18
Legal Entanglements of Cloud Computing In India
Sambhabi Patnaik and Lipsa Dash*
KIIT School of Law, KIIT University, Bhubaneswar, India
Abstract
Technology has never failed to surprise us! The legal aspects of cloud computing is integral for us to understand the complexities and challenges that an individual has to deal with under the Indian regime. Data ownership, intellectual property issues, privacy concerns, cyber security issues, intermediary liability, government surveillance powers and interoperability are a few threats involved in cloud computing. Cloud service providers handle sensitive personal information and any breach/leakage could attract legal actions. “Right to Privacy” was recently declared as a Fundamental Right under Constitution of India. The Personal Data Protection Bill, 2019 in India recognizes right of privacy as a natural right and has paved the way for a transformational shift towards safeguarding personal data which is an essential aspect of informational privacy, thus, keeping pace with the rapid digitization the country is experiencing. The worldwide accessibility and usage of cloud computing makes the choice of law and jurisdiction a pertinent concern for the larger perspective of the worldwide legal framework and India’s interaction with the same. The authors will also analyze different international laws to curb the problems, bridge the gap and simplify the international issues in cloud computing.
Keywords: Privacy, data protection, cloud computing, Information Technology Act 2000, sensitive personal information, cyber security
18.1 Cloud Computing Technology
Cloud computing is a rapidly growing configured technology which has significant demand and is an effective platform for organizations and individuals to share their resources. The users, service providers and the businesses requiring these IT services are acquainted with the needs to combat the risks associated with it. Every year, billions is spent in the IT sector innovations. The service providers are leveraging the cyberspace and the physical world to achieve their goals which might be for the greater good. Services of the cloud include a stack of layers namely Infrastructure as a service (IaaS), Platform as a service (PaaS) and Software as a service (SaaS) having different functions. The services might be paid or free depending on the service provider’s discretion. IaaS is the Information Technology infrastructure which belongs to the cloud provider and this infrastructure is used as a platform. PaaS, is where a developer manages to develop, test and maintain the created software applications and mobile apps without worrying about the storage, network or other requirements. The supply of software applications as per subscriptions by the users are delivered under the SaaS layer. The cloud helps store and recover data in huge quantities. The cloud can be a public, private or hybrid cloud based on architectural model and beneficial for organizational sectors like IT, telecom, healthcare, hospitality, entertainment and educational, etc. It is considered as one of the most impactful economic innovations of this century. Companies rely on cloud services for cost savings, flexibility and its easy accessibility resulting in exponential and potential growth of the technology. They are more centralized, offering stricter privacy policy and quicker responses to cyber security breaches and compromises. A few service providers are highly trusted in the use of sophisticated technical service. The structure of the internet and the constant innovations in the IT field widely impacts the society. The whole architecture of cloud is to prevent breach of the security and provide privacy of stored data with high encryption tools and techniques. The strength of each type of cloud is different depending on its shape and size. It is a virtual space leading to save energy and time thereby assuring a quality service simultaneously.
However, the virtual environment of cyberspace is vulnerable to cyber attacks and monitoring them is expensive [1]. The cyber security threat is increasing rapidly and thus overcoming its impact has become difficult. Cloud computing has an adverse effect on the cyber security as it detaches computers and other devices and stores information on a huge space that is solely dependent on the internet. The vendors and stakeholders pay a hefty price for high security firewalls to protect data of clients from cyber attacks.
The social benefit derived from resource pooling includes facilitating innovations which are agile, scalable and cost reducing. The cloud enables convenient working model and on-demand network access to a shared pool of configurable computing resource networks (servers, storage, applications and services). The cyberspace fundamentally shapes the nature of cyber threats and the widespread nature of the internet is one of the main reasons of cyber insecurity. The dilemma of stronger encryption is highly required as they have proved to be the best protection mechanism for all the sensitive personal information in the information networks and systems. However the probability of creating a rift between law enforcement bodies, technology companies and other government organizations is relatively high. The extensive implementation of the strong encryption technologies limits a few law enforcement bodies access to the cloud’s data [3]. The cryptographic standards and their implementation in the cloud increase the safety standard. Easy access to data because of the indefinable structure of cloud contributes to cyber threats. In the cloud the actual data exists giving exposure to high risk of sensitive data loss even with strong encrypted virtual systems. Those who get access are capable of misusing, causing real damage and targeting the exact vulnerabilities putting the users in highly compromising circumstances. The controls of the infrastructure are kept transparent in terms of security, though both the concepts of sharing and security are slightly contradictory of each other. These resources can be rapidly provisioned and released by service provider interactions and minimal management efforts. The elastic nature of cloud computing gives rise to different service models for their working. Firstly, the acquisition model is based on purchasing of these services. Secondly, the technical model is scalable, elastic, multi-tenant and sharable. Thirdly, the access model brings data over the network to any device. And lastly, the business model is based on pay for use [4]. The Figure 18.1 below depicts the system of cloud computing, its types and model. The picture represents the different types of cloud on basis of their location and services and their working including the advantages and disadvantages of the same.
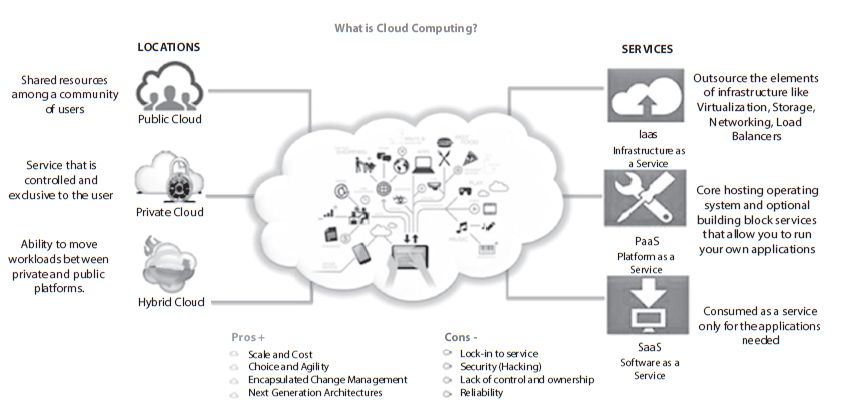
Figure 18.1 Which depicts the system of cloud computing, its types and model [2]. Ihe picture represents the different types of cloud on basis of their location and services and their working including the advantages and disadvantages of the same.
The belief of this generation is that computing is the backbone of advanced technology for the upcoming decade. The agreement or standards to use the cloud exists but it lacks in successful implementation both by people and legislations to end the dichotomy of trust and control. A virtual access layer in the cloud can be protected by a security service layer. However, the security network layers are obviously kept a secret as no one would go public with their security infrastructure, keeping the weak links undisclosed to prevent breaches. In March 2020, during the pandemic of Covid 19 it was declared that few service providers would provide free cloud computing platform to researchers to save data collected for accelerated research, innovation and development using cloud computing. The workflow of cases becomes smoother as it removes cost limitations and other barriers. There is an internal team working on deployment of the resources around the world. Many artificial intelligence bots are created using the cloud and a natural conservation of data is experienced [5]. Cloud helps in task management by integrating huge amount of data and organizes it in the cloud for the users. Racks of servers are disintegrated in accordance to required resources and virtual servers are created individually as cloud. The economic aspect for the cloud providers is also definitely one of the cost beneficiary roads to be considered. The returns of their investments by an effective monetization strategy is very important which leads to resource bundling options, licensing and making different priced models affordable. A range of applications are cloud hosted like Microsoft Suite, ERP applications, CRM applications, etc. The most established players expand their IT infrastructure and create lasting impressions.
18.2 Cyber Security in Cloud Computing
When we store any kind of data on our individual smart phones, we would like to believe that we have secured these data with a security lock (pattern lock, biometric security features, etc.) on our devices. But, the question arises, is it absolutely safe in the real sense? Moreover, what about those data which we upload on our Google drive, iPhone cloud or any other cloud services offered by mobile operating systems? Are there chances of hacking of these data and unauthorized dissemination of the same? Cyber criminals are on the rise and use various available platforms to level up their game. They are no longer stuck to age old desktops but are expanding their wings to other available resources be it, mobile phones, tablets, smart devices and Voice over Internet Protocol technology (VoIP). It can be seen that VoIP has become a preferable medium for cyber criminals to carry out data theft, financial frauds and other crimes. One would be surprised to see the extent that cyber criminals would go to carry out malware attacks via social engineering. For example, it is very common to see how an attacker tricks any naive user over the internet and gains their confidence which later helps them to execute malicious code on the user’s system. Cloud services also come under the radar for such kinds of attacks because the attacker wants to take advantage of the massive amount of sensitive data available over cloud.
Cloud security can be achieved with a system that includes government policies, procedures, various control mechanisms and its related technologies that cooperate as a single entity to ensure protection of data stored and available in the cloud’s infrastructure. The service providers have security measures to protect data/information in the cloud and protect each client’s privacy. These security features can help in compliance with mandatory regulatory framework as well as can help in establishing authentication regulation for individual users and their devices [6]. Users have come across various cyber security threats which make the cloud a high risk premise. With each passing day, the natures of threats are constantly changing. Their sophisticated features makes it even more pertinent for any individual or business enterprise to use cloud providing customized security features for the protection of the user’s most valuable possession, i.e. data. The implementation of cloud security is not an individual entity’s job but a joint responsibility of the business owner and the solution provider.
18.3 Security Threats in Cloud Computing
A cloud involves ample collection of processors, memory, computer applications and other resources, connected together to the World Wide Web. Cyber attackers are always on the prowl to find the security lapses and cloud vulnerabilities with mala fide intentions. Protection and security of software and data will top the list of concerns when there is an involvement of a third party outsourcing the services making it further inaccessible for the organization’s firewall (security) system. It is of utmost importance to be aware as to where exactly one’s system could be at risk, and what one can do about fixing the loopholes and system vulnerabilities. Some of the major cybersecurity threats that could affect one’s cloud computing services are discussed below.
18.3.1 Data Breaches
This is the easiest and the most recurring threat in cloud computing. Hackers majorly get attracted towards cloud service providers because of the availability of huge amount of data stored on the clouds. Data breaches can majorly lead to unauthorized access to one’s cloud accounts by cyber criminals which further can cause loss/leakage of data. These breaches can expose financial information, personal information; if related to health, intellectual property of an organization, etc. resulting in severe damage. Data breach attracts legal liabilities as they result in violation of various legal compliance and contractual obligations.
18.3.2 Denial of Service (DoS)
The DoS attack is one of the common destructive threats against cloud computing. Stopping the DoS attacks, are mostly impossible so one might not be able to mitigate its effects only. DoS attacks usually subdue resources of a cloud service making users unable to access data or resources. This kind of attack is capable of making the cloud services shut down by sending massive amount of web traffic, which further affects the servers. Servers are backbone of any business and the DoS attack will directly hit them by making it inaccessible for any kind of buffering and processing. If any business is entirely dependent on cloud services, then it will be doomed by such deadly DoS attack.
18.3.3 Botnets
These robots are malware programs that slyly get installed on a system helping an unauthorized person to remotely access and control the system for carrying out any malicious activity. Botnets are considered dangerous for cloud security as compared to other malware, because they have a distributed platform which can provide a hot bed for all cyber criminal activities over the cloud. For example, a botnet can be used to spam any operation system by blasting out millions of messages. Botnets are useful for an attacker who wants to crack open password-protected or encrypted information.
18.3.4 Crypto Jacking
It is a fairly recent form of cyber attack which indulges in mining for cryptocurrencies like bitcoin. The attackers can easily access computing systems/resources from one’s cloud system which can make one’s operation slow while the program still runs. Therefore, detection of this attack is complicated and can easily go under the radar. Many just believe that there is either processing issue or slow internet issue while their system is being crypto-jacked.
18.3.5 Insider Threats
It is a common belief that cyber criminals/hackers are major cyber security threats for cloud services. However, it is surprising to know that security issues can not only originate from outside but inside as well because of their unique position and access to networks and systems. As the name suggests, threats which can occur from the organization itself. Insiders (staff, employees and administrators) of the organization or cloud service providers might abuse their authorized access or because of their negligence and error can become the threat. Sometimes, a malicious insider can cause more harm than an outside attacker. The malicious insider might be a revenge seeking previous employee or a present member of the organization, or an accessory with the credentials intentionally gaining access and misusing the secured information. Therefore, organizations have to be alert and keep a tab on any cyber criminal activity caused by their employees and make full proof off-boarding process, which will make sure that the access of employees is deactivated after they leave the organization.
18.3.6 Hijacking Accounts
This is one of the most explored cyber crimes to date. Hijacking can easily be done by employing various techniques like phishing, password cracking which becomes easy for cyber criminals to access numerous accounts, including cloud services. Hackers once having secured access to accounts can create havoc easily while the users are unaware of the occurrence of a crime. Proper training, permission management and end user agreements can be some basic techniques to minimize the risks associated with such attacks. Organizations and celebrity cloud accounts are extremely vulnerable to such hijacking.
18.3.7 Insecure Applications
Securing your own applications, systems and network sometimes is not enough as one might get a threat form an external source even though downloaded from authentic app stores. Any third-party service or application has the potential for serious cloud security risks, even though the organization’s own system is well insulated against most common cyber threats. Therefore, it is highly advisable that proper precautionary measures should be followed while installation of any third party applications as to its viability and security to the organization’s own network. It is usually discouraged to download an external unauthorized file by a member of organization without proper approval of the IT team of the organization, whose primary business involves securing client data.
18.3.8 Inadequate Training
A few instances of cyber attacks can be seen to have been caused by employees due to their negligence in their conduct. This can sometimes be due to lack of seriousness of threat of a cyber crime or mishandling of a threat. Therefore, it is advised by the experts that each and every member should be trained from time to time, which will equip them with updated and adequate information and can help in early detection resulting in timely handling of any kind of cyber threat, specially to cloud services [7].
18.3.9 General Vulnerabilities
Users of cloud services use different web browsers to navigate and maximize various services offered by cloud service providers. Web browsers also have their own share of cyber security vulnerabilities via which different malicious code gets executed and perform malicious activities on the user’s computer, without the knowledge of users. For instance, Cross-Site Scripting (XSS) is a threat that can affect the user system as it can install malicious script into web pages, while a user is using the web browser.
18.4 Cloud Security Probable Solutions
18.4.1 Appropriate Cloud Model for Business
It is advisable for organization to opt for private cloud service model over public cloud service for their businesses. Public clouds are cost effective than private clouds, which makes it popular. Private clouds have been proved to be more secure than the public clouds as these are used by only one single entity. Business involves financial transactions, confidential information and trade secrets, which makes private clouds the safer option over public clouds. Therefore, choosing the appropriate cloud model for any business is the very first step against any cyber security issues.
18.4.2 Dedicated Security Policies Plan
Strategies always make it easier in shaping the future of a system and prepare one to handle all kinds of risks, which makes security strategies even more crucial. Therefore, service providers of the cloud have explicit security policies which guarantee data security. Users or organizations, being more aware these days, will not trust any service provider with their client information, which does not have a formalized security policy.
18.4.3 Multifactor Authentication
This kind of authentication is common today for anyone using net-banking or making a digital payment. This simple method can be effective for any service provider against any kind of threat. For instance, the cloud providers provides the multilayered authentication system to secure its data with the help of one time passwords, captchas, image identification, user behavior authentication and mobile codes. Even if a hacker tries to access by unlocking through password, he will not succeed. The data owner has exclusive access on his device to the one time password required for authentication, making the hacker’s attempt futile to login and access the data. Multifactor authentication is a good arrangement to make the level of protection of data more stringent [8].
18.4.4 Data Accessibility
This is one of the most basic and crucial step towards protecting data over cloud against any misuse. The access to data should be very limited and must be given to administrators only. This restricted access will be instrumental in providing the much required security to the data over the cloud with enhanced protection. A large number of cloud applications provide unpaid programming trials and openings in administration to probable attackers, having client collaborations. These attackers might take advantage by downloading or signing in Denial of Service attacks, through spammed emails, or a system to extort through computerized clicks. The cloud service supplier has to be equipped with a strong team and IT experts who being in charge of controlling the quality of the structure can come up with unique solutions by observing their own cloud condition in such situations.
18.4.5 Secure Data Destruction
The lifecycle of data also includes destruction of the data which needs to be done securely. Data not destroyed under careful supervision can be retrieved anytime and misused. The risks of data leakage and misappropriation of the same will always be lurking, in case of unsecure data destruction. One has to be careful and be aware of the information annihilation process of the cloud services. All sensitive and classified information will be at risk, if the service provider does not appropriately pulverize information which is no longer required.
18.4.6 Encryption of Backups
Data, being the primary subject of cloud service, needs to be backed up in regular intervals to prevent loss of data. Whenever data over cloud is being backed up, it needs to be secured. Encryption of cloud backups of data is necessary to avoid data compromise. A hacker can easily get access to these data which will no longer be secured, if data backups are not protected with appropriate encryption methods. Data, at all times, during its entire lifecycle should be protected from all kinds of intrusion.
18.4.7 Regulatory Compliance
Compliance is a crucial aspect for any organization and these entities must ensure that effective governance, risk and compliance, regular audit processes exist for achieving required security standards to their cloud services. The chapter in the later part deals with it in details.
18.4.8 External Third-Party Contracts and Agreements
Security standards have to be spelled out with specific onus of liabilities in cloud service agreement, as it might involve more than a single entity. Whenever, the cloud service provider is subcontracting, there is involvement of a cloud merchant who has access to massive amount of classified data that might be manhandled by another supplier while storing. The general security of the data chain must be maintained at all times, otherwise the guarantee of complete security against any cyber attack as provided by the seller might be compromised [9].
18.5 Cloud Security Standards
The Cloud Standards Customer Council (CSCC) has been established as “an end user advocacy group which is devoted to accelerate cloud’s successful adoption, lying down the standards, catering to security and interoperability issues which usually surround the transition to the cloud”. It is reported that majority of leading organizations from around the world having similar interests have joined the CSCC [10]. The Council has prescribed ten steps that each cloud service customer must consider to implement for managing the security of their cloud environment which can help them to handle the cloud security risks. Each step has its own cloud specific security standards and certifications which can be utilized for a safe and secured cloud environment. Following are those ten steps:
- Ensure effective governance, risk and compliance processes exist
- Audit operational and business processes
- Manage people, roles and identities
- Ensure proper protection of data and information
- Enforce privacy policies
- Assess the security provisions for cloud applications
- Ensure cloud networks and connections are secure
- Evaluate security controls on physical infrastructure and facilities
- Manage security terms in the cloud service agreement
- Understand the security requirements of the exit process [10].
18.6 Cyber Security Legal Framework in India
India at present does not have an exclusive cyber security law per se; instead what we have is a National Cyber Security Policy, 2013. The policy was framed by the Ministry of Communication and Information Technology aiming at encouraging all organizations to implement best international practices by developing security policies coordinated with their business model and strategies. The policy has laid down certain recommendations for creating a secure cyber ecosystem which can strengthen existing legislations and create methods for detection of security threats on time and managing corresponding responses to avoid such threats. The National Cyber Security Policy, 2013 is expected to be updated in 2020.
Currently, India regulates cyber security issues, with the aid of the IT Act 2000, IT rules and regulations framed there under. The provisions of the IT Act 2000 can be made applicable to cloud services in India as it uses digital medium and is rendered over the internet. The Act also has provisions for the constitution of Computer Emergency Response Team (CERT-In) read with the Information Technology (The Indian Computer Emergency Response Team and Manner of Performing Functions and Duties) Rules 2013 (the CERT Rules). CERT is the nodal agency that is bestowed with the responsibility of collecting, analyzing and disseminating information of any incident in the cyber world and also assists in providing emergency mechanisms to control cyber incidents. The protected system of various organizations, identified under the IT Act 2000, must adhere to the information security measures as laid down under the “Information Technology (Information Security Practices and Procedures for Protected System) Rules 2018 (the Protected System Rules)” to mitigate any security threats.
Legislation other than IT Act 2000, such as the Indian Penal Code 1860, The Companies Act, 2013 read with the Companies (Management and Administration) Rules, 2014 contain laws dealing with cyber security issues. The above mentioned rules under the Companies Act 2013 make sure that companies adhere to measures that can ensure security of electronic records and security systems from any kind of unauthorized access and tampering. In addition to these legislations and rules there are sector specific regulators such as the Department of Telecommunication (DoT), the Securities Exchange Board of India (SEBI), the Reserve Bank of India (RBI), the Insurance Regulatory and Development Authority of India (IRDA). These various regulators regulate entities (banks, telecom service providers and others) by mandating certain cybersecurity standards to be maintained by them. For instance, SEBI requires ISO/IEC 27001, ISO/IEC 27002 and COBIT 5 standards to be followed by stock exchanges, depositories and clearing corporations. The RBI regulates for ensuring protection to sensitive information by mandating banks to adhere to the ISO/IEC 27001 and ISO/IEC 27002 standards. If a situation arises where parties involved have not agreed upon any fixed security practices and procedures under a contract, the organization which is in possession of sensitive personal information would be required to follow a minimum standard provided under IS/ISO/IEC/27001 for safeguarding the same information [11].
The Government of India has come up with various initiatives and beneficial measures for improving cyber security standards in India for different organization for both public and private. The Ministry of Electronics and Information Technology (MeitY) has set up the Cyber Swachhta Kendra (Botnet Cleaning and Malware Analysis Centre) under the very ambitious Digital India initiative. This center will be handled by CERT-In, delegated with the power of tackling issues with internet service providers, product or antivirus companies and will help users to tackle botnet and malware threats. The government in order to create awareness for India’s cybersecurity preparedness and relevant stakeholders in this field has launched online repository on cyber tech called ‘Techsagar’. This repository is the brain child of the National Cyber Security Coordinator and the Data Security Council of India which aims at facilitating the businesses and academia in collaboration and exchange on matters of cybersecurity and innovations [12].
Cybersecurity insurance is creating a wave in different sectors of India and can be seen to have gained popularity in the all the major sectors, including banking, information technology, etc. Like any other insurance, it is will prove to be helpful in protecting online users and victims against any loss arising from any cyber attack.
18.7 Privacy in Cloud Computing—Data Protection Standards
The digitization primarily has acted on improving lifestyle of an average citizen. Individuals, organizations and nations are not fully protected and India is among the top nations in field of cyber crime expecting a higher standard of protection. The data in the cloud is stored and the service providers follow strict international and national privacy policy to avoid legal issues. The regulatory framework of law in India with respect to data protection and privacy is incorporated in the IT Act, 2000 and doesn’t have a sui generis law. There is a bill pending under review of the legislators, “The Data Protection Privacy Bill, 2019” which aims to take care of the collection, storage and dissemination of sensitive personal data and rights and duties of the data subjects and data fiduciaries respectively. The data protection principles are widely laid down in the General Data Protection Rights Law (EU—GDPR). The cloud attracts the storage limitation principle to the extent that the data subject gives freedom to store. All users are entitled the right to restrict the free movement of their personal data. The standard of the protection is maintained by data fiduciaries and personal data is processed with certain restrictions. The protection of the personal data stored between data subjects and data fiduciaries is harmonized. All companies and business bodies are using the cloud to store their electronic data as it provides huge network storage capabilities with minimum efforts to manage the data, making the service provider interactions smooth. It reduces the IT costs and increases efficiency. The transborder data flow turns out to be a threat. The data in the cloud while transcending national boundaries show potential dangers of loss, being compromised or hacked so it’s done within restrictive data privacy and protection laws. Corporations under investigation must make their arguments ready looking into all relevant laws from gathering, reviewing and producing responsive electronic data [13]. Transgression of any law may result in heavy loss to the corporation unless it falls under any exception between legal obligations. Few countries have their own ministries and autonomous decision making bodies to deal with data protection.
Taking the example of Facebook, the data processors use the cloud to archive and analyze the shared information, locations and interests in different posts tracking likes of users and stores it. In 2018, Facebook reported that Cambridge Analytica, a third party application which was also a political consultancy had breached into their system and the data of 87 million people was inappropriately shared [14]. The system wasn’t infiltrated rather the system and its working as designed was flawed. Later Facebook brought the changes and declared that it had successfully changed its DNA hinting at its platform with higher security and user focused privacy requirements. There are two folds of privacy, one being collecting less information and limiting the retention of such data, and the other being limiting the access of information to other people. Backup, recovery, segmentation, fragmentation and duplication are all included. The third party application could be compromised or even lost and irretrievable in a later stage as faced by different companies. The cloud might be getting transferred due to fall of an organization putting people in a skeptical situation about the new environment, posing it as an existing or new threat, bounded by a lock-in period. The choice principle incorporated in data protection here might be at stake. Portability of the data, data provenance, anonymization of the data and data placements makes it risk prone. The procedures of security practices and due diligence to be strictly followed by different organizations is the need of the hour. They can also choose to obfuscate information using techniques of encryption, tokenization, conversion of data to a non-readable format and computational derivation of a value for the original data keeping it in a secure lookup table like the vault [15]. The migration of data includes legal issues in copyright, laws of contract, competition law and other liability fixing legislations.
The personal data privacy guidelines were framed looking into European General Data Protection Regulation, Organization of Economic Cooperation and Development (OECD) privacy guidelines of 1981, the Asia-Pacific Economic Cooperation (APEC), Privacy Framework of 2005; the Data Protection Convention of the Council of Europe of 1981; and finally the European Union’s data protection Directive of 1995 on privacy and other international laws. Apart from EU GDPR other legislations include The UK Data Protection Law, the Swiss Federal Act on Data Protection, Russian Data Privacy Law, The Canadian Personal Information Protection and Electronic Documents Act.
Principles of OECD have national application in most of the developing countries. The set of principles are henceforth discussed to understand their application. The collection limitation principle provides a limit on the means to collect the data lawfully with the proper consent and knowledge of the user. The security safeguard principles protect the data by reasonably safeguarding security from any kind of threat/data loss/unauthorized access, use, modifications, disclosures of data and any kind of destructions. Due to lack of physical measures like biometrics or locked doors the virtual measures are implemented. Theft, erasure or destruction of the stored data will lead to legal consequences. The individual participation principle enables the data subject to obtain any kind of information from the data controller through communication and requests. This principle is followed by the openness principle which states the practice of collecting the information and storage of the personal data is with prior knowledge of the data subject. The accountability principle obligates the data controller to be responsible for compliance of the standards simultaneously allowing free flow of data with legitimate restrictions. Any transborder data flow should be done with due diligence and reasonable care, and security [16].
In India, The Constitution of India recognizes Right to Privacy as a fundamental right. The Contract Act 1972, The Indian Copyright Act 1957, and Indian Penal Code 1860 are a few statutes dealing with privacy regulation. The Sensitive Personal Data and Information Rules 2011 govern the transfer of data which is not equipped enough to face the privacy battles. The data protection draft bill which has been constantly under revision was last revised on December 2019.
18.8 Recognition of Right to Privacy
A certain level of restriction is required to be imposed on the organizations which get hold of the personal information of the public starting from name, age, sexual orientation, preferences, and friends to prevent them from misappropriating personal data of the public. Collection of the personal information could result in loss of life, image, independence, free flow of movement, speech, etc. of an individual. Article 21 of The Constitution of India ensures the “right to life and personal liberty” of every person and with continuous judicial interpretation over time it has expanded its reach to different corners including right to privacy which was recently declared as sacrosanct to every individual in the case of Justice KS Puttaswammy v. State of Kerela (2017) 10 SCC 1. There was however a constant need of making privacy a fundamental part of Article 21 of The Constitution of India. It is now a natural right and not just an elitist construct which is historic for the Indian legal regime decided by the nine judge bench unanimously. Previously, in the case of Govind v. State of Madhya Pradesh [AIR 1975 SC 1378] it was decided that the “right to privacy is not absolute and could be compromised if there is a greater need for public good”. A dynamic data protection law is important to ensure individual’s informational privacy as the introduction of ADHAAR card was criticized by majority due to the high chances of data leakage. The data stored in the cloud server makes it prone to cyber attacks. Right to privacy was categorized in three aspects in the Puttuswamy judgment, as right to bodily autonomy, informational privacy, and privacy of choice. These aspects were also considered by the committee of the data protection bill which was chaired by Shri Justice BN Srikrishna. It also ensures a restricted power to the government. With the internet growing as a disruptive technology in keeping private matters of our lives secure, any data collected that is sensitive and personal in nature, the data subject has to have a choice of how the data is being stored or processed and its distribution and usage. The data that once stored in the cloud can be erased or modified as per the data subject’s choice. The standards of data protection include direction from the data controller to comply with the rules and provide all information to the data subject. Freedom of speech and expression was ensured to protect liberty of citizens and acceptance of criticisms for the welfare of the government and public. To secure a personal life is to include all physical details as well as informational details to set a boundary from interference by the unwanted. As discussed in the chapter later, the liability of intermediaries have undergone a shift from strict to contributory liability.
The Data Protection Bill, 2019 dealing with personal data includes storage in the definition of “processing” under the umbrella of which the cloud can easily be implied to be a part of. The bill defines ‘data principal’ [Section 2(14) of the Data Protection Bill] as “any natural person to whom the personal data is related to and ‘data fiduciary’] Section 2(13) of the Data Protection Bill] as any person (including juristic persons and the State) who is involved in processing of the personal data” [17]. Personal data can include passwords, financial data, biometric data, etc. and all of them require explicit consent of an individual. The bill explicitly mentions and directs the data fiduciaries whose data centers are located in India to keep a ‘serving copy’ of the personal data in their remote servers. The bill has been on extensive debate from different stakeholders. The data can also be categorized as critical personal data if the central government deems necessary. The Constitution doesn’t confer absolute right and it can be infringed and restrictions can be imposed for larger public interest in coherence with the rule of law [18]. This is also known as the doctrine of proportionality.
There is a primary duty to ensure that the individual has an utmost right on its information along with ensuring public security and safeguard of the general masses. In the case of Modern Dental College & Ors. V. State of MP & Ors. [(2016) 7 SCC 353] the doctrine of proportionality is explained. It was held that if fundamental right is infringed, it should be for a legitimate state purpose and the action infringing the right should be proportionate to the necessity to interfere with the right and more importantly such action should be sanctioned by law. This doctrine is in the form of “reasonable restrictions” in our Constitution as discussed in the case of Kharak Singh v. State of Uttar Pradesh (AIR 1963 SC 1295). The Right to Privacy might be violated only by procedures established by/under the laws to the extent of interference which must be consistent with the need to interfere.
This digitally driven age mandates the need and adoption of a data protection law to uphold human dignity. The IT Act 2000 read along with the IT (Reasonable Security Practices and Procedures and sensitive personal data or information) Rules 2011 contain specific provisions regarding collection, usage and transfer of personal data/information. These provisions of law distinguishes between “personal information” and “sensitive personal data or information” as a subset [19]. The information posted or provided online can be accessed anytime considering the vast storage capacity of the internet and easy accessibility. The existing data protection laws recognize the liability for the failure of protecting sensitive personal data by a body corporate.
18.9 Government Surveillance Power vs Privacy of Individuals
“Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.”—Benjamin Franklin
In a world of digital data transfer, there is a continuous exchange of information internationally, but the security of the information is often compromised. The collection of large quantity information about online user habits has become a vital source of profit. Online footprints of an individual can reveal a lot about the individual. The organizations use this valuable information to target users via online advertisements. The government bodies and political parties have mala fide intentions and are interested to use the data sets for their personal agenda, election campaigning and propaganda.
The Personal Data Protection Bill 2019 highlights on safeguarding data such as a user’s biometrics, financial details, religious and caste beliefs, etc. which can be used for identification of a person. This information collected can be instrumental for the purpose of investigation by concerned authorities. On the other hand, the government can access the personal data for appropriate reasons like national security, sovereignty and integrity of the country to intrude in the lives of the citizen’s privacy which defeats the very purpose of the bill. This flexibility proves to be contrary to the bill’s primary purpose.
Despite being highly secured network service providers, Facebook and Twitter, were using user’s information and sending targeted ads which is clearly a breach of trust. If ever these companies get incentives to collect the government IDs, nothing can then prevent them from breaching user’s privacy.
The outbreak of a pandemic known as Covid-19 has led different government bodies across the globe to take all possible measures and protect the public. In India, to control the spread of the virus, there is constant tracking, collecting and processing of the information about individual’s travel history, symptoms and their contact with affected patients or public in general is recorded by the central government, state government, public health authorities, not-for-profit organizations, corporate and other stakeholders. But the government has failed to provide any sort of guidance or prescribe any boundaries for the data processing activities of aforementioned agencies.
During any government probe or the pendency of a law suit, the organizations might seek access to user’s data available in the cloud for the process of investigation. Few of the Indian laws, such as the Indian Telegraph Act 1885, Indian Wireless Telegraphy Act 1933 under the Department of Telecommunications (DoT) and the IT Act 2000, has provisions that throws light on the instrumental part of being an intermediary thus assisting in legal interception, helping the government and regulatory bodies to access the private exchange of information and data. The Telegraph Act authorizes the government to intercept all kinds of messages, subject to prescribed safeguards, under the grounds of interest of national security, prevention of crime, and public safety as provided under the Act [20]. The IT Act 2000 having similar provisions empowers the government and its authorized agencies to intercept messages. Section 69 of the IT Act 2000 provides that “Any person or officer authorized by the government (central or state) can, it is satisfied that it is necessary or expedient to do so in the interest of sovereignty and the integrity of India, the defense of India, the security of the state, friendly relations with foreign states, public order or preventing incitement to the commission of any cognizable offence relating to the above, or for the investigation of any offence, can inter alia, direct any of its agencies to intercept, monitor or decrypt, or cause to be intercepted, monitored or decrypted, any information that is generated, transmitted, received or stored in any computer resource, in the event it is satisfied that it is necessary or expedient to do so in the interest of sovereignty and the integrity of India, the defense of India, the security of the state, friendly relations with foreign states, public order or preventing incitement to the commission of any cognizable offence relating to the above, or for the investigation of any offence”. The Government has been also empowered to monitor and collect data traffic or any information for the cyber security through any computer resource under Section 69 B of the IT Act 2000. The Information Technology (Reasonable security practices and procedures and sensitive personal data or information) Rules 2011, authorizes governmental agencies to seek for any information including sensitive personal information from a body corporate or service provider, taking prior consent of the data subject, if such disclosure is required under law. However, the IT Act 2000 has provisions to hold a government official liable who has information under their possession and discloses the same information to a third party without prior consent from the provider; shall be liable to pay damages for any wrongful loss suffered by the aggrieved person under 72 A of the IT Act 2000. These provisions prove fruitful for government agencies whenever there is any contravention or investigation of a cyber crime to intercept data for cyber security incidents.
18.10 Data Ownership and Intellectual Property Rights
The nature of the cloud is multi-jurisdictional and this uncertain nature gives rise to complications in intellectual property rights specifically patent laws causing difficulty in targeting potential infringers. When a technology is innovated and patented which uses a cloud service in some other country that helps in processing the data and few other activities, there arises a chance of infringement and the question of data ownership might shift. Each component of the cloud is operated and managed by different parties and subsequently the issue of sub-contracting within the departments leads to attaching different responsibilities and accordingly provides its service to the users. Further this gives rise to divided infringement issues which is one of the biggest shortcomings in our legislative framework. The service provider of the cloud may be liable for inducing the infringers by not protecting the client’s patents in the best interest. According to World Intellectual Property Organization (WIPO), an IP is an asset and in collaboration with different corporations and organizations which accelerates the global economy. The collaboration is easier in the cloud and offers unprecedented advantages in terms of storing and syncing data across multiple devices in the digital world [21]. The cloud enables cross border coordination and smooth access to files in intervals as many organizers sign to stay in the cloud and use the services. These trends definitely have started a concern of protecting Intellectual Property online while identifying trademark/copyright/patent infringements by cybercriminals. The threats that we encounter has already been discussed among the cyber security issues initially in this chapter. Access and privileges of few people makes it riskier and prone to infringements. Most companies restrict users to use their personal phones for work as there are high chances of linking it to the cloud and the loss of a phone will lead to loss of huge amount of data compromising company and its client’s. The files need to be encrypted to make it difficult for the infringer to decrypt the files. Clouds can be equipped with firewalls to protect our intellectual property right and information giving an additional layer of protection to their servers. Along with benefit of the cloud, a company can secure its data safely as the in-built mechanism is encryption. The process of effective encryption and decryption of personal data or sensitive content is to ensure high digital protection and any person trying to break it will be liable under the IT Act 2000. In cloud, neither any unauthorized user nor the service provider can access an individual’s data ensuring strong security. Rigorous and constant monitoring by the technology prevents data breaches and theft. The standard of encryption differs from country to country, where India allows up to 40 bit according to the telecom licensing condition and Section 84 A of the IT Act 2000 but there are countries who allow beyond 256 bit which furthers strengthens the security of the cloud. The service provider has to maintain minimum regulatory standards of monitoring, interception, encryption, decryption, providing minimum and maximum limits to manage the cloud. There are arrangements between countries like the Wassenar Arrangement [22] established to contribute international and national security of dual use technologies promoting transparency and reliability within member states preventing destabilizing accumulations of these technologies. India being a member of the arrangement participates and understands the risks attached to exchange of information of the sensitive technologies. The data’s nature of confidentiality, ideas and expressions, trademarks and brand secrets, designing and software blueprints are attached to the cloud making it targets of potential infringement. The facilitation of exchanging of assents in the cloud is spreading worldwide, whether or not a country signs up for the use. There could be chances of reverse engineering and misuse. The non availability of a definite law to tackle the issue makes the hardware owner, service providers of the cloud, and other parties’ accomplice to the infringement. An international consensus along with a flexible tool and its territorial use to avoid any sort of infringement is necessary. The alarming feature of the cloud, whenever there is an attempt of hacking or attacking a particular IP is communicated to the user giving a chance to stop the breach. Revoking access of public and ex-employees are a few steps to prevent misappropriation of data. Each file has a level of protection in the cloud server giving it a myriad of advantage in storing IP, sharing them and managing collaborative projects working together with people and creating a safe work environment [23]. The Figure 18.2 above depicts a chart that estimates cloud computing market report by the survey of by markets and markets. The comparison is between the regions of North America, Asia Pacific, Europe and rest of the world for the year 2016 to prospective 2023.

Figure 18.2 The estimated cloud computing market report by the survey of by markets and markets [24]. The comparison is between the regions of North America, Asia Pacific, Europe and rest of the world for the year 2016 to prospective 2023.
Technology giants enter into agreements to run these software applications as their assets under the umbrella of intellectual property. The devices and their components are designed as highly sophisticated automation softwares. Due to the technology competition in the market, the tech giants are proving to be the best protector in the market.
18.11 Cloud Service Provider as an Intermediary
Section 2(w) of the Information Technology Act 2000 defines Intermediary means “any person who on behalf of another person receives stores or transmits an electronic record or provides any service with respect to that record and includes telecom service providers, network service providers, internet service providers (ISPs), web-hosting service providers, search engines, online payment sites, online auction sites, online market places and cyber cafes”. Almost all cloud service providers, depending on business model, are considered as an intermediary, according to the above mentioned definition. All cloud service providers/intermediaries will have to adhere to due diligence procedures and compliance under the IT Act 2000 and other relevant laws. Intermediaries being platforms which are gateways that can regulate the sharing and flow of information has always been presumed to have control over content of data being uploaded and shared. In general, data protection laws provide exception from liability to intermediaries in form of safe harbor principles. Intermediaries can only be able to exercise their right of exemption from liabilities if they have exercised due diligence as provided and instructed by the Government timely under different regulations. It is daunting for law makers to make these platforms liable for hosting content that belongs to third parties. The Indian courts have to ascertain the extent of liability and responsibility for intermediaries for facilitating the hosting of any user content. However, the legislature of India has enacted certain provisions specifically for intermediaries:-
- Section 79 of the Information Technology Act 2000 read with the Information Technology (Intermediaries Guidelines) Rules 2011 (which got amended in 2018) mandates intermediaries for implementation of reasonable security practices and procedures for security of their computer resources.
- Cybersecurity incidents are required to be reported to CERT-In by the intermediaries under the Act. Any failure on the part of intermediaries to report such incidents to CERT-In will lead to liability under the Act. The fine will be a sum not exceeding 25,000 rupees. CERT-In may request for information from body corporate, service providers, intermediaries who fail to comply with such request. They are liable to imprisonment up to one year or a fine which may extend to 100,000 rupees, or both.
- The intermediary while discharging his duties under the Intermediary rules 2018 has to take proper due diligence “(1) The intermediary shall have to publish the privacy policy, rules and regulations, and user agreement for access or usage of the intermediary’s computer resource by any person. (2) Such rules and regulations, terms and conditions as included in the user agreement shall inform the users of computer resource not to host, upload, display, modify, publish, transmit, update or share any information that, which might affect public health and safety and Critical Information structure [25]”.
- According to Clause 3 of Section 79 of the IT Act 2000, an intermediary would not be able to take the advantage of exemption “if it has conspired or abetted or aided or induced whether by threats or promise or otherwise in the commission of the unlawful act; or the intermediary upon receiving actual knowledge, or on being notified by the appropriate Government that any information, or communication link residing in or connected to a computer resource controlled by the intermediary is being used to commit the unlawful act, the intermediary fails to expeditiously remove or disable access to that material on that resource without vitiating the evidence in any manner”.
In India, the landmark case for deliberating on the liability of any intermediary by the court is Avnish Bajaj v. State [(2005) 3 Comp LJ 364], which involved the upload of a MMS video clip available on a website and Mr. Bajaj was the CEO of the website. This came under the scrutiny of the public as well as the Court because it was believed, that the content should have been removed from the internet as soon as possible. The video rather went on being circulated rapidly which invited criticism and created much havoc. The Court discharged the Managing Director of the concerned website (Baazee.com) from all criminal charges owing to discrepancies in the provision of Section 292 of the Indian Penal Code.
Internet being so vast and having global reach is difficult to be regulated. It was believed that by introducing liability for intermediaries, law makers will be successful in filtering the unlawful content and they could be equated to that of ‘Gatekeepers of Information’ [26]. India has incorporated the safe-harbor model with respect to the intermediary liability under the cyber law legislation along with other countries which provides for both conditional immunity and complete immunity. The legislation requires these internet intermediaries to exercise due diligence and comply with the regulation requirement to enjoy conditional immunity/protection against liability. The complete immunity is provided to all these facilitators who merely provide the third parties access to information [27]. Initially, the safe harbor principle was rendered to the intermediaries only. The amendment brought to the IT Act in the year 2008 extended the exemption for intermediaries against liability along with amendments to other laws. The exemption from any liability provided to the intermediaries is subject to the fulfillment of requirements as provided under clauses (2) and (3) of Section 79.
Cloud service involves three main stakeholders: the cloud service provider, the customer and the telecom service provider/internet service provider. India lacks an exclusive law on cloud computing governing these three stakeholders together. Department of Telecommunications (DoT) had sought recommendations from Telecom Regulatory Authority of India which is the regulatory body, on different broad aspects of cloud computing. TRAI had also sought views via consultation paper [28] during October 2019 to check whether the industry is capable of self regulating. According to TRAI, cloud service providers can come under the regulation of TRAI. However, currently, these service providers are being regulated under MeitY [29]. TRAI has recommenced amendments for smooth regulation of cloud, which is yet to be incorporated. The Ministry of Information Technology and other government departments needs to work together to implement any of the proposed changes.
Finding the right balance is difficult, but there is definitely the pressing need for intermediaries to maintain the digital freedom. The balance that is required for these gate keepers is to have the freedom to formulate methods/policies for regulation of illegal content and at the same time ensure that there is no compromise in freedom of online medium.
18.12 Challenges in Cloud Computing
18.12.1 Classification of Data
The emerging clashes between the internet engineering, omnipresence of cloud all over the globe and the legal compliance requirement of different individual jurisdictions is a major international concern. A cloud service provider might require data-centers, users, end clients, a team and their resources to keep up the system running in various geographical areas. The regulatory bodies seek compliance of their jurisdiction specific requirements, such as cyber security, privacy safeguard, national security, regulation of content, etc., which will be an intimidating undertaking for the service providers due to the above concern. The global architecture of cloud services is defeated because of such legal compliance requirements.
It is not possible for cloud service providers to classify available data on any given parameters as there is no advanced technology available for the same. However, most legislation requires these service providers to segregate data—lawful/unlawful as a part of their legal compliance. The provisions of section 79 under the IT (Amendment) Act 2008, which is applicable to all intermediaries, including cloud service providers is a good instance of the requirement of the above mentioned data classification. This provision provides service providers to regulate unlawful data and removes it whenever such data comes to the knowledge of the intermediary. But, the irony is that these service providers (including cloud service provider) usually have confidentiality clause signed with its users, which does not authorize them to be aware of the contents of data [30].
18.12.2 Jurisdictional Issues
The new means of delivering in the cloud as the advancement of technology giving a platform to users, allowing remote access of applications, resource allocation from one place to another, is economic in nature while jurisdictional issues accompany them. The law has to operate beyond territorial limits and the theories and precedents are to be followed to fix the jurisdiction whether it is under Civil Procedure Code 1908 or Criminal Procedure Code 1973; tests are applied in different transborder disputes or other dispute resolution mechanism. Every application we use including social media accounts use cloud services globally.
The traditional notions of private international law makes the individual nation’s laws related to jurisdictions applicable to the nationals and any transactions carried out within the customary limits of the country. However, this traditional concept of jurisprudence on jurisdiction is no longer confined within territorial limits, and has evolved to keep pace with the advancement of technology and commerce. The cloud computing system involves an organization in a country, which might be storing data in a cloud located in another country, under control of a different vendor. Therefore, this may give rise to a situation where the laws of all the above jurisdictions are applicable making parties fight for the applicability of law and proper forum of adjudication. Usually to avoid any such situation, organizations decide on the dispute resolution mechanism while drafting and entering into the agreement. Harmonizing the domestic laws to avoid any conflict and determining the appropriate jurisdiction is a difficult task to attain.
Indian legislation grants the parties involved, the right to choose appropriate laws applicable to them, while entering into any contractual obligations. Indian courts also take into account the nexus to the transaction in accordance to the law as agreed in the contract by choice, while deciding any dispute arising out of any such contracts. The Indian Arbitration and Conciliation Act 1996 which is adopted from the UNCITRAL Model Law (as recommended by the U.N. General Assembly) is instrumental in facilitating international commercial arbitration, domestic arbitration and conciliation, taking care of disputes arising from such cloud service vendor agreements. India, being a party to the New York Convention (1960) agreed upon by major countries makes it easier for enforcing foreign decree. The nature of the cloud is dynamic which allows transits, more often leading to jurisdictional claims causing unrest between nations and their citizens. The decision of one country might affect another country as well.
18.12.3 Interoperability of the Cloud
The revolution of technology and the cloud attract the issues of incompatibility, integration and operational complexity. Software portability and interoperability ensures those issues to be mitigated, and the standards of which needs to be widely adopted. It has the ability to exchange information between two or more systems and to mutually use the information. Similarly, cloud interoperability is the ability to interact with the user’s systems or other cloud services by method of information exchange and obtain predictable results [31]. There are five stages of Interoperability. Firstly, the transport interoperability where the exchange of data takes place using physical networks like an external internet or broadband connection. Secondly, the syntactic inoperability which deals with the coding and structure of the stored data. The data may be even coded to different characters to hide the plain text. The semantic interoperability is related to the intended meaning of the written language according to the context and finally the behavior of the service provider [32]. Cloud portability is the transferring of data within clouds without the need of re-entering the data and migrating the applications in the cloud between systems. If an user needs to relocate an application from one cloud to another, needs subscribing to more than one cloud and link their services, connect private cloud to public/hybrid and vice versa or is interested in migrating in-house applications within clouds the mechanism of interoperability is applied. The standards under ISO/IEC 19941:2017 and other recommendations are to be kept in mind to avoid complexities. In India, there is a collaborative effort to address inter-cloud issues to continue using the flexibility along with protecting the data.
18.12.4 Vendor Agreements
The Indian Contract Act 1872 regulates and provides basic principles for all contracts in India, including e-contracts. Section 10A of the IT Act 2000 states that “communication, revocation and acceptance of offer shall not be deemed to be unenforceable solely on the ground that electronic form or means were used for expressing such offer, acceptance or revocation”, thereby making any e-contract (click wrap contracts) valid and enforceable in court of law. Cloud computing service providers offer service agreements that are often biased and non-negotiable as being a standard form of contract. Usually, these agreements do not account for any indemnity, warranties with respect to the data security, and provisions for consequential damages or clause for breach of privacy obligations from limitations of liability [33]. Courts have also held that any standard form of contract including online contracts cannot be held invalid solely on the ground of being non-negotiable by one party. Cloud service vendors often limit their liability up to a certain fixed amount, irrespective of the actual loss faced by the party. Therefore, one has to be very careful while entering into an agreement with service provider and check the extent of responsibility that a service provider is willing to take. Cloud services will play a major role in transforming any organization’s information technology architecture when used appropriately and can even help in cost savings. It is advised that the entity’s legal counsel should carefully negotiate and review agreements entered with cloud service providers, creating a favorable situation for both parties.
18.13 Conclusion
Cloud computing is in emerging stages in India and is facing several problems. It demands automatic on time data backups over a network which can prove to be a manual task, needing a self-healing property. The information can be duplicated in multiple servers. Simultaneously, many users can try to use the feature which sometime creates a rift or conflict, also known as multi tenancy feature that poses a major challenge and needs to be tackled. The cloud fails to handle processing beyond a liner proportion along with simultaneously managing, distributing, processing and protecting the data which puts us in a position to think whether our data is truly safe. The need of clarity with respect to location or jurisdiction, the issues related to its operation, contractual obligations on the stakeholders, issues of security which are persistent and the need of risk management should be our priority. The protection authorities need to have a thorough investigation and the controller has to assert restrictions accordingly. Holding the cloud providers liable for hosting or transmitting any form of illegal data is important. Any exception to this rule should definitely have repercussions. The responsibility is to be specified among the service provider/the board of directors/the company/an individual responsible for any breach or leakage and hold them accountable for the security of user’s data and information. The parameters to track the agencies are to be widened beyond the location as these can be difficult to track due to multi-layering and multiple locations of servers. India not being a signatory to the Budapest Convention of cybercrime is in a situation to rethink the necessity of adoption of legal principles of the convention. The free flow of data across the internet is to be controlled and standards of privacy are to be maintained. Indemnifying the providers is a need not to keep the user stranded in a situation of loss. The clause of indemnification is important in an agreement entered by data fiduciary and data subject.
The cloud is in the hands of data fiduciary; however the ownership of any kind of personal information should be exclusively vested on the data principal. The entity involved in storing, processing or retaining of the data should behave like custodians and not owners having rights over the data. The payment for the cloud service should be for custody of the personal data and not for the ownership. Any processing of the data by the cloud service should be consensual. The consent of the data principal should be our utmost priority. Non-consensual data storing or processing will lead to illegitimate interest and liabilities. The Supreme Court in the Puttuswamy judgment commented on non-consensual processing of personal data stating few circumstances where considerations like criminal investigation, prevention strategies, and allocation of resources or need of national security could be required. The data collected by the government should be to the extent of regulatory functions, keeping in mind the data quality principle providing welfare benefits and social service. The creation of the Data Protection Authority under the bill for handling the body should be given independent authority to work consisting of its own committee. Cloud computing comes with its own share of unique hurdles as well as massive opportunities because of its multi-jurisdictional nature. Different regulators from around the world are wrestling to find unique mechanisms exclusively for cloud computing. Cloud computing is a growing business model which will be regulated by the standards as fixed by the big players of the industry. In absence of an international code, we have witnessed that cloud computing is regulated through few bilateral agreements between governments and multinational corporations. A comprehensive robust international policy or treaty has become a vital requirement that can address various aspects of cloud computing across the globe like jurisdictional issues, different regulatory schemes of nations, etc. by setting up a uniform standard for all nations to adhere to while making their own domestic laws. There have also been few alternative suggestions for addressing conflicts between nations stemming from cloud computing issues. Conflicts pertaining to issues like ownership of data, security of data, privacy of an individual, etc. can be resolved via creating of private-public Memorandum of Understanding (MOUs) between large data center operators and different sovereign governments. The legal framework of safe harbor principles of the European Union and the US can be used to establish a multilateral agreement for all nations for addressing issues of cloud computing.
Currently, our nation lacks an all-inclusive legislation for protecting privacy and protection of data which can aid in regulating issues of cloud computing. The IT Act 2000, with its present form does limited justice for regulation of cloud computing services. It can be witnessed that there has been a sharp rise in number of internet users across pan India because of various government initiatives like ‘Digital India’ promoting public to go digital. National Digital Communications Policy-2018 conceives that India will become a global hub for cloud computing, data communication systems and services, content delivery and hosting, by developing the required regulatory model for the same [28].
One of the challenges that cloud computing in India is facing is the lack of trust for the service providers and the public’s comparative unfamiliarity with the working of this technology. These providers can easily be compelled to disclose any information, including sensitive information, by different government agencies which do not even require an order from the Court. Different departments of government also have their share of inhibitions from using cloud services for their work as they are of the opinion that data is not safe when stored over clouds. Indian law makers need to review existing laws and create a comprehensive framework which can mirror the realities of cloud computing [34]. Government should be careful enough while formulating any policy with respect to cloud services that can strike a balance between regulation of interest of the public and freedom for innovation of different technologies. There seems to be light at the end of tunnel as the Indian government is on its way of drafting the much sought after privacy legislation. The Indian entities should maximize benefit from the recent cloud revolution which can further accelerate growth in economy by effectively dodging the risks associated with it [30].
References
1. Robert et al., The nature of cyber threats, Center for a New American Security, https://www.cnas.org/search?q=The+nature+of+cyber+threats, 2011.
2. Javed, A., The Lessons of #CloudComputing—What Have We Learned So Far?, 2017. [Online]. Available: http://www.xorlogics.com/2017/07/31/the-lessons-of-cloudcomputing-what-have-we-learned-so-far/.
3. The Transatlantic Digital Dialogue, Cyber-Security Cooperation and Strong Encryption, German Marshall Fund of the United States, 2015.
4. Cilluffo, F., Ritchey, R., Tinker, T., Cloud Computing Risks and National Security Keeping Pace With Expanding Technology, Center for Cyber and Homeland Security at Auburn University, 2010.
5. Miller, S., COVID researchers can apply for free cloud services, [Online]. Available: https://techagainstcovid.com/.
6. CyberEdu, What is Cloud Security?, [Online]. Available: https://www.forcepoint.com/cyber-edu/cloud-security.
7. Avey, C., 7 Key Cybersecurity Threats to Cloud Computing, 11 September 2019. [Online]. Available: https://cloudacademy.com/blog/key-cybersecurity-threats-to-cloud-computing/.
8. Dinh, H.T., Lee, C., Niyato, D., Wang, P., A survey of mobile cloud computing: architecture, applications, and approaches. Wireless Commun. Mobile Comput., 2011, geo.edu.al/cloud/wp-content/uploads/2013/12/MCC.pdf.
9. Tabassam, S., Security and Privacy Issues in Cloud Computing Environment. J. Inf. Technol. Software Eng., 2017, https://www.researchgate.net/publication/322120849.
10. Needham, M., Cloud Standards Customer Council Announces Version 3.0 of Practical Guide to Cloud Computing, 05 December 2007. [Online]. Available: https://www.businesswire.com/news/home/20171205005186/en/Cloud-Standards-Customer-Council-Announces-Version-3.0. [Accessed 17 June 2020].
11. Nishith Desai Associates, Cloud Computing—Risks/Challenges—Legal & tax Issues, [Online]. Available: http://www.nishithdesai.com/fileadmin/user_upload/pdfs/Cloud_Computing.pdf. [Accessed 23 06 2020].
12. Rana, A. and Bagai, R., Cybersecurity in India, [Online]. Available: https://www.lexology.com/library/detail.aspx?g=4cd0bdb1-da7d-4a04-bd9c-30881dd3eadf. [Accessed 18 june 2020].
13. Eustice, J.C., Flying into the cloud without falling: understanding the intersection between data privacy laws and cloud computing solutions, [Online]. Available: https://legal.thomsonreuters.com/en/insights/articles/understanding-data-privacy-and-cloud-computing. [Accessed 17 06 2020].
14. Hutchinson, B., 87 million Facebook users to find out if their personal data was breached, [Online]. Available: https://abcnews.go.com/US/87-million-facebook-users-find-personal-data-breached/story?id=54334187. [Accessed 18 06 2020].
15. S.C.W. Headquarters, Data Privacy and Compliance in the cloud, [Online]. Available: https://docs.broadcom.com/doc/data-privacy-and-compliance-in-the-cloud-en. [Accessed 19 06 2020].
16. OECD’s Revised Guidelines on the Protection of Privacy and Transborder Flows of Personal Data, [Online], Available: https://www.oecd.org/internet/ieconomy/oecdguidelinesontheprotection-ofprivacyandtransborderflowsofpersonaldata.htm.
17. The Data Protection Bill, 2019.
18. Barak, A., Proportionality: Constitutional Rights and their Limitations, in: Proportionality: Constitutional Rights and their Limitations, Cambridge University Press, 2012.
19. Duraiswami, D., Privacy and Data Protection in India. J. Law Cyber Warfare, 166–186, 2017.
20. The Telegraph Act, 1885, [Online]. Available: https://dot.gov.in/act-rules-content/2442. [Accessed 20 June 2020].
21. Cidon, A., Protecting Intellectual Property in the Cloud, June 2015. [Online]. Available: https://www.wipo.int/wipo_magazine/en/2015/03/article_0004.html. [Accessed 15 June 2020].
22. The Wassenaar arrangement on export controls for conventional arms and dual-use goods and technologies, 05 December 2019. [Online]. Available: https://www.wassenaar.org/. [Accessed 20 06 2020].
23. Cidon, A., Protecting Intellectual Property in the Cloud, June 2015. [Online]. Available: https://www.wipo.int/wipo_magazine/en/2015/03/article_0004.html. [Accessed 18 June 2020].
24. MarketandMarkets, Cloud Computing Market, 2019.
25. Menon, M.G., Regulatory Issues in Cloud Computing—An Indian Perspective. J. Eng. Comput. Appl. Sci., 18–22, 2013.
26. Arun, C., Gatekeeper liability and Article 19(1)(A) of the Constitution of India, NUJS Law Review. 73–87, 2014, https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2643278.
27. Article19, Internet intermediaries: Dilemma of Liability, 2013. [Online]. Available: https://www.article19.org/data/files/Intermediaries_ENGLISH.pdf. [Accessed 18 June 2020].
28. Telecom Regulatory Authority of India, Consultation Paper, 2019.
29. Singh, J., TRAI may regulate cloud service companies, [Online]. Available: https://entrackr.com/2020/02/cloud-service-companies-trai-chairman/. [Accessed 21 06 2020].
30. Data Security Council of India, Legal and Policy Issues in Cloud Computing, [Online]. Available: https://www.dsci.in/sites/default/files/documents/resource_centre/Discussion%20Paper%20on%20Policy%20Legal%20Issues%20in%20Cloud.pdf. [Accessed 17 June 2020].
31. ISO/IEC 19941:2017: Information technology—Cloud computing—Interoperability and portability, 2017. [Online]. Available: https://www.iso.org/standard/66639.html.
32. Sheppard, D., Cloud interoperability and portability—Necessary or nice to have?, [Online]. Available: https://insightaas.com/cloud-interoperability-and-portability-necessary-or-nice-tohave/#:~:text=Cloud%20interoperability%20is%20the%20ability,method%20to%20obtain%20predictable%20results. [Accessed 22 06 2020].
33. Chen, D.Y. and Wilson, W.F., Cloud Computing Agreements: Negotiating Privacy Issues with Large Cloud Vendors, 24 06 2016. [Online]. Available: https://www.accdocket.com/articles/cloud-computing-agreements-privacy-issues.cfm. [Accessed 21 06 2020].
34. Menon, M.G., Regulatory issues in cloud computing—An Indian Perspecting. J. Eng. Comput. Appl. Sci., 2013.
- *Corresponding author: [email protected]
