Chapter 4
Communication and Network Security (Domain 4)
- Gary wants to distribute a large file and prefers a peer-to-peer CDN. Which of the following is the most common example of this type of technology?
- CloudFlare
- BitTorrent
- Amazon CloudFront
- Akamai Edge
- During a security assessment of a wireless network, Jim discovers that LEAP is in use on a network using WPA. What recommendation should Jim make?
- Continue to use LEAP. It provides better security than TKIP for WPA networks.
- Use an alternate protocol like PEAP or EAP-TLS and implement WPA2 if supported.
- Continue to use LEAP to avoid authentication issues, but move to WPA2.
- Use an alternate protocol like PEAP or EAP-TLS, and implement Wired Equivalent Privacy to avoid wireless security issues.
- Ben has connected his laptop to his tablet PC using an 802.11ac connection. What wireless network mode has he used to connect these devices?
- Infrastructure mode
- Wired extension mode
- Ad hoc mode
- Standalone mode
- Selah's and Nick's PCs simultaneously send traffic by transmitting at the same time. What network term describes the range of systems on a network that could be affected by this same issue?
- The subnet
- The supernet
- A collision domain
- A broadcast domain
- Sarah is manually reviewing a packet capture of TCP traffic and finds that a system is setting the RST flag in the TCP packets it sends repeatedly during a short period of time. What does this flag mean in the TCP packet header?
- RST flags mean “Rest.” The server needs traffic to briefly pause.
- RST flags mean “Relay-set.” The packets will be forwarded to the address set in the packet.
- RST flags mean “Resume Standard.” Communications will resume in their normal format.
- RST means “Reset.” The TCP session will be disconnected.
- Gary is deploying a wireless network and wants to deploy the fastest possible wireless technology. Which one of the following wireless networking standards should he use?
- 802.11a
- 802.11g
- 802.11n
- 802.11ac
- Michele wants to replace FTP traffic with a secure replacement. What secure protocol should she select instead?
- TFTP
- HFTPS
- SecFTP
- SFTP
- Jake has been told that there is a layer 3 problem with his network. Which of the following is associated with layer 3 in the OSI model?
- IP addresses
- TCP and UDP protocols
- MAC addresses
- Sending and receiving bits via hardware
- Frank is responsible for ensuring that his organization has reliable, supported network hardware. Which of the following is not a common concern for network administrators as they work to ensure their network continues to be operational?
- If the devices have vendor support
- If the devices are under warranty
- If major devices support redundant power supplies
- If all devices support redundant power supplies
- Brian is selecting an authentication protocol for a PPP connection. He would like to select an option that encrypts both usernames and passwords and protects against replay using a challenge/response dialog. He would also like to reauthenticate remote systems periodically. Which protocol should he use?
- PAP
- CHAP
- EAP
- LEAP
- Which one of the following protocols is commonly used to provide back-end authentication services for a VPN?
- HTTPS
- RADIUS
- ESP
- AH
- Isaac wants to ensure that his VoIP session initialization is secure. What protocol should he ensure is enabled and required?
- SVOIP
- PBSX
- SIPS
- SRTP
For questions 13–15, please refer to the following scenario and diagram:
Chris is designing layered network security for his organization.
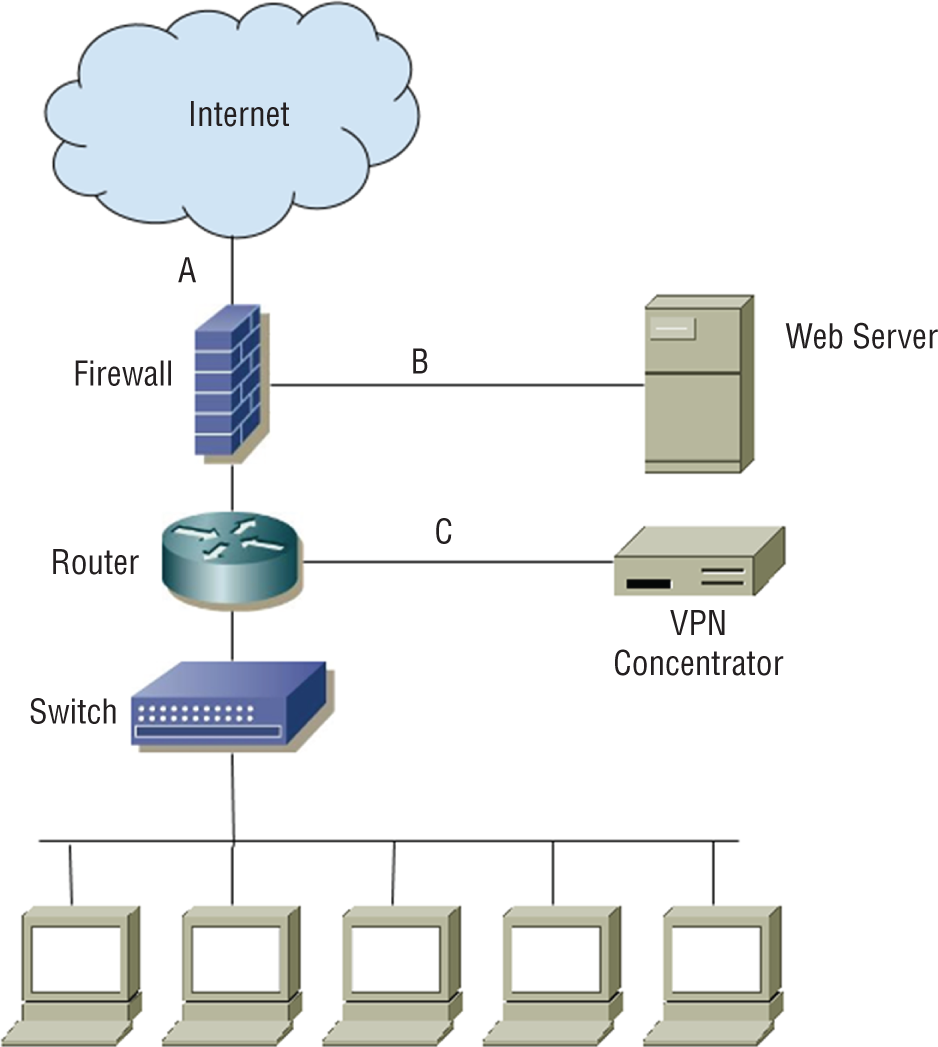
- What type of firewall design is shown in the diagram?
- A single-tier firewall
- A two-tier firewall
- A three-tier firewall
- A four-tier firewall
- If the VPN grants remote users the same access to network and system resources as local workstations have, what security issue should Chris raise?
- VPN users will not be able to access the web server.
- There is no additional security issue; the VPN concentrator's logical network location matches the logical network location of the workstations.
- Web server traffic is not subjected to stateful inspection.
- VPN users should only connect from managed PCs.
- If Chris wants to stop cross-site scripting attacks against the web server, what is the best device for this purpose, and where should he put it?
- A firewall, location A
- An IDS, location A
- An IPS, location B
- A WAF, location C
- Susan is deploying a routing protocol that maintains a list of destination networks with metrics that include the distance in hops to them and the direction traffic should be sent to them. What type of protocol is she using?
- A link-state protocol
- A link-distance protocol
- A destination metric protocol
- A distance-vector protocol
- Ben has configured his network to not broadcast an SSID. Why might Ben disable SSID broadcast, and how could his SSID be discovered?
- Disabling SSID broadcast prevents attackers from discovering the encryption key. The SSID can be recovered from decrypted packets.
- Disabling SSID broadcast hides networks from unauthorized personnel. The SSID can be discovered using a wireless sniffer.
- Disabling SSID broadcast prevents issues with beacon frames. The SSID can be recovered by reconstructing the BSSID.
- Disabling SSID broadcast helps avoid SSID conflicts. The SSID can be discovered by attempting to connect to the network.
- What network tool can be used to protect the identity of clients while providing Internet access by accepting client requests, altering the source addresses of the requests, mapping requests to clients, and sending the modified requests out to their destination?
- A switch
- A proxy
- A router
- A firewall
- Susan wants to secure her communications traffic via multiple internet service providers as it is sent to her company's second location. What technology should she use to protect the traffic for an always on, always connected link between the sites?
- FCoE
- SDWAN
- A point-to-point IPsec VPN
- Zigbee
- Melissa wants to combine multiple physical networks in her organization in a way that is transparent to users but allows the resources to be allocated as needed for networked services. What type of network should she deploy?
- iSCSI
- A virtual network
- SDWAN
- A CDN
- Which email security solution provides two major usage modes: (1) signed messages that provide integrity, sender authentication, and nonrepudiation; and (2) an enveloped message mode that provides integrity, sender authentication, and confidentiality?
- S/MIME
- MOSS
- PEM
- DKIM
- During a security assessment, Jim discovers that the organization he is working with uses a multilayer protocol to handle SCADA systems and recently connected the SCADA network to the rest of the organization's production network. What concern should he raise about serial data transfers carried via TCP/IP?
- SCADA devices that are now connected to the network can now be attacked over the network.
- Serial data over TCP/IP cannot be encrypted.
- Serial data cannot be carried in TCP packets.
- TCP/IP's throughput can allow for easy denial-of-service attacks against serial devices.
- Ben provides networking and security services for a small chain of coffee shops. The coffee shop chain wants to provide secure, free wireless for customers. Which of the following is the best option available to Ben to allow customers to connect securely to his wireless network without needing a user account if Ben does not need to worry about protocol support issues?
- Use WPA2 in PSK mode.
- Use WPA3 in SAE mode.
- Use WPA2 in Enterprise mode.
- Use a captive portal.
- Alicia's company has implemented multifactor authentication using SMS messages to provide a numeric code. What is the primary security concern that Alicia may want to express about this design?
- SMS messages are not encrypted.
- SMS messages can be spoofed by senders.
- SMS messages may be received by more than one phone.
- SMS messages may be stored on the receiving phone.
- What speed and frequency range are used by 802.11n?
- 5 GHz only
- 900 MHz and 2.4 GHz
- 2.4 GHz and 5 GHz
- 2.4 GHz only
- The Address Resolution Protocol (ARP) and the Reverse Address Resolution Protocol (RARP) operate at what layer of the OSI model?
- Layer 1
- Layer 2
- Layer 3
- Layer 4
- Which of the following is a converged protocol that allows storage mounts over TCP, and which is frequently used as a lower-cost alternative to Fibre Channel?
- MPLS
- SDN
- VoIP
- iSCSI
- Chris is building an Ethernet network and knows that he needs to span a distance of more than 150 meters with his 1000BaseT network. What network technology should he use to help with this?
- Install a repeater, a switch, or a concentrator before 100 meters.
- Use Category 7 cable, which has better shielding for higher speeds.
- Install a gateway to handle the distance.
- Use STP cable to handle the longer distance at high speeds.
For questions 29–31, please refer to the following scenario and diagram:
Selah's organization has used a popular messaging service for a number of years. Recently, concerns have been raised about the use of messaging.

- What protocol is the messaging traffic most likely to use based on the diagram?
- SLACK
- HTTP
- SMTP
- HTTPS
- What security concern does sending internal communications from A to B raise?
- The firewall does not protect system B.
- System C can see the broadcast traffic from system A to B.
- It is traveling via an unencrypted protocol.
- Messaging does not provide nonrepudation.
- How could Selah's company best address a desire for secure messaging for users of internal systems A and C?
- Use a third-party messaging service.
- Implement and use a locally hosted service.
- Use HTTPS.
- Discontinue use of messaging and instead use email, which is more secure.
- Which of the following drawbacks is a concern when multilayer protocols are allowed?
- A range of protocols may be used at higher layers.
- Covert channels are allowed.
- Filters cannot be bypassed.
- Encryption can't be incorporated at multiple layers.
- Which of the following is not an example of a converged protocol?
- MIME
- FCoE
- iSCSI
- VoIP
- Chris uses a cellular hot spot to provide internet access when he is traveling. If he leaves the hot spot connected to his PC while his PC is on his organization's corporate network, what security issue might he cause?
- Traffic may not be routed properly, exposing sensitive data.
- His system may act as a bridge from the internet to the local network.
- His system may be a portal for a reflected DDoS attack.
- Security administrators may not be able to determine his IP address if a security issue occurs.
- In her role as an information security professional, Susan has been asked to identify areas where her organization's wireless network may be accessible even though it isn't intended to be. What should Susan do to determine where her organization's wireless network is accessible?
- A site survey
- Warwalking
- Wardriving
- A design map
- What features can IPsec provide for secure communication?
- Encryption, access control, nonrepudiation and message authentication
- Protocol convergence, content distribution, micro-segmentation, and network virtualization
- Encryption, authorization, nonrepudiation, and message integrity checking
- Micro-segmentation, network virtualization, encryption, and message authentication
- Casey has been asked to determine if Zigbee network traffic can be secured in transit. What security mechanism does Zigbee use to protect data traffic?
- 3DES encryption
- AES encryption
- ROT13 encryption
- Blowfish encryption
- Sue modifies her MAC address to one that is allowed on a network that uses MAC filtering to provide security. What is the technique Sue used, and what nonsecurity issue could her actions cause?
- Broadcast domain exploit, address conflict
- Spoofing, token loss
- Spoofing, address conflict
- Sham EUI creation, token loss
- Joanna wants to deploy 4G LTE as an out-of-band management solution for devices at remote sites. Which of the following security capabilities is not commonly available from 4G service providers?
- Encryption capabilities
- Device-based authentication
- Dedicated towers and antennas for secure service subscribers
- SIM-based authentication
- SMTP, HTTP, and SNMP all occur at what layer of the OSI model?
- Layer 4
- Layer 5
- Layer 6
- Layer 7
- Melissa uses the ping utility to check whether a remote system is up as part of a penetration testing exercise. If she does not want to see her own ping packets, what protocol should she filter out from her packet sniffer's logs?
- UDP
- TCP
- IP
- ICMP
- Selah wants to provide port-based authentication on her network to ensure that clients must authenticate before using the network. What technology is an appropriate solution for this requirement?
- 802.11a
- 802.3
- 802.15.1
- 802.1x
- Ben has deployed a 1000BaseT gigabit network and needs to run a cable across a large building. If Ben is running his link directly from a switch to another switch in that building, what is the maximum distance Ben can cover according to the 1000BaseT specification?
- 2 kilometers
- 500 meters
- 185 meters
- 100 meters
- What security control does MAC cloning attempt to bypass for wired networks?
- Port security
- VLAN hopping
- 802.1q trunking
- Etherkiller prevention
- The company that Kathleen works for has moved to remote work for most employees and wants to ensure that the multimedia collaboration platform that they use for voice, video, and text-based collaboration is secure. Which of the following security options will provide the best user experience while providing appropriate security for communications?
- Require software-based VPN to the corporate network for all use of the collaboration platform.
- Require the use of SIPS and SRTP for all communications.
- Use TLS for all traffic for the collaboration platform.
- Deploy secure VPN endpoints to each remote location and use a point-to-point VPN for communications.
- Chris wants to use a low-power, personal area network wireless protocol for a device he is designing. Which of the following wireless protocols is best suited to creating small, low-power devices that can connect to each other at relatively short distances across buildings or rooms?
- WiFi
- Zigbee
- NFC
- Infrared
- Which of the following options includes standards or protocols that exist in layer 6 of the OSI model?
- NFS, SQL, and RPC
- TCP, UDP, and TLS
- JPEG, ASCII, and MIDI
- HTTP, FTP, and SMTP
- Cameron is worried about distributed denial-of-service attacks against his company's primary web application. Which of the following options will provide the most resilience against large-scale DDoS attacks?
- A CDN
- Increasing the number of servers in the web application server cluster
- Contract for DDoS mitigation services via the company's ISP
- Increasing the amount of bandwidth available from one or more ISPs
- There are four common VPN protocols. Which group listed contains all of the common VPN protocols?
- PPTP, LTP, L2TP, IPsec
- PPP, L2TP, IPsec, VNC
- PPTP, L2F, L2TP, IPsec
- PPTP, L2TP, IPsec, SPAP
- Wayne wants to deploy a secure voice communication network. Which of the following techniques should he consider? (Select all that apply.)
- Use a dedicated VLAN for VoIP phones and devices.
- Require the use of SIPS and SRTP.
- Require the use of VPN for all remote VoIP devices.
- Implement a VoIP IPS.
- Which OSI layer includes electrical specifications, protocols, and interface standards?
- The Transport layer
- The Device layer
- The Physical layer
- The Data Link layer
- Ben is designing a WiFi network and has been asked to choose the most secure option for the network. Which wireless security standard should he choose?
- WPA2
- WPA
- WEP
- WPA3
- Kathleen has two primary locations in a town and wants the two environments to appear like the same local network. Each location has a router, switches, and wireless access points deployed to them. What technology would best work to allow her to have the two facilities appear to be on the same network segment?
- SDWAN
- VXLAN
- VMWAN
- iSCSI
- Segmentation, sequencing, and error checking all occur at what layer of the OSI model that is associated with SSL, TLS, and UDP?
- The Transport layer
- The Network layer
- The Session layer
- The Presentation layer
- The Windows
ipconfigcommand displays the following information:BC-5F-F4-7B-4B-7D
What term describes this, and what information can usually be gathered from it?
- The IP address, the network location of the system
- The MAC address, the network interface card's manufacturer
- The MAC address, the media type in use
- The IPv6 client ID, the network interface card's manufacturer
- Chris has been asked to choose between implementing PEAP and LEAP for wireless authentication. What should he choose, and why?
- LEAP, because it fixes problems with TKIP, resulting in stronger security
- PEAP, because it implements CCMP for security
- LEAP, because it implements EAP-TLS for end-to-end session encryption
- PEAP, because it can provide a TLS tunnel that encapsulates EAP methods, protecting the entire session
- Ben is troubleshooting a network and discovers that the NAT router he is connected to has the 192.168.x.x subnet as its internal network and that its external IP is 192.168.1.40. What problem is he encountering?
- 192.168.x.x is a nonroutable network and will not be carried to the internet.
- 192.168.1.40 is not a valid address because it is reserved by RFC 1918.
- Double NATing is not possible using the same IP range.
- The upstream system is unable to de-encapsulate his packets, and he needs to use PAT instead.
- What is the default subnet mask for a Class B network?
- 255.0.0.0
- 255.255.0.0
- 255.254.0.0
- 255.255.255.0
- Jim's organization uses a traditional PBX for voice communication. What is the most common security issue that its internal communications are likely to face, and what should he recommend to prevent it?
- Eavesdropping, encryption
- Man-in-the-middle attacks, end-to-end encryption
- Eavesdropping, physical security
- Wardialing, deploy an IPS
- What technical difference separates wireless communication via WiFi and LiFi?
- LiFi is not susceptible to electromagnetic interference.
- LiFi cannot be used to deliver broadband speeds.
- WiFi is not susceptible to electromagnetic interference.
- WiFi cannot be used to deliver broadband speeds.
- Selah's organization has deployed VoIP phones on the same switches that the desktop PCs are on. What security issue could this create, and what solution would help?
- VLAN hopping; use physically separate switches.
- VLAN hopping; use encryption.
- Caller ID spoofing; MAC filtering.
- Denial-of-service attacks; use a firewall between networks.
For questions 62–65, please refer to the following scenario:
Susan is designing her organization's new network infrastructure for a branch office.
- Susan wants to use a set of nonroutable IP addresses for the location's internal network addresses. Using your knowledge of secure network design principles and IP networking, which of the following IP ranges are usable for that purpose? (Select all that apply.)
- 172.16.0.0/12
- 192.168.0.0/16
- 128.192.0.0/24
- 10.0.0.0/8
- Susan knows that she will need to implement a WiFi network for her customers and wants to gather information about the customers, such as their email address, without having to provide them with a wireless network password or key. What type of solution would provide this combination of features?
- NAC
- A captive portal
- Pre-shared keys
- WPA3's SAE mode
- With her wireless network set up, Susan moves on to ensuring that her network will remain operational even if disruptions occur. What is the simplest way she can ensure that her network devices, including her router, access points, and network switches, stay on if a brownout or other temporary power issue occurs?
- Purchase and install a generator with an automatic start.
- Deploy dual power supplies for all network devices.
- Install UPS systems to cover all network devices that must remain online.
- Contract with multiple different power companies for redundant power.
- Susan wants to provide 10 gigabit network connections to devices in the facility where the new branch will operate. What connectivity options does she have for structured wiring that can meet those speeds? (Select all that apply.)
- Cat5e
- Fiber
- Cat6
- Coaxial cable
- Data streams occur at what three layers of the OSI model?
- Application, Presentation, and Session
- Presentation, Session, and Transport
- Physical, Data Link, and Network
- Data Link, Network, and Transport
- Lucca wants to protect endpoints that are in production use but that are no longer supported and cannot be patched from network attacks. What should he do to best protect these devices?
- Install a firewall on the device.
- Disable all services and open ports on the devices.
- Place a hardware network security device in front of the devices.
- Unplug the devices from the network because they cannot be properly secured.
- Selah's networking team has been asked to identify a technology that will allow them to dynamically change the organization's network by treating the network like code. What type of architecture should she recommend?
- A network that follows the 5-4-3 rule
- A converged network
- A software-defined network
- A hypervisor-based network
- Jason knows that protocols using the OSI model rely on encapsulation as data moves from layer to layer. What is added at each layer as data flows up the OSI layers?
- Information is added to the header.
- Information is added to the main body of the data.
- The data is encrypted with a new secret key.
- A security envelope that provides perfect forward secrecy
- During a troubleshooting process, the support technician that Alyssa is talking to states that the problem is a layer 3 problem. Which of the following possible issues is not a layer 3 problem?
- A TTL mismatch
- An MTU mismatch
- An incorrect ACL
- A broken network cable
- During a review of her organization's network, Angela discovered that it was suffering from broadcast storms and that contractors, guests, and organizational administrative staff were on the same network segment. What design change should Angela recommend?
- Require encryption for all users.
- Install a firewall at the network border.
- Enable spanning tree loop detection.
- Segment the network based on functional requirements.
- ICMP, RIP, and network address translation all occur at what layer of the OSI model?
- Layer 1
- Layer 2
- Layer 3
- Layer 4
For questions 73–75, please refer to the following scenario:
Ben is an information security professional at an organization that is replacing its physical servers with cloud-hosted virtual machines. As the organization builds its virtual environment, it is moving toward a hybrid cloud operational model with some systems and services remaining in its local data center and others hosted in the cloud. The following diagram shows the local data center and cloud VPC's network IP ranges, which you should consider as you answer the questions.

- Ben wants to ensure that the instance-to-instance (system-to-system) traffic in his cloud-hosted infrastructure as a service environment is secure. What can he do to fully ensure that the virtualized network traffic is not being captured and analyzed?
- Prevent the installation of a packet sniffer on all hosts.
- Disable promiscuous mode for all virtual network interfaces.
- Disallow the use of any virtual taps.
- Encrypt all traffic between hosts.
- What issue is most likely to occur due to the subnets configured for the data center and VPC?
- IP address conflicts
- Routing loops
- MAC address conflicts
- All of the above
- Ben wants to use multiple internet service providers (ISPs) to connect to his cloud VPC to ensure reliable access and bandwidth. What technology can he use to manage and optimize those connections?
- FCoE
- VXLAN
- SDWAN
- LiFi
- WPA2's Counter Mode Cipher Block Chaining Message Authentication Mode Protocol (CCMP) is based on which common encryption scheme?
- DES
- 3DES
- AES
- TLS
- When a host on an Ethernet network detects a collision and transmits a jam signal, what happens next?
- The host that transmitted the jam signal is allowed to retransmit while all other hosts pause until that transmission is received successfully.
- All hosts stop transmitting, and each host waits a random period of time before attempting to transmit again.
- All hosts stop transmitting, and each host waits a period of time based on how recently it successfully transmitted.
- Hosts wait for the token to be passed and then resume transmitting data as they pass the token.
- Mark is concerned about the physical security of his network cables. What type of network connection would be the hardest to tap without specialized equipment?
- WiFi
- Bluetooth
- Cat5/Cat6 twisted pair
- Fiber optic
- Rich wants to connect his network to a building a half-mile away from his current location. There are trees and terrain features along the way, but a road passes between the trees to the other location. What type of transmission media is best suited to this type of deployment?
- Ethernet cable with repeaters every 200 to 300 yards
- A WiFi directional antenna
- Fiber-optic cable
- A LiFi system
- What challenge is most common for endpoint security system deployments?
- Compromises
- The volume of data
- Monitoring encrypted traffic on the network
- Handling non-TCP protocols
- What type of address is 127.0.0.1?
- A public IP address
- An RFC 1918 address
- An APIPA address
- A loopback address
- Susan is writing a best practices statement for her organizational users who need to use Bluetooth. She knows that there are many potential security issues with Bluetooth and wants to provide the best advice she can. Which of the following sets of guidance should Susan include?
- Use Bluetooth's built-in strong encryption, change the default PIN on your device, turn off discovery mode, and turn off Bluetooth when it's not in active use.
- Use Bluetooth only for those activities that are not confidential, change the default PIN on your device, turn off discovery mode, and turn off Bluetooth when it's not in active use.
- Use Bluetooth's built-in strong encryption, use extended (eight digits or longer) Bluetooth PINs, turn off discovery mode, and turn off Bluetooth when it's not in active use.
- Use Bluetooth only for those activities that are not confidential, use extended (eight digits or longer) Bluetooth PINs, turn off discovery mode, and turn off Bluetooth when it's not in active use.
- What type of networking device is most commonly used to assign endpoint systems to VLANs?
- Firewall
- Router
- Switch
- Hub
- Steve has been tasked with implementing a network storage protocol over an IP network. What storage-centric converged protocol is he likely to use in his implementation?
- MPLS
- FCoE
- SDN
- VoIP
- Michelle is told that the organization that she is joining uses an SD-WAN controller architecture to manage their WAN connections. What can she assume about how the network is managed and controlled? (Select all that apply.)
- The network uses predefined rules to optimize performance.
- The network conducts continuous monitoring to support better performance.
- The network uses self-learning techniques to respond to changes in the network.
- All connections are managed by the organization's primary internet service provider.
- Which of the following shows the layers of the OSI model in correct order, from layer 1 to layer 7? Place the layers of the OSI model shown here in the appropriate order, from layer 1 to layer 7.
- Layer 1 = Data Link; Layer 2 = Physical; Layer 3 = Network; Layer 4 = Transport; Layer 5 = Session; Layer 6 = Presentation; Layer 7 = Applications
- Layer 1 = Physical; Layer 2 = Data Link; Layer 3 = Network; Layer 4 = Transport; Layer 5 = Session; Layer 6 = Presentation; Layer 7 = Applications
- Layer 1 = Physical; Layer 2 = Data Link; Layer 3 = Network; Layer 4 = Transport; Layer 5 = Session; Layer 6 = Applications; Layer 7 = Presentation
- Layer 1 = Physical; Layer 2 = Data Link; Layer 3 = Network; Layer 4 = Session; Layer 5 = Transport; Layer 6 = Presentation; Layer 7 = Applications
- Valerie enables port security on the switches on her network. What type of attack is she most likely trying to prevent?
- IP spoofing
- MAC aggregation
- CAM table flooding
- VLAN hopping
- Alaina wants to ensure that systems are compliant with her network security settings before they are allowed on the network and wants to ensure that she can test and validate system settings as possible. What type of NAC system should she deploy?
- A pre-admit, clientless NAC system
- A postadmission, client-based NAC system
- A pre-admit, client-based NAC system
- A postadmission, clientless NAC system
- Derek wants to deploy redundant core routers, as shown in the diagram. What model of high availability clustering will provide him with the greatest throughput?

- Active/active
- Line interactive
- Active/passive
- Nearline
- Angela needs to choose between the following protocols for secure authentication and doesn't want to create unneeded technical complexity. Which authentication protocol should she choose and why?
- EAP, because it provides strong encryption by default
- LEAP, because it provides frequent reauthentication and changing of WEP keys
- PEAP, because it provides encryption and doesn't suffer from the same vulnerabilities that LEAP does
- EAP-TLS
- What is a frequent concern for systems that require high-performing internet connectivity when satellite internet is the only available option?
- Security
- Compatibility with protocols like LiFi
- Compatibility with protocols like Zigbee
- Latency
- What layer of an SDN implementation uses programs to communicate needs for resources via APIs?
- The data plane
- The control plane
- The application plane
- The monitoring plane
- Which of the following is not a drawback of multilayer protocols?
- They can allow filters and rules to be bypassed.
- They can operate at higher OSI levels.
- They can allow covert channels.
- They can allow network segment boundaries to be bypassed.
- Place the following layers of the TCP/IP model in order, starting with the Application layer and moving down the stack.
- Application layer
- Network Access layer
- Internet layer
- Transport layer
- 1, 2, 3, 4
- 1, 4, 2, 3
- 1, 4, 3, 2
- 4, 1, 3, 2
- What is the maximum speed that Category 5e cable is rated for?
- 5 Mbps
- 10 Mbps
- 100 Mbps
- 1000 Mbps
- What are two primary advantages that 5G networks have over 4G networks? (Select all that apply.)
- Anti-jamming features
- Enhanced subscriber identity protection
- Mutual authentication capabilities
- Multifactor authentication
- What function does VXLAN perform in a data center environment?
- It removes limitations due to maximum distance for Ethernet cables.
- It allows multiple subnets to exist in the same IP space with hosts using the same IP addresses.
- It tunnels layer 2 connections over a layer 3 network, stretching them across the underlying layer 3 network.
- All of the above
- Chris is setting up a hotel network and needs to ensure that systems in each room or suite can connect to each other, but systems in other suites or rooms cannot. At the same time, he needs to ensure that all systems in the hotel can reach the internet. What solution should he recommend as the most effective business solution?
- Per-room VPNs
- VLANs
- Port security
- Firewalls
- During a forensic investigation, Charles is able to determine the Media Access Control (MAC) address of a system that was connected to a compromised network. Charles knows that MAC addresses are tied back to a manufacturer or vendor and are part of the fingerprint of the system. To which OSI layer does a MAC address belong?
- The Application layer
- The Session layer
- The Physical layer
- The Data Link layer
- Mikayla is reviewing her organization's VoIP environment configuration and finds a diagram that shows the following design. What concern should she express?

- The voice connection is unencrypted and could be listened to.
- There are no security issues in this diagram.
- The session initialization connection is unencrypted and could be viewed.
- Both the session initialization and voice data connection are unencrypted and could be captured and analyzed.
