Understanding and Assessing the Impact of Legal and Compliance Issues on an Organization
An organization must know what laws and regulations apply to it because noncompliance can have serious consequences. Some laws assess hefty fines on an organization, some laws can result in jail time, and some laws can negatively affect an organization’s ability to do business. Once pertinent laws and regulations have been identified, the organization needs to ensure that it is in compliance.
In this context, compliance is a mitigation control. Controls are implemented to mitigate risk, which they do by reducing or neutralizing threats or vulnerabilities to an acceptable level.
For example, Health Insurance Portability and Accountability Act (HIPAA) fines can be as high as $25,000 a year for mistakes, and General Data Protection Regulation (GDPR) fines can be as high as $22 million or 4 percent of a business’s annual global turnover, whichever is greater. An internal compliance program can ensure that these costly mistakes don’t happen. When assessing the impact of compliance issues in an organization, two distinct steps need to be taken. The first step is to identify what compliance issues apply to the organization, and the second step is to assess the impact of these issues on the organization’s business operations. These two topics are presented in the following sections.
Corporate compliance has become so important in some organizations that they have created a new position, the chief compliance officer (CCO). Some companies use the title of chief ethics compliance officer (CECO) or ethics compliance officer (ECO).
Legal Requirements, Compliance Laws, Regulations, and Mandates
Although there are many laws and regulations that apply to IT, they don’t all apply to IT. Therefore, one of the important issues to understand first is which laws apply to an organization.
As a reminder, some of the key laws that apply to organizations are:
- Health Insurance Portability and Accountability Act (HIPAA, enacted 1996)
- Sarbanes-Oxley Act (SOX, enacted 2002)
- Federal Information Security Management Act (FISMA, enacted 2002)
- Federal Information Security Modernization Act (FISMA, enacted 2014)
- Family Educational Rights and Privacy Act (FERPA, enacted 1974)
- Children’s Internet Protection Act (CIPA, enacted 2000)
- Payment Card Industry Data Security Standard (PCI DSS, enacted 2004)
- Gramm-Leach-Bliley Act (GLBA, enacted 1999)
- General Data Protection Regulation (GDPR, enacted 2018)
The following sections identify how an organization can determine whether a law applies to it. Some laws are specific and narrow in scope, whereas others, such as HIPAA, apply to a wide range of organizations.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA applies to any organization that handles health information. The obvious organizations that handle health information are hospitals and doctor’s offices. However, HIPAA reaches much further than the medical industry.
Health information includes any data that relates to the health of an individual. This data includes a person’s past, present, and future health; condition, physical health, or mental health; and any past, present, or future payments for health care. If an organization creates or receives health information, it must comply with HIPAA, and this includes employers, health plan sponsors, health care providers, public health authorities, and more. If an organization isn’t involved in health care but does provide a health plan, it falls under HIPAA.
Sarbanes-Oxley Act (SOX)
SOX applies to any business that is required to be registered with the Securities and Exchange Commission, which include all publicly traded companies. In other words, if someone can buy stock in the company, then SOX applies.
SOX establishes a set of standards. Even if they don’t apply directly to private businesses, private businesses can use these same standards. If the organization faces legal issues later, it can point to its actions as good faith efforts to avoid the problems.
Federal Information Security Management Act (FISMA)
FISMA applies to all U.S. federal agencies. Its goal is to ensure that federal agencies take steps to protect their data.
The National Institute of Standards and Technology (NIST) is tasked by FISMA to develop standards, guidelines, and best practices to support FISMA. Special publications created by NIST for FISMA are available at http://csrc.nist.gov/publications/sp.
Family Educational Rights and Privacy Act (FERPA)
FERPA applies to all education institutions and agencies that receive funding under any program administered by the U.S. Department of Education (ED).
The obvious examples are any public schools from grades kindergarten through 12. However, many other entities can receive funding from the ED, which include any school or agency offering preschool programs, and any institution of higher education, such as colleges and universities.
Funding is often indirect. Although public grade schools receive their funding directly from the ED, other institutions receive their funding indirectly. The ED provides student aid and grants for college. If a student receives this funding and uses the money to pay for college, the college is receiving ED funding.
The ED updated FERPA in 2012. Amendments allow for greater disclosures of student personal information and student information in the school’s directory. They also regulate student IDs and email addresses.
Children’s Internet Protection Act (CIPA)
CIPA applies to any school or library that receives funding from the U.S. E-Rate program, which is sponsored by the Federal Communications Commission (FCC). It provides discounts for Internet access.
Schools and libraries are not required to use the E-Rate program, but, if they choose to take advantage of the discounts, schools and libraries are governed by CIPA. The annual E-Rate application requires schools and libraries to certify that they are complying with CIPA.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is not a law. Instead, it is a standard that was jointly created by several credit card companies and is overseen by the Payment Card Industry (PCI) Security Standards Council. Any organization that accepts credit card payments must comply.
Many credit card companies support PCI DSS. They include Visa International, MasterCard Worldwide, American Express, Discover Financial Services, and JCB International. The PCI Security Standards Council includes employees of these companies.
Smaller companies can certify that they are compliant by completing a self-assessment questionnaire, and large organizations are independently audited by a qualified security assessor.
The PCI Security Standards Council released PCI DSS v3.2 in May 2018.
 TIP
TIP
PCI compliance and PCI DSS compliance mean the same thing.
General Data Protection Regulation (GDPR)
The GDPR is a European Union regulation regarding data and privacy protection. The law addresses the transfer of personal information of EU and European Economic Area (EEA) residents outside their region. The law seeks to give control to individuals of this region over their own personal data and information, especially as it pertains to international organizations trading outside of the EU and EEA. The law applies to any business, regardless of its location and the citizenship of the data subject.
The law differentiates a data controller from a data processor. The data controller is the business or individual who determines the purpose of the personal data that is collected and how it is processed. The processor, on the other hand, is the business or individual who acts on behalf of the controller, excluding the controller’s employees. The law is supported by a number of privacy protection principles. The GDPR is the major reason for all websites asking permission to use cookies, which allow them to track a visit.
Assessing the Impact of Legal and Compliance Issues on an Organization’s Business Operations
Once the compliance requirements for an organization have been determined, the next step is to determine the impact that these requirements have on the organization. The impact can be significantly different depending on the law or standard being applied.
The following sections present potential impacts for some of the common laws and standards.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA affects a wide spectrum of a business, and the cost of noncompliance is high. The steps required to comply can be complex, depending on how much health-related information an organization handles.
First, the penalties are severe if the rules aren’t being followed. Organizations can be fined $100 per violation and up to $25,000 per year for mistakes. If someone knowingly obtains or releases data he or she shouldn’t, the penalties can be as high as $50,000 and one year in prison. If data is obtained or disclosed under false pretenses, penalties can be as high as $100,000 and five years in prison. If data is obtained or disclosed for personal gain or malicious harm, penalties can be as high as $250,000 and 10 years in prison.
However, compliance can also be expensive. Organizations that handle health data must take specific steps to protect it, which include protecting any data that they create, receive, or send and protecting any of the systems that handle health data.
The responsibility to keep the data secure rests with the organization. The data must be protected while at rest, which means that, if it is stored on a hard drive or in a filing cabinet, it must be protected. Protecting data at rest can be done through access controls or physical security, depending on the type of data.
Use of health information is restricted. Employees who handle and review health information must be trained so they know the requirements. As an example, data cannot be released to a third party without the written consent of the patient.
Data must also be protected when transmitted. When any health data is transmitted, it must be transmitted in a specific format. The good news is that health plan providers are well versed in HIPAA. A company that outsources a health plan can also outsource handling of the health data. For example, a health plan provider can be contracted to provide insurance to employees, and employees can then be directed to the health plan provider’s website to enroll. When a health plan is managed in this manner, the provider hosts almost all the information. The originating company has very little data, and its risks are limited.
Sarbanes-Oxley Act (SOX)
The business impact of SOX is a high liability for the accuracy of data. High-level officers, such as CEOs and chief financial officers (CFOs), must personally verify and attest to the accuracy of financial data. The goal is to avoid mega scandals, such as the loss of $11 billion by Enron’s investors.
Because of this high liability, organizations are required to take extra steps to ensure the accuracy and integrity of the data, which includes implementing internal controls and requiring both internal and external audits to verify compliance. Two key benefits are that SOX increased executives’ accountability to act in their shareholders’ interest and its required monitoring helped provide better control of internal costs.
Some opponents of SOX have argued that the costs of compliance are excessive. However, the costs for most organizations are manageable according to a 2013 survey by Protiviti.
Federal Information Security Management Act (FISMA)
Because FISMA applies only to federal agencies, it does not affect the revenue of any organization. However, it can have a significant effect on operations.
A core requirement of FISMA is to identify, certify as compliant, and authorize for operation all IT systems in the organization, a process that can be lengthy. One of the primary problems is the slow implementation of new systems.
FISMA encourages the use of baselines. As long as a system follows the same baseline as another system, it can be certified and authorized quickly.
 NOTE
NOTE
A baseline is any known starting point. A baseline for an IT system represents the same hardware, software, and configuration as another system’s. For example, if one server has been authorized using a baseline, another server can be authorized much more quickly by using the same baseline.
Family Educational Rights and Privacy Act (FERPA)
FERPA requires covered organizations to share student records with students or their parents. If a student or a parent makes the request, the school must comply.
Students or parents can request the correction of errors in the student’s record, and the school has an obligation to consider the request. However, the school isn’t required to make all the changes a student asks for. For example, if a student requests a poor grade to be removed from a record but the grade is accurate, the school isn’t required to remove it.
Students can grant access to their record to specific third parties. For example, a student may grant access when applying for admission to a college or university. Some specific third parties are automatically granted access to the records. Many school officials, for instance, do not need student permission to view the record.
The biggest impact FERPA has on business operations is ensuring that employees know the rules, which can be done with training. If a student under 18 requests access to his or her record, the employee should know the right belongs to the parent. If a parent of a 20-year-old requests access, the employee should know the right belongs to the student. Similarly, if a third party requests access, the employee should know whether access should be granted.
 TIP
TIP
FERPA grants specific rights to parents of students under 18. However, when the student turns 18, these rights transfer to the student, and the parents no longer have rights to the information without the student’s knowledge and consent.
Children’s Internet Protection Act (CIPA)
CIPA imposes several technical requirements on schools and libraries. They must be able to filter offensive content to ensure that minors aren’t exposed to it. If the school or library cannot comply with CIPA, it risks losing all E-Rate discounts.
E-Rate funding provides discounts to schools and libraries for Internet access. Any school or library that requests discounts under the E-Rate program is required to certify that it complies with CIPA rules.
The first challenge in complying with CIPA is identifying offensive content. CIPA allows the school or library to define offensive using local standards, which means that what is deemed offensive content in a library in one area of the country may be acceptable in a library in another area of the country.
Schools and libraries filter the content with a technology protection measure (TPM). FIGURE 10-5 shows an example of a proxy server used as a TPM. A proxy server receives requests from clients for webpages, retrieves the webpages, and then serves the webpages to the clients. It can also filter the requests to block content requests.
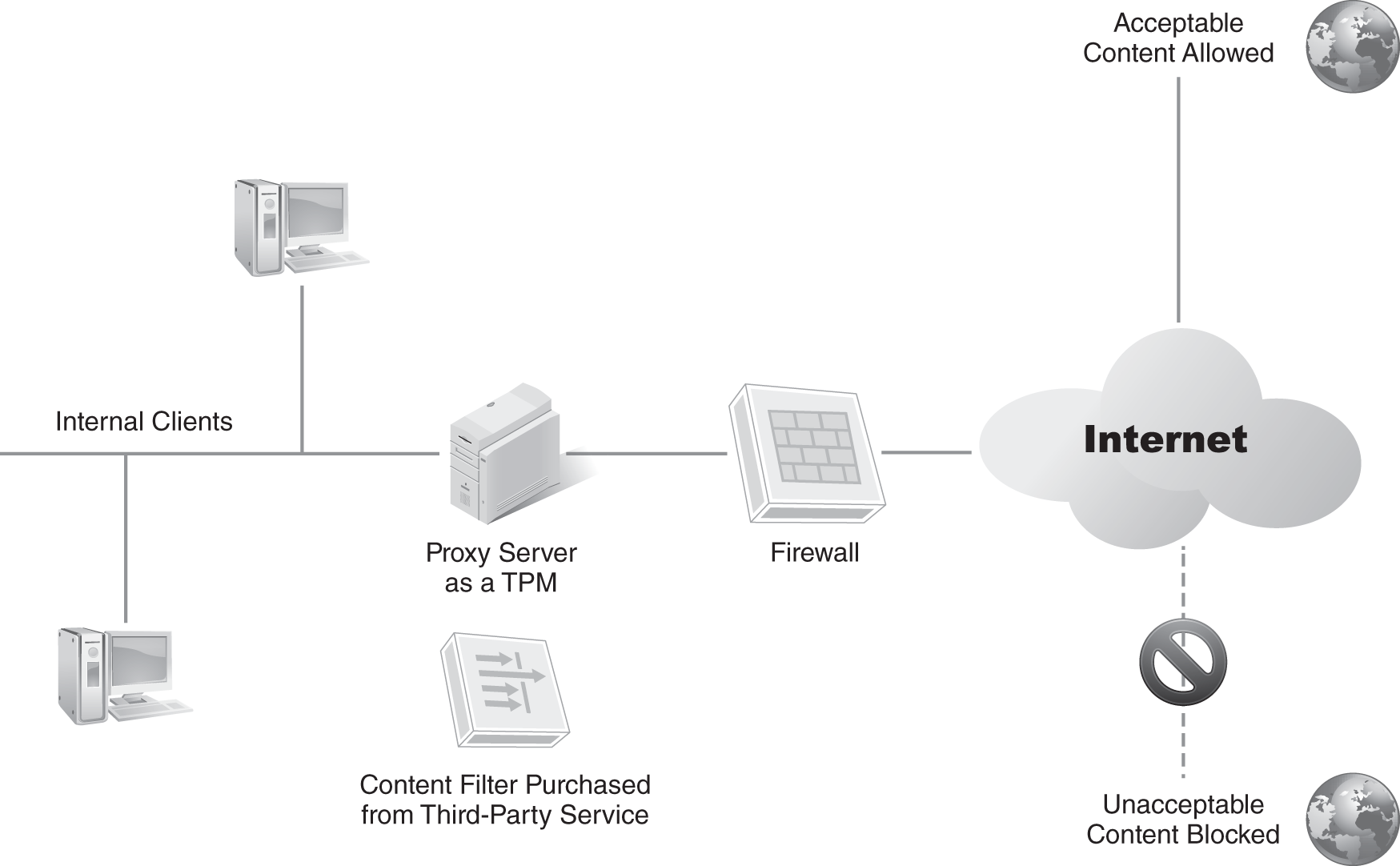
FIGURE 10-5 Proxy server used as a TPM.
Users are able to access the Internet through the proxy server. All content requests are filtered using the content filter. If the content is acceptable, the page is retrieved and sent to the client. If the content is unacceptable, the content is blocked.
A proxy server commonly works with data provided by a third-party service, which provides a list of content to filter. The list is often in the format of specific website Uniform Resource Locators, or URLs. The proxy server uses this list to prevent the content from reaching the requesting computer.
CIPA defines a minor as anyone under the age of 17. Their access should be restricted by the TPM. However, anyone 17 years old or over should be able to use the computer without restrictions. For example, if an adult wants to use it, he or she can request that the TPM filter be removed. An administrator or librarian should be able to remove the filter in a timely manner.
General Data Protection Regulation (GDPR)
The GDPR requires data controllers and processors to put appropriate technical and organizational measures in place to protect the privacy of EU/EEA citizens. The GDPR is built around the following principles:
- Principles relating to the processing of personal data
- Lawfulness of processing
- Conditions of consent
- Conditions applicable to a child’s consent in relation to information society services
- Processing of special categories of personal data
- Processing of personal data relating to criminal convictions and offenses
- Processing that does not require identification
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is built around the following six principles and 12 requirements:
- Build and Maintain a Secure Network
- Requirement 1: Install and maintain a firewall.
- Requirement 2: Do not use defaults, such as default passwords.
- Protect Cardholder Data
- Requirement 3: Protect stored data.
- Requirement 4: Encrypt transmissions.
- Maintain a Vulnerability Management Program
- Requirement 5: Use and update antivirus software.
- Requirement 6: Develop and maintain secure systems.
- Implement Strong Access Control Measures
- Requirement 7: Restrict access to data.
- Requirement 8: Use unique logons for each user. Don’t share usernames and passwords.
- Requirement 9: Restrict physical access.
- Regularly Monitor and Test Networks
- Requirement 10: Track and monitor all access to systems and data.
- Requirement 11: Regularly test security.
- Maintain an Information Security Policy
- Requirement 12: Maintain a security policy.
All of the principles and requirements are IT related, but they also reflect many common best practices. If an organization is already using best practices, PCI DSS won’t have much effect on its business operations. However, if an organization is not currently using common security practices, PCI DSS compliance may affect its budget and operations.
