LAN Domain Business Drivers
An organization has two main security concerns when it comes to information collected, stored, and processed: Is the information safe? Can you prevent confidential information from leaving the organization? These seem like easy questions but are complicated to answer. In part, these questions are answered through well-defined policies. Security policies ensure alignment to business requirements. When risks exist, security policies ensure a risk assessment is performed so that management can make a balanced decision.
Network auditing refers to the process of gathering, analyzing, and studying network data to assess the network’s health. Network auditing gives businesses insight into how successful their network control, risk assessments, and management operations are, particularly regarding both internal policy and external compliance regulations.
Network auditing typically involves analyzing the following network components:
Business products and goals
Network risk assessments
Control implementation
Availability
Security
Management
Performance
As part of network audits planning, a deep understanding of the business products and goals is essential to understanding if the right network resources are in place. An organization whose revenue is primarily built on having an Internet presence may have very different network needs than a business selling products at a retail store location.
A denial-of-service (DoS) attack occurs by flooding the targeted host on a network with traffic until the target host cannot respond or simply crashes. What does this mean for the user? Legitimate users like customers are unable to access information, products, and services. DoS attacks have many costs, such as reputation, inability to service customers, time and resources to restore services, systems, devices, or other network resources due to the actions of a malicious cyberthreat actor. Services affected may include email, websites, online accounts (e.g., banking), or other services that rely on the affected computer or network. A denial-of-service condition is accomplished by preventing access for legitimate users.
As LANs become increasingly useful to authorized users and attackers, it is more important than ever to ensure compliance to policies and industry norms within the LAN Domain. Figure 10-1 shows the LAN Domain in the context of the seven domains in the IT infrastructure.
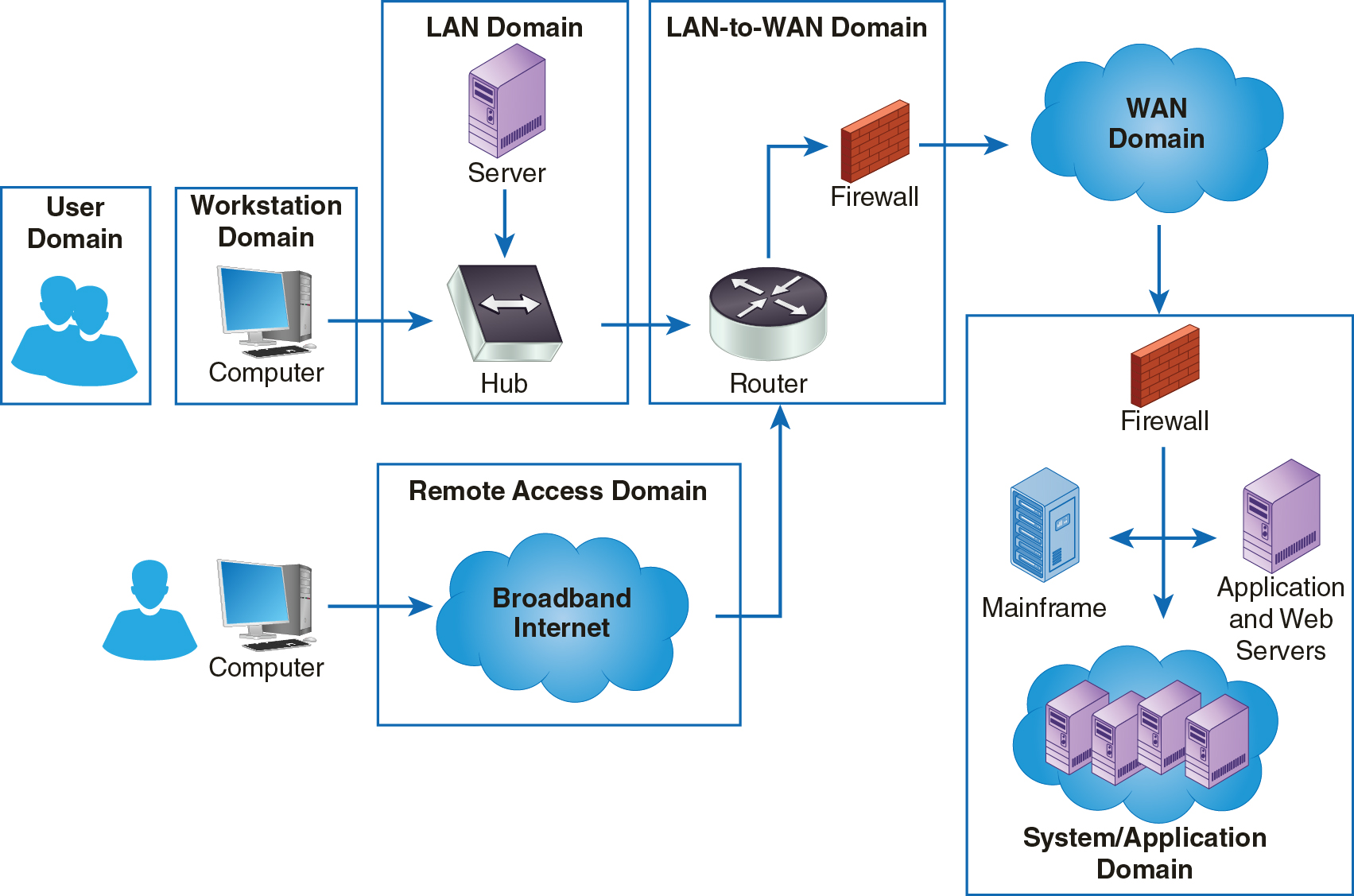
FIGURE 10-1 The LAN Domain within the seven domains of a typical IT infrastructure
Organizations rely on networked resources more than ever in today’s environments. LANs make it possible to share expensive resources, such as color printers and high-performance disk subsystems. LANs enable more efficiency in critical business functions by supporting faster information transfer and resource sharing. These benefits often result in direct cost reductions and productivity increases. Organizations rely on LAN resources to maintain cost-efficient operations. Protecting the LAN-based services directly affects costs and efficiency. A solid security policy that includes compliance with all appropriate requirements should support efficient and cost-effective operations. Implementing the controls necessary to support your security policy in the LAN Domain makes your organization more secure and more effective.
Data Leakage Protection
In this section, you will focus on the business concern of how to prevent confidential information from leaving the organization. Network capability plays a significant role as do other domains such as User and System/Application. Data leakage protection (DLP) does overlap some with other domains.
Security policies define what’s often called either a data loss protection (DLP) or a data leakage protection (DLP) program. Both terms refer to a formal program that reduces the likelihood of accidental or malicious loss of data leaving the network.
Company managers worry about secret business information ending up in competitors’ hands. Managers must also protect customer privacy as required by law. A hacker does not have to be physically present to steal your business secrets, especially if the hacker is a disgruntled employee who might work in a data-sensitive area of the company. Your top salesperson might leave the company to work for a competitor and email your entire sales database to his home Internet account. These are not theoretical losses to a business. You must ensure that all of your potential data leaks, both physical and digital, are plugged.
The concept of DLP comes from the acknowledgment that data are often copied, change form, move, and are stored in many places. This sensitive data often leave the protection of application databases and end up in emails, spreadsheets, and personal workstation files. Business is most concerned about data that live outside the hardened protection of an application.
A typical DLP program provides several layers of defense to prevent confidential data from leaving the network, including the following examples:
Network device connectivity—Limiting device connectivity also limits data flow.
Network monitoring and blocking—Network traffic is monitored, and unusual data traffic leaving the network is blocked based on defined thresholds.
Classifying and tagging data—Data labeled confident or sensitive can be more easily identified and blocked from leaving the network.
Encryption of end-user devices—Data residing in end-user devices remain protected.
Communication monitoring and blocking—Communication is monitored, and emailing confidential data, such as files, to a personal “Gmail” or “Hotmail” account is blocked.
Inventory
The DLP inventory component attempts to identify where sensitive data may be stored. This inventory includes both the network devices and the application. An inventory would include scanning workstations, email folders, and file servers. The process requires inspecting the content of files and determining if they contain sensitive information such as Social Security numbers. Once identified, data would be appropriately classified, and the access rights adjusted as needed. For example, this helps prevent private customer information from accidentally being stored in a public email folder.
“Flat” networks are a challenge at a network layer. These are networks with little to no segmentation. The result is virtually all network devices can talk to each other. This approach simplifies network management and reduces maintenance costs. The problem is it does not allow confidential and sensitive data to be isolated and protected. Worse yet, once the network is hacked, all devices on the network are potential targets. Understanding the network topography is an important part of the network audit.
Perimeter
The DLP perimeter component ensures that data are protected on every endpoint on your network, regardless of the operating system or type of device. It checks data as it moves, including writing data to non-network services and devices such as email, CDs, USB devices, instant messaging, and print.
When sensitive data are written to an unauthorized device, the technology can either stop and archive the file or send an alternate. It stops data loss initiated by malware and file-sharing that can hijack employee information.
You can also establish and manage security policies to regulate and restrict how your employees use and transfer sensitive data. It uses the same basic technology that is applied with the inventory component. It has the same limitations. Because you are dealing with data movement, you can add rules not often found in the inventory process, such as not permitting certain file types, such as database files, to be emailed. Regardless of content, these rules can stop a hacker from sending a large volume of data outside the network.
Encryption of Mobile Devices
In many ways, mobile devices like phones are mobile external hard drives. It’s the same information that can sit on a workstation or server. When an executive receives an email on an upcoming merger or a doctor about a patient, the information needs the same protection as if it were on a workstation or server. The information on mobile devices is subject to the same regulatory requirements. This means you must also apply the same level of controls, such as encryption. Mobile devices are physically outside your control. The hard drive of mobile devices can be removed and scanned. While physically removing the mobile drive cannot be prevented, encrypting it means the data are useless and only be accessed by an authorized user.
Implementing Proper Security Controls for the LAN Domain
A LAN in the business world is far more complex than a home network. The business LAN has many layers of controls. Let’s look at two general types of LANs, flat and segmented networks.
As discussed, a flat network has little to no controls to limit network traffic. When a workstation connects to a flat network, the workstation can communicate with any other computer on the network. Think of a flat network as an ordinary neighborhood with each home representing a network device. Anyone can drive into the neighborhood and knock on any door. This does not mean whoever answers the door will let the visitor in. However, the visitor has the opportunity to talk their way in. In the case of flat networks, you can talk your way in by being authorized or by breaching a server, such as guessing the right ID and password combination. Flat networks are considered less secure than segmented networks because they rely on each computer (i.e., each home on the block) to withstand every possible type of breach. They are also less secure because every computer in the network can potentially see all the network traffic. This means a computer with a sniffer can monitor a sizable portion of the communication with a LAN.
A segmented network limits what and how computers can talk to each other. By using switches, routers, internal firewalls, and other devices, you can restrict network traffic. Continuing the analogy from the previous paragraph, think of a segmented network as a gated community. To access that neighborhood, you must first approach a gate with a guard. The guard opens the gate only for certain traffic to enter the community. Once inside, you can knock on any door. A segmented network acts as a guard, filtering out unauthorized network traffic. Many standards like Payment Card Industry Data Security Standard (PCI DSS) require network segmentation to further protect credit cardholder information.
Why do you want to segment a network? The basic idea is that by limiting certain types of traffic to a group of computers, you are eliminating a number of threats. For example, if you have a database server with sensitive information that by design should only receive database calls (such as Structured Query Language (SQL) traffic), why allow File Transfer Protocol (FTP) traffic? If the server is not properly configured, the FTP service could be used as a method to hack into the computer. By eliminating the FTP traffic, you have effectively eliminated that attack vector. You should still make sure the server is properly configured to prevent such an attack. However, you reduced the likelihood of a successful breach because the attacker must first breach the segment (i.e., get by the guard at the gate) and then breach the database server (i.e., break down the door). Security is never absolute, but segmenting your network creates layers of security that dramatically reduce the likelihood of a data breach.
The following network devices are commonly found on LANs:
Switch—A switch connects multiple devices within a LAN. A switch has ports that can filter traffic. You can set up rules that control what traffic can flow where. A switch can route traffic only to the port to which the system is connected. This reduces the amount of network traffic, thus reducing the chance that someone will intercept communication. The ability to configure a switch to control traffic is a real advantage to blocking potential hacks of the network.
Router—A router connects LANs or a LAN and a WAN.
Firewall—A firewall comprises software or hardware device that filters the traffic in and out of a LAN. Many firewalls can do deep-packet inspections in which the firewall examines the contents of the traffic as well as the type of traffic. A firewall can be used internally on the network to further protect segments and isolate sensitive and confidential data. Firewalls are most used to filter traffic between the public Internet WAN and the internal private LAN.
