2
Measures for Improving IoT Security
Richa Goel1*, Seema Sahai1, Gurinder Singh1 and Saurav Lall2
1Amity International Business School, Noida, India
2Azure IoT, Microsoft Seattle, Seattle, Washington, USA
Abstract
In today’s world of Digital Transformation, IoT banking/online transaction is a major point of concern for the user. IoT security plays a vital role to develop the trust of end users for making frequent use of the same. There have been IoT security breaches in recent years. As a result, immoral hackers have ample opportunities to intercept and change or misuse the information. Through this paper we are going to discuss various issuse/problems faced in terms of IoT security along with the measure to be chosen to achieve higher security while going for online transactions.
Keywords: IoT security, digital transformation, breach of trust
2.1 Introduction
Through the World Wide Web, we’ve entered into a brand new era of connectivity. “Things have identities and virtual personalities operating in smart places using intelligent interfaces to connect and communicate inside social, environmental and user contexts [7].” More than twenty billion devices were connected with each other in 2017. This means that the potential risk of cyber-attacks is going on increasingly, equally.
Gartner’s special report indicates that there is a high level of risk to all the IoT devices, whether it is the platform, their operating systems or even the other devices to which they are connected [10]. The kind of risk that exists is that ranging from physical tampering to information hacking and impersonation and many more. Organizations’ functioning has completely changed with the coming in of IOT. With this change a whole range of risks have also emerged and it has become the utmost priority of organizations to manage these risks.
A variety of possible security threats are posed by IOT which could affect users: (1) Enabling unauthorized access and abuse of data and confidential information and (2) enabling attacks on linked networks and devices (3) developing security risks [22]. Scientists have proposed that privacy and online protection should not be segregated. All security policies need to be addressed with respect to IOT and its linking systems and apps. It’s also true that online protection is the main problem for cloud computing. “Safety is one of the key concerns required to avoid the occurrence and use of IOT,” the World Health Organization states. There are also several barriers to health at IoT. It would be necessary to explain:
- a. Expansion of the ‘IoT’ to the ordinary network, network controls and cell network
- b. website that links everyone
- c. exchange of objects with each other
- d. Accessible easily.
The code layer, information layer, physical layer and networking layer contain many technical obstacles to IoT security. To order to protect IoT, numerous reports discuss these security topics. Experiments that illustrate IoT’s human experience are rare, though. Some of the latest works on IoT defense still consider the technical aspect. In order to achieve success in technology performance or safety management, users need to understand Dhillon and Torkzadeh’s [9] expectations, values and beliefs.
We recognize that consumer expectations and values are balanced against technology to achieve positive results for information technology and the effective management of legislation. IoT Securing Science is in its infancy as it is a very active and recent research field. Further emphasis should also be placed on the confidentiality, fairness and privacy of IoT data and their credibility. Inside this article, we perform a thorough analysis to address numerous IoT security issues/problems along with the step to use the firewall for greater protection when performing online transactions.
2.2 Perceiving IoT Security
Researcher’s Agarwal and Dey [4] note, “a safe and secure world allowed by IoT promises to lead to truly connected environments, where people and things cooperate to improve the overall quality of life. Truly IoT will give us operating information at our fingertips, without us having to ask for it or even recognizing that it might be required.” According to some researchers, the IoT is “a dynamic global network infrastructure with self-configuring capabilities based on a standard and interoperable communication convention where physical and virtual ‘things’ have identities, physical attributes, and virtual personalities, use intelligent interfaces and are flawlessly united into the information network.” With regards to securing IoT, some authors state that “In this context the information pump of the real world of interest is represented across billions of ‘things,’ many of which are updating in real-time and a transaction or data change is updated across hundreds or thousands of ‘things’ with differing update policies, opens up for many security challenges and security techniques across multiple policies. In order to prevent the unauthorized use of private information, research is needed in the area of vigorous trust, security and privacy management.” Agarwal and Dey [4] also note that “security IoT means providing access control procedure and policies and being able to implement them, particularly in the face of the huge number of varied devices.”
2.3 The IoT Safety Term
No doubt after pre-IoT days, human interaction with technology has developed as an automated control and tracking (e.g. various IoT devices) to access information and utilities (e.g. e-commerce). The IoT word is sweet. This involves intelligent machines followed by various network participants. Research is in the early stages on IoT and its safety characteristics. It is due to creativity and the expansion of this program in different fields such as eHealth, e-commerce and e-traffic.
Several scholars have looked into the health implications of IoT; there is still a shortage of systemic comprehension. IoT technology work primarily addresses problems relevant to privacy concerns. The safety of people, the protection of company structures and the security of third parties are three main concerns for Technology. For IoT environments, there are four complex integrated devices interacting with each other.
These components are individuals, artifacts, software and equipment, which are required to oppose anonymity, protection which transparent confidence problems. Previous threats in normal networks contributing to IoT pose passive and aggressive attacks; hinders its efficiency and invalidates the benefits in utilizing the amenities.
Because IoT devices are limited by hardware tools, the usage of common safety measures is troublesome, let alone user standards that would govern protection choices. At the technical point, there are three kinds of protection restrictions: equipment limitations, device limitations and network shortages. All three tell how protection can be configured for IoT apps.
Restrictions often offer a context for consumers and organizations to focus strategically on the value of IoT protection. Hardware limitations on IoT protection are critical. According to the battery-driven IoT systems it is impossible to relay fully inefficient algorithms for encryption.
Restrictions on memory often face a major challenge. Standard protection algorithms are believed to be important RAM and hard drive space.
This will not refer to IoT devices. Thanks to the small scale and the remote location that is a security threat, IoT systems run the risk of still being compromised [3]. The smallness of the systems at the software level is the reason of some worry regarding the principle of security. To order to maintain the power and resistance characteristics safe enough, IoT systems have small network protocol batteries.
IoT systems also have issues with remote reprogramming and even reprogramming can be challenging, if not difficult. On a networking point of view, there are several questions concerning effectiveness and expandability. Because IoT systems are mobile by design, the need for the versatility of reliable protocols to ensure protection is important. It is impossible for the current network access control protocol to withstand topological changes in the network.
Given the complexity of IoT and protection issues, traditional safety standards and the usage of technologies are troublesome. OWASP [27] also described many threats to harmful hazards that are unique to IoT. It provides the ability to gain usernames by communicating with authentication and raising forgotten passwords. The possibility that poor passwords mix user name information can be a security nightmare. Unencrypted networks will also raise security issues as well as the incomplete upgrade process.
2.4 Objectives
2.4.1 Enhancing Personal Data Access in Public Repositories
Conversations with our respondents showed that there was a great deal of anxiety over two key topics. The first problem is the inappropriate handling of private data in public forums. Most IoT systems and software transmit data to other apps and servers on a daily basis.
The second problem is the lack of consistency with the quality of search data. Seeing that every quest made on some of the IoT related devices and sites has been going on which increases concern among interviewees that their quest habits are not explicitly documented and are accessible. “There is a great deal of interest in the privacy literature around preserving the confidentiality of personal details in public datasets Geo-location is sensitive knowledge regarding privacy and its disclosure will seriously harm consumer privacy.”
2.4.2 Develop and Sustain Ethicality
Respondents in our research described two factors relevant to the nature of ethics in the IoT world—legal principles and fair usage. Existing literature has found rational usage and ethics to be significant, in particular because of the pervasive existence of technology.
According to Abbas, Michael and Michael [1], “The four topics underpinning socioethical studies involve the analysis into what is the human intent, what is legal, how fairness is served and the values that direct the usage of that methodology. Participants; their relationships with systems; people’s interests and personal expectations; societal and moral beliefs; processes, laws and norms; and fairness, personal benefits and personal harms are all areas of interest in a socio-ethical approach.” Figure 2.1 shows the various types of data.

Figure 2.1 Types of data.
2.4.3 Maximize the Power of IoT Access
Often the main objective of ensuring data confidentiality is to achieve this essential objective. Organizations may have a wealth of confidential information, but the data are not widely available to anyone. As regards IoT, there are further attack vector and hence better probability of attack, together with a large number of linked computers. Unauthorized exposure could exploit security vulnerabilities that could lead to physical security risks [28] (Figure 2.2).
2.4.4 Understanding Importance of Firewalls
The IoT is a frightening place. Criminals on the IoT have the potential to put out of sight behind their computers, or even other people’s computers, while they attempt to intervene in your computer to thieve personal information or to use it for their own purposes. But how you can prevent it or safeguard? The answer is that you can protect yourself with a firewall.
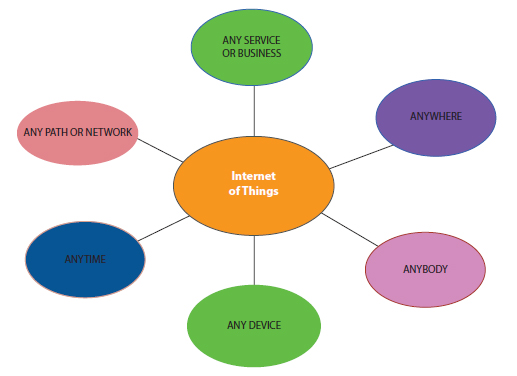
Figure 2.2 IoT and its components.
2.5 Research Methodology
We use the value-focused reasoning approach suggested by Keeney [19] to define IoT protection objectives. Keeney [20] applies this method to IoT business-associated consumer personality principles. He claims the only approach to figure out what the interest of the consumer is to question them. It is important to ask other prospective consumers since many individuals have specific beliefs and they convey various beliefs.
As values are produced, they are not automatically grouped into well-integrated classes with a good comprehension of which values are linked to the others and why. Within this analysis, the value-focused mindset methodology is used to produce IoT protection principles, goals and behavior of IT practitioners who rely on optimizing IoT protection (Figure 2.3).
According to Keeney [19], creative reasoning techniques are seen as the foundation for certain decision-making processes. In the research, the number of people to be questioned differs. Nonetheless, Hunter [16] questioned 53 people in two organisations and generated participant inceptions by performing a content review. Keeney [20] holds conversations and debates with more than 100 people about their principles for IoT transactions. In this report, we performed 40–50 min of interviews with 58 IT practitioners with different backgrounds and experience. Both participants have extensive day-today interaction with the IoT. Respondents covered the following sectors: transport and distribution, education, hospitality, finance and banking. We used a three-step method to define and coordinate the values and protection measures that a person has in relation to IoT protection (Figure 2.4).

Figure 2.3 IoT access control.
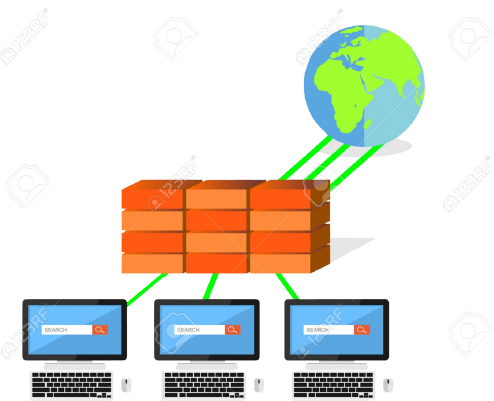
Figure 2.4 Concept of firewall.
Includes these steps:
- Developing a value list of consumers, involving asking the people concerned what they value for IoT safety?
- Management of priorities to identify ways to accomplish end-of-life (fundamental) objectives;
- Safety mechanisms to be chosen for the firewall to ensure better protection as electronic transactions are ongoing.
2.6 Security Challenges
Security issues associated with IoT are various. Security is the only such problem. To order to ensure the security of user knowledge from IoT exposure, the Internet of Things requires special requirements to order to have a specific identity for virtually every physical or virtual person or device, which will autonomously communicate with the Web or related networks. The table below illustrates that all privacy can be impaired.
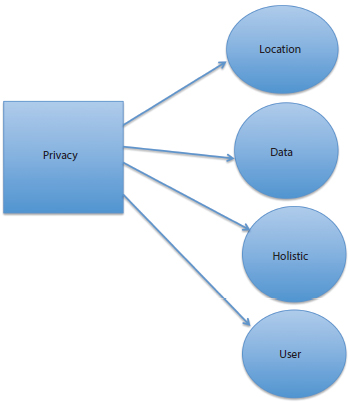
Figure 2.5 Privacy in IoT.
Challenge is of Privacy
An IoT security plan requires a holistic strategy that includes IT infrastructure, operational commands, cloud and consumer technology that function in tandem to ensure security. IoT-based threats have far too many implications to ignore. Hackers may now endanger human security and might even trigger confrontations.
Internet of Things connectivity provides versatility for remote control of devices
And in some situations, enabling the collection of data from physical sensors. There has been a huge rise in the Internet of Things, with a growing amount of physical devices connected with each other over the network. The environment created by IoT where different devices are connected through different software and operating systems, make them more vulnerable to attacks. Most IoT devices have no protection features, and even those that are there, are mostly rudimentary. Hence it is easy to attack them. IoT devices may become points of entry into smart homes and organizations Figure 2.5.
2.6.1 Challenge of Data Management
Organizations use the collected data for evaluating, preserving and enhancing operating performance. The pattern of rapid processing and use of data has contributed to a rise in data-driven business practices. Saving and sharing the collected data, however, can be a big concern for business leaders. With the issue of data privacy, businesses need to be extremely careful.
2.7 Securing IoT
2.7.1 Ensure User Authentication
This objective explores how authentication mechanisms must be established to enhance IoT security. Inherently ambiguous, yet weak verification mechanisms such as passwords. Two-factor authentication hardware tokens are usually best suited to IoT authentication. To order to enhance system security, 2FA based protection frames are now introduced. The enhanced use of biometrics often demonstrates the IoT client’s identification by means of a robust and identifying tool. You can replicate your password or hardware key, but with your downward reader, you can not replicate your fingerprint. The principles and the legal responsibility for social networking sites are also assured of the authentication process Figure 2.6.
2.7.2 Increase User Autonomy
The value of the consent of the user to the processing of IoT powered data. This underlines the need for verification and preference for individual influence of sensitive data and hence for increased privacy. Not all data has to be selected. If the usage of data is incompatible with the meaning of experiences, a simple and easy-to-read alternative will be given to individuals. Similar claims have been made in the literature. As regards the freedom of individuals, in particular with regard to IoT privacy security (Kounelis et al. [21]), it is argued that only if a mixture of person and artifact retains the ability to make deliberate choices and decisions in architecture, and awareness and vigilance in the field of freedom and security, can the overall interactions maintain confidence and trust Figure 2.7.
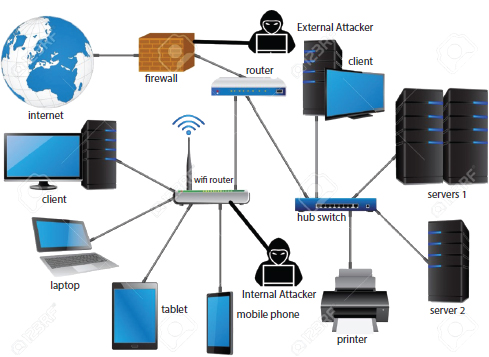
Figure 2.6 Internal and external attacker on IoT Infrastructure.
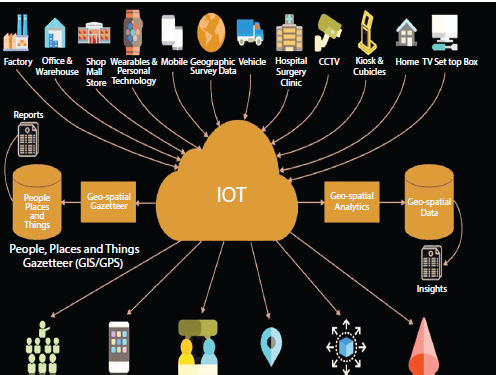
Figure 2.7 Different data sources of IoT.
2.7.3 Use of Firewalls
Earlier firewalls were high-ticket items of hardware that solely corporations would make use.The general public weren’t on the web, and if they were they were connected via a dial up that isn’t quick enough for many hacker’s functions. Consequently, hackers primarily attack United Nations organizations which with wider repositories of information available. At present, almost everyone has the ability to link to the website, and many hackers tend to concentrate on the house user since they are additionally capable of not securing their computers properly, which transform them into an unimpressive target. This in mind, yet strong home firewall technologies were built by developers to protect themselves. The house users’ firewalls are either a hardware or a cable.
Hardware firewall: A hardware firewall may be a bridge between your network association and the other blocked computers. In addition, these firewalls have an interconnected gateway that allows you to connect several devices to them so that anyone can join a network association. Such firewalls secure any single device linked to the Network Address Translation or NAT using a technology. Both secure computers, such as 192.168.1.X, that can not be reached via the network are secure by victimization and non-public data abuse. These internal data processors are then combined into one by the firewall. This allows the hardware firewall to accept all incoming requests you received and forward them to the internal PC received. This system, beyond machines, cannot be linked to the computers by the victimization of this technique.
Personal firewall: Any computer to be covered will be a Private Firewall kit that is installed into it. This kit then filters all input and generally outgoing traffic and makes only required or specifically allowed information. Computer firewalls are typically abundant in additional functionality than hardware models, but they have little capacity to connect the site connection with other network computers.
The decision on which form of firewall is based on what you want to use. Unless you want to just protect 1 pc, then mainly personal firewall kit is more than sufficient. When you want to protect many machines, a hardware-based solution is also of great benefit. Many people also say you can use a hardware firewall to save your network and a virtual firewall to secure your device. While sometimes this is not a good program, for other consumers it will be a prevention feature. When cash isn’t paired in nursing, instead through victimization will provide a degree of protection, as the bigger practicality found in personal firewalls.
2.7.4 Firewall Features
Filtering is carried out once a firewall examines the passage of information and determines whether that information is permitted to be transmitted and received or if supported rules and filters that are created must be discarded. It is the firewall’s usually first operation, and the protection demands extremely the way it performs these functions. The general public believes that the firewall is the most significant firewall operation, specifically, the transfer of inward knowledge to the computers. However, the departing filtering also plays a key role in protecting your machine. You may have malware inserted on your PC while your data was not, and you will suddenly see that the PC package tries to transmit information to a foreign host someplace on the web after you install a firewall with departing filtering. Now, you don’t just understand this package, but the filtering stopped distributing non-public information.
These filters can be modified so that all PCs on the network can effectively transfer information into your device or probably apps on your computer. Nevertheless, your desires will be guided by these laws. You would need to open port for remote desktop-related communications protocol (port 3389) to allow the traffic to move through your firewall, for example if you want remote users to connect to the remote victimization device remotely. The following example of this can be found in the nursing when permission to access the computer behind the firewall is granted to a particular remote PC Figure 2.8.
2.7.5 Mode of Camouflage
It’s critical that your firewall doesn’t actually obstruct attempts to access your laptop, but it doesn’t even appear like your laptop exists on the network. You are in what is known as concealment mode after square measuring connected to the web and your laptop can not be detected by samples on the laptop. Hackers will see how the computer is scanned with special expertise and the findings on the site. If you calculate in a cover-up mode, the firewall does not return this information, but appears to be connected. This information is not really connected. Thanks to this hacker your laptop does not continue to hit, because they believe that you are not online.
2.7.6 Protection of Data
There are actually a great number of firewalls with the ability to dam spyware, hijackers and adware. It helps you to shield your machine from interference of code which is marvelous to expose sensitive knowledge about what you do on the net or other programming activities. Ses square solutions are also packaged into firewall kit business versions.

Figure 2.8 Firewall that allows remote user access to a firewall device.
2.7.7 Integrity in Service
Integrity of operation is where the firewall controls the computer’s files to change them or how they are released. If such an alteration is detected, the user will be informed and the application will not be able to execute or transmit IoT information. Sometimes those improvements could have been used in an update, but now you will be told of it, if, it is changed by the malicious software.
2.7.8 Sensing of Infringement
Intruders use various techniques to breach the computer’s protection. Intrusion detection checks incoming system signature data and notifies you when these attempts are detected. With intrusion detection, you can see what a hacker wants to do to hack your computer.
Notifications help you to see what’s going on your firewall and to warn you of potential intrusion attempts on your device in different ways.
2.8 Monitoring of Firewalls and Good Management
2.8.1 Surveillance
Whatever firewall you use, it is a smart thing to obey and occasionally show firewall logs. You will improve your protection automatically through careful observance of your logs. Most hacks can theoretically be avoided if people track their logs because most hackers will check a laptop before hacking them. When a participant in the PC nursing supervisor detects these tests, they will check that their machines are sensitive to what they were checking. You’ll be shocked by the amount of people WHO tries to access your laptop, but not your results, until you start installing your firewall and reviewing logs.
The reasons behind tracking the log files are three: There are three key reasons:
Preventative Measures: You can see what harbors and services hackers are able to manipulate by tracking the firewall logs. Such knowledge will then be used to guarantee that the machine is safe against such exploits. For starters, when you see on your logs that other people are checking and investigating your machine for port 3127, you will discover that people and viruses will check for the backdoors on your machine which are left behind by the early version of the My Doom virus. You will then ensure that this new attack doesn’t damage the computers.
2.8.2 Forensics
If your machine is hit by a long distance virus, then you can check the date and time it was installed on your device by the hacker. Forensics: You will be able to search your log files for maltreatment of this data through all of this point of time, however the hacker has infiltrated your computer. This information is then used to encrypt your computer.
Officials reporting: With the data stored in the log files, you are able to supply officials with the details whether a hack or attempt is a success. The logs send you the IP address, system and time and date of the offending device.
2.8.3 Secure Firewalls for Private
- A Free online armor of Emsisoft
- The Firewall Outpost
- Zone Free Alarm
2.8.4 Business Firewalls for Personal
- The McAfee Human Firewall
- The Firewall Outpost Pro
- Zone Pro/Plus Alarm
2.8.5 IoT Security Weaknesses
There’s no single IoT security vendor that can provide a full end-to-end security solution. However, some organizations provide more than others and some may provide a full end-to-end IoT security solution in tandem with their partner ecosystem.
Authentication/authorization is one of the biggest issues to tackle in IoT security, followed by access control and data encryption. IoT security respondents didn’t consider firewall, passwords, server security and privacy as a major weakness.
2.9 Conclusion
This chapter uses a value-driven reasoning method to establish goals for securing IoT. Some studies [9] have used Keeney’s meaning-focused approach in order to explain the goals and their relationships dependent on people’s interest, according to Keeney [20] values of knowledge. and their relationships based on people values and learning the importance of firewalls Figure 2.9.

Figure 2.9 Where is security in IoT needed.
The value-focused thought methodology has not been used to describe the protection goals of IoT from the consumer viewpoint. Extracting IoT security relevance from consumer expectations will enable administrators and professionals optimize IoT protection based on a detailed set of objectives.
This research adds to the scope of the literature by incorporating basic goals and strategies for protecting IoT. This research explores the largely unexplored field of IoT protection. We perform a systematic analysis utilizing value-focused reasoning that has helped to identify goals and protection steps clustered into four simple and medium-sized priorities, which are important for protecting IoT from the individual perspective. We see why the device’s firewall is a must to defend the device from unethical hackers or viruses. We should be able to use the applications on the IoT with sufficient supervision and rules to further improve the protection of our device. We lock our doors to deter stolen robes when we leave our building, why not use a firewall to protect your computer?
References
1. Abbas, R., Michael, K., Michael, M.G., Using a Social-Ethical Framework to Evaluate Location-Based Services in an IoT of Things World. Int. Rev. Inf. Ethics, 22, 12, 2015.
2. Abie, H. and Balasingham, I., Risk-based adaptive security for smart IoT in eHealth, in: Proceedings of the 7th International Conference on Body Area Networks, February, ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering), pp. 269–275, 2012.
3. Agarwal, Y. and Dey, A.K., Toward Building a Safe, Secure, and Easy-to-Use IoT of Things Infrastructure. Computer, 49, 4, 88–91, 2016.
4. Bassi, A. and Horn, G., IoT of Things in 2020 A ROADMAP FOR THE FUTURE, European Commission: Information Society and Media, 22, 97–114, 2008.
5. Dhillon, G. and Torkzadeh, G., Value-focused assessment of information system security in organizations. Inf. Syst. J., 16, 3, 293–314, 2006.
6. Gartner, (n.d.), IoT of Things: The Gartner Perspective, Retrieved May 2, 2020, from https://www.gartner.com/en/information-technology/insights/IoT-of-things.
7. Hunter, M.G., The use of RepGrids to gather interview data about information systems analysts. Inf. Syst. J., 7, 1, 67–81, 1997.
8. Keeney, R.L. and McDaniels, T.L., Value-focused thinking about strategic decisions at BC Hydro. Interfaces, 22, 6, 94–109, 1992.
9. Keeney, R.L., The value of IoT commerce to the customer. Manage. Sci., 45, 4, 533–542, 1999.
10. Kounelis, I., Baldini, G., Neisse, R., Steri, G., Tallacchini, M., Pereira, A.G., Building trust in the human? IoT of things relationship. IEEE Technol. Soc. Mag., 33, 4, 73–80, 2014.
11. Rakic-Skokovic, M., Guidelines for Overcoming some IoT Security Issues, XVII International Scientific Conference on Industrial Systems, 1–6, 2017, Retrieved from http://www.iim.ftn.uns.ac.rs/is17.
12. OWASP Application Security – Building and Breaking Applications, OWASP, https://owasp.org/www-community/OWASP_Application_Security_FAQ
13. FTC. (2017). Privacy & Data Security Update, | Federal Trade Commission, 2016. Retrieved from https://www.ftc.gov/reports/privacy-data-security-update-2016.
- *Corresponding author: [email protected]
