 Computer Forensics
Computer Forensics

Computer forensics is certainly a popular buzzword in computer security. This chapter addresses the key aspects of computer forensics in preparation for the CompTIA Security+ certification exam. It is not intended to be a treatise on the topic or a legal tutorial regarding the presentation of evidence in a court of law. This material is only an introduction to the topic, and before anyone enters into forensic work or practice, much additional study is necessary. The principles presented in this chapter are of value in conducting any investigative processes, including internal or external audit procedures, but the many nuances of handling legal cases are far beyond the scope of this text.
The term forensics relates to the application of scientific knowledge to legal problems. Specifically, computer forensics involves the preservation, identification, documentation, and interpretation of computer data. In today’s practice, computer forensics can be performed for these three purposes:
![]() Investigating and analyzing computer systems as related to a violation of law
Investigating and analyzing computer systems as related to a violation of law
![]() Investigating and analyzing computer systems for compliance with an organization’s policies
Investigating and analyzing computer systems for compliance with an organization’s policies
![]() Responding to a request for digital evidence (e-discovery)
Responding to a request for digital evidence (e-discovery)
![]()
Cross Check
Incident Response
Incident response and associated policies and procedures are covered in Chapter 22.
Forensics is often associated with incident response, which is the procedure used to respond to an abnormal condition in a system. There is a subtle difference, however. Incident response is about corrective action—returning the system to a normal operational state—whereas forensics is about figuring out what happened.
If an unauthorized person accesses a system, that person likely has violated the law. However, a company employee who performs similar acts (accessing data remotely) may or may not violate laws—the determination of which depends on many factors, including specific authorizations and job duties. Someone can violate corporate policies while acting lawfully with respect to computer laws. It is worth noting that knowingly exceeding one’s authorizations with respect to system access is a violation of the law.
Any of these situations could ultimately result in legal action and may require legal disclosure. Therefore, it is important to note that computer forensic actions may, at some point in time, deal with legal violations, and investigations could go to court proceedings. As a potential first responder, you should always seek legal counsel. Also seek legal counsel ahead of time as you develop and implement corporate policies and procedures. It is extremely important to understand that even minor procedural missteps can have significant legal consequences. The rule to follow is simple: always assume that the material will be used in a court of law and thus must be handled in a perfectly proper manner at all times. This further means that when dealing with forensics, you must ensure that all steps are performed by qualified forensic examiners.
 Evidence
Evidence
Evidence consists of the documents, verbal statements, and material objects that are admissible in a court of law. Evidence is critical to convincing management, juries, judges, or other authorities that some kind of violation has occurred. The submission of evidence is challenging, but it is even more challenging when computers are used because the people involved may not be technically educated and thus may not fully understand what has happened.
Computer evidence presents yet more challenges because the data itself cannot be experienced with the physical senses—that is, you can see printed characters, but you can’t see the bits where that data is stored. Bits of data are merely magnetic pulses on a disk or some other storage technology. Therefore, data must always be evaluated through some kind of “filter” rather than sensed directly. This is often of concern to auditors because good auditing techniques recommend accessing the original data or a version that is as close as possible to the original data.
Types of Evidence
All evidence is not created equal. Some evidence is stronger and better than other evidence. Several types of evidence can be germane, as listed here:
![]() Direct evidence This is oral testimony that proves a specific fact (such as an eyewitness’s statement). The knowledge of the facts is obtained through the five senses of the witness, with no inferences or presumptions.
Direct evidence This is oral testimony that proves a specific fact (such as an eyewitness’s statement). The knowledge of the facts is obtained through the five senses of the witness, with no inferences or presumptions.
![]() Real evidence Also known as associative or physical evidence, this includes tangible objects that prove or disprove a fact. Physical evidence links the suspect to the scene of a crime.
Real evidence Also known as associative or physical evidence, this includes tangible objects that prove or disprove a fact. Physical evidence links the suspect to the scene of a crime.
![]() Documentary evidence This is evidence in the form of business records, printouts, manuals, and the like. Much of the evidence relating to computer crimes is documentary evidence.
Documentary evidence This is evidence in the form of business records, printouts, manuals, and the like. Much of the evidence relating to computer crimes is documentary evidence.
![]() Demonstrative evidence This type of evidence is used to aid the jury and can be in the form of a model, experiment, chart, and so on, offered to prove that an event occurred.
Demonstrative evidence This type of evidence is used to aid the jury and can be in the form of a model, experiment, chart, and so on, offered to prove that an event occurred.

The digital forensic process is a technically demanding one, with no room for errors. The most common cause of evidence from an investigation being excluded from court proceedings is spoliation, the unauthorized alteration of digital evidence. If the forensic process is less than perfect, spoliation is assumed. The best guidance is (1) always perform forensics as if you are going to court with the evidence, and (2) if you do not have qualified digital forensic investigators in house, do nothing to the device/media—let a professional handle it.
Standards for Evidence
Evidence in U.S. federal court cases is governed by a series of legal precedents, the most notable of which is the Daubert standard. Three U.S. Supreme Court cases articulate the Daubert standard and shape how materials are entered into evidence. Four specific elements are associated with the admission of scientific expert testimony. This is important with respect to digital forensics because the form of the evidence means that it can rarely speak for itself; rather, it must be interpreted by an expert and presented to the court.
The first element is that the judge is the gatekeeper. Materials are not considered evidence until declared so by the judge. This is to ensure that experts are determined to be experts before the court relies upon their judgment. A second element consists of reliability and relevance. The trial judge is to determine that the expert’s testimony is relevant to the proceedings at hand and that the expert’s methods are reliable with respect to the material being attested to. The third element is that expert knowledge should be based on science—specifically, science that is based on the scientific method with a replicable methodology. The final element relates to this scientific methodology, stating that it must be based on proven science, subjected to peer review, with a known error rate or potential error rate and consensus among the scientific community that the methodology is generally accepted. After these elements are satisfied, the judge can admit the expert’s testimony as evidence.
These factors all relate to a U.S. federal court decision and therefore are binding only in the U.S. federal judiciary, but the test is recognized and applied in similar form at many levels of jurisdiction. The bottom line is simple: the data can’t speak for itself, and experts who can interpret the data operate under strict guidelines with respect to conduct, qualifications, principles, and methods.
To be credible, especially if evidence will be used in court proceedings or in corporate disciplinary actions that could be challenged legally, evidence must meet these three standards:
![]() Sufficient evidence It must be convincing or measure up without question.
Sufficient evidence It must be convincing or measure up without question.
![]() Competent evidence It must be legally qualified and reliable.
Competent evidence It must be legally qualified and reliable.
![]() Relevant evidence It must be material to the case or have a bearing on the matter at hand.
Relevant evidence It must be material to the case or have a bearing on the matter at hand.

Tech Tip
Evidence Control Mental Checklist
Keep these questions in mind as you collect evidence:
![]() Who collected the evidence?
Who collected the evidence?
![]() How was it collected?
How was it collected?
![]() Where was it collected?
Where was it collected?
![]() Who has had possession of the evidence?
Who has had possession of the evidence?
![]() How was it protected and stored?
How was it protected and stored?
![]() When was it removed from storage? Why? Who took possession?
When was it removed from storage? Why? Who took possession?
Three Rules Regarding Evidence
An item can become evidence when it is admitted by a judge in a case. These three rules guide the use of evidence with regard to its use in court proceedings:
![]() Best evidence rule Courts prefer original evidence rather than a copy to ensure that no alteration of the evidence (whether intentional or unintentional) has occurred. In some instances, an evidence duplicate can be accepted, such as when the original is lost or destroyed by acts of God or in the normal course of business. A duplicate is also acceptable when a third party beyond the court’s subpoena power possesses the original.
Best evidence rule Courts prefer original evidence rather than a copy to ensure that no alteration of the evidence (whether intentional or unintentional) has occurred. In some instances, an evidence duplicate can be accepted, such as when the original is lost or destroyed by acts of God or in the normal course of business. A duplicate is also acceptable when a third party beyond the court’s subpoena power possesses the original.
![]() Exclusionary rule The Fourth Amendment to the U.S. Constitution precludes illegal search and seizure. Therefore, any evidence collected in violation of the Fourth Amendment is not admissible as evidence. Additionally, if evidence is collected in violation of the Electronic Communications Privacy Act (ECPA) or other related provisions of the U.S. Code, it may not be admissible to a court. For example, if no policy exists regarding the company’s intent to monitor network traffic or systems electronically and the employee has not acknowledged this policy by signing an agreement, sniffing the employee’s network traffic could be a violation of the ECPA.
Exclusionary rule The Fourth Amendment to the U.S. Constitution precludes illegal search and seizure. Therefore, any evidence collected in violation of the Fourth Amendment is not admissible as evidence. Additionally, if evidence is collected in violation of the Electronic Communications Privacy Act (ECPA) or other related provisions of the U.S. Code, it may not be admissible to a court. For example, if no policy exists regarding the company’s intent to monitor network traffic or systems electronically and the employee has not acknowledged this policy by signing an agreement, sniffing the employee’s network traffic could be a violation of the ECPA.
![]() Hearsay rule Hearsay is secondhand evidence—evidence offered by the witness that is not based on the personal knowledge of the witness but is being offered to prove the truth of the matter asserted. Typically, computer-generated evidence is considered hearsay evidence because the maker of the evidence (the computer) cannot be interrogated. There are exceptions being made where items such as logs and headers (computer-generated materials) are being accepted in court. There are exceptions, but they rarely apply to digital evidence.
Hearsay rule Hearsay is secondhand evidence—evidence offered by the witness that is not based on the personal knowledge of the witness but is being offered to prove the truth of the matter asserted. Typically, computer-generated evidence is considered hearsay evidence because the maker of the evidence (the computer) cannot be interrogated. There are exceptions being made where items such as logs and headers (computer-generated materials) are being accepted in court. There are exceptions, but they rarely apply to digital evidence.
![]()
The laws mentioned here are U.S. laws. Other countries and jurisdictions may have similar laws that would need to be considered in a similar manner.
 Chain of Custody
Chain of Custody
Evidence, once collected, must be properly controlled to prevent tampering. The chain of custody accounts for all people who handled or had access to the evidence. The chain of custody shows who obtained the evidence, when and where it was obtained, where it was stored, and who had control or possession of the evidence for the entire time since the evidence was obtained.
The following are the critical steps in a chain of custody:
1. Record each item collected as evidence.
2. Record who collected the evidence, along with the date and time it was collected or recorded.
3. Write a description of the evidence in the documentation.
4. Put the evidence in containers and tag the containers with the case number, the name of the person who collected it, and the date and time it was collected or put in the container.
5. Record all message digest (hash) values in the documentation.
6. Securely transport the evidence to a protected storage facility.
7. Obtain a signature from the person who accepts the evidence at this storage facility.
8. Provide controls to prevent access to and compromise of the evidence while it is being stored.
9. Securely transport the evidence to court for proceedings.

Never analyze the seized evidence directly. The original evidence must be secured and protected with a chain of custody. It should never be subjected to a forensic examination due to the fragile nature of digital evidence. A forensic copy, however, can be examined and, if something goes wrong, discarded, and the copy process can be repeated. A good forensics process will prove that the forensic copy is identical to the original at the start and at the end of the examination. From a practical standpoint, investigators usually make multiple forensic copies and perform their analysis in parallel on the multiple copies.
Tags
As previously discussed, a chain of custody document records all accesses to evidence from time of collection until destruction. But how does one refer to a specific piece of evidence, especially if it is hardware containing data, such as a USB drive? This is done though tags. Physical serialized tags are attached to each item, and the tag number is used to identify a specific item. Frequently the items are then stored in antistatic bags to protect them from damage.
 Forensic Process
Forensic Process
Forensics is the use of scientific methods in the analysis of matters in connection with crime or other legal matters. Because of the connection to law, it is an exacting process, with no room for error. In digital forensics, the issue of alteration becomes paramount because changing 1s to 0s does not leave a trace in many situations. Because of the issue of contamination or spoliation of evidence, detailed processes are used in the processing of information.
From a high-level point of view, multiple steps are employed in a digital forensic investigation:
1. Identification Recognize an incident from indicators and determine its type and scope. This is not explicitly within the field of forensics but is significant because it impacts other steps. What tools were used? How many systems are involved? How much data is to be copied? These questions all have ramifications on the successful outcome of a forensic process.
2. Preparation Prepare tools, techniques, and search warrants and monitor authorizations and management support.
3. Approach/strategy Dynamically formulate an approach based on potential impact on bystanders and the specific technology in question. The goal of the strategy should be to maximize the collection of untainted evidence while minimizing impact to the victim or owner.
4. Preservation Isolate, secure, and preserve the state of physical and digital evidence. This includes preventing people from using the digital device or allowing other electromagnetic devices to be used within a certain proximity. Proper preservation is essential to prevent alteration of the source.
5. Collection Record the physical scene and duplicate digital evidence using standardized and accepted procedures. This is where a digital camera and microphone are vital tools for capturing details—serial numbers, layouts, and so forth—quickly and definitively.
6. Examination In-depth, systematic search of evidence relating to the suspected crime. This step occurs later, in a lab, and focuses on identifying and locating potential specific evidence elements, possibly within unconventional locations. It is important to construct detailed documentation for analysis, documenting the metadata and data values that may be relevant to the issues at hand in the investigation.
7. Analysis Determine significance, reconstruct fragments of data, and draw conclusions based on the elements of evidence found. The data itself cannot tell a story, and in this step the investigator weaves the elements into a picture, ideally the only one that can be supported. Although the intuition is to prove guilt, the skilled and seasoned investigator focuses on painting the picture that the data describes, regardless of outcome, and making it comprehensive and complete so that it will stand up to challenge. Multiple people with different skill sets may be needed to complete the picture.
8. Presentation Summarize and provide an explanation of the conclusions. The results should be written in layperson’s terms using abstracted terminology. If you cannot explain the information to a nontechnical layperson, then you do not understand it well enough to complete this aspect. All abstracted terminology should reference the specific details of the case.
9. Returning evidence Ensure physical and digital property is returned to its proper owner and determine how and what criminal evidence must be removed. (For example, hardware may be returned, but images of child pornography would be removed.) This is not an explicit step of forensic investigation, and most models that address how to seize evidence rarely address this aspect. But at the end of the day, the job is not done until all aspects are finished, and this includes this level of cleanup activity.
When information or objects are presented to management or admitted to court to support a claim, that information or those objects can be considered as evidence or documentation supporting your investigative efforts. Senior management will always ask a lot of questions—second- and third-order questions that you need to be able to answer quickly. Likewise, in a court, credibility is critical. Therefore, evidence must be properly acquired, identified, protected against tampering, transported, and stored.
![]()
A digital camera is great for recording a scene and information. Screenshots of active monitor images may be obtained as well. Pictures can detail elements such as serial number plates, machines, drives, cable connections, and more. Photographs are truly worth a thousand words.
Data Recovery
Data recovery in a digital forensics sense is associated with determining the relevant information for the issue at hand—simply stated, recover the evidence associated with an act. But what if the act is not precisely known? For example, suppose a sales manager for a company quits and goes to work with a competitor. Because she is a sales manager, she has had access to sensitive information that would benefit the new employer. But how do you know whether she took sensitive information with her? And even if she did, how do you determine for purposes of recovery which information she took, and where to look for it? Since forensics software has yet to invent a “Find Evidence” button, and there is no field in any computer protocol to tell investigators this is the data they are looking for, the act of recovering the necessary information can be a significant challenge. What’s more, with today’s multiterabyte drives, the volumes of data can be daunting.
Acquiring Evidence
When an incident occurs, you will need to collect data and information to facilitate your investigation. If someone is committing a crime or intentionally violating a company policy, she will likely try to hide her tracks. Therefore, you should collect as much information as soon as you can. In today’s highly networked world, evidence can be found not only on the workstation or laptop computer but also on company-owned file servers, security appliances, and servers located with the Internet service provider (ISP).

Tech Tip
When Is Evidence Really Evidence?
Evidence is the term used in legal system for when an exhibit is produced in court and is accepted by the court. Technically, the use of the word evidence throughout this chapter is in error, because what is being collected is a series of exhibits that may be presented to the court for consideration. For an exhibit to be admitted, it must pass a test of admissibility. Although many criteria can apply, in the case of digital exhibits, careful attention is paid to the entire pedigree, from time of creation, to collection, analysis, and preparation as an exhibit. If at any point in this cycle there is a chance that the element could have changed, it will be objected to and likely be ruled inadmissible. This is why adherence to perfection is important in the evidentiary chain.
In the process of acquiring evidence, one must do as much as possible to prevent damage or loss of evidence. Photographs can be used to document the scene, but the crucial item is in the acquisition of digital information. Most interactions with digital media involve reading and writing data, and any written changes during acquisition can destroy critical elements.
![]()
Try This!
Find and Create a Tool
Microsoft produced a forensic tool for law enforcement called Computer Online Forensics Evidence Extractor (COFEE) that can be used to collect a wide range of data from a suspect machine. Restricted by license to law enforcement, it was out of reach for most investigators, until it was published by WikiLeaks. An examination of how it functions provides useful information, and many of its functions can be readily copied by investigators. COFEE is a wrapper for a whole host of utilities—think Sysinternals and more—all integrated by script. This automated process can be re-created by any competent forensic investigator. Automated scripts and tools reduce errors and increase effectiveness.
When an incident occurs and the computer being used is going to be secured, you must consider two questions: should it be turned off, and should it be disconnected from the network? Forensic professionals debate the reasons for turning a computer on or turning it off. Some state that the plug should be pulled in order to freeze the current state of the computer. However, this results in the loss of any data associated with an attack in progress from the machine. Any data in RAM will also be lost. Further, it may corrupt the computer’s filesystem and could call into question the validity of your findings.

File timestamps may be of use during the analysis phase. To correlate file timestamps to actual time, it is important to know the time offset between the system clock and real time. Recording the time offset while the system is live is critical if the system clock is different from the actual time. This information is lost if the machine is powered off.
Imaging or dumping the physical memory (RAM) of a computer system can help identify evidence that is not available on a hard drive. This is especially appropriate for rootkits, for which evidence on the hard drive is hard to find. Once the memory is imaged, you can use a hex editor to analyze the image offline on another system. (Memory-dumping tools and hex editors are available on the Internet.) Note that dumping memory is more applicable for investigative work where court proceedings will not be pursued. If a case is likely to end up in court, do not dump memory without first seeking legal advice to confirm that live analysis of the memory is acceptable; otherwise, the defendant will easily be able to dispute the claim that evidence was not tampered with.
On the other hand, it is possible for the computer criminal to leave behind a software bomb that you don’t know about, and any commands you execute, including shutting down or restarting the system, could destroy or modify files, information, or evidence. The criminal may have anticipated such an investigation and altered some of the system’s binary files.
Further, if the computer being analyzed is a server, it is unlikely management will support taking it offline and shutting it down for investigation. So, from an investigative perspective, either course may be correct or incorrect, depending on the circumstances surrounding the incident. What is most important is that you are deliberate in your work, you document your actions, and you can explain why you took the actions you performed.
Many investigative methods are used. Figure 23.1 shows the continuum of investigative methods from simple to more rigorous.
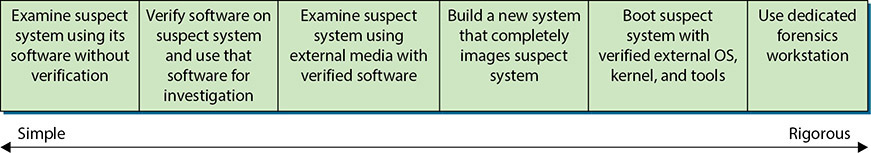
• Figure 23.1 Investigative method rigor
Figure 23.2 shows the relationship between the complexity of your investigation and both the reliability of your forensic data and the difficulty of investigation.
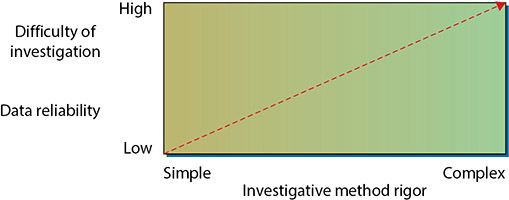
• Figure 23.2 Required rigor of the investigative method versus both data reliability and the difficulty of investigation
Order of Volatility
There are many sources of data in a computer system, and if the machine is running, some of these sources can be volatile. Things such as the state of the CPU and its registers are always changing, as are memory and even storage. These elements tend to change at different rates, and you should pay attention to the order of volatility so that collection priority is devoted where it can matter.

Tech Tip
Data Volatility
Here are some sources listed from the most volatile to the most persistent:
![]() CPU storage (registers/cache)
CPU storage (registers/cache)
![]() System storage (RAM, routing tables, ARP cache, process tables, kernel stats)
System storage (RAM, routing tables, ARP cache, process tables, kernel stats)
![]() Data on fixed media (complete image)
Data on fixed media (complete image)
![]() Removable media
Removable media
![]() Output/hardcopy
Output/hardcopy
The collection of electronic data can be a difficult task. In some cases, such as volatile data, there may be only one chance to collect it, after which it becomes lost forever. Volatile information locations such as the RAM change constantly, and data collection should occur in the order of volatility or lifetime of the data.
The following is the order of volatility of digital information in a system:
1. CPU, cache, and register contents (collect first)
2. Routing tables, ARP cache, process tables, kernel statistics
3. Live network connections and data flows
4. Memory (RAM)
5. Temporary filesystem/swap space
6. Data on hard disk
7. Remotely logged data
8. Data stored on archival media/backups (collect last)
When you’re collecting digital evidence, it is important to use the proper techniques and tools. Some of the key tasks are using write blockers when making forensic copies, hashing and verifying hash matches, documenting handling and storage, and protecting media from environmental change factors. Of particular note is that the data present on a system can be a function of both the filesystem and the hardware being employed. A physical hard disk drive will persist data longer than a solid state drive. Additionally, the newer filesystems with journaling and shadow copies can have longer persistence of information than older systems such as File Allocation Table (FAT) systems. Raw disk blocks can be recovered in some filesystems long after data has been rewritten or erased because of the nature of how the filesystems manage the data.

Understanding the order of volatility of digital information in a system is an important issue, for once violated, information can be lost forever. This is not an academic exercise; this information is used in every investigation.
Capture System Image
Capturing a system image of a system is more than just copying the hard drive. Information also exists in the RAM and may be preserved in the files used for hibernation. Having a process that can copy the RAM image as well as the hard drives in a coordinated manner, preserving the evidence, is important in many investigations. Investigations involving malware or rootkits will depend upon this type of data collection if they are to be effective. As previously mentioned in this chapter, this level of data collection has many issues, both technical and procedural. Ensuring a plan is developed and understood before execution is critical to avoid missing elements or spoiling the data.
The other system image is that of the internal storage devices. Making forensic duplicates of all partitions is a key step in preserving evidence. A forensic copy is a bit-by-bit copy and has supporting integrity checks in the form of hashes. The proper practice is to use a write blocker when making a forensic copy of a drive. This device allows a disk to be read but prevents any writing actions to the drive, guaranteeing that the copy operation does not change the original media. Once a forensic copy is created, working copies from the master forensic copy can be created for analysis and sharing with other investigators. The use of hash values provides a means of demonstrating that all of the copies are true to each other and the original.

A digital forensic copy can only be made with specific methods designed to perform bit-by-bit copying of the files’ free and slack space, making a verifiably true copy of the medium as demonstrated by hash values.
Network Traffic and Logs
An important source of information in an investigation can be the network activity associated with a device. There can be a lot of useful information in the network logs associated with the network infrastructure. The level and breadth of this information are determined by the scope of the investigation. While the best data would be from that of a live network forensic collection process, in most cases this type of data will not be available. There are many other sources of network forensic data, including firewall and IDS logs, network flow data, and event logs on key servers and services.
Capture Video
A convenient method of capturing significant information at the time of collection is video capture. Videos allow high-bandwidth data collection that can show what was connected to what, how things were laid out, desktops, and so forth. A picture can be worth a thousand words, so take the time to document everything with pictures. Pictures of serial numbers and network and USB connections can prove invaluable later in the forensics process. Complete documentation is a must in every forensics process, and photographs can assist greatly in capturing details that would otherwise take a long time and be prone to transcription error.
Another source of video data is in the closed-circuit television (CCTV) cameras that are used for security, both in industry and in growing numbers of homes. This is digital information like all other digital information; it can be copied and manipulated and needs to be preserved in the same manner as other digital information.
Social media has created a “marketplace” for people to share videos, and this has led to a dramatic increase in user-created video content, commonly from smartphones. These videos are uploaded to social media platforms and shared with others. The process of uploading the videos can remove a lot of metadata that would be useful from a forensics point of view, but they are still used in legal proceedings under the aspect of the evidence speaking for itself. As AI-generated deep fakes become more advanced, this will have to change. For example, a video of you delivering a speech can be faked with fairly high fidelity, resulting in “evidence” of you giving a speech you never gave. Again, this will make metadata and traceability more important.
![]()
A digital camera is great for recording a scene and information. Screenshots of active monitor images may be obtained as well. Pictures can detail elements such as serial number plates, machines, drives, cables connections, and more. Photographs are truly worth a thousand words.
Record Time Offset
Files and events logged on a computer will have timestamp markings that are based on the clock time on the machine itself. It is a mistake to assume that this clock is accurate. To allow the correlation of timestamp data from records inside the computer with any external event, it is necessary to know any time offset between the machine clock and the actual time.

Understanding time elements for forensics is important. Pay attention to time zones and the specific details in the question.

Tech Tip
Record Time Offset
A common data element needed later in the forensics process is an accurate system time with respect to an accurate external time source. A record time offset is calculated by measuring system time with an external clock such as a Network Time Protocol (NTP) server. This can be lost if the system is powered down, so it is best collected while the system is still running. Another form of time offset is the difference between local time zones and UTC. As discussed earlier, with most time records being in UTC, conversion to local time zones may be necessary to make sense of some records.
Take Hashes
If files, logs, and other information are going to be captured and used for evidence, you need to ensure that the data isn’t modified. In most cases, a tool that implements a hashing algorithm to create message digests is used.
A hashing algorithm performs a function similar to the familiar parity bits, checksum, and cyclic redundancy check (CRC). It applies mathematical operations to a data stream (or file) to calculate some number (the hash) that is unique based on the information contained in the data stream (or file). If a subsequent hash created on the same data stream results in a different hash value, it usually means that the data stream was changed.
The mathematics behind hashing algorithms has been researched extensively, and although it is possible that two different data streams could produce the same message digest, it is very improbable. This is an area of cryptography that has been rigorously reviewed, and the mathematics behind Message Digest 5 (MD5) and Secure Hash Algorithm (SHA) are sound. In 2005, weaknesses were discovered in the MD5 and SHA implementations, leading the National Institute of Standards and Technology (NIST) to announce a competition to find a new cryptographic hashing algorithm, named SHA-3. Although MD5 is still used, best practice is to use the SHA-2 series and then SHA-3 once it becomes integrated into tools.
The hash tool is applied to each file or log, and the message digest value is noted in the investigation documentation. It is a good practice to write the logs to a write-once media such as a CD-ROM. If the case actually goes to trial, the investigator may need to run the tool on the files or logs again to show that they have not been altered in any way.
![]()
Hashing is used throughout digital forensics to measure integrity between copies of data. Checksums do not have the specificity of hashes, so hashes are the primary tool.
![]()
Checksums are mathematical algorithms that produce a check digit based on an incoming stream. Designed for error testing across small data sets, they have advantages and disadvantages. For example, for error checking, they are fast and can detect a single bit error. However, they miss larger numbers of errors as the effect cancels out. Thus, checksums serve no real purpose in digital forensics. If two checksums are different, the incoming data streams are different. If the checksums are the same, you might still have different data streams.
Screenshots
Particular attention should be paid to the state of what is on the screen at the time of evidence collection. The information on a video screen is lost once the system changes or power is removed. Taking screenshots, using a digital camera or smartphone camera, can provide documentation as to what was on the screen at the time of collection. Because you cannot trust the system internals themselves to be free of tampering, do not use internal screenshot capture methods.
Witness Interviews
Remember that witness credibility is extremely important. It is easy to imagine how quickly credibility can be damaged if the witness is asked “Did you lock the filesystem?” and can’t answer affirmatively. The same is true if the witness is asked “When you imaged this disk drive, did you use a new system?” and can’t answer that the destination disk was new or had been completely formatted using a low-level format before data was copied to it. Witness preparation can be critical in a case, even for technical experts.
Identifying Evidence
Evidence must be properly marked as it is collected so that it can be identified as a particular piece of evidence gathered at the scene. Properly label and store evidence, and make sure the labels can’t be easily removed. Keep an evidence control log book identifying each piece of evidence (in case the label is removed); the people who discovered it; the case number; the date, time, and location of the discovery; and the reason for collection. Keep a log of all staff hours and expenses. This information should be specific enough for recollection later in court. It is important to log other identifying marks, such as device make, model, serial number, cable configuration or type, and so on. Note any type of damage to the piece of evidence.

You should never examine a system with the utilities provided by that system. You should always use utilities that have been verified as correct and uncorrupted. Even better, use a forensic workstation, a computer system specifically designed to perform computer forensic activities. Do not open any files or start any applications. If possible, document the current memory and swap files, running processes, and open files. Disconnect the system from the network and immediately contact senior management. Unless you have appropriate forensic training and experience, consider calling in a professional.
Being methodical is extremely important when identifying evidence. Do not collect evidence by yourself—have a second person who can serve as a witness to your actions. Keep logs of your actions both during seizure and during analysis and storage. A sample log, providing the minimum contents of an evidence control log book entry, is shown here:

Protecting Evidence
Evidence must be properly acquired, identified, protected against tampering, transported, and stored. Digital evidence has one huge glaring issue: it can change and not leave a record of the change. The fact that the outcome of a case can hinge on information that can be argued as being not static leads to the crucial element of preservation. From the initial step in the forensics process, the most important issue must always be the preservation of the data. There is no recovery from data that has been changed, so from the beginning safeguards must be in place. There are several key steps that assist the forensic investigator in avoiding data spoilage. First, when data is collected, a solid chain of custody is maintained until the case is completed and the materials are released or destroyed. Second, when a forensic copy of the data is obtained, a hash is collected as well to allow for the verification of integrity. All analysis is done on forensic copies of the original data collection, not on the master copy itself. Also, each copy is verified before and after testing with hash values compared to the original set to demonstrate integrity.
Protect evidence from electromagnetic or mechanical damage. Ensure that evidence is not tampered with, damaged, or compromised by the procedures used during the investigation. This helps avoid potential liability problems later. Protect evidence from extremes in heat and cold, humidity, water, magnetic fields, and vibration. Use static-free evidence-protection gloves as opposed to standard latex gloves. Seal the evidence in a proper container with evidence tape, and mark it with your initials, date, and case number. For example, if a mobile phone with advanced capabilities is seized, it should be properly secured in a hard container designed to prevent accidentally pressing the keys during transit and storage. If the phone is to remain turned on for analysis, radio frequency isolation bags that attenuate the device’s radio signal should be used. This will prevent remote wiping, locking, or disabling of the device.
![]()
Third-party investigators are commonly used in civil matters. When doing digital forensics for a civil litigation–based case, it is important to consult with the retaining counsel concerning the level of detail and records desired. In civil litigation, anything written will be requested to be disclosed during pretrial discovery. This can provide strategy disclosure beyond what is desired by counsel. The alternative is to keep minimal required records as determined by counsel.
This process adds a lot of work and time to an investigation, but it yields one crucial element: repudiation of any claim that the data was changed/tampered/damaged in any way. Should a hash value vary, the action is simple: discard the copy, make a new copy, and begin again. This process shows the courts two key things: process rigor to protect the integrity of the data, and traceability via hash values to demonstrate the integrity of the data and the analysis results derived from the data.
Transporting Evidence
Properly log all evidence in and out of controlled storage. Use proper packing techniques, such as placing components in static-free bags, using foam packing material, and using cardboard boxes. Be especially cautious while transporting evidence to ensure custody of evidence is maintained and the evidence isn’t damaged or tampered with.

Tech Tip
Protecting Evidence
Any and all collected digital evidence needs to be protected from a wide range of potential losses—environmental, theft, actual loss, alteration, physical or electrical damage, or even the perception of the possibility of loss occurring. In any legal proceeding, whether criminal or civil, the other party will always examine the storage conditions and, if less than perfect, place the burden on the person storing it to prove that it is still intact. This is just one reason why recording hash values upon collection is so important.
Storing Evidence
Store the evidence in an evidence room that has low traffic, restricted access, camera monitoring, and entry-logging capabilities. Store components in static-free bags, foam packing material, and cardboard boxes, and inside metal tamper-resistant cabinets or safes whenever possible. Many of today’s electronics are sensitive to environmental factors. It is important for storage areas to have environmental controls to protect devices from temperature and humidity changes. It is also prudent to have environmental-monitoring devices to ensure that temperature and humidity remain within safe ranges for electronic devices.
Conducting the Investigation
When analyzing computer storage components, you must use extreme caution. A copy of the system should be analyzed—never the original system, because that will have to serve as evidence. A system specially designed for forensic examination, known as a forensic workstation, can be used. Forensic workstations typically contain hard drive bays, write blockers, analysis software, and other devices to safely image and protect computer forensic data. Analysis should be done in a controlled environment with physical security and controlled access.
Never analyze the seized system directly. Always make multiple images of the device and analyze a copy.

Tech Tip
Tools of the Trade
The following are the tools of the forensics trade:
![]() Disk wipe utilities Tools to completely delete files and overwrite contents
Disk wipe utilities Tools to completely delete files and overwrite contents
![]() File viewers Text and image viewers
File viewers Text and image viewers
![]() Forensic programs Tools to analyze disk space, file content, system configuration, and so on
Forensic programs Tools to analyze disk space, file content, system configuration, and so on
![]() Forensic workstations Specialized workstations containing hardware, software, and component interface capabilities to perform computer forensic activities
Forensic workstations Specialized workstations containing hardware, software, and component interface capabilities to perform computer forensic activities
![]() Hard drive tools Partition-viewing utilities, bootable CDs
Hard drive tools Partition-viewing utilities, bootable CDs
![]() Unerase tools Tools to reverse file deletions
Unerase tools Tools to reverse file deletions
One of the key elements to preserving the chain of custody, protecting evidence, and having copies of data for analysis is the concept of digital forensic duplication of data. A digital forensic copy is a carefully controlled copy that has every bit the same as the original. Not just files, but all data structures associated with the device, including unused space, are copied in a digital forensic image copy, every bit, bit by bit. Making this type of copy is not something done with normal file utilities; specialty programs are required.

When conducting a digital forensic investigation, consider local laws. Many states require that independent investigators be licensed private investigators. If you are working as an analyst on in-house systems, the laws may have differing levels of applicability. Before consulting, it is best to investigate the need of a license.
It is also important not to interface with the digital media using the host system because all filesystems both read and write to the storage media as part of their normal operation, thus altering the media. This type of alteration changes information, potentially damaging the trace evidence needed in the investigation. For this reason, a write blocker is commonly used to connect the media to the investigator’s computer. Figure 23.3 shows a kit that contains both write blockers and a forensic duplicator.
It is common for forensic duplicator devices to have additional features to assist an investigator, such as making multiple copies at once and calculating hash values for the device and the duplicate. Capturing the hash values for all items is an essential first step in handling any digital evidence.

• Figure 23.3 (a) Write blocker devices and (b) forensic duplicator device

Tech Tip
Forensics-Based Drive Imaging
When a forensic investigation on a series of computers is needed to determine facts in a computer investigation, a variety of methods can be used to discover and recover the evidence. For example, if a developer group is being investigated, the investigator could look at each machine and find the specific evidence that is being sought. The problem with this approach is that in the process of doing the investigation, the other developers in the area become aware and have a chance to destroy critical evidence. For this reason, and to minimize disruption to a team, many times the investigation begins with a large-scale forensic duplication effort. The steps are remarkably simple and well-practiced by many investigative firms, as shown here:
1. Document the scope of the machines being investigated, noting the number of drives and sizes.
2. Send in a team after hours to do the duplication.
3. Open each machine, disconnect the hard drives, and attach external cables.
4. Duplicate each drive using a forensic duplication procedure that makes a complete image of the hard drive on a separate media source.
5. Reassemble the machines, leaving no evidence that the duplication was performed.
The forensic images are then examined one by one at a later time, away from inquisitive and prying eyes.
 Message Digest and Hash
Message Digest and Hash
If files, logs, and other information are going to be captured and used for evidence, you need to ensure that the data isn’t modified. In most cases, a tool that implements a hashing algorithm to create message digests is used.
![]()
Cross Check
Hash Algorithms and Forensics
Hash algorithms offer digital forensics the ability to “bag and tag” evidence. Although it does not protect the evidence from tampering, it provides clear proof of whether data has been changed. This is an important issue to resolve, given how easy it is to change digital data and the fact that typically no trace is left of the change. You can find a complete review of hashing algorithms in Chapter 5. The important question regarding hashes and forensics is this: how and where do you record hash values to protect their integrity as part of the investigative process?
The hash tool is applied to each file or log, and the message digest value is noted in the investigation documentation. It is a good practice to write the logs to a write-once media such as CD-ROM. When the case actually goes to trial, the investigator may need to run the tool on the files or logs again to show that they have not been altered in any way since being obtained.
 Analysis
Analysis
After successfully imaging the drives to be analyzed and calculating and storing the message digests, the investigator can begin the analysis. The details of the investigation will depend on the particulars of the incident being investigated. However, in general, the following steps will be involved:
1. Check the Recycle Bin for deleted files.
2. Check the web browser history files and address bar histories.
3. Check the web browser cookie files. Different web browsers store cookies in different places.
4. Check the Temporary Internet Files folders.
5. Search files for suspect character strings. To conserve valuable time, be wise in the choice of words you search for, choosing confidential, sensitive, sex, or other explicit words and phrases related to your investigation.
6. Search the slack and free space for suspect character strings, as described previously.
![]()
The number of files stored on today’s hard drives can be large—literally hundreds of thousands of files. Obviously this is far too many for the investigator to directly analyze. However, by matching the message digests for files installed by the most popular software products to the message digests of files on the drive being analyzed, the investigator can avoid analyzing approximately 90 percent of the files because he can assume they are unmodified. The National Software Reference Library (NSRL) collects software from various sources and incorporates file profiles into a Reference Data Set available for download as a service. See www.nsrl.nist.gov.
![]()
The CAINE Computer Forensics Linux Live distro and SANS Investigative Forensic Toolkit (SIFT) are just two examples of the many tools you can use to perform computer forensic activities.

Tech Tip
Cleanup: Possible Remediation Actions After an Attack
Here’s a list of things you’ll need to do to restore your system after you’ve responded to an incident and completed your initial investigation:
![]() Place the system behind a firewall.
Place the system behind a firewall.
![]() Reload the OS.
Reload the OS.
![]() Run scanners.
Run scanners.
![]() Install security software.
Install security software.
![]() Remove unneeded services and applications.
Remove unneeded services and applications.
![]() Apply patches.
Apply patches.
![]() Restore the system from backup.
Restore the system from backup.
Timelines of Sequence of Events
Digital forensic investigations begin with a scope—a charge of what is of interest and should be investigated. In a modern computer environment, asking for everything that happened is a scope that is impossible to fulfill, because just booting up a machine can result in hundreds of events, in literally seconds. Once a scope is defined, it inevitably includes a time element, typically something in the order of “between a beginning date and time and an ending date and time, for user XYZ, examine with respect to (insert what is interesting here—keywords, specific types of actions, and so on).” With this information as the boundaries, it is common to produce a timeline of specific events that fall within the scope and time boundaries. This timeline will have the specifics, including the metadata to document it, demonstrating the sequence of events as recorded by the computer. The sequence can be very important because it provides key clues as to what actually happened, even when there is not a direct artifact. For instance, if the first time a USB drive was attached to a system, as recorded metadata in the registry, is after the time a file was last touched, then that file is probably not being transported on the USB with a later time of use. User logins and logoffs also help determine sequencing and operations. If a user is accused of performing a certain transaction on a network resource at a specific time and date, but their PC shows they were not logged in, then either they used another machine or something else is happening, such as the account is being hijacked. Building a timeline of activities from multiple perspectives can provide a lot of useful information as to what did happen, what could happen, and what makes no sense (because more data is needed).
Provenance
Provenance is a reference to the origin of data. In the case of digital forensics, it is not enough to present a specific data element as “proof”; one must also show where it came from. Provenance is specific, as in where on a file structure and where on a device, and in most cases there will be multiple representations, as in where the file resides in the file structure with respect to the OS (logical) and its location on a physical drive in sectors (physical). Provenance involves metadata, which can include timestamps, access control information, and a host of other data that can assist in determining which user performed which action at what time with respect to the object. In most cases, there is not a single location for this evidence; like the timeline, it must be constructed from several different artifacts.
Recovery
In a digital forensics sense, recovery is associated with determining the relevant information for the issue at hand. As presented in the earlier example, suppose a sales manager quits and goes to work for a competitor. Since the employee had access to sensitive information that would benefit the new employer, does this change the situation or raise questions? What would you be specifically looking for in the analysis? Analysis works by examining hypotheses, which are specific statements that can be disproved. In other words, what data provides information pertinent to the case at hand? Since forensics software has yet to invent a Find Evidence button, the act of determining what to analyze to demonstrate a hypothesis can be be a significant challenge. If the question is, did person X move a specific file to an external drive, then if your analysis shows the evidence that this movement occurred, hypothesis proven. If not, you can’t say it didn’t happen, only that there is no evidence to support the statement.
Asking a forensic investigator to tell you everything that happened on a 1TB drive is asking for the impossible. The number of events, files, and processes that occur as a normal part of computing leads to thousands of events for every logon/logoff cycle. Finding a specific activity is not like looking for a needle in a haystack; it is like looking for a needle in all the fields of Kansas. However, there are ways to trim down the work, such as creating timelines to indicate when the suspected activity happened, using keywords to see what strings of information make a record relevant, and looking for specific activities. When you can specify specific activities and those activities have logs associated with their occurrence, you can begin to build a solid data set.
This leads to the idea of active logging. Ideally, you want to minimize logging so when you have to use logs, the event you are interested in stands out without being hidden in a sea of irrelevant log items. Before the problem occurs, if the company sets up logging for specific events in the preparation phase, such as copying sensitive files, then later if questions arise as to whether the event happened or not, a log file exists to provide the information. Active logging is covered in more detail later in the chapter.
Strategic Intelligence/Counterintelligence Gathering
Strategic intelligence is the use of all resources to make determinations. This can make a large difference in whether a firm is prepared for threats. The same idea fits into digital forensics. Strategic intelligence can provide information that limits the scope of an investigation to a manageable level. If you have an idea of specific acts you want to have demonstrable evidence of either happening or not happening, you can build a strategic intelligence data set on the information. Where is it, what is it, and what is allowed/not allowed? These are all pieces of information that, when arranged and analyzed, can lead to a data logging plan to help support forensic event capture. What about things such as adding and removing data wiping programs? The list is long, but just like strategic threat intelligence, it is manageable, and when worked on in concert with other firms and professionals, a meaningful plan can emerge.
Counterintelligence gathering is the act of gathering information specifically targeting the strategic intelligence effort of another entity. Knowing what people are looking at and what information they are obtaining can provide information into their motives and potential future actions.
Active Logging
When you have an idea of what information you will want to examine, you can make an active logging plan that ensures the information is logged when it occurs and, if at all possible, is logged in a location that prevents alteration. Active logging is determined during the preparation phase, and when it comes time for recovery, the advance planning pays off in the production of evidence.
Track Man-Hours
Demonstrating the efforts and tasks performed in the forensics process may become an issue in court and other proceedings. Having the ability to demonstrate who did what, when they did it, and how long it took can establish that the steps were taken per the processes employed. Having solid accounting data on man-hours and other expenses can provide corroborating evidence as to the actions performed.
Reports
Reports are the official description of the forensic data. Reports can have a variety of elements—from pure descriptive information, such as machine/device identifiers (make, model and serial number), to information on the data, including size and hash values. Reports can also have specific elements that are derived from this information, such as a timeline, an analysis of keywords, specific artifacts, and present or missing items. An expert can opine on what these elements mean or can mean with respect to the system. For instance, if timestamps are significantly different, the expert may note that the difference exists. From a professional perspective, it is important for the forensics investigator to stick to just what the information can show and not add any commentary. For example, if the timestamp data has been tampered with, this is a provable fact, but then opining on who did it is more speculation and may result in the expert being called out on this in court. Experts who stray from the provable can be reprimanded by the judge, and being stricken from a case is a black mark that will call into question one’s opinions both now and in the future. As such, reports tend to be very sanitized, and the lawyers add color to the case later.
 Host Forensics
Host Forensics
Host forensics refers to the analysis of a specific system. Host forensics includes a wide range of elements, such as the analysis of filesystems and artifacts of the operating system. These elements often are specific to individual systems and operating systems, such as Linux or Windows.
Filesystems
When a user deletes a file, the file is not actually deleted. Instead, a pointer in a file allocation table is deleted. This pointer was used by the operating system to track down the file when it was referenced, and the act of “deleting” the file merely removes the pointer and marks the cluster (or clusters) holding the file as available for the operating system to use. The actual data originally stored on the disk remains on the disk (until that space is used again); it just isn’t recognized as a coherent file by the operating system.
Partitions
Physical memory storage devices can be divided into a series of containers; each of these containers is called a partition. A partition is a logical storage unit that is subsequently used by an operating system. Systems can have multiple partitions for a wide variety of reasons, ranging from hosting multiple operating systems to performance-maximizing efforts to protection efforts. The broad issue of partition operation and management is outside the scope of this chapter, but this is a critical topic to understand and examine when looking at a system forensically.
Free Space
Since a deleted file is not actually completely erased or overwritten, it sits on the hard disk until the operating system needs to use that space for another file or application. Sometimes the second file that is saved in the same area does not occupy as many clusters as the first file, so a fragment of the original file is left over.
The cluster that holds the fragment of the original file is referred to as free space because the operating system has marked it as usable when needed. As soon as the operating system stores something else in this cluster, it is considered allocated. The unallocated clusters still contain the original data until the operating system overwrites them. Looking at the free space might reveal information left over from files the user thought were deleted from the drive.
Slack Space
Another place that should be reviewed is slack space, which is different from free space. When a file is saved to a hard drive or other storage medium, the operating system allocates space in blocks of a predefined size, called clusters. Even if your file contains only ten characters, the operating system will allocate a full cluster—with space left over in the cluster. This is slack space.
It is possible for a user to hide malicious code, tools, or clues in slack space, as well as in the free space. You may also find information in slack space from files that previously occupied that same cluster. Therefore, an investigator should review slack space using utilities that can display the information stored in these areas.
Hidden Files
There are numerous ways to hide data on a system. One method is to hide files by setting the hidden attribute, which limits the listing of them by standard file utilities. Devised so that system files that should not be directly manipulated are hidden from easy view, this concept raises a broader question with respect to forensics: how can a user hide information from easy accessibility?
There is a wide range of methods for hiding files, and any attempt to list them would be long and subject to continual change. The major ones typically encountered include changing a file extension, encryption, streams, and storage on other partitions. You already learned about partitions—it is obvious that a forensic investigation should find, enumerate, and explore all partitions. Streams will be covered in the next section. Encrypted data, by its very nature, is hidden from view. Without the key, modern encryption methods resist any brute force attempts to determine the contents. It is important to find encrypted data stores and document the locations for later use by legal counsel.
Changing a file’s extension does not actually alter the contents or usability of a file. It merely breaks the automated runtime association manager that determines what executable is associated with the file type to properly handle it. The challenge of how to handle file types goes back to the early days of computers, when the magic number method was created. The term magic number describes a series of digits near the beginning of the file that provides information about the file format. In some cases, the magic number can be read by humans; for example, GIF87a or GIF89a indicates both Graphics Interchange Format (GIF) and the specification. Other file types are less obvious, such as a Tagged Image File Format (TIFF) file on an Intel platform, which is II followed by 42 as a 2-byte integer (49 49 2A 00).
Most integrated forensic tool suites handle file identification via magic number and are thus able to find hidden videos, pictures, and other items. The other thing these tools can do is complete searches across the entire storage structure for strings, and this can find many “hidden” items.
Streams
Streams is a short name for alternate data streams, a specific data structure associated with NTFS in Windows. The normal location for data in an NTFS-based system is in the data stream, a location identified by a record in the master file table (MFT) called $DATA:, which is technically an unnamed data stream. Alternate data streams have names and are identified by $DATA:StreamName, where StreamName is the name of the stream being used. Streams can be used to hide information; although the information is still present, most of the normal file utilities do not deal with streams, so it will not be seen. Forensic tool suites have tools that can search for, report on, and analyze stream data on Windows systems.
Artifacts
Artifacts are the key element in modern digital forensics. Most of the items used to demonstrate a specific action as occurring fall into one of two categories: metadata or OS artifact. Metadata examples include items like registry entries, timestamps, and sizes. OS artifacts include things like prefetch files, jump list artifacts such as most frequently used (MFU) and most recently used (MRU), shellbags, link files, and more. The metadata artifacts are items that the OS uses to perform its duties, while most of the OS artifacts are related to improving performance. Keeping a cache of links to most recently used files will speed up activity if the user returns to previous work, a common task. Also, deletion of the work (a file) does not delete the associated artifacts. Hence, artifacts can live on after a file is gone, leaving proof that the file existed.
![]()
Artifacts are the principal data element used in forensics. They are connected to how the computer manages data to perform a task. Understanding the artifacts of a particular system is important in the digital forensics process.
Swap/Pagefile
The swap or pagefile is a structure on a system’s disk to provide temporary storage for memory needs that exceed a system’s RAM capacity. The operating system has provisions to manage the RAM and pagefile, keeping in RAM what is immediately needed and moving excess to the pagefile when RAM is full. This causes a performance hit, and with the reasonable cost of RAM, most systems avoid this with sufficient RAM. Capturing the pagefile in a forensics investigation is important any time the RAM is captured, as it is an extension of the RAM.
Firmware
Firmware is a set of software that is associated with a physical device. Firmware exists for almost every electronic device, not just computers. It can even be found in things like USB devices. Firmware can be of interest in a forensics investigation when the malfunctioning of a device is an issue, as malware has targeted firmware. As such, it takes a very specialized set of tools and equipment to analyze, as firmware is not readily accessible to outside users.
Snapshot
A snapshot is a picture of a particular moment in time. Snapshots are common in virtual machines, providing a point in time to which the machine can be recovered to. Operating systems also have adopted this technology for some of their information: a point-in-time recovery point to assist in fixing problems from updates or changes to the system. These captures of points in time can be useful to a forensic investigator, as they allow a means of looking at specific content at an earlier point of time. The scope of what is covered by a snapshot can vary between different systems, and this may limit usefulness.
Cache
Caches are temporary storage locations used for commonly used items, designed to speed up processing. Caches exist all over in computer systems and are performance-enhancing items. Caches exist for files, for memory, and for artifacts; they exist for fast retrieval of items that the OS expects. As such, they are inherently relevant to something that has been done and is likely to be done again, and they can serve as evidence of things that have been done.
Windows Metadata
Microsoft Windows–based systems have a wide range of artifacts with forensic value. Before examining some of these artifacts, it is important to understand why they exist. The vast majority of artifacts exist for the purpose of improving the user experience. Tracking what users do and have done and making that information available to the operating system to improve future use is one of the primary reasons for the information; its forensic value is secondary.
Registry Analysis
The first and foremost Windows artifact is the system Registry, which acts a database repository of a whole host of information and provides a one-stop shop for a wide range of Windows forensic artifacts—what applications have been installed, user activity, activity associated with external devices, and more. Although the specific artifacts needed in an investigation differ based on the scope of the investigation, it is safe to assume that metadata recorded by the Windows operating system will serve a useful purpose in the investigation, especially since the Registry is stored by user and therefore the activity recorded in the Registry is attributable to a user.
The list of artifacts stored by the Registry is extremely long, but one of the major types is the event logs of a wide range of system and security information. There is also a wide range of file activity artifacts that can be analyzed, including analysis of shellbags, which provides evidence of folder opening. LNK files and most recently used (MRU) elements can point to filesystem activity. A wide range of date/time stamps on files, even deleted files, can be present for examination. There are specific toolsets designed to forensically explore the Registry and retrieve the desired artifacts from this voluminous store.

Tech Tip
Windows USB Analysis
Windows records a wide array of information on each USB device used in the system, including the following:
![]() Vendor/make/version and possibly unique serial number
Vendor/make/version and possibly unique serial number
![]() Volume name and serial number
Volume name and serial number
![]() Last drive letter assigned
Last drive letter assigned
![]() MountPoints2, a registry entry that stores the last drive mapping per user
MountPoints2, a registry entry that stores the last drive mapping per user
![]() Username of the user who used the USB device
Username of the user who used the USB device
![]() Time of first USB device connection
Time of first USB device connection
![]() Time of last USB device connection
Time of last USB device connection
![]() Time of last USB device removal
Time of last USB device removal
As mentioned before and will be mentioned again, Windows forensic analysis is no different from any other forensic analysis with respect to forensic procedures. Skill and proficiency in forensic procedures is the most important issue when analyzing a system because damage may make the use of the information impossible.
Linux Metadata
Linux systems have their own sets of artifacts. From a forensics perspective, Linux systems differ from Windows systems in these three main ways:
![]() No registry Program data is stored in scattered locations.
No registry Program data is stored in scattered locations.
![]() Different filesystem A multitude of different filesystems are used, each with different attributes.
Different filesystem A multitude of different filesystems are used, each with different attributes.
![]() Plaintext abounds Files and data tend to be in plaintext, which impacts searching.
Plaintext abounds Files and data tend to be in plaintext, which impacts searching.
The lack of a registry to hold system and program information does not mean that the information is not there; it just means that it is distributed. The same is true of filesystems. Rather than offering only two filesystem structures (NTFS and FAT), Linux comes with a whole host of different forms. Each of these has quirks, such as no file creation dates in many of them and the zeroing of metadata when files are deleted, thus resulting in forensic challenges.
When it comes to performing forensics on a Linux system, the value of a good sysadmin cannot be understated. Many of the artifacts of activity on a Linux system are scattered to various local locations, and a good sysadmin can assist in locating and recovering the essential elements for analysis. This is not a license for a sysadmin to begin performing forensic activities, however. The same rules and procedural requirements listed earlier still apply, and in most cases these necessitate the use of forensically trained professionals.
Timestamps
Timestamps are specific metadata entries used as artifacts in a computer system investigation. While a log entry may have one, some items can have multiple timestamps, stored in multiple locations. In NTFS, there are three common file times (Creation, Modification, and Accessed) and one metadata time (MFT Change). These four timestamps are stored in two places: one with the $File_Name attribute, and one with $Standard_Info. And if that isn’t enough confusion, the two different attributes are updated differently, meaning they may differ. This is important to forensic investigations because timestamps can be changed on systems, and this can lead to erroneous conclusions. Tampering with timestamps is challenging given that most tools do not handle all timestamps in the same way, which can lead to evidence of tampering.
Time is measured differently in Linux and Windows. Linux uses the concept of Epoch time—the number of seconds that have elapsed since January 1, 1970 (midnight UTC/GMT), not counting leap seconds. It is stored as a signed 32-bit number, enabling times before January 1, 1970, as well as after. The system clock has a resolution of a second, although there are timer elements that allow down to nanosecond timing measurements. Microsoft Windows uses a 64-bit value that represents the elapsed time since 12:00 A.M. January 1, 1601 Coordinated Universal Time (UTC), with a resolution of 100-nanosecond intervals. Note that both systems use UTC as a base, and most storage of time elements is done in UTC, with conversions to local time happening upon reading a value.
One of the challenges for all timestamp usage is inconsistency in the OS in keeping values up to date. While Microsoft Windows has a plethora of different timestamps to look at, there is great inconsistency on many of these values being updated by the OS or an application. The primary reason for this revolves around performance, as most timestamps are mere artifacts and are not important in many standard OS functions. Not maintaining the timestamps, or not maintaining all copies of timestamps, can improve the performance of some operations.
 Device Forensics
Device Forensics
Device forensics is the application of digital forensic principles to devices—mobile phones, tablets, the endless list of devices that comprise the “Internet of Things,” and more. The fact that it is a device does not change the principles pertaining to collecting and handling evidence. All of the forensic principles still apply and are just as important. What does change are the tools and processes employed to retrieve and analyze the data. This is because the filesystems, data structures, operating systems, and artifacts are different from those in the world of servers and PCs.

Tech Tip
SSD Forensics
The advent of solid state drives brings substantial improvements in performance. It also brings new issues with respect to forensics. Because of the way the solid state drives work, they are “leveled” periodically to maintain wear across the memory. This results in data being rewritten, and elements that are no longer valid are lost. Thus, a lot of the “standard” artifacts that would be found in a magnetic memory system are not preserved in solid state drives. As these drives are becoming common in systems, forensic analysts have to take all of these technical issues into consideration when attempting to reconstruct what happened.
 Network Forensics
Network Forensics
Network forensics consists of capturing, recording, and analyzing network events to discover the source of network problems or security incidents. Examining networks in a forensic fashion introduces several challenges. First is scale. The scale of a network is related to the number of nodes and the speed of traffic. Second is the issue of volume. Packet capture is not technically difficult, but it can necessitate large quantities of storage. And although storage is relatively cheap, large numbers of packets can be difficult to sort through and analyze. Because of these issues, network forensics becomes an issue of specificity; if you know what target and what protocols you are looking for, you can selectively capture and analyze the traffic for those segments and have data that is useful. But therein lies the other challenge. Network data is temporal. It exists while the packet is in transit, and then it is gone, forever. Metadata such as NetFlow data can provide some information, but it does not contain any content of the data being transmitted.
As a general-purpose tool, network forensics is nearly impossible because of the scale issues. But in specific situations, such as in front of high-value targets that have limited data movement, it can prove to be valuable. It can also be valuable in troubleshooting ongoing incidents and problems in the network.
The same rules apply to network forensics as apply to all other forensic collection efforts. Preserving the integrity of the data is paramount, and maintaining control over the data is always a challenge. Forensic rules (admissibility, chain of custody, and so on) do not change because the source of data has changed.
 Legal Hold
Legal Hold
In the U.S. legal system, legal precedent requires that potentially relevant information must be preserved at the instant a party “reasonably anticipates” litigation or another type of formal dispute. Although this sounds technical, it is fairly simple: once you realize you need to preserve evidence, you must use a legal hold, or litigation hold, process by which you properly preserve any and all digital evidence related to a potential case. This event is usually triggered by one firm issuing a litigation hold request to another. Once this notice is received, the receiving firm is required to maintain in complete, unaltered form (both in data and metadata) any and all information related to the issue at hand. This means that ordinary data retention policies no longer are in effect and that even alterations to metadata can be considered to be a violation of the hold request, and if the court believes this can materially affect the ability of a jury to make a decision, the jury can be instructed to consider the act as hiding evidence. Major awards have been decided based on failure to retain information.
Where does this information reside? It resides everywhere, including e-mail, office documents, network shares, mobile phones, tablets, and databases. Just think of everywhere the information is shared; all copies need to be produced unaltered, often years after the document was created. Finding and managing all of this information falls under a topic called e-discovery, which is a branch of digital forensics dealing with identifying, managing, and preserving digital information that is subject to legal hold.

Understanding the consequences of legal hold on record retention is important, and legal holds supersede any standard corporate policy or procedure.
E-discovery
Electronic discovery, or e-discovery, is the term used for the document and data production requirements as part of legal discovery in civil litigation. When a civil lawsuit is filed, under court approval, a firm can be compelled to turn over specific data from systems pursuant to the legal issue at hand. Electronic information is considered to be the same as paper documents in some respects and completely different in others. The evidentiary value can be identical. The fragility can be substantial—electronic records can be changed without leaving a trace. Electronic documents can also have metadata associated with them, such as who edited the document, previous version information, and more.
One of the pressing challenges in today’s enterprise record store is the maintenance of the volumes of electronic information. Keeping track of the information stores based on a wide range of search terms is essential to comply with e-discovery requests. It is common for systems to use forensic processes and tools to perform e-discovery searches.
Reference Model
EDRM, a coalition of consumers and providers focused on improving e-discovery and information governance, has created a reference model for e-discovery. The Electronic Discovery Reference Model, shown in Figure 23.4, provides a framework for organizations to prepare for e-discovery. The major steps of the framework are thoroughly described on the EDRM website (http://edrm.net). Additional resources available from EDRM include XML schemas, glossaries, metrics, and more.

• Figure 23.4 Electronic Discovery Reference Model (courtesy of EDRM, EDRM.net)
Big Data
It may seem that big data is all the rage in business today, but in reality it is simply a description of the times. We have created large data stores in most enterprises as a byproduct of cheap storage and the ubiquity of the Internet. Big data is an issue in e-discovery as well. The cataloging, storage, and maintenance of corporate records often become big data issues. This facilitates the use of big data methods in many cases. This is an area of rapid development, both for forensics and for e-discovery, as data volumes continue to grow exponentially.
Cloud
The cloud has become a resource for enterprise IT systems, and as such it is intimately involved in both e-discovery and forensics. Having data that may or may not be directly accessed by the tools of e-discovery and forensics can complicate the needed processes. An additional complication is the legal issues associated with the contracts between the organization and the cloud provider. As both forensics and e-discovery are secondary processes from a business perspective, they may or may not be addressed in a standard cloud agreement. Because these processes can become important—and if they do, it may be too late to contractually address them—it behooves an organization to prepare by addressing them in cloud agreements with third parties. The topic of cloud computing is covered in detail in Chapter 18.
Right to Audit Clauses
Audits are the mechanism used to verify that systems are performing to their designed levels of purpose, security, and efficiency. The ability to audit involves access to a system and the data. When the information is stored or processed in the cloud, users need the ability to audit the cloud provider. The level and scope of the audit can vary given the dynamic natures of both the cloud and the regulatory environment, but one thing does not vary. The only rights the customer has are detailed in the service level agreements/contracts with the cloud provider. This makes the right to audit clause a critical requirement of any service level agreement, and its specificity needs to match the operational and regulatory scope of the cloud engagement.
Regulatory/Jurisdiction
Whether on premises or in the cloud, there will be cases where regulatory or law enforcement actions raise jurisdictional issues. If you have your software development data in the cloud, and the servers/storage elements are in a foreign country, whose laws will apply? It is important to consult with the company legal counsel to understand the ramifications of data location with respect to forensics and subsequent data use.
Chapter 23 Review
 Chapter Summary
Chapter Summary
After reading this chapter and completing the exercises, you should understand the following about incident response and forensics.
Explore the basics of digital forensics
![]() Digital forensics is the collection of processes and procedures used to prepare digital information for use in legal or administrative proceedings.
Digital forensics is the collection of processes and procedures used to prepare digital information for use in legal or administrative proceedings.
![]() Because of the importance of veracity and the fragility of digital data to integrity violations that cannot be detected, it is imperative that processes be complete and comprehensive.
Because of the importance of veracity and the fragility of digital data to integrity violations that cannot be detected, it is imperative that processes be complete and comprehensive.
Identify the rules and types of evidence
![]() Evidence must meet the three standards of being sufficient, competent, and relevant if it is to be used in legal proceedings.
Evidence must meet the three standards of being sufficient, competent, and relevant if it is to be used in legal proceedings.
![]() There are four different types of evidence: direct, real, documentary, and demonstrative.
There are four different types of evidence: direct, real, documentary, and demonstrative.
![]() There are three rules regarding evidence: the best evidence rule, the exclusionary rule, and the hearsay rule.
There are three rules regarding evidence: the best evidence rule, the exclusionary rule, and the hearsay rule.
Collect and preserve evidence
![]() Evidence must be properly collected, protected, and controlled to be of value during court or disciplinary activities.
Evidence must be properly collected, protected, and controlled to be of value during court or disciplinary activities.
![]() When acquiring evidence, one must be deliberate to ensure evidence is not damaged and operations are not negatively impacted.
When acquiring evidence, one must be deliberate to ensure evidence is not damaged and operations are not negatively impacted.
![]() Evidence must be properly marked so that it can be readily identified as that particular piece of evidence gathered at the scene.
Evidence must be properly marked so that it can be readily identified as that particular piece of evidence gathered at the scene.
![]() Evidence must be protected so that it is not tampered with, damaged, or compromised.
Evidence must be protected so that it is not tampered with, damaged, or compromised.
![]() Evidence should be transported cautiously to ensure custody of the evidence is maintained and the evidence itself is not tampered with or damaged.
Evidence should be transported cautiously to ensure custody of the evidence is maintained and the evidence itself is not tampered with or damaged.
![]() Evidence should be stored in properly controlled areas and conditions.
Evidence should be stored in properly controlled areas and conditions.
![]() When conducting an investigation on computer components, one must be deliberate and cautious to ensure evidence is not damaged.
When conducting an investigation on computer components, one must be deliberate and cautious to ensure evidence is not damaged.
Maintain a viable chain of custody
![]() A chain of custody that accounts for all persons who handled or have access to the evidence must be maintained to prevent evidence tampering or damage.
A chain of custody that accounts for all persons who handled or have access to the evidence must be maintained to prevent evidence tampering or damage.
Investigate a computer crime or policy violation
![]() Information can be recorded and possibly hidden in various ways on a computer. Sometimes information will be hidden in either the free space or the slack space of the computer’s disk drive.
Information can be recorded and possibly hidden in various ways on a computer. Sometimes information will be hidden in either the free space or the slack space of the computer’s disk drive.
![]() Free space is the space (clusters) on a storage medium that is available for the operating system to use.
Free space is the space (clusters) on a storage medium that is available for the operating system to use.
![]() Slack space is the unused space on a disk drive created when a file is smaller than the allocated unit of storage, such as a cluster.
Slack space is the unused space on a disk drive created when a file is smaller than the allocated unit of storage, such as a cluster.
![]() The use of a message digest or hashing algorithm is essential to ensure that information stored on a computer’s disk drives has not been changed.
The use of a message digest or hashing algorithm is essential to ensure that information stored on a computer’s disk drives has not been changed.
![]() If the information in the data stream or file is changed, a different message digest will result, indicating the file has been tampered with.
If the information in the data stream or file is changed, a different message digest will result, indicating the file has been tampered with.
![]() Forensic analysis of data stored on a hard drive can begin once the drive has been imaged and message digests of important files have been calculated and stored.
Forensic analysis of data stored on a hard drive can begin once the drive has been imaged and message digests of important files have been calculated and stored.
![]() Analysis typically involves investigating the Recycle Bin, web browser and address bar history files, cookie files, temporary Internet file folders, suspect files, and free space and slack space.
Analysis typically involves investigating the Recycle Bin, web browser and address bar history files, cookie files, temporary Internet file folders, suspect files, and free space and slack space.
![]() Experience and knowledge are your most valuable tools available when performing computer forensic activities.
Experience and knowledge are your most valuable tools available when performing computer forensic activities.
Examine system artifacts
![]() Different systems can have different artifacts based on the operating system and equipment employed.
Different systems can have different artifacts based on the operating system and equipment employed.
![]() Windows and Linux systems have many similar artifacts, although they are located in different areas and preserved in different ways.
Windows and Linux systems have many similar artifacts, although they are located in different areas and preserved in different ways.
Develop forensic policies and procedures
![]() The overarching principle for all digital forensic investigations is proper procedures. Any deviation from proper procedures can permanently alter evidence and render information unusable in follow-on procedures, whether criminal, civil, or administrative. Ensuring proper procedures by trained professionals is essential from the first aspect of an investigation.
The overarching principle for all digital forensic investigations is proper procedures. Any deviation from proper procedures can permanently alter evidence and render information unusable in follow-on procedures, whether criminal, civil, or administrative. Ensuring proper procedures by trained professionals is essential from the first aspect of an investigation.
Examine the policies and procedures associated with e-discovery
![]() E-discovery is the term used for the document and data production requirements as part of legal discovery in civil litigation.
E-discovery is the term used for the document and data production requirements as part of legal discovery in civil litigation.
![]() The Electronic Discovery Reference Model provides a framework for organizations to prepare for e-discovery.
The Electronic Discovery Reference Model provides a framework for organizations to prepare for e-discovery.
 Key Terms
Key Terms
active logging (893)
admissibility (882)
artifacts (896)
best evidence rule (879)
cache (897)
chain of custody (880)
checksums (887)
competent evidence (879)
counterintelligence gathering (893)
data recovery (882)
demonstrative evidence (878)
device forensics (899)
direct evidence (878)
documentary evidence (878)
e-discovery (900)
event logs (897)
evidence (877)
exclusionary rule (879)
firmware (896)
forensics (877)
free space (895)
hash (886)
hashing algorithm (886)
hearsay rule (879)
host forensics (894)
legal hold (900)
litigation hold (900)
magic number (895)
network forensics (899)
on-premises vs. cloud (902)
order of volatility (884)
partition (894)
preservation (888)
provenance (892)
real evidence (878)
record time offset (886)
relevant evidence (879)
reports (893)
right to audit clause (902)
slack space (895)
snapshot (897)
strategic intelligence (893)
stream (896)
sufficient evidence (879)
swap/pagefile (896)
tags (880)
timestamps (898)
write blocker (889)
 Key Terms Quiz
Key Terms Quiz
Use terms from the Key Terms list to complete the sentences that follow. Don’t use the same term more than once. Not all terms will be used.
1. Evidence collected in violation of the Fourth Amendment of the U.S. Constitution, the Electronic Communications Privacy Act (ECPA), or other aspects of the U.S. Code may not be admissible to a court under the terms of the _______________.
2. Evidence that is legally qualified and reliable is _______________.
3. Documents, verbal statements, and material objects admissible in a court of law are called _______________.
4. The rule whereby courts prefer original evidence rather than a copy to ensure that no alteration of the evidence (whether intentional or unintentional) has occurred is termed the _______________.
5. To understand time values relative to other systems in a network, one should _______________.
6. _______________ consists of the preservation, identification, documentation, and interpretation of computer data to be used in legal proceedings.
7. _______________ is evidence that is material to the case or has a bearing on the matter at hand.
8. _______________ is the unused space on a disk drive when a file is smaller than the allocated unit of storage.
9. _______________ is oral testimony or other evidence that proves a specific fact (such as an eyewitness’s statement, fingerprint, photo, and so on). The knowledge of the facts is obtained through the five senses of the witness. There are no inferences or presumptions.
10. _______________ consists of the remaining sectors of a previously allocated file that are available for the operating system to use.
 Multiple-Choice Quiz
Multiple-Choice Quiz
1. What is the order of collecting evidence at a scene?
A. Take a picture of the screen, RAM, copy USBs, copy hard disk, live network connections
B. RAM, live network connections, temporary swap space, data on hard disk(s)
C. Hard disk, RAM, any USBs
D. ARP cache, live network connections, RAM, hard disk
2. Which of the following correctly defines evidence as being relevant?
A. The evidence is material to the case or has a bearing on the matter at hand.
B. The evidence is presented in the form of business records, printouts, or other items.
C. The evidence is convincing or measures up without question.
D. The evidence is legally qualified and reliable.
3. Which of the following correctly defines documentary evidence?
A. The evidence is presented in the form of business records, printouts, manuals, and other items.
B. The knowledge of the facts is obtained through the five senses of the witness.
C. The evidence is used to aid the jury and may be in the form of a model, experiment, chart, or other item and be offered to prove an event occurred.
D. Physical evidence that links the suspect to the scene of a crime.
4. Which of the following correctly defines real evidence?
A. The evidence is convincing or measures up without question.
B. The evidence is material to the case or has a bearing on the matter at hand.
C. The evidence is used to aid the jury and may be in the form of a model, experiment, chart, or other item and be offered to prove an event occurred.
D. Tangible objects that prove or disprove a fact.
5. Which of the following is the least rigorous investigative method?
A. Using a dedicated forensic workstation
B. Verifying software on a suspect system and using that software for the investigation
C. Examining the suspect system using its software without verification
D. Booting the suspect system with a verified external OS kernel and tools
6. Which of the following correctly defines slack space?
A. The space on a disk drive that is occupied by the boot sector
B. The space located at the beginning of a partition
C. The remaining sectors of a previously allocated file that are available for the operating system to use
D. The unused space on a disk drive when a file is smaller than the allocated unit of storage
7. Which of the following correctly describes the minimum contents of an evidence control log book?
A. Description, Investigator, Case #, Date, Time, Location, Reason
B. Description, Investigator, Case #, Date, Location, Reason
C. Description, Case #, Date, Time, Location, Reason
D. Description, Coroner, Case #, Date, Time, Location, Reason
8. Which of the following correctly describes the chain of custody for evidence?
A. The evidence is convincing or measures up without question.
B. It accounts for all persons who handled or had access to a specific item of evidence.
C. Description, Investigator, Case #, Date, Time, Location, Reason.
D. The evidence is legally qualified and reliable.
9. Which of the following correctly defines the exclusionary rule?
A. Any evidence collected in violation of the Fourth Amendment is not admissible as evidence.
B. The evidence consists of tangible objects that prove or disprove a fact.
C. The knowledge of the facts is obtained through the five senses of the witness.
D. The evidence is used to aid the jury and may be in the form of a model, experiment, chart, or the like, offered to prove an event occurred.
10. Which of the following correctly defines free space?
A. The unused space on a disk drive when a file is smaller than the allocated unit of storage (such as a sector).
B. The space on a disk drive that is occupied by the boot sector.
C. The space located at the beginning of a partition.
D. The remaining sectors of a previously allocated file that are available for the operating system to use.
11. A judge has issued an order for all e-mail to be preserved, and that order is in effect. Which of the following statements is correct?
A. You can delete old e-mail after the standard retention period.
B. You should have legal determine which records must be saved.
C. You should continue archiving all e-mail.
D. You can delete the e-mail after making a copy to save for e-discovery.
12. You have been tasked with assisting in the forensic investigation of an incident relating to employee misconduct. The employee’s supervisor believes evidence of this misconduct can be found on the employee’s assigned workstation. Which of the following choices best describes what should be done?
A. Create a timeline of events related to the scope.
B. Copy the user profile to reduce the search space.
C. Sign in as the user and search through their recent efforts.
D. Examine log file entries under the user’s profile.
 Essay Quiz
Essay Quiz
1. A supervisor has brought to your office a confiscated computer that was allegedly used to view inappropriate material. He has asked you to look for evidence to support this allegation. Because you work for a small company, you do not have an extra computer you can dedicate to your analysis. How would you boot the system and begin forensic analysis? Provide a reason for your method.
2. Explain why you should always search the free space and slack space if you suspect a person has deliberately deleted files or information on a workstation that you are analyzing.
3. You have been asked by management to secure the laptop computer of an individual who was just dismissed from the company under unfavorable circumstances. Pretend that your own computer is the laptop that has been secured. Make the first entry in your log book and describe how you would start this incident off correctly by properly protecting and securing the evidence.
Lab Projects
• Lab Project 23.1
Use an MD5 or SHA-1 algorithm to obtain the hash value for a file of your choice. Record the hash value. Change the file with a word processor or text editor. Obtain the hash value for the modified file. Compare the results.
• Lab Project 23.2
To understand what information is stored on your computer, examine the contents of the Temporary Internet Files folders. Review the filenames and examine the contents of a few of the files. Describe how this information could be used as evidence of a crime.
