Compliance Law Requirements and Business Drivers
Users typically access information from workstations. This is not always the case, especially as organizations are increasingly using mobile devices such as smartphones and tablets. But workstations are still the most common way for corporate users to view and modify your organization’s information. Because workstations provide access to information, they become an attack vector for unauthorized users. It is important that you ensure all items in the Workstation Domain are compliant. Figure 9-1 shows the Workstation Domain in the context of the seven domains in the IT infrastructure.
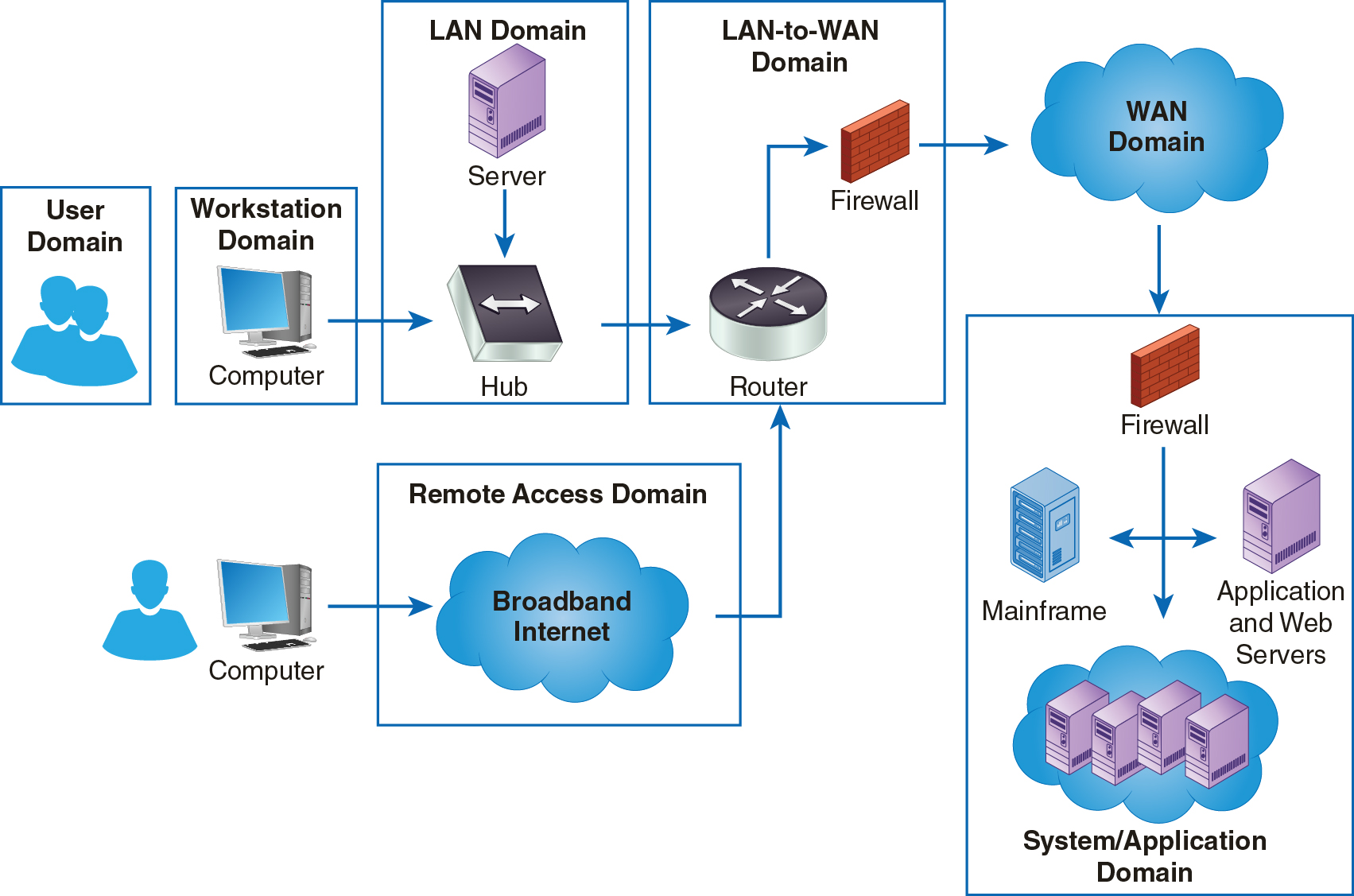
FIGURE 9-1 The Workstation Domain Within the Seven Domains of a Typical IT Infrastructure
The Workstation Domain defines the controls within the workstation itself, such as limiting who can install software on the workstation. It’s not uncommon that workstations are shared by multiple end users. Workstation settings must be stable, and one end user cannot impact another. To achieve this, the end user often has limited rights on a workstation. Meaning, they can typically access the software that has been installed, have some rights to configure the software to their needs, but do not have unlimited rights to make any change that could impact another user. This also ensures that an end user does not inadvertently infect the workstation with a virus or malware. For example, in Microsoft Windows operating systems, two common accounts are encountered: standard user account and administrator account.
As the name implies, the standard user account allows the user to use installed software such as office applications like MS Excel and MS PowerPoint, web browsers, and email. A standard user is not allowed to install new software, or create, edit, or delete system files. System files are those files that are needed to keep the operating system of the workstation working properly. To make these types of changes, you need privileges that come with an administrator account.
Importance of Policies
Policies are one of the first places an auditor should start when auditing workstations. Policies will define the level of compliance required and the strength of the security controls to be deployed. Policies will often identify who is accountable for deploying workstations and, thus, point the auditor in the direction to obtain the supporting process documentation. It’s rare that an organization installs a clean operating system and configures each machine from scratch for each newly purchased computer. Doing so would increase the likelihood of human errors, that could lead to expensive and dangerous as each workstation is potentially applying different levels of security controls.
As applications, technology, and the needs of your organization change over time, it’s important to keep these workstation images up to date. This includes at a minimum an annual security review. This will ensure you know how all the systems are configured. If security software and policies are put into place based on how one set of computers is configured, the outlier computers can be more readily identified.
Security policies are good at outlining the rules for protecting the workstation. Let us consider a security policy that states “all data at rest that are stored outside the organization network must be encrypted.” Would this typically apply to workstations behind locked doors in the nonpublic offices in the corporate headquarters? Probably not. Those corporate offices would be using the corporate network to connect those desktop computers. How about laptops? Yes! Because laptops are portable and can be used outside the corporate offices, the laptop’s hard drive would need to be encrypted. With the increased use of mobile computing, it’s common for sensitive data to leave the network. As a result, many companies that handle sensitive information encrypt employee laptop hard drives. That way, in the event the laptop is lost or stolen the sensitive data remain protected.
While not an exhaustive list, the following illustrates common workstation policies:
- Password complexity such as lengthy passwords
- Screen lock after a certain amount of idle time and requiring authentication to get back in
- USB port access restrictions limit the ability to copy company data to an unencrypted thumb drive
- Personal usage outlining many employees use their devices such as browsing nonwork websites
- Loss and theft to make sure employees have a clear process to follow if their work device gets lost or stolen.
Protecting Data Privacy
Many recent legislative and regulatory requirements extend the scope of threats to information to include all users. There is no assurance users will be compliant. Organizations need additional layers of controls to protect information because not all threats come from malicious users. Some threats come from simple ignorance. For example, procedural changes might prohibit users from transferring protected files to remote workstations. Properly trained users should not attempt to transfer files to remote workstations, but well-meaning users who are not aware of the new policy might unknowingly violate the policy. The proper way to handle this situation is to do the following:
- Ensure all users receive updated training.
- Place access controls in the Workstation Domain to prohibit inappropriate actions such as encrypting laptop hard drives.
You need both types of controls to secure information from all users.
Increased attention to security increases the need to hold employees accountable for security. Because employees generally have more access to information than other authorized users do, they have greater ability to affect the information’s security. A greater ability to affect security means you need a greater scope of controls. The most common concern for information security that is reflected in most recent legislation is protecting information privacy. Although information integrity and availability are important, privacy is a primary concern of many regulations. All information system users are accountable for the privacy of the information they access. This puts a greater amount of responsibility and accountability on users.
A solid security strategy should include several types of controls to ensure user compliance. You’ve already seen some controls in the User Domain. The Workstation Domain is the domain that contains the devices and components to access information. Controlling activities in the Workstation Domain can provide an effective layer of information security. Workstation Domain controls should validate and support controls in other domains. Although controls in the User Domain are important, you need additional controls to ensure compliance with your security policy and any additional security requirements. Controls in the Workstation Domain should work with controls in other domains to ensure a high level of overall compliance.
Implementing Proper Security Controls for the Workstation Domain
Computers prepared by major manufacturers come preloaded with software and user accounts with default passwords. It is not unusual to find preloaded software with known security vulnerabilities that have been common targets by hackers. Even seemingly common original equipment manufacturer (OEM) applications, firmware, and hardware drivers can make the new workstation already vulnerable.
Not properly configuring the workstation can be costly. If you have a workstation on which the system has been irreparably damaged by a virus or just an ill-timed power outage, restoring it to its OEM state may not solve the underlining security vulnerability. Especially, if you don’t have spare computers properly imaged ready to go, this also means lost hours of productivity for the staff.
Workstation Domain controls are security controls that prohibit, validate, or detect user actions. Users initiate actions in the Workstation Domain that generally involve some stored information. In short, users generally access information using some type of workstation device. It makes sense to place controls at the workstation level to ensure information access is compliant. Proper controls in the Workstation Domain should work with other controls in all domains to enforce compliance without interrupting normal operation.
For example, the Payment Card Industry Data Security Standard (PCI DSS) prohibits merchants from storing the card verification value (CVV). The CVV is a three- or four-digit number that card issuers print on each credit card. The CVV provides additional authentication when rendering payment for online transactions. One control to avoid storing the CVV is to remove any user prompts for the CVV. Although that complies with the PCI DSS data requirement, it also disables the merchant’s ability to ask for the CVV to authenticate the transaction. You should not implement this control because it interrupts a necessary business function. Look for another control that balances security and business requirements.
Management Systems
Workstation security is often a matter of determining some basic security configuration rules and applying them consistently across your enterprise. Applying such security without disrupting the business is a concern. The days of sending a person to each desk to configure a workstation for most organizations are long past. Security policies can help establish a reliable patch management process that is automated. Security policies can specify the type and frequency of patches that need to be applied. The policies often require such patches to be tested in a lab setting before being applied to workstations. Changes are typically rolled out through management systems across the workstation population.
Workstations are typically managed by a central management system that can update software, apply patches, and update configuration as needed. These management systems have evolved and help apply workstation changes in a timely manner. These systems are capable of many functions:
-
Inventory—Refers to tracking assets such as workstations and what software is installed
-
Patch management—Refers to applying patches to workstation operating system and software
-
Help desk—Refers to allowing help desk technical personnel to remotely access the workstation
-
Log—Refers to capturing workstation logs for forensic and support purposes
-
Security—Refers to ensuring security configurations are appropriately maintained
