Chapter 12
Identifying a Security Breach
IN THIS CHAPTER
![]() Understanding why it’s critical to know if you were breached
Understanding why it’s critical to know if you were breached
![]() Identifying overt and covert breaches
Identifying overt and covert breaches
![]() Recognizing various symptoms of covert breaches
Recognizing various symptoms of covert breaches
Despite valiant efforts to protect your computer systems and data, you may suffer some sort of breach. In fact, the odds that your data will — at some point — be somehow breached by someone are close to 100 percent. The only real question is whether the breach will take place on a device or network that you operate or one that is owned and operated by someone else.
Because you’re ultimately responsible for maintaining your own computer systems, you need to be able to recognize the signs of a potential breach occurring of your equipment. If a hacker does manage to penetrate your systems, you need to terminate the attacker’s access as quickly as possible. If your data has been manipulated or destroyed, you need to restore an accurate copy within a reasonable amount of time. If systems are malfunctioning, you need to stop them from performing inappropriate activities and get them back on track to deliver service as expected.
In this chapter, you learn about the typical symptoms of a breach. Armed with this knowledge, you can hopefully recognize if something is amiss so that you can take appropriate corrective actions, as discussed in the next chapter.
Identifying Overt Breaches
The easiest breaches to identify are those in which the attacker announces to you that you’ve been breached and provides proof of that accomplishment. Three of the most common overt breaches are those involving ransomware, defacement, and claimed destruction.
Ransomware
Ransomware is a form of malware that encrypts or steals data on a user’s device and demands a ransom in order to restore the data to the user’s control (see Figure 12-1). Typically, ransomware includes an expiration date with a warning to the tune of “pay within x hours or the data will be destroyed forever!” (See Chapter 2 for more on ransomware.)
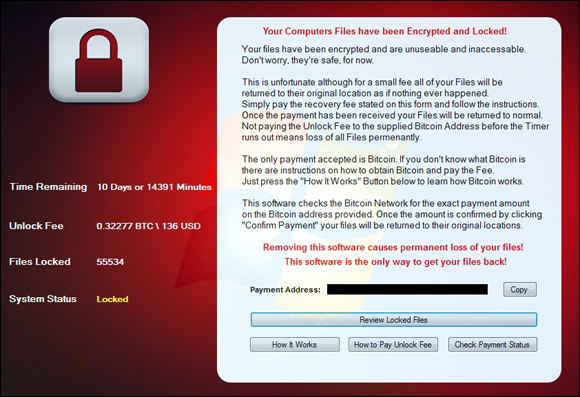
FIGURE 12-1: A ransomware screen from an overt infection.
Obviously, if your device presents you with such a demand and important files that should be accessible to you aren’t available because they’re missing or encrypted, you can be reasonably sure that you need to take corrective action.
Over the past few years, ransomware has become increasingly dominant as a weapon of choice by financially-motivated cyberattackers, both in terms of opportunistic attacks and in terms of targeted attacks.
Defacement
Defacement refers to breaches in which the attacker defaces the systems of the victim — for example, changing the target’s website to display a message that the hacker hacked it (in an almost “virtual subway graffiti”-like sense) or a message of support for some cause, as is often the case with hacktivists (see Figure 12-2).
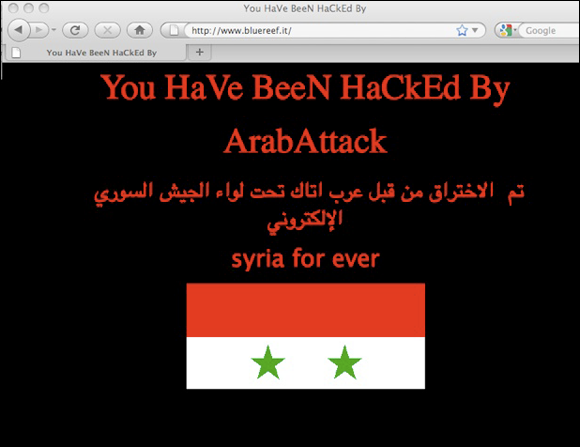
FIGURE 12-2: A defaced website (ostensibly by the hacker group known as the Syrian Electronic Army).
If you have a personal website and it’s defaced or if you boot up your computer and it displays a hacked by <some hacker> message, you can be reasonably certain that you were breached and that you need to take corrective action. Of course, the breach may have occurred at the site hosting your site, and not on your local computer — a matter that I discuss in Chapter 13.
Claimed destruction
Hackers can destroy data or programs, but so can technical failures or human errors. The fact that data has been deleted, therefore, doesn't necessarily mean that a system was breached. However, if some party claims responsibility, the odds that the problems are the result of a breach can skyrocket. (Although there have been instances in which parties falsely claimed responsibility for cyberattacks ostensibly in order to convince the public of their technical prowess.)
Detecting Covert Breaches
While some breaches are obviously discernable to be breaches, many breaches are actually quite hard to detect. In fact, breaches are sometimes so hard to notice that various enterprises that spend tens of millions of dollars a year, or even hundreds of millions of dollars a year, on cybersecurity technology including systems that try to identify breaches have had breaches go undetected for significant periods of time — sometimes even for years! The following sections describe some symptoms that may indicate that your computer, tablet, or smartphone has been breached.
However, if a device suddenly seems to suffer from multiple suspicious behaviors or if the relevant issues develop just after you left the device unattended for some period of time in a public location, clicked on a link in an email or text message, downloaded and ran some software provided by a source with potentially deficient security practices, opened some questionable attachment, or did something else about which wisdom you now question, you may want to take corrective action, as described Chapter 13.
Your device seems slower than before
Malware running on a computer, tablet, or smartphone often impacts the performance of the device in a noticeable fashion. Malware that transmits data can also sometimes slow down a device’s connection to the Internet or even to internal networks.
On Android devices, one of the three buttons or swipe actions on the bottom of the screen will usually load up a list of active applications (exactly which button varies between devices).
Your Task Manager doesn’t run
If you try to run Task Manager on Windows (see Figure 12-3) or Activity Monitor on a Mac (see preceding section) and the tool does not run, your computer may be infected with malware. Various strains of malware are known to impact the ability of these programs to operate.
Your Registry Editor doesn’t run
If you try to run Registry Editor on Windows (for example, by typing regedit at the Run prompt) and it does not run, your computer may be infected with malware. Various strains of malware are known to impact the ability of the Registry Editor to execute.
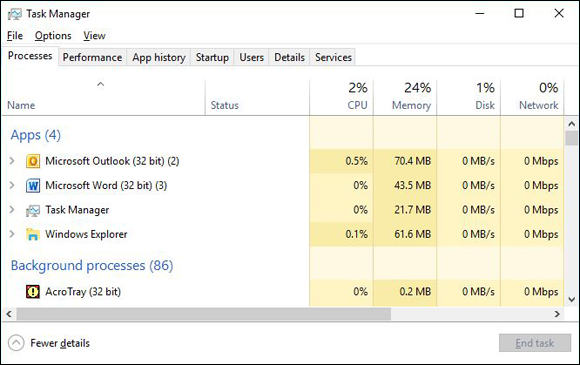
FIGURE 12-3: The Microsoft Windows Task Manager.
Your device starts suffering from latency issues
Latency refers to the time it takes for data to begin to travel after the instruction is issued to make it travel. If you’re noticing delays that were not present before — especially if the delays seem significant — something may be amiss. Of course, you may also have a poor network connection, so check the network connection strength. If that connection is fine, it is still possible that your Internet provider or some other provider along the network path between yourself and the resources you are trying to access may be experiencing problems, and everything may be fine on your local device. However, if the latency issues appear from only one device or a particular set of devices and not from all devices connected to the same network and if rebooting the impacted device/s does not ameliorate the situation, your device/s may have been compromised.
Your device starts suffering from communication and buffering issues
One highly visual symptom of communication-performance problems that can easily be discerned without much technical knowledge is if streaming videos seem to freeze while preloading future frames, or buffering, far more often than they did in the past (see Figure 12-4). While buffering is an annoyance that happens to most folks from time to time, if it is happening regularly on a connection that previously did not suffer on a regular basis from such an ailment or it’s happening from only one or more particular devices using the connection but not on others even when connected wirelessly and situated in the same location or using the same physical network wire, it may be indicative of a compromised system. If the device is using a wired network connection, be sure to check any physical cables that may be causing network issues.
FIGURE 12-4: An example of communication problems while streaming video. Note the viewable portion of the rotating circle in the middle of the video image.
Your device’s settings have changed
If you notice that some of your device’s settings have changed — and you’re certain that you did not make the change — that may be a sign of problems. Of course, some software makes setting changes, too (especially on classic computers, as opposed to smartphones), so changes may have a legitimate source as well. Most software, however, does not make major changes without notifying you. If you see dramatic settings changes, beware.
Your device is sending or receiving strange email messages
If your friends or colleagues report receiving emails from you that you did not send to them, something is likely amiss — this is especially true if the messages appear to be spam. Likewise, if you’re receiving emails that appear to be from people who claim to have never sent the relevant messages, you may have suffered a breach.
Your device is sending or receiving strange text messages
If your friends or colleagues report receiving text messages or other smartphone-type communications from you that you did not send to them, your smartphone may have been breached. Likewise, if you’re receiving messages that appear to be from people who claim to have never sent the relevant messages, you may have suffered a breach. As before, there could be other explanations for such a situation, and it is possible that some other system or collection of systems are the actual victims who have been breached.
New software (including apps) is installed on your device — and you didn’t install it
If new programs or apps suddenly appear on your device and you did not install them, something may be amiss. While, especially in the case of some portable devices, the manufacturer or relevant service provider may occasionally install certain types of apps without your knowledge, if new apps suddenly appear, you should always look into the matter. Of course, if you are using a corporate device that is centrally managed, the system administrators may have “pushed down” an app to you, so check with them.
Do a Google search on the apps and see what reliable tech sites say about them. If the apps are not showing up on other people’s devices, you may have a serious issue on your hands.
Your device’s battery seems to drain more quickly than before
Malware running in the background uses battery power and can help drain the battery of laptops, smartphones, and tablets. Keep in mind, however, that the performance of rechargeable batteries can deteriorate over time due to repeated draining and charging. So, if your three-year-old laptop that you use every day does not seem to be holding a charge quite as well as it did three years prior, that may not be indicative of anything other than natures conforming to the laws of physics.
Your device seems to run hotter than before
Malware running the background uses CPU cycles and can cause a device to run physically hotter than before. You may hear internal cooling fans going on louder or more often than you usually do, or you may feel that the device is physically hotter to the touch.
File contents have been changed
If the contents of files have changed without you changing them and without you running any software that you expect would change them, something may be seriously amiss. Of course, if you let other people use your computer and gave them access to the files in question, before blaming malware or a hacker, be sure to check with the people you let use the computer whether they made any changes either on purpose or by accident.
Files are missing
If files seem to have disappeared without you deleting them and without you running any software that you expect might delete them, something may be seriously amiss. Of course, technical failures and human mistakes can also cause files to disappear — and, if you let someone else use your computer, that person may be the culprit.
Websites appear different than before
If someone has installed malware that is proxying on your device — that is, sitting between your browser and the Internet and relaying the communications between them (while reading all the contents of the communications and, perhaps, inserting various instructions of its own) — it may affect how some sites display and/or cause some sites, apps, or features within either or both, to malfunction.
Your Internet settings show a proxy, and you never set one up
If someone has configured your device to use their server as a proxy, that party may be attempting to read data sent to and from your device and may try to modify the contents of your session or even seek to hijack it altogether.
Some legitimate programs do configure Internet proxies — but such proxy information should show up when the software is installed and initially run, not suddenly after you click on a questionable link or download a program from a less-than-trustworthy source. (See Figure 12-5.)
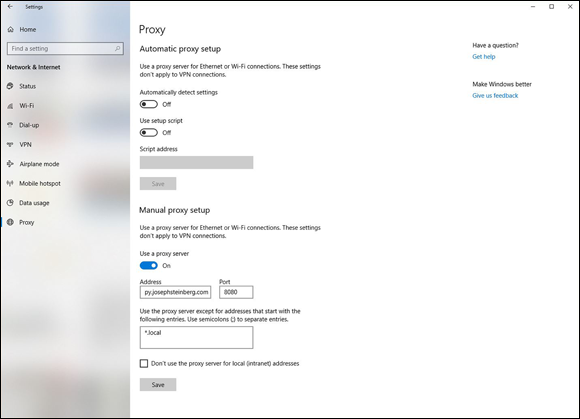
FIGURE 12-5: Internet connections configured to use a proxy. If you do not use a proxy and suddenly one appears listed in your Internet settings, something is likely amiss.
Some programs (or apps) stop working properly
If apps that you know used to work properly on your device suddenly stop functioning as expected, you may be experiencing a symptom of either proxying or malware interfering with the apps’ functionality.
Security programs have turned off
If the security software that you normally run on your device has suddenly been disabled, removed, or configured to ignore certain problems, it may be a sign that a hacker (or malware) has penetrated your device and has turned off its defenses to prevent both the attacker’s efforts from being blocked as well as to ensure that you do not receive warnings as the attacker carries out various additional nefarious activities.
An increased use of data or text messaging (SMS)
If you monitor your smartphone’s data or SMS usage and see greater usage figures than you expect, especially if that increase begins right after some suspicious event, it may be a sign that malware is transmitting data from your device to other parties. You can even check your data usage per app — if one of them looks like it is using way too much data for the functionality that it provides, something may be amiss.
Increased network traffic
If you monitor your device’s Wi-Fi or wired network usage and see greater levels of activity than you expect, especially if that increase begins right after some suspicious event, it may be a sign that malware is transmitting data from your device to other parties.
Keep in mind that different types of apps can use wildly different amounts of bandwidth. An app used for sending email messages, for example, should usually be using no more than a tiny fraction of the bandwidth used by someone’s Netflix app if that user streams and watches shows and/or movies on a regular basis.
Unusual open ports
Computers and other Internet-connected devices communicate using “ports” that can be thought of as numbered ports virtually lined up along the device as if they were piers along the coast. Communications for different applications typically enter the device via different ports. Ports are numbered, and most port numbers should always be closed — that is, not configured to allow communications in.
Your device starts crashing
If your computer, tablet, or smartphone suddenly starts to crash on a much more frequent basis than in the past, malware may be running on it. Of course, if you just upgraded your operating system, installed or updated drivers for hardware components, or installed some significant new software package, that is a more likely source for the problem.
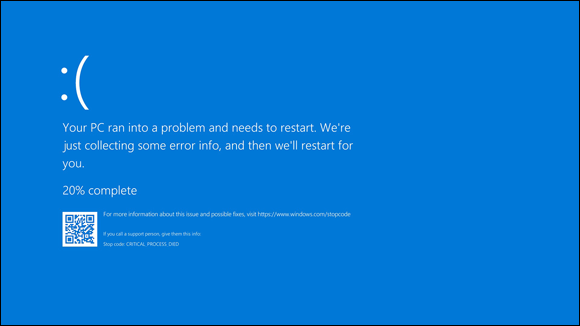
FIGURE 12-6: The modern version of the notorious Blue Screen of Death that appears after a severe crash of a computer running Microsoft Windows 10.
Your cellphone bill shows unexpected charges up to here
Criminals are known to have exploited compromised smartphones in order to make expensive overseas phone calls on behalf of a remote party proxying through the device. Likewise, they can use a breached device to send SMS messages to international numbers and can ring up various other phone charges in other ways.
Unknown programs request access
Most security software for computers warns users when a program first attempts to access the Internet. If you receive such warnings and you don’t recognize the program that is seeking access, or you recognize the program but can’t understand why it would need to access the Internet (for example, Windows Calculator or Notepad), something may be amiss.
External devices power on unexpectedly
If one or more of your external input devices (including devices such as cameras, scanners, and microphones) seem to power on at unexpected times (for example, when you’re not using them), it may indicate that malware or a hacker is communicating with them or otherwise using them. There are attacks that are known to have involved criminals remotely turning on people’s cameras and spying on them.
Your device acts as if someone else were using it
Malicious actors sometimes take over computers and use them via remote access almost as if they were sitting in front of the device’s keyboard. If you see your device acting as if someone else is in control — for example, you see the mouse pointer moving or keystrokes being entered while you’re not using your mouse or keyboard — it may be a sign that someone else is actually controlling the machine.
New browser search engine default
As part of several attack techniques, hackers are known to change the default search engine used by people browsing the web. If your own browser’s default search engine changed and you did not change it, something may be amiss. (To check if your search engine changed, check the list of default applications by searching for “default apps” in the Windows search box.)
Your device password has changed
If the password to your phone, tablet, or computer changed without you changing it, something is wrong, and the cause is likely something serious.
Pop-ups start appearing
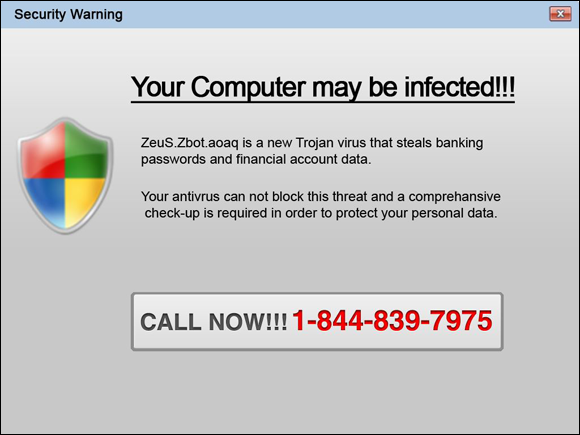
FIGURE 12-7: This pop-up window from adware malware attempts to scare people into purchasing bogus security software.
Keep in mind that pop-ups that appear when you’re not using a web browser are a big red flag, as are pop-ups advising you to download and install “security software” or to visit websites of questionable repute. Pop-ups should never appear on an Android device.
New browser add-ons appear
You should be prompted before any browser add-on is installed. If a new add-on is installed without your knowledge, it likely indicates a problem. Some malware is delivered in poisoned versions of various browser toolbars.
New browser home page
As part of several attack techniques, hackers are known to change the home page of users’ browsers. If your own browser’s home page changed and you did not change it, something may be amiss.
Your email from the device is getting blocked by spam filters
If email that you send from the device in question used to be able to reach intended recipients with no problem, but is suddenly getting blocked by spam filters, it may be a sign that someone or something altered your email configuration in order to relay your messages through some server that is allowing an attacker to read, block, or even modify, your messages, and which other security systems are flagging as problematic. There are also other possible causes, however, so if you cannot find the source of the issue, you may want to check with your network administrator, email provider, or Internet provider.
Your device is attempting to access “bad” sites
If you use your computer, tablet, or smartphone on a network that blocks access to known problematic sites and networks (many businesses, organizations, and government entities have such technology on both their internal and bring-your-own-device [BYOD] networks) and you find out that your device was trying to access such sites without your knowledge, your device is likely compromised.
You’re experiencing unusual service disruptions
If your smartphone seems to be suddenly dropping calls in locations with good cellular signal, or if you find your device unable to make calls altogether at times when you appear to have ostensibly good signal strength, something may be amiss.
Keep in mind that in most cases, the symptoms described here emanate from technical issues unrelated to a breach. However, in some cases, a breach is the reason for such ailments. So, if you noticed the relevant symptoms shortly after you took some action that you now question or regret, you may want to consider whether you need to take corrective action (see Chapter 13).
Your device’s language settings changed
People rarely change the language settings on their computers after performing the initial language setup procedure upon acquiring their devices or upon configuring a new keyboard, and few software packages change such settings either. So, if your computer is suddenly displaying menus and/or prompts in a foreign language or even has a language installed that you never installed, something is likely wrong.
You see unexplained activity on the device
If, on your device, you see emails in your Sent folder that you did not send, your device or email account was likely compromised. Likewise, if files that you’re certain that you never downloaded appear in your Downloads folder, someone else may have downloaded them to your device.
You see unexplained online activity
If your social media account has social media posts that you’re certain that neither you nor any app that you have authorized made, something is clearly amiss. It may be that your account was breached, and your devices are all secure, or it may be that one of your devices with access to the account was breached and became the conduit for the unauthorized access to your account.
The same is true if you see videos that you never ordered appearing in your previous rentals of a video streaming service, purchases that you never made appearing in your order history at an online retailer, and so on.
Your device suddenly restarts
While restarts are an integral part of many operating system updates, they should not happen suddenly outside the context of such updates. If your device is regularly rebooting without your approval, something is wrong. The only question is whether the problem emanates from a security breach or from some other issue.
You see signs of data breaches and/or leaks
Of course, if you know that some of your data has leaked, you should try to determine the source of the problem — and the process of checking obviously includes examining for signs of problems on all your smartphones, tablets, and computers.
You are routed to the wrong website
If you’re sure that you typed in a correct URL, but were still routed to the wrong website, something is amiss. The problem may reflect a security breach elsewhere, but it could indicate that someone has compromised your device as well.
If the misrouting happens from only one or more particular devices, but not from others on the same network, the odds are that the devices in question were compromised. A hacker or malware could have configured poisoned routing tables on your device, for example. If you see that you are being incorrectly routed from multiple devices but only when they are connected to a particular network, or that a device that routes properly when connected to other networks routes improperly when connected to a particular network, networking equipment from that network, or a provider of routing services (such as DNS) to that network may have been compromised.
In any case, never perform any sensitive task (such as logging into a website) from a device that is routing you incorrectly. Even better, don’t use the device at all (other than for debugging) until you figure out what is going on.
Your hard drive or SSD light never seems to turn off
If your hard drive or solid state drive (SSD) light remains on constantly, or near constantly, malware may be doing something to the drive. Of course, hard drive and SSD lights can come on for legitimate reasons when you are not actively using a computer — and, sometimes, a legitimate reason such as the system optimizing the disk in the background or performing a search for malware will cause the light to be on for quite some time — so don’t panic if the light being on is the only sign that something might be amiss.
Other abnormal things happen
It is impossible to list all the possible symptoms that malware can cause a device to exhibit. So, if you keep in mind that parties are seeking to hack into your systems, and that anomalous behavior by your device may be a sign of problems, you increase your odds of noticing when something seems off — and, of properly responding to a breach if one does, in fact, occur.

 If you’ve already received notification from a third-party provider where you store data, or where others store data about you, that your data has been compromised or may have been compromised, refer to
If you’ve already received notification from a third-party provider where you store data, or where others store data about you, that your data has been compromised or may have been compromised, refer to  One note: Some strains of bogus smartphone ransomware — yes, that is a real thing — display such messages but do not actually encrypt, destroy, or pilfer data. Before taking any corrective action — and certainly before paying any ransoms or ransom negotiation services — always check that ransomware is real.
One note: Some strains of bogus smartphone ransomware — yes, that is a real thing — display such messages but do not actually encrypt, destroy, or pilfer data. Before taking any corrective action — and certainly before paying any ransoms or ransom negotiation services — always check that ransomware is real. Keep in mind that none of the following clues exists in a vacuum, nor does the presence of any individual symptom, on its own, provide a guarantee that something is amiss. Multiple reasons other than the occurrence of a breach may cause devices to act abnormally and to exhibit one or more of the ailments described in the following sections.
Keep in mind that none of the following clues exists in a vacuum, nor does the presence of any individual symptom, on its own, provide a guarantee that something is amiss. Multiple reasons other than the occurrence of a breach may cause devices to act abnormally and to exhibit one or more of the ailments described in the following sections.