Chapter 14
Network Threats and Mitigation
THE FOLLOWING COMPTIA NETWORK+ EXAM OBJECTIVES ARE COVERED IN THIS CHAPTER:
✓ 3.3 Explain common scanning, monitoring, and patching processes and summarize their expected outputs
- Port scanning
- Patch management—Rollback
- Reviewing baselines
✓ 3.5 Identify policies and best practices
- Licensing restrictions
- International export controls
- Incident response policies
- System life cycle
- Asset disposal
✓ 4.1 Summarize the purposes of physical security devices
- Detection
- Motion detection
- Video surveillance
- Asset tracking tags
- Tamper detection
✓ 4.3 Given a scenario, secure a basic wireless network
- WPA
- WPA2
✓ 4.4 Summarize common networking attacks
- DoS
- Reflective
- Amplified
- Distributed
- Social engineering
- Insider threat
- Logic bomb
- Rogue access point
- Evil twin
- War-driving
- Phishing
- Ransomware
- DNS poisoning
- ARP poisoning
- Spoofing
- Deauthentication
- Brute force
- VLAN hopping
- Man-in-the-middle
- Exploits vs. vulnerabilities
✓ 4.5 Given a scenario, implement network device hardening
- Changing default credentials
- Avoiding common passwords
- Upgrading firmware
- Patching and updates
- File hashing
- Disabling unnecessary services
- Using secure protocols
- Generating new keys
- Disabling unused ports
- IP ports
- Device ports (physical and virtual)
✓ 4.6 Explain common mitigation techniques and their purposes
- Privileged user account
- File integrity monitoring
- Role separation
- Restricting access via ACLs
It’s true…you’re not paranoid if they really are out to get you. Although “they” probably aren’t after you personally; your network—no matter the size—is seriously vulnerable, so it’s wise to be very concerned about keeping it secure. Unfortunately, it’s also true that no matter how secure you think your network is, it’s a good bet that there are still some very real threats out there that could breach its security and totally cripple your infrastructure!
I’m not trying to scare you; it’s just that networks, by their very nature, are not secure environments. Think about it—the whole point of a having a network is to make resources available to people who aren’t at the same physical location as the network’s resources. Because of this, it follows that you’ve got to open access to those resources to users you may not be able to identify. One network administrator I know referred to a server running a much-maligned network operating system as “a perfectly secure server until you install the NIC.” You can see the dilemma here, right?
Okay, with all this doom and gloom, what’s a network administrator to do? Well, the first line of defense is to know about the types of threats out there because you can’t do anything to protect yourself from something you don’t know about. But once you understand the threats, you can begin to design defenses to combat bad guys lurking in the depths of cyberspace just waiting for an opportunity to strike.
I’m going to introduce you to some of the more common security threats and teach you about the ways to mitigate them. I’ll be honest—the information I’ll be giving you in this chapter is definitely not exhaustive. Securing computers and networks is a huge task and there are literally hundreds of books on this subject alone. If you want to learn more about security on a much deeper level (and get another powerful certification in the process), get your hands on the CompTIA Security+ Study Guide: Exam SY0-501 7th Edition by Emmett Dulaney and Chuck Easttom (Sybex 2018).
 |
To find Todd Lammle CompTIA videos and practice questions, please see www.lammle.com/network+. |
Recognizing Security Threats
I’m not trying to freak you out, but I’m not exaggerating the dangers to your network security either. Here’s an example: Recently, I hooked up a friend’s computer to a high-speed network connection from his phone company. He had antivirus software but no personal firewall in place yet, and before I could get that firewall set up (which usually takes about 10 minutes), 15 virus alerts popped up!
Although viruses are common threats that we hear about all the time, there are many other nasty things out there as well. Bad guys who create threats to a network generally have one of two purposes in mind: destruction or reconnaissance. They’re seeking to destroy data or deny access, and maybe even nick information that you definitely don’t want them to have. Some types of attacks can accomplish both, but they’re usually combinations of simpler forms. In the following sections, we’ll look at several common approaches that bad guys use to breach the security of our precious networks.
Denial of Service
A denial of service (DoS) attack does exactly what it sounds like it would do—it prevents users from accessing the network and/or its resources. Today, DoS attacks are commonly launched against a major company’s intranet and especially its websites. “Joe the Hacker” (formerly a plumber) thinks that if he can make a mess of, say, Microsoft’s or Amazon’s website, he’s done that company some serious damage. And you know what? He’s right!
Even though DoS attacks are nasty, strangely, hackers don’t respect other hackers who execute them because they’re really easy to deploy. It’s true—even a pesky little 10-year-old can execute one and bring you to your knees. (That’s just wrong!) This means that “real” bad guys have no respect for someone who uses DoS attacks, and they usually employ much more sophisticated methods of wreaking havoc on you instead. I guess it comes down to that “honor among thieves” thing. Still, know that even though a DoS-type attack won’t gain the guilty party any esteemed status among “real” hackers, it’s still not exactly a day at the beach to deal with.
Worse, DoS attacks come in a variety of flavors. Let’s talk about some of them now.
The Ping of Death
Ping is primarily used to see whether a computer is responding to IP requests. Usually, when you ping a remote host, what you’re really doing is sending four normal-sized Internet Control Message Protocol (ICMP) packets to the remote host to see if it’s available. But during a Ping of Death attack, a humongous ICMP packet is sent to the remote host victim, totally flooding the victim’s buffer and causing the system to reboot or helplessly hang there, drowning. It’s good to know that patches are available for most operating systems to prevent a Ping of Death attack from working.
Unreachable Gateway
An attacker can make a host’s default gateway unreachable; the end game is to get the host to change their gateway address to that of one controlled by the attacker to accomplish a man-in-the-middle attack.
- First, the attacker takes control of a secondary gateway available to the host, shown as G1 in Figure 14.1.
- The attacker, acting as the destination host, sends a TCP open packet to the acting source host.
- While a reply is in transit from the source host to the destination host through gateway G2, the attacker, spoofing as G2, sends an ICMP route redirect message to the source host.
- The source host will accept the route change control message as valid and thus change its routing table to route all traffic bound for the destination host through gateway G1.
- Now the attacker, acting as a man-in-the-middle host, will quietly read/modify and forward all traffic bound for the destination host to gateway G2.
Figure 14.1 Unreachable gateway

Distributed DoS (DDoS)
Denial of service attacks can be made more effective if they can be amplified by recruiting helpers in the attack process. In the following sections, some terms and concepts that apply to a distributed denial of service attack are explained.
Botnet
A botnet is a group of programs connected on the Internet for the purpose of performing a task in a coordinated manner. Some botnets, such as those created to maintain control of Internet Relay Chat (IRC) channels, are legal, while others are illegally created to foist a DDoS. An attacker can recruit and build a botnet to help amplify a DoS attack, as illustrated in Figure 14.2.
Figure 14.2 Botnet
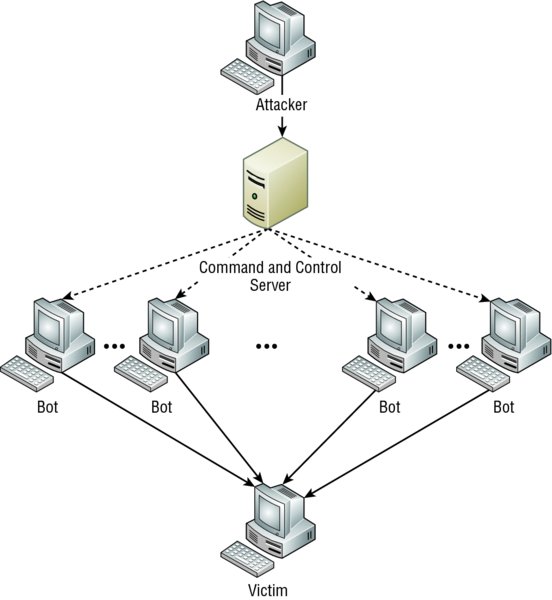
The steps in the process of building a botnet are as follows:
- A botnet operator sends out viruses or worms whose payloads are malicious applications, the bots, infecting ordinary users’ computers.
- The bots on the infected PCs log into a server called a command and control (C&C) server under the control of the attacker.
- At the appropriate time, the attacker, through the C&C server, sends a command to all bots to attack the victim at the same time, thereby significantly amplifying the effect of the attack.
Traffic Spike
One of the hallmarks of a DDoS attack is a major spike in traffic in the network as bots that have been recruited mount the attack. For this reason, any major spike in traffic should be regarded with suspicion. A network intrusion detection system (IDS) can recognize these traffic spikes and may be able to prevent them from growing larger or in some cases prevent the traffic in the first place.
Some smaller organizations that cannot afford some of the more pricy intrusion prevention systems (IPSs) or IDSs make use of features present on their load balancers. Many of these products include DDoS mitigation features such as the TCP SYN cookie option. It allows the load balancer to react when the number of SYN requests reaches a certain point. At that point, the device will start dropping requests when the SYN queue is full.
Coordinated Attack
Another unmistakable feature of a DDoS attack is the presence of a coordinated attack. As shown in Figure 14.2 and as just described in the section “Botnet,” to properly amplify the attack the bots must attack the victim at the same time. The coordination of the bots is orchestrated by the command and control server depicted in Figure 14.2. If all the bots can be instructed to attack at precisely the same second, the attack becomes much more dangerous to the victim.
Friendly/Unintentional DoS
An unintentional DoS attack (also referred to as attack from “friendly fire”) is not one that is not caused by malicious individuals; instead, it’s a spike in activity to a website or resource that overpowers its ability to respond. In many cases, it is the result of a relatively unknown URL suddenly being shared in a larger medium such as a popular TV or news show. For example, when Michael Jackson died, the amount of Twitter and Google traffic spiked so much that at first it was thought that an automated attack was under way.
Physical Attack
Physical attacks are those that cause hardware damage to a device. These attacks can be mitigated, but not eliminated, by preventing physical access to the device. Routers, switches, firewalls, servers, and other infrastructure devices should be locked away and protected by strong access controls. Otherwise, you may be confronted with a permanent DoS, covered in the next section.
Permanent DoS
A permanent DoS attack is one in which the device is damaged and must be replaced. It requires physical access to the device, or does it? Actually, it doesn’t! An attack called a phlashing denial of service (PDoS) attacks the firmware located in many systems. Using tools that fuzz (introduce errors) the firmware, attackers cause the device to be unusable. Another approach is to introduce a firmware image containing a Trojan or other types of malware.
Smurf
Smurfs are happy little blue creatures that like to sing and dance, but a Smurf attack is far more nefarious. It’s a version of a DoS attack that floods its victim with spoofed broadcast ping messages. I’ll talk about spoofing in more detail later; for now, understand that it basically involves stealing someone else’s IP address.
Here’s how it works: The bad guy spoofs the intended victim’s IP address and then sends a large number of pings (IP echo requests) to IP broadcast addresses. The receiving router responds by delivering the broadcast to all hosts in the subnet, and all the hosts respond with an IP echo reply—all of them at the same time. On a network with hundreds of hosts, this results in major network gridlock because all the machines are kept busy responding to each echo request. The situation is even worse if the routers have not been configured to keep these types of broadcasts confined to the local subnet (which thankfully they are by default!). Figure 14.3 shows a Smurf attack in progress.
Figure 14.3 Smurf attack in progress

Fortunately, Smurf attacks aren’t very common anymore because most routers are configured in a way that prevents them from forwarding broadcast packets to other networks. Plus, it’s really easy to configure routers and hosts so they won’t respond to ping requests directed toward broadcast addresses.
SYN Flood
A SYN flood is also a DoS attack that inundates the receiving machine with lots of packets that cause the victim to waste resources by holding connections open. In normal communications, a workstation that wants to open a Transmission Control Protocol/Internet Protocol (TCP/IP) communication with a server sends a TCP/IP packet with the SYN flag set to 1. The server automatically responds to the request, indicating that it’s ready to start communicating with a SYN-ACK. In the SYN flood, the attacker sends a SYN, the victim sends back a SYN-ACK, and the attacker leaves the victim waiting for the final ACK. While the server is waiting for the response, a small part of memory is reserved for it. As the SYNs continue to arrive, memory is gradually consumed.
Figure 14.4 shows an example of a simple DoS/SYN flood attack.
Figure 14.4 A simple DoS/SYN flood attack

You can see that the preyed-upon machine can’t respond to any other requests because its buffers are already overloaded, and it therefore rejects all packets requesting connections, even valid ones, which is the idea behind the attack. The good news is that patches to help guard against this type of attack are available for the various network operating systems today.
Stacheldraht
This is actually a mélange of techniques that translates from the German word for barbed wire. It basically incorporates Tribal Flood Network (TFN) techniques (certain botnet attacks including ICMP floods, SYN floods, UDP floods, and Smurf attacks) and adds a dash of encryption to the mix. The nightmare begins with a huge invasion at the root level, followed with a DoS attack finale.
Reflective/Amplified Attacks
Reflected or amplified attacks increase the effectiveness of a DoS attack. Two of the more effective of these types of attacks involve leveraging two functions that almost all networks use, DNS and NTP. In the next two sections these attacks are described.
DNS
A DNS amplification attack is a form of reflection attack in that the attacker delivers traffic to the victim by reflecting it off a third party. Reflection conceals the source of the attack. It relies on the exploitation of publicly accessible open DNS servers to deluge victims with DNS response traffic.
The attacker sends a small DNS message using the victim’s IP address as the source to an open resolver. The type of request used returns all known information about the DNS zone, which allows for the maximum level of response amplification directed to the victim’s server. The attack is magnified by recruiting a botnet to send the small messages to a large list of open resolvers (DNS servers). The response from the DNS server overwhelms the victim, as shown in Figure 14.5.
Figure 14.5 DNS amplification attack

NTP
While NTP refection attacks use the same process of recruiting bots to aid the attack, the attacks are not reflected off DNS servers; they are instead reflected off Network Time Protocol (NTP) servers. These servers are used to maintain time synchronization between devices in a network.
The attacker (and his bots) sends a small spoofed 8-byte UDP packet to vulnerable NTP servers that requests a large amount of data (megabytes worth of traffic) be sent to the DDoS’s target IP address. The attackers use the monlist command, a remote command in older versions of NTP, that sends the requester a list of the last 600 hosts who have connected to that server. This attack can be prevented by using at least NTP version 4.2.7 (which was released in 2010).
ARP Cache Poisoning
ARP cache poisoning is usually a part of a man-in-the middle attack. The ARP cache contains IP address to MAC address mappings that a device has learned through the ARP process. One of the ways this cache can be poisoned is by pinging a device with a spoofed IP address. In this way, an attacker can force the victim to insert an incorrect IP address to MAC address mapping into its ARP cache. If the attacker can accomplish this with two computers having a conversation, they can effectively be placed in the middle of the transmission. After the ARP cache is poisoned on both machines, they will be sending data packets to the attacker, all the while thinking they are sending them to the other member of the conversation.
Packet/Protocol Abuse
After an attacker has broken into the system, attained access, and escalated their privileges, it is important for them to maintain their authority on the system so they can access it at a later time. They could put an operating system backdoor on the target, but in some cases the firewall on the victim may not allow outgoing TCP connections.
One of the ways in which a hacker can get traffic through a firewall that would typically not be allowed is by concealing one protocol within another, which is a form of tunneling. TCP can be encapsulated into either DNS or ICMP, thereby bypassing the firewall restrictions.
An example of this is using a program called Iodine to encapsulate IP traffic in DNS packets. Once the DNS packets reach the local DNS server, they are forwarded to a second machine running Iodine that de-encapsulates the packets and sends them on to the hacker. The DNS traffic is allowed by the firewall and is able to reach the client. In this way, the attacker is able to communicate with the victim machine. This process is illustrated in Figure 14.6.
Figure 14.6 IP4 packets tunneled in DNS

Spoofing
IP spoofing is the process of changing a source IP address so that one computer appears to be a different computer. It’s usually done to get traffic through a firewall that would normally not be allowed. It may also be used to access a server to which the hacker would normally be disallowed access by their IP address.
While IP spoofing may be the most well-known type of spoofing, it is not the only type used by hackers. The following forms of this subterfuge also exist:
- ARP spoofing (discussed earlier in the section “ARP Cache Poisoning”).
- Referrer spoofing, in which the referrer header of an HTTP packet is changed to reflect an allowed referral page, which some sites require for access.
- Email spoofing, in which the “from” field is changed to hide the true origin of an email. In most cases this is to conceal the identity of an email spammer.
Brute Force
A brute force attack is a form of password cracking. The attacker attempts every possible combination of numbers and letters that could be in a password. Theoretically, given enough time and processing power, any password can be cracked. When long, complex passwords are used, however, it can take years.
Setting an account lockout policy is the simplest mitigation technique to defeat brute force attacks. With such a policy applied, the account becomes locked after a set number of failed attempts.
Session Hijacking
Session hijacking attacks attempt to take over a user’s session with a secure server after the user has been authenticated. This can be done in the following ways:
Session Fixation The attacker sets the session ID ahead of time by sending a link to the victim with the ID preset. When the user connects, the attacker waits for the authentication to complete and takes over the session by disconnecting the user and using the ID to reconnect.
Session Sidejacking The attacker uses a sniffer to steal a session cookie from the user. Alternately, if the attacker has physical access to the user’s machine, they can steal the session key from memory.
Cross-Site Scripting The attacker uses the user’s computer to run code on the site that may allow him to obtain the cookie. The attacker does this by putting malware on the user’s computer; the malware runs the code on the site after the user authenticates to the site.
VLAN Hopping
VLANs, or virtual LANs, are Layer 2 subdivisions of the ports in a single switch. A VLAN may also span multiple switches. When devices are segregated into VLANs, access control lists (ACLs) can be used in a router to control access between VLANs in the same way it is done between real LANs. When VLANs span switches, the connection between the switches is called a trunk link, and it carries the traffic of multiple VLANs. Trunk links are also used for the connection from the switch to the router.
A VLAN hopping attack results in traffic from one VLAN being sent to the wrong VLAN. Normally, this is prevented by the trunking protocol placing a VLAN tag in the packet to identify the VLAN to which the traffic belongs. The attacker can circumvent this by a process called double tagging, which is placing a fake VLAN tag into the packet along with the real tag. When the frame goes through multiple switches, the real tag is taken off by the first switch, leaving the fake tag. When the frame reaches the second switch, the fake tag is read and the frame is sent to the VLAN to which the hacker intended the frame to go. This process is shown in Figure 14.7.
Figure 14.7 VLAN hopping

Authentication Issues
Since the process of authenticating a user or a device forms the basis for securing most resources, authentication issues can lead to improper access, stolen data, and a whole host of other problems. In the following sections, we’ll look at some common authentication issues.
TACACS/RADIUS Misconfiguration
Terminal Access Controller Access-Control System Plus (TACACS+) and Remote Access Dial-In User Service (RADIUS) are both examples of authentication, authorization, and accounting (AAA) servers that verify the identity of, grant access to, and track the actions of users. Misconfiguration of these devices can result in an inability of users and devices to connect to the access devices that are clients of the AAA server (switches, WAPs, dial-up servers, VPN servers). Some of the most common mistakes that result in this situation prevent communication between the AAA server and the AAA client. When this happens, check the following:
- Verify the port numbers. Even if standard port numbers for these services have been selected, that doesn’t mean the product you are using uses those port numbers. Make sure the client and server are using the correct port numbers.
- Check to see if there is a mismatch in the pre-shared key between the client and the server.
When the problem is an issue between the supplicant (user or device requesting access) and the authenticating server (switch, WAP, dial-up server), check the following:
- Verify that the AAA method configured on the supplicant lists the appropriate RADIUS or TACACS+ server group.
- Verify that the authentication port number matches the configured port number.
- Verify that the user is configured on the AAA server (user account).
Default Passwords/Settings
All network devices are configured with default administrator accounts and their default passwords. These accounts should be disabled and renamed if possible. At the very least, the passwords for these accounts should be changed from the default because they are well known, available in documentation that comes with the product, and also widely available on the Internet.
Viruses
Viruses with catchy names like Chernobyl, Michelangelo, Melissa, I Love You, and Love Bug are probably the best-known threats to your computer’s security because they get a lot of media coverage as they proliferate and cause tons of damage to legions of people. In their simplest form, viruses are basically little programs that cause a variety of very bad things to happen on your computer, ranging from merely annoying to totally devastating. They can display a message, delete files, or even send huge amounts of meaningless data over a network to block legitimate messages. A key trait of viruses is that they can’t replicate themselves to other computers or systems without a user doing something like opening an executable attachment in an email to propagate them. Figure 14.8 shows how fast a virus can spread through an email system.
Figure 14.8 An email virus spreading rapidly

There are several different kinds of viruses, but the most popular ones are file viruses, macro (data file) viruses, and boot-sector viruses. Each type differs slightly in the way it works and how it infects your system. Predictably, many viruses attack popular applications like Microsoft Word, Excel, and PowerPoint because those programs are easy to use so it’s easy to create a virus for them. Unlike with DoS attacks, writing a unique virus is considered a programming challenge, so the scoundrel who’s able to come up with it not only gains respect from the hacking community but also gets to bask in the glow of the media frenzy that results from their creation and relish their 15 minutes of fame. This is also a big reason why viruses are becoming more and more complex and harder to eliminate.
Logic Bomb
A logic bomb is a type of malware that executes when a particular event takes place. For example, that event could be a time of day or a specific date or it could be the first time you open notepad.exe. Some logic bombs execute when forensics are being undertaken, and in that case the bomb might delete all digital evidence.
Ransomware
Ransomware is a class of malware that prevents or limits users from accessing their information or systems. In many cases the data is encrypted and the decryption key is only made available to the user when the ransom has been paid.
Effect of Malware on the Network
Malicious software (or malware) is a term that describes any software that harms a computer, deletes data, or takes actions the user did not authorize. There is a wide array of malware types, including ones you have probably heard of, like viruses. Some types of malware require the assistance of a user to spread, while others do not.
A worm is a type of malware that can spread without the assistance of the user. A worm is a small program that, like a virus, is used to deliver a payload. One way to help mitigate the effects of worms is to place limits on sharing, writing, and executing programs. However, the real solution is to deploy antivirus and anti-malware software to all devices in the network. This software is designed to identify viruses, Trojans, and worms and delete them, or at least quarantine them until they can be removed.
File Viruses
A file virus attacks executable application and system program files like those with filenames ending in .com, .exe, and .dll. These viruses do their damage by replacing some or all of the target program’s code with their own. Only when the compromised file is executed can the virus do its dirty work. First, it loads itself into memory and waits to infect other executables, propagating its destructive effects throughout a system or network. A couple of well-known file viruses are Jerusalem and Nimda, the latter of which is actually an Internet worm that infects common Windows files and other files with filename extensions like .html, .htm, and .asp.
 |
Don’t fall into the trap of thinking that just because you have a Mac, you don’t need to worry about viruses. It’s a common misconception that Mac operating systems are immune to viruses, but they’re not. Today’s Macs are really BSD Unix machines with a couple of proprietary programs running on top that provide users with a slick interface. And although it’s true that more sophisticated programming skills are required to write viruses for Mac, BSD Unix, and Linux operating systems than for DOS-based operating systems like Windows, all operating systems are vulnerable to attacks. True, it’s a lot easier for a bad guy to write malicious code for Windows machines, but the real reason few programmers spend their time creating viruses for Sun workstations and Macs is that there aren’t nearly as many people using them. On the other hand, Windows machines are everywhere, so viruses written for them will clearly infect multitudes, giving bad guys who want to infect as many computers as possible a lot more bang for their evil programming buck! |
Macro Viruses
A macro is basically a script of commonly enacted commands used to automatically carry out tasks without requiring a user to initiate them. Some popular programs even give you the option of creating your own, personal scripts to perform tasks you do repeatedly in a single step instead of having to enter the individual commands one by one.
Similar to this, a macro virus uses something known as the Visual Basic macro-scripting language to perform nasty things in data files created with programs like those in the Microsoft Office Suite. Because macros are so easy to write, they’re really common and usually fairly harmless, but they can be super annoying! People frequently find them infecting the files they’re working on in Microsoft Word and PowerPoint. Suddenly you can’t save the file even though the Save function is working, or you can’t open a new document, only a template. As I said, these viruses won’t crash your system, but they can ruin your day. Cap and Cap A are examples of macro viruses.
Boot-Sector Viruses
Boot-sector viruses work their way into the master boot record that’s essentially the ground-zero sector on your hard disk where applications aren’t supposed to live. When a computer boots up, it checks this area to find a pointer for its operating system. Boot-sector viruses overwrite your boot sector, making it appear as if there’s no pointer to your operating system. You know you’ve got this type of virus when you power up the computer and get a Missing Operating System or Hard Disk Not Found error message. Monkey B, Michelangelo, Stoned, and Stealth Boot are a few examples of boot-sector viruses.
Multipartite Viruses
A multipartite virus is one that affects both the boot sector and files on your computer, making such a virus particularly dangerous and exasperatingly difficult to remove. Figure 14.9 gives you an idea of how a multipartite virus works. You can see that it is attacking the boot sector, memory, and the disk at once.
Figure 14.9 Multipartite virus

Anthrax and Tequila are both multipartite viruses. These viruses are so nasty that you might end up reformatting your computer if you get one. The Anthrax virus, however, was more of a hoax then a real virus; what is really interesting about the Tequila virus is that it does nothing until the next reboot—it was no hoax!
Although many software companies can handle these, the best way to save your computer from a complete overhaul is to make sure you do not get a virus in the first place by using a good virus scan program as well as Windows Defender.
 |
Some viruses infect your system through something known as a Trojan horse. Troy was successfully invaded by troops hidden inside a giant horse; a Trojan virus hides within other programs and is launched when the program it’s lurking in starts up. Often viruses come as attachments to emails with double filename extensions to hide the true extension. Dmsetup.exe and love-letter-for-you .txt.vbs are examples of viruses. Displaying filename extensions for known file types can help spot naming tricks like these, but they make up only a short list of the viruses out there. For a more complete inventory, see your antivirus software manufacturer’s website. |
Zero-Day Attacks
Antivirus software uses definition files that identify known malware. These files must be updated frequently, but the update process can usually be automated so that it requires no help from the user. If a new virus is created that has not yet been identified in the list, you will not be protected until the virus definition is added and the new definition file is downloaded. This condition is known as a zero-day attack because it is the first day the virus has been released and therefore no known fix exists. This term may also be applied to an operating system bug that has not been corrected.
Insider Threat/Malicious Employee
It is often said that an organization has the most to fear from its own employees. They have already completed two phases of the hacking process, that is, discovery and penetration. They are already inside your network and probably have learned quite a bit about the network just doing their job.
The first step to mitigating damage that may be caused by disgruntled or malicious employees is to adhere to the principle of least privilege. This concept prescribes that users should be given access only to resources required to do their job.
Another principle that should be followed is called separation of duties. It calls for breaking up sensitive operations into two parts and having different users perform each part. This means there would have to be collusion between the two to take advantage of the process, which is not likely to occur.
Finally, all network access should be taken from a user who has been terminated before they have a chance to access the network.
Vulnerabilities
While malware certainly presents an ongoing danger to your network, it is not the only concern of the security professional. In the following sections, I’ll cover some other issues.
Exploits vs. Vulnerabilities
A vulnerability is the absence of a countermeasure or a weakness in a countermeasure that is in place. Vulnerabilities can occur in software, hardware, or personnel. An example of a vulnerability is unrestricted access to a folder on a computer. Most organizations implement a vulnerability assessment to identify vulnerabilities.
An exploit occurs when a threat agent takes advantage of a vulnerability and uses it to advance an attack.
Unnecessary Running Services
Services that are not required to be running on a system should be disabled. Running services present an additional attack surface to the hacker. Once they identify the running services on a machine, they will research all the vulnerabilities presented by those services and attempt to use them to compromise the target.
Open Ports
In the same way that unnecessary services present attack options, so do open ports. Software port numbers are used to identify protocols and services and serve as a connection point to a service on a target machine. Port scanners can be used to identify the ports that are open on all machines in a network. An open port means the device is listening on that port number and is willing to make a connection using that port. Unused ports should be shut down.
Unpatched/Legacy Systems
Systems that use older or legacy operating systems and applications may lack the security required in today’s networks. These devices may require special protection, such as placing them in a secure VLAN or installing host-based IPSs.
Even modern operating systems and applications will not be secure if they are not maintained by applying updates and security patches as they are released. A formal, and preferably automated, process should be set up to ensure that this maintenance is ongoing.
Unencrypted Channels
If it isn’t clear to you by now, in any situation where sensitive data is being transmitted, attention should be given to the type of channel across which the data is traveling. When no other method is available, IPSec is a Network layer protocol suite that can be used to provide end-to-end protection of any data that resides above the Network layer.
Many protocols provide the ability to control access through authentication. However, while some protect the confidentiality of the process by hiding the credentials as they are exchanged, others do not. For example, Telnet (a protocol used for remote command-line management of devices) transmits credentials in clear text; Secure Shell (SSH) does not.
Another example is Password Authentication Protocol (PAP), one of two authentication options offered when a PPP connection is being set up. PAP transmits credentials in clear text, while Challenge-Handshake Authentication Protocol (CHAP), the other option, uses a process that never sends the credential across the network. You should never use a protocol that transmits credentials in clear text.
TEMPEST/RF Emanation
Spying on information systems can also be accomplished by capturing and analyzing leaking emanations of things like radio or electrical signals, sounds, and vibrations. TEMPEST is a National Security Agency specification and NATO certification that addresses methods of spying used and how to protect against them. Distance, shielding, filtering, and masking are used to protect equipment from spying. The TEMPEST standards are used to describe the level of protection a system is certified to provide.
Malicious Users
Damaging activity on your network can come from both inside and outside the network. In the following sections, we’ll look at the two types of malicious users you will encounter and an operation often performed in the execution of their mayhem.
Trusted Users
While we would like to think that all of our own people can be trusted, that’s often not the case. Even your “trusted” users can go to the dark side with the proper motivation. The following are among the motives that can turn a trusted user into a malicious user:
- Perceived slight by the company
- Jealousy of other employees
- Monetary reward
The real danger presented by a trusted employee who turns malicious is that the employee is already inside your network and probably knows quite a bit about it. This is the reason for following the principle of least privilege, which prescribes that users be given access only to resources required to do their job.
Untrusted Users
While it may take untrusted users or users outside your network a bit longer to make their way into your network, once they get there they will probably have a significantly higher level of skill than a disgruntled employee has. Discovering and penetrating your network from outside takes some skill. The best mitigation for these attacks is a combination of perimeter defense (keep them out) and strong access control at the point of resource access (prevent access to devices holding information). A multilayer approach works best.
Packet Sniffing
One of the basic tools a hacker will possess is a protocol analyzer, or packet sniffer. These devices capture raw packets off the network for analysis. Normally, a device will only process packets that are destined for itself, but this software places the network interface of the hacker’s device in promiscuous mode, which means it captures all packets on the network.
This software can also be used legitimately to examine your network traffic for things that should not be there. Figure 14.10 shows an example of the output from the packet analyzer Wireshark. In the output, it can be seen that packet 4 failed a Frame Check Sequence, which would require it to be sent again. While the list of packets captured is displayed, you can click on any packet and examine it in detail. If the data is in clear text, you will be able to read it.
Figure 14.10 Wireshark

Buffer Overflow
When programs execute, they write commands into memory, or to a buffer. Well-written programs allow a certain location and/or amount of memory space for these commands to execute. If a hacker is able to inject a command that overflows the amount of memory allocated and the command is able to execute with the proper security privileges, the hacker could execute commands that would not normally be allowed. They may be able to take control of the machine and create havoc.
A number of well-known exploits, such as the Code Red worm, employed buffer overflows to create their mayhem. The way to prevent buffer overflows is to include input validation into programs to mitigate the possibility of them occurring.
DNS Poisoning
DNS clients send requests for name to IP address resolution (called queries) to a DNS server. The search for the IP address that goes with a computer or domain name usually starts with a local DNS server that is not authoritative for the DNS domain in which the requested computer or website resides. When this occurs, the local DNS server makes a request of the DNS server that does hold the record in question. After the local DNS server receives the answer, it returns it to the local DNS client. After this, the local DNS server maintains that record in its DNS cache for a period called the Time to Live (TTL), which is usually an hour but can vary.
In a DNS cache poisoning attack, the attacker attempts to refresh or update that record when it expires with a different address than the correct address. If the attacker can convince the DNS server to accept this refresh, the local DNS server will then be responding to client requests for that computer with the address inserted by the attacker. Typically, the address they now receive is for a fake website that appears to look in every way like the site the client is requesting. The hacker can then harvest all the name and password combinations entered on his fake site.
To prevent this type of attack, the DNS servers should be limited in the updates they accept. In most DNS software, you can restrict the DNS servers from which a server will accept updates. This can help prevent the server from accepting these false updates.
Wireless Threats
The proliferation of wireless communication has introduced a number of security challenges that are unique to the wireless environment. Some of these threats even take advantage of the security measures that have been created to protect wireless networks and hosts. Wireless threats such as WEP and WPA cracking (discussed in the following sections) remind us that network attackers never stop evolving their methods and that constant review and adaptation of security measures are required to maintain security in the network.
War Driving
War driving is one of the oldest wireless threats and perhaps one of the easiest to discourage (although you can’t defeat it if the hacker is determined). The attacker simply drives around with a high-powered antenna connected to a wireless laptop scanning for networks. The networks will be listed by network name (SSID) in the wireless client software, and depending on the software, the channel and security measures in use will also be displayed.
If the network is not secured, the attacker can connect to it. This is not just a matter of stealing bandwidth for Internet access. Once connected, the attacker may be able to proceed on into your wired network as well. They can then attempt other attacks, such as port scanning and peer-to-peer attacks. The point is that they have completed the first step in the hacking process, which is penetration.
War driving cannot be entirely prevented, but you can make it harder for an attacker. One of the simplest things you can do is limit the transmission power on the access point (AP) such that the signal does not go any further than required! Additionally, if you set the access point to not broadcast the SSID, the name of the network will not appear in the display when they scan for networks. This means that to connect, they will have to know the SSID and create a wireless profile specifying it.
If an attacker is determined, however, they can learn the SSID by using a wireless protocol analyzer or sniffer to capture the raw packets. This is something you cannot prevent without turning off the AP. When you set the AP to not broadcast the SSID, it will remove the SSID from packets called beacons (these are the packets that populate the display when you scan for networks), but the SSID will still be present in many other packet types.
In most cases, hiding the SSID will be sufficient because if an attacker doesn’t see your network when scanning, they probably won’t be motivated to use the sniffer.
War Chalking
War chalking is really just an extension of war driving. The hacker simply writes the SSID and security employed on the sidewalk or wall somewhere near your facility, sort of like advertising “here’s a wireless network” to anyone who recognizes that code. Most of this type of activity has moved online where websites have sprung up that allow hackers to post and share these networks on maps indicating their location.
WEP Cracking
Wired Equivalent Privacy (WEP) is a security protocol created in the early years of 802.11 development that was designed to both authenticate users and encrypt the wireless data they transmitted. It uses the RC4 algorithm in the encryption process. Soon after its adoption as a security measure, it was discovered that due to a weakness in the way the algorithm was employed, programs that became widely available on the Internet could be used to crack the WEP key. Once the key was known, it could be used to decrypt the data. Because of this, WEP is no longer considered to be a sufficient security mechanism in any situation where the data is sensitive.
WPA/WPA2 Cracking
After WEP cracking became an issue, the manufacturers of wireless equipment were faced with a problem. The IEEE was working on creating a new security standard (which became known as 802.11i) but were moving at their usual deliberate pace. In the meantime, companies were not deploying wireless networks because of security concerns. The Wi-Fi Alliance created a temporary solution called Wi-Fi Protected Access (WPA) that was an improvement on WEP.
Soon after WPA was rolled out, it was discovered that it also could be cracked. Cracking WPA required more effort than cracking WEP, and it required what is called a dictionary file (a file of words that could possibly be used as a password). It also required that the passphrase or password be a word in the dictionary. Finally, it required capturing a large number of wireless frames, and the cracking process took a lot of time. Keep in mind that this type of attack is effective on any password-based system, including Wi-Fi Protected Access 2 (WPA2) when it uses passwords.
But the point is that if the hackers had good reason to believe they were capturing valuable data, it could be done. Therefore, WPA is not considered good security unless it is employed as WPA2, which is based in the secure 802.11i architecture.
Deauthentication
A wireless deauthentication attack is a form of a DoS attack in which the attacker sends a large number of management packets called deauthentication frames on the WLAN, causing stations to be disconnected from the access point.
WPS Attacks
Wi-Fi Protected Setup (WPS, originally Wi-Fi Simple Config) is a network security standard that attempts to allow users to easily secure a wireless home network. It works by enabling the user to add a device to the network without typing credentials; all the user needs to do is push the WPS button located on many home wireless access points.
When this function is enabled, which it is by default on many systems, it is possible for a hacker to perform a brute force attack on the password and then later on the network pre-shared key for WPA or WPA2. Users should disable this feature if the device allows this change.
Rogue Access Points
Rogue access points are access points that you do not control and manage. There are two types: those that are connected to your wired infrastructure and those that are not. The ones that are connected to your wired network present a danger to your wired and wireless network. They may be placed there by your own users without your knowledge, or they may purposefully be put there by a hacker. In either case, they allow access to your wired network. Wireless intrusion prevention system (IPS) devices are usually used to locate them and to alert administrators of their presence.
Rogue access points that are not connected to your wired infrastructure are usually used as part of a hijacking attack, which is discussed in the next section.
Evil Twin
An evil twin is an AP that is not under your control but is used to perform a hijacking attack. A hijacking attack is one in which the hacker connects one or more of your users’ computers to their network for the purpose of a peer-to-peer attack.
The attack begins with the introduction of an access point that is under the hacker’s control. This access point will be set to use the same network name or SSID your network uses, and it will be set to require no authentication (creating what is called an open network). Moreover, this access point will be set to use a different channel than the access point under your control.
To understand how the attack works, you must understand how wireless stations (laptops, PDAs, and so on) choose an access point with which to connect. It is done by SSID and not by channel. The hacker will “jam” the channel on which your access point is transmitting. When a station gets disconnected from an access point, it scans the area for another access point with the same SSID. The stations will find the hacker’s access point and will connect to it.
Once the station is connected to the hacker’s access point, it will receive an IP address from a DHCP server running on the access point and the user will now be located on the same network as the hacker. At this point, the hacker is free to commence a peer-to-peer attack.
Bluejacking
Bluejacking is an attack aimed at Bluetooth connections. It sends unsolicited messages to the devices. These messages are typically in the form of a vCard that contains the message in the name field. While these attacks are annoying, they are not serious when compared to the attack in the next section, which is also a Bluetooth attack.
Bluesnarfing
Bluesnarfing is unauthorized access of a Bluetooth-enabled device. These attacks allow access to the data on the device and make use of the pairing function used to connect two devices to transfer data between them. Users should be advised to disable the function that makes their device “discoverable” and enable it manually only when a connection needs to be made.
Attackers and Their Tools
The old adage “Never talk to strangers” applies here because you can’t spot a hacker by looking at one. That quiet 15-year-old kid next door or the head of the PTA could secretly be a criminal hacker (or cracker, in nerd-speak)—you just never know. But instead of living your life being suspicious of everyone you meet, it’s much better to understand the ways and strategies bad guys use to infiltrate your defenses.
The interaction between a hacker and a network administrator can be anything from a harmless game of cat and mouse to a terrorist attack on national security. Either way, there’s someone out there trying to break into or crash your system, and it’s up to you to track and prevent the attacks.
Network attacks executed by an actual hacker are called directed attacks. For instance, a bad guy can use the WinNuke utility, which I’ll describe soon, to generate a packet and send it to a specific machine. On the other hand, viruses aren’t usually directed attacks—instead they’re just blindly copied from user to user.
I’ll start by telling you about some common network attacks and then move on to cover the techniques used to prevent them from happening to you.
 Real World Scenario
Real World Scenario
Do We Really Need Firewalls?
Believe it or not, the honor system used to apply to the Internet, and it pretty much worked, so firewalls just weren’t needed. Now, nothing could be further from the truth! Today, multitudes of companies have their entire corporate intranets connected to the Internet; plus, a legion of e-commerce sites like eBay and Amazon transfer seriously sensitive personal and financial data over the Internet. Corporate espionage and identity theft are currently the fastest-growing crimes worldwide—evil deeds pulled off by bad guys lurking on the Net. So, we all need to practice “Safe Net,” and one popular way to do that is by implementing firewalls on our networks.
Application-Layer Attacks
Application-layer attacks usually zero in on well-known holes in software that’s running on our servers. Favorite targets include FTP, sendmail, and HTTP because the permissions level granted to these accounts is often privileged. This means that bad guys who break in not only gain access to your network but also get the added bonus of having privileged status while they’re in there—yikes!
ActiveX Attacks
A fairly new form of attack makes its way to your computer through ActiveX and Java programs (applets). These are miniature programs that run on a web server or that you download to your local machine. Most ActiveX and Java applets are safe, but some contain viruses or snoop or spyware programs. Snoop or spyware programs allow a hacker to look at everything on your hard drive from a remote location without you knowing about it, which is really bad, so be sure you properly configure the on-access component of your antivirus software to check and clean for these types of attacks.
Autorooters
You can think of autorooters as a kind of hacker automaton. Hackers use something called a rootkit to probe, scan, and then capture data on a strategically positioned computer that’s poised to give them “eyes” into entire systems automatically. This is clearly very bad for you and your data. Note that this is typically how a cracker can attack a Mac or Unix box.
Backdoors
Backdoors are simply paths leading into a computer or network. From simple invasions to elaborate Trojan horses, villains can use their previously placed inroads into a specific host or a network whenever they want to—that is, unless you can detect them and stop them in their tracks.
Network Reconnaissance
Before breaking into a network, bad guys gather all the information they can about it because the more they know about the network, the better they can compromise it. This is called network reconnaissance. Hackers accomplish their objectives through methods like port scans, Domain Name Service (DNS) queries, and ping sweeps—even social engineering, or phishing, which I’ll cover in a bit.
Packet Sniffers
A packet sniffer is a software tool that can be incredibly effective in troubleshooting a problematic network, but it can also be a hacker’s friend. Here’s how it works: A network adapter card is set to promiscuous mode so it will send all packets snagged from the network’s Physical layer through to a special application to be viewed and sorted out. A packet sniffer can nick some highly valuable, sensitive data, including, but not limited to, passwords and usernames, making such a tool a prize among identity thieves.
Port Scanners
Port scanners are programs that ping every port on the target to identify which ports are open. It does this by pinging the IP address of the target with the port number appended after a colon. If an answer is received, the port is open. Open ports can lead to services the hacker can potentially exploit.
FTP Bounce
This attack is a variation of the port scan in that the attacker uses the FTP PORT command to request access to ports indirectly by using the victim machine as a middleman for the request. This cloaks the identity of the device performing the port scan.
Port-Redirection Attacks
A port-redirection attack requires a host machine the hacker has broken into and uses to redirect traffic that normally wouldn’t be allowed passage through a firewall. The attacker gains access to a trusted computer that is outside the firewall and installs software on the machine. They then redirect traffic bound for a particular port on the trusted yet now compromised host to their machine.
Trust-Exploitation Attacks
Trust-exploitation attacks happen when someone exploits a trust relationship in your network. The attacker gains control of a host that is outside the firewall yet is trusted by hosts that are inside the firewall. Once compromised, the host outside the firewall can be used as a platform to exploit the fact it is trusted by those inside the firewall.
Man-in-the-Middle Attacks
Interception! But it’s not a football, it’s a bunch of your network’s packets—your precious data. A man-in-the-middle attack happens when someone intercepts packets intended for one computer and reads the data. A common guilty party could be someone working for your very own ISP using a packet sniffer and augmenting it with routing and transport protocols. Rogue ATM machines and even credit-card swipers are tools that are also increasingly used for this type of attack. Figure 14.11 shows a man-in-the-middle attack.
Figure 14.11 Man-in-the-middle attack

Improper Access/Backdoor Access
A backdoor is a piece of software installed by a hacker that allows them to return later and connect to the computer without going through the normal authentication process. Some commercial applications inadvertently include backdoors because programmers forget to remove them before release to market. In many cases, the program is listening on a specific port, and when attempting to connect to that port, the attacker is allowed to connect without authentication. An example is Back Orifice 2000 (BO2K), an application-level Trojan horse used to give an attacker backdoor network access.
ARP Issues
ARP cache poisoning, usually a part of a man-in-the-middle attack, was discussed earlier in the section “ARP Cache Poisoning.”
Banner Grabbing/OUI
Banners are messages that are configured on some devices (routers, switches, servers) and appear under certain conditions, such as when someone is presented with a login screen, upon making a connection or when an error is encountered. These messages can impart information that can be used during the discovery phase of the hacking process. It may reveal the operating system or the version of firmware.
Banner grabbing is the process of connecting to the device using protocols such as Telnet, SMTP, or HTTP and then generating an error displaying the banner. Once the hacker discovers information contained in the banner such as the operating system and its version, they can research weaknesses in the system. For this reason, any service not in use should be disabled to eliminate it as a source of connection.
Domain/Local Group Configurations
In cases where computers are part of a domain, the domain member computers will have both domain accounts and local accounts. Local accounts are thus only effective on the local machine and cannot be used to access the domain.
However, there are default local accounts that exist on these computers that can be used to log on locally to the computer, thereby circumventing the domain login process. It’s dangerous to leave some of these enabled, such as the local administrator account. While they cannot be deleted, it is possible to rename them and/or disable them.
Jamming
Jamming is the process of sending out radio waves on the frequency used by a wireless network. It will have the effect of disassociating (disconnecting) all of the stations from the AP, at least while the jam signal is still there. When used for that purpose, jamming could be considered a DoS attack.
However, it is usually part of an evil twin attack, when the hacker is attempting to get your wireless stations to connect to their access point. They will set their AP to the same SSID as your wireless network but in a different channel (frequency). When they jam the real frequency, it causes the stations to seek another frequency with the same SSID, and they will find the hacker’s AP all too willing to allow their association.
Misconfiguration Issues
In many cases, security issues arise due to our own mistakes rather than the efforts of hackers. In the following sections, we’ll take a look at (and in some cases review) some of the most common misconfiguration errors and omissions.
Misconfigured Firewall
If the access control lists are misconfigured on a firewall, the damage will fall into one of three categories:
- Traffic is allowed that shouldn’t be allowed.
- Traffic that should be allowed is blocked.
- No traffic is allowed at all.
The first two problems are a matter of specifying the wrong traffic type in a permit or deny rule. Because in many cases the traffic type is specified in terms of a port number, it is critical to know the port numbers of the traffic you are dealing with.
The last problem can be either a simple omission or a complete misunderstanding of how ACLs work. At the end of every ACL is an implied rule that blocks all traffic that has not been allowed by earlier rules in the rule set. This means that all ACLs should have a rule at the end that allows all traffic that should be allowed. An ACL with no permit statements will block all traffic.
Misconfigured ACLs/Applications
Misconfigured applications can also cause issues. Web applications that do not perform proper input validation can allow for attacks such as buffer overflows. They can also in some cases allow for commands to be executed on the web server. For this reason, web-based applications should undergo strict code review and fuzz testing, and you should ensure that all input is validated before it is accepted by the application.
Open/Closed Ports
As discussed in the section on misconfiguration of firewalls, destination services and applications are specified in a packet in terms of a port number. When a device is open to receiving a connection to a service or application, it is said to be listening on the corresponding port. Therefore, closing or disabling a port eliminates the possibility of a malicious user connecting to that port and leveraging any weakness that may be known to be present with that service.
It is a standard device hardening practice to close any ports not required for the proper functioning of a device based on its role in the network. For example, a DNS server should have no other ports open but port 53, which is used to service DNS.
Unpatched Firmware/OSs
The best defense against the majority of malware types and attack modes is to keep current on all updates. This includes operating system patches, firmware updates, and application updates. Many devices that fall prey to malware and attacks do so needlessly because a patch existed that would have prevented the attack. A formal update system should be in place to ensure that no updates fall through the cracks.
Social Engineering (Phishing)
Hackers are more sophisticated today than they were 10 years ago, but then again, so are network administrators. Because most of today’s sys admins have secured their networks well enough to make it pretty tough for an outsider to gain access, hackers decided to try an easier route to gain information: they just asked the network’s users for it.
Social engineering, or phishing, refers to the act of attempting to illegally obtain sensitive information by pretending to be a credible source. Common phishing tactics include sending emails, making phone calls, or even starting up a conversation in person.
Some email phishing scams have made the news. In one case, bad guys sent out a mass email that was all dressed up to appear as though the message actually came from a real bank. The email said that the bank had an issue with one of its servers, so it now required you to confirm your user-account information to verify that none of your data was lost. All you needed to do was click the link provided in the email, enter your information, and snap—your identity went poof! If you possess a working brain and someone you didn’t know phoned and asked for your bank-account number, you certainly wouldn’t give it to them, right? No way—but the same request, coming in the form of a really legitimate-looking email, seems more believable for some reason. This has become a popular phishing tool, notoriously used to separate people from anything from a few bucks to their entire identity. Be careful!
Oh, and speaking of phone calls…let’s say you get a call to your desk at work from “Joe” in IT. He says he’s noticed some unusual activity on your network account and wants to check it out, but for security purposes, he needs your permission first. So he proceeds to confirm your login, and then he tells you he needs to enter your password into the network tracker. He asks, “What’s your password?” To protect yourself from this one, all you need to do is confirm his information and verify it with your IT department before you give him any of your data. You know by now that just because “Joe” knows your login doesn’t mean he’s on the up-and-up; even if “Joe” hangs up on you, you should still report the call to IT.
How did Joe get your login and telephone number? Remember network reconnaissance? First, because company phone directories are often on the Web, getting your phone number was easy. Even if it isn’t published, maybe Joe did some earlier phishing by calling one of your coworkers and, pretending to be a colleague at another site, asking for your phone number. But what about the username? On most networks, your username is the same as your email address because that makes things easier for your sys admin. This means that knowing that information is probably just a good guess on the attacker’s part. Maybe Joe the Hacker has gotten an email from someone at your company and knows what your email format is, and he may have some other information to help him figure out your network login. And even if the number on your caller ID when Joe called was an internal phone number, it doesn’t mean a thing—remember IP spoofing? Well, you can do that with phone numbers too.
The golden rule is don’t ever give any of your information or anyone else’s to anyone you’re not absolutely sure should have it. And if they are someone who should have it, they probably already do, and they shouldn’t be contacting you for it!
Understanding Mitigation Techniques
To be honest, I’m not going to go into detail about how to mitigate each and every one of the security threats I just talked about, not only because that would be outside the scope of this book, but also because the methods I am going to teach you will truly protect you from being attacked in general. You’ll learn enough tricks to make all but the most determined bad guys give up on you and search for easier prey. Basically, think of this as a section on how to practice “Safe Net.”
Safe networking techniques fall into three major categories: policies and procedures, training, and patches and upgrades. But before we go there, let’s cover some of those general defense techniques I just referred to.
Okay—first know that there are three main ways to detect an intruder and defend yourself against one:
- Active detection, which involves constantly scanning the network for possible break-ins
- Passive detection, which involves logging all network events to a file
- Proactive defense methods, which involve using tools to shore up your network walls against attack
Active Detection
Active detection is analogous to a security guard walking the premises, rattling doors to make sure they’re locked, and checking for intruders and any unusual activity. Similarly, there’s special network software that searches for hackers attempting known attack methods and scans for the kind of suspicious activity and weird network traffic that hackers leave behind as they travel over the network. Some sophisticated active systems go a step further and take action by doing things like shutting down the communications sessions a bad guy is using as well as emailing or paging you. Some security packages will even go as far as trying to cripple the computer from which the hacker is attacking! Cisco’s NetRanger, Memco’s Session Wall, and Snort are all forms of active intrusion-detection software.
Passive Detection
Using video cameras is a good example of using a passive intrusion detection system. Their counterparts in networking are files that log events that occur on the network. Tripwire for Unix systems is one of the earliest programs of this variety. It identifies changes in files using checksums. Changes in files indicate that someone has accessed them. Passive detection systems work by examining files and data and then calculating the checksums for each. The checksums are stored in a log file so that if the sys admin notices that a security breach has occurred on the network, they can access the log files to find clues about it.
Proactive Defense
A proactive defense is something you do or implement to ensure that your network is impenetrable. You can accomplish a lot through solid research and vigilant maintenance—you absolutely must stay current regarding any known security holes relevant to your type of network and the devices that populate it. You can also use tools like the unfortunately dubbed Security Administrator Tool for Analyzing Networks (SATAN) to find the holes in your security walls and plug them with software patches.
Clearly, before you can patch a hole, you’ve got to know it’s there, right? This is why I said it’s so important to stay current. Even better, stay a step ahead of bad guys by knowing your enemy’s strategies because the war against attackers is ever evolving—as soon as one hole is patched, bad guys will search for and find another vulnerability to exploit. And because patches usually take some time to develop, you can lose your shirt to a hacker in the interim. This is a big reason I’m saying it’s a better idea for you to know thy enemy than to rely on patches and the like.
Incident Response
Often when an attack or security breach occurs in the network, valuable time and information are lost in the critical first minutes and hours after the incident occurs. In some cases, evidence is inadvertently destroyed, making prosecution of the offending party impossible. In other cases, attacks that could have been interrupted and prevented before damage occurs are allowed to continue.
An incident response policy is designed to prevent this by establishing in advance the procedures that should be followed when an attack occurs. It may categorize incidents in such a way that certain event types (such as an active port scan) may require a response (such as disabling certain services) within 10 minutes while other events (such as an attempt to access a file without proper credentials) may only require a notation and follow-up in the next few days. The point is to establish these rules ahead of time to ensure that events are handled in a way that minimizes damage and preserves evidence.
 |
There is a host of great shareware and freeware available on the Internet today, including Windows Defender, Spybot Search & Destroy, and Ad-Aware as well as Windows Update. |
Basic Forensic Concepts
When security incidents occur in a network, a proper response is key, especially in the early stages. Computer forensics principles must be applied. These principles are specific to the nature of digital devices and the environment in which security incidents occur. From a high level, the steps in incident response are as follows:
- Detect the incident.
- Respond to the incident.
- Report the incident to the appropriate personnel.
- Recover from the incident.
- Remediate all components affected by the incident to ensure that all traces of the incident have been removed.
- Review the incident, and document all findings.
In the following sections, we’ll take a look at some of the salient details of these six steps.
First Responder
The first responder is responsible for securing the crime scene and protecting the evidence from corruption. This requires addressing the evidence in the order of volatility. Some types of data may be fragile and therefore need to be collected before other types. For example, a Polaroid photo (not a digital photo) should be taken of anything showing on the computer screen since that could go away at any time if the system goes off.
Secure the Area
The area should be sealed off to prevent anyone from touching or tampering with anything. Access to the crime scene should be tightly controlled and limited only to individuals who are vital to the investigation. As part of the documentation process, make sure to note anyone who has access to the crime scene. Once a crime scene is contaminated, there is no way to restore it to the original condition.
Escalate When Necessary
In any case where the first responder is not trained in forensics, the issue should be escalated to other personnel. In some cases it may involve calling the police, but be aware that when you do that you may lose control of the crime scene because they will take over the investigation. All users should be trained in basic crime scene concepts, such as don’t turn the machine off and don’t touch anything.
Document the Scene
Everything about the crime scene should be recorded and documented. Polaroid pictures should be taken to show the position of everything in the scene. Diagrams can be drawn to indicate positioning as well. Interviews of witnesses and first responders should be conducted as soon as possible because memory of details fades quickly.
eDiscovery
In the United States, discovery is the exchange of evidence by both sides in a lawsuit. eDiscovery is simply the application of this principle to electronic documents, such as emails, chat records, and other electronic forms of data. When this data is identified as potentially relevant to a case, it is placed on legal hold. Then it is gathered using digital forensic procedures to prevent its contamination as evidence.
Evidence/Data Collection
When you’re collecting evidence, the order of volatility is critical. Collecting it in the following order ensures that investigators get evidence from the components that are most volatile first. The order of volatility is as follows:
- Memory contents
- Swap files
- Network processes
- System processes
- File system information
- Raw disk blocks
You should create a bit-level copy of the system image and isolate the system from the network when you do this. Keep two copies of this image, one to be stored as an accurate backup copy of the evidence and the other to use to examine the image. You should create message digests (hashes) of the images to ensure that you can later prove that the images have not been tampered with.
Chain of Custody
Chain of custody records document who controlled the evidence, who secured the evidence, and who obtained the evidence. To successfully prosecute a suspect, a proper chain of custody must be preserved and the evidence must be collected following predefined procedures in accordance with all laws and regulations. Proper chain of custody ensures that all evidence is admissible in court.
Data Transport
When the data or evidence is being transported in any way, the process must be recorded and documented in detail. All physical evidence must be tagged, and the evidence tags must document the mode and means of transportation, a complete description of the evidence (including quality), who received the evidence, and who had access to the evidence. Any transmission of evidence should include a hash so the integrity of the evidence can be maintained.
Forensics Report
A forensics report should be created based on the findings. While evidence is being examined, any characteristics, such as time stamps and identification properties, should be determined and documented. Once the evidence has been fully analyzed using scientific methods, the full incident should be reconstructed and documented.
Legal Hold
During the eDiscovery process, evidence that is deemed to be possibly relevant will be placed on legal hold. This process may be initiated by a notice or communication from legal counsel to an organization. It requires suspension of normal processing of the data, such as backup tape recycling, archiving media, and using other forms of document and information storage and management.
Policies and Procedures
Every company should have written policies to effectively enable security on their computer networks. The policies should have the approval of the highest-ranking security or IT officer within the company, and they should address all aspects of the company network. Procedures should also be in place to determine the appropriate course of action if there is a security breach. And all network administrators absolutely need to be thoroughly trained on all policies and procedures—no weak links.
All of this might sound a bit militaristic in nature, but it’s truly necessary. Speaking of the military, though, the U.S. Department of Defense (DoD) has some really good standards; it wouldn’t hurt to keep them in mind when you’re setting up the security policies for your own network.
 |
You can find the evaluation criteria for the DoD computer standards at https://csrc.nist.gov/csrc/media/publications/conference-paper/1998/10/08/proceedings-of-the-21st-nissc-1998/documents/early-cs-papers/dod85.pdf In the past, this was known as the Rainbow Series because of the color of the books, but that’s been replaced by the much less colorful Common Criteria Evaluation and Validation Scheme (CCEVS). |
Security Policies
So what, exactly, is a security policy? Ideally, it should precisely define how security is to be implemented within an organization and include physical security, document security, and network security. Plus, you have to make sure these forms of security are implemented completely and solidly because if they aren’t, your security policy will be a lot like a block of Swiss cheese—some areas are covered, but others are full of holes.
Before a network can be truly secure, the network support staff should post the part of the security policy that applies to employee conduct on bulletin boards. It should, for example, forbid posting any company and/or employee information that’s not absolutely necessary—like, believe it or not, sticking Post-its with usernames and passwords on computer screens. Really clean desks, audits, and recording email communications and, in some cases, phone calls should also be requirements. And don’t forget to also post the consequences of not complying with the security policy.
Security Audit
Let me take a minute to explain all this a little more, beginning with security audits. A security audit is a thorough examination of your network that includes testing all its components to make sure everything is secure. You can do this internally, but you can also contract an audit with a third party if you want the level of security to be certified. A valid and verified consultant’s audit is a good follow-up to an internal audit. One reason for having your network’s security certified like this is that government agencies usually require it before they’ll grant you contract work, especially if that work is considered Confidential, Secret, or Top Secret.
Clean-Desk Policy
That clean-desk policy doesn’t mean just “get rid of the crumbs from your last snack.” It means requiring that all potentially important documents like books, schematics, confidential letters, notes to self, and so on aren’t left out in the open when someone’s away from their desk. Instead, they’re locked away, securely out of sight. And make sure it’s clear that this rule applies to users’ PC desktops too. Policies like this apply to offices, laboratories, and workbenches as well as desks, and it’s really important for employees who share workspaces and/or workstations.
It’s super easy to nick something off someone’s desk or screen. Because most security problems involve people on the inside, implementing and enforcing a clean-desk policy is a simple way to guard against security breaches.
 |
The International Computer Security Association (ICSA, www.icsa.net) reports that as many as 80 percent of all network break-ins occur from within the company and are carried out by employees, so protecting your data with a firewall is just the beginning of establishing network security. |
It might sound really nitpicky, but for a clean-desk policy to be effective, users have to clean up their desks every time they walk away from them—without exception. The day someone doesn’t will be the very day some prospective tenant is being shown the building’s layout and a sensitive document suddenly disappears. You should make sure workstations are locked to desks and do random spot checks once in a while to help enforce the policy. For obvious reasons, before company picnics and parties and before “bring your child to work day” are good times to do this.
 |
The ICSA is a vendor-neutral organization that certifies the functionality of security products as well as makes recommendations on security in general. |
Recording Equipment
Recording equipment—such as tape recorders, cell phones, and small memory devices like USB flash memory keychains—can contain sensitive, confidential information, so a good security policy should prohibit their unauthorized presence and use.
Just walk into almost any large technology company and you’ll be immediately confronted with signs. A really common one is a camera with a circle surrounding it and a slash through the center of the circle. Read the text below the sign and you’ll be informed that you can’t bring any recording devices onto the premises.
Here’s a good example. The NSA has updated its policy to include prohibiting Furby dolls on government premises because they have reasonably sophisticated computers inside them, complete with a digital recording device. The doll repeats what it hears at a certain interval of time, which is either cute or creepy but pretty much harmless—maybe even protective—in a children’s daycare center. Not so much at the NSA, though—no recording conversations there. Maybe, at least in some locations, it’s not such a good idea for your company either.
Licensing Restrictions
Software piracy is the unauthorized reproduction or distribution of copyrighted software. Although software piracy is a worldwide issue, it is much more prevalent in Asia, Europe, Latin America, and Africa/Middle East.
Security professionals and the organizations they work with must ensure that the organizations take measures to ensure that employees understand the implications of installing pirated software. They also need to ensure that these issues are covered specifically in the security policy.
In addition, large organizations might need to utilize an enterprise software inventory application that will provide administrators with a report on the software that is installed.
International Export Controls
Many organizations today develop trade relationships with organizations that are in other countries. Organizations must be aware of the export and import laws of both the source and destination countries. Encryption technologies are some of the most restricted technologies when it comes to import and export laws. Although the United States does limit the export of encryption technologies for national security reasons, other countries, such as China and Russia, limit the import of these same technologies because they do not want their citizens to have access to them. Publicly available technology, including software, is exempt from most export laws, except for encryption technologies.
Any organization that engages in export and import activities with entities based in other countries should ensure that legal counsel is involved in the process so that all laws and regulations are followed. In addition, the organization should implement the appropriate controls to ensure that personnel do not inadvertently violate any import and export laws, regulations, or internal corporate policies.
Other Common Security Policies
So you get the idea—security policies can cover literally hundreds of items. Here are some common ones:
Notification Security policies aren’t much good if no one knows about them, right? So make sure you give users a copy of the security policy when you give them their usernames and passwords. It’s also a good idea to have computers display a summarized version of the policy when any user attempts to connect. Here’s an example: “Unauthorized access is prohibited and will be prosecuted to the fullest extent of the law.” Remember—your goal is to close loopholes. One hacker actually argued that because a computer didn’t tell him otherwise, anyone was free to connect to and use the system!
Equipment Access Disable all unused network ports so that any nonemployees who happen to be in the building can’t connect a laptop to an unused port and gain access to the network. And don’t forget to place all network equipment under lock and key.
Wiring Your network’s wires should never run along the floor where they can be easily accessed (or tripped over, getting you sued). Routers, switches, and concentrators should live in locked closets or rooms, with access to those rooms controlled by anything ranging from a good lock to a biometric access system, depending on the level of security your specific network and data require.
Door Locks/Swipe Mechanisms Be sure that only authorized people know the combination to the cipher lock on your data-center doors or that only the appropriate people have badges that allow access to the data center. Change lock combinations often, and never ever leave server room doors open or unlocked.
Badges Require everyone to wear an ID badge, including contractors and visitors, and assign appropriate access levels to everyone.
Tracking Require badge access to all entrances to buildings and internal computer rooms. Track and record all entry to and exits from these rooms.
Passwords Reset passwords at least every month. Train everyone on how to create strong passwords. Set BIOS passwords on every client and server computer to prevent BIOS changes.
Monitor Viewing Place computer monitors strategically so that visitors or people looking through windows can’t see them, and make sure unauthorized users/persons can’t see security-guard stations and server monitors. Use monitor privacy screens if necessary.
Accounts Each user should have their own, unique user account, and employees should never share user accounts. Even temporary employees should have their own account. Otherwise, you won’t be able to isolate a security breach.
Testing Review and audit your network security at least once a year.
Background Checks Do background checks on all network support staff. This may include calling their previous employers, verifying their college degrees, requiring a drug test, and checking for a criminal background.
Firewalls Use a firewall to protect all Internet connections, and use the appropriate proxies and dynamic-packet-filtering equipment to control access to the network. Your firewall should provide as much security as your company requires and your budget allows.
Intrusion Detection Use intrusion detection and logging software to discover security breaches, and be sure you’re logging the events you want to monitor.
Cameras Cameras should cover all entrances to the building and the entire parking lot. Be sure that cameras are in weather-proof and tamper-proof housings, and review the output at a security-monitoring office. Record everything on extended-length tape recorders.
Mail Servers Provide each person with their own email mailbox, and attach an individual network account to each mailbox. If several people need to access a mailbox, don’t give all of them the password to a single network account. Instead, assign individual privileges to each person’s network account so you can track activity down to a single person, even with a generic address like [email protected].
DMZ Use a demilitarized zone (DMZ) for all publicly viewable servers, including web servers, FTP servers, and email relay servers. Figure 14.12 shows a common DMZ setup.
Figure 14.12 A common DMZ configuration

It is not advisable to put a DMZ outside the firewall because any servers outside your firewall defeat the whole purpose of having one. However, it is possible that you may see a DMZ outside the firewall in some networks.
Mail Relay Mail servers relay to other email servers by design. When the email server relays from any server that requests it, it is called open relay. Hackers use this feature to forward spam. Modern email systems allow you to control which servers your email server will relay for, which helps to prevent this.
Patches Make sure the latest security updates are installed after being properly tested on a nonproduction computer.
Backups Store backup tape cartridges securely, not on a shelf or table within reach of someone working at the server. Lock tapes in a waterproof, fireproof safe, and keep at least some of your backups off site.
Modems Do not ever allow desktop modems because they can be used to get to the Internet without your knowledge. Restrict modem access to approved server-based modem pools.
Guards If you need security guards, they shouldn’t patrol the same station all the time. As people become familiar with an environment and situation, they tend to become less observant about that environment, so rotating guards to keep their concentration at the highest possible level makes a lot of sense. Clearly, guards are people who need breaks to ensure alertness, but make sure that all patrol areas are covered during shift changes, rotations, and breaks. Guards should also receive periodic training and testing to make sure they can recognize a threat and take appropriate action.
 |
Believe it or not, covering all these bases still won’t guarantee that your network or facility is secure. All of this is really just a starting point that’s meant to point you in the right direction. |
Breaking Policy
You know that for your policy to be effective it’s got to be enforced consistently and completely. Nobody is so special that they don’t have to adhere to it. And people have to understand the consequences of breaking policy too. Your network users need to have a clearly written document, called a security policy, that fully identifies and explains what’s expected of them and what they can and can’t do. Plus, people must be made completely aware of the consequences of breaking the rules, and penalties have to match the severity of the offense and be carried out quickly, if not immediately, to be effective.
Let’s take a minute and talk about those penalties. As far back as the mid-1980s, employees were immediately terminated for major technology policy infractions. For example, one guy from a large computer company immediately got his pink slip when pornography was found on his computer’s hard drive. The situation was handled decisively—his manager informed him that he was being immediately terminated and that he had one hour to vacate the premises. A security guard stood watch while he cleaned out his desk to make sure the employee touched only personal items—no computer equipment, including storage media—and when he had finished gathering his personal things, the guard then escorted him from the building.
Downloading and installing software from the Internet to your PC at work is not as major (depending on where you work), but from the things we’ve been over so far, you know that doing that can compromise security. Beta products, new software, and patches need to be tested by the IT department before anyone can use them, period! Here’s an example: After an employee installed the untested beta release of a web browser and rebooted their PC, the production Windows NT server at a national telephone company crashed. The resulting action was to revoke that employee’s Internet FTP privileges for three months.
 Real World Scenario
Real World Scenario
Implement the Appropriate Policies or Procedures
You operate a mid-sized network for Acme Inc. Recently a rogue access point was discovered in the network, which constituted a security breach. While the original fear was that it was installed as an evil twin, further investigation revealed it was placed there by an employee so his department could have wireless access. It has now been removed. What two actions do you need to take and what security policy document do you need to access?
Answer
Remind/inform the employee of the security policy prohibiting this activity and discipline the employee. This will require access to an acceptable use policy, specifically the one that the employee signed when hired.
To prevent this in the future, you should schedule a training session for employees that reinforces the rules contained in the acceptable use policy and explains the motivation behind each.
The Exit Interview
Sometimes, the importance of an employee’s position and the amount of knowledge they have about the company and its systems justifies requiring an exit interview when they’re terminated. It’s done to minimize the risk of that employee being disgruntled and to attempt to ensure that they’re leaving under the most favorable circumstances possible. The interview can include the IT manager, a human resources representative, a sys admin, and sometimes even security personnel.
When an employee leaves the company—whether they’re quitting to move on to another job or being terminated—all company property needs to be turned in and logged. This includes things like company cell phones, pagers, toolkits, keys, badges, security tokens, models, and, obviously, all company documents.
And clearly, IT needs to disable all accounts immediately, including those for network access and voicemail, and remaining employees should be informed that the employee is leaving at this time. This is especially important when that employee has access to sensitive documents because even if they’re leaving under favorable conditions, they could still log in and copy data to take with them for their own use. For instance, salespeople can easily hurt a company by taking client information with them, and it has happened, as in the case of a salesperson who accessed their former company’s voicemail system and stole sales leads. So it’s not just the obviously disgruntled ex–network administrator who could demolish your website after leaving that you need to be concerned about.
Security Procedures
A security procedure defines how to respond to any security event that happens on your network. Here’s a short list of items you might include:
- What to do when someone has locked themselves out of their account
- How to properly install or remove software on servers
- What to do if files on the servers suddenly appear to be “missing” or altered
- How to respond when a network computer has a virus
- Actions to take if it appears that a hacker has broken into the network
- Actions to take if there is a physical emergency such as a fire or flood
Privileged User Accounts
Privileged user accounts represent those that have been provided rights normally reserved for the administrator. For example, if Jeff is granted the right to manage a printer, he now possesses a privileged account. Privileged accounts represent a potential security vulnerability, and their use should be monitored continually to ensure that they are used responsibly. When implementing them, you should always follow the principle of least privilege, which specifies that users should only be granted privileges required to do their job.
File Integrity Monitoring
File integrity refers to the prevention of unauthorized alteration. File hashing can be used to verify that changes to files have not occurred. See the section “File Hashing” later in this chapter for more details.
Role Separation
Separation of duties is a concept that specifies that any operation that is susceptible to fraud or abuse by employees should be broken into two tasks and then these two tasks should be assigned to different individuals. While there is no guarantee that these two individuals don’t collude, the chance of that occurring are much less than the chance of a single individual committing fraud.
Restricting Access via ACLs
Access control lists identify those who have access to resources and what type of access they have. ACLs are attached to the resource and are consulted whenever access is requested by an entity. These ACLs are your primary means of preventing access to unauthorized individuals. When implementing them you should always follow the principle of need to know, which specifies that users should only be granted access to information required to do their job.
Security Training
This brings us to the human element of network security. It’s true that most of your users want to do the right thing to protect the company—and their jobs—from the prying eyes of hackers, but the problem is that people don’t always know the right thing to do. That’s why training is so vital. It can include classroom sessions and/or web-based training, but experience has shown me that actual classroom-based instruction works the best. It’s also a good idea to have separate training classes for IT personnel and end users.
End-User Training
End-user training is pretty easy—it can take just an hour or so to bring employees up to speed. The “keep it short and simple” rule applies here or you’ll just end up with nap time. This is a great time to include detailed security protocol training. But if you see eyes beginning to glaze over or hear anyone snoring, you might want to make security protocol training a separate session because, as I said, it’s really important to the effectiveness of your security policy for everyone to know about and understand it. You can even use a year-end bonus or something else cool as a motivational reward for the employees who complete their training and test well on it.
And you have to back up your training by providing your end users with hard-copy, printed reference manuals in case they forget something (which they will). Include things like the following items:
- Recommended policies for creating safe passwords
- The number to call if they’ve locked themselves out of their accounts
- What to do if they think someone is phishing for information
- What to do if they think their computer has a virus
Clearly, new employees to the company or division should be required to go through training, but requiring that everybody attend refresher courses is also a good idea. And don’t hesitate to call a meeting if new threats arise or any sudden changes occur to keep everyone up-to-date.
Administrator Training
Obviously, training sessions for your IT personnel have to be a lot more in depth because they’ll be the ones who set up and configure policies, and they’ll also be the first responders to any security emergency.
It’s important to cover every aspect of your security policy with these people. And be sure they understand the correct ways to escalate issues in case of an emergency. Reacting to a security emergency is pretty stressful, and you don’t want your administrators to panic or feel isolated if one occurs. Making sure they know where their lifelines are and how to reach them quickly if they need backup will relieve a lot of pressure when something nasty happens.
Patches and Upgrades
The operating systems and applications we use today are really just gigantic collections of computer code. Windows Vista has about 50 million lines of code, and Windows XP has 35 to 40 million lines of code, whereas they shaved down Windows 7 to 40 million lines of code, Windows 8 is rumored to be between 50 and 80 million lines of code. And if you look at the subsystems within Windows, you’ll find that there are more than 50 dependency layers—processes that depend on other processes. Experts who work on developing Windows say that it typically takes someone about five years to fully learn two or three of these layers. So it’s pretty easy to imagine that with that much code being created by a couple of thousand different people, sometimes a few things get mixed up—and that’s the reason there always seems to be a few holes, glitches, and bugs to fix.
The good news is, as operating systems and applications are released, their developers have a chance to catch and repair the problems they uncover. In addition, as hackers find and take advantage of vulnerabilities, software developers work to plug those holes. The repairs are usually released to the public as patches or hotfixes. To address large-scale issues or add major features and components to a program, companies release complete upgrades instead.
Here’s where we get into the software side of security, which includes things like applying patches, hotfixes, and upgrades, plus how to choose and install the right third-party software to protect yourself against viruses.
Ensuring that your software is up-to-date is one of the best ways to protect against bad guys exploiting the security holes on your network.
Automatic Updates Through Windows Update
It’s really easy to get updates for Windows-based operating systems from Windows via Windows Update—a utility that’s usually automatically installed when you install Windows. If you need to get more information, go to www.microsoft.com.
To ensure that Windows Update is enabled, open your System Properties dialog (right-click My Computer and then choose Properties). You will see a screen similar to the one shown in Figure 14.13.
Figure 14.13 Automating Windows Update

If you have Windows Update installed, it will periodically scan your system for the version of Windows components you already have installed and compare them to the most current versions available from Microsoft. If your software is out-of-date, a Windows Update dialog box will appear, asking if you want to install the software updates. If you click Continue, the installation will proceed in the background; you’ll still be able to work in the foreground without skipping a beat.
Downloading Patches and Hotfixes
If you don’t have automatic updates set up, you can download patches and hotfixes manually. A hotfix is just like a patch that updates software, but this term is reserved for a solution to potentially serious issues that could compromise your network and hosts. When a company like Microsoft has created a whole bunch of patches, hotfixes, and upgrades, it will put them together in a larger bundle called a service pack. For instance, you can download Windows 7 Service Pack 1 (SP1) or Windows Server 2008 Service Pack 2 (SP2), which will update lots of components and address security, performance, and stability issues all at the same time. For the latest service pack for your Windows-based operating system or application, visit support.microsoft.com.
But let’s say you think you have a smaller, specific issue and you only want to download a patch for that particular problem. Maybe you’re dealing with an issue with IPSec and you want to know about creating IPSec security filters in Windows XP. After surfing Microsoft’s support site, you come across article KB914841 (https://www.microsoft.com/en-us/download/details.aspx?id=735). (KB stands for Knowledge Base, and it’s one way Microsoft organizes its support documents.) This article will give you background information as well as allow you to download hotfixes for the operating system you’re running.
Firmware Updates
While keeping operating system and application patches up-to-date gets most of the attention, there are devices on your network that may require firmware updates from time to time. Firmware is a form of program code and related data that is stored in persistent memory of some sort, such as non-volatile RAM (NVRAM).
In many cases firmware updates are designed to increase the functionality of a device. In other cases it may correct a bug or flaw in the system. Firmware updates are much more infrequent than other types of updates, so it’s easy to forget about them. You should always agree to be contacted by manufacturers regarding these updates because they are not as widely publicized as other types of updates.
Updating firmware is a process sometimes called flashing, in which the old firmware instructions are overwritten by the new ones. You should carefully follow the process described in the manufacturer’s documentation because failure to do so can lead to the device being made useless (sometimes called bricking the device).
Driver Updates
Drivers are files that allow a peripheral or component to talk to the hardware layer of the hosting device. In most cases, the drivers you need for a device will already be present in the drive cache that is installed with the operating system, but in some cases, especially with new devices, this will not be the case. In those instances, you will have to allow the system to locate the driver file from the CD that came with the device, or in extreme instances, you may have to search for it on the Internet. You should always start your search on the website of the manufacturer. Drivers found elsewhere may be problematic and in some cases may introduce malware.
Drivers also need to be updated from time to time. If you have computers set to receive updates automatically, updated drivers can be among the items you select to receive. Not all devices can benefit from automatic updating, and you may be required to check manually from time to time for driver updates for other devices, such as printers, scanners, and cameras.
File Hashing
Another security feature that can be utilized to prevent issues caused when malware attempts to alter or delete system files is file hashing. A hash function takes a message of variable length and produces a fixed-length hash value. Hash values, also referred to as message digests, are calculated using the original message. If the receiver calculates a hash value that is the same as the hash value of the original message, the original message is intact. If the receiver calculates a hash value that is different, then the original message has been altered.
Using a given function H, the following equation must be true to ensure that the original message, M1, has not been altered or replaced with a new message, M2:
- H(M1)<>H(M2)
By using software that computes hash values for all system files, and continually verifying these values, you can detect changes to system files.
Generating New Keys
Devices can use keys, which are long, randomly generated character streams, as input to encryption algorithms when encrypting data either in transit or at rest. At specified intervals, these keys must be renewed. While it is possible to renew the use of the same key (or key pair), generating a new key or key pair is advised. The longer a key is in use, the more likely the key will be compromised. Generating new keys at renewal time increases security.
Upgrading vs. Downgrading
Whenever a new version of an operating system or application is released, it usually generates a debate over whether the upgrade should be implemented. This is because experience has taught many IT technicians that there are often problems with a new release that they would prefer to avoid until someone else locates and corrects them.
Waiting until “all the bugs are ironed out” in an upgraded release is probably not a bad idea unless the upgrade addresses a security issue. In those cases, the risk is probably worth taking to close the security hole.
In some cases it may be necessary to reverse or downgrade a system to the old version if the new version causes substantial issues in the production environment. You can save yourself a lot of grief and possible downtime in the production environment by testing all new versions of applications, operating systems, and firmware before deploying them.
 Real World Scenario
Real World Scenario
Applying Your Knowledge
In your new position at ABB Tech Inc., one of your responsibilities is to maintain all software and firmware updates for the Sales department, which contains the following devices:
- 38 Windows 8.1 desktop systems
- 4 Red Hat Linux servers
- 1 Cisco 3550 switch
- 2 HP printers
- 1 Windows Server 2012 R2
Your latest assignment is to develop a plan for maintaining the updates on all of these machines. Complete the following table to provide the data required to create the plan. Research your answers using the websites of the vendors listed. You can check your answers in the following chart.
| Device | Update types (OS, firmware, driver) | Most efficient method | Schedule |
| Windows 8.1 | OS, driver | WSUS | Weekly |
| Red Hat Linux | OS, driver | Individual application | As notified by errata advisories through the Red Hat Customer Portal |
| Cisco 3550 | Firmware | Individual application | As notified by subscribing to field advisories and security emails from Cisco |
| HP printers | Driver | Individual application | As notified by subscribing to HP |
| Windows Server 2012 R2 | OS, driver | WSUS | Weekly |
Asset Disposal
When the time comes to decommission an asset such as a server or a hard drive, the handling of any data that remains is a big security issue. Whenever data is erased or removed from a storage media, residual data can be left behind. This can allow data to be reconstructed when the organization disposes of the media, resulting in unauthorized individuals or groups gaining access to data. Media that security professionals must consider include magnetic hard disk drives, solid-state drives, magnetic tapes, and optical media, such as CDs and DVDs. When considering data remanence, security professionals must understand three countermeasures: clearing, purging, and destruction.
- Clearing includes removing data from the media so that the data cannot be reconstructed using normal file recovery techniques and tools. With this method, the data is only recoverable using special forensic techniques.
- Purging, also referred to as sanitization, makes the data unreadable even with advanced forensic techniques. With this technique, data should be unrecoverable.
- Destruction involves destroying the media on which the data resides.
- Overwriting is a destruction technique that writes data patterns over the entire media, thereby eliminating any trace data.
- Degaussing, another destruction technique, exposes the media to a powerful, alternating magnetic field, removing any previously written data and leaving the media in a magnetically randomized (blank) state.
- Encryption scrambles the data on the media, thereby rendering it unreadable without the encryption key.
- Physical destruction involves physically breaking the media apart or chemically altering it. For magnetic media, physical destruction can also involve exposure to high temperatures.
Most of the countermeasures given work for magnetic media. However, solid-state drives present unique challenges because they cannot be overwritten. Most solid-state drive vendors provide sanitization commands that can be used to erase the data on the drive. Security professionals should research these commands to ensure that they are effective. Another option for these drives is to erase the cryptographic key. Often a combination of these methods must be used to fully ensure that the data is removed.
Data remanence is also a consideration when using any cloud-based solution for an organization. Security professionals should work with their organization when negotiating any contract with a cloud-based provider to ensure that the contract covers data remanence issues, although it is difficult to determine that the data is properly removed. Using data encryption is a great way to ensure that data remanence is not a concern when dealing with the cloud.
Detection
Certain devices and the features they offer can help us to detect when something is awry. Technicians shield make use of these tools and features to apprise themselves of issues that require their attention.
Motion detection
In areas that require constant attention to security it may be advisable to install motion detectors of some sort. Server rooms, wiring closets and other critical areas may need these. Let’s look at a few types
Infrared Sensors
Passive infrared systems (PIR) operate by identifying changes in heat waves in an area. Because the presence of an intruder would raise the temperature of the surrounding air particles, this system alerts or sounds an alarm when this occurs.
Electromechanical Systems
Electromechanical systems operate by detecting a break in an electrical circuit. For example, the circuit might cross a window or door and when the window or door is opened the circuit is broken, setting off an alarm of some sort. Another example might be a pressure pad placed under the carpet to detect the presence of individuals.
Photoelectric Systems
Photometric or photoelectric systems operate by detecting changes in the light and thus are used in windowless areas. They send a beam of light across the area and if the beam is interrupted (by a person, for example) the alarm is triggered.
Acoustical Detection Systems
Acoustical systems use strategically placed microphones to detect any sound made during a forced entry. These systems only work well in areas where there is not a lot of surrounding noise. They are typically very sensitive, which would cause many false alarms in a loud area, such as a door next to a busy street.
Wave Motion Detector
These devices generate a wave pattern in the area and detect any motion that disturbs the wave pattern. When the pattern is disturbed, an alarm sounds.
Capacitance Detector
These devices emit a magnetic field and monitor that field. If the field is disrupted, which will occur when a person enters the area, the alarm will sound.
Asset tracking tags
Proper asset management is not rocket science. It boils down to knowing exactly what you have, when you got it, where it is and where the license to use it is. The devil as they say is in the details. Most server administrators don’t set out to intentionally exercise poor asset management; they simply don’t give the importance it requires to be done correctly.
Labeling or tagging servers, workstations, printers, ports on infrastructure devices (routers and switches) and other items is another form of asset documentation that often doesn’t receive enough attention. Not only does this make your day to day duties easier, it makes the process of maintaining accurate records simpler and supports a proper asset management plan. When periodic inventories are taken (you are doing that, right?) having these items labeled makes the process so much quicker. This goes for cables in the server room as well
Tamper detection
Tamper detection refers to any method that alerts you when a device or the enclosure in which it resides has been opened or an attempt has been made to open it. A good example is chassis intrusion detection.
You should use settings in the BIOS to alert you when the case has been opened. These settings are shown in Figure 14.14. In this case the open case warning has not been enabled yet.
Figure 14.14 Open case warning in the BIOS

Anti-malware Software
Of all the update types that need to be maintained, anti-malware updates are the most critical to the organization. You must maintain updates to the malware definitions as well the updates to the malware engine itself. When choosing an anti-malware solution, there are two approaches, host based (also called premises based) and cloud based. In the following sections, we will examine both.
Host Based
Host- or premises-based anti-malware is a solution that you install and run inside your network. It has the advantage of giving you total control over the process but also requires you to stay on top of updates. It also requires the deployment of some hardware to hold the engine and the definition files.
Cloud/Server Based
Cloud antivirus products run not on local computers but in the cloud, creating a smaller footprint on the client and utilizing processing power in the cloud. They have the following advantages:
- They allow access to the latest malware data within minutes of the cloud antivirus service learning about it.
- They eliminate the need to continually update your antivirus software.
- The client is small, and it requires little processing power.
Cloud antivirus products have the following disadvantages:
- There is a client-to-cloud relationship, which means they cannot run in the background.
- They may scan only the core Windows files for viruses and not the whole computer.
- They are highly dependent on an Internet connection.
 Real World Scenario
Real World Scenario
Should I Install Host-Based or Cloud/Server-Based Anti-malware for My Network?
You manage a very large enterprise network and need to keep a close eye on the most common attacks today: malware. You should install a next-generation IPS device, but you don’t have the money for that type of equipment and the necessary training. You need something that will stop zero-day attacks if possible and don’t want to add much processing or even more software on the hosts in the network than you already have. You don’t want to install any new hardware, if possible, to get this done. With all this in mind, cloud/server-based anti-malware is your answer! It allows access to the latest malware data within minutes of the cloud antivirus service learning about it, and you don’t need to install any new hardware at your location. You just need a good, solid Internet connection.
Configuration Backups
We create device configurations over time that can be quite complicated, and in some cases where multiple technicians have played a role, no single person has a complete understanding of the configuration. For this reason, configurations should be backed up.
Configurations may sometimes exist as text files, such as in a router or switch. Other times, such as with a Microsoft server, you will back up what is called the system state. This backs up only the configuration of the server and not the data. In this case, a system state backup and a data backup should be performed. It is also possible to back up the entire computer, which would include both data sets.
Considering the time it takes to set up a new device, install the operating system, and reconfigure it to replace a defective device, it makes great sense to keep backups of configurations so that if a device fails, you can quickly reimage a new machine and simply apply the system state to it or apply the configuration file (in the case of routers and switches).
Updating Antivirus Components
A typical antivirus program consists of two components:
- The definition files
- The engine
The definition files list the various viruses, their types, and their footprints and tell you how to remove them. More than 100 new viruses are found in the wild each month, so it’s easy to see that an antivirus program would be totally useless if it didn’t keep up with all those emerging viruses.
The engine accesses the definition files (or database), runs virus scans, cleans the files, and notifies the appropriate people and accounts. Eventually, viruses become so sophisticated that a new engine, or even a whole new technology, is required to combat them effectively.
 |
Heuristic scanning is a technology that allows an antivirus program to search for a virus even if there’s no definition for it yet. The engine looks for suspicious activity of the kind that usually indicates the presence of a virus. But use such a tool with caution—if it’s turned on, this scanning technique can mistake harmless or even necessary code for suspicious code, and that can give you some major grief. |
For your antivirus program to work for you, you have to upgrade, update, and scan in a specific order:
- Upgrade the antivirus engine.
- Update the definition files.
- Create an antivirus emergency boot disk.
- Configure and run a full on-demand scan.
- Schedule monthly full on-demand scans.
- Configure and activate on-access scans.
- Make a new antivirus emergency boot disk monthly.
- Get the latest update when fighting a virus outbreak.
- Repeat all steps when you get a new engine.
I’m going to cover only the steps in this list that map to objectives of the Network+ exam, but looking into the others on your own won’t hurt and will give you some worthwhile knowledge.
Upgrading an Antivirus Engine
An antivirus engine is the core program that runs the scanning process, and virus definitions are keyed to an engine version number. For example, a 3.x engine won’t work with 4.x definition files. When the manufacturer releases a new engine, consider both the cost to upgrade and how much you’ll benefit before buying it.
 |
Before installing new or upgraded software, back up your entire computer system, including all your data. |
Updating Definition Files
I recommend that you update your list of known viruses—called the virus definition files—no less than weekly. You can do this manually or automatically through the manufacturer’s website, and you can use a staging server within your company to download and distribute the updates or set up each computer to download updates individually.
Scanning for Viruses
An antivirus scan is the process that an antivirus program deploys to examine a computer suspected of having a virus, identify the virus, and then get rid of it. There are three types of antivirus scans, and to really make sure your system is clean, you should use a combination of the types I’m covering in this section:
On-Demand Scan An on-demand scan is a virus scan initiated by you or an administrator that searches a file, a directory, a drive, or an entire computer but only checks the files you’re currently accessing. I recommend doing this at least monthly, but you’ll also want to do an on-demand scan when the following occurs:
- You first install the antivirus software.
- You upgrade the antivirus software engine.
- You suspect a virus outbreak.
 |
Before you initiate an on-demand scan, be sure you have the latest virus definitions. |
On-Access Scan An on-access scan runs in the background when you open a file or use a program in situations like these:
- Inserting a floppy disk or thumb drive
- Downloading a file with FTP
- Receiving email messages and attachments
- Viewing a web page
This kind of scan slows down the processing speed of other programs, but it’s worth the inconvenience.
Emergency Scan During an emergency scan, only the operating system and the antivirus program are running. You initiate one of these scans when a virus has totally invaded your system and taken control of the machine. In this situation, insert your antivirus emergency boot disk and boot the infected computer from it. Then, scan and clean the entire computer. If you don’t have your boot disk, go to another, uninfected machine and create one from it. Another possibility is to use an emergency scan website like https://housecall.trendmicro.com, which allows you to scan your computer via high-speed Internet access without using an emergency disk.
Fixing an Infected Computer
So what do you do if you know you have a virus? First, you want to make sure to scan all potentially affected hard disks plus any external disks that could be infected. Establish a cleaning station, and quarantine the infected area. You’ll have a really hard time doing this if anyone continues to use the computer while it is infected, so make sure all users in the infected area stop using their computers.
Then, remove all external memory devices from all disk drives and perform a scan and clean at the cleaning station. Update the virus definitions of any computers that are still operational. For the ones that aren’t, or the ones that are still working but are infected, boot to an antivirus emergency boot disk. After you’ve done that, run a full scan and clean the entire system on all computers in the office space. With luck, you will be done before your users return from lunch.
 |
It’s frustrating, but a lot of programs won’t install unless you disable the on-access portion of your antivirus software. Clearly, this is dangerous if the program has a virus. If you want to be really safe, do an on-demand scan of the software before installing it. If things are all good, go ahead and disable on-access scanning during installation, and then reactivate it when the installation is complete. |
Summary
Whew—this was a long chapter with a lot of good information in it. We talked about the dark side of computer networking: bad guys and the threats and attacks they use to victimize our systems and networks. You learned a lot about tactics like denial of service attacks, viruses, worms, social engineering, and other devious methods that hackers use. After that, you learned about ways to mitigate these threats and protect yourself by establishing policies and procedures, providing training, and ensuring that all your software is up-to-date. You also learned what to do about the ubiquitous problem of viruses. It’s a lot to remember, I know, but believe me, you’ll be really glad you’re armed with this knowledge because unfortunately, you’ll probably deal with these threats sooner or later.
Exam Essentials
Recognize vulnerabilities that may exist in your network. These vulnerabilities include unnecessary running services, open ports, unpatched systems, unencrypted channels, and the transmission of clear-text authentication credentials.
Know what types of threats can adversely affect your network. Threats include denial of service attacks, viruses, worms, rogue access points, phishing, and various other attack methods employed by hackers.
Understand how attackers attempt to get information about your network. Attackers have various methods they can use to gather information. Some of the most common reconnaissance tools are packet sniffers and social engineering.
Know how to keep your systems automatically updated. Programs such as Windows Update can keep your operating systems current, which will reduce opportunities for attackers to exploit your computers and network.
Know where to go to find downloadable software updates. Check the manufacturer’s website for the most current security information, patches, and updates.
Understand and implement proper forensic concepts. This includes following the six steps in the incident response process.
Written Lab
Write the answers to the following questions. You can find the answers in Appendix A.
-
A ___________ is a group of computers connected on the Internet for the purpose of performing a task in a coordinated manner.
-
How often should you update your virus definitions in your antivirus software?
-
What type of attack injects a command that overflows the amount of memory allocated and executes commands that would not normally be allowed?
-
___________ attacks are those that increase the effectiveness of a DoS attack.
-
What kind of tool could a hacker use to intercept traffic on your network?
-
What type of virus uses Microsoft’s Visual Basic scripting language?
-
What is it called when someone intercepts traffic on your network that’s intended for a different destination computer?
-
If someone installed a wireless router on your network without your knowledge, the WAP would be called ___________.
-
What software application can automatically ensure that your Windows-based computers have the most current security patches?
-
The two different types of virus scans are ___________.
Review Questions
You can find the answers to the review questions in Appendix B.
-
Which of the following is a type of denial of service attack?
- Ping of Death
- Stacheldraht
- SYN flood
- All of the above
-
In which attack does the attacker set the session ID ahead of time by sending a link to the victim with the ID preset?
- Session fixation
- Cross-site scripting
- Session sidejacking
- Session seeding
-
Which type of virus impacts files with the filename extensions .com, .exe, and .dll?
- File viruses
- SYN flood
- Smurf
- Tribe Flood Network
-
In which type of attack does the attacker scan for networks using a high-powered antenna connected to a wireless laptop?
- War driving
- Evil twin
- WEP cracking
- WPA cracking
-
Monkey B, Michelangelo, Stoned, and Stealth Boot are examples of which type of virus?
- IP spoofing
- Multipartite
- Macro
- Boot sector
-
Which type of virus affects both the boot sector and files on a computer?
- Mulipartite
- Macro
- Tribe Flood Network 2000 (TFN2K)
- Smurf
-
What is the main difference between a worm and a virus?
- Worms require user action for replication; viruses do not.
- Worms can be spread by email and viruses cannot.
- Worms can replicate without user intervention; viruses cannot.
- None of the above.
-
What kind of attack involves the hacker attempting all combinations of characters for a password to gain access?
- Packet sniffers
- Brute force attack
- Worm
- Backdoor
-
What type of security threat allows an attacker to learn your password through the use of an email or phone call?
- Phishing
- Trust-exploration attack
- Man-in-the-middle attack
- Rogue access point
-
Which type of policy should be implemented to secure important company documents and materials when employees leave their workstations?
- Clean housekeeping
- Clean desk
- Security audit
- Proactive defense
-
If you implement a set of policies and procedures that define corporate information as confidential and then train employees on these procedures, what type of attack can you prevent?
- DoS
- Man-in-the-middle attacks
- Smurf
- Social engineering
-
What type of wireless frame populates the display when someone is scanning for wireless networks?
- Probe response
- Beacon
- SSID
- Discovery
-
What defines the appropriate response to a security event on a network?
- Implementing security procedures
- Installing a new router
- Turning off the network
- Implementing an HR policy for dress code
-
Which of the following security mechanisms has been compromised?
- WEP
- 802.11i
- WPA2 Enterprise
- RADIUS
-
What process allows you to update your Windows-based operating system?
- Technet
- Windows Update
- Text message
- Hotfix
-
Why is it important to keep your system patched and up-to-date?
- To completely stop your need for security
- To increase the functionality of your applications
- To fix system vulnerabilities
- To make Windows completely safe and worry free
-
Who is responsible for securing a crime scene and protecting the evidence from corruption?
- First responder
- CIO
- Police
- User
-
Which type of scanning allows an antivirus program to search for a virus even if there is no definition for it?
- Update scan
- Signature-file scan
- Database scan
- Heuristic scan
-
What type of files need to be updated in order for your antivirus program to have the latest information about attacks and viruses?
- Definition files
- Email files
- DOC (.doc) files
- EXE (.exe) files
-
What type of scan can be done by an antivirus program?
- Emergency
- On-demand
- On-access
- All of the above
