 Types of Attacks and Malicious Software
Types of Attacks and Malicious Software

Attacks can be made against virtually any layer or level of software, from network protocols to applications. When an attacker finds a vulnerability in a system, they exploit the weakness to attack the system. The effect of an attack depends on the attacker’s intent and can result in a wide range of effects, from minor to severe. An attack on one system might not be visible on the user’s system because the attack is actually occurring on a different system, and the data the attacker will manipulate on the second system is obtained by attacking the first system.
 Avenues of Attack
Avenues of Attack
A computer system is attacked for one of two general reasons: it is specifically targeted by an attacker, or it is a target of opportunity. In the first case, the attacker has chosen the target not because of the hardware or software the organization is running, but for another reason, such as a political reason. For example, an individual in one country might attack a government system in another country to gather secret information. Or the attacker might target an organization as part of a “hacktivist” attack—the attacker could deface the website of a company that sells fur coats, for example, because the attacker believes using animals in this way is unethical. Perpetrating some sort of electronic fraud is another reason a specific system might be targeted for attack. Whatever the reason, the attacker usually begins an attack of this nature before they know which hardware and software the organization uses.
The second type of attack, an attack against a target of opportunity, is launched against a site that has hardware or software that is vulnerable to a specific exploit. The attacker, in this case, is not targeting the organization; they have instead learned of a specific vulnerability and are simply looking for an organization with this vulnerability that they can exploit. This is not to say that an attacker might not be targeting a given sector and looking for a target of opportunity in that sector. For example, an attacker who wants to obtain credit card or other personal information may search for any exploitable company that stores credit card information on its system to accomplish the attack.
Targeted attacks are more difficult and take more time and effort than attacks on a target of opportunity. The latter type of attack simply relies on the fact that, with any piece of widely distributed software, somebody in the organization will not have patched the system like they should have.

Tech Tip
Defense Begins with Eliminating Vulnerabilities
Defense against attacks begins with eliminating vulnerabilities. Vulnerabilities are exploited by attackers to gain access to a system. Minimization of vulnerabilities is one of the foundational elements of defense.
![]()
Cross Check
Anatomy of an Attack
Hackers use a process when attacking, and this is covered in detail in Chapter 22.
Minimizing Possible Avenues of Attack
By understanding the steps an attacker can take, you can limit the exposure of your system and minimize the possible avenues an attacker can exploit. Your first step in minimizing possible attacks is to ensure that all patches for the operating system and applications are installed. Many security problems, such as viruses and worms, exploit known vulnerabilities for which patches actually exist. These attacks are successful only because administrators have not taken the appropriate actions to protect their systems.
The next step is to limit the services that are running on the system. As mentioned in earlier chapters, limiting the number of services to those that are absolutely necessary provides two safeguards: it limits the possible avenues of attack (the possible services for which a vulnerability may exist and be exploited), and it reduces the number of services the administrator has to worry about patching in the first place.
![]()
Cross Check
Baseline Analysis and Patching of Systems
Keeping a system patched and up to date for the operating system and applications is the best defense against exposed vulnerabilities. How up to date is the system you are currently using? How do you know? Chapter 14 covers the topics of baselining and patching of systems in order to understand and remove vulnerabilities. Refer to that chapter for more in-depth information on how to perform these activities.
Another step is to limit public disclosure of private information about your organization and its computing resources. Since the attacker is after this information, don’t make it easy to obtain.
 Malicious Code
Malicious Code
Malicious code refers to software that has been designed for some nefarious purpose. Malicious code can damage a system in many ways, and lead to compromise and risk. Most malware instances attack vulnerabilities in programs or operating systems. This is why patching of vulnerabilities is so important, because it closes the point of entry for most malware. Typically the installation of malicious code is done in such a way that it is not obvious to the authorized users. There are a wide array of different types of malicious software including viruses, trojan horses, logic bombs, spyware, and worms, and ransomware.
Malware can be fairly complex in its construction, with specific features designed to assist malware in avoiding detection. Modern malware can be multipart in construction, where several pieces work together to achieve a desired effect. When malware has multiple different objects that it specifically attacks, it is called multipartite. Many types of malware can include a changing encryption layer to resist pattern-matching detection. These are called polymorphic. If the malware actually changes the code at the time of infection, this property is called metamorphic.
 Malware
Malware
Malware refers to software that has been designed for some nefarious purpose. Such software can be designed to cause damage to a system, such as by deleting all files, or it can be designed to create a backdoor into the system to grant access to unauthorized individuals. Generally the installation of malware is done so that it is not obvious to the authorized users. Several different types of malicious software can be used, such as viruses, trojan horses, logic bombs, spyware, and worms, and they differ in the ways they are installed and their purposes.
Ransomware
Ransomware is a form of malware that performs some action and extracts a ransom from the user. Ransomware typically encrypts files on a system and then leaves them unusable either permanently, acting as a denial of service, or temporarily until a ransom is paid, thus the name. Ransomware is typically a worm, completely automated, and when targeted as a means of denial of service, the only repair mechanism is to rebuild the system. This can be time consuming and/or impractical in some cases, making this attack mechanism equivalent to the physical destruction of assets. Crypto-malware is an early name given to ransomware.
A ransomware threat that first appeared in 2013 was CryptoLocker, a trojan horse that encrypted certain files using RSA public key encryption. When the user attempted to get these files, they were provided with a message instructing them how to purchase the decryption key. Because the system is using 2048-bit RSA encryption, brute force decryption was out of the realm of recovery options. The system was highly automated, and users have a short time window in which to get the private key. Failure to get the key resulted in the loss of the data.
In May of 2017, a cryptoworm form of malware called WannaCry was released, resulting in a ransomware attack that swept across many government computers in Europe, including medical devices in the UK’s NHS. This ransomware created havoc by exploiting the EternalBlue vulnerability in Microsoft Windows systems that was exposed by the group known as Shadow Brokers. The U.S. announced in December of 2017 that it believed that the Lazarus Group, which works on behalf of the North Korean government, carried out the WannaCry attack.

Tech Tip
WannaCry and Marcus Hutchins
WannaCry was stopped by Marcus Hutchins, a hacker turned white hat (authorized). Marcus found a vulnerability in the WannaCry worm and was able to disable it globally. His story as a hacker is an amazing journey, involving crime, prosecution, and eventually vindication when he stopped WannaCry. This story can be read in Wired magazine’s treatise at www.wired.com/story/confessions-marcus-hutchins-hacker-who-saved-the-internet/.
Trojans
A trojan horse, or simply trojan, is a piece of software that appears to do one thing (and may, in fact, actually do that thing) but hides some other functionality. The analogy to the famous story of antiquity is very accurate. In the original case, the object appeared to be a large wooden horse, and in fact it was. At the same time, it hid something much more sinister and dangerous to the occupants of the city of Troy. As long as the horse was left outside the city walls, it could cause no damage to the inhabitants. However, it had to be taken in by the inhabitants of Troy, and it was inside that the hidden purpose was activated. A computer trojan works in much the same way. Unlike a virus, which reproduces by attaching itself to other files or programs, a trojan is a standalone program that must be copied and installed by the user—it must be “brought inside” the system by an authorized user. The challenge for the attacker is enticing the user to copy and run the program. This generally means that the program must be disguised as something that the user would want to run—a special utility or game, for example. Once it has been copied and is inside the system, the trojan will perform its hidden purpose with the user often still unaware of its true nature.
![]()
Ransomware is a form of malware that locks the user out of their files or even the entire device until an online ransom payment is made to restore access. In most cases, the best solution is to have a complete and accurate backup available to recover the lost files.
A good example of a trojan is Back Orifice (BO), originally created in 1999 and now offered in several versions. BO can be attached to a number of types of programs. Once it is attached, and once an infected file is run, BO will create a way for unauthorized individuals to take over the system remotely, as if they were sitting at the console. BO is designed to work with Windows-based systems. Many trojans communicate to the outside through a port that the trojan opens, and this is one of the ways trojans can be detected.

Tech Tip
Famous Trojans
There have been many “famous” trojans that have caused significant havoc in systems. Back Orifice (BO), created in 1999, was offered in several versions. BO can be attached to a number of types of programs. Koobface is a trojan that affects Facebook users. Zeus is a financial trojan/malware that has a wide range of functionality.
![]()
Worms act like a virus but also have the ability to travel without human action. They do not need help to spread.
Worms
It was once easy to distinguish between a worm and a virus. Recently, with the introduction of new breeds of sophisticated malicious code, the distinction has blurred. Worms are pieces of code that attempt to penetrate networks and computer systems. Once a penetration occurs, the worm will create a new copy of itself on the penetrated system. Reproduction of a worm thus does not rely on the attachment of the virus to another piece of code or to a file, which is the definition of a virus.
Viruses were generally thought of as a system-based problem, and worms were network-based. If the malicious code is sent throughout a network, it may subsequently be called a worm. The important distinction, however, is whether the code has to attach itself to something else (a virus) or if it can “survive” on its own (a worm).
![]()
Tech Tip
Protection Against Worms
How you protect your system against worms depends on the type of worm. Those attached and propagated through e-mail can be avoided by following the same guidelines about not opening files and not running attachments unless you are absolutely sure of their origin and integrity. Protecting against worms involves securing systems and networks against penetration in the same way you would protect your systems against human attackers: install patches, eliminate unused and unnecessary services, enforce good password security, and use firewalls and intrusion detection systems (IDSs). More sophisticated attacks, such as the Samy worm, are almost impossible to avoid.
Viruses
The best-known type of malicious code is the virus. Much has been written about viruses as a result of several high-profile security events that involved them. A virus is a piece of malicious code that replicates by attaching itself to another piece of executable code. When the other executable code is run, the virus also executes and has the opportunity to infect other files and perform any other nefarious actions it was designed to do. The specific way that a virus infects other files, and the type of files it infects, depends on the type of virus. The first viruses created were of two types—boot sector viruses and program viruses.
Boot Sector Virus
A boot sector virus infects the boot sector portion of the bootable media for a system. When a computer is first turned on, a small portion of the operating system is initially loaded from hardware. This small operating system then attempts to load the rest of the operating system from a specific location (sector) on either the USB thumb drive or detachable hard drive. A boot sector virus infects this portion of the drive.
An early example of this type of virus was the Stoned virus, which moved the true Master Boot Record (MBR) from the first to the seventh sector of the first cylinder and replaced the original MBR with the virus code. When the system was turned on and the virus was first executed, it had a one-in-seven chance of displaying a message stating the computer was “stoned.” Otherwise, it would not announce itself and would instead attempt to infect other boot sectors. This virus was rather tame in comparison to other viruses of its time, which were often designed to delete the entire hard drive after a period of time in which they would attempt to spread.
Boot sector viruses still exist. NotPetya would overwrite the boot sector, and hackers routinely use this method to modify boot sectors to load drivers used by malware.
Program Virus
A second type of virus is the program virus, which attaches itself to executable files—typically files ending in .exe or .com on Windows-based systems. The virus is attached in such a way that it is executed before the program executes. Most program viruses also hide a nefarious purpose, such as deleting the hard drive data, which is triggered by a specific event, such as a particular date or after a certain number of other files are infected. Like other types of viruses, program viruses are often not detected until after they execute their malicious payload. One method that has been used to detect this sort of virus before it has an opportunity to damage a system is to calculate checksums for commonly used programs or utilities. Should the checksum for an executable ever change, it is quite likely that it is due to a virus infection.

Tech Tip
Modern Virus and Worm Threats
Early virus and worm attacks would cause damage to PCs, but they were generally visible to users. Many modern viruses and worms are used to deliver payloads that lead to machines becoming zombies in a botnet, controlled by an attacker. This type of attack is typically invisible to the end user, so as not to alert them to the malware.
Macro Virus
In the late 1990s, another type of virus appeared that now accounts for the majority of viruses. As systems and operating systems became more powerful, the boot sector virus, which once accounted for most reported infections, became less common. Systems no longer commonly booted from floppies, which were the main method for boot sector viruses to spread. Instead, the proliferation of software that included macro programming languages resulted in a new breed of virus—the macro virus.
The Concept virus was the first known example of this new breed. It appeared to be created to demonstrate the possibility of attaching a virus to a document file, something that had been thought to be impossible before the introduction of software that included powerful macro language capabilities. By this time, however, Microsoft Word documents could include segments of code written in a derivative of Visual Basic. Further development of other applications that allowed macro capability, and enhanced versions of the original macro language, had the side effect of allowing the proliferation of viruses that took advantage of this capability.
This type of virus is so common today that it is considered a security best practice to advise users never to open a document attached to an e-mail if it seems at all suspicious. Many organizations now routinely have their mail servers eliminate any attachments containing Visual Basic macros.
Fileless Malware
Most antivirus/anti-malware solutions find malware through monitoring the filesystem for writes and then filter the writes for known signatures. When a piece of malware operates only in memory, never touching the filesystem, it is much harder to detect. This type of attack is called a fileless malware, or memory-based attack.
![]()
Remember that unlike a traditional virus, which attaches itself to a file, a fileless virus lives in memory and will continue to run until the device is powered down.
Avoiding Virus Infection
Always being cautious about executing programs or opening documents sent to you is a good security practice. “If you don’t know where it came from or where it has been, don’t open or run it” should be the basic mantra for all computer users. Another security best practice for protecting against virus infection is to install and run an antivirus program. Since these programs are designed to protect against known viruses, it is also important to maintain an up-to-date listing of virus signatures for your antivirus software. Antivirus software vendors provide this information, and administrators should stay on top of the latest updates to the list of known viruses.
Two advances in virus writing have made it more difficult for antivirus software to detect viruses. These advances are the introduction of stealth virus techniques and polymorphic viruses. A stealthy virus employs techniques to help evade being detected by antivirus software that uses checksums or other techniques. Polymorphic viruses also attempt to evade detection, but they do so by changing the virus itself (the virus “evolves”). Because the virus changes, signatures for that virus may no longer be valid, and the virus can thus escape detection by antivirus software.
Armored Virus
When a new form of malware/virus is discovered, antivirus companies and security researchers will decompile the program in an attempt to reverse-engineer its functionality. Much can be determined from reverse engineering, such as where the malware came from, how it works, how it communicates, how it spreads, and so forth. Armoring malware can make the process of determining this information much more difficult, if not impossible. Some malware, such as Zeus, comes encrypted in ways to prevent criminals from stealing the intellectual property of the very malware that they use.
![]()
Modern viruses have a whole host of defenses from detection and analysis. Polymorphic viruses change their appearance, making signature matches difficult. Armored viruses resist being reverse-engineered to determine how they operate. Viruses are designed to be quiet, avoid detection, avoid analysis, and still work—they are significant threats.
Virus Hoaxes
Viruses have caused so much damage to systems that many Internet users become extremely cautious any time they hear a rumor of a new virus. Many users will not connect to the Internet when they hear about a virus outbreak, just to be sure their machines don’t get infected. This has given rise to virus hoaxes, in which word is spread about a new virus and the extreme danger it poses. It may warn users to not read certain files or connect to the Internet.
Hoaxes can actually be even more destructive than just wasting time and bandwidth. Some hoaxes warning of a dangerous virus have included instructions to delete certain files if they’re found on the user’s system. Unfortunately for those who follow the advice, the files may actually be part of the operating system, and deleting them could keep the system from booting properly. This suggests another good piece of security advice: make sure of the authenticity and accuracy of any virus report before following somebody’s advice. Antivirus software vendors are a good source of factual data for this sort of threat as well.
Polymorphic Malware
The detection of malware by anti-malware programs is primarily done through the use of a signature. Files are scanned for sections of code in the executable that act as markers—unique patterns of code that enable detection. Just as the human body creates antigens that match marker proteins, anti-malware programs detect malware through unique markers present in the code of the malware.
Malware writers are aware of this functionality and have adapted methods to defeat it. One of the primary means of avoiding detection by sensors is the use of polymorphic code, which is code that changes on a regular basis. These changes or mutations are designed not to affect the functionality of the code, but rather to mask any signature from detection. Polymorphic malware can change its coding after each use, making each replicant different from a detection point of view.
Potentially Unwanted Programs
Potentially unwanted program (PUP) is a designation used by security companies and antivirus vendors to identify programs that may have adverse effects on a computer’s security or privacy. Frequently these involve adware or spyware components and are used for revenue generation purposes.
![]()
Potentially unwanted programs are a form of malware. The name is one the industry chose because the makers of PUPs claim you read and agreed to their terms as part of a download agreement. It is easy to miss these details when installing programs, and then you have unwanted apps. PUPs can exhibit some very undesired characteristics, such as the following:
![]() Slowing down your computer
Slowing down your computer
![]() Displaying a ton of annoying ads
Displaying a ton of annoying ads
![]() Adding toolbars that steal space on the browser
Adding toolbars that steal space on the browser
![]() Collecting private information
Collecting private information
A common source of PUPs is third-party download sites for downloading apps—even legitimate apps can be bundled by third-party distributers. The use of an anti-malware solution should catch and enable PUPs to be stopped before installation.
Command and Control
Command-and-control servers are used by hackers to control malware that has been launched against targets. Malware infections are seldom a single file on a single machine when an attack occurs in an enterprise. Multiple malware elements, on multiple systems, under various IDs, all working to provide a means for hackers to re-enter a system are commonly found in enterprises. These malware elements also work to exfiltrate stolen data.
Botnets
Malware can have a wide range of consequences on a machine, from relatively benign to extremely serious. One form of malware that is seemingly benign to a user is a botnet zombie. Hackers create armies of machines by installing malware agents on the machines, which then are called zombies. These collections of machines are called botnets. These zombie machines are used to conduct other attacks and to spread spam and other malware. Botnets have grown into networks of over a million nodes and are responsible for tens of millions of spam messages daily.
![]()
Sometime before 2007, the FBI began an anti-botnet operation dubbed Bot Roast. The operation dismantled several botnets and led to several convictions of botnet operators. Other successful anti-botnet operations include the McColo takedown, which decimated Rustock, and coordinated efforts by industry, academia, and law enforcement that have led to the dismantling of BredoLabs, Mariposa, and made significant inroads against Conficker and Zeus.
Bots use a structure by which large legions of infected machines are controlled by a smaller number of command-and-control (C2) servers. These servers are also typically machines owned by someone else, infected with just a different set of malware. The C2 machines allow the bots to be controlled, letting the botnet owner rent out the spam or use it for other evil intent. The C2 aspect is both a strength and a weakness. Attacking the individual bots on machines worldwide is a losing cause since they can number in the millions. Attacking the C2 side and taking these bots down has proven to be an effective method against botnets.

Tech Tip
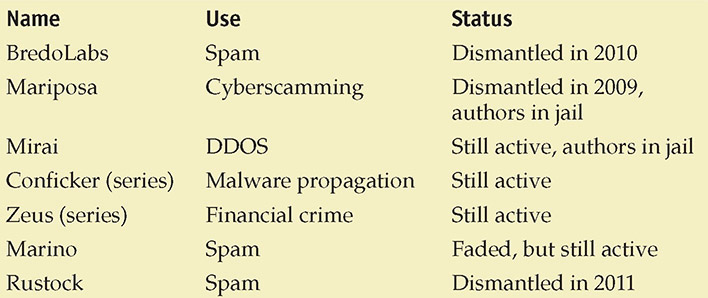
Famous Botnets
The following are some famous botnets and their current status (as of the end of 2020):
Crypto-Malware
The first thought when one sees the term crypto-malware is ransomware, but that would be wrong. Crypto-malware is now the name the security industry uses for malware that uses a system’s resources to mine cryptocurrency. This is really just a theft-of-services attack, where an attacker is using the CPU cycles of someone else’s computer to do the crypto mining.
Logic Bombs
Logic bombs, unlike viruses and Trojans, are a type of malicious software that is deliberately installed, generally by an authorized user. A logic bomb is a piece of code that sits dormant for a period of time until some event invokes its malicious payload. An example of a logic bomb might be a program that is set to load and run automatically, and that periodically checks an organization’s payroll or personnel database for a specific employee. If the employee is not found, the malicious payload executes, deleting vital corporate files.
![]()
If the event invoking the logic bomb is a specific date or time, the program will often be referred to as a time bomb. In one famous example, a disgruntled employee left a time bomb in place just prior to being fired from his job. Two weeks later, thousands of client records were deleted. Police were eventually able to track the malicious code to the disgruntled ex-employee, who was prosecuted for his actions. He had hoped that the two weeks that had passed since his dismissal would have caused investigators to assume he could not have been the individual who had caused the deletion of the records.
Logic bombs are difficult to detect because they are often installed by authorized users and, in particular, by administrators who are also often responsible for security. This demonstrates the need for a separation of duties and a periodic review of all programs and services that are running on a system. It also illustrates the need to maintain an active backup program so that if your organization loses critical files to this sort of malicious code, it loses only transactions that occurred since the most recent backup and no permanent loss of data results.
Spyware
Spyware is software that “spies” on users, recording and reporting on their activities. Typically installed without user knowledge, spyware can perform a wide range of activities. It can record keystrokes (commonly called keylogging) when the user logs in to specific websites. It can monitor how a user uses a specific piece of software (for example, monitoring attempts to cheat at games).

Keylogging is one of the holy grails for attackers, because if they can get a keylogger on a machine, the capturing of user-typed credentials is a quick win for the attacker.
Many uses of spyware seem innocuous at first, but the unauthorized monitoring of a system can be abused very easily. In other cases, the spyware is specifically designed to steal information. Many states have passed legislation banning the unapproved installation of software, but many cases of spyware circumvent this issue through complex and confusing end-user license agreements.
Adware
The business of software distribution requires a form of revenue stream to support the cost of development and distribution. One form of revenue stream is advertising. Software that is supported by advertising is called adware. Adware comes in many different forms. With legitimate adware, the user is aware of the advertising and agrees to the arrangement in return for free use of the software. This type of adware often offers an alternative, ad-free version for a fee. Adware can also refer to a form of malware that is characterized by software that presents unwanted ads. These ads are sometimes an irritant, and at other times represent an actual security threat. Frequently these ads are in the form of pop-up browser windows, and in some cases they cascade upon any user action.
Keyloggers
As the name suggests, a keylogger is a piece of software that logs all the keystrokes a user enters. Keyloggers in their own respect are not necessarily evil—you could even consider Microsoft Word to be a keylogger. What makes a keylogger a malicious piece of software is when its operation is (1) unknown to the user, and (2) not under the user’s control. Keyloggers have been marketed for a variety of uses—from surveillance over your children’s activity, or the activity of a spouse, to maintaining records of what has been done on a machine. Malicious keyloggers have several specific characteristics: they are frequently hidden from the user’s view, even when looking at Task Manager, and they are used against the end user’s interests. Hackers use keyloggers to obtain passwords and other sensitive pieces of information, enabling them to use these secrets to act as the user without the user’s consent. Keylogger functionality has even been found in legitimate programs, where keystrokes are recorded for “legitimate” purposes and then are stored in a fashion that enables unauthorized users to steal the data.
Remote-Access Trojans (RATs)
A remote-access trojan (RAT) is a toolkit designed to provide the capability of covert surveillance and/or the capability to gain unauthorized access to a target system. RATs often mimic the behavior of keyloggers and packet sniffers using the automated collection of keystrokes, usernames, passwords, screenshots, browser history, e-mails, chat logs, and more, but they also do so with a design of intelligence. RATs can also employ malware to infect a system with code that can be used to facilitate the exploitation of a target. Rather than just collect the information, RATs present it to an attacker in a form to facilitate the capability to gain unauthorized access to the target machine. This frequently involves the use of specially configured communication protocols that are set up upon initial infection of the target computer. This backdoor into the target machine can allow an attacker unfettered access, including the ability to monitor user behavior, change computer settings, browse and copy files, access connected systems, and more. RATs are commonly employed by the more skilled threat actors, although there are RATs that are easy enough for even beginners to employ.
A RAT should be considered another form of malware, but rather than just being a program, it has an operator behind it, guiding it to do even more persistent damage. RATs can be delivered via phishing e-mails, watering holes, or any of a myriad of other malware infection vectors. RATs typically involve the creation of hidden file structures on a system and are vulnerable to detection by modern anti-malware programs. There are several major families of RATs, but an exhaustive list would be long and ever increasing. When facing a more skilled adversary, it is not uncommon to find RAT packages that have been modified for specific use, such as the program used in the Ukraine electric grid attack in 2015.
Rootkit
Rootkits are a form of malware that is specifically designed to modify the operation of the operating system in some fashion to facilitate nonstandard functionality. The history of rootkits goes back to the beginning of the UNIX operating system, where rootkits were sets of modified administrative tools. Originally designed to allow a program to take greater control over an operating system’s functions when it fails or becomes unresponsive, the technique has evolved and is used in a variety of ways. One high-profile case occurred at Sony BMG Corporation, when rootkit technology was used to provide copy protection technology on some of the company’s CDs. Two major issues led to this being a complete debacle for Sony: First, the software modified systems without the users’ approval. Second, the software opened a security hole on Windows-based systems, creating an exploitable vulnerability at the rootkit level. This led the Sony case to be labeled as malware, which is the most common use of rootkits.
A rootkit can do many things—in fact, it can do virtually anything that the operating system does. Rootkits modify the operating system kernel and supporting functions, changing the nature of the system’s operation. Rootkits are designed to avoid, either by subversion or evasion, the security functions of the operating system to avoid detection. Rootkits act as a form of malware that can change thread priorities to boost an application’s performance, perform keylogging, act as a sniffer, hide other files from other applications, or create backdoors in the authentication system. The use of rootkit functionality to hide other processes and files enables an attacker to use a portion of a computer without the user or other applications knowing what is happening. This hides the exploit code from antivirus and anti-spyware programs, acting as a cloak of invisibility.
Rootkits can load before the operating system loads, acting as a virtualization layer, as in SubVirt and Blue Pill. Rootkits can exist in firmware, and these have been demonstrated in both video cards and expansion cards. Rootkits can exist as loadable library modules, effectively changing portions of the operating system outside the kernel. Further information on specific rootkits in the wild can be found at www.antirootkit.com.
![]()
Five types of rootkits exist:
![]() Firmware Attacks firmware on a system
Firmware Attacks firmware on a system
![]() Virtual Attacks at the virtual machine level
Virtual Attacks at the virtual machine level
![]() Kernel Attacks the kernel of the OS
Kernel Attacks the kernel of the OS
![]() Library Attacks libraries used on a system
Library Attacks libraries used on a system
![]() Application level Attacks specific applications
Application level Attacks specific applications
Once a rootkit is detected, it needs to be removed and cleaned up. Because of the invasive nature of rootkits, and the fact that many aspects of rootkits are not easily detectable, most system administrators don’t even attempt to clean up or remove them. It is far easier to use a previously captured clean system image and reimage the machine than to attempt to determine the depth and breadth of the damage and attempt to fix individual files.
Backdoors and Trapdoors
Backdoors were originally (and sometimes still are) nothing more than methods used by software developers to ensure that they can gain access to an application even if something were to happen in the future to prevent normal access methods. An example would be a hard-coded password that could be used to gain access to the program in the event that administrators forget their own system password. The obvious problem with this sort of backdoor (also sometimes referred to as a trapdoor) is that, because it is hard-coded, it cannot be removed. Should an attacker learn of the backdoor, all systems running that software would be vulnerable to attack.
The term backdoor is also more commonly used to refer to programs that attackers install after gaining unauthorized access to a system to ensure that they can continue to have unrestricted access to the system, even if their initial access method is discovered and blocked. Backdoors can also be installed by authorized individuals inadvertently, should they run software that contains a trojan horse (introduced earlier). A variation on the backdoor is the rootkit, discussed in the previous section, which is established not to gain root access but rather to ensure continued root access.

Common backdoors include Zeus, NetBus, and Back Orifice. Any of these, if running on your system, can allow an attacker remote access to your system—access that allows them to perform any function on your system.
Application-Level Attacks
Attacks against a system can occur at the network level, at the operating system level, at the application level, or at the user level (social engineering). Early attack patterns were against the network, but most of today’s attacks are aimed at the applications. This is primarily because this is where the objective of most attacks resides—or in the infamous words of bank robber Willie Sutton, “because that’s where the money is.” In fact, many of today’s attacks on systems are combinations of using vulnerabilities in networks, operating systems, and applications, all as a means to an end to obtain the desired objective of an attack, which is usually some form of data.
Application-level attacks take advantage of several facts associated with computer applications. First, most applications are large programs written by groups of programmers and, by their nature, have errors in design and coding that create vulnerabilities. For a list of typical vulnerabilities, see the Common Vulnerability and Exposures (CVE) list maintained by MITRE (https://cve.mitre.org). Second, even when vulnerabilities are discovered and patched by software vendors, end users are slow to apply patches, as evidenced by the SQL Slammer incident in January of 2003. The vulnerability exploited was a buffer overflow, and the vendor supplied a patch six months prior to the outbreak, yet the worm still spread quickly due to the multitude of unpatched systems.

Cross Check
Application Vulnerabilities
Applications are a common target of attacks, as attackers have shifted to easier targets as the network and OS have become more hardened. What applications are not up to date on the PC you use every day? How would you know? How would you update them? A more complete examination of common application vulnerabilities is presented in Chapter 19.
Malware Defenses
Malware in all forms—virus, worm, spyware, botnet, and so on—can be defended against by following these simple steps:
![]() Use an antivirus/anti-malware program. Most major-vendor antivirus/anti-malware suites are designed to catch most widespread forms of malware. In some markets, the antivirus software is being referred to as anti-x software, indicating that it covers more than viruses. However, because the threat environment changes literally daily, the signature files for the software need regular updates, which most antivirus programs offer to perform automatically.
Use an antivirus/anti-malware program. Most major-vendor antivirus/anti-malware suites are designed to catch most widespread forms of malware. In some markets, the antivirus software is being referred to as anti-x software, indicating that it covers more than viruses. However, because the threat environment changes literally daily, the signature files for the software need regular updates, which most antivirus programs offer to perform automatically.
![]() Keep your software up to date. Many forms of malware achieve their objectives through exploitation of vulnerabilities in software, both in the operating system and applications. Although operating system vulnerabilities were the main source of problems, today application-level vulnerabilities pose the greatest risk. Unfortunately, while operating system vendors are becoming more and more responsive to patching, most application vendors are not, and some, like Adobe, have very large footprints across most machines.
Keep your software up to date. Many forms of malware achieve their objectives through exploitation of vulnerabilities in software, both in the operating system and applications. Although operating system vulnerabilities were the main source of problems, today application-level vulnerabilities pose the greatest risk. Unfortunately, while operating system vendors are becoming more and more responsive to patching, most application vendors are not, and some, like Adobe, have very large footprints across most machines.
One of the challenges in keeping a system up to date is keeping track of the software that is on the system and keeping track of all vendor updates. There are several utility programs that one can use for this function across the enterprise. The key element is ensuring coverage across your application base.

Tech Tip
Defenses Against Malware
There are two primary defense mechanisms against malware: backups and updates. Malware acts against vulnerabilities, which are patched by keeping software up to date. One of the primary sources of loss is from the inability to recover something covered by backups.
 Attacking Computer Systems and Networks
Attacking Computer Systems and Networks
From a high-level standpoint, attacks on computer systems and networks can be grouped into two broad categories: attacks on specific software (such as an application or the operating system) and attacks on a specific protocol or service. Attacks on a specific application or operating system are generally possible because of an oversight in the code (and possibly in the testing of that code) or because of a flaw, or bug, in the code (again indicating a lack of thorough testing). Attacks on specific protocols or services are attempts either to take advantage of a specific feature of the protocol or service or to use the protocol or service in a manner for which it was not intended. This section discusses various forms of attacks of which security professionals need to be aware.
Denial-of-Service Attacks
A denial-of-service (DoS) attack is an attack designed to prevent a system or service from functioning normally. A DoS attack can exploit a known vulnerability in a specific application or operating system, or it can attack features (or weaknesses) in specific protocols or services. In a DoS attack, the attacker attempts to deny authorized users access either to specific information or to the computer system or network itself. This can be accomplished by crashing the system—taking it offline—or by sending so many requests that the machine is overwhelmed.

Tech Tip
Resource Exhaustion Attacks
Resource exhaustion attacks result in a denial of service as a result of a shortage of required resources. An example is a SYN flood attack, in which excess SYN packets consume all the memory needed to create new connections.
The purpose of a DoS attack can be simply to prevent access to the target system, or the attack can be used in conjunction with other actions to gain unauthorized access to a computer or network. For example, a SYN flood attack can be used to prevent service to a system temporarily in order to take advantage of a trusted relationship that exists between that system and another.
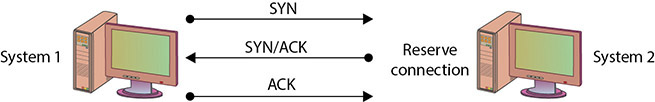
SYN flooding is an example of a DoS attack that takes advantage of the way TCP/IP networks were designed to function, and it can be used to illustrate the basic principles of any DoS attack. SYN flooding uses the TCP three-way handshake that establishes a connection between two systems. Under normal circumstances, the first system sends a SYN packet to the system with which it wants to communicate. The second system responds with a SYN/ACK if it is able to accept the request. When the initial system receives the SYN/ACK from the second system, it responds with an ACK packet, and communication can then proceed. This process is shown in Figure 15.1.
• Figure 15.1 The TCP three-way handshake
![]()
A SYN/ACK is actually the SYN packet sent to the first system combined with an ACK packet acknowledging the first system’s SYN packet.
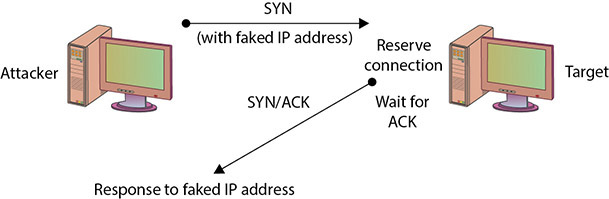
In a SYN flooding attack, the attacker sends fake communication requests to the targeted system. Each of these requests will be answered by the target system, which then waits for the third part of the handshake. Since the requests are fake (a nonexistent IP address is used in the requests, so the target system is responding to a system that doesn’t exist), the target will wait for responses that never come, as shown in Figure 15.2. The target system will drop these connections after a specific timeout period, but if the attacker sends requests faster than the timeout period eliminates them, the system will quickly be filled with requests. The number of connections a system can support is finite, so when more requests come in than can be processed, the system will soon be reserving all its connections for fake requests. At this point, any further requests are simply dropped (ignored), and legitimate users who want to connect to the target system will not be able to do so, because use of the system has been denied to them.
• Figure 15.2 A SYN flooding–based DoS attack
Another simple DoS attack is the infamous ping of death (POD), and it illustrates the other type of attack—one targeted at a specific application or operating system, as opposed to SYN flooding, which targets a protocol. In the POD attack, the attacker sends an Internet Control Message Protocol (ICMP) ping packet equal to, or exceeding, 64 KB. Certain older systems are not able to handle this size of packet, and the system will hang or crash.
Distributed Denial of Service
DoS attacks are conducted using a single attacking system. A DoS attack employing multiple attacking systems is known as a distributed denial-of-service (DDoS) attack. The goal of a DDoS attack is also to deny the use of or access to a specific service or system. DDoS attacks were made famous in 2000 with the highly publicized attacks on eBay, CNN, Amazon, and Yahoo!
![]()
A botnet is a network of machines controlled by a malicious user. Each of these controlled machines is commonly referred to as a zombie.
In a DDoS attack, service is denied by overwhelming the target with traffic from many different systems. A network of attack agents (sometimes called zombies) is created by the attacker, and upon receiving the attack command from the attacker, the attack agents commence sending a specific type of traffic against the target. If the attack network is large enough, even ordinary web traffic can quickly overwhelm the largest of sites.
Creating a DDoS attack network is not a simple task. The attack agents are not willing agents—they are systems that have been compromised and on which the DDoS attack software has been installed. To compromise these agents, the attacker has to have gained unauthorized access to the system or have tricked authorized users into running a program that installed the attack software. The creation of the attack network may in fact be a multistep process in which the attacker first compromises a few systems and then uses those systems as handlers or masters, which in turn compromise other systems. Once the network has been created, the agents wait for an attack message, which will include data on the specific target, before launching the attack. One important aspect of a DDoS attack is that with just a few messages to the agents, the attacker can have a flood of messages sent against the targeted system. Figure 15.3 illustrates a DDoS network with agents and handlers.
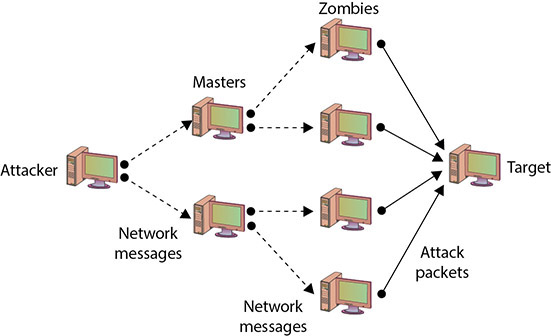
• Figure 15.3 DDoS attack

Tech Tip
Edge Blocking of ICMP
Blocking ICMP at the edge device of the network will prevent ICMP-based attacks from external sites while still allowing full ICMP functionality for traffic inside the network. Common practice is to block ICMP at the edge of IPv4 networks, although in IPv6, ICMP is a must-carry item and cannot be blocked.
A final option you should consider that will address several forms of DoS and DDoS attacks is to block ICMP packets at your border, since many attacks rely on ICMP. Blocking ICMP packets at the border devices prevents external ICMP packets from entering your network, and although this may block some functionality, it will leave internal ICMP functionality intact. It is also possible to block specific forms of ICMP; blocking Type 8, for instance, will block ICMP-based ping sweeps. It is worth noting that not all pings occur via ICMP; some tools, such as hping2, use TCP and UDP to carry ping messages.
Smurf Attack
In a specific DoS attack known as a smurf attack, the attacker sends a spoofed packet to the broadcast address for a network, which distributes the packet to all systems on that network. Further details are listed in the “IP Address Spoofing” section.
Defending Against DOS-Type Attacks
How can you stop or mitigate the effects of a DoS or DDoS attack? One important precaution is to ensure that you have applied the latest patches and upgrades to your systems and the applications running on them. Once a specific vulnerability is discovered, it does not take long before multiple exploits are written to take advantage of it. Typically you will have a small window of opportunity in which to patch your system between the time the vulnerability is discovered and the time exploits become widely available. A vulnerability can also be discovered by hackers, and exploits provide the first clues that a system has been compromised. Attackers can also reverse-engineer patches to learn what vulnerabilities have been patched, allowing them to attack unpatched systems.
Another approach involves changing the timeout option for TCP connections so that attacks such as the SYN flooding attack are more difficult to perform, because unused connections are dropped more quickly.
For DDoS attacks, much has been written about distributing your own workload across several systems so that any attack against your system would have to target several hosts to be completely successful. While this is effective against some DDoS attacks, if large enough DDoS networks are created (with tens of thousands of zombies, for example), any network, no matter how much the load is distributed, can be successfully attacked. Such an approach also involves additional costs to your organization to establish this distributed environment. Addressing the problem in this manner is actually an attempt to mitigate the effect of the attack rather than preventing or stopping it.
To prevent a DDoS attack, you must either be able to intercept or block the attack messages or keep the DDoS network from being established in the first place. Tools have been developed that will scan your systems, searching for sleeping zombies waiting for an attack signal. Many of the current antivirus/spyware security suite tools will detect known zombie-type infections. The problem with this type of prevention approach, however, is that it is not something you can do to prevent an attack on your network—it is something you can do to keep your network from being used to attack other networks or systems. You have to rely on the community of network administrators to test their own systems to prevent attacks on yours.
War-Dialing and War-Driving
War-dialing is the term used to describe an attacker’s attempt to discover unprotected modem connections to computer systems and networks. The term’s origin is the 1983 movie WarGames, in which the star has his machine systematically call a sequence of phone numbers in an attempt to find a computer connected to a modem. In the case of the movie, the intent was to find a machine with games the attacker could play, though obviously an attacker could have other purposes once access is obtained.
War-dialing was surprisingly successful, mostly because of rogue modems—unauthorized modems attached to computers on a network by authorized users. In most cases the reason for attaching the modem is not malicious—an individual may simply want to be able to go home and then connect to the organization’s network to continue working. This has become history with the rise of remote desktop technology and ubiquitous Internet connectivity.
Another avenue of attack on computer systems and networks has seen a tremendous increase over the last few years because of the increase in the use of wireless networks. War-driving is the unauthorized scanning for and connecting to wireless access points, frequently done while driving near a facility. Wireless networks have some obvious advantages—they free employees from the cable connection to a port on their wall, allowing them to move throughout the building with their laptops and still be connected.

Cross Check
Wireless Vulnerabilities
Wireless systems have their own vulnerabilities unique to the wireless protocols. Wireless systems are becoming very common. If your machine is wireless capable, how many wireless access points can you see from your current location? Securing wireless systems from unauthorized access is an essential element of a comprehensive security program. This material is covered in depth in Chapter 12.
Social Engineering
Social engineering relies on lies and misrepresentation, which an attacker uses to trick an authorized user into providing information or access the attacker would not normally be entitled to. Complete coverage of social engineering attacks can be found in Chapter 4.
Sniffing
The group of protocols that makes up the TCP/IP suite was designed to work in a friendly environment in which everybody who connected to the network used the protocols as they were designed. The abuse of this friendly assumption is illustrated by network-traffic sniffing programs, sometimes referred to as sniffers. Sniffing is when someone examines all the network traffic that passes their NIC, whether addressed for them or not.
A network sniffer is a software or hardware device that is used to observe traffic as it passes through a network on shared broadcast media. The device can be used to view all traffic, or it can target a specific protocol, service, or even string of characters (looking for logins, for example). Normally, the network device that connects a computer to a network is designed to ignore all traffic that is not destined for that computer. Network sniffers ignore this friendly agreement and observe all traffic on the network, whether destined for that computer or others, as shown in Figure 15.4. Some network sniffers are designed not just to observe all traffic but to modify traffic as well. Network sniffing is more difficult in switched network environments due to the way collision domains are eliminated in full-duplex switching, but certain techniques can be used (spanning ports, ARP poisoning, and attacks forcing a switch to fail and act as a hub) to circumvent this.
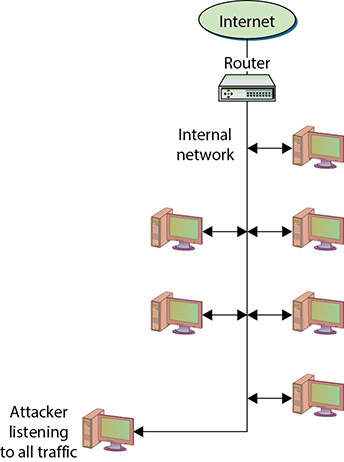
• Figure 15.4 Network sniffers listen to all network traffic.
![]()
A network interface card (NIC) that is listening to all network traffic and not just its own is said to be in “promiscuous mode.”
Network sniffers can also be used by attackers to gather information that can be used in penetration attempts. Information such as an authorized username and password can be viewed and recorded for later use. The contents of e-mail messages can also be viewed as the messages travel across the network. It should be obvious that administrators and security professionals will not want unauthorized network sniffers on their networks because of the security and privacy concerns they introduce. Fortunately, for network sniffers to be most effective, they need to be on the internal network, which generally means that the chances of outsiders using them against you are extremely limited. This is another reason that physical security is an important part of information security in today’s environment.

Cross Check
Physical Access and Security
One of the challenges in a modern network is getting a connection to a point in the network where your sniffing will result in the discovery of interesting information. Getting access to an open port, or to an equipment room where routers and switches are maintained, is a failure of physical security. Physical security is an important component of a comprehensive information security program. At this point ask yourself, Where can I connect into my company network? Can I get connections near high-value targets such as database servers? Details on physical security measures are covered in Chapter 8.
Spoofing
Spoofing is nothing more than making data look like it has come from a different source. This is possible in TCP/IP because of the friendly assumptions behind the protocols. When the protocols were developed, it was assumed that individuals who had access to the network layer would be privileged users who could be trusted.

Tech Tip
What Is Spoofing?
Spoofing is when you assemble packets with false header information to deceive the receiver as to the true address of the sender. This can be done to manipulate return packets in the case of ping sweeps, or to provide anonymity for e-mails.
When a packet is sent from one system to another, it includes not only the destination IP address and port but the source IP address as well. You are supposed to fill in the source with your own address, but nothing stops you from filling in another system’s address. This is one of the several forms of spoofing.
Spoofing E-mail
In e-mail spoofing, a message is sent with a From address that differs from that of the sending system. This can be easily accomplished in several different ways using several programs. To demonstrate how simple it is to spoof an e-mail address, you can telnet to port 25 (the port associated with e-mail) on a mail server. From there, you can fill in any address for the From and To sections of the message, whether or not the addresses are yours or even actually exist.
You can use several methods to determine whether an e-mail message was sent by the source it claims to have been sent from, but most users do not question their e-mail and will accept as authentic where it appears to have originated. A variation on e-mail spoofing, though not technically spoofing, is for the attacker to acquire a URL similar to the URL they want to spoof so that e-mail sent from their system appears to have come from the official site—until the recipient reads the address carefully. For example, if attackers want to spoof XYZ Corporation, which owns XYZ.com, the attackers might gain access to the URL XYZ.Corp.com. An individual receiving a message from the spoofed corporation site would not normally suspect it to be a spoof but would take it to be official. This same method can be, and has been, used to spoof websites. If, however, the attackers made their spoofed site appear similar to the official one, they could easily convince many potential viewers that they were at the official site. Today, many .com and other domains of common sites, as well as common typos of URLs, are purchased and directed to the legitimate site.
![]()
Cross Check
E-mail Spoofing
E-mail was created in an era with a different security environment—one where attribution was not even an afterthought. This has led to issues associated with trust regarding e-mails. Full details of securing e-mails are covered in Chapter 17.
IP Address Spoofing
IP is designed to work so that the originators of any IP packet include their own IP address in the From portion of the packet. Although this is the intent, nothing prevents a system from inserting a different address in the From portion of the packet. This is known as IP address spoofing. An IP address can be spoofed for several reasons. In a specific DoS attack known as a smurf attack, the attacker sends a spoofed packet to the broadcast address for a network, which distributes the packet to all systems on that network. In the smurf attack, the packet sent by the attacker to the broadcast address is an echo request with the From address forged so that it appears another system (the target system) has made the echo request. The normal response of a system to an echo request is an echo reply, and it is used in the ping utility to let a user know whether a remote system is reachable and is responding. In the smurf attack, the request is sent to all systems on the network, so all will respond with an echo reply to the target system, as shown in Figure 15.5. The attacker has sent one packet and has been able to generate as many as 254 responses aimed at the target. Should the attacker send several of these spoofed requests, or send them to several different networks, the target can quickly become overwhelmed with the volume of echo replies it receives.
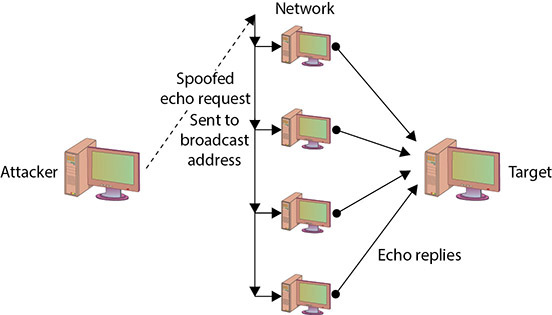
• Figure 15.5 Spoofing used in a smurf DOS attack
![]()
A smurf attack allows an attacker to use a network structure to send large volumes of packets to a victim. By sending ICMP requests to a broadcast IP address, with the victim as the source address, the multitudes of replies will flood the victim system.
Spoofing and Trusted Relationships
Spoofing can also take advantage of a trusted relationship between two systems. If two systems are configured to accept the authentication accomplished by each other, an individual logged on to one system might not be forced to go through an authentication process again to access the other system. An attacker can take advantage of this arrangement by sending a packet to one system that appears to have come from a trusted system. Because the trusted relationship is in place, the targeted system may perform the requested task without authentication.
Because a reply will often be sent once a packet is received, the system that is being impersonated could interfere with the attack, since it would receive an acknowledgment for a request it never made. The attacker will often initially launch a DoS attack (such as a SYN flooding attack) to temporarily take out the spoofed system for the period of time that the attacker is exploiting the trusted relationship. Once the attack is completed, the DoS attack on the spoofed system would be terminated, and the system administrators, apart from having a temporarily nonresponsive system, might never notice that the attack occurred. Figure 15.6 illustrates a spoofing attack that includes a SYN flooding attack.
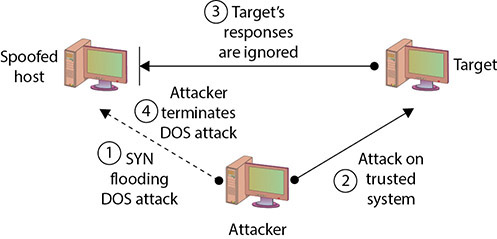
• Figure 15.6 Spoofing to take advantage of a trusted relationship
Because of this type of attack, administrators are encouraged to strictly limit any trusted relationships between hosts. Firewalls should also be configured to discard any packets from outside of the firewall that have From addresses indicating they originated from inside the network (a situation that should not occur normally and that indicates spoofing is being attempted).
Spoofing and Sequence Numbers
How complicated the spoofing is depends heavily on several factors, including whether the traffic is encrypted and where the attacker is located relative to the target. Spoofing attacks from inside a network, for example, are much easier to perform than attacks from outside of the network, because the inside attacker can observe the traffic to and from the target and can do a better job of formulating the necessary packets.
Formulating the packets is more complicated for external attackers because a sequence number is associated with TCP packets. A sequence number is a 32-bit number established by the host that is incremented for each packet sent. Packets are not guaranteed to be received in order, and the sequence number can be used to help reorder packets as they are received and to refer to packets that may have been lost in transmission.
In the TCP three-way handshake, two sets of sequence numbers are created, as shown in Figure 15.7. The first system chooses a sequence number to send with the original SYN packet. The system receiving this SYN packet acknowledges with a SYN/ACK. It sends an acknowledgment number back, which is based on the first sequence number plus one (that is, it increments the sequence number sent to it by one). It then also creates its own sequence number and sends that along with it. The original system receives the SYN/ACK with the new sequence number. It increments the sequence number by one and uses it as the acknowledgment number in the ACK packet with which it responds.
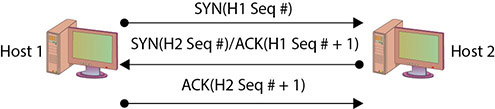
• Figure 15.7 Three-way handshake with sequence numbers
The difference in the difficulty of attempting a spoofing attack from inside a network and from outside involves determining the sequence number. If the attacker is inside of the network and can observe the traffic with which the target host responds, the attacker can easily see the sequence number the system creates and can respond with the correct sequence number. If the attacker is external to the network and the sequence number the target system generates is not observed, it is next to impossible for the attacker to provide the final ACK with the correct sequence number. Therefore, the attacker has to guess what the sequence number might be.
Sequence numbers are somewhat predictable, based on the operating systems in question. Sequence numbers for each session are not started from the same number, so different packets from different concurrent connections will not have the same sequence numbers. Instead, the sequence number for each new connection is incremented by some large number to keep the numbers from being the same. The sequence number may also be incremented by some large number every second (or some other time period). An external attacker has to determine what values are used for these increments. The attacker can do this by attempting connections at various time intervals to observe how the sequence numbers are incremented. Once the pattern is determined, the attacker can attempt a legitimate connection to determine the current value and then immediately attempt the spoofed connection. The spoofed connection sequence number should be the legitimate connection incremented by the determined value or values.
Sequence numbers are also important in session hijacking, which is discussed in an upcoming section. When an attacker spoofs addresses and imposes their packets in the middle of an existing connection, this is known as an on-path attack, although still often referred to as a man-in-the-middle attack.
MAC Spoofing
MAC spoofing is the act of changing a MAC address to bypass security checks based on the MAC address. This can work when the return packets are being routed by IP address and can be correctly linked to the correct MAC. Not all MAC spoofing is an attack; small firewall routers have commonly had a MAC clone function, by which the device can clone a MAC, making it seem transparent to other devices such as the cable modem connection.
TCP/IP Hijacking
TCP/IP hijacking and session hijacking are terms used to refer to the process of taking control of an already existing session between a client and a server. The advantage to an attacker of hijacking over attempting to penetrate a computer system or network is that the attacker doesn’t have to circumvent any authentication mechanisms, because the user has already authenticated and established the session. Once the user has completed the authentication sequence, the attacker can then usurp the session and carry on as if they, not the user, had authenticated with the system. To prevent the user from noticing anything unusual, the attacker can decide to attack the user’s system and perform a DoS attack on it, taking it down so that the user, and the system, will not notice the extra traffic that is taking place.
Hijack attacks generally are used against web and Telnet sessions. Sequence numbers as they apply to spoofing also apply to session hijacking, since the hijacker will need to provide the correct sequence number to continue the appropriated sessions.
Man-in-the-Middle Attacks
A man-in-the-middle attack, as the name implies, generally occurs when attackers are able to place themselves in the middle of two other hosts that are communicating. Ideally, this is done by ensuring that all communication going to or from the target host is routed through the attacker’s host (which can be accomplished if the attacker can compromise the router for the target host). The attacker can then observe all traffic before relaying it and can actually modify or block traffic. To the target host, it appears that communication is occurring normally, since all expected replies are received. Figure 15.8 illustrates this type of attack.
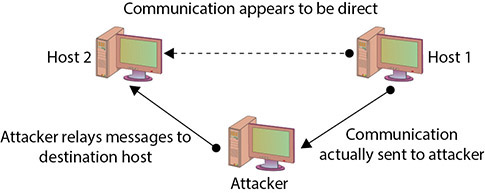
• Figure 15.8 A man-in-the-middle attack
![]()
CompTIA has chosen new names for several terms. Man-in-the-middle attacks has been renamed on-path attacks. For the purpose of the Security+ exam, be cognizant of these names. This book will reference both the historical and new names to assist in transitional learning of the new terms when examined against historical literature.
There are numerous methods of instantiating a man-in-the-middle attack; one of the common methods is via session hijacking. Session hijacking can occur when information such as a cookie is stolen, allowing the attacker to impersonate the legitimate session. This attack can be as a result of a cross-site scripting attack, which tricks a user into executing code resulting in cookie theft. The amount of information that can be obtained in a man-in-the-middle attack will obviously be limited if the communication is encrypted. Even in this case, however, sensitive information can still be obtained, since knowing what communication is being conducted, and between which individuals, may in fact provide information that is valuable in certain circumstances.
Man-in-the-Middle Attacks on Encrypted Traffic
The term man-in-the-middle attack is sometimes used to refer to a more specific type of attack—one in which the encrypted traffic issue is addressed. If you wanted to communicate securely with your friend Bob, you might ask him for his public key so you could encrypt your messages to him. You, in turn, would supply Bob with your public key. An attacker can conduct a man-in-the-middle attack by intercepting your request for Bob’s public key and the sending of your public key to him. The attacker would replace your public key with their public key, and they would send this on to Bob. The attacker’s public key would also be sent to you (by the attacker) instead of Bob’s public key. Now when either you or Bob encrypts a message, it will be encrypted using the attacker’s public key, enabling the attacker to intercept it, decrypt it, and then send it on by re-encrypting it with the appropriate key for either you or Bob. Each of you thinks you are transmitting messages securely, but in reality your communication has been compromised. Well-designed cryptographic products use techniques such as mutual authentication to avoid this problem.
![]()
Cross Check
Encryption
Cryptography and encryption are tools that can solve many of our secrecy problems. The challenges solved through encryption and the new problems associated with the use of encryption require an understanding of the technical details. Public key encryption, discussed in detail in Chapters 5 and 6, uses two keys: a public key, which anybody can use to encrypt or “lock” your message, and a private key, which only you know and which is used to “unlock” or decrypt a message locked with your public key. One of the key challenges associated with the use of public keys and corresponding private keys is determining who has what key values. Do you have your own key pair? If so, do you know the public key value you need to share with others?
Man-in-the-Browser
The man-in-the-browser (MITB) attack is a variant of a man-in-the-middle attack. In an MITB attack, the first element is a malware attack that places a trojan element that can act as a proxy on the target machine. This malware changes browser behavior through browser helper objects or extensions. When a user connects to their bank, the malware recognizes the target (a financial transaction) and injects itself in the stream of the conversation. When the user approves a transfer of $150 to pay a utility bill, the malware intercepts the user’s keystrokes and modifies them to perform a different transaction. A famous example of an MITB attack is the financial malware Zeus, which targeted financial transactions on users’ machines, manipulating and changing them after the user had entered password credentials.
Replay Attacks
A replay attack occurs when the attacker captures a portion of a communication between two parties and retransmits it at a later time. For example, an attacker might replay a series of commands and codes used in a financial transaction to cause the transaction to be conducted multiple times. Generally, replay attacks are associated with attempts to circumvent authentication mechanisms, such as the capturing and reuse of a certificate or ticket.
![]()
The best method for defending against replay attacks is through the use of encryption and short time frames for legal transactions. Encryption can protect the contents from being understood, and a short time frame for a transaction prevents subsequent use.
The best way to prevent replay attacks is with encryption, cryptographic authentication, and timestamps. If a portion of the certificate or ticket includes a date/timestamp or an expiration date/time, and this portion is also encrypted as part of the ticket or certificate, then replaying it at a later time will prove useless because it will be rejected as having expired.
Transitive Access
Transitive access is a means of attacking a system by violating the trust relationship between machines. A simple example is when servers are well protected and clients are not, and the servers trust the clients. In this case, attacking a client can provide transitive access to the servers.
![]()
Trust is an essential part of security. If B trusts A, and C trusts B, then C trusts A. A transitive attack takes advantage of this trust chain by obtaining trust from one element in the chain (for example, through spoofing) and then using that to gain transitive access to another trusted system via the chain of trust.
Scanning Attacks
Scanners can be used to send specifically crafted packets in an attempt to determine TCP/UDP port status. An XMAS scan, named because the alternating bits in the TCP header look like Christmas lights, uses the URG, PSH, and FIN flags to determine TCP port availability. If the port is closed, an RST is returned. If the port is open, there is typically no return. An XMAS scan can help determine OS type and version, based on TCP/IP stack responses, and can also help determine firewall rules. These attacks can also be used to consume system resources, resulting in DoS.

Tech Tip
XMAS Attack
The XMAS attack, or Christmas attack, comes from a specific set of protocol options. A Christmas tree packet is a packet that has many of its options turned on. The name comes from the observation that these packets are lit up like a Christmas tree. When sent as a scan, a Christmas tree packet has the FIN, URG, and PSH options set. Many OSs implement their compliance with RFC 791, the RFC governing IP packets, in slightly different ways. Their response to the packet can tell the scanner what type of OS is present. Another option is in the case of a DoS attack, where Christmas tree packets can take up significantly greater processing on a router, thus consuming resources.
Simple stateless firewalls check for the SYN flag set to prevent SYN floods, and Christmas tree packets are designed not to have SYN set, so they pass right by these devices. Newer security devices such as advanced firewalls can detect these packets, alerting people to the scanning activities.
Attacks on Encryption
Encryption is the process of transforming plaintext into an unreadable format known as ciphertext using a specific technique or algorithm. Most encryption techniques use some form of key in the encryption process. The key is used in a mathematical process to scramble the original message to arrive at the unreadable ciphertext. Another key (sometimes the same one and sometimes a different one) is used to decrypt or unscramble the ciphertext to re-create the original plaintext. The length of the key often directly relates to the strength of the encryption.
Cryptanalysis is the process of attempting to break a cryptographic system—it is an attack on the specific method used to encrypt the plaintext. Cryptographic systems can be compromised in various ways.
Weak Keys
Certain encryption algorithms may have specific keys that yield poor, or easily decrypted, ciphertext. Imagine an encryption algorithm that consists solely of a single XOR function (an exclusive OR function where two bits are compared and a 1 is returned if either of the original bits, but not both, is a 1), where the key is repeatedly used to XOR with the plaintext. A key where all bits are 0’s, for example, would result in ciphertext that is the same as the original plaintext. This would obviously be a weak key for this encryption algorithm. In fact, any key with long strings of 0’s would yield portions of the ciphertext that were the same as the plaintext. In this simple example, many keys could be considered weak.
Encryption algorithms used in computer systems and networks are much more complicated than a simple, single XOR function, but some algorithms have still been found to have weak keys that make cryptanalysis easier.
Exhaustive Search of Key Space
Even if the specific algorithm used to encrypt a message is complicated and has not been shown to have weak keys, the key length will still play a significant role in how easy it is to attack the method of encryption. Generally speaking, the longer a key, the harder it will be to attack. Thus, a 40-bit encryption scheme will be easier to attack using a brute force technique (which tests all possible keys, one by one) than a 256-bit based scheme. This is easily demonstrated by imagining a scheme that employs a 2-bit key. Even if the resulting ciphertext were completely unreadable, performing a brute force attack until one key is found that can decrypt the ciphertext would not take long, since only four keys are possible. Every bit that is added to the length of a key doubles the number of keys that have to be tested in a brute force attack on the encryption. It is easy to understand why a scheme utilizing a 40-bit key would be much easier to attack than a scheme that utilizes a 256-bit key.
The bottom line is simple: an exhaustive search of the keyspace will decrypt the message. The strength of the encryption method is related to the sheer size of the keyspace, which with modern algorithms is large enough to provide significant time constraints when using this method to break an encrypted message. Algorithmic complexity is also an issue with respect to brute forcing, and you cannot immediately compare different key lengths from different algorithms and assume relative strength.
Indirect Attacks
One of the most common ways of attacking an encryption system is to find weaknesses in mechanisms surrounding the cryptography. Examples include poor random-number generators, unprotected key exchanges, keys stored on hard drives without sufficient protection, and other general programmatic errors, such as buffer overflows. In attacks that target these types of weaknesses, it is not the cryptographic algorithm itself that is being attacked but rather the implementation of that algorithm in the real world.
Address System Attacks
Many aspects of a computer system are controlled by the use of addresses. IP addresses can be manipulated, as shown earlier, and the other address schemes can be manipulated as well. In the summer of 2008, much was made of a serious Domain Name System (DNS) vulnerability that required the simultaneous patching of systems by over 80 vendors. This coordinated effort was to close a technical loophole in the domain name resolution infrastructure that would allow the hijacking and man-in-the-middle attack on the DNS system worldwide.
![]()
The process of using a new domain name for the five-day “test” period and then relinquishing the name, only to repeat the process again—in essence, obtaining a domain name for free—is called DNS kiting..
The DNS system has been the target of other attacks. One attack, DNS kiting, is an economic attack against the terms of using a new DNS entry. New DNS purchases are allowed a five-day “test period” during which the name can be relinquished for no fee. Creative users learned to register a name, use it for less than five days, relinquish the name, and then get the name again and begin all over, repeating this cycle many times to use a name without paying for it. Typical registration versus permanent entry ratios of 15:1 occur, and in February of 2007 GoDaddy reported that out of 55.1 million requests only 3.6 million were not canceled.
Another twist on this scheme is the concept of domain name front running, where a registrar places a name on a five-day hold after someone searches for it, and then offers it for sale at a higher price. In January of 2008, Network Solutions was accused of violating the trust as a registrar by forcing people to purchase names from them after they engaged in domain name testing.
Cache Poisoning
Many network activities rely on various addressing schemes to function properly. When you point your web browser at your bank, by typing the bank’s URL, your browser consults the system’s Domain Name System to turn the words into a numerical address. When a packet is being switched to your machine by the network, a series of address caches is involved. Whether the cache is for the DNS system or the ARP system, it exists for the same reason: efficiency. These caches prevent repeated redundant lookups, saving time for the system. However, they can also be poisoned, sending incorrect information to the end user’s application, redirecting traffic, and changing system behaviors.
DNS Poisoning
The DNS system is used to convert a name into an IP address. There is no single DNS system, but rather a hierarchy of DNS servers, from root servers on the backbone of the Internet, to copies at your ISP, your home router, and your local machine, each in the form of a DNS cache. To examine a DNS query for a specific address, you can use the nslookup command. Figure 15.9 shows a series of DNS queries executed on a Windows machine. In the first request, the DNS server was with an ISP, whereas on the second request, the DNS server was from a VPN connection. Between the two requests, the network connections were changed, resulting in different DNS lookups. This is a form of DNS poisoning attack.
• Figure 15.9 An nslookup of a DNS query
At times, nslookup will return a nonauthoritative answer, as shown in Figure 15.10. This typically means the result is from a cache as opposed to a server that has an authoritative answer (that is, one known to be current).
• Figure 15.10 Cache response to a DNS query
• Figure 15.11 Cache response to a DNS table query
You can use other commands to examine and manipulate the DNS cache on a system. In Windows, the ipconfig/displaydns command will show the current DNS cache on a machine. Figure 15.11 shows a small DNS cache. This cache was recently emptied using the ipconfig /flushdns command to make it fit on the screen.
Looking at DNS as a complete system shows that there are hierarchical levels from the top (root server) down to the cache in an individual machine. DNS poisoning can occur at any of these levels, with the effect of the poisoning growing wider the higher up it occurs. In 2010, a DNS poisoning event resulted in the “Great Firewall of China” censoring inbound Internet traffic into China from the United States until caches were resolved. Today, after further examination, the attack was shown to be much more complex. The efforts of the Chinese government actively seek to strictly control all aspects of Internet traffic in China.
DNS poisoning is a variant of a larger attack class referred to as DNS spoofing, in which an attacker changes a DNS record through any of a multitude of means. There are many ways to perform DNS spoofing, a few of which include compromising a DNS server, the use of the Kaminsky attack, and the use of a false network node advertising a false DNS address. An attacker can even use DNS cache poisoning to result in DNS spoofing. When an upstream DNS cache is poisoned, all of the downstream users will get spoofed DNS records.
Because of the importance of integrity on DNS requests and responses, a project has begun to secure the DNS infrastructure using digital signing of DNS records. This project, initiated by the U.S. government and called Domain Name System Security Extensions (DNSSEC), works by digitally signing records. This is done by adding records to the DNS system, a key, and a signature attesting to the validity of the key. With this information, requestors can be assured that the information they receive is correct. It will take a substantial amount of time (years) for this new system to propagate throughout the entire DNS infrastructure, but in the end, the system will have much greater assurance.
ARP Poisoning
In moving packets between machines, a device sometimes needs to know where to send a packet using the MAC or Layer 2 address. Address Resolution Protocol (ARP) handles this problem through four basic message types:
![]() ARP request “Who has this IP address?”
ARP request “Who has this IP address?”
![]() ARP reply “I have that IP address; my MAC address is…”
ARP reply “I have that IP address; my MAC address is…”
![]() Reverse ARP request (RARP) “Who has this MAC address?”
Reverse ARP request (RARP) “Who has this MAC address?”
![]() RARP reply “I have that MAC address; my IP address is…”
RARP reply “I have that MAC address; my IP address is…”
These messages are used in conjunction with a device’s ARP table, where a form of short-term memory associated with these data elements resides. The commands are used as a simple form of lookup. When a machine sends an ARP request to the network, the reply is received and entered into all devices that hear the reply. This facilitates efficient address lookups, but also makes the system subject to attack.
When the ARP table gets a reply, it automatically trusts the reply and updates the table. Some operating systems will even accept ARP reply data if they never heard the original request. The ARP message received in this case is called a gratuitous ARP. There is no mechanism to verify the veracity of the data received. An attacker can send messages, corrupt the ARP table, and cause packets to be misrouted. This form of attack is called ARP poisoning and results in malicious address redirection. This can allow a mechanism whereby an attacker can inject themselves into the middle of a conversation between two machines, known as a man-in-the-middle attack.

ARP poisoning involves the altering of the ARP cache on the local system. Using the Windows command prompt (as an administrator), examine the ARP table with the arp -1 command. The results will be a table showing the IP addresses in the left column and the MAC addresses in the middle. If the table contains two different IP addresses that share the same MAC address, you are probably undergoing an ARP poisoning attack.
Local MAC addresses can also be poisoned in the same manner, although it is called ARP poisoning. This can cause miscommunications locally. Poisoning attacks can be used to steal information, establish man-in-the-middle attacks, and even create DoS opportunities.
Amplification
Certain types of attacks could be considered dependent upon volume, such as denial of service and distributed denial of service. For these attacks to generate a sufficient volume of packets to overwhelm a host, typically a large server, more than a single home PC is required. Amplification is a trick whereby the attacker uses a specific protocol aspect to achieve what a single machine cannot by itself. As an example, let’s look at the ICMP command ping. When you issue an ICMP ping command, the machine receiving it provides a ping reply packet. What if you send the ICMP request to a network address, in essence to all active hosts within that network? They would all reply with a packet. Now, you could forge the requesting packet so that the reply address is a specific machine. The net effect is that all those machines will reply to the forged address—one machine—with an amplified response.
Domain Hijacking
Domain hijacking is the act of changing the registration of a domain name without the permission of its original registrant. Technically a crime, this act can have devastating consequences because the DNS system will automatically spread the false domain location far and wide. The original owner can request it to be corrected, but that takes time.
Pass-the-Hash Attacks
Pass the hash is a hacking technique where the attacker captures the hash used to authenticate a process. They can then use this hash by injecting it into a process in place of the password. This is a highly technical attack, targeting the Windows authentication process, injecting a copy of the password hash directly into the system. The attacker does not need to know the password but instead can use a captured hash and inject it directly, which will verify correctly, thus granting access. Because this is a very technically specific hack, tools have been developed to facilitate its operation.

Tech Tip
Mimikatz
Mimikatz is a toolset that can provide insight and exploration into Windows security elements, including obtaining Kerberos credentials and creating a “golden ticket,” a universal Kerberos ticket. Mimikatz has been included in Metasploit, making it an awesome post-exploitation tool that can enable tremendous attacker functionality on a Windows machine.
Software Exploitation
An attack that takes advantage of bugs or weaknesses in software is referred to as software exploitation. These bugs and weaknesses can be the result of poor design, poor testing, or poor coding practices. Software exploitation is covered in Chapter 19.
Client-Side Attacks
The web browser has become the major application for users to engage resources across the Web. The popularity and the utility of this interface has made it a prime target for attackers to gain access and control over a system. A wide variety of attacks can occur via a browser, typically resulting from a failure to validate input properly before use. Unvalidated input can result in a series of injection attacks, header manipulation, and other forms of attack.
Tech Tip
All Input Is Evil
You can never trust input from a client machine. A client can manipulate the input, the data can be changed in transit, and simple transmission errors can occur. The net result is that inputs can be manipulated, spoofed, or otherwise changed. The bottom line is to never trust input—always verify it before use.
Header Manipulations
When Hypertext Transfer Protocol (HTTP) elements are being dynamically generated through the use of user inputs, unvalidated inputs can give attackers an opportunity to change these HTTP elements. When user-supplied information is used in a header, it is possible to deploy a variety of attacks, including cache poisoning, cross-site scripting, cross-user defacement, page hijacking, cookie manipulation, and open redirect.
Typo Squatting/URL Hijacking
Typo squatting is a form of attack that involves capitalizing on common typographical errors. If a user mistypes a URL, then the result should be a 404 error, or “resource not found.” However, if an attacker has registered the mistyped URL, the user would land on the attacker’s page. This attack pattern is also referred to as either URL hijacking, fake URL, or brandjacking (if the objective is to deceive based on branding).
URL hijacking is a generic name for a wide range of attacks that target the URL. The URL is the primary means by which a user receives web content. If the correct URL is used, you get the desired content. If the URL is tampered with or altered, you can get different content. There is a wide range of URL-based attacks, from malware manipulations, to typo squatting, to ad-based attacks that make the user think they are clicking the correct link. The net result is the same: the user thinks they are asking for content A, but they get content B instead.
There are several reasons why an attacker might pursue this avenue of attack. The most obvious one is to conduct a phishing attack. The fake site collects credentials, passing them on to the real site, and then steps out of the conversation to avoid detection once the credentials are obtained. It can also be used to plant drive-by malware on the victim machine. In addition, it can move the packets through an affiliate network, thus earning click-through revenue based on the typos. There are numerous other forms of attacks that can be perpetrated using a fake URL as a starting point.

Drive-by downloads can occur via a couple different mechanisms. It is possible for an ad that is rotated into content on a reputable site to contain a drive-by download. Users don’t have control over what ads are presented. A second, more common method is a website that the user gets to either by mistyping a URL or by following a search link without vetting where they are clicking first. Just like cities can have bad neighborhoods, so too does the Internet, and surfing in a bad neighborhood can result in bad outcomes.
Drive-by Download Attack
Browsers are used to navigate the Internet, using HTTP and other protocols to bring files to users’ computers. Some of these files are images, some are scripts, and some are text based. Together they form the web pages we see. Users don’t ask for each component—it is the job of the browser to identify the needed files and fetch them. A new type of attack takes advantage of this mechanism by initiating a download of malware, regardless of whether a user clicks it. This automated download of materials is referred to as a drive-by download attack.
Watering Hole Attack
The most commonly recognized attack vectors are those that are direct to a target. Because of their incoming and direct nature, defenses are crafted to detect and defend against them. But what if the user “asked” for the attack by visiting a website? Just as a hunter waits near a watering hole for animals to come drink, attackers can plant malware at sites where users are likely to frequent. First identified by RSA, watering hole attacks involve the infecting of a target website with malware. In some of the cases detected, the infection was constrained to a specific geographical area. These are not simple attacks, yet they can be very effective at delivering malware to specific groups of end users. Watering hole attacks are complex to achieve and appear to be backed by nation-states and other high-resource attackers. In light of the stakes, the typical attack vector will be a zero-day attack to further avoid detection.
![]()
A zero-day attack or threat is a computer threat that tries to exploit computer application vulnerabilities that are unknown to others or possibly even the software developer.

Tech Tip
Watering Hole Attacks
Watering hole attacks can occur from even innocent websites. Brian Krebs gives a strong analysis of watering hole attacks on his blog, Krebs on Security, at https://krebsonsecurity.com/2012/09/espionage-hackers-target-watering-hole-sites.
Clickjacking
Clickjacking is an attack against the design element of a user interface. Clickjacking tricks a web browser user into clicking on something different from what the user perceives, by means of malicious code in the web page. This malicious code can be an overlay, and other means, but the net result is the user thinks they clicked No, but in reality they clicked Yes, and the browser executes the corresponding code. If the attacker modifies a page so that a transparent overlay with invisible clickable elements aligns with the actual elements, then the code that runs when a click occurs can be the attacker’s code.
Driver Manipulation
Drivers are pieces of software that sit between the operating system and a peripheral device. In one respect, drivers are a part of the OS; they’re an extension. In another respect, drivers are code that is not part of the OS and is developed by firms other than the OS developer.
Shimming
Shimming is the process of putting a layer of code between the driver and the OS. Shimming allows for flexibility and portability because it enables changes between different versions of an OS without modifying the original driver code. Shimming also represents a means by which malicious code can change a driver’s behavior without changing the driver itself.
Refactoring
Refactoring is the process of restructuring existing computer code without changing its external behavior. Refactoring is done to improve nonfunctional attributes of the software, such as improving code readability and/or reducing complexity. Refactoring can uncover design flaws that lead to exploitable vulnerabilities, allowing these to be closed without changing the external behavior of the code.
 Advanced Persistent Threat
Advanced Persistent Threat
The advanced persistent threat (APT) is a method of attack that primarily focuses on stealth and continuous presence on a system. APT is a very advanced method, requiring a team to maintain access, and typically involves high-value targets. APT typically uses specially crafted attack vectors, coupled with phishing or spear phishing for the initial entry. Then techniques are employed to develop backdoors and multiple account access routes. The skill level of the attackers is typically exceedingly high, and their aim is to completely own a system without being detected.

Cross Check
APT Groups
Information on different nation-state groups performing APT attacks is covered in detail in Chapter 1.
Once the attackers have completely penetrated a system and gain the ability to read e-mails to watch for reports of detection, they can accomplish their goal of stealing materials. Their long-term objectives are to remain hidden and undetected, while harvesting information over months and years. APT is the attack method of choice for nation-states and industrial espionage.

Tech Tip
Signs of an APT Attack
The following are indications of an APT attack:
![]() Off-hours activity If logs demonstrate “normal” activity at times when your workers are at home, this is a sign of compromised accounts. Look for large numbers of occurrences, as APT attackers tend to use multiple accounts.
Off-hours activity If logs demonstrate “normal” activity at times when your workers are at home, this is a sign of compromised accounts. Look for large numbers of occurrences, as APT attackers tend to use multiple accounts.
![]() Finding multiple backdoor trojans or remote-access trojans When security scans begin to find a lot of malware, this can be a sign of an APT.
Finding multiple backdoor trojans or remote-access trojans When security scans begin to find a lot of malware, this can be a sign of an APT.
![]() Finding unknown files APTs tend to bundle exfiltration data and keep it in encrypted form before slowly siphoning it out. Large files of unknown origin can be these bundles.
Finding unknown files APTs tend to bundle exfiltration data and keep it in encrypted form before slowly siphoning it out. Large files of unknown origin can be these bundles.
![]() Finding spear phishing e-mails and pass-the-hash tools These advanced attack methods are indications of an advanced adversary.
Finding spear phishing e-mails and pass-the-hash tools These advanced attack methods are indications of an advanced adversary.
![]() Strange data flows This is the most telltale sign. Finding unusual data flows—movement of data outside the normal course of business—indicates leakage.
Strange data flows This is the most telltale sign. Finding unusual data flows—movement of data outside the normal course of business—indicates leakage.
 Password Attacks
Password Attacks
The most common form of authentication is the user ID and password combination. While it is not inherently a poor mechanism for authentication, the combination can be attacked in several ways. All too often, these attacks yield favorable results for the attacker, not as a result of a weakness in the scheme, but usually due to the user not following good password procedures.
Password Guessing
Passwords are secrets that are supposed to be known by only the authorized user. However, people tend to pick things easy to remember and also reuse these secrets. This makes the password guessing attack possible. If a site has a leak of password data and users have reused a password, attackers can start with disclosed passwords associated with data breaches and many times can guess a password. This is why the addition of a single number that you change doesn’t provide security because attackers will try other numbers.
Poor Password Choices
The least technical of the various password-attack techniques consists of the attacker simply attempting to guess the password of an authorized user of the system or network. It is surprising how often this simple method works, and the reason it does is because people are notorious for picking poor passwords. Users need to select a password that they can remember, so they create simple passwords, such as their birthday, their mother’s maiden name, the name of their spouse or one of their children, or even simply their user ID itself. All it takes is for the attacker to obtain a valid user ID (often a simple matter, because organizations tend to use an individual’s names in some combination—first letter of their first name combined with their last name, for example) and a little bit of information about the user before guessing can begin.

One of the realities of modern data breaches is that your e-mail and password may be lost. Technically, if companies handled passwords correctly, a salted hash of your password would be exposed, but that is for another chapter. If your e-mail and password end up exposed, then what other accounts do you use the same password on? With so many accounts and our limited ability to manage passwords, it is a given that many times passwords are repeated. When a repeated password is exposed, it is up to the user to change the password on other systems. This is a good reason why you shouldn’t repeat passwords on sites with direct financial implications.
Spraying
Password spraying is an attack that uses a limited number of commonly used passwords and applies them to a large number of accounts. Traditional brute force attacks attempt to gain unauthorized access to a single account by guessing the password. Spraying is the reverse of this, using a limited number of passwords and trying them against all the accounts. This is a useful attack when you don’t care which account you get and is fairly successful when given a large set of accounts. Defending against this is important in organizations, because if one account is breached, it is the foothold needed to gain entry.
Dictionary Attack
Another method of determining passwords is to use a password-cracking program that uses a list of dictionary words to try to guess the password, hence the name dictionary attack. The words can be used by themselves, or two or more smaller words can be combined to form a single possible password. A number of commercial and public-domain password-cracking programs employ a variety of methods to crack passwords, including using variations on the user ID.
These programs often permit the attacker to create various rules that tell the program how to combine words to form new possible passwords. Users commonly substitute certain numbers for specific letters. If the user wants to use the word secret for a password, for example, the letter e could be replaced with the number 3, yielding s3cr3t. This password will not be found in the dictionary, so a pure dictionary attack would not crack it, but the password is still easy for the user to remember. If a rule were created that tried all words in the dictionary and then tried the same words substituting the number 3 for the letter e, however, the password would be cracked.
Rules can also be defined so that the password-cracking program will substitute special characters for other characters or combine words. The ability of the attacker to crack passwords is directly related to the method the user employs to create the password in the first place, as well as the dictionary and rules used.
A dictionary attack involves the use of a lookup table to try and find an answer. With that in mind, repeated use of passwords, coupled with data breaches, provides a set of passwords to try. This is why unique passwords for security-sensitive sites are so important, because a data breach at one firm could cost you all of your accounts, because the attacker’s job becomes as simple as looking them up.
Brute Force Attack
If the user has selected a password that is not found in a dictionary, even if simply by substituting various numbers or special characters for letters, then the only way the password can be cracked is for an attacker to attempt a brute force attack, in which the password-cracking program attempts all possible character combinations.

Tech Tip
Password Cracking with GPUs
The following data comes from a 2017 PC running multiple GPUs (8 GeForce GTX 1080 Ti, using hashcat v3.40) dedicated to cracking passwords. Note the differences in speeds based on hashing method. (This is why simple hashes don’t provide the protection that newer, stronger methods do.)
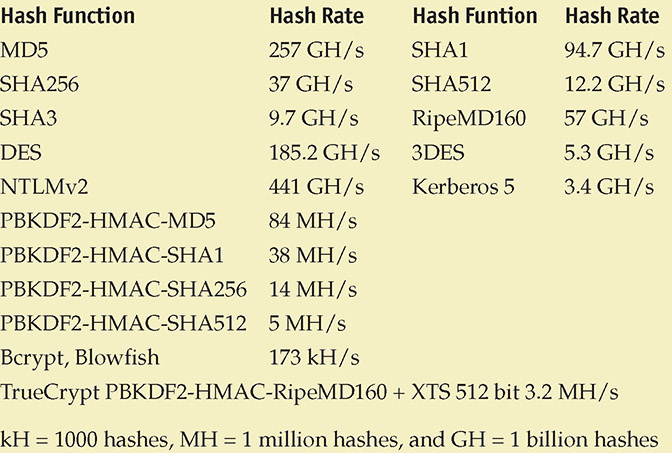
This shows the speed penalties against brute forcing that PBKDF2 and Bcrypt offer. More details on these can be found in Chapter 6. Although newer machines are faster, the relative differences will still hold true.
The length of the password and the size of the set of possible characters in the password will greatly affect the time a brute force attack will take. A few years ago, this method of attack was very time consuming, because it took considerable time to generate all possible combinations. With the increase in computer speed, however, generating password combinations is much faster, making it more feasible to launch brute force attacks against certain computer systems and networks.

Modern multicore GPUs and large on-chip cache memories have significantly improved the speed of password-cracking programs, making brute force methods practical in many cases. Today, all 10-character passwords can be cracked in less than a month. This is why salting passwords is essential to increase the effective length.
A brute force attack on a password can take place at two levels: the attacker can use a password-cracking program to attempt to guess the password directly at a login prompt, or the attacker can first steal a password file, use a password-cracking program to compile a list of possible passwords based on the list of password hashes contained in the password file (offline), and then use that narrower list to attempt to guess the password at the login prompt. The first attack can be made more difficult if the account locks after a few failed login attempts. The second attack can be thwarted if the password file is securely maintained so that others cannot obtain a copy of it.

Tech Tip
Offline Password Attacks
Because an attacker who obtains a password file has unlimited time offline to prepare for the online attack, and can prepare without tipping off the target, all passwords should be considered to be vulnerable over extended periods of time. For this reason, even batch passwords (used for system-run batch jobs) should be changed periodically to prevent offline attacks.
Offline
Offline brute force attacks can be employed to perform hash comparisons against a stolen password file. This has the challenge of stealing the password file, but if accomplished, it is possible to use high-performance GPU-based parallel machines to try passwords at very high rates and against multiple accounts at the same time.
Online
When the brute force attack occurs in real time against a system, it is frequently being done to attack a single account with multiple examples of passwords. Success or failure is determined by the system under attack, and the attacker either gets in or doesn’t. Online brute force attacks tend to be very noisy and easy to see by network security monitoring, and they are also limited by system response time and bandwidth.
Hybrid Attack
A hybrid password attack is an attack that combines the preceding dictionary and brute force methods. Most cracking tools have this option built in, first attempting a dictionary attack, and then moving on to brute force methods.
The programs often permit the attacker to create various rules that tell the program how to combine words to form new possible passwords. Users commonly substitute certain numbers for specific letters. If the user wanted to use the word secret as a base for a password, for example, they could replace the letter e with the number 3, yielding s3cr3t. This password will not be found in the dictionary, so a pure dictionary attack would not crack it, but the password is still easy for the user to remember. If the attacker created a rule that instructed the program to try all words in the dictionary and then try the same words substituting the number 3 for the letter e, however, the password would be cracked.
Birthday Attack
The birthday attack is a special type of brute force attack that gets its name from something known as the birthday paradox, which states that in a group of at least 23 people, the chance that two individuals will have the same birthday is greater than 50 percent. Mathematically, the equation is 1.25×k1/2, where k equals the size of the set of possible values, which in the birthday paradox is 365 (the number of possible birthdays). This same phenomenon applies to passwords, with k (number of passwords) being quite a bit larger.
Rainbow Tables
Rainbow tables are precomputed tables or hash values associated with passwords. Using rainbow tables can change the search for a password from a computational problem to a lookup problem. This can tremendously reduce the level of work needed to crack a given password. The best defense against rainbow tables is salted hashes, as the addition of a salt value increases the complexity of the problem by making the precomputing process not replicable between systems. A salt is merely a random set of characters designed to increase the length of the item being hashed, effectively making rainbow tables too big to compute.
![]()
A salt is a random set of characters designed to increase the length of the item being hashed. It is an effective defense against rainbow table attacks.
Plaintext/Unencrypted
Passwords that are stored are subject to retrieval. Any time a system can send you a copy of your password, there is a security issue. Plaintext password attacks are those taken against these specific issues. Lest anyone think that this is only a problem from rogue systems or programs, even mainstream systems can fall prey to this trap. Microsoft allows administrators to push out passwords for local accounts via group policy preferences. To protect the passwords, they are encrypted using Advanced Encryption Standard (AES). For reasons of compatibility with other systems, Microsoft published the AES key. See the problem?
In Microsoft Windows systems, Mimikatz is a security tool that can extract Kerberos tickets from memory, and it also possesses the ability to extract plaintext passwords from process dumps of the LSASS process. This means that by using the security tools ProcDump and Mimikatz, one can harvest plaintext passwords from a system.
Chapter 15 Review
 Chapter Summary
Chapter Summary
After reading this chapter and completing the exercises, you should understand the following aspects of attacks and malware.
Identify the different types of malicious software that exist, including viruses, worms, trojan horses, logic bombs, time bombs, and rootkits
![]() Malware is the common name for a wide range of code used to attack systems.
Malware is the common name for a wide range of code used to attack systems.
![]() Viruses are pieces of malware that require a file to infect a system.
Viruses are pieces of malware that require a file to infect a system.
![]() Worms are pieces of malware that can exist without infecting a file.
Worms are pieces of malware that can exist without infecting a file.
![]() Trojan horses are pieces of malware disguised as something else, something the user wants or finds useful.
Trojan horses are pieces of malware disguised as something else, something the user wants or finds useful.
![]() Logic bombs trigger when specific events occur in code, allowing an attack to be timed against an event.
Logic bombs trigger when specific events occur in code, allowing an attack to be timed against an event.
![]() Time bombs are delayed malware designed to occur after a set period of time or on a specific date.
Time bombs are delayed malware designed to occur after a set period of time or on a specific date.
![]() Rootkits are pieces of malware designed to alter the lower-level functions of a system in a manner to escape detection.
Rootkits are pieces of malware designed to alter the lower-level functions of a system in a manner to escape detection.
![]() Keyloggers capture user entries such as passwords.
Keyloggers capture user entries such as passwords.
![]() Remote-access trojans provide attackers significant capabilities.
Remote-access trojans provide attackers significant capabilities.
Describe the various types of computer and network attacks, including denial of service, spoofing, hijacking, and password guessing
![]() Understand how denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are performed and the defenses against them.
Understand how denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks are performed and the defenses against them.
![]() Both packet headers and e-mail headers can be spoofed to take advantage of the trust users place in these data elements, even when they are not protected from change.
Both packet headers and e-mail headers can be spoofed to take advantage of the trust users place in these data elements, even when they are not protected from change.
![]() Understand how session hijacking and on-path (formerly man-in-the-middle) attacks are performed and what the defenses are against these attacks.
Understand how session hijacking and on-path (formerly man-in-the-middle) attacks are performed and what the defenses are against these attacks.
![]() Password systems can have numerous vulnerabilities—some based on the system and some on the choice of password itself.
Password systems can have numerous vulnerabilities—some based on the system and some on the choice of password itself.
Recognize the different types of password attacks
![]() Password guessing is a real thing and takes advantage of predictable patterns.
Password guessing is a real thing and takes advantage of predictable patterns.
![]() Poor password choices can lead to account compromise.
Poor password choices can lead to account compromise.
![]() Common attacks include spraying, dictionary attacks, brute force, and rainbow tables.
Common attacks include spraying, dictionary attacks, brute force, and rainbow tables.
 Key Terms
Key Terms
adware (583)
ARP poisoning (602)
backdoor (585)
birthday attack (608)
botnet (582)
buffer overflow (586)
clickjacking (604)
crypto-malware (577)
denial-of-service (DoS) attack (587)
distributed denial-of-service (DDoS) attack (588)
DNS kiting (599)
domain hijacking (602)
drive-by download attack (604)
fileless malware (580)
keylogger (583)
logic bomb (582)
MAC spoofing (595)
malware (576)
man in the browser (MITB) (596)
on-path/man-in-the-middle attack (595)
pass the hash (602)
phishing (603)
polymorphic malware (581)
potentially unwanted program (PUP) (581)
rainbow tables (609)
ransomware (577)
remote-access trojan (RAT) (584)
replay attack (597)
rootkit (584)
sequence number (594)
smurf attack (589)
sniffing (591)
spear phishing (605)
spoofing (592)
spyware (583)
SYN flood (587)
TCP/IP hijacking (595)
transitive access (597)
trojan (577)
typo squatting (603)
URL hijacking (603)
virus (578)
war-dialing (590)
war-driving (590)
watering hole attacks (604)
worm (578)
zero-day attack (604)
zombie (582)
 Key Terms Quiz
Key Terms Quiz
Use terms from the Key Terms list to complete the sentences that follow. Don’t use the same term more than once. Not all terms will be used.
1. Changing a source IP address for malicious purpose is an example of _______________.
2. A(n) _______________ is a way back into a machine via an unauthorized channel of access.
3. A malicious proxy could create a(n) _______________ attack.
4. Abusing the TCP handshake in an effort to overuse server resources can be done using a(n) _______________.
5. The main TCP/IP defense against an on-path/man-in-the-middle attack is the use of a(n) _______________.
6. Holding a DNS name without paying is called _______________.
7. When a keylogger is installed as malware, it is referred to as _______________.
8. Rendering a resource useless is called a(n) _______________.
9. An attack designed to match any user’s password as opposed to a specific user’s password is an example of a(n) _______________.
10. A NIC can be set to promiscuous mode to enable _______________.
 Multiple-Choice Quiz
Multiple-Choice Quiz
1. A SYN flood is an example of what type of attack?
A. Malicious code
B. Denial-of-service attack
C. On-path/man-in-the-middle attack
D. Spoofing
2. An attack in which the attacker simply listens for all traffic being transmitted across a network, in the hope of viewing something such as a user ID and password combination, is known as:
A. An on-path/man-in-the-middle attack
B. A denial-of-service attack
C. A sniffing attack
D. A backdoor attack
3. Which attack takes advantage of a trusted relationship that exists between two systems?
A. Spoofing
B. Password guessing
C. Sniffing
D. Brute force
4. In what type of attack does an attacker re-send the series of commands and codes used in a financial transaction to cause the transaction to be conducted multiple times?
A. Spoofing
B. Man in the middle
C. Replay
D. Backdoor
5. Why are rootkits challenging security problems?
A. They can be invisible to the operating system and end user.
B. Their true functionality can be cloaked, preventing analysis.
C. They can do virtually anything an operating system can do.
D. All of the above.
6. An attack in which an attacker attempts to lie and misrepresent himself in order to gain access to information that can be useful in an attack is known as which of the following?
A. Social science
B. Authenticated/white-hat hacking
C. Social engineering
D. Social manipulation
7. An attack that is designed to deny a system access to its files and spread across a network causing destruction is called?
A. Worm
B. Ransomware
C. Trojan horse
D. Remote access trojan
8. What is the best way to minimize possible avenues of attack for your system?
A. Install a firewall and check the logs daily.
B. Monitor your intrusion detection system for possible attacks.
C. Limit the information that can be obtained on your organization and the services that are run by your Internet-visible systems.
D. Ensure that all patches have been applied for the services that are offered by your system.
9. A war-driving attack is an attempt to exploit what technology?
A. Fiber-optic networks, whose cables often run alongside roads and bridges
B. Cellular telephones
C. The public switched telephone network (PSTN)
D. Wireless networks
10. Malicious code that is set to execute its payload on a specific date or at a specific time is known as which of the following?
A. A logic bomb
B. A trojan horse
C. A virus
D. A time bomb
 Essay Quiz
Essay Quiz
1. Compare and contrast port scanning and ping sweeps.
2. What is the best practice to employ to mitigate malware effects on a machine?
Lab Projects
• Lab Project 15.1
Using the Internet, research password-cracking tools. Then, using a tool of choice, examine how easy it is to crack passwords on Windows- and Linux/UNIX-based systems. Create a series of accounts with different complexities of passwords and see how well they fare.
• Lab Project 15.2
Obtain a copy of the nmap scanning tool. Explore the various command-line options to scan networks, fingerprint operating systems, and perform other network-mapping functions.
Note: Students should try these options, but only in a lab environment, not across the Internet from their home ISP.
