CHAPTER 13
Sniffing Cryptocurrency Traffic
If you work as an investigator, I feel sure that when you read the title of this chapter regarding sniffing network traffic, you will think of the potential issues involved that could make it difficult or impossible. If you work within government or law enforcement, you will immediately think of the application of wiretap and intercept legislation—here in the UK, this type of activity requires an intercept warrant, which can be difficult to obtain. If you are a civilian investigator, you may assume that this type of activity is illegal and outside your sphere of expertise.
It is true that most countries have laws against intercepting any type of communications—whether it's voice, radio, or data—and parts of this chapter assume that you have the legal right to acquire data. I will make it clear when I'm talking about a technique that is likely covered by legislation, but it is your responsibility to check the local laws in your country and follow them. This also applies to government and law enforcement officers that will need to consider what approvals are needed.
This brief chapter will teach you how to monitor a specific Bitcoin node, wherever it may be in the world, and will also look at analyzing data packets for Bitcoin traces.
What Is Intercept?
Intercept legislation is usually described as intercepting and storing communications that are destined for a specific destination. Using mobile phone intercept as an example, let's say Alice calls Bob. Alice and Bob have an expectation of privacy, and the voice traffic is between two specific end-points: the voice from Alice is destined for Bob and vice versa. To listen to that phone call means positioning a receiver between the two endpoints, and it is this detail that is usually classed as intercept and hence illegal.
However, if Alice stood in the street and shouted across a road to Bob, Alice is broadcasting, so there are no defined endpoints and no expectation of privacy. Listening in to that conversation would not be illegal.
We can apply the same principle to data packets. If IP address 192.168.1.2 is sending data to 192.168.2.3, there are defined endpoints, and if we used technical measures to put a receiver between them and intercept that data, then this would likely be illegal. However, there are data packets that are broadcast to everyone, such as very specific broadcast packets from WiFi routers that broadcast the WiFi access point name. If I look at my phone and see a number of WiFi access points close by, it is because the phone has received broadcast packets announcing their existence. This is not intercept.
Another area that is not intercept is requesting data from a server of some type and receiving a response. This chapter will teach you how to watch a Bitcoin node and record the transactions and block information that is flowing out of it. It can feel a bit like intercepting the data, but because you are simply watching a flow of data making up the publicly available blockchain, this is not intercept.
Blockchain data for most cryptocurrencies is unencrypted because the data is public and there is no need to protect the data flow over the Internet. This means that it is possible to set up a WiFi-based or wire-based wiretap and watch the data flowing to and from peers on the blockchain network. Other cryptocurrencies such as ZCash are taking a different approach and encrypting their data. Please remember that a WiFi or wire-based wiretap on an Internet connection not owned by you would be classed as intercept in most territories.
If a suspect is using a thin client such as Electrum that does not run a full node, any transactions that are intercepted from the suspect can be considered the originator of the transaction. This can be very useful in watching the movement of coins and the attribution of public addresses. It is worth noting that the private key will never be broadcast.
Watching a Bitcoin Node
You can watch any Bitcoin node simply by connecting to it and requesting the flow of transactions. You are then able to see and record all of the blocks and transactions that are broadcast by the node to its peers.
The first thing you need to find is your target node IP address. This may be something you already have as part of an investigation, but for demonstration purposes, browse to http://bit.ly/2GfHSvz on the Bitnodes website. This page lists all of the current live Bitcoin nodes. Choose a node that was seen recently with its block height as close as possible to the up-to-date block number. Record the IP address and port number, which is usually 8333 as shown in Figure 13-1.

Figure 13-1: A Bitcoin node recorded by Bitnodes.
Once you have a target IP address, a great tool is available to enable you to watch transactions and blocks coming from the node. It's called the Bitcoin P2P Network Sniffer, and it's available at http://bit.ly/2o4VL9s. You just need to download the Python file sniffer.py.
Open sniffer.py in your chosen text editor (such as Notepad++). In the section titled “Default Settings if no configuration file is given,” find the line that begins with "host" followed by an IP address as shown in Figure 13-2. Adjust the IP address and port to your target address and save the sniffer.py file.

Figure 13-2: Change the IP address to the target node.
Next, open a terminal or a command shell in the folder where sniffer.py is located and type the following:
python sniffer.py
The command shell will connect to the remote terminal and start to write out each block hash as well as each transaction with the TX Hash and the output addresses and their values in satoshis. The output will look similar to Figure 13-3.

Figure 13-3: Output from the target node using sniffer.py.
This isn't the same as a network intercept or packet sniffing; this is just requesting the remote Bitcoin node for its public transaction data. This gives you the ability to watch an online node on the Bitcoin network; however, a developer could also utilize this code to attempt to watch every node on the network. If you can get to this point, then you can figure out, with a reasonable degree of certainty, what IP address was responsible for generating a transaction.
By the definition of most intercept legislation, this is not intercept. The information is publicly available—anyone can be a node on the peer-to-peer network and there is no expectation of privacy of this data.
Sniffing Data on the Wire
This book is not the forum to teach you how to set up a wired or wireless intercept. Most modernized countries have the capability to enable approved government agents or law-enforcement officers to watch data flowing to and from a particular IP address via agreements with Internet service providers (ISPs) or some central monitoring location. Tools in the public domain also enable equipment to be connected to a network in an attempt to intercept specific traffic or all the available traffic. It should be noted that trying to achieve full network intercept can cause many problems including bandwidth considerations and storage of the data in real time.
Intercept of WiFi-based traffic is considerably easier to achieve, and plenty of commercial and open-source tools are available to set up a WiFi-based tap. With a WiFi intercept, the limitations of antennas and the fact that it must be in listening mode only means that received packets are not acknowledged. The result of this is that there will almost certainly be missed packets that can add up to significant data loss over time.
As discussed at the start of the chapter, both of these intercept methods, WiFi and wired, are likely illegal in your country unless you own the traffic or have legal approval to do so.
Bitcoin traffic generally flows over port 8333 and is a fairly simple protocol. You can find the entire protocol documentation at http://bit.ly/2tZgcYw.
Perhaps the best way to learn and practice this technique is by monitoring the traffic that flows from your own Bitcoin node if you set up Bitcoin Core as discussed in Chapter 1. I recommend downloading and installing Wireshark, which you can find at http://bit.ly/1OKJhf7. Wireshark is an outstanding network protocol analyzer, and although it's a freely downloadable tool, it's arguably the best software available for packet analysis. When prompted, you will also need to accept the installation of the WinPCAP driver to enable Wireshark to capture traffic from your network.
Once Wireshark is installed, browse to the Capture Interfaces window by selecting Capture ![]() Options. As you can see in Figure 13-4, this displays all of the available network adapters on your computer. In this example, I selected Ethernet0 to capture data via the wired Ethernet port on my system. (Your system may have WiFi as an option too.) Ensure that the Enable Promiscuous Mode On All Interfaces box is selected and then click Start.
Options. As you can see in Figure 13-4, this displays all of the available network adapters on your computer. In this example, I selected Ethernet0 to capture data via the wired Ethernet port on my system. (Your system may have WiFi as an option too.) Ensure that the Enable Promiscuous Mode On All Interfaces box is selected and then click Start.

Figure 13-4: Wireshark capture options.
Wireshark will begin to capture all data packets from all ports flowing through your chosen network adapter. Ensure that Bitcoin Core is running so that Bitcoin transactions and blocks are syncing with your node.
The main Wireshark window will begin to fill up very quickly, especially if you have other network-connected services running (such as e-mail, web browser, Skype, or anything that signals the network). The window should start to resemble the example in Figure 13-5.

Figure 13-5: The main Wireshark window.
If you haven't used Wireshark before, I would recommend investing some time to learn it properly. Many excellent books and tutorials are available online that can teach you how to use Wireshark. A good place to start is the online help guide published on the Wireshark.org website at http://bit.ly/2CujtAf.
The Wireshark window has four primary sections:
- At the top of the window are the menu options, the toolbar, and an editable expression bar for creating filters.
- The next section contains a list of each captured packet. The Time column displays the default time. This is not an actual world time—it's the time offset from the first captured packet, which can be changed. The columns to the right of the Time column are Source, which displays the source IP address; the Destination, which displays the destination IP address; Protocol, which displays the protocol used; Length, which displays the length of the packet; and Info, which is an interpretation of the packet content.
- The third section breaks down the selected packet into its constituent parts. This is known as the packet details section. You can expand each part to view detailed raw and interpreted data about the packet.
- The bottom section provides the raw hex that makes up the selected packet, with the ACSII interpretation on the right. Each line displays the data offset, then 16 hex bytes, followed by 16 ASCII bytes.
You can filter the packets to just show Bitcoin-related packets. You can do this while Wireshark is running or stop the packet capture first by clicking using the round red Stop button (can be square in some versions) at the bottom-left corner of the window. You have a number of ways to apply a filter:
- Using the filter bar near the top of the Wireshark window, type the following:
tcp.port == 8333
Running this filter will just leave all the packets that use port 8333 (the port used by Bitcoin Core) as shown in Figure 13-6.

Figure 13-6: Packets filtered to just port 8333.
- Wireshark also has a built-in filter for Bitcoin. To use it, you simply type Bitcoin into the filter.
- You can also filter just the packets that are part of the Bitcoin network. For example, you can filter just on the Bitcoin magic value that corresponds to the first 4 bytes of the packet by typing
bitcoin.magic == 0xf9beb4d9
- Alternatively, you can filter on frames containing the IP addresses of peers on the peer-to-peer network by typing
bitcoin.services.network
You can decode transactions using the protocol documentation found at http://bit.ly/2EOjCDI. Figure 13-7 shows the raw hex that can be decoded using the protocol documentation. (Some decoding of the raw hex was discussed in Part 1 of the book).

Figure 13-7: Raw transaction packet.
A standard packet will begin with a packet header that includes IP addresses, Mac addresses, and so on.
If you use any of bitcoin filters described in the last three bullet points in the preceding list, you can click the Bitcoin protocol in the middle section of the Wireshark window, and the offset zero will shift to be the Bitcoin magic value. The Bitcoin header is 24 bytes in size before the payload of the transactions begins. Here is a breakdown of what those 24 bytes contain:
- The first 4 bytes are the magic value at the offset zero (
F9 BE B4 D9in Figure 13-8). The offset, in this case 000000, is the number to the left of the hexadecimal output.
Figure 13-8: Identifying the Bitcoin magic value.
- The next 12 bytes identify the packet type. In Figure 13-9, the value
74 78with 20 zeros (which istxin ASCII) identifies this as a transaction packet.
Figure 13-9: The packet type.
- The next 4 bytes are the length of the payload in bytes. This can be found at offset
000010and are02 01. This is formatted in internal byte order, so01 02in hex corresponds to a payload of 258 bytes. See Figure 13-10.
Figure 13-10: The size of the payload in bytes.
- The last 4 bytes are a checksum, which is a double 256 hash of the payload: sha256(sha256(payload)). In the example in Figure 13-11, they are
E2 93 CD BE.
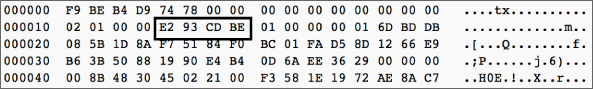
Figure 13-11: The checksum value.
Following these 24 bytes is the payload, which consists of the transaction input and output addresses, values, and so on.
Other Bitcoin clients may use different ports. For example, Electrum uses port 50002 for Bitcoin transactions. Ethereum runs a listener on TCP port 30303 and also a discovery service on UDP port 30303. As described earlier in this chapter, you can filter on these ports by using tcp.port == <port_Number>.
Where a thin client is being used, it may still be possible to intercept traffic by identifying the ports being used and filtering accordingly. However, some thin clients use encryption to encrypt the data from the client to the peer, which would prevent the effective intercept of the content of the data. It is worth remembering that encryption only affects the content of a packet, not the header. Because the header contains the source and destination IP addresses and ports, you are still able to see the IP addresses that are the peers on the network, which could be useful data to an investigator.
Summary
This short chapter is not designed to be a detailed explanation of sniffing cryptocurrency traffic on a network. Instead, it provides an overview of what is possible and an example of how to achieve it. Traffic sniffing and network protocol analysis are specific skills that need to be learned and practiced.
In this chapter, I also discussed how carrying out any type of traffic intercept is probably illegal in your country unless you own the data, have approval from the owner of the data, or are working as a government or law enforcement officer. Even for an officer of the law, there will likely still be legal requirements and legislation to work in line with.
Putting those restrictions aside, because Bitcoin traffic and the traffic of other cryptocurrencies is unencrypted, the data is readable, and which could be very useful in connecting a user to specific cryptocurrency addresses and trades. If you see a need to engage in traffic analysis of any cryptocurrency, I recommend that you do significant research, practice, and get the assistance of a specialist in this field.
