals, objectives, influence, and guidance for developing the plan and then implementing the institution’s EMP once completed. Leaders who are engaged provide a positive impact in the plan design and development process but more importantly their engagement during the implementation process is additionally required to influence change in culture and facilitate adoption of the plan. The higher education control agency—the technology committee—uses the EMP as the foundation to develop and maintain the technology plan. Leadership engagement provides the stimulus and backing for the technology committee’s success.
The technology committee makeup includes a chair selected by the president/chancellor with four key leaders plus stakeholders from across the institution. Its primary job is to define learning and information technology strategic direction and goals, verifying they are consistent with the institution’s strategic goals. The reason for having both information and learning technology leadership as part of the four key leaders is to promote teamwork across the institution, reduce fractured implementation, and provide both perspectives needed in the higher education plan.
The technology committee is not only involved with strategic planning but also becomes the focal point for information and learning technology governance across the institution, determining who makes or contributes to the process. They establish policies and standards, working across the institution and aligning them to the technology plan. They have to understand and verify that the institution is adhering to national, regional, and local regulations (e.g., the US Family Educational Rights and Privacy Act, the UK Data Protection Act, the Australian Privacy Act, other national, regional, and local data loss laws and regulations) or face stiff penalties for not protecting private data on their network.
The technology committee is also responsible for prioritizing technologies based on the strategic plan, funding requirements, and the strategic and tactical level implementation plans. According to Grajek and Pirani (2012) funding should be accomplished at the strategic level. The technology committee fulfills this responsibility using the technology strategic plan. Funding is based on the priority they establish to support technology infrastructure, training, personnel, digital resources, and staff development. By tying funding to strategic planning and decision-making, it becomes mission oriented and not just about acquiring the latest new technology trend. It establishes an institutional mindset and ownership for the control and security of the systems they use.
The technology committee establishes the basic research and assessment model for learning and information technology groups to implement. Each of the respective groups or units then focuses on its area of expertise to find, assess, and recommend technologies to the technology committee based on a near-, mid-, or long-term goal. Additionally, they recommend training for faculty development, student learning, and professional development for staff. This requires working as a team and having an understanding of the learning and information technology groups to facilitate collegial communication. Having relevant technology committee leaders facilitates this process provides a solid link for cross-organizational work and teaming.
19.12 Learning Technology Group
Learning technology is the study and ethical practice of facilitating learning and improving performance by creating, using, and managing appropriate technological processes and resources (Januszewski and Molenda 2008). As universities shift to deeper learner-centric immersive environments, technology becomes the environment for educators to provide learners with environments and tools to guide and assist them in finding answers to their questions. Learning technology therefore needs individuals experienced and educated in learning technologies to facilitate, recommend, and control technology-rich learning environments. This puts the learning technology group in the education business and not the computer or infrastructure businesses.
This unique group needs to understand how technology works and how to best implement what the institution owns in support of institutional learning and integration. The group provides analysis, design, development, implementation, evaluation, training, planning, and assistance across the institution for senior leaders (e.g., president, chancellor, deans), faculty, and students. Responsibility falls to them to work with entities to collect data and help facilitate planning and learning technology along with professional development to achieve the desired plan of action and achieve integration into the classroom and facilitate student learning. According to Januszewski and Molenda (2008) the learning technology group should also take responsibility for change management and diffusion to ensure stakeholders (e.g., students, faculty) accept, support, and use the final product. This group varies from institution to institution, based on size, geography, organizational and governance structure, and funding, and may range from a single support person to an entire department.
The learning technology group also guides faculty during the initial part of the design process in order to assist in implementing the most effective teaching strategies for online and/or classroom instruction. They provide nonevaluative feedback on classroom observations when needed and suggest appropriate technology to meet learning objectives and learner’s needs. In addition, they assure that required security measures are enforced to ensure continuous operation. They design, develop, and implement professional development related to teaching and learning technology to include the best practices for using technology to deliver instruction and facilitate learning. The implementation of professional development aids information technology in providing a more secure environment by increasing faculty, staff, and student technology fluency and security awareness.
As part of the institution control mechanism, the learning technology group researches, tests, and suggests learning technologies (e.g., learning and content management systems, learning lab setup, classrooms, other digital resources) for the institution’s technology committee and other learning organizations, including aligning with the committee’s near-, mid-, and long-term plans. They look at emerging technology (e.g., augmented reality, biometrics, MOOCs, multi-touch surfaces) researching and testing potential solutions that can enhance learning and potentially decrease costs (Grantham 2012). According to the US Department of Education (2013) the learning technology group should be continually monitoring, evaluating, and looking to improve the effectiveness of learning technology and its resources. Additionally, they assist the technology committee with establishing learning technology policy and standards.
The learning technology leader is a key member of the leadership team and a core member of the technology committee. They provide learning technology leadership in strategic planning for classroom and online learning focused on the control and integration aspect of the institution’s technology integration. They must work closely with peers from administration, deans, faculty, information technology, support services, finance, and the library.
The learning technology leader should be well grounded in learning technology theory and operations and have, at minimum, a working knowledge of information technology. They should strive to continue their own professional development through publication, presentations, and teaching based on president/chancellor guidance. Although not an information technology person, they should partner with information technology leadership to facilitate teamwork. Lastly, they need to understand change theory and be able to relate technology adoption to employees, faculty, staff, leaders, and administration. This position can significantly impact the successful control of learning technology by understanding and championing the best available learning technology that meets the EMP, technology plan, and faculty/student engagement.
19.13 Information Technology Group: The Security Organization
The information technology group is responsible for the security and continuous operations of the institution’s network infrastructure (wireless and wired), web, library and administrative services, computing, and databases. It is the first line of defense against cyber attacks, intrusions, or user error. It is responsible for the strategic planning, oversight, and direction (based in part on the learning technology committee’s strategic plan) of the institution’s infrastructure, resources, and services. Additionally, it provides critical technology support (e.g., helpdesk, training) across the institution and around the world for research and web. The remit is similar to that of the learning technology group, working with technology, but focused on the main goals of continuous operations and security. Users expect that like the electrical outlet on the wall, the technology infrastructure will simply work when their device is connected.
Unfortunately, according to Green’s Campus Computing Project (Green 2013) higher education information technology organizations have been historically understaffed. This is partly due to tight and shrinking budgets, competing with the private sector for quality individuals, and lack of training to meet diverse information technology requirements (Grajek 2013). To compensate, higher education institutions need to rethink, retrain, and reform their information technology groups to match the mission.
Based on the strategic technology plan, information technology groups work with academic, administrative, and research organizations to evaluate information technology requirements, capabilities, and requests. They are the experts on what and how the technology works and when it starts to fail they are proactive in fixing the problem or routing the needed capabilities to another viable source until it is working efficiently again. Their scope of operations is wide, including areas such as administrative systems and information management, networking, telecommunications, data centers, information security and privacy, technical aspects of the learning and content management systems, computing infrastructure, information technology services and sourcing accessible technology, customer service, and technology business acumen. They are responsible for analyzing, designing, and implementing professional development related to the above areas. In addition, they research, test, and suggest information technologies for the institution’s technology committee and other organizations, including aligning with the committee’s near-, mid-, and long-term plans.
While the learning technology team is looking at emerging technologies as a way to advance learning and control costs, information technology looks at emerging technology for potential threats, compatibility issues, ways to defend against cyber attacks, and control costs associated with securing and operating the network infrastructure.
Additionally, information technology assists the technology committee with establishing information technology policy and standards, including hardware and software standards for purchases, plus developing a hardware and software lifecycle plan. They review leadership policies and guidelines to establish information technology procedures (e.g., assess security risks, implementing a defense against the risk, operating procedures on how to defend and eradicate the problem) and best use guides for faculty, administration, and students. They are also responsible for establishing and implementing a technology-training plan and program to ensure every institution member using technology understands the risk and knows their responsibility when using technology.
Similar to the learning technology staff the information technology staff is made up of specialists in their fields: systems engineers, network managers, developers, database administrators, and information technology managers and architects. The majority concentrate on technical security and operations applications while others focus on specific information technology capabilities (e.g., database, web, theory, analytics, research). Additionally, they work with the library, administrative services, and the learning technology group to ensure they use integrated solutions and capabilities.
The information technology leader, similar to the learning technology leader, is a member of the leadership team and core technology committee. In most institutions they are the CIO. The CIO (Allison 2010) provides information technology leadership in strategic planning for security, infrastructure, technology services, policies, and operations to ensure the prioritization process is straightforward and meets the strategic guidelines established (Weiss 2011). They must work closely with peers from administration, faculty, learning technology, student services, finance, and the library. They provide oversight of the information technology group, ensuring budget and operations are focused on the strategic plan of the institution.
Higher education CIOs must work in an open computing environment (Allison 2010) but still adhere, as do corporate CIOs, to regulations, security, and operational necessities. According to Hawkins and Oblinger (2005), it is essential they are educated, understand the higher education operations, priorities, resources, and work environment, and have the ability to go beyond technology. CIOs (Weiss 2011) need to foster a culture of teamwork, leadership, quality service, and continuous improvement. Although not a learning technology person, they partner with learning technology leadership to include regular meetings, especially before attending the technology committee. Additionally, according to Weiss (2011), CIOs understand the adoption cycle and how to influence the change process for all levels of the institution.
19.14 Fostering Teamwork
There is a significant capacity for conflict between the information technology and learning technology groups, especially open access versus security, long-term infrastructure requirements versus immediate classroom needs, etc. At some institutions, learning technology is a subset of information technology, while at others they are distinct enterprises. Luke Waltzer (2009), Assistant Director for Educational Technology at the Bernard L. Schwartz Communication Institute at Baruch College, describes the difference by saying that:
Information technology makes our phones and networks and computers and smart boards work, and collects and protects student, staff, and faculty data so that we can get credits and get paid. This is crucial stuff. But it is not about teaching and learning. Learning technology is about pedagogy, about building community, about collaboration and helping each other imagine and realize teaching and learning goals with the assistance of technology.
Leaders and staff in both groups have differing experiences and expectations. In order to reduce potential conflict, institutions must establish clear governance and control over technology structures that encourage communication and teamwork between information technology and learning technology.
Since higher education technology opens a wide variety of opportunities for teaching, learning, and outreach, it additionally opens itself to abuse and attacks. Technology has become a standard component for many institutions, but for institutions to succeed with integrating technology it must be useable and secure. The enduring global recession and changes in technology in higher education mean the future is not business as usual and institutions must innovate (Grajek 2013). Efficiencies must be sought and best practices implemented. Information technology and learning technology must work more as a team and less as independent entities. It is only by connecting the two organizations within and across institutions they will be able to achieve their common strategic priorities (Grajek 2013). Although both groups operate independently they have overlap when it comes to technology adoption, security, and control. Whether through working groups, meetings, research, or projects the two technology groups can leverage a more collaborative philosophy to shape and share lessons, information, and services to benefit their institution.
It is time for higher education institutions to implement a planning process and governance structure that provides parity for learning technology and information technology. Learning technology can no longer be considered a subset of information technology, not in today’s world of expanding learning technology integration and cyber attacks. Learning technology and the technology committee provide the control the institution needs to meet the mission while information technology and technology committee provide the security.
19.15 Conclusion
Learning and information technology has moved from being discretional to essential across higher education institutions. The maintenance, expansion, funding, control, and security of learning and information technology remain an issue for higher education leadership. The cost to maintain and protect aging technology significantly increases support costs. Additionally, older technology does not meet the needs for today’s learning environment. Too often technology replacement and integration appears to be disjointed and unplanned; more often they are quick fixes for security or someone’s special project (Howell, Williams, and Lindsay 2003). Many of these learning and information technology challenges are bound together, but both require separate and focused expertise to solve the problem. For an institution to succeed at solving these challenges and looking to the future, it must have a solid plan and institutional wide teamwork.
The EMP provides the foundation for learning and information technology adoption, control, and security. The EMP is a systematic planning process made up of three distinct levels of planning, enabling higher education institutions to commit resources to accomplish its mission. This is where institutional technology control and security should originate in pursuit of student learning and outcomes. The key is to have the right blend of information technology and learning technology personnel working together with the understanding that learning technology is about pedagogy and learning goals while information technology is about infrastructure operations and securing the equipment and associated data.
While the two communities are different, they must work together in higher education where money is limited and staffs are small. This is accomplished through a technology planning committee representing the institution’s participants. The leader must be empowered with a vision on how technology enhances and assists learning and support processes. Although the committee needs representatives from across the institution, there needs to be a core of empowered representatives with authority and understanding of the EMP and leadership guidance. The core representatives should include a decision-maker from the leadership staff, finance, information technology, and learning technology to facilitate technology integration in a timely and efficient manner.
The technology committee serves as the institution’s technology oversight and funding committee, responsible for setting technology direction and the primary focus for dissemination of information and policy recommendation regarding technology. It provides equality for learning and information technology by being responsible for the control of institutional learning and information technology. It understands there must be a balance between control and security while maintaining the traditional open environment that fosters sharing and academic freedoms. The committee fulfills its responsibility through the technology strategic plan.
While the technology committee is the focal point for all institutional technology, it is much too small and lacks the ability to run daily technology operations. It must rely on two institutional groups for expertise, operations, training, research, and testing. The information technology group is responsible for the security and operations of the institution’s technology infrastructure and databases. They are the emergency and helpdesk team for solving information technology issues along with being the institution’s barrier against outside intrusions. The learning technology group is responsible for implementing, training, and supporting learning through the use of technology and instructional design. Their focus is not on fixing or securing equipment or infrastructure but on enhancing teaching and learning.
Learning technology personnel can no longer be enveloped within the broader notion of information technology. They need to be separate and focused on their area of expertise. Learning technology courses (e.g., online, blended, face-2-face, hybrid) require control, thought, time investment, and an understanding of student and faculty learning. Similarly, information technology, a client-service organization, must continue to work towards securing networks and data. To succeed there must be a close working relationship between the two organizations, but they must also remain separate and acknowledge each other’s rôles, strengths, and weaknesses while learning and assisting each other in today’s austere environment.
References
- Allen, I. Elaine and Jeff Seaman. 2014. “Grade Change – Tracking Online Education in the United States.” Eleventh Annual Babson Study. Newburyport, MA: Sloan Consortium.
- Allison, Debra H. 2010. “The Future CIO: Critical Skills and Competencies.” Research Bulletin 15. Boulder, CO: EDUCAUSE Center for Research. Accessed 3 September 2013: http://www.educause.edu/library/resources/future-cio-critical-skills-and-competencies.
- Anderson, Larry S. and John F. PerryJr. 1994. Technology Planning: Recipe for Success. Paper presented at the Annual Meeting of the Society for Technology and Teacher Education, Washington DC. Accessed 20 March 2013: http://www.nctp.com/tp.recipe.html.
- Armstrong, Scott, Lauren Simer, and Lee Spaniol. 2011. “Models of Technology Management at the Community College: The Role of the Chief Information Officer.” In Technology Management: New Directions for Community Colleges, Number 154, edited by Tod Treat: pp. 87–95. Hoboken, NJ: Jossey-Bass.
- Avery, Greg. 2013. “Hack attacks: Cyber spies hitting more companies.” Denver Business Journal. Accessed 5 August 2013: http://www.bizjournals.com/denver/print-edition/2013/06/14/hack-attacks-cyber-spies-hitting.html?page=all.
- Bement, Arden L. 2007. Blazing a Bold Trail of Education. Arlington, VA: National Science Foundation. Accessed 4 June 2013: http://www.nsf.gov/news/speeches/bement/07/alb070624_doe_scholars_prog.jsp.
- Bonk, Curtis J., Jack A. Cummings, Noriko Hara, Robert B. Fischler, and Sun Myung Lee. 1999. “A Ten Level Web Integration Continuum for Higher Education: New Resources, Partners, Courses, and Markets.” In Instructional Cognitive Impacts of Web-based Education, edited by Beverly Abbey: pp. 56–77. Hershey, PA: Idea Group Publishing. doi:10.4018/978-1-878289-59-9.ch004.
- Bradbury, Danny. 2013. “Information Security on Campus – Lesson from the US.” The Guardian. Accessed 12 September 2013: http://www.theguardian.com/media-network/partner-zone-infosecurity/information-security-higher-education-lessons-us.
- Brown, Phillip, Hugh Lauder, and David Ashton. 2008. Education, globalization and the knowledge economy: A Commentary by the Teaching and Learning Research Programme. London: Institute of Education. Accessed 28 February 2014: http://www.tlrp.org/pub/documents/globalisationcomm.pdf.
- Cao, Yingxia and Sut Sakchutchawan. 2011. “Online vs. Traditional MBA: An Empirical Study of Students’ Characteristics, Course Satisfaction, and Overall Success.” Journal of Human Resources and Adult Learning 7 2. Accessed 15 March 2014: http://www.hraljournal.com/Page/1%20Yingxia%20Cao.pdf.
- Carr, Tony. 2013. “e/merging Across Africa: Five Papers on the Use of Educational Technology in African Higher Education.” African Journal of Information Systems 5 3. Accessed 17 March 2014: http://digitalcommons.kennesaw.edu/cgi/viewcontent.cgi?article=1172&context=ajis.
- Dyason, Karin and Jonathan Harle. 2014. Research project management in African universities. Regional and Thematic Papers on Research Management. Cape Town: European Union’s ACP S&T Programme and Research Africa. Accessed 30 October 2015: https://www.acu.ac.uk/publication/download?id=536.
- Elzarka, Sammy. 2012. “Technology Use in Higher Education Instruction.” Claremont Graduate University Theses & Dissertations. Accessed 14 March 2014: http://scholarship.claremont.edu/cgi/viewcontent.cgi?article=1039&context=cgu_etd.
- Fain, Paul. 2007. “Vision for Excellence.” Chronicle of Higher Education 54 6: A26–A29. Accessed 20 May 2013: http://chronicle.com/article/Vision-for-Excellence/4138.
- Garrett, Richard. 2004. “The Real Story Behind the Failure of U.K. eUniversity.” Educause Quarterly 27 4. Accessed 25 March 2014: https://net.educause.edu/ir/library/pdf/eqm0440.pdf.
- Georgina, David A. and Myrna R. Olson. 2008. “Integration of technology in higher education: A review of faculty perceptions.” The Internet and Higher Education 11 1: 1–8. doi:10.1016/j.iheduc.2007.11.002. Accessed 17 March 2014: http://webpages.csus.edu/~sac43949/pdfs/faculty%20perceptions%20tech%20integration%20higher%20ed.pdf.
- Glazer, Louis and Donald Grimes. 2014. Michigan’s Transition to a Knowledge-Based Economy: Fifth Annual Progress Report. Ann Arbor, MI: Michigan Future Inc. Accessed 10 March 2015: http://www.michiganfuture.org/03/2014/michigans-transition-to-a-knowledge-based-economy-fifth-annual-progress-report/.
- Glenn, Marie. 2008. The future of higher education: How technology will shape learning. New York: The Economist Intelligence Unit. Accessed 6 June 2013: http://www.nmc.org/pdf/Future-of-Higher-Ed-(NMC).pdf.
- Grajek, Susan. 2013. “Top-Ten IT Issues 2013.” Educause Review May/June: 31–56. Accessed 3 March 2014: https://net.educause.edu/ir/library/pdf/ERM1333.pdf.
- Grajek, Susan and Judith A Pirani. 2012. “Top-Ten IT Issues 2012.” Educause Review May/June: 37–53. Accessed 18 June 2013: http://www.educause.edu/ero/article/top-ten-it-issues-2012.
- Grantham, Nick. 2012. “Five technologies that will shape our classrooms.” Edutopia Blog. Accessed 20 May 2013: http://www.edutopia.org/blog/five-future-education-technologies-nick-grantham.
- Green, Kenneth. 2013. Campus IT Officers Affirm the Instructional Integration of IT as Their Top Priority, Offer Mixed Reviews on IT Effectiveness and Outsourcing for Online Education. Encino, CA: Campus Computing Project. Accessed 25 September 2013: www.campuscomputing.net.
- Hannan, Andrew. 2005. “Innovating in higher education: contexts for change in learning technology.” British Journal of Educational Technology 36 6: 975–85. doi:10.1111/j.1467-8535.2005.00568.x.
- Hawkins, Brian L. and Diana G. Oblinger. 2005. “The Myth about CIOs, If We Could Just Find a Good CIO, These Problems would Go Away.” Educause Review January/February: 12–33. Accessed 28 February 2014: http://www.educause.edu/ero/article/myth-about-cios.
- Higher Ed CIO. 2011. Why Strategic Planning Fails. Accessed 25 March 2014: http://blog.thehigheredcio.com/2011/08/16/why-strategic-planning-fails/.
- Hinton, Karen E. 2012. A Practical Guide to Strategic Planning in Higher Education. Ann Arbor, MI: Society for College and University Planning. Accessed 25 March 2014: http://oira.cortland.edu/webpage/planningandassessmentresources/planningresources/SCPGuideonPlanning.pdf.
- Howell, Scott L., Peter B. Williams, and Nathan K. Lindsay. 2003. “Thirty-two Trends Affecting Distance Education: An Informed Foundation for Strategic Planning.” Online Journal of Distance Learning Administration 6 3. Accessed 17 March 2014: http://www.westga.edu/~distance/ojdla/fall63/howell63.html.
- Jacka, Mike and Paulette Keller. 2009. Business Process Mapping: Improving Customer Satisfaction. Oxford: Wiley. ISBN 0-470-44458-4.
- Januszewski, Alan and Michael Molenda. 2008. Educational Technology: A Definition with Commentary. New York: Taylor & Francis Group. ISBN-10: 080585861X.
- Jasinski, Marie. 2007. Innovate and integrate: embedding innovative practices. Canberra: Department of Education Science and Training. Accessed 8 June 2013: http://flexible-Learning.net.au/wp-content/uploads/Innovate_and_Integrate_Report1.pdf.
- Johnson, Larry, Samantha Adams, Malcolm Cummins, Victoria Estrada, Alex Freeman, and Holly Ludgate. 2013. NMC Horizon Report: 2013 Higher Education Edition. Austin, TX: The New Media Consortium. Accessed 3 November 2013: http://net.educause.edu/ir/library/pdf/hr2013.pdf.
- Johnson, Larry, Samantha Adams Becker, Victoria Estrada, and Alex Freeman. 2014. NMC Horizon Report: 2014 Higher Education Edition. Austin, TX: The New Media Consortium. Accessed 18 March 2014: http://www.nmc.org/pdf/2014-nmc-horizon-report-he-EN.pdf.
- Kerr, Clark. 1999. Testimony of Dr Clark Kerr. Joint Committee to Develop a Master Plan for Education: Kindergarten through University. Oakland, CA: University of California. Accessed 1 May 2013: http://www.ucop.edu/acadinit/mastplan/kerr082499.htm.
- MacGregor, Karen, 2013. “Cultural Imperialism? MOOCs make waves in higher education worldwide.” University World News. Accessed 22 September 2013: http://www.universityworldnews.com/article.php?story=20130920142318192.
- Mann, Ian. 2008. Hacking the Human: Social Engineering Techniques and Security Countermeasures. Aldershot: Gower. ISBN-10: 0566087731.
- Matthews, Tim, Gloria Pickar, and Tom Schneid. 2007. “e-Learning Risks: Why Universities Should NOT Go It Alone.” Online Journal of Distance Learning Administration 10 3. Accessed 26 March 2014: http://www.westga.edu/~distance/ojdla/fall103/matthews103.htm.
- McVicar, Brian. 2013. “Ferris State’s Online Security Breach: Experts say cyber attacks on higher education growing.” mLive. Accessed 22 August 2013: http://www.mlive.com/news/grand-rapids/index.ssf/2013/08/ferris_states_online_security.html.
- Meyer, Katrina A. 2003. “Quality in distance education: Focus on on-line learning.” ASHE-ERIC Higher Education Report 24 4: 67. ISBN 978-0-7879-6349-1. Accessed 15 March 2014: http://files.eric.ed.gov/fulltext/ED470042.pdf.
- Millard, Elizabeth. 2012. “5 Reasons Flipped Classrooms Work: Turning lectures into homework to boost student engagement and increase technology-fuelled creativity.” University Business. Accessed 20 October 2013: http://www.universitybusiness.com/article/5-reasons-flipped-classrooms-work.
- Moser, Franziska M. 2007. “Faculty Adoption of Technology.” Educause Quarterly 30 1. Accessed 15 March 2014: https://net.educause.edu/ir/library/pdf/EQM07111.pdf.
- Pisel, Kenneth P. 2008. “A Strategic Planning Process Model for Distance Education.” Online Journal of Distance Learning Administration 11 2. Accessed 20 July 2013: http://www.westga.edu/~distance/ojdla/summer112/pisel112.html.
- Prensky, Marc. 2001. “Digital Natives, Digital Immigrants Part 1.” On the Horizon 9 5: 1–6. doi:10.1108/10748120110424816.
- Rogers, Everett. 2003. Diffusion of Innovations, 5th ed. New York: Free Press. ISBN-10: 0743222091.
- Shawyun, Teay. 2012. Developing and Actioning Strategic Planning in Higher Education Institutions. Bangkok: Assumption University of Thailand Press. ISBN 978-974-615-051-4. Accessed 27 February 2014: http://www.academia.edu/1529149/Developing_and_Actioning_Strategic_Planning_in_Higher_Education_Institutions.
- Surry, Daniel W. 2002. “A Model for Integrating Instructional Technology into Higher Education. Paper presented at the annual meeting of the American Educational Research Association, April 2002, New Orleans, LA. Accessed 10 March 2015: https://sites.google.com/site/ripplesmodel/ripples-files/aera021.pdf?attredirects=0.
- Surry, Daniel W., David C. Ensminger, and Melissa Haab. 2005. “A model for integrating instructional technology into higher education.” British Journal of Educational Technology 36 2: 327–29. doi:10.1111/j.1467-8535.2005.00461.x.
- US Department of Education. 2013. Expanding Evidence Approaches for Learning in Digital World. Washington, DC: US Department of Education. Accessed 10 March 2015: tech.ed.gov/files/2013/02/Expanding-Evidence-Approaches.pdf.
- Waltzer, Luke. 2009. “Towards the Next Stage of EdTech at CUNY…” Cacophony: Communication Across the Curriculum. Accessed 27 September 2013: http://cac.ophony.org/2009/05/29/towards-the-next-stage-of-edtech-at-cuny/.
- Weiss, Meredith L. 2011. Technology Leadership: Today’s Higher Education CIO. ECAR Research Bulletin 11. Boulder, CO: EDUCAUSE Center for Research. Accessed 1 March 2014: https://net.educause.edu/ir/library/pdf/ERB1111.pdf.
- Wildavsky, Ben. 2012. The Great Brain Race: How Global Universities Are Reshaping the World. Princeton, NJ: Princeton University Press. ISBN 9780691154558.
- Woods, Dexter R. 2014. “Applying the Quality Matters (QM) Rubric to improve online business course materials.” Research in Higher Education Journal 23. Accessed 28 February 2014: http://www.aabri.com/manuscripts/131706.pdf.
