13
DDoS Attacks: Tools, Mitigation Approaches, and Probable Impact on Private Cloud Environment
R. K. Deka1, D. K. Bhattacharyya2, and J. K. Kalita3
1Department of Computer Science and Engineering, Assam Don Bosco University, Guwahati, Assam, India
2Department of Computer Science and Engineering, School of Engineering, Tezpur University, Tezpur, Assam, India
3Department of Computer Science, College of Engineering and Applied Science, University of Colorado, Boulder, CO, USA
13.1 Introduction
The cloud computing infrastructure allows a service provider on the Internet to provide the use of computing resources to fulfill the necessary demands of users. Due to virtualization, it is possible to provide services using optimal resources. Khorshed et al. [1] define cloud computing as “a system of shared resources of a data centre using virtualization technology. Such systems provide elasticity based on demand and ask for charges based on customer usage.”
Scanning, DoS, and penetration [2] can occur in a live network of computers. The Arbor Networks1 reported the largest (at that time) DDoS attack of 400 Gbps in 2014. In Figure 13.1, we can see DDoS attack trends in 20202. In particular, large‐scale DDoS attack frequency has continued to trend upward, as shown in Figure 13.2.
The Mirai botnet attack is launched using IoT devices such as DVR players and digital cameras. The victims were the servers of Dyn, a company that controls much of the Internet’s Domain Name System (DNS) infrastructure. It was hit on 21 October 2016 with an extraordinary attack strength of around 1.2 Tbps and remained under sustained assault for most of the day, bringing down many sites including Twitter, The Guardian, Netflix, Reddit, CNN, and many others in Europe and United States3.
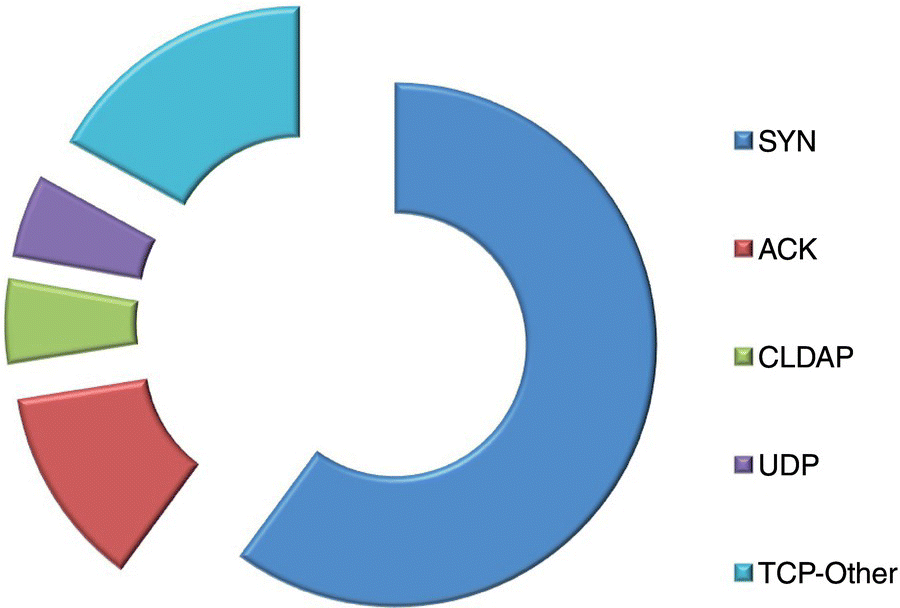
Figure 13.1 Types of intrusion scenario in 2020.
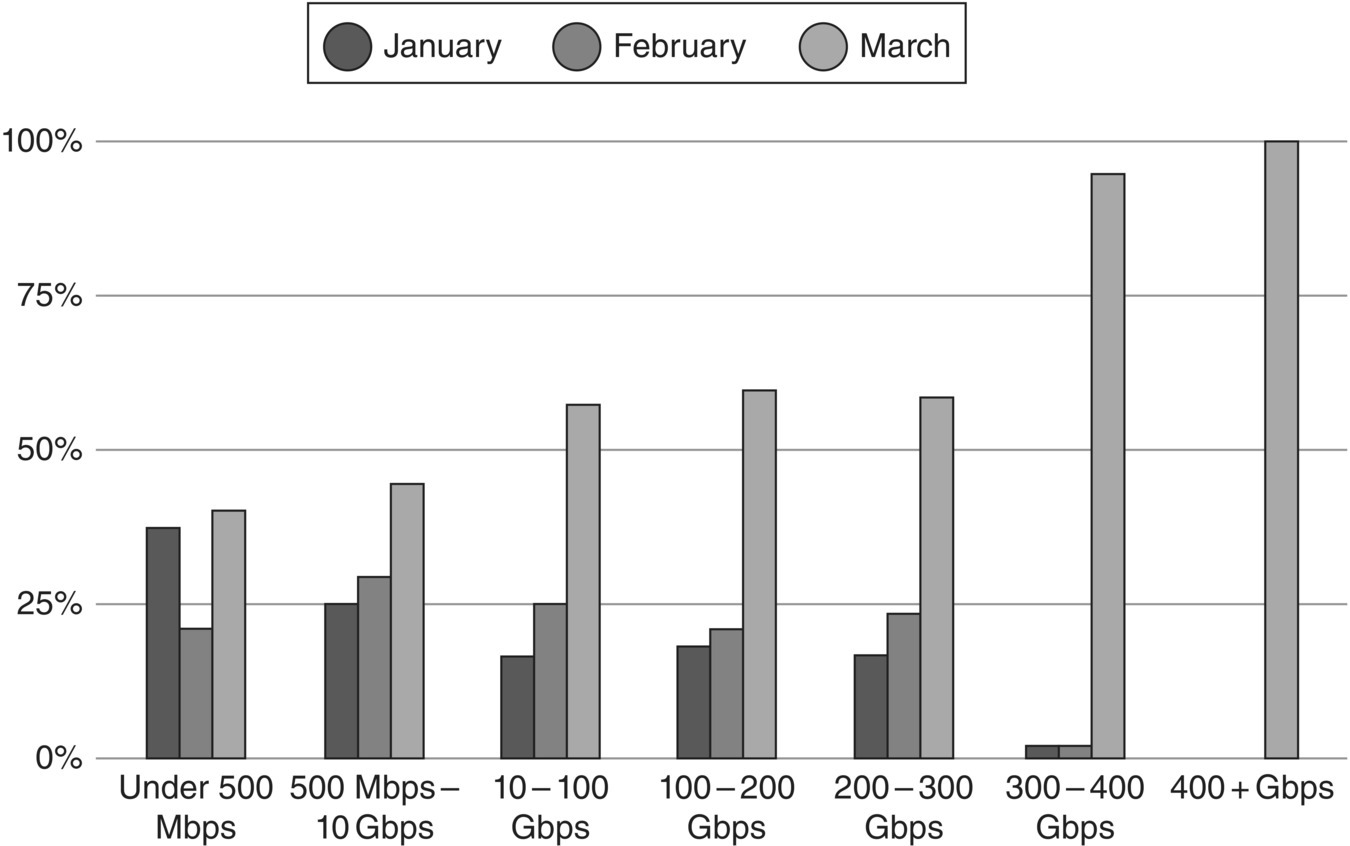
Figure 13.2 Statistics on DDoS attacks in 2020.
13.1.1 State of the Art
Research on DDoS attacks and defense in the cloud environment is still at an evolving stage. These days, researchers are very much concerned about services in the cloud and cloud security. Sabahi [3], Pitropakis et al. [4], and Grover and Sharma [5] discuss efforts to secure user data in the cloud. Rather than storing the information locally at the client’s infrastructure, data are stored in the cloud provider’s location. It is evident that in such a situation, people are worried about the security of their data. Thus, cloud organizations should provide adequate protection for the customer and also for the safety of their own.
In the context of the cloud, requests for resources like virtual machines (VM) can be made by any user through the Internet. As a result, a network of zombies can quickly launch DDoS attacks by sending fake requests for resources. Modi et al. [6] provide a survey of different types of intrusions which can take place in the cloud environment. Khorshed et al. [1], and Subashini and Kavitha [7] focus on flaws, challenges, and security concerns in different service layers.
In this article, we discuss the seriousness of the threats posed by DDoS attacks in the context of the cloud, particularly in the personal private cloud. We present a discussion of different approaches which used to defend or mitigate DDoS attacks in general network architecture, and also some methods that consider cloud computing technology in particular. Unlike [6], we highlight challenges and issues faced particularly by the private cloud environment when facing DDoS attacks in a general way. We have discussed about a generic framework to defend against DDoS attacks in an individual private cloud environment looking after different challenges and issues.
The first report on DDoS attack was in 1999 against servers of the University of Minnesota. In the early 2000s, many famous and major Websites like Yahoo!, eBay, CNN, and Amazon.com were assaulted by DDoS attacks [8]. Their systems were down for hours, and users were denied access to services [9]. These attacks were able to create a disaster because of the use of botnets. Stone‐Gross et al. [10] and Hoque et al. [11] provide a detailed investigation of botnets [12], a network of compromised machines under the control of a master. Khorshed et al. [1] provide a survey of challenges related to the cloud and present a proactive approach toward detection of attacks in the cloud.
In [13], the methods or approaches are based on supervised learning, unsupervised learning, probabilistic learning, and soft computing. Yu et al. [14] and Xiang et al. [15] present detection methods depending on rates of traffic.
There has been some work on mitigating or tolerating DDoS attacks in the cloud environment. With the increased sophistication of attackers, protection of open systems is increasingly challenging. Nguyen and Sood [16] opine that intrusion tolerance should be a part of overall in‐depth security. They compare three types of intrusion‐tolerant system architectures. Lua and Yow [17] propose a method in which an intelligent large swarm network is used against the attack to mitigate it. The swarm network constantly reconfigures itself through the use of a parallel optimization algorithm i.e., the intelligent water drop mechanism [18]. Amazon has created a technique called cloudWatch4 to monitor resources and to mitigate the situation according to the attack. Yu et al. [19] attempt to provide the theory of optimal resource allocation in a cloud platform when defending a DDoS attack. Wang et al. [20] have also developed a method on optimal resource allocation, which is adaptable to the cloud scenario.
In Table 13.1, a comparison is provided among a few existing survey papers with our work. For comparison, we choose four parameters, inclusion of attacks, description of defense solutions, issues and challenges, and addition of recommendations in these papers.
Security and complications with data privacy and data protection continue to restrict the growth of the cloud market, and these survey papers are more specific to the security issues that have been raised due to the nature of the service delivery system of a cloud environment. Sabahi [3] also pose the same concern about the cloud environment. Comparison between the benefits and risks of cloud computing is necessary for a full evaluation of the viability of cloud computing. Some critical issues that clients need to consider as they contemplate moving to cloud computing. Sabahi summarizes reliability, availability, and security issues faced by cloud computing, and proposed feasible and available solutions for some of them [21].
Zhang et al. [22], Wong and Tan [23], Kumar and Gohil [24], Chiba et al. [25], and Mishra et al. [26] present different survey‐work focusing on various IDSs developed in the last few years concerning the cloud environment. Basu et al. [27] mentioned that there are differences between mappings of different challenges/issues regarding cloud security with their own solutions. Few researchers present the virtualization challenges/issues and resolution mechanisms while others focus on techniques of the control procedure. Dong et al. [28] showed details about the DDoS attack in SDN and cloud environments. Their works also pointed out the open research problems in the identification and mitigation of DDoS attacks.
13.1.2 Contribution
This chapter presents an organized survey concerning security in the network infrastructure of cloud computing; specifically the impact of DoS and DDoS attacks on the networking services of a cloud environment. It begins with a description of types of cloud environments and then different types of DDoS attacks. It also highlights the seriousness of DDoS attacks in private clouds. We present an in‐depth discussion of the challenges and issues in defending such attacks. The significant contributions of this survey are the following:
Table 13.1 Comparison with existing survey articles.
| Authors | Year | Attacks included | Defense solutions | Issues and challenges | Recommendations |
|---|---|---|---|---|---|
| Subashini and Kavitha [7] | 2010 | √ | × | √ | × |
| Sabahi [3] | 2011 | √ | × | √ | × |
| Khorshed et al. [1] | 2012 | √ | × | √ | × |
| Modi et al. [6] | 2013 | √ | × | × | × |
| Wong and Tan [23] | 2014 | √ | √ | √ | × |
| Kumar and Gohil [24] | 2015 | √ | √ | × | × |
| Chiba et al. [25] | 2016 | √ | √ | √ | × |
| Mishra et al. [26] | 2017 | √ | √ | √ | × |
| Basu et al. [27] | 2018 | √ | √ | √ | × |
| Dong et al. [28] | 2019 | √ | √ | √ | × |
| Our survey | 2020 | √ | √ | √ | √ |
- Our presentation is specific to the security of cloud computing.
- There are just a handful of surveys on cloud security, and published reviews do not emphasize the impact of DDoS attacks on individual private clouds. We present challenges and issues to help the researcher in creating a defense theory and in building a defense system against DDoS attacks.
- Pros and cons analysis of a large number of detection and mitigation methods is included.
- We also discuss trending concepts such as the role of big data and software‐defined networking in cloud security.
- A generic framework for device defense mechanism in a cloud‐based environment is also presented.
13.1.3 Organization
The rest of the chapter is organized as follows. Different deployment models of clouds, DDoS attacks, and types of DDoS attacks along with the probable impact on private clouds are discussed in Section 13.2. Different existing approaches and potential solutions are briefed, and some recommendations for developing a defense model are presented in Section 13.3. In Section 13.4, challenges and issues related to a private cloud in defending against DDoS attacks are mentioned. A generic framework to defend against DDoS attacks is discussed in Section 13.5. Finally, we conclude in Section 13.6. In Figure 13.3, the taxonomy of terms and concepts used in the entire article is provided for better understanding for the reader.
13.2 Cloud and DDoS Attack
13.2.1 Cloud Deployment Models
A cloud node can provide three basic services to customers: IaaS, PaaS, and SaaS (Figure 13.4). The deployment differences can be seen in Figure 13.5, and an explanation of different deployment models are given below.
- Public cloud: The cloud is created for the general public where free or rental services are provided. This can be accessed by any authorized user. Examples of public clouds include Amazon Elastic Compute Cloud (EC2), Google AppEngine, and Windows Azure Services Platform. A public cloud provides abstractions for resources using virtualization techniques on a large scale. It benefits the user by delivering for backup and access to secure resources by synchronizing, replicating, and allocating the resources throughout the network.
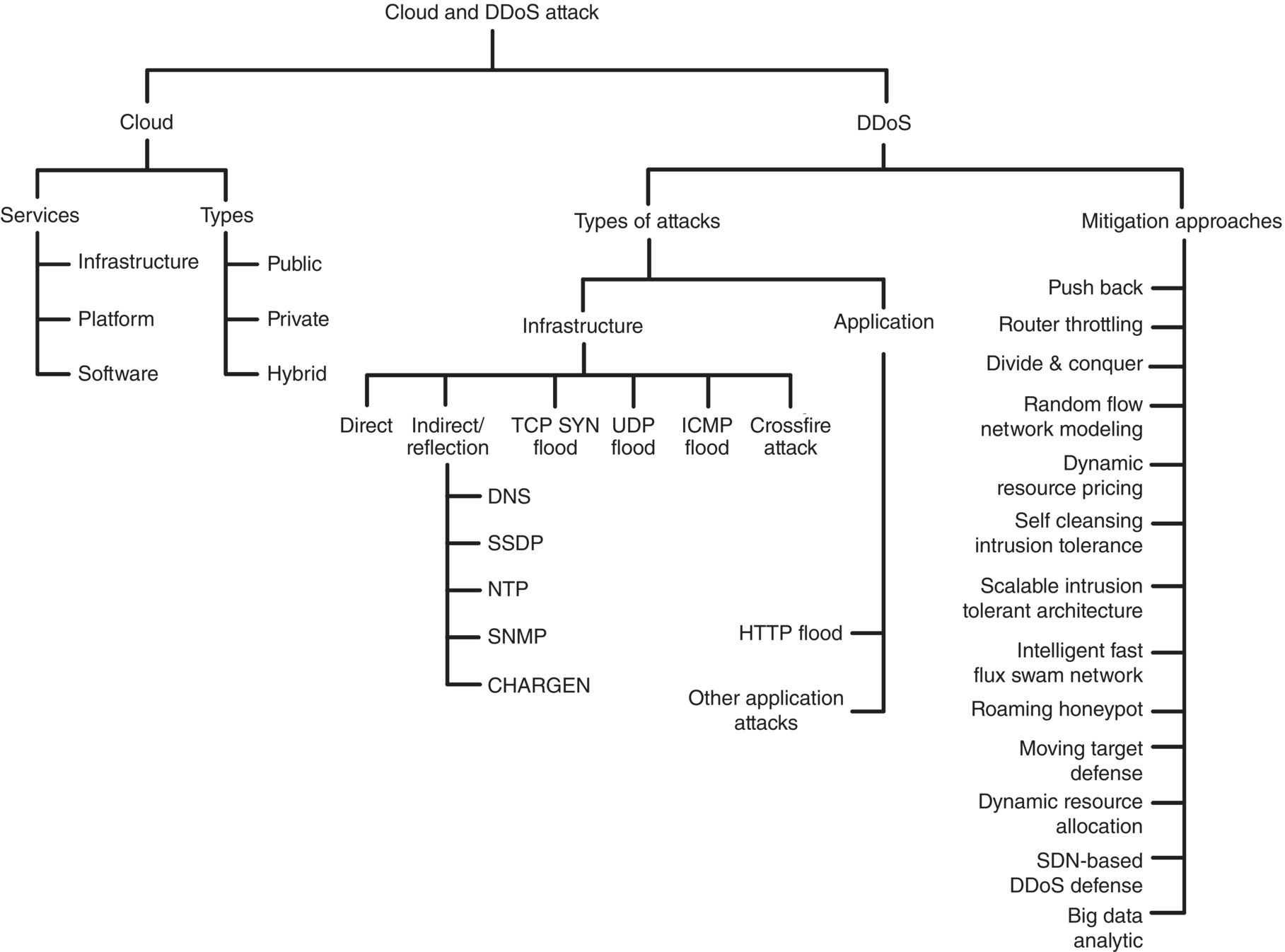
Figure 13.3 Taxonomy.

Figure 13.4 A cloud node.
- Private cloud: A private cloud is designed to offer the same features and benefits of public cloud systems, usually with limited resources for maintaining the cloud environment. Unlike a public cloud, a private cloud remains within the corporate firewall, which means the private cloud is privately managed by a company for the private use of its individual users and not for the public on pay per use basis. Also, a private cloud can be used by a company. In this scenario, in that cloud, sensitive data can be stored internally and also provide the advantages of cloud computing infrastructure to their business. For example, as per the demand, Apache CloudStack, OpenStack, VMware vCloud Suite, etc., allocate the resources to the clients. Individual private cloud customers as well as the provider.
- Community cloud: Few groups of users or organizations may have shared concerns (e.g. mission, security requirements, policy, and compliance considerations). Community cloud can be controlled by one or more organizations of that community, or a third party, or mixture of both. Some examples are Dimension Data, Layer‐ Stack, and Zoolz.

Figure 13.5 Deployment models.
- Hybrid cloud: It is a mixture of two or more linked cloud deployment models with a provision to transfer data between them. The combination may include both private and public clouds. For example, a company can maximize its efficiency by deploying public cloud services for all non‐sensitive operations, but only deploy private cloud when it needs to store sensitive operations as it is surrounded by a firewall, and ensure that all of their platforms are seamlessly integrated. Some examples are Amazon Web Services, Rackspace Hybrid Cloud, EMC Hybrid Cloud, and HP Hybrid Cloud.
13.2.1.1 Differences Between Private Cloud and Public Cloud
In Table 13.2, differences between private and public clouds are enumerated. A cloud has shared general features, whether private or public. As clouds have evolved on and from the Internet, we can build defense models based on research that has been conducted on general defense solutions against DDoS attacks and features of clouds. We can then proceed to discuss individual private cloud defense. Private clouds require more attention because they have limited resources, and the cost is high during an attack compared to a public cloud. We know that a private cloud is accessed by authorized users or private organizations paying money as per need. Both ends (customer and service provider) heavily rely on security. A DDoS attack can cripple the whole private cloud and jeopardize entire businesses. So, DDoS attack is more threatening to individual private cloud customers than a public cloud’s customers.
Table 13.2 Differences between private and public cloud.
| Key points | Private | Public |
|---|---|---|
| Use of Technology | Old | New |
| Capital expenses | Not shifted | Shifted to operational expenses |
| Utilization rate | Low | High |
| Infrastructure cost | High | Low |
| Elasticity | Less | More |
| Economies of sale | Less | High |
| Business attraction | Low | High |
| Security | Less | High |
| Perimeter complacency | Suffer | Not suffer |
| Skill level | Unknown | Usually high |
| Penetration testing | Insufficient | Sufficient |
| Business focus | Deeply in data center | Out of data center |
13.2.2 DDoS Attacks
13.2.2.1 Attacks on Infrastructure Level
In a Dos attack, legitimate users are denied access to the resources over the network. A botnet or a network of attackers inflicts severe damage on the victim. This distributed and coordinated attack can be called as DDoS attack. Nowadays, a lot of resources are in cloud in concentrated way and also a large number of users shared the same infrastructure. In this scenario, a DDoS attack will create huge loss [29].
Resources to compute, resource to transmit, and resources to route can be considered in the category of infrastructure. During infrastructure‐level attacks, attackers can overwhelm the capacity of a limited infrastructure of individual or private cloud. Attackers send a large numbers of fake requests to access the server so that the performance of the servers can be degraded.
- Direct: An example of direct infrastructure‐level attack can be visualized in Figure 13.6 [30]. A DDoS attack includes an overwhelming quantity of packets sent from multiple attack sites to a victim site. These packets arrive in such a high quantity that some key resource at the victim is quickly exhausted. The victim either crashes or spends so much time handling the attack traffic that it cannot attend to its real work.
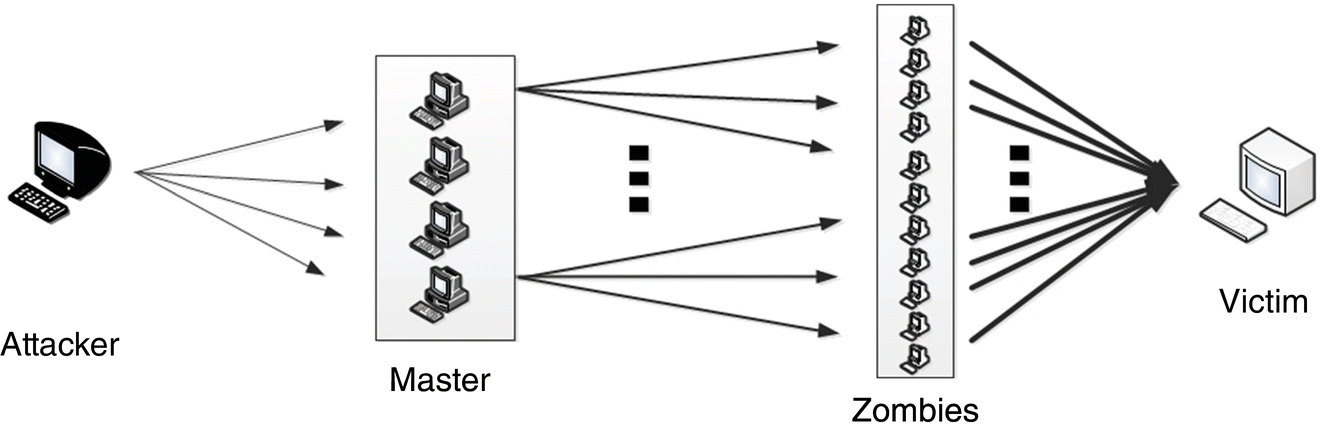
Figure 13.6 Direct DDoS attack.

Figure 13.7 Indirect DDoS attack.
- Indirect: This DoS attack compromises victim machines so that they unwillingly participate in a DDoS attack. Flashes of requests to the victim host machines are redirected or reflected from the victim hosts to the target. Some reflection or indirect‐based attacks are mentioned below. The general approach is as shown in Figure 13.7.
- Domain Name Service (DNS) reflection or amplification attacks use botnets that send a large number of DNS queries to open DNS resolver using spoofed IP addresses of victims. Thus, such an attack can do a lot of damage as it is difficult to stop this type of attack at an early stage.
- Simple Service Discovery Protocol (SSDP) reflection attacks are created using the Simple Object Access Protocol (SOAP) to deliver control messages to universal plug and play (UPnP) devices and to communicate information. These requests are created to elicit responses, which reflect and amplify a packet and redirect responses toward a target.
- Network Time Protocol (NTP) reflection attacks are created by the attacker to send a crafted packet in which requests for a large amount of data are sent to the host. NTP is used to synchronize the time between client and server.
- In an Simple Network Management Protocol (SNMP) reflection attack, the culprits send out a huge number of SNMP queries with forged IP addresses to numerous victim machines. SNMP is a network management protocol for configuring and collecting information from servers.
- Character Generator Protocol (CHARGEN) is often misused when attackers use the testing features of the protocol to create malicious payloads and reflect them by spoofing the address of the source to direct them to the target. CHARGEN is a debugging and measurement tool and also a character generator service.
- TCP SYN flood: Manipulating the three‐way handshake in a TCP connection, lots of SYN fragments are flooded by attackers so that legitimate users are denied.
- UDP flood: Massive numbers of datagrams are transmitted to random opened ports of the victim side. Sometimes, ports remain open without knowledge of administrators, causing the server to respond. A response to each UDP packet with an IMCP unreachable reply to the spoofed source IP address makes the situation worse by overwhelming the network environment of the victimized IP addresses.
- ICMP flood: ICMP flood is a ping‐based DoS attack that sends large numbers of ICMP packets to a server and attempts to crash the TCP/IP stack on the server and cause it to stop responding to incoming TCP/IP requests.
- Crossfire attack: A botnet controller can compute a large set of IP addresses whose advertised routes cross the same link, and then direct its bots to send low‐intensity traffic toward these addresses. This type of attack is called the Crossfire attack [31].
13.2.2.2 Attacks on Application Level
- Common application‐layer DDoS attack types: When a heavy amount of legitimate application‐layer requests or normal requests that consume heavy resources.
- HTTP flood attacks: Application layer attacks come in the form of GET floods. HTTP request attacks are those attacks where attackers send HTTP GETs and POSTs to Web servers in an attempt to flood them by consuming a large amount of resources. The HTTP POST method enables attackers to POST large amounts of data to the application layer at the victim side, and it happens to be the second most popular approach among the application layer attacks.
13.2.3 DoS/DDoS Attack on Cloud: Probable Impact
The public cloud infrastructure stands a better chance against DDoS attack because a public cloud usually has a lot of resources that make it easy to counter the attack dynamically. It is almost impossible to shut down such clouds by attacking them. But, if an intense DDoS attack occurs on customers of an individual private cloud like a data center with limited resources, it cannot escape from such attack, and it becomes a battle of survival using all the resources there are to confront [32, 33]. If we allocate necessary and sufficient resources on mitigation process efficiently, then we can defeat DDoS attack on cloud platform without much caring about efficient detection and prevention mechanism [34].
Cloud Service Provider (CSP) provides two plans for the customers, i.e. for short duration and for long duration or both [35]. Economic Denial of Sustainability (EDoS) can exploit this business model of resource allocation [36–38]. Initially, the allocated resources for any application in these models are limited. Thus, it will lead to a severe DDoS attack [39, 40], whether it is spot instance allocation or any reservation of resources for maximum use.
Some possible examples of DDoS attacks in cloud environments are Smurf attack, IP spoofing attack, Tear drop attack, SYN flood attack, ping of death attack, Buffer overflow attack, LAND attack, etc., as shown in Figure 13.8 [41, 42]. From news report we can state that large‐scale IoT‐enabled DDOS attacks will continue to dominate enterprise security. Darwish et al. [43] discuss DDoS attacks as attacks that target the resources of these services, lowering their ability to provide optimum usage of the network infrastructure, due to the nature of cloud computing, the methodologies for preventing or stopping.

Figure 13.8 DDoS attack types in cloud.
If we compare DDoS attacks in cloud with traditional network infrastructure, we will find quite differences. But, the new approaches to tackle DDoS attack in cloud which are published through various research platforms are actually the updated or adapted versions of old or traditional ones.
We summarize below the security concerns in the private cloud against DDoS attacks in the following:
- The customers or clients associated with cloud infrastructure are in large number. Thus, it has high potential to launch a severe and huge DDoS attack.
- Characteristics of DoS/DDoS attacks are unusual slow network performance, nonavailability of resources or inability to access the servers of websites and increase in spam attack dramatically.
- The patterns of DDoS attack are always changing. Attack growth, intensity, and penetration time change fast along with the Internet world.
- In the resource‐constrained environment of a private cloud network, it is essential to handle a DDoS attack as quickly as possible.
- It is usually a battle for survival with all the resources the private cloud can muster.
- In an individual private cloud, deft resource management is necessary and most definitive way to defend against a DDoS attack. Putting the best detection or filtering algorithm may not always work. But tolerating the attack by optimal resource utilization may resist the attack and may help counter the DDoS attack.
- Virtualization of resources gives some edge in a cloud environment to defeat DDoS attack.
13.3 Mitigation Approaches
DDoS attack mitigation is a classic problem. However, in the cloud environment, it becomes a more significant challenge [44]. We also cannot separate a cloud environment from the traditional network infrastructure. All approaches presented in this section have some advantages, which can be adapted for private cloud‐like environment. Some promising new approaches have also been developed in the context of the cloud. These include like SDN‐based ideas and ideas from the big data analytic point of view [45]. A defense approach can be deployed in the network itself or in the host (victim) environment. We analyze different existing approaches, and based on features of the approaches such as the level of operation, time to respond, and time to cooperate with other devices, we divide active response into two main categories, as shown in Figure 13.9.
In a proactive approach, a step taken to control potential incident activity before it happens rather than waiting for it to happen.
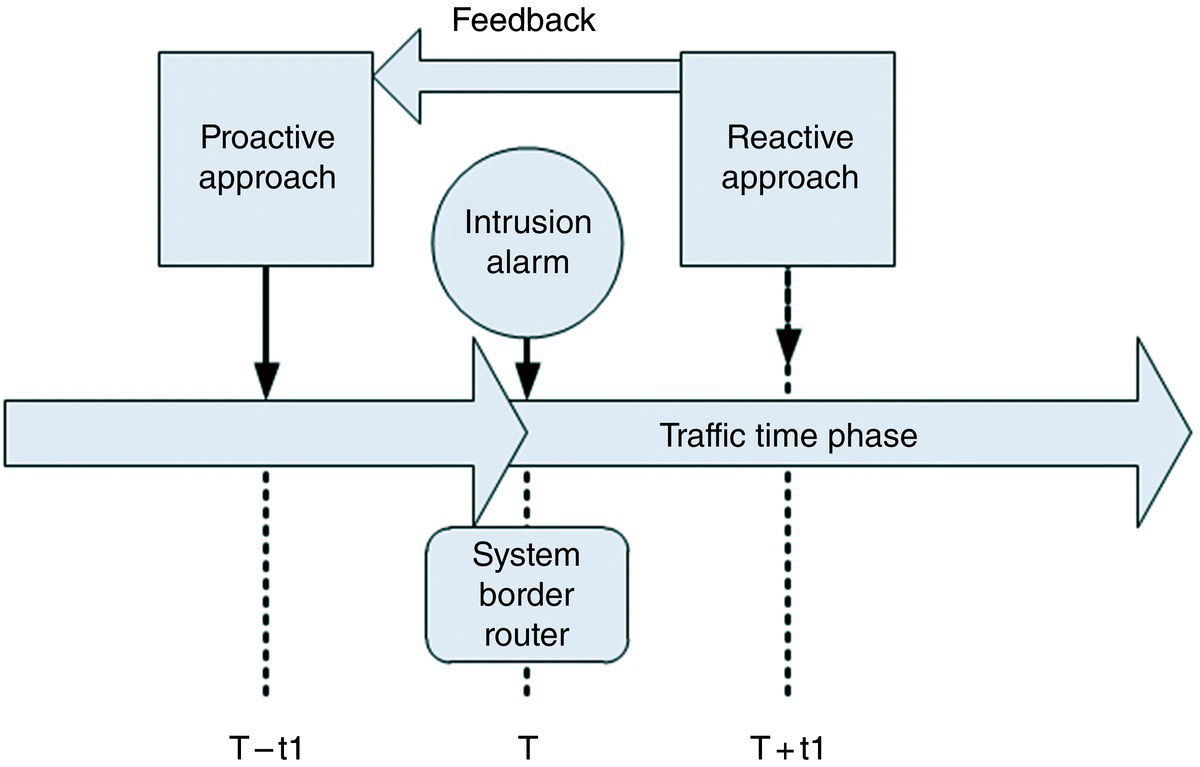
Figure 13.9 Attack response scenario.
A reactive approach detects the abnormality and informs the security administrator or automatically takes a responsive counter‐action immediately, i.e. in real time. A reactive response reacts only after the intrusion is detected.
In the rest of this section, a few prominent approaches are discussed. The models developed by different authors based on these approaches are analyzed. Each of the methods can be included either in the proactive or the reactive category. It very much remains open to debate which type of category will work best in the individual private cloud environment.
Push‐back: To mitigate the DDoS attack, the congestion in the network traffic needs to be controlled. Because essentially DDoS attack mitigation is a congestion control problem. The congestion occurs due to not obeying the traditional end‐to‐end congestion policies by the malicious host. Most researchers think that the problem needs to be handled by routers. To detect and to drop malicious packets as per the preference, the functionality can be added in the router. Those dropped packets might belong to an attack. A push‐back mechanism based on managing congestion at the routers has been implemented by Ioannidis and Bellovin [46].
Router Throttling: Participating routers can regulate the packet rate destined for a server. Yau et al. [47] propose and simulate a router throttling model to establish the efficacy of the concept, as shown in Figure 13.10. This idea can also increase the service reliability for legal users. Using the improvised K‐level max‐min fairness theory [48], Yau et al. find that the throttling mechanism is highly effective in countering an aggressive attacker. They efficiently regulate the server load to a level below its design limit amid a DDoS attack.

Figure 13.10 Router throttling model proposed by Yau et al. [47].
Source: Based on Yau, D. K., Lui, J. C., Liang, F., and Yam, Y. (2005). Defending against distributed denial‐of‐service attacks with max‐min fair server‐centric router throttles. IEEE/ACM Transactions on Networking, 13(1), 29–42.
Divide and Conquer: Chen et al. [49] use the divide and conquer strategy to actively throttle the attacking traffic. They present a diagnosis and attack mitigation scheme that combines the concepts of push‐back and packet marking. Detection of attacks is executed near the source‐end. Initially, IDS detects the attack on the victim side. The traceback scheme is carried out till the source end is reached. We believe that this idea can be adapted to the cloud environment.
Random Flow Network Modeling: This approach adapts the theoretical concept represented by the max‐flow min‐cut theorem of [50] concerning flow in a network. Kong et al. [51] rely on this theory in designing a random flow network model to mitigate DDoS attacks. They show that this mitigation problem can be reduced to an instance of the maximum flow problem. We know that a DDoS attacker heavily pumps the flow of traffic toward the sink. The strategy depends on the fact that the maximum achievable flow value from the source to the sink is equal to the capacity of a certain cut in the flow network. This method is suitable for any kind of computing environment because it does not depend on the end infrastructure; rather it is concerned with the intermediate network infrastructure.
Self‐Cleansing Intrusion Tolerance (SCIT): SCIT [52], a method based on virtualization technology, tries to achieve mitigation by constantly cleansing the servers and rotating the roles of individual servers, as shown in Figure 13.11. We know that virtualization is a key technique in a cloud‐based environment. If a server is initiated, SCIT places a pristine, malware‐free copy of the server’s operating system into a VM. To coordinate among server modes, rotations can be performed with the help of a central controller or a distributed control mechanism using the Cluster Communication Protocol (CCP) [53]. In the rotation process, online servers are set offline. Afterward, the system is rebooted to initiate cleansing procedures.
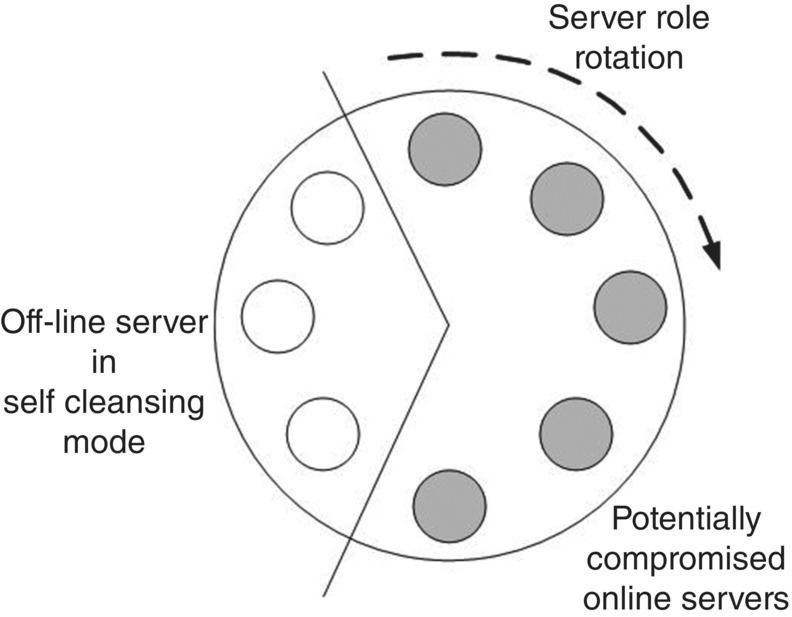
Figure 13.11 A high‐level view of SCIT model.
Dynamic Resource Pricing: Mankins et al. [54] discuss the applicability of dynamic resource pricing to discriminate well from bad traffic. They implement a dynamic pricing strategy that favors good user behavior and punishes aggressive adversarial behavior. They propose a distributed gateway framework and a payment protocol. The idea is to impose dynamically changing prices on both network servers and information resources so that the approach can push the cost of initiating service requests, in terms of monetary payments and/or computational burdens, to requesting clients. Thus, the architecture can provide for service quality discrimination to separate good client behavior from adversarial behavior in a private cloud environment serving a large set of heterogeneous consumers.
Intelligent Fast‐Flux Swarm Network: Lua et al. [17] describe an autonomous intelligent coordinated network of swarm nodes to mitigate DDoS attacks. This swarm network ensures autonomous co‐ordination among nodes and allocation of swarm nodes (deploying nodes densely) to maintain connection. A load‐balancing process checks the health of nodes and removes those that are unresponsive. However, when a DDoS attack is in progress, it may not be robust. For better optimization, they use IWD [18]. It is a nature‐inspired algorithm. The algorithm mimics how water drops behave in the flow of a river, i.e. the dynamic behavior of a river.
Roaming Honeypot: Khattab et al. [55] and Sardana and Joshi [56] propose the concept of roaming honeypots, changing the locations of the honeypots continuously and disguising them within a server pool. The roaming honeypot mitigates attacks from behind the firewall by dropping all connections when a server switches from acting as honeypot to become an active server. So, if we can adapt this approach to the individual private cloud environment, a roaming honeypot may be a very good defender for that environment with limited resources for legitimate users.
Target Defense Moving: Researchers have proposed an innovative way to defend DDoS attack. Aspects of the systems to present the attackers are changed and created a varied surface for the attacker. Thus, it becomes more difficult to exploit the vulnerability. In general, the attacker looks for exploiting the drawbacks or loopholes that exist in a system. But, while analyzing and learning the vulnerabilities by an attacker, the system will change its aspects so that the required time to launch an attack and to disrupt the functionality of the system is reduced. In that time, the system has changed to more or less a new system [57, 58]. This approach may provide an effective defense solution in context of private cloud environment as well.
Dynamic Resource Allocation: In addition the traditional defense approaches, we need to explore resource allocation and utilization strategies for defending DDoS attacks in the cloud. Yau et al. [47] contend that DDoS defense is a resource management problem. Every day the attack patterns keep changing. It will be a fruitless waste of time and resources to try to defend against DDoS attacks by just looking at patterns learned earlier. In addition, it is important to not only defend against an attack but also make services available during an attack. To beat DDoS attacks in the cloud, Yu et al. [19] propose a dynamic resource allocation procedure within an individual cloud, as shown in Figure 13.12. It is a simple methodology of cloning Intrusion Prevention Servers from idle resources to filter out attack packets quickly and provide general services simultaneously. Some other specific resource allocation approaches have been proposed as well.
Virtualization is a key concept in resource provisioning and management in the cloud. Virtualization provides a view of resources used to instantiate VMs. Isolating and migrating the state of a machine help improve optimization of resource allocation. Live VM migration transfers the “state” of a VM from one physical machine to another, and can mitigate overload conditions and enable uninterrupted maintenance activities. Mishra et al. [59] incorporate dynamic resource management in a virtual environment. Their approach answers basic questions such as when to migrate, how to migrate, types of migration, and where to migrate. It also treats the migration of resources differently in different network architectures, e.g. local area networks (LAN) and wide area networks (WAN).
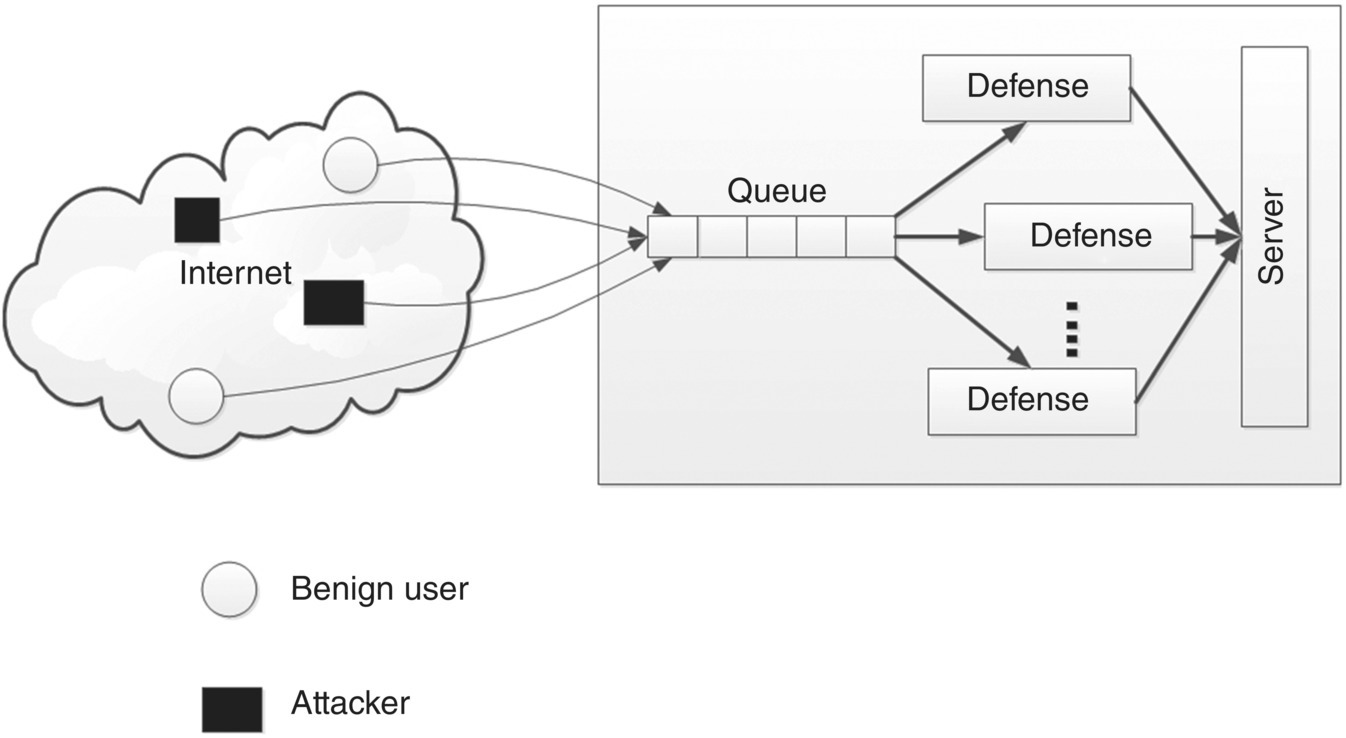
Figure 13.12 Dynamic resource allocation strategy by Yu et al. [19].
Source: Based on Yu, S., Tian, Y., Guo, S., and Wu, D. O. (2013). Can we beat DDoS attacks in clouds?IEEE Transactions on Parallel and Distributed Systems, 25(9), 2245–2254.
The cloud environment can be described as probabilistic in nature. So there is a need to assess the performance of a cloud center for resource provisioning. The probabilistic nature of the cloud can be represented in terms of stochastic processes [60–64]. Shawky [65] introduces an approach to model and analyze the performance of the resource allocation process using stochastic process algebra.
SDN‐based DDoS Defense: An attacker can infect a sufficient number of machines in a short time frame in traditional networks. Attackers are also known to use cloud as Malware as a Service by renting different VMs and using them as bots [66]. Separation of the control plane from the data plane enables one to establish easily large‐scale attack and defense experiments. A logical centralized controller of an SDN permits a system defender to build consistent security policies and to monitor or analyze traffic patterns for potential security threats. A programmable intermediate network architecture can be setup easily in an SDN.
The cloud networks face challenges such as guaranteed performance of applications when applications are moved from on‐premise to the cloud facility, flexible deployment of appliances (e.g. intrusion detection systems or firewalls), and security and privacy protection. An environment, providing good programmable, flexible, and secure infrastructure is needed. SDNs are evolving as the key technology that can improve cloud manageability, scalability, controllability, and dynamism [67]. In the past few years, several innovative SDN‐based defense solutions have been introduced. These solutions belong to the three basic types of SDN‐based DDoS defense mechanisms as shown in Figure 13.13. In [68], include a detailed discussion of SDNs, SDN‐based clouds, and autonomous defense in clouds.
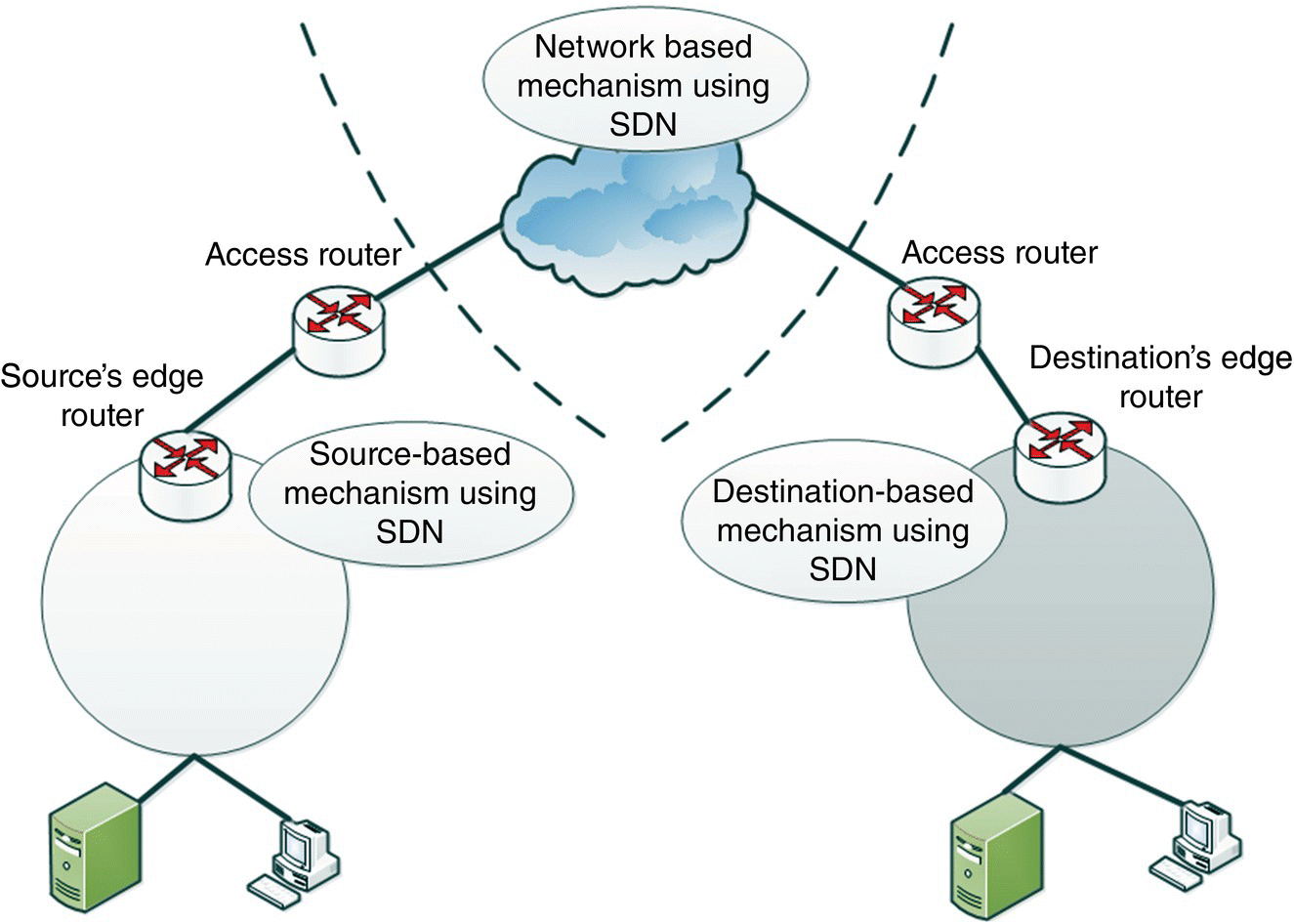
Figure 13.13 SDN to defend DDoS attack.
Lin et al. [69] refer to SDNs as an emerging wave to transform network industries. They discuss SDNs and standardization in terms of components such as controllers, applications, service chains, network function virtualization, and interfaces. Braga et al. [70] presents a lightweight method for DDoS attack detection based on traffic flow features, in which the extraction of such information is made with a very low overhead compared to traditional approaches. This is possible due to the use of the NOX platform [71], which provides a programmatic interface to facilitate the handling of switch information. Shin and Gu [72] show a new attack to fingerprint SDN networks and further launch efficient resource consumption attacks. This attack demonstrates that SDNs also introduce new security issues that may not be ignored. Flow Table Overloading in Software‐Defined Networks is a vulnerability to be handled carefully. Yuan et al. [73] point out this issue and provide a security service in an SDN using QoS‐aware mitigation strategy, namely, peer support strategy, integrating the available idle flow table resource of the whole SDN system to mitigate such an attack on a single switch of the system.
Nguyen et al. [74] propose a SDN‐based approach, Whack‐a‐Mole. It is a cloud resource management procedure using network obfuscation to help CSPs. This approach protects critical services proactively against a DDoS attack and putting very less service interruption. It deploys VM spawning model to assign random address space by creating multiple replicated VM instances for the services which are critical. They have shown its effectiveness using such optimized VM spawning based on real Service‐level Agreements and implemented the whole approach using SDN/OpenFlow controllers over Open vSwitches on a GENI testbed. Xu et al. [75] devised a defensive approach by classifying the traffic using SDNFV for flexibility. Thus, it reduces load on SDN.
SDNs have been accepted as a new paradigm to provide an entire set of virtualization and control mechanisms to meet defense challenges in cloud networking [2876–78]. Thus, exploring the use of SDNs in providing better DDoS defense solutions in the cloud computing environment is likely to be beneficial.
Big Data Analytics: For detecting DDoS attacks, Jiao et al. [79] identifies FSIA and RSIA for extraction of TCP traffic features and better classification through Big Data analytics using two decision tree classifiers [80].
Vieira et al. [81] propose the Intrusion Responsive Autonomic System (IRAS) to analyze real‐time traffic to detect intrusion and mitigate attacks in the cloud platform, as shown in Figure 13.14. IRAS is an autonomous intrusion response technique endowed with self‐awareness, self‐optimization, and self‐healing properties.
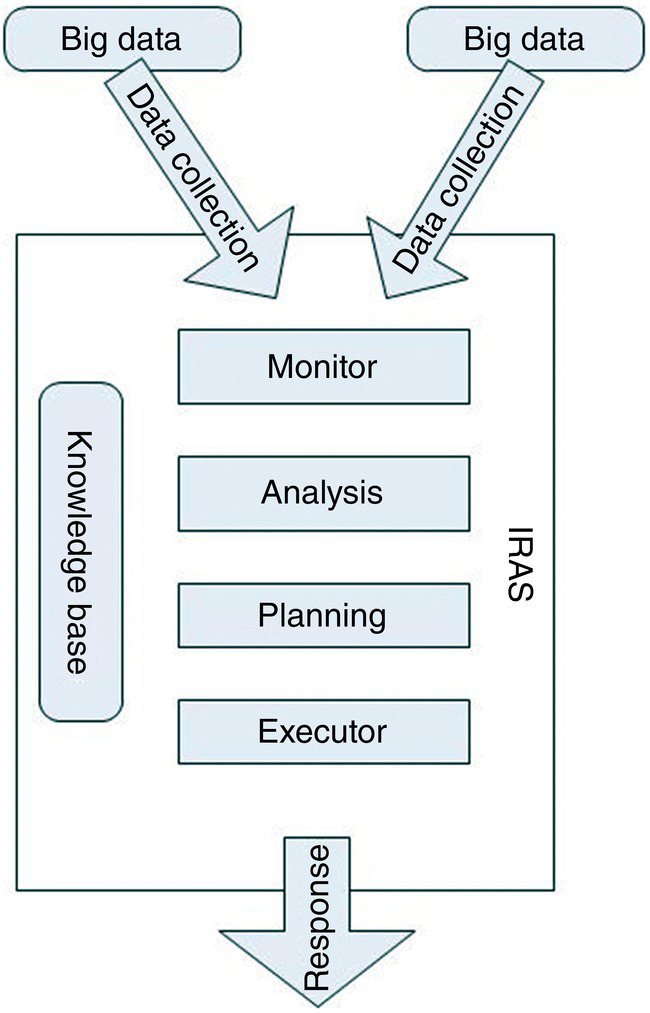
Figure 13.14 Intrusion responsive autonomic system (IRAS).
Internet evolves and the computing infrastructure changes rapidly. All these are happening because more processing power produces more data at every opportunity. Researchers have coined the concept of “Big Data” to refer to data handled by large enterprises like Google, Facebook, IBM, and so on [82]. Lee et al. [83] propose a method to analyze Internet traffic using the MapReduce [84] framework within the cloud computing platform. They compare their results with Hadoop [85] and other tools concluding 72% improvement in computational efficiency. Tripathi et al. [86] also study characteristics of DDoS attacks in the cloud and developed a scheme to detect such attacks in a Hadoop‐based environment. Lee et al. [87] also provide two algorithms to detect DDoS attacks using packet tracing method in a MapReduce environment.
Govinda and Sathiyamoorthy [88] introduce a process of clustering the traffic into different groups. These groups are flash traffic, interactive traffic, latency sensitive traffic, non‐real time traffic, and unknown traffic, as shown in Figure 13.15. They use Hadoop technology to analyze big data traffic. If any of these packets is categorized as unknown traffic, it is identified as a part of DDoS attack and eliminated by the packet analyzer.
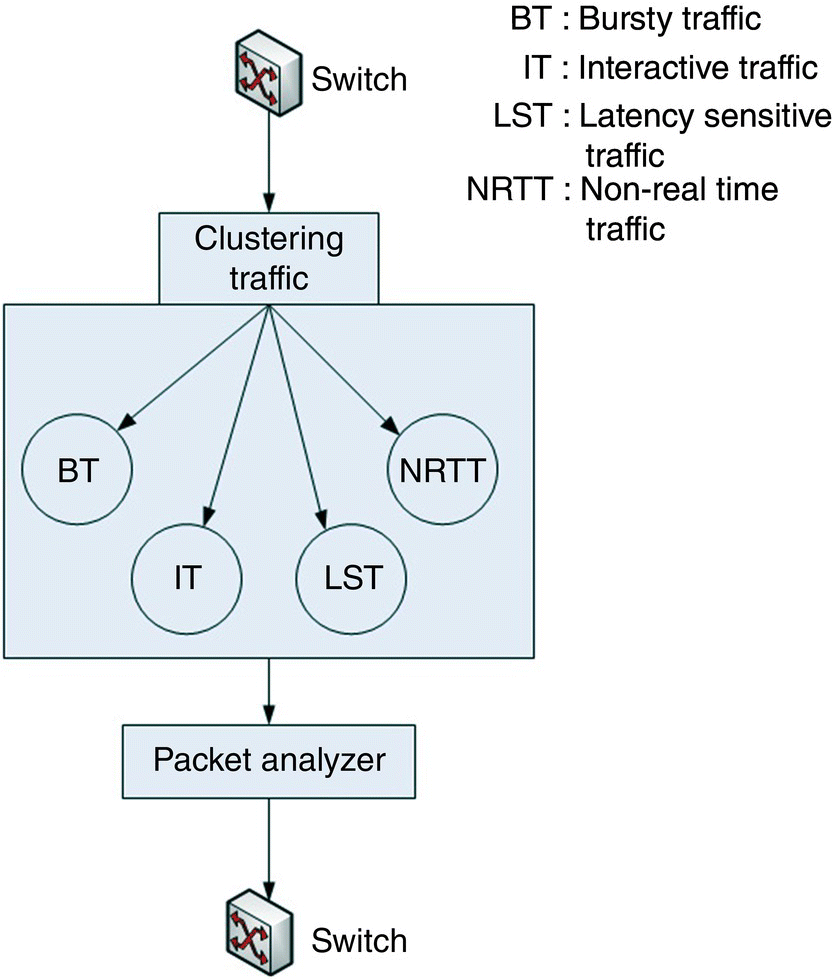
Figure 13.15 Traffic cluster analysis by [88].
Source: Based on Govinda, K., and Sathiyamoorthy, E. (2014). Secure traffic management in cluster environment to handle DDoS attack. World Applied Sciences Journal, 32(9), 1828–1834.
Table 13.3 Selected approaches handling DDoS attacks.
| Authors | Key points | Real‐time | High rate/Low rate |
|---|---|---|---|
| Lua and Yow [17] |
|
Yes | Does not depend on rate |
| Wang et al. [20] |
|
Yes | Not mentioned |
| Ioannidis and Bellovin [46] |
|
Yes | High rate |
| Yau et al. [47] |
|
Yes | High rate |
| Chen et al. [49] |
|
Yes | Does not depend on rate |
| Kong et al. [51] |
|
Yes | Not mentioned |
| Bangalore and Sood [52] |
|
Yes | Does not depend on rate |
| Mankins et al. [54] |
|
Yes | Not mentioned |
| Khattab et al. [55] |
|
Yes | High rate |
| Yu et al. [19] |
|
Yes | Does not depend on rate |
| Nguyen et al. [74] |
|
Yes | Not mentioned |
| Xu et al. [75] |
|
Yes | Not mentioned |
| Jiao et al. [79] |
|
Yes | Not mentioned |
| Vieira et al. [81] |
|
Yes | Not mentioned |
| Tripathi et al. [86] |
|
Yes | Not mentioned |
| Lee et al. [87] |
|
Yes | Flow/Rate analysis |
| Govinda and Sathiyamoorthy [88] |
|
Yes | Traffic analysis |
13.3.1 Discussion
The approaches discussed in this section are presented compactly in Table 13.3. We can summarize our discussions in the following observations:
- It is necessary to build a real‐time defense system, whether it is network based or host based.
- Incorporating dynamic behavior in the solution can provide adaptability to the defense.
- The discussed methods employ the tolerance approach. Thus, allocating and utilizing resources effectively can provide a good defense.
- As cloud computing systems incorporate traditional network topology and also new resource sharing methods, defense solutions against DDoS in the individual private cloud environment need to evolve to adapt to both.
- Resource utilization in a virtualized cloud computing environment is important. So, resource sharing and utilization need to be smooth enough to provide services along with security.
- In a large infrastructure network, the converging network traffic will be always high enough for analysis. New data analysis techniques need to be adapted for better defense.
13.4 Challenges and Issues with Recommendations
A service provider usually has adequate amount of resources for specific service seekers. Challenges and issues regarding DDoS defense in limited resource environment of cloud are listed below.
- For a cyber‐defense tool, effectiveness should be measured in terms of time taken and accuracy of detection obtained in real time. Lack of efficient performance can be a roadblock to large‐scale adoption of any real‐time defense mechanism.
- A mitigation technique for flooding attacks must take into account in system and protocol design to ensure an effective and successful implementation.
- The service provider must ensure that its DDoS attack defense operations neither affect nor are affected by other cloud activities.
- If the cloud provider has only the resources required to provide services to its customers but not much more to defend, this may encourage undesirable DDoS attacks if attackers can guess the situation.
- In a private cloud environment, we need to build the defense strategy using virtualization technology [89].
- Resource allocation and VM migration processes are fast‐paced. So, for any approach to defend DDoS attack in such scenario needs to adapt the dynamisms of a network and adapt the topological changes. Along with that, it has to maintain high detection rate showing smooth reaction capability. In other words, a successful defense mechanism must be dynamic and adaptive.
- Patterns for different attacks are different. It is obvious that one cannot build defensive approaches for each type of attack in a private cloud with a particular amount of resource dedicated to each attack.
- No security precautions can guarantee that a system will never be intruded and so at the critical moment when the system is designed, applications still need to provide minimal services to the legal customers.
13.5 A Generic Framework
Based on the recommendations presented earlier, we believe that an automatic host‐based approach emphasizing tolerance can provide better utilization of resources in the cloud environment to respond to DDoS attacks in an individual private cloud. With limited resources, it is necessary to develop a procedure to defend against DDoS attacks and to provide general service. A generic conceptual framework is shown in Figure 13.16. It is a combination of different phases and components. The whole defense module is just a conceptual depiction of cloud‐based defense solution against DDoS attacks adapting concepts borrowed from existing techniques, adapted to a new environment. Detection and prevention phases of this framework incorporate some ideas of the traditional Internet and also tolerance techniques to the cloud environment. The framework, which we discuss below, abides by the recommendations discussed previously.
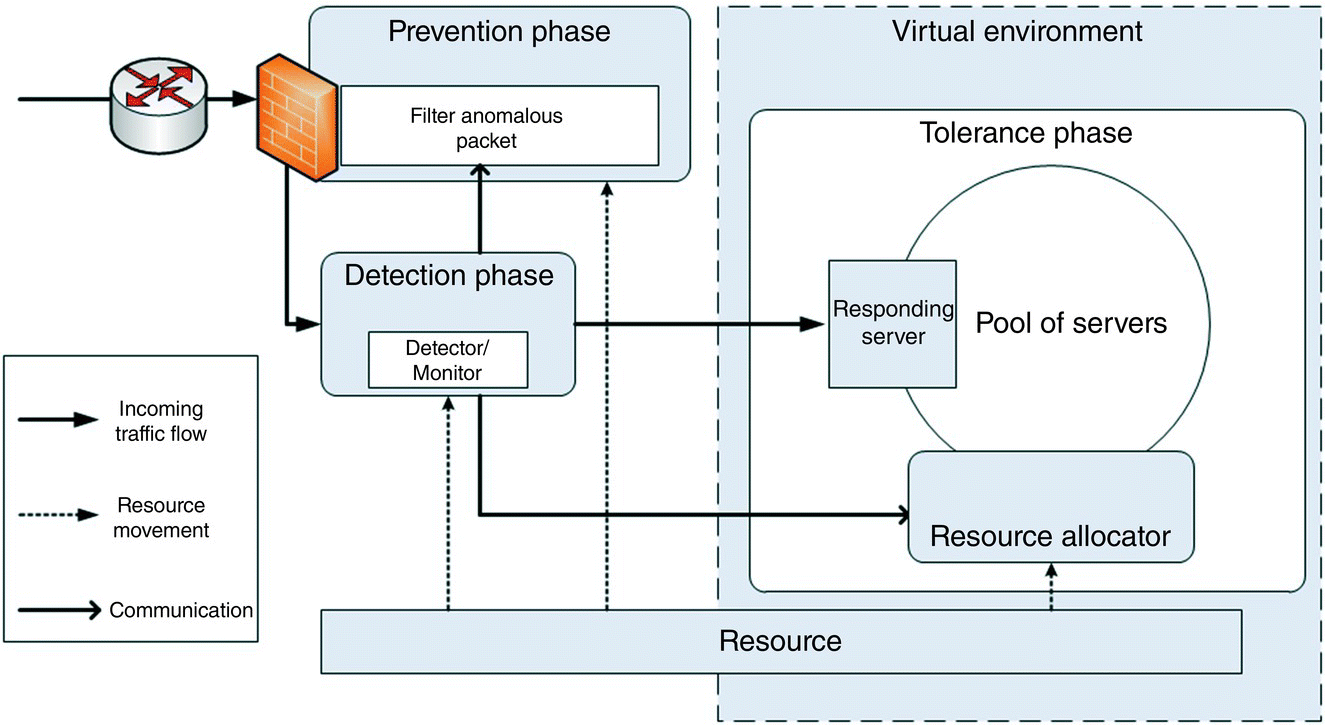
Figure 13.16 A generic cloud‐based defense framework.
- Detection Phase: In this phase, the monitor component analyzes the behavior of the traffic coming to a responding server which handles incoming requests. If the incoming traffic shows any abnormality, the monitor catches it automatically and sends an alert message to the resource allocator. The alert message contains the threat level, how to act to tackle the abnormality, and when to initiate the migration stage. The monitor will also communicate with the prevention component with alert messages about the incoming traffic. This component needs to detect abnormal changes in network traffic in real time.
- Tolerance Phase: In this phase, we can utilize the resources effectively using a virtualization technique available in the cloud environment. For example, the data center or the private cloud provider has the ability to provide the resources to users using virtualization. So, the utilization of the resources should be appropriate for the security needed in a crisis situation since resources are always limited in private cloud environment.
- The resource allocator maintains a queue of fresh server copies to provide services that must be rendered by the responding server. Depending on the level of the alert message, it tries to maintain a dynamic queue of spare resources to fight back if a rapid change in service demands occurs because of any high traffic attack. It can also push unnecessary resources back to the resource pool when the state becomes normal.
- A responding server may be detached from service depending on two things, time and computation load. A server needs to be exposed only for a limited amount of time and if the computation load exceeds a threshold level due to malicious activity, it can be switched to inactive status. Before switching, using live migration we can copy the necessary states of the server to an incoming fresh server so that the usual services can be resumed with minimum delay.
- Prevention Phase: An adaptive and dynamic mapping intrusion response system for effective prevention of DDoS attacks in real time is essential. In the prevention phase, alert messages coming from the detection component need to be analyzed and correlated to discover patterns or strategy in attacks. Using these, we can filter out matching incoming packets later with a low false‐positive rate. If the traffic flow is high, the amount of alert messages may be high enough to analyze. In such a situation, we need to use newly developed data analysis techniques, such as big data analytics to analyze the patterns.
13.6 Conclusion and Future Work
We can definitely say that in the near future, most computing activities and resources will migrate to the cloud and security will be a prime concern. DDoS attacks may be resisted with generic solutions to survive and to provide best services under the circumstances. However, to be successful, more than the usual is necessary in the cloud context. In this chapter, we have discussed issues in handling DDoS attacks, specifically in a private cloud environment. We have highlighted issues and challenges faced in the private cloud environment when providing defense solutions against DDoS attacks. Some useful approaches developed by researchers to address these issues have been presented and analyzed in this chapter. The importance of mitigating the attack by tolerating it and by optimized use of resources in the private cloud scenario has been emphasized. Finally, the role of big data analytics in defending DDoS attacks in the cloud has been introduced.
In the near future, we plan to deploy the conceptual cloud framework in a testbed to demonstrate and analyze the effectiveness of our proposed framework. It is important to know how far this framework can resolve different issues and challenges when defending against DDoS attacks in an individual private cloud environment.
References
- 1 Khorshed, M.T., Ali, A.S., and Wasimi, S.A. (2012). A survey on gaps, threat remediation challenges and some thoughts for proactive attack detection in cloud computing. Future Generation Computer Systems 28 (6): 833–851.
- 2 Deka, R.K., Kalita, K.P., Bhattacharya, D.K., and Kalita, J.K. (2015). Network defence: approaches, methods and techniques. Journal of Network and Computer Applications 57: 71–84.
- 3 Sabahi, F. (2011). Cloud computing security threats and responses. Proceedings of 2011 IEEE 3rd International Conference on Communication Software and Networks, Xi'an, China (27–29 May 2011), pp. 245–249. IEEE.
- 4 Pitropakis, N., Darra, E., Vrakas, N., and Lambrinoudakis, C. (2013). It's all in the cloud: reviewing cloud security. Proceedings of the 2013 IEEE 10th International Conference on Ubiquitous Intelligence and Computing and 2013 IEEE 10th International Conference on Autonomic and Trusted Computing, Italy (18–21 December 2013), 355–362. IEEE.
- 5 Grover, J., and Sharma, M. (2014). Cloud computing and its security issues—a review. Fifth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Hefei, China (11–13 July 2014), 1–5. IEEE.
- 6 Modi, C., Patel, D., Borisaniya, B. et al. (2013). A survey of intrusion detection techniques in cloud. Journal of Network and Computer Applications 36 (1): 42–57.
- 7 Subashini, S. and Kavitha, V. (2011). A survey on security issues in service delivery models of cloud computing. Journal of Network and Computer Applications 34 (1): 1–11.
- 8 Lau, F., Rubin, S. H., Smith, M. H., and Trajkovic, L. (2000). Distributed denial of service attacks. SMC 2000 Conference Proceedings 2000 IEEE International Conference on Systems, Man and Cybernetic:. Cybernetics Evolving to Systems, Humans, Organizations, and Their Complex Interactions Sheraton Music City Hotel, Nashville, Tennessee, USA (8–11 October 2000), 2275–2280. IEEE.
- 9 Peng, T., Leckie, C., and Ramamohanarao, K. (2007). Survey of network‐based defence mechanisms countering the DoS and DDoS problems. ACM Computing Surveys (CSUR) 39 (1): 3‐es.
- 10 Stone‐Gross, B., Cova, M., Cavallaro, L., Gilbert, B., Szydlowski, M., Kemmerer, R., and Vigna, G. (2009). Your botnet is my botnet: analysis of a botnet takeover. Proceedings of the 16th ACM conference on Computer and Communications Security, CCS 2009, Chicago, Illinois, USA (9–13 November 2009), 635–647. ACM.
- 11 Hoque, N., Bhuyan, M.H., Baishya, R.C. et al. (2014). Network attacks: taxonomy, tools and systems. Journal of Network and Computer Applications 40: 307–324.
- 12 Fabian, M. A. R. J. Z., and Terzis, M. A. (2007). My botnet is bigger than yours (maybe, better than yours): why size estimates remain challenging. Proceedings of the 1st USENIX Workshop on Hot Topics in Understanding Botnets, HotBots'07, Cambridge, MA, USA (10 April 2007), 18. USENIX Association.
- 13 Bhattacharyya, D.K. and Kalita, J.K. (2013). Network Anomaly Detection: A Machine Learning Perspective. CRC Press.
- 14 Yu, S., Zhou, W., Jia, W. et al. (2011). Discriminating DDoS attacks from flash crowds using flow correlation coefficient. IEEE Transactions on Parallel and Distributed Systems 23 (6): 1073–1080.
- 15 Xiang, Y., Li, K., and Zhou, W. (2011). Low‐rate DDoS attacks detection and traceback by using new information metrics. IEEE Transactions on Information Forensics and Security 6 (2): 426–437.
- 16 Nguyen, Q. and Sood, A. (2010). A comparison of intrusion tolerant system architectures. IEEE Security and Privacy 9 (4): 24–31.
- 17 Lua, R. and Yow, K.C. (2011). Mitigating DDoS attacks with transparent and intelligent fast‐flux swarm network. IEEE Network 25 (4): 28–33.
- 18 Shah‐Hosseini, H. (2009). The intelligent water drops algorithm: a nature‐inspired swarm‐based optimization algorithm. International Journal of Bio‐inspired computation 1 (1‐2): 71–79.
- 19 Yu, S., Tian, Y., Guo, S., and Wu, D.O. (2013). Can we beat DDoS attacks in clouds. IEEE Transactions on Parallel and Distributed Systems 25 (9): 2245–2254.
- 20 Wang, H., Wang, F., Liu, J., and Groen, J. (2012). Measurement and utilization of customer‐provided resources for cloud computing. 2012 Proceedings IEEE INFOCOM 2012, Orlando, FL, USA (25–30 March 2012), 442–450. IEEE.
- 21 Bhadauria, R., Chaki, R., Chaki, N., and Sanyal, S. (2011). A survey on security issues in cloud computing. ArXiv 1109 (5388): 1–15.
- 22 Zhang, Z., Wu, C., and Cheung, D.W. (2013). A survey on cloud interoperability: taxonomies, standards, and practice. ACM SIGMETRICS Performance Evaluation Review 40 (4): 13–22.
- 23 Wong, F. and Tan, C.X. (2014). A survey of trends in massive DDoS attacks and cloud‐based mitigations. International Journal of Network Security & Its Applications 6 (3): 57.
- 24 Kumar, U. and Gohil, B.N. (2015). A survey on intrusion detection systems for cloud computing environment. International Journal of Computer Applications 109 (1).
- 25 Chiba, Z., Abghour, N., Moussaid, K., El Omri, A., and Rida, M. (2016). A survey of intrusion detection systems for cloud computing environment. 2016 International Conference on Engineering & MIS (ICEMIS), Ibn Zohr University, Agadir, Morocco (22–24 September 2016), 1–13. IEEE.
- 26 Mishra, P., Pilli, E.S., Varadharajan, V., and Tupakula, U. (2017). Intrusion detection techniques in cloud environment: a survey. Journal of Network and Computer Applications 77: 18–47.
- 27 Basu, S., Bardhan, A., Gupta, K., Saha, P., Pal, M., Bose, M., and Sarkar, P. (2018). Cloud computing security challenges & solutions‐A survey. 2018 IEEE 8th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA (8–10 January 2018), 347–356. IEEE.
- 28 Dong, S., Abbas, K., and Jain, R. (2019). A survey on distributed denial of service (DDoS) attacks in SDN and cloud computing environments. IEEE Access 7: 80813–80828.
- 29 Devarapalli, S.J. and Joshi, P.S. (2013). Domain name system security extensions (DNSSEC) for global server load balancing. Google Patents, US Patent 8,549,148, 1 October 2013.
- 30 Mirkovic, J. and Reiher, P. (2004). A Taxonomy of DDoS attack and DDoS defence mechanisms. ACM SIGCOMM Computer Communication Review 34 (2): 39–53.
- 31 Kang, M. S., Lee, S. B., and Gligor, V. D. (2013). The crossfire attack. 2013 IEEE Symposium on Security and Privacy, SP 2013, Berkeley, CA, USA (19–22 May 2013), 127–141. IEEE Computer Society.
- 32 Miao, R., Potharaju, R., Yu, M., and Jain, N. (2015). The dark menace: Characterizing network‐based attacks in the cloud. In: Proceedings of the 2015 Internet Measurement Conference, IMC 2015, Tokyo, Japan (28–30 October 2015), 169–182. ACM.
- 33 Peng, C., Kim, M., Zhang, Z., and Lei, H. (2012). VDN: Virtual machine image distribution network for cloud data centres. 2012 Proceedings IEEE INFOCOM 2012, Orlando, FL, USA (25–30 March 2012), 181–189. IEEE.
- 34 Vissers, T., Van Goethem, T., Joosen, W., and Nikiforakis, N. (2015). Maneuvering around clouds: Bypassing cloud‐based security providers. Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA (12–16 October 2015), 1530–1541. ACM.
- 35 Chaisiri, S., Lee, B.S., and Niyato, D. (2011). Optimization of resource provisioning cost in cloud computing. IEEE Transactions on Services Computing 5 (2): 164–177.
- 36 Idziorek, J., Tannian, M.F., and Jacobson, D. (2012). The insecurity of cloud utility models. IT Professional 15 (2): 22–27.
- 37 Somani, G., Gaur, M. S., and Sanghi, D. (2015). DDoS/EDoS attack in cloud: affecting everyone out there! Proceedings of the 8th International Conference on Security of Information and Networks, SIN 2015, Sochi, Russian Federation (8–10 September 2015), 169–176. ACM.
- 38 Sqalli, M. H., Al‐Haidari, F., and Salah, K. (2011). EDoS‐shield‐a two‐steps mitigation technique against EDoS attacks in cloud computing. 2011 Fourth IEEE International Conference on Utility and Cloud Computing, UCC 2011, Melbourne, Australia (5–8 December 2011), 49–56. IEEE Computer Society.
- 39 Wang, Q., Ren, K., and Meng, X. (2012). When cloud meets Ebay: towards effective pricing for cloud computing. 2012 Proceedings IEEE INFOCOM, Orlando, FL, USA (25–30 March 2012), 936–944. IEEE.
- 40 Yi, S., Andrzejak, A., and Kondo, D. (2011). Monetary cost‐aware check pointing and migration on amazon cloud spot instances. IEEE Transactions on Services Computing 5 (4): 512–524.
- 41 Yan, Q. and Yu, F.R. (2015). Distributed denial of service attacks in software‐defined networking with cloud computing. IEEE Communications Magazine 53 (4): 52–59.
- 42 Deshmukh, R.V. and Devadkar, K.K. (2015). Understanding DDoS attack and its effect in cloud environment. Procedia Computer Science 49: 202–210.
- 43 Darwish, M., Ouda, A., and Capretz, L. F. (2013). Cloud‐based DDoS attacks and defences. In: International Conference on Information Society (i‐Society 2013) (pp. 67–71). IEEE.
- 44 Anwar, Z. and Malik, A.W. (2014). Can a DDoS attack meltdown my data centre? A simulation study and defence strategies. IEEE Communications Letters 18 (7): 1175–1178.
- 45 Fayaz, S. K., Tobioka, Y., Sekar, V., and Bailey, M. (2015). Bohatei: Flexible and elastic DDoS defence. In: 24th {USENIX} Security Symposium ({USENIX} Security 15), Washington, DC, USA (12–14 August 2015), 817–832. USENIX Association.
- 46 Ioannidis, J. and Bellovin, S.M. (2002). Implementing pushback: router‐based defence against DDoS attacks. Proceedings of the Network and Distributed System Security Symposium, NDSS 2002, San Diego, California, USA. doi: 10.7916/D8R78MXV. The Internet Society 2002.
- 47 Yau, D.K., Lui, J.C., Liang, F., and Yam, Y. (2005). Defending against distributed denial‐of‐service attacks with max‐min fair server‐centric router throttles. IEEE/ACM Transactions on Networking 13 (1): 29–42.
- 48 Nace, D. and Pióro, M. (2008). Max‐min fairness and its applications to routing and load‐balancing in communication networks: a tutorial. IEEE Communication Surveys and Tutorials 10 (4): 5–17.
- 49 Chen, R., Park, J.M., and Marchany, R. (2007). A divide‐and‐conquer strategy for thwarting distributed denial‐of‐service attacks. IEEE Transactions on Parallel and Distributed Systems 18 (5): 577–588.
- 50 Dantzig, G. and Fulkerson, D.R. (2003). On the max flow min cut theorem of networks. Linear Inequalities and Related Systems 38: 225–231.
- 51 Kong, J., Mirza, M., Shu, J. et al. (2003). Random flow network modeling and simulations for DDoS attack mitigation. IEEE International Conference on Communications, 2003, ICC'03, Anchorage, Alaska, USA (11–15 May 2003), 487–491. IEEE.
- 52 Bangalore, A. K., & Sood, A. K. (2009). Securing web servers using self‐cleansing intrusion tolerance (scit). 2009 Second International Conference on Dependability, Athens/Glyfada, Greece (18–23 June 2009), 60–65. IEEE.
- 53 Huang, Y., Arsenault, D., and Sood, A. (2010). U.S. Patent No. 7,680,955. Washington, DC: U.S. Patent and Trademark Office.
- 54 Mankins, D., Krishnan, R., Boyd, C., Zao, J., and Frentz, M. (2001). Mitigating distributed denial of service attacks with dynamic resource pricing. Seventeenth Annual Computer Security Applications Conference (ACSAC 2001), New Orleans, Louisiana, USA (11–14 December 2001), 411–421. IEEE Computer Society.
- 55 Khattab, S. M., Sangpachatanaruk, C., Mossé, D., Melhem, R., and Znati, T. (2004). Roaming honeypots for mitigating service‐level denial‐of‐service attacks. Proceedings of the 24th International Conference on Distributed Computing Systems (ICDCS 2004), Hachioji, Tokyo, Japan (24–26 March 2004), 328–337. IEEE Computer Society.
- 56 Sardana, A. and Joshi, R. (2009). An auto‐responsive honeypot architecture for dynamic resource allocation and QoS adaptation in DDoS attacked networks. Computer Communications 32 (12): 1384–1399.
- 57 Touch, J. D., Finn, G. G., Wang, Y. S., and Eggert, L. (2003). DynaBone: dynamic defence using multi‐layer Internet overlays. In: Proceedings DARPA Information Survivability Conference and Exposition (DISCEX‐III 2003), Washington, DC, USA (22–24 April 2003), 271–276. IEEE Computer Society.
- 58 Venkatesan, S., Albanese, M., Amin, K., Jajodia, S., and Wright, M. (2016). A moving target defence approach to mitigate DDoS attacks against proxy‐based architectures. 2016 IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA (17–19 October 2016), 198–206. IEEE.
- 59 Mishra, M., Das, A., Kulkarni, P., and Sahoo, A. (2012). Dynamic resource management using virtual machine migrations. IEEE Communications Magazine 50 (9): 34–40.
- 60 Doob, J.L. (1953). Stochastic Processes, vol. 101. New York;: Wiley.
- 61 Coşgun, Ö. and Büyüktahtakın, İ.E. (2018). Stochastic dynamic resource allocation for HIV prevention and treatment: an approximate dynamic programming approach. Computers & Industrial Engineering 118: 423–439.
- 62 Cui, J., Liu, Y., and Nallanathan, A. (2019). Multi‐agent reinforcement learning‐based resource allocation for UAV networks. IEEE Transactions on Wireless Communications 19 (2): 729–743.
- 63 Mireslami, S., Rakai, L., Wang, M., and Far, B.H. (2019). Dynamic Cloud Resource Allocation Considering Demand Uncertainty. IEEE Transactions on Cloud Computing.
- 64 Jyoti, A. and Shrimali, M. (2020). Dynamic provisioning of resources based on load balancing and service broker policy in cloud computing. Cluster Computing 23 (1): 377–395.
- 65 Shawky, D. M. (2013). Performance evaluation of dynamic resource allocation in cloud computing platforms using Stochastic Process Algebra. 2013 8th International Conference on Computer Engineering & Systems (ICCES), Cairo, Egypt (26–28 November 2013), 39–44. IEEE.
- 66 Banikazemi, M., Olshefski, D., Shaikh, A. et al. (2013). Meridian: an SDN platform for cloud network services. IEEE Communications Magazine 51 (2): 120–127.
- 67 Azodolmolky, S., Wieder, P., and Yahyapour, R. (2013). SDN‐based cloud computing networking. 2013 15th International Conference on Transparent Optical Networks (ICTON), Cartagena, Spain (23–27 June 2013), 1–4. IEEE.
- 68 Yan, Q., Yu, F.R., Gong, Q., and Li, J. (2015). Software‐defined networking (SDN) and distributed denial of service (DDoS) attacks in cloud computing environments: a survey, some research issues, and challenges. IEEE Communication Surveys and Tutorials 18 (1): 602–622.
- 69 Lin, Y.D., Pitt, D., Hausheer, D. et al. (2014). Software‐defined networking: standardization for cloud computing second wave. Computer 47 (11): 19–21.
- 70 Braga, R., Mota, E., and Passito, A. (2010). Lightweight DDoS flooding attack detection using NOX/OpenFlow. IEEE Local Computer Network Conference, Denver, Colorado, USA (10–14 October 2010), 408–415. IEEE Computer Society.
- 71 Gude, N., Koponen, T., Pettit, J. et al. (2008). NOX: towards an operating system for networks. ACM SIGCOMM Computer Communication Review 38 (3): 105–110.
- 72 Shin, S., and Gu, G. (2013). Attacking software‐defined networks: a first feasibility study. In: Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, HotSDN 2013, The Chinese University of Hong Kong, Hong Kong, China (16 August 2013), 165–166. ACM.
- 73 Yuan, B., Zou, D., Yu, S. et al. (2016). Defending against flow table overloading attack in software‐defined networks. IEEE Transactions on Services Computing 12 (2): 231–246.
- 74 Nguyen, M., Pal, A., and Debroy, S. (2018). Whack‐a‐mole: software‐defined networking driven multi‐level DDoS defence for cloud environments. 2018 IEEE 43rd Conference on Local Computer Networks LCN 2018, Chicago, IL, USA (1–4 October 2018), 493–501. IEEE.
- 75 Xu, C., Lin, H., Wu, Y. et al. (2019). An SDNFV‐based DDoS defence technology for smart cities. IEEE Access 7: 137856–137874.
- 76 Sahoo, K.S., Puthal, D., Tiwary, M. et al. (2018). An early detection of low rate DDoS attack to SDN based data centre networks using information distance metrics. Future Generation Computer Systems 89: 685–697.
- 77 Bhushan, K. and Gupta, B.B. (2019). Distributed denial of service (DDoS) attack mitigation in software defined network (SDN)‐based cloud computing environment. Journal of Ambient Intelligence and Humanized Computing 10 (5): 1985–1997.
- 78 Chen, Z., Jiang, F., Cheng, Y., Gu, X., Liu, W., and Peng, J. (2018). XGBoost classifier for DDoS attack detection and analysis in SDN‐based cloud. In: 2018 IEEE International Conference on Big Data and Smart Computing, BigComp 2018, Shanghai, China (15–17 January 2018), 251–256. IEEE Computer Society.
- 79 Jiao, J., Ye, B., Zhao, Y., Stones, R. J., Wang, G., Liu, X., Wang, S. & Xie, G. (2017). Detecting TCP‐based DDoS attacks in Baidu cloud computing data centres. In 2017 IEEE 36th Symposium on Reliable Distributed Systems SRDS 2017, Hong Kong, Hong Kong (26–29 September 2017), 256–258. IEEE Computer Society.
- 80 Fontugne, R., Mazel, J., and Fukuda, K. (2014). Hashdoop: a MapReduce framework for network anomaly detection. In: 2014 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada (27 April to 2 May 2014), 494–499. IEEE.
- 81 Vieira, K. M., Schubert, F., Geronimo, G. A., de Souza Mendes, R., and Westphall, C. B. (2014). Autonomic intrusion detection system in cloud computing with big data. Proceedings of the International Conference on Security and Management (SAM), Las Vegas, USA (July 2014), 173–178. WorldComp.
- 82 Lohr, S. (2012). The age of big data. New York; Times 11 (2012).
- 83 Lee, Y., Kang, W., and Son, H. (2010). An internet traffic analysis method with MapReduce. 2010 IEEE/IFIP Network Operations and Management Symposium Workshops, NOMS 2010, Osaka, Japan (19–23 April 2010), 357–361. IEEE.
- 84 Dean, J. and Ghemawat, S. (2008). MapReduce: simplified data processing on large clusters. Communications of the ACM 51 (1): 107–113.
- 85 White, T. (2012). Hadoop: The Definitive Guide. O’Reilly Media, Inc.
- 86 Tripathi, S., Gupta, B., Almomani, A. et al. (2013). Hadoop based defence solution to handle distributed denial of service (DDoS) attacks. Journal of Information Security 04 (03): 150–164.
- 87 Lee, Y., Kang, W., and Lee, Y. (2011). A Hadoop‐based packet trace processing tool. In: International Workshop on Traffic Monitoring and Analysis, 51–63. Berlin, Heidelberg: Springer.
- 88 Govinda, K. and Sathiyamoorthy, E. (2014). Secure traffic management in cluster environment to handle DDoS attack. World Applied Sciences Journal 32 (9): 1828–1834.
- 89 Clark, C., Fraser, K., Hand, S., Hansen, J. G., Jul, E., Limpach, C., Pratt, I., & Warfield, A. (2005). Live migration of virtual machines. In: Proceedings of the 2nd conference on Symposium on Networked Systems Design & Implementation. Vol. 2 (pp. 273–286).
Notes
- 1 http://www.arbornetworks.com accessed June 2020.
- 2 https://blog.cloudflare.com/network‐layer‐ddos‐attack‐trends‐for‐q1‐2020/ accessed June 2020.
- 3 https://www.theguardian.com/technology/2016/oct/26/ddos‐attack‐dyn‐mirai‐botnet accessed February 2020.
- 4 https://aws.amazon.com/cloudwatch accessed August 2019.
